NSE8_812 Network Security Expert 8 Written Exam Questions and Answers
A FortiGate is configured to perform outbound firewall authentication with Azure AD as a SAML IdP.
What are two valid interactions that occur when the client attempts to access the internet? (Choose two.)
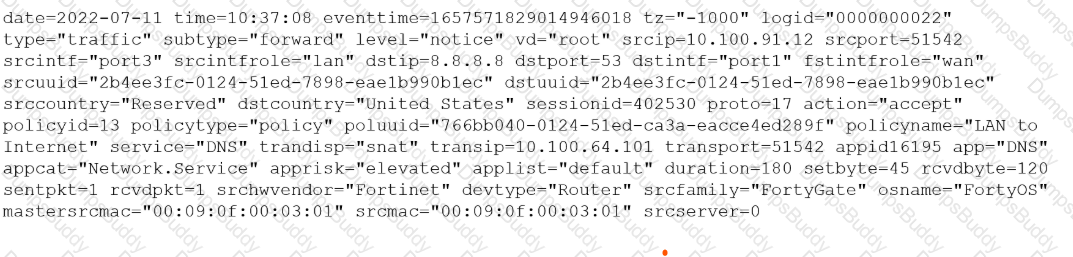
You must analyze an event that happened at 20:37 UTC. One log relevant to the event is extracted from FortiGate logs:
The devices and the administrator are all located in different time zones Daylight savings time (DST) is disabled
• The FortiGate is at GMT-1000.
• The FortiAnalyzer is at GMT-0800
• Your browser local time zone is at GMT-03.00
You want to review this log on FortiAnalyzer GUI, what time should you use as a filter?
Refer to the exhibit showing an SD-WAN configuration.
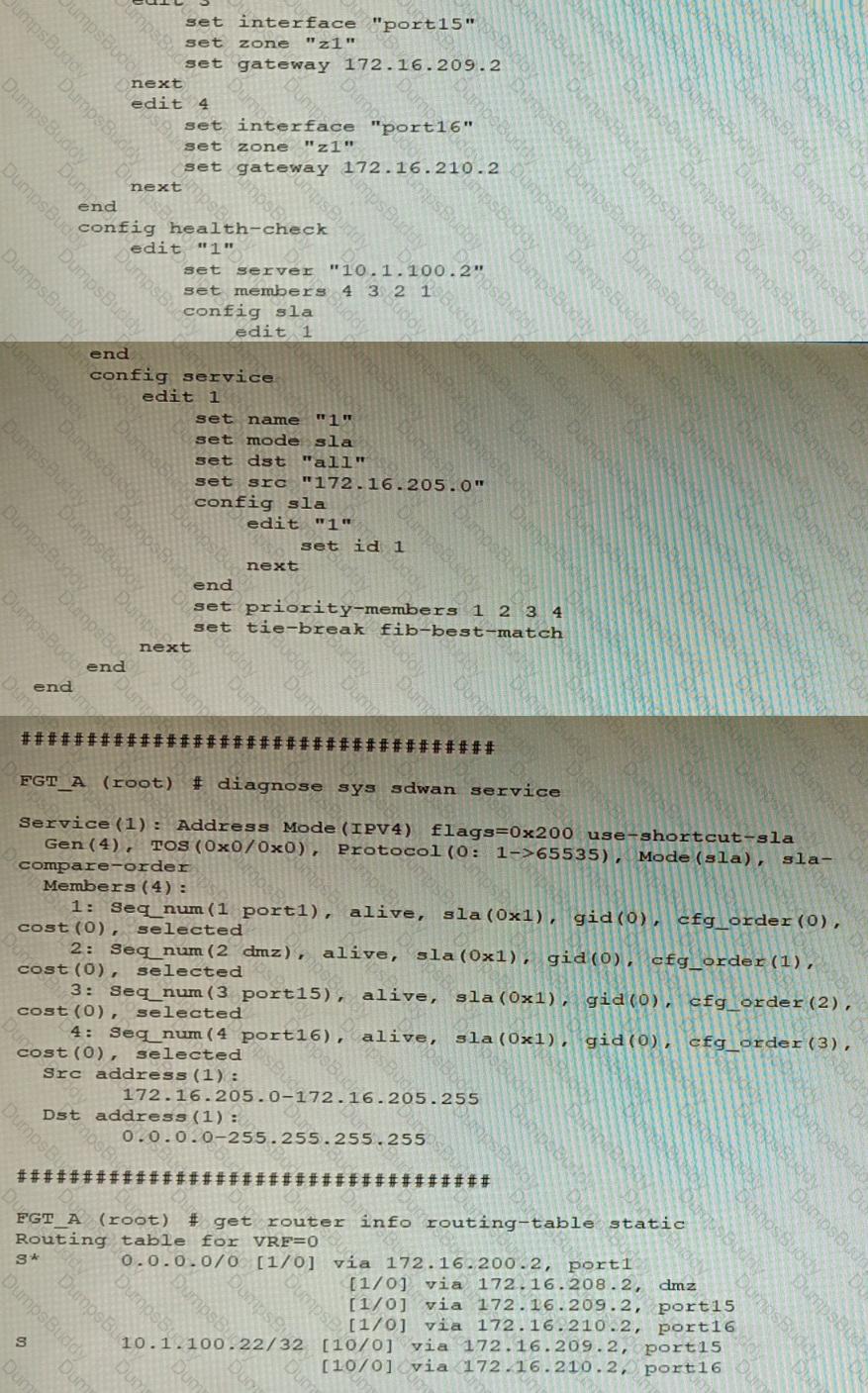
According to the exhibit, if an internal user pings 10.1.100.2 and 10.1.100.22 from subnet 172.16.205.0/24, which outgoing interfaces will be used?
Refer to the exhibits.
