- Home
- Paloalto Networks
- PSE-Software Firewall Professional
- PSE-SWFW-Pro-24
- Palo Alto Networks Systems Engineer Professional - Software Firewall Questions and Answers
PSE-SWFW-Pro-24 Palo Alto Networks Systems Engineer Professional - Software Firewall Questions and Answers
Which three resources can help conduct planning and implementation of Palo Alto Networks NGFW solutions? (Choose three.)
Options:
Technical assistance center (TAC)
Partners / systems Integrators
Professional services
Proof of Concept Labs
QuickStart services
Answer:
B, C, EExplanation:
Several resources are available to assist with planning and implementing Palo Alto Networks NGFW solutions:
A. Technical assistance center (TAC): While TAC provides support for existing deployments, they are generally not directly involved in the initial planning and implementation phases. TAC helps with troubleshooting and resolving issues after the firewall is deployed.
B. Partners / systems Integrators: Partners and system integrators play a crucial role in planning and implementation. They possess expertise in network design, security best practices, and Palo Alto Networks products, enabling them to design and deploy solutions tailored to customer needs.
C. Professional services: Palo Alto Networks professional services offer expert assistance with all phases of the project, from planning and design to implementation and knowledge transfer. They can provide specialized skills and best-practice guidance.
D. Proof of Concept Labs: While valuable for testing and validating solutions, Proof of Concept (POC) labs are more focused on evaluating the technology before a full-scale implementation. They are not the primary resources for the actual planning and implementation process itself, though they can inform it.
E. QuickStart services: QuickStart packages are a type of professional service specifically designed for rapid deployment. They provide a structured approach to implementation, accelerating the time to value.
References:
Information about these resources can be found on the Palo Alto Networks website and partner portal:
Partner locator: The Palo Alto Networks website has a partner locator tool to find certified partners and system integrators.
Professional services: Details about Palo Alto Networks professional services offerings, including QuickStart packages, are available on their website.
These resources confirm that partners/system integrators, professional services (including QuickStart), are key resources for planning and implementation. While TAC and POCs have roles, they are not the primary resources for this phase.
What is the primary purpose of the pan-os-python SDK?
Options:
To create a Python-based firewall that is compatible with the latest PAN-OS
To replace the PAN-OS web interface with a Python-based interface
To automate the deployment of PAN-OS firewalls by using Python
To provide a Python interface to interact with PAN-OS firewalls and Panorama
Answer:
DExplanation:
The question asks about the primary purpose of the pan-os-python SDK.
D. To provide a Python interface to interact with PAN-OS firewalls and Panorama: This is the correct answer. The pan-os-python SDK (Software Development Kit) is designed to allow Python scripts and applications to interact programmatically with Palo Alto Networks firewalls (running PAN-OS) and Panorama. It provides functions and classes that simplify tasks like configuration management, monitoring, and automation.
Why other options are incorrect:
A. To create a Python-based firewall that is compatible with the latest PAN-OS: The pan-os-python SDK is not about creating a firewall itself. It's a tool for interacting with existing PAN-OS firewalls.
B. To replace the PAN-OS web interface with a Python-based interface: While you can build custom tools and interfaces using the SDK, its primary purpose is not to replace the web interface. The web interface remains the standard management interface.
C. To automate the deployment of PAN-OS firewalls by using Python: While the SDK can be used as part of an automated deployment process (e.g., in conjunction with tools like Terraform or Ansible), its core purpose is broader: to provide a general Python interface for interacting with PAN-OS and Panorama, not just for deployment.
Palo Alto Networks References:
The primary reference is the official pan-os-python SDK documentation, which can be found on GitHub (usually in the Palo Alto Networks GitHub organization) and is referenced on the Palo Alto Networks Developer portal. Searching for "pan-os-python" on the Palo Alto Networks website or on GitHub will locate the official repository.
The documentation will clearly state that the SDK's purpose is to:
Provide a Pythonic way to interact with PAN-OS devices.
Abstract the underlying XML API calls, making it easier to write scripts.
Support various operations, including configuration, monitoring, and operational commands.
The documentation will contain examples demonstrating how to use the SDK to perform various tasks, reinforcing its role as a Python interface for PAN-OS and Panorama.
Per reference architecture, which default PAN-OS configuration should be overridden to make VM-Series firewall deployments in the public cloud more secure?
Options:
Intrazone-default rule action and logging
Intrazone-default rule service
Interzone-default rule action and logging
Interzone-default rule service
Answer:
CExplanation:
Comprehensive and Detailed In-Depth Step-by-Step Explanation:The Palo Alto Networks Systems Engineer Professional - Software Firewall documentation, particularly the reference architectures for VM-Series firewalls in public cloud environments (e.g., AWS, Azure, GCP), provides best practices for securing deployments. By default, PAN-OS includes predefined security rules like the interzone-default and intrazone-default rules, which need adjustment to enhance security in cloud settings.
Interzone-default rule action and logging (Option C): In PAN-OS, the interzone-default rule is applied to traffic between different security zones (e.g., traffic between a public cloud subnet and an on-premises network). By default, this rule allows all traffic with logging enabled, which can pose a security risk in public cloud environments where traffic should be restricted by default. The reference architecture recommends overriding this rule to deny all interzone traffic by default (changing the action from “allow” to “deny”) and enabling logging to monitor and control traffic more securely. This aligns with the principle of least privilege and enhances security for VM-Series deployments in public clouds, as outlined in the documentation’s security best practices.
Options A (Intrazone-default rule action and logging), B (Intrazone-default rule service), and D (Interzone-default rule service) are incorrect. The intrazone-default rule applies to traffic within the same security zone and typically allows traffic by default, but it is less critical to override in public cloud deployments compared to the interzone rule, as intrazone traffic is often trusted. Changing the “service” (Options B, D) rather than the action and logging is not the primary focus for enhancing security; the action (allow/deny) and logging configuration are more significant for securing traffic flows in VM-Series deployments.
References: Palo Alto Networks Systems Engineer Professional - Software Firewall, Section: VM-Series Reference Architectures, PAN-OS Security Policy Guide, Public Cloud Security Best Practices.