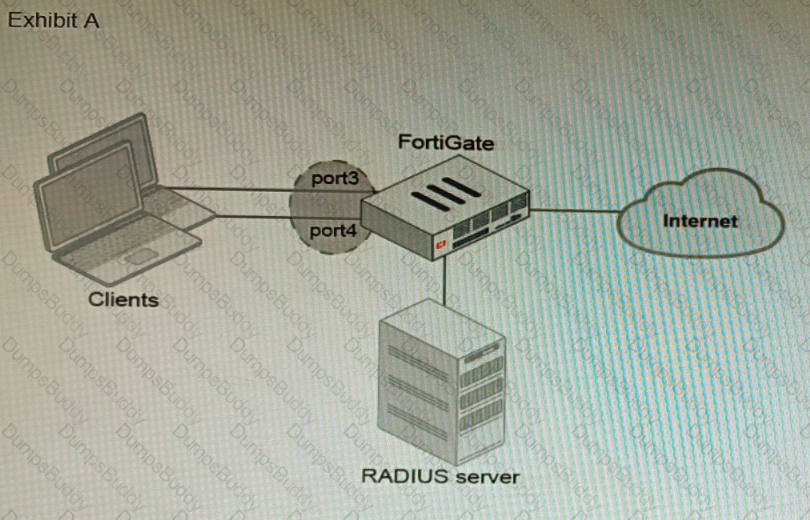
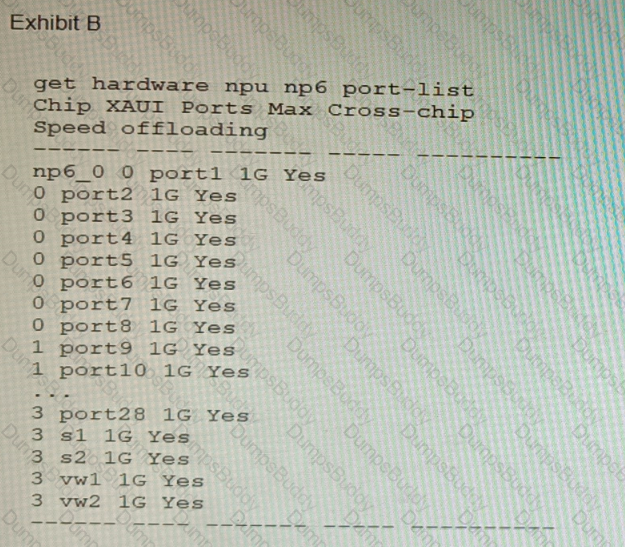
A customer is looking for a solution to authenticate the clients connected to a hardware switch interface of a FortiGate 400E.
Referring to the exhibits, which two conditions allow authentication to the client devices before assigning an IP address? (Choose two.)
A customer is planning on moving their secondary data center to a cloud-based laaS. They want to place all the Oracle-based systems Oracle Cloud, while the other systems will be on Microsoft Azure with ExpressRoute service to their main data center.
They have about 200 branches with two internet services as their only WAN connections. As a security consultant you are asked to design an architecture using Fortinet products with security, redundancy and performance as a priority.
Which two design options are true based on these requirements? (Choose two.)
Refer to the exhibit.
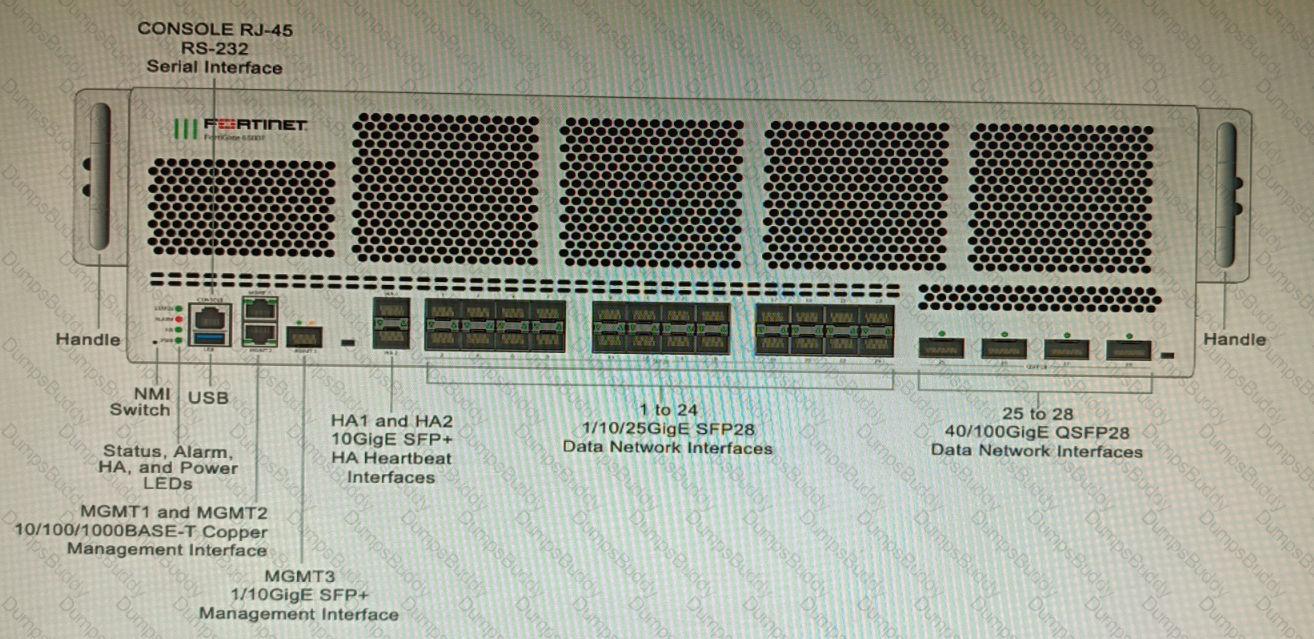
You are deploying a FortiGate 6000F. The device should be directly connected to a switch. In the future, a new hardware module providing higher speed will be installed in the switch, and the connection to the FortiGate must be moved to this higher-speed port.