Which statement applies when identifying the appropriate Palo Alto Networks firewall platform for virtualized as well as cloud environments?
Options:
VM-Series firewalls cannot be used to protect container environments.
All NGFW platforms support API integration.
Panorama is the only unified management console for all NGFWs.
CN-Series firewalls are used to protect virtualized environments.
Answer:
BExplanation:
A. VM-Series firewalls cannot be used to protect container environments: This is incorrect. While CN-Series is specifically designed for container environments, VM-Series can also be used in certain container deployments, often in conjunction with other container networking solutions. For example, VM-Series can be deployed as a gateway for a Kubernetes cluster.
B. All NGFW platforms support API integration: This is correct. Palo Alto Networks firewalls, including PA-Series (hardware), VM-Series (virtualized), CN-Series (containerized), and Cloud NGFW, offer robust API support for automation, integration with other systems, and programmatic management. This is a core feature of their platform approach.
C. Panorama is the only unified management console for all NGFWs: This is incorrect. While Panorama is a powerful centralized management platform, it's not the only option. Individual firewalls can be managed locally via their web interface or CLI. Additionally, Cloud NGFW has its own management interface within the cloud provider's console.
D. CN-Series firewalls are used to protect virtualized environments: This is incorrect. CN-Series is specifically designed for containerized environments (e.g., Kubernetes, OpenShift), not general virtualized environments. VM-Series is the appropriate choice for virtualized environments (e.g., VMware vSphere, AWS EC2).
Where are auth codes registered in the bootstrapping process?
Options:
ESXi server manifest
AutoConfig template
Palo Alto Networks Support Portal
Palo Alto Networks App Hub
Answer:
CExplanation:
Comprehensive and Detailed In-Depth Step-by-Step Explanation:Bootstrapping is an automation method for VM-Series firewalls that simplifies initial deployment, configuration, licensing, and content updates. The Palo Alto Networks Systems Engineer Professional - Software Firewall documentation details the process, including how authentication codes (auth codes) are managed during bootstrapping.
Palo Alto Networks Support Portal (Option C): Auth codes, which are used to activate licenses for VM-Series firewalls, must be registered in the Palo Alto Networks Customer Support Portal (also referred to as the Support Portal). During the bootstrapping process, the auth codes are included in the bootstrap package (e.g., in the license file or init-cfg.txt) and are validated against the serial number of the firewall. The Support Portal is where customers register auth codes, generate licenses, and manage credit-based licensing, ensuring the firewall is properly licensed during automated deployment. The documentation emphasizes the Support Portal as the central location for auth code registration and licensing management.
Options A (ESXi server manifest), B (AutoConfig template), and D (Palo Alto Networks App Hub) are incorrect. An ESXi server manifest (Option A) is specific to VMware ESXi and does not handle auth code registration for Palo Alto Networks firewalls. An AutoConfig template (Option B) is not a recognized term in the bootstrapping context; the correct file is init-cfg.txt, but it does not register auth codes—it uses them after registration. The Palo Alto Networks App Hub (Option D) focuses on application visibility and control, not licensing or auth code registration, making it irrelevant for this process.
References: Palo Alto Networks Systems Engineer Professional - Software Firewall, Section: Bootstrapping Guide, VM-Series Licensing Documentation, Customer Support Portal Documentation.
Which two capabilities are shared by the deployments of Cloud NGFW for Azure and VM-Series firewalls? (Choose two.)
Options:
Using NGFW credits to deploy the firewall
Securing public and private datacenter traffic
Performing firewall administration using Azure Firewall Manager
Securing inbound, outbound, and lateral traffic
Answer:
A, DExplanation:
Comprehensive and Detailed In-Depth Step-by-Step Explanation:Both Cloud NGFW for Azure and VM-Series firewalls are Palo Alto Networks solutions designed to secure cloud and virtualized environments, but they share specific capabilities as outlined in the Palo Alto Networks Systems Engineer Professional - Software Firewall documentation.
Using NGFW credits to deploy the firewall (Option A): Both Cloud NGFW for Azure and VM-Series firewalls can be deployed using Palo Alto Networks’ NGFW credit-based flexible licensing model. This allows customers to allocate credits from a credit pool to deploy and manage these firewalls in Azure, providing flexibility and cost efficiency without requiring separate licenses for each instance. The documentation emphasizes this as a shared licensing approach for software firewalls in cloud environments.
Securing inbound, outbound, and lateral traffic (Option D): Both solutions provide comprehensive traffic protection, including inbound (external to internal), outbound (internal to external), and lateral (east-west) traffic within the cloud environment. This is a core capability of both Cloud NGFW for Azure, which uses a distributed architecture, and VM-Series, which can be configured for similar traffic flows in virtualized or cloud settings, ensuring full visibility and control over all network traffic.
Options B (Securing public and private datacenter traffic) and C (Performing firewall administration using Azure Firewall Manager) are incorrect. While both firewalls can secure traffic, they are primarily designed for cloud environments, not explicitly for public and private datacenter traffic as a shared capability. Azure Firewall Manager is a native Azure tool and does not manage Palo Alto Networks Cloud NGFW or VM-Series firewalls, making Option C inaccurate for this context.
References: Palo Alto Networks Systems Engineer Professional - Software Firewall, Section: Cloud NGFW and VM-Series Deployment, Flexible Licensing Documentation, Traffic Security and Policy Enforcement Guide for Azure and VM-Series.
A prospective customer wants to deploy VM-Series firewalls in their on-premises data center, CN-Series firewalls in Azure, and Cloud NGFWs in Amazon Web Services (AWS). They also require centralized management.
Which solution meets the requirements?
Options:
NGFW Software credits and Strata Cloud Manager (SCM)
Fixed VM-Series firewalls, Cloud NGFW credits, and Panorama
NGFW Software credits, Cloud NGFW, and Strata Cloud Manager (SCM)
NGFW Software credits and Panorama
Answer:
DExplanation:
Comprehensive and Detailed In-Depth Step-by-Step Explanation:The customer’s requirements involve deploying three different Palo Alto Networks software firewalls—VM-Series (on-premises), CN-Series (Azure), and Cloud NGFW (AWS)—and requiring centralized management. The Palo Alto Networks Systems Engineer Professional - Software Firewall documentation provides guidance on licensing and management solutions for multi-environment deployments.