You must ensure that the initial FortiGate interface connected to the switch does not affect any other port when the new module is installed and the new port speed is defined.
How should the initial connection be made?
Refer to the exhibit.
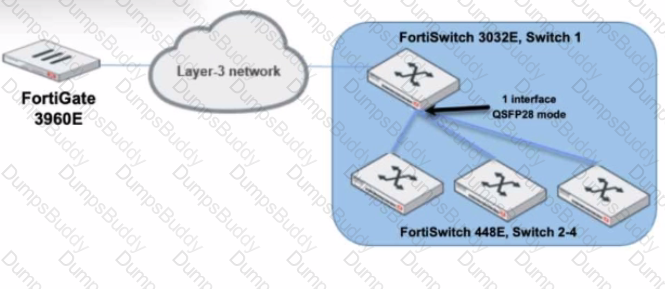
You are managing a FortiSwitch 3032E that is managed by FortiLink on a FortiGate 3960E. The 3032E is heavily utilized and there is only one port free.
The requirement is to add an additional three FortiSwitch 448E devices with 10Gbps SFP+ connectivity directly to the 3032E. The plan is to use split port (phy-mode) with QSFP28 mode to connect the new 448E switches.
In this scenario, which statement about the switch deployment is correct?
Refer to the exhibit.
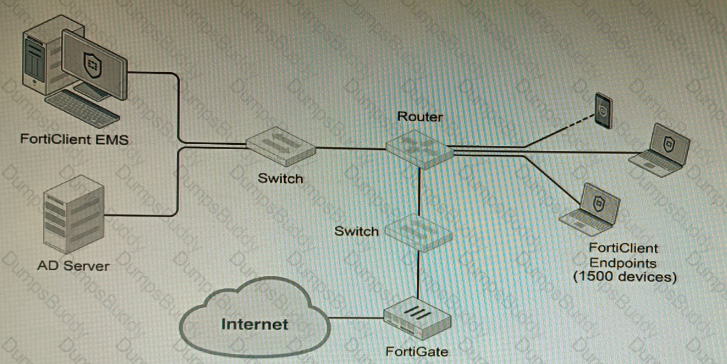
A customer wants FortiClient EMS configured to deploy to 1500 endpoints. The deployment will be integrated with FortiOS and there is an Active Directory server.
Given the configuration shown in the exhibit, which two statements about the installation are correct? (Choose two.)
Refer to the exhibit.
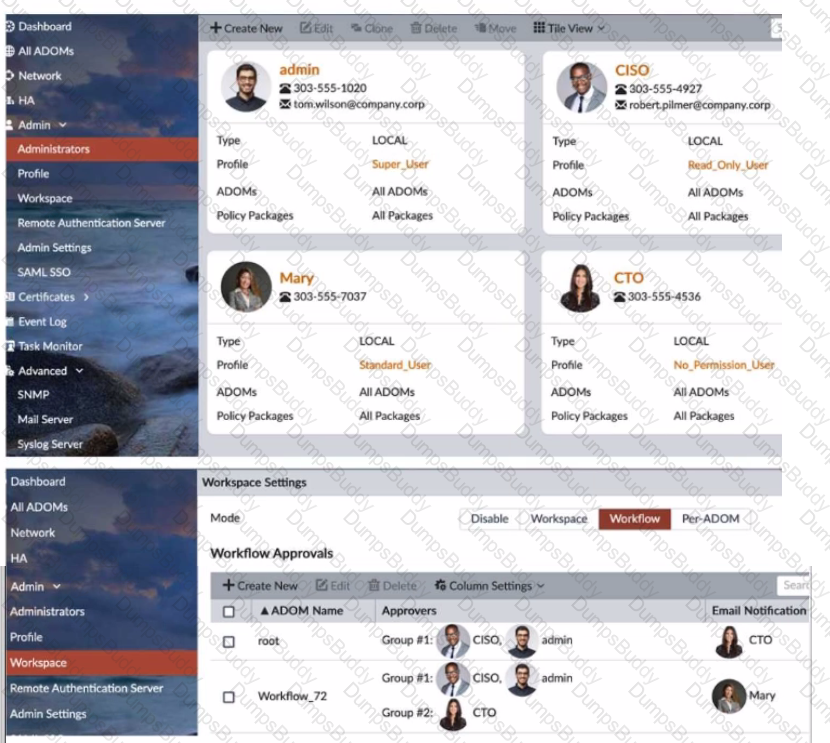
The Company Corp administrator has enabled Workflow mode in FortiManager and has assigned approval roles to the current administrators. However, workflow approval does not function as expected. The CTO is currently unable to approve submitted changes.
Given the exhibit, which two possible solutions will resolve the workflow approval problems with the Workflow_72 ADOM? (Choose two.)
SD-WAN is configured on a FortiGate. You notice that when one of the internet links has high latency the time to resolve names using DNS from FortiGate is very high.
You must ensure that the FortiGate DNS resolution times are as low as possible with the least amount of work.
What should you configure?
An administrator has configured a FortiGate device to authenticate SSL VPN users using digital certificates. A FortiAuthenticator is the certificate authority (CA) and the Online Certificate Status Protocol (OCSP) server.