NGFW Software credits and Panorama (Option D): NGFW credit-based flexible licensing allows the customer to allocate credits for VM-Series, CN-Series, and Cloud NGFW deployments across on-premises, Azure, and AWS environments. Panorama, Palo Alto Networks’ centralized management platform, can manage all three firewall types: VM-Series for on-premises data centers, CN-Series for containerized workloads in Azure, and Cloud NGFW for AWS (via integration with cloud APIs). The documentation specifies that Panorama provides unified policy management, logging, and monitoring for software firewalls, regardless of deployment location, making it the ideal solution for centralized management. NGFW credits simplify licensing across these environments, ensuring flexibility and scalability.
Options A (NGFW Software credits and Strata Cloud Manager [SCM]), B (Fixed VM-Series firewalls, Cloud NGFW credits, and Panorama), and C (NGFW Software credits, Cloud NGFW, and Strata Cloud Manager [SCM]) are incorrect. SCM (Options A, C) is designed for cloud-delivered security services and does not fully support on-premises VM-Series or CN-Series management to the extent Panorama does, as Panorama is the standard management solution for all three firewall types. Fixed VM-Series firewalls (Option B) are not flexible and do not align with the customer’s need for scalable, credit-based licensing, which is better suited for software firewalls across clouds. Option C redundantly mentions Cloud NGFW and does not add value beyond what Panorama and NGFW credits already provide, while SCM is not necessary for this specific multi-environment setup.
References: Palo Alto Networks Systems Engineer Professional - Software Firewall, Section: Multi-Cloud Deployment, Flexible Licensing Overview, Panorama Management Documentation, VM-Series, CN-Series, and Cloud NGFW Deployment Guides.
Which method fully automates the initial deployment, configuration, licensing, and threat content download when setting up a new VM-Series firewall?
Options:
Register the VM-Series firewall and launch the Day 1 Configuration Wizard.
Use Panorama to push device groups and template stack configurations to the new VM-Series firewall.
Deploy a complete bootstrap package by using an ISO image, block storage, or a storage bucket.
Connect the VM-Series firewall to Panorama and push the configuration package by using the bootstrap plugin.
Answer:
CExplanation:
Comprehensive and Detailed In-Depth Step-by-Step Explanation:Automating the deployment of VM-Series firewalls is essential for scalability and efficiency in cloud and virtualized environments. The Palo Alto Networks Systems Engineer Professional - Software Firewall documentation provides detailed guidance on automation methods, with bootstrapping being the most comprehensive approach.
Deploy a complete bootstrap package by using an ISO image, block storage, or a storage bucket (Option C): Bootstrapping is the most automated method for deploying a VM-Series firewall. A bootstrap package includes all necessary files—init-cfg.txt (for initial configuration), license files, authentication codes, and content updates (e.g., application and threat signatures)—stored in a location accessible to the VM (e.g., an ISO image, AWS S3 bucket, Azure Blob storage, or GCP storage bucket). When the VM-Series firewall boots, it automatically retrieves and applies these files, completing initial deployment, configuration, licensing, and threat content downloads without manual intervention. The documentation emphasizes bootstrapping as the preferred method for fully automated, zero-touch deployments in public clouds, private clouds, or on-premises environments.
Options A (Register the VM-Series firewall and launch the Day 1 Configuration Wizard), B (Use Panorama to push device groups and template stack configurations to the new VM-Series firewall), and D (Connect the VM-Series firewall to Panorama and push the configuration package by using the bootstrap plugin) are incorrect. The Day 1 Configuration Wizard (Option A) requires manual interaction and does not fully automate all steps, such as licensing and content downloads. Using Panorama to push configurations (Options B, D) requires the firewall to be initially deployed and connected to Panorama, which is not fully automated for initial setup; it assumes manual steps or partial automation, not covering licensing and content downloads comprehensively like bootstrapping. There is no specific “bootstrap plugin” mentioned in the documentation for Panorama in this context, making Option D inaccurate.
References: Palo Alto Networks Systems Engineer Professional - Software Firewall, Section: VM-Series Deployment Automation, Bootstrapping Guide, VM-Series Licensing and Configuration Documentation.
Which two products are deployed with Terraform for high levels of automation and integration? (Choose two.)
Options:
Cloud NGFW
VM-Series firewall
Cortex XSOAR
Prisma Access
Answer:
A, BExplanation:
Terraform is an Infrastructure-as-Code (IaC) tool that enables automated deployment and management of infrastructure.
Why A and B are correct:
A. Cloud NGFW: Cloud NGFW can be deployed and managed using Terraform, allowing for automated provisioning and configuration.
B. VM-Series firewall: VM-Series firewalls are commonly deployed and managed with Terraform, enabling automated deployments in public and private clouds.
Why C and D are incorrect:
C. Cortex XSOAR: While Cortex XSOAR can integrate with Terraform (e.g., to automate workflows related to infrastructure changes), XSOAR itself is not deployed with Terraform. XSOAR is a Security Orchestration, Automation, and Response (SOAR) platform.
D. Prisma Access: While Prisma Access can be integrated with other automation tools, the core Prisma Access service is not deployed using Terraform. Prisma Access is a cloud-delivered security platform.
Palo Alto Networks References:
Terraform Registry: The Terraform Registry contains official Palo Alto Networks providers for VM-Series and Cloud NGFW. These providers allow you to define and manage these resources using Terraform configuration files.
Palo Alto Networks GitHub Repositories: Palo Alto Networks maintains GitHub repositories with Terraform examples and modules for deploying and configuring VM-Series and Cloud NGFW.
Palo Alto Networks Documentation on Cloud NGFW and VM-Series: The official documentation for these products often includes sections on automation and integration with tools like Terraform.