Part of the FortiGate configuration is shown below:
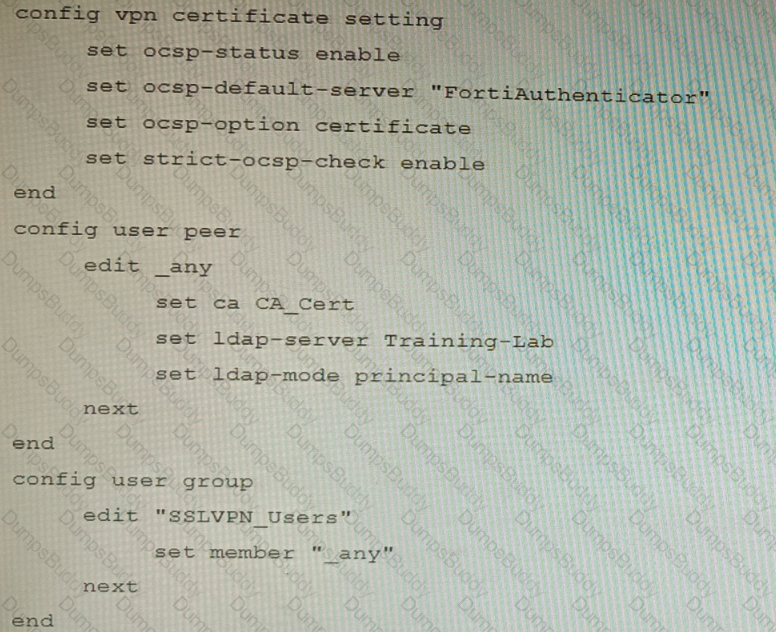
Based on this configuration, which two statements are true? (Choose two.)
An administrator has configured a FortiGate device to authenticate SSL VPN users using digital certificates. A FortiAuthenticator is the certificate authority (CA) and the OCSP server.
Part of the FortiGate configuration is shown below:
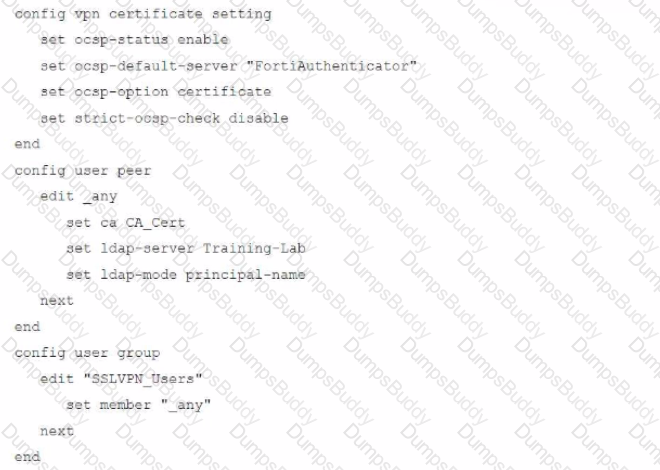
Based on this configuration, which authentication scenario will FortiGate deny?
A customer's cybersecurity department needs to implement security for the traffic between two VPCs in AWS, but these belong to different departments within the company. The company uses a single region for all their VPCs.
Which two actions will achieve this requirement while keeping separate management of each department's VPC? (Choose two.)
An HA topology is using the following configuration:
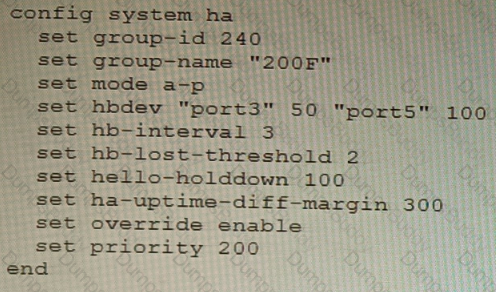
Based on this configuration, how long will it take for a failover to be detected by the secondary cluster member?
A customer would like to improve the performance of a FortiGate VM running in an Azure D4s_v3 instance, but they already purchased a BYOL VM04 license.
Which two actions will improve performance the most without making a FortiGate license change? (Choose two.)
Refer to the exhibits.
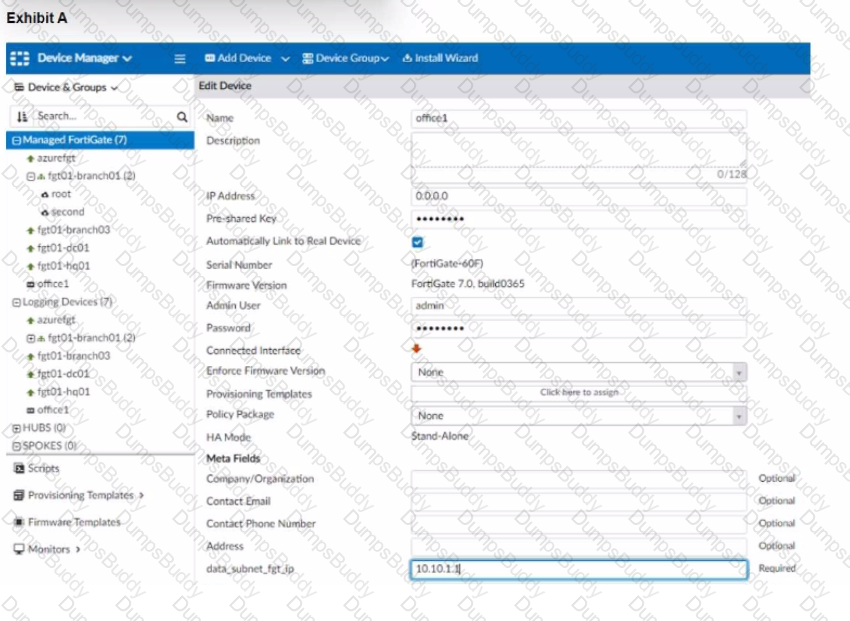
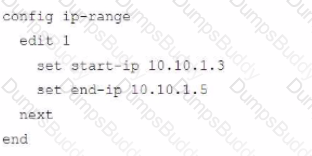
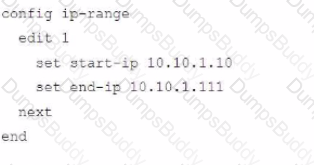
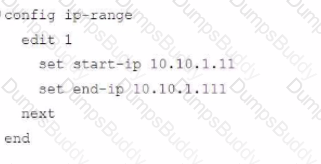
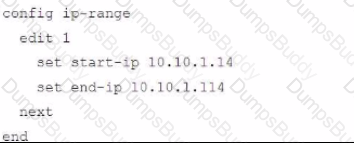
The exhibit shows a FortiGate model device that will be used for zero touch provisioning and a CLI Template.
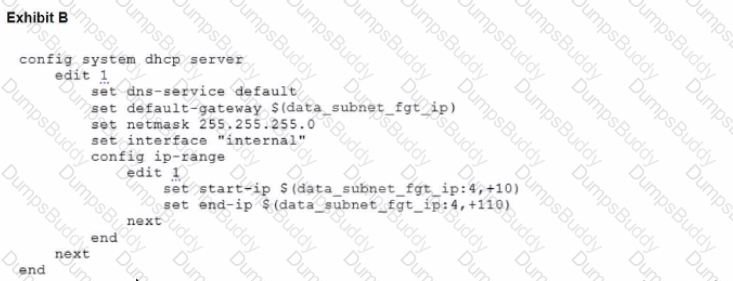
To facilitate a more efficient roll out of FortiGate devices, you are tasked with using meta fields with the CLI Template to configure the DHCP server on the "office1" FortiGate.
Given this scenario, what would be the output of the config ip-range section on the CLI Template?
Refer to the exhibits.
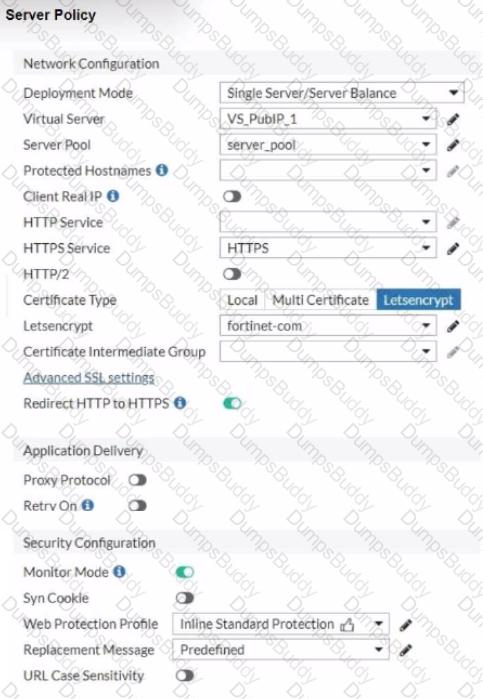
You are configuring a Let's Encrypt certificate to enable SSL protection to your website. When FortiWeb tries to retrieve the certificate, you receive a certificate status failed, as shown below.

Based on the Server Policy settings shown in the exhibit, which two configuration changes will resolve this issue? (Choose two.)
Review the Application Control log.
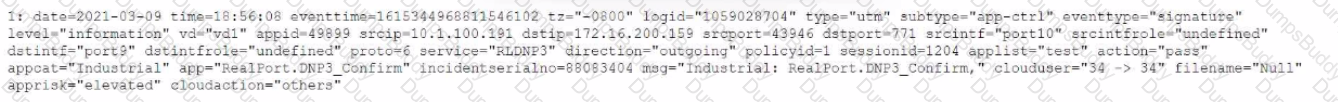
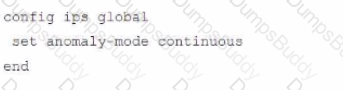
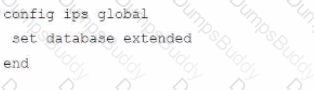
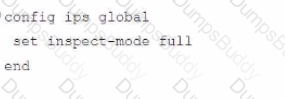
Which configuration caused the IPS engine to generate this log?
Refer to the exhibit, which shows diagnostic output.
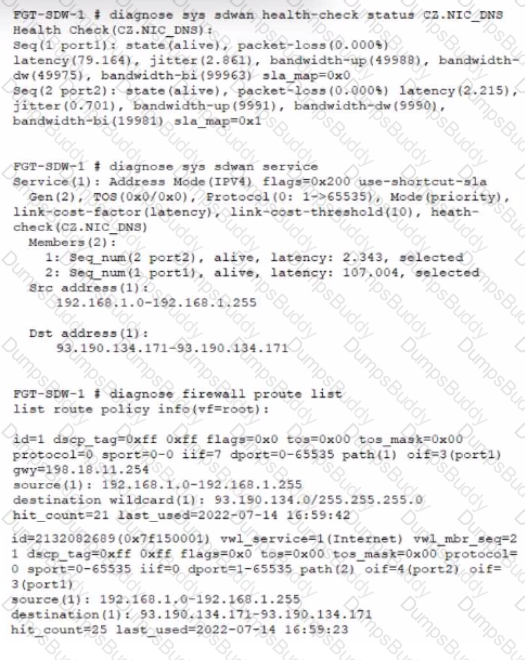
A customer reports that ICMP traffic flow from 192.168.1.11 to 93.190.134.171 is not corresponding to the SD-WAN setup.
What is the problem in this scenario?
Refer to the exhibits.