These resources clearly demonstrate that VM-Series and Cloud NGFW are designed to be deployed and managed using Terraform.
Which three statements describe restrictions or characteristics of Firewall flex credit profiles of a credit pool in the Palo Alto Networks customer support portal? (Choose three.)
Options:
The number of licensed cores must match the number of provisioned CPU cores per instance.
Allocate credits for use with Cloud NGFW for AWS and Azure.
Each VM-Series firewall deployment profile is either fixed or flexible.
All firewalls activated to a deployment profile will have the same Cloud-Delivered Security Services (CDSS).
Each deployment profile is either CN-Series firewall or VM-Series firewall.
Answer:
A, C, DExplanation:
Firewall flex credits have specific characteristics.
Why A, C, and D are correct:
A: For flex credits, the number of licensed cores must match the number of provisioned CPU cores. This is a key requirement for accurate credit consumption.
C: Deployment profiles are either fixed (predefined resources) or flexible (using credits).
D: All firewalls within a deployment profile share the same Cloud-Delivered Security Services (CDSS) subscriptions.
Why B and E are incorrect:
B: Flex credits are the mechanism used to deploy Cloud NGFW instances in AWS and Azure, not a separate allocation.
E: Deployment profiles are for VM-Series firewalls. CN-Series firewalls have their own licensing and deployment models.
Palo Alto Networks References: The official Palo Alto Networks documentation on VM-Series licensing, flex credits, and deployment profiles contains this information.
What three benefits does flex licensing for VM-Series firewalls offer? (Choose three.)
Options:
Licensing additional memory resources to increase session capacity
Licensing Strata Cloud Manager, Panorama with Dedicated Log Collectors, and CDSS per deployment profile
Using a pool of credits for both CN-Series firewall and VM-Series firewall deployment profiles
Moving credits between public and private cloud VM-Series firewall deployments
Vertically scaling the number of licensed cores in an existing fixed deployment profile
Answer:
C, D, EExplanation:
Flex licensing provides flexibility in how you consume Palo Alto Networks firewall capabilities, especially in cloud environments:
A. Licensing additional memory resources to increase session capacity: Flex licensing primarily focuses on CPU cores and does not directly license memory resources. Memory is tied to the instance size you select in the cloud provider.
B. Licensing Strata Cloud Manager, Panorama with Dedicated Log Collectors, and CDSS per deployment profile: Strata Cloud Manager, Panorama, and CDSS are licensed separately and are not part of the flex licensing model for VM-Series.
C. Using a pool of credits for both CN-Series firewall and VM-Series firewall deployment profiles: This is a key benefit of flex licensing. You can use a shared pool of credits to deploy both CN-Series (containerized) and VM-Series (virtual machine) firewalls, providing flexibility in your deployment strategy.
D. Moving credits between public and private cloud VM-Series firewall deployments: This is another significant advantage. Flex licensing allows you to transfer credits between public cloud (AWS, Azure, GCP) and private cloud VM-Series deployments, optimizing resource utilization and cost.
E. Vertically scaling the number of licensed cores in an existing fixed deployment profile: Flex licensing allows you to dynamically adjust the number of licensed cores for your VM-Series firewalls. This vertical scaling enables you to meet changing performance demands without needing to redeploy or reconfigure your firewalls significantly.
References:
Palo Alto Networks Flex Licensing documentation: Search for "Flex Licensing" on the Palo Alto Networks support portal. This documentation provides detailed information about the flex licensing model, including the benefits and use cases.
This documentation confirms that sharing credits between CN-Series and VM-Series, moving credits between public and private clouds, and vertically scaling licensed cores are core benefits of flex licensing.
A company that purchased software NGFW credits from Palo Alto Networks has made a decision on the number of virtual machines (VMs) and licenses they wish to deploy in AWS cloud.
How are the VM licenses created?
Options:
Access the AWS Marketplace and use the software NGFW credits to purchase the VMs.
Access the Palo Alto Networks Application Hub and create a new VM profile.
Access the Palo Alto Networks Customer Support Portal and request the creation of a new software NGFW serial number.
Access the Palo Alto Networks Customer Support Portal and create a software NGFW credits deployment profile.
Answer:
DExplanation:
The question focuses on how VM licenses are created when a company has purchased software NGFW credits and wants to deploy VM-Series firewalls in AWS.
D. Access the Palo Alto Networks Customer Support Portal and create a software NGFW credits deployment profile. This is the correct answer. The process starts in the Palo Alto Networks Customer Support Portal. You create a deployment profile that specifies the number and type of VM-Series licenses you want to deploy. This profile is then used to activate the licenses on the actual VM-Series instances in AWS.
Why other options are incorrect:
A. Access the AWS Marketplace and use the software NGFW credits to purchase the VMs. You do deploy the VM-Series instances from the AWS Marketplace (or through other deployment methods like CloudFormation templates), but you don't "purchase" the licenses there. The credits are managed separately through the Palo Alto Networks Customer Support Portal. The Marketplace deployment is for the VM instance itself, not the license.
B. Access the Palo Alto Networks Application Hub and create a new VM profile. The Application Hub is not directly involved in the license creation process. It's more focused on application-level security and content updates.
C. Access the Palo Alto Networks Customer Support Portal and request the creation of a new software NGFW serial number. You don't request individual serial numbers for each VM. The deployment profile manages the allocation of licenses from your pool of credits. While each VM will have a serial number once deployed, you don't request them individually during this stage. The deployment profile ties the licenses to the deployment, not individual serial numbers ahead of deployment.
Palo Alto Networks References:
The Palo Alto Networks Customer Support Portal documentation and the VM-Series Deployment Guide are the primary references. Search the support portal (live.paloaltonetworks.com) for "software NGFW credits," "deployment profile," or "VM-Series licensing."
The documentation will describe the following general process:
Purchase software NGFW credits.
Log in to the Palo Alto Networks Customer Support Portal.
Create a deployment profile, specifying the number and type of VM-Series licenses (e.g., VM-Series for AWS, VM-Series for Azure, etc.) you want to allocate from your credits.
Deploy the VM-Series instances in your cloud environment (e.g., from the AWS Marketplace).
Activate the licenses on the VM-Series instances using the deployment profile.
This process confirms that creating a deployment profile in the customer support portal is the correct way to manage and allocate software NGFW licenses.
A company wants to make its flexible-license VM-Series firewall, which runs on ESXi, process higher throughput.
Which order of steps should be followed to minimize downtime?
Options:
1. Increase the vCPU within the deployment profile.
2. Retrieve or fetch license keys on the VM-Series NGFW.
3. Confirm the correct tier level and vCPU appear on the NGFW dashboard.
4. Power-off the VM and increase the vCPUs within the hypervisor.
5. Power-on the VM-Series NGFW.
1. Power-off the VM and increase the vCPUs within the hypervisor.
2. Increase the vCPU within the deployment profile.
3. Retrieve or fetch license keys on the VM-Series NGFW.
4. Confirm the correct tier level and vCPU appear on the NGFW dashboard.
5. Power-on the VM-Series NGFW.
1. Increase the vCPU within the deployment profile.
2. Retrieve or fetch license keys on the VM-Series NGFW.
3. Power-off the VM and increase the vCPUs within the hypervisor.
4. Power-on the VM-Series NGFW.
5. Confirm the correct tier level and vCPU appear on the NGFW dashboard.
1. Power-off the VM and increase the vCPUs within the hypervisor.
2. Power-on the VM-Series NGFW.
3. Retrieve or fetch license keys on the VM-Series NGFW.
4. Increase the vCPU within the deployment profile.
5. Confirm the correct tier level and vCPU appear on the NGFW dashboard.
Answer:
BExplanation:
Comprehensive and Detailed In-Depth Step-by-Step Explanation:Increasing throughput for a VM-Series firewall running on VMware ESXi with flexible licensing requires adjusting virtual CPU (vCPU) resources, which impacts performance tiers. The Palo Alto Networks Systems Engineer Professional - Software Firewall documentation outlines the process for modifying VM-Series resources to minimize downtime, particularly for flexible-license models.
Option B (Correct Answer): This order minimizes downtime by ensuring all steps are performed efficiently and safely:
Power-off the VM and increase the vCPUs within the hypervisor: Shutting down the VM-Series firewall on ESXi avoids any risk of corruption or performance issues during resource changes. Increasing vCPUs in the hypervisor (e.g., VMware vSphere) adjusts the hardware resources allocated to the VM, enabling higher throughput.
Increase the vCPU within the deployment profile: After adjusting the hypervisor, update the deployment profile in the Palo Alto Networks Customer Support Portal or Strata Cloud Manager to reflect the new vCPU count, ensuring the flexible license aligns with the updated resources.
Retrieve or fetch license keys on the VM-Series NGFW: With the vCPU change applied, the VM-Series fetches or retrieves new license keys based on the updated deployment profile, activating the higher-tier performance level (e.g., from Tier 1 to Tier 2).
Confirm the correct tier level and vCPU appear on the NGFW dashboard: After powering on and licensing, verify the VM-Series dashboard shows the updated vCPU count and corresponding performance tier, ensuring throughput increases as expected.
Power-on the VM-Series NGFW: Restart the VM to apply changes, minimizing downtime by ensuring all preparatory steps (power-off, resource adjustment, licensing) are completed before rebooting.This sequence minimizes downtime by handling resource changes offline, updating licensing, and validating the configuration before bringing the firewall back online, as recommended in the documentation for flexible licensing and VM resource adjustments.
Options A, C, and D are incorrect because they involve powering off the VM after licensing or resource changes, increasing downtime or risking configuration errors. For example, Option A powers off after increasing vCPUs in the profile and licensing, delaying the physical resource adjustment. Option C powers off after licensing, potentially causing licensing mismatches. Option D powers on the VM before licensing and profile updates, risking operational issues or downtime during reconfiguration. The documentation emphasizes minimizing downtime by completing all preparatory steps before rebooting, making Option B the optimal sequence.
References: Palo Alto Networks Systems Engineer Professional - Software Firewall, Section: VM-Series Flexible Licensing, VMware ESXi Deployment Guide, Performance Tuning and Resource Adjustment Documentation.
Which three Cloud NGFW management tasks are inherently performed by the service within AWS and Azure? (Choose three.)
Options:
Horizontally scaling out to meet increased traffic demand
Installing new content (applications and threats)
Installing new PAN-OS software updates
Blocking high-risk S2C threats in accordance with SOC2 compliance
Decrypting high-risk SSL traffic
Answer:
A, B, CExplanation:
The question asks about Cloud NGFW management tasks performed inherently by the service within AWS and Azure. This means we are looking for tasks that are automated and handled by the Cloud NGFW service itself, not by the customer.
Here's a breakdown of why A, B, and C are correct and why D and E are incorrect, referencing relevant Palo Alto Networks documentation where possible (though specific, publicly accessible documentation on the inner workings of the managed service is limited, the principles are consistent with their general cloud and firewall offerings):
A. Horizontally scaling out to meet increased traffic demand: This is a core feature of cloud-native services. Cloud NGFW is designed to automatically scale its resources (compute, memory, etc.) based on traffic volume. This eliminates the need for manual intervention by the customer to provision or de-provision resources. This aligns with the general principles of cloud elasticity and autoscaling, which are fundamental to cloud-native services like Cloud NGFW. While explicit public documentation detailing the exact scaling mechanism is limited, it's a standard practice for cloud-based services and is implied in the general description of Cloud NGFW as a managed service.
B. Installing new content (applications and threats): Palo Alto Networks maintains the threat intelligence and application databases for Cloud NGFW. This means that updates to these databases, which are crucial for identifying and blocking threats, are automatically pushed to the service by Palo Alto Networks. Customers do not need to manually download or install these updates. This is consistent with how Palo Alto Networks manages its other security services, such as Threat Prevention and WildFire, where content updates are delivered automatically.