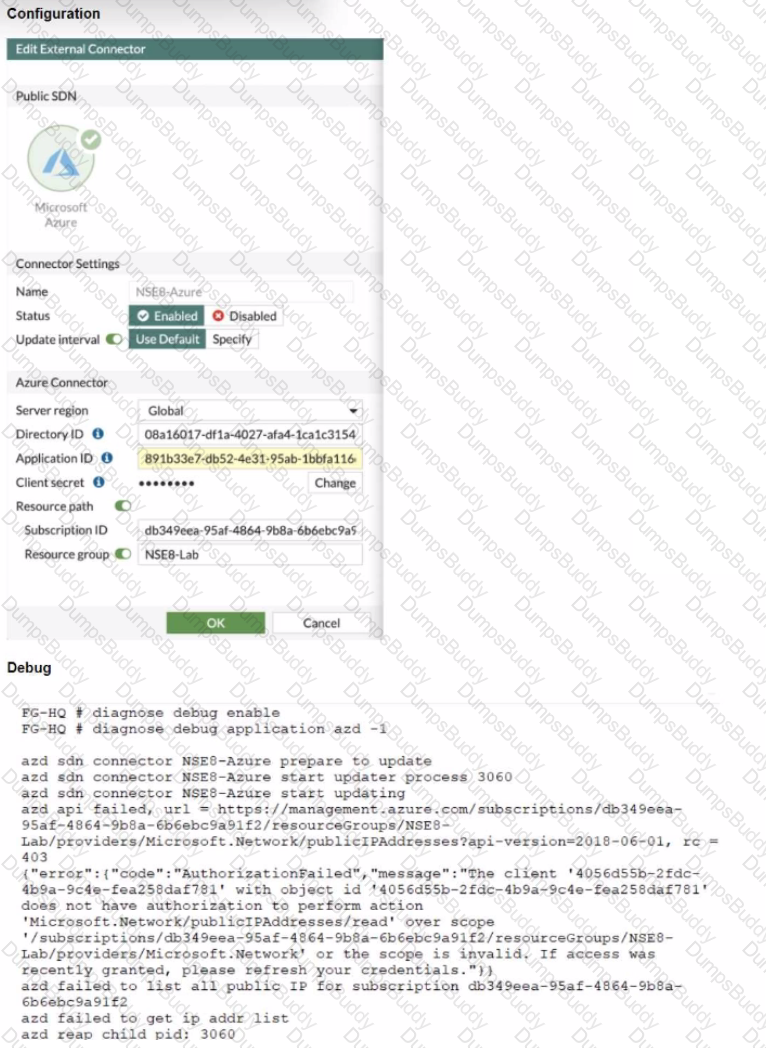
The exhibits show the configuration and debug output from a FortiGate Public SDN Connector.
What is a possible reason for this dynamic address object to be empty?
Refer to the exhibit.
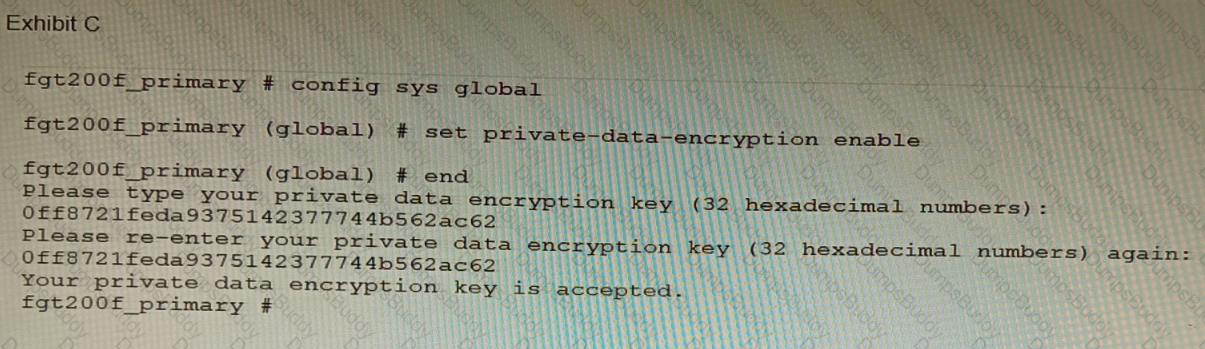
A customer has deployed a FortiGate 200F high-availability (HA) cluster that contains & TPM chip. The exhibit shows output from the FortiGate CLI session where the administrator enabled TPM.
Following these actions, the administrator immediately notices that both FortiGate high availability (HA) status and FortiManager status for the FortiGate are negatively impacted.
What are the two reasons for this behavior? (Choose two.)
Which two methods are supported for importing user defined Lookup Table Data into the FortiSIEM? (Choose two.)
Refer to the exhibit containing the configuration snippets from the FortiGate. Customer requirements:
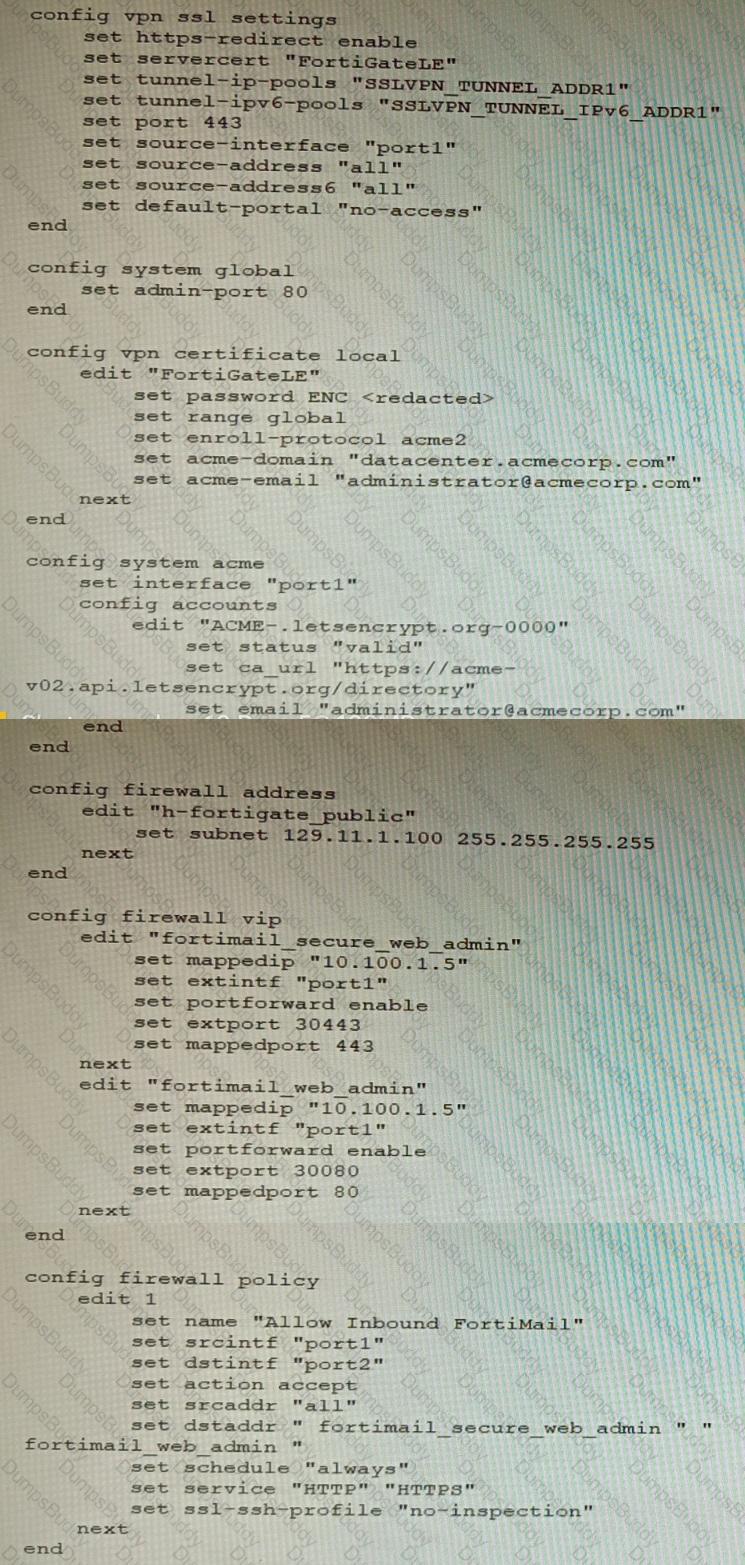
• SSLVPN Portal must be accessible on standard HTTPS port (TCP/443)