C. Installing new PAN-OS software updates: Just like content updates, PAN-OS software updates are also managed by Palo Alto Networks for Cloud NGFW. This ensures that the service is always running the latest and most secure version of the operating system. This removes the operational burden of managing software updates from the customer. This is a key advantage of a managed service.
D. Blocking high-risk S2C threats in accordance with SOC2 compliance: While Cloud NGFW does block threats, including server-to-client (S2C) threats, the management of this blocking is not inherently performed by the service in the context of SOC2 compliance. SOC2 is an auditing framework, and compliance is the customer's responsibility. The service provides the tools to achieve security controls, but demonstrating and maintaining compliance is the customer's task. The service does not inherently manage the compliance process itself.
E. Decrypting high-risk SSL traffic: While Cloud NGFW can decrypt SSL traffic for inspection (SSL Forward Proxy), the question asks about tasks inherently performed by the service. Decryption is a configurable option. Customers choose whether or not to enable SSL decryption. It is not something the service automatically does without explicit configuration. Therefore, it's not an inherent management task performed by the service.
In summary, horizontal scaling, content updates, and PAN-OS updates are all handled automatically by the Cloud NGFW service, making A, B, and C the correct answers. D and E involve customer configuration or compliance considerations, not inherent management tasks performed by the service itself.
What are two benefits of using a Palo Alto Networks NGFW in a public cloud environment? (Choose two.)
Options:
Complete security solution for the public cloud provider's physical host regardless of security measures
Automatic scaling of NGFWs to meet the security needs of growing applications and public cloud environments
Ability to manage the public cloud provider's physical hosts
Consistent Security policy to inbound, outbound, and east-west network traffic throughout the multi-cloud environment
Answer:
B, DExplanation:
Using a Palo Alto Networks Next-Generation Firewall (NGFW) in a public cloud environment offers several key advantages related to security and scalability:
A. Complete security solution for the public cloud provider's physical host regardless of security measures: Palo Alto Networks NGFWs operate at the network layer (and above), inspecting traffic flowing in and out of your virtual networks (VPCs in AWS, VNETs in Azure, etc.). They do not provide security for the underlying physical infrastructure of the cloud provider. That's the cloud provider's responsibility. NGFWs secure your workloads within the cloud environment.
B. Automatic scaling of NGFWs to meet the security needs of growing applications and public cloud environments: This is a significant benefit. Cloud NGFWs can often be configured to auto-scale based on traffic demands. As your applications grow and require more bandwidth and processing, the NGFW can automatically scale up its resources (or deploy additional instances) to maintain performance and security. This elasticity is a core advantage of cloud-based firewalls.
C. Ability to manage the public cloud provider's physical hosts: As mentioned above, NGFWs do not provide management capabilities for the cloud provider's physical infrastructure. You manage your virtual network resources and the NGFW itself, but not the underlying hardware.
D. Consistent Security policy to inbound, outbound, and east-west network traffic throughout the multi-cloud environment: This is a crucial advantage, especially in multi-cloud deployments. Palo Alto Networks NGFWs allow you to enforce consistent security policies across different cloud environments (AWS, Azure, GCP, etc.). This ensures consistent protection regardless of where your workloads are running and simplifies security management. East-west traffic (traffic between workloads within the same cloud environment) is also a key focus, as it's often overlooked by traditional perimeter-based security.
Which two deployment models does Cloud NGFW for AWS support? (Choose two.)
Options:
Hierarchical
Centralized
Distributed
Linear
Answer:
B, CExplanation:
Cloud NGFW for AWS supports two primary deployment models:
A. Hierarchical: This is not a standard deployment model for Cloud NGFW for AWS. Hierarchical typically refers to a parent-child relationship in management, which isn't the core focus of the Cloud NGFW's deployment models.
B. Centralized: This is a VALID deployment model. In a centralized deployment, the Cloud NGFW is deployed in a central VPC (often a Transit Gateway VPC) and inspects traffic flowing between different VPCs and on-premises networks. This provides a single point of control for security policies.
Why should a customer use advanced versions of Cloud-Delivered Security Services (CDSS) subscriptions compared to legacy versions when creating or editing a deployment profile?
(e.g., using Advanced Threat Prevention instead of Threat Prevention.)
Options:
To improve firewall throughput by inspecting hashes of advanced packet headers
To download and install new threat-related signature databases in real-time
To use cloud-scale machine learning inline for detection of highly evasive and zero-day threats
To use external dynamic lists for blocking known malicious threat sources and destinations
Answer:
CExplanation:
Advanced CDSS subscriptions offer enhanced threat prevention capabilities:
A. To improve firewall throughput by inspecting hashes of advanced packet headers: While some security features use hashing, this is not the primary advantage of advanced CDSS.
B. To download and install new threat-related signature databases in real-time: Both standard and advanced CDSS subscriptions receive regular threat updates.
C. To use cloud-scale machine learning inline for detection of highly evasive and zero-day threats: This is a key differentiator of advanced CDSS. It leverages cloud-based machine learning to detect sophisticated threats that traditional signature-based methods might miss.
D. To use external dynamic lists for blocking known malicious threat sources and destinations: Both standard and advanced CDSS can use external dynamic lists.
References:
Information about the specific features of advanced CDSS, such as inline machine learning, can be found on the Palo Alto Networks website and in datasheets comparing different CDSS subscription levels.
A customer with multiple virtual private clouds (VPCs) in Amazon Web Services (AWS) protected by the cloud-native firewall experiences a cloud breach. As a result, malware spreads quickly across the VPCs, infecting several workloads.
Which minimum solution should be proposed to prevent similar incidents in the future?
Options:
Purchase a software credit pool for flexible Cloud NGFW deployment across the VPCs.
Deploy a single Cloud NGFW.
Subscribe to Palo Alto Networks Advanced Threat Protection for the cloud-native firewall.
Implement a Cloud NGFW for each VPC.
Answer:
DExplanation:
Comprehensive and Detailed In-Depth Step-by-Step Explanation:The customer’s AWS environment, with multiple VPCs protected by a cloud-native firewall, experienced a breach due to malware spreading across VPCs, indicating inadequate segmentation and visibility. The Palo Alto Networks Systems Engineer Professional - Software Firewall documentation provides guidance on securing multi-VPC AWS environments with Cloud NGFW, focusing on preventing lateral movement and enhancing threat prevention.
Implement a Cloud NGFW for each VPC (Option D): Deploying a Cloud NGFW instance in each VPC ensures localized traffic inspection, segmentation, and control, preventing malware from spreading laterally across VPCs. Cloud NGFW for AWS supports a distributed deployment model, allowing each VPC to have its own firewall instance integrated with AWS services (e.g., VPC routing, Security Groups) to enforce policies, block threats, and maintain visibility. The documentation recommends this approach for multi-VPC environments to minimize risk exposure and ensure granular security, addressing the customer’s breach scenario by isolating and securing each VPC independently.
Options A (Purchase a software credit pool for flexible Cloud NGFW deployment across the VPCs), B (Deploy a single Cloud NGFW), and C (Subscribe to Palo Alto Networks Advanced Threat Protection for the cloud-native firewall) are incorrect. A software credit pool (Option A) is a licensing mechanism, not a deployment solution, and does not address the need for multiple VPC protection. A single Cloud NGFW (Option B) cannot effectively secure multiple VPCs without introducing latency or complexity (e.g., centralized routing), failing to prevent lateral movement as seen in the breach. Advanced Threat Protection (Option C) enhances threat detection but does not resolve the segmentation issue; it requires a distributed deployment (like Option D) to prevent malware spread across VPCs.
References: Palo Alto Networks Systems Engineer Professional - Software Firewall, Section: Cloud NGFW for AWS Deployment, Multi-VPC Security Architecture, Advanced Threat Prevention Documentation.
Which three statements describe common characteristics of Cloud NGFW and VM-Series offerings? (Choose three.)
Options:
In Azure, both offerings can be integrated directly into Virtual WAN hubs.
In Azure and AWS, both offerings can be managed by Panorama.
In AWS, both offerings can be managed by AWS Firewall Manager.
In Azure, inbound destination NAT configuration also requires source NAT to maintain flow symmetry.
In Azure and AWS, internal (east-west) flows can be inspected without any NAT.
Answer:
B, D, EExplanation:
This question asks about common characteristics of Cloud NGFW (specifically referring to Cloud NGFW for AWS and Azure) and VM-Series firewalls.
B. In Azure and AWS, both offerings can be managed by Panorama. This is correct. Panorama is the centralized management platform for Palo Alto Networks firewalls, including both VM-Series and Cloud NGFW deployments in AWS and Azure. Panorama allows for consistent policy management, logging, and reporting across these different deployment models.
D. In Azure, inbound destination NAT configuration also requires source NAT to maintain flow symmetry. This is accurate specifically within the Azure environment. Due to how Azure networking functions, when performing destination NAT (DNAT) for inbound traffic to resources behind a firewall (whether VM-Series or Cloud NGFW), it's typically necessary to also implement source NAT (SNAT) to ensure return traffic follows the same path. This maintains flow symmetry and prevents routing issues. This is an Azure networking characteristic, not specific to the Palo Alto offerings themselves, but it applies to both in Azure.
E. In Azure and AWS, internal (east-west) flows can be inspected without any NAT. This is generally true. For traffic within the same Virtual Network (Azure) or VPC (AWS), both VM-Series and Cloud NGFW can inspect traffic without requiring NAT. This is a key advantage for microsegmentation and internal security. The firewalls can act as transparent security gateways for internal traffic.
Why other options are incorrect:
A. In Azure, both offerings can be integrated directly into Virtual WAN hubs. While VM-Series firewalls can be integrated into Azure Virtual WAN hubs as secured virtual hubs, Cloud NGFW for Azure is not directly integrated into Virtual WAN hubs in the same way. Cloud NGFW for Azure uses a different architecture, deploying as a service within a virtual network.
C. In AWS, both offerings can be managed by AWS Firewall Manager. AWS Firewall Manager is a service for managing AWS WAF, AWS Shield, and network firewalls (AWS Network Firewall). While AWS Firewall Manager can be used to manage AWS Network Firewall, it is not the management plane for Palo Alto Networks VM-Series or Cloud NGFW for AWS. These are managed by Panorama.
Palo Alto Networks References:
To validate these points, refer to the following documentation areas on the Palo Alto Networks support site (live.paloaltonetworks.com):
Panorama Administrator's Guide: This guide details the management capabilities of Panorama, including managing VM-Series and Cloud NGFW deployments in AWS and Azure.
Cloud NGFW for AWS/Azure Documentation: This documentation outlines the architecture and deployment models of Cloud NGFW, including its management and integration with cloud platforms.
VM-Series Deployment Guides for AWS/Azure: These guides describe the deployment and configuration of VM-Series firewalls in AWS and Azure, including networking considerations and integration with cloud services.
Which two statements accurately describe cloud-native load balancing with Palo Alto Networks VM-Series firewalls and/or Cloud NGFW in public cloud environments? (Choose two.)
Options:
Cloud NGFW’s distributed architecture model requires deployment of a single centralized firewall and will force all traffic to the firewall across pre-built VPN tunnels.
VM-Series firewall deployments in the public cloud will require the deployment of a cloud-native load balancer if high availability (HA) or redundancy is needed.
Cloud NGFW in AWS or Azure has load balancing built into the underlying solution and does not require the deployment of a separate load balancer.
VM-Series firewall load balancing is automated and is handled by the internal mechanics of the NGFW software without the need for a load balancer.
Answer:
B, CExplanation:
Cloud-native load balancing with Palo Alto Networks firewalls in public clouds involves understanding the distinct approaches for VM-Series and Cloud NGFW:
A. Cloud NGFW’s distributed architecture model requires deployment of a single centralized firewall and will force all traffic to the firewall across pre-built VPN tunnels: This is incorrect. Cloud NGFW uses a distributed architecture where traffic is steered to the nearest Cloud NGFW instance, often using Gateway Load Balancers (GWLBs) or similar services. It does not rely on a single centralized firewall or force all traffic through VPN tunnels.