• Public IP address (129.11.1.100) is assigned to portl
• Datacenter.acmecorp.com resolves to the public IP address assigned to portl
The customer has a Let's Encrypt certificate that is going to expire soon and it reports that subsequent attempts to renew that certificate are failing.
Reviewing the requirement and the exhibit, which configuration change below will resolve this issue?
A)
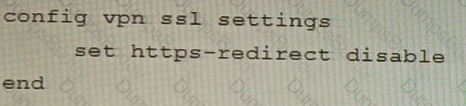
B)
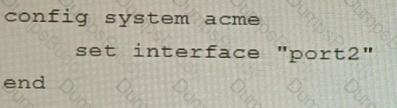
C)
D)

Refer to the exhibit, which shows a VPN topology.
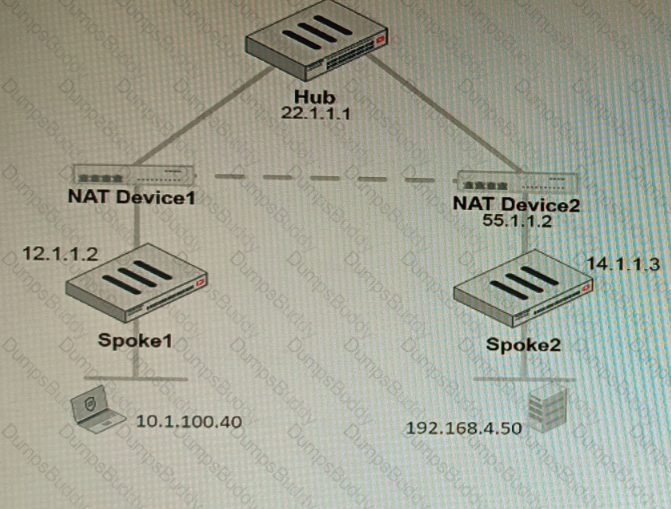
The device IP 10.1.100.40 downloads a file from the FTP server IP 192.168.4.50
Referring to the exhibit, what will be the traffic flow behavior if ADVPN is configured in this environment?
Refer to the exhibit, which shows the high availability configuration for the FortiAuthenticator (FAC1).
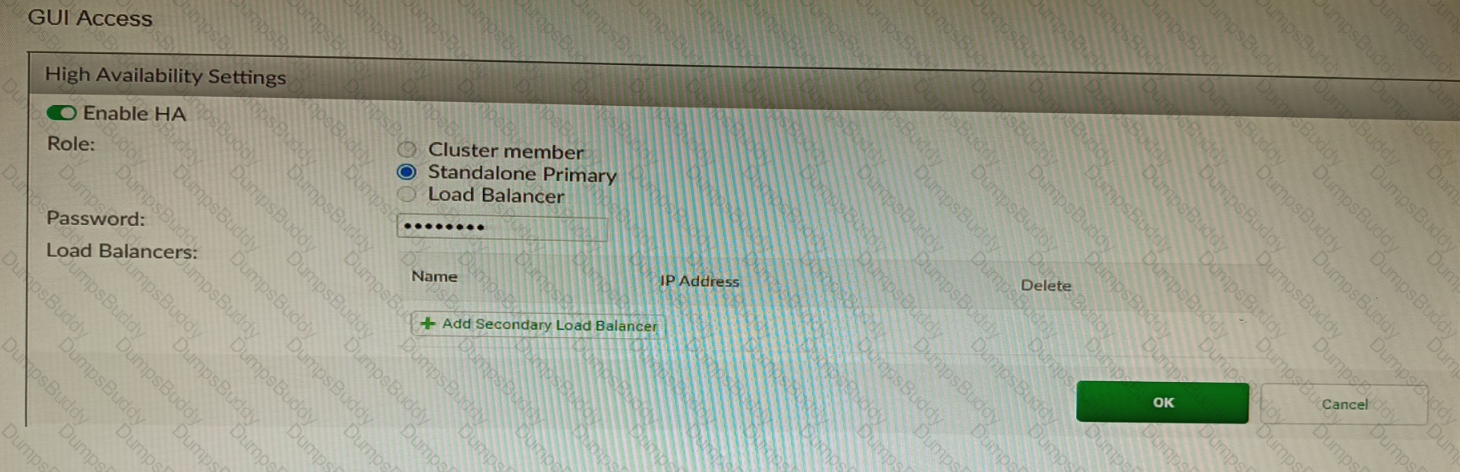
Based on this information, which statement is true about the next FortiAuthenticator (FAC2) member that will join an HA cluster with this FortiAuthenticator (FAC1)?