B. VM-Series firewall deployments in the public cloud will require the deployment of a cloud-native load balancer if high availability (HA) or redundancy is needed: This is correct. VM-Series firewalls, when deployed for HA or redundancy, require a cloud-native load balancer (e.g., AWS ALB/NLB/GWLB, Azure Load Balancer) to distribute traffic across the active firewall instances. This ensures that if one firewall fails, traffic is automatically directed to a healthy instance.
C. Cloud NGFW in AWS or Azure has load balancing built into the underlying solution and does not require the deployment of a separate load balancer: This is also correct. Cloud NGFW integrates with cloud-native load balancing services (e.g., Gateway Load Balancer in AWS) as part of its architecture. This provides automatic scaling and high availability without requiring you to manage a separate load balancer.
D. VM-Series firewall load balancing is automated and is handled by the internal mechanics of the NGFW software without the need for a load balancer: This is incorrect. VM-Series firewalls do not have built-in load balancing capabilities for HA. A cloud-native load balancer is essential for distributing traffic and ensuring redundancy.
References:
Cloud NGFW documentation: Look for sections on architecture, traffic steering, and integration with cloud-native load balancing services (like AWS Gateway Load Balancer).
VM-Series deployment guides for each cloud provider: These guides explain how to deploy VM-Series firewalls for HA using cloud-native load balancers.
These resources confirm that VM-Series requires external load balancers for HA, while Cloud NGFW has load balancing integrated into its design.
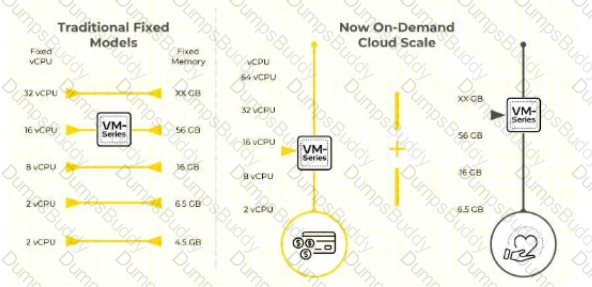
Which feature allows customers to dynamically increase the capability of their VM-Series firewalls without needing to increase performance they do not need?
Options:
Elastic vCPU profiles
Increased RAM cache
Increased fixed vCPUs and memory
Elastic Memory Profiles
Answer:
AExplanation:
Comprehensive and Detailed In-Depth Step-by-Step Explanation:The Palo Alto Networks Systems Engineer Professional - Software Firewall documentation describes the flexible licensing and resource management options for VM-Series firewalls, particularly under PAN-OS 11.x and later versions. The question focuses on dynamically adjusting VM-Series firewall capabilities (e.g., performance and throughput) without over-provisioning unnecessary resources, a key feature of Palo Alto Networks’ credit-based flexible licensing model.
Elastic vCPU profiles (Option A): Elastic vCPU profiles, part of the flexible licensing model for VM-Series firewalls, allow customers to dynamically adjust the number of virtual CPUs (vCPUs) allocated to their firewalls based on current performance needs. This is enabled through NGFW credits managed in the Palo Alto Networks Customer Support Portal or Strata Cloud Manager, where deployment profiles can be configured with flexible vCPU counts (e.g., 2, 4, 8, 16, 32, or 64 vCPUs, corresponding to Tiers 1–4). The documentation highlights that this feature enables customers to scale up or down vCPU resources without over-provisioning fixed performance (e.g., memory or throughput) they do not need, ensuring cost efficiency and scalability in public clouds (e.g., AWS, Azure, GCP) and private clouds. The diagram in the question contrasts traditional fixed models (e.g., VM-100 with fixed vCPUs and memory) with the “On-Demand Cloud Scale” approach, where elastic vCPU profiles allow dynamic adjustment (e.g., adding vCPUs as shown by the upward arrow) without increasing unnecessary performance, aligning with the question’s intent.
Options B (Increased RAM cache), C (Increased fixed vCPUs and memory), and D (Elastic Memory Profiles) are incorrect. Increased RAM cache (Option B) is not a configurable feature for VM-Series firewalls and does not address dynamic capability adjustment; RAM is tied to vCPU tiers but not independently scalable in this context. Increased fixed vCPUs and memory (Option C) refers to traditional fixed models (e.g., VM-100, VM-300), which do not allow dynamic scaling and would over-provision performance the customer does not need, contradicting the question’s focus on avoiding unnecessary increases. Elastic Memory Profiles (Option D) is not a recognized feature in the documentation for VM-Series; memory allocation is linked to vCPU tiers, but there is no standalone “elastic memory” option, making this inaccurate. The documentation emphasizes elastic vCPU profiles as the solution for dynamic, on-demand scaling without over-provisioning, as shown in the diagram’s “On-Demand Cloud Scale” visualization.
References: Palo Alto Networks Systems Engineer Professional - Software Firewall, Section: VM-Series Flexible Licensing, Elastic vCPU Profiles Documentation, NGFW Credits and Deployment Profiles Guide, PAN-OS 11.x Deployment and Scaling Documentation.
Which public cloud provider requires the creation of subnets that are dedicated to Cloud NGFW endpoints?
Options:
Google Cloud Platform (GCP)
Alibaba Cloud
Amazon Web Services (AWS)
Microsoft Azure
Answer:
CExplanation:
AWS: Cloud NGFW for AWS leverages AWS Gateway Load Balancer (GWLB) endpoints. These endpoints require dedicated subnets in your VPC for each Availability Zone where you want to deploy the Cloud NGFW. This ensures high availability and proper traffic routing.
Let's look at why the other options are not the primary answer:
Google Cloud Platform (GCP): While GCP has its own networking constructs, Cloud NGFW for GCP doesn't have the same dedicated subnet requirement for endpoints as AWS.
Alibaba Cloud: I don't have specific information about Cloud NGFW deployment models for Alibaba Cloud.
Microsoft Azure: Cloud NGFW for Azure integrates with Azure Virtual WAN and doesn't have the same dedicated subnet requirement for endpoints as AWS.