Refer to the exhibits.
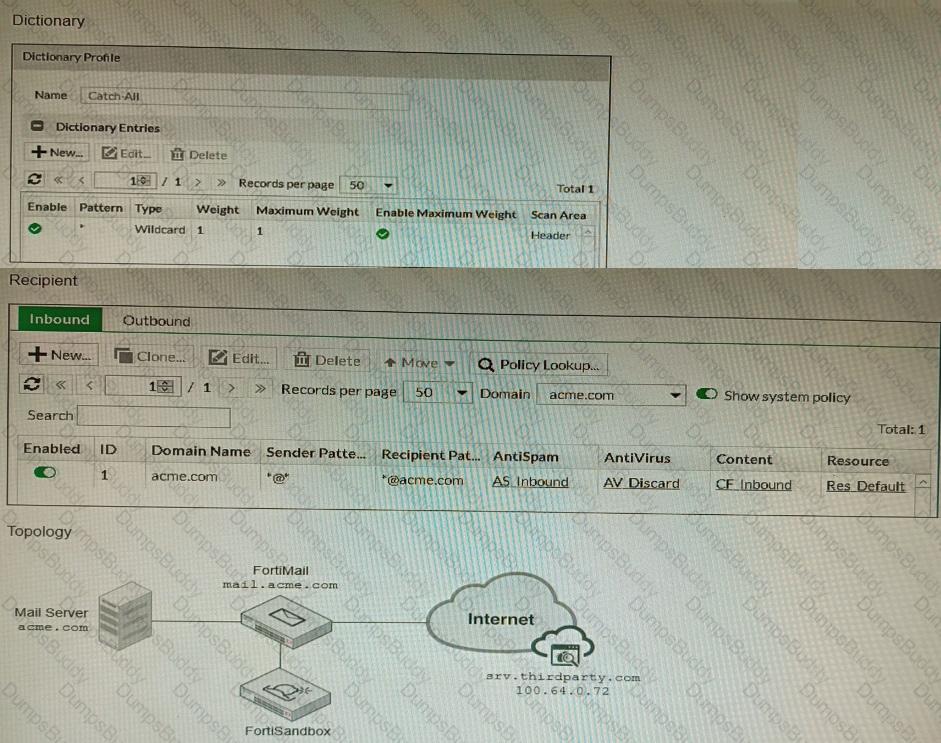
The exhibits show a FortiMail network topology, Inbound configuration settings, and a Dictionary Profile.
You are required to integrate a third-party's host service (srv.thirdparty.com) into the e-mail processing path.
All inbound e-mails must be processed by FortiMail antispam and antivirus with FortiSandbox integration. If the email is clean, FortiMail must forward it to the third-party service, which will send the email back to FortiMail for final delivery, FortiMail must not scan the e-mail again.
Which three configuration tasks must be performed to meet these requirements? (Choose three.)
Refer to the exhibit of a FortiNAC configuration.
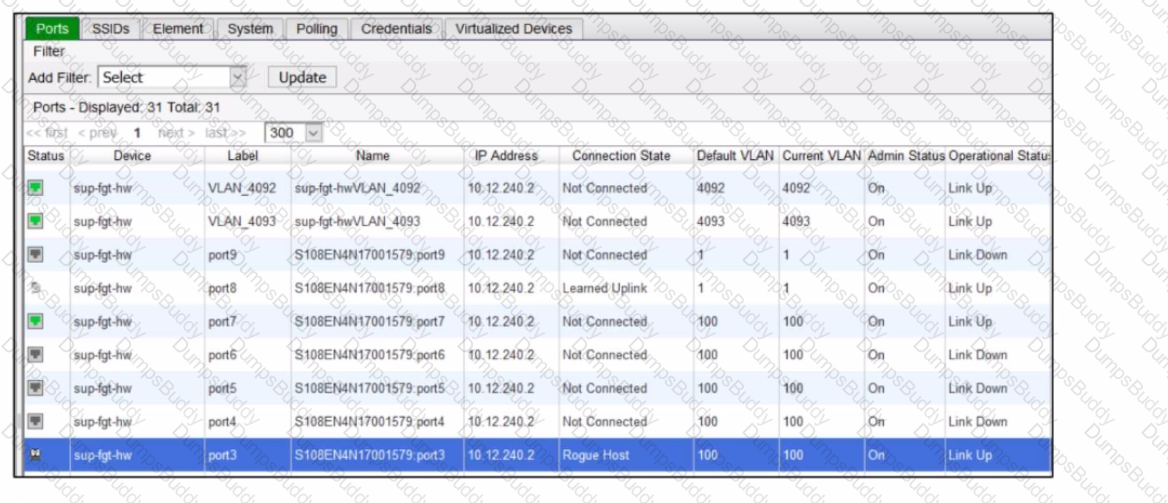
In this scenario, which two statements are correct? (Choose two.)
Refer to the exhibits, which show a topology and diagnostic commands.
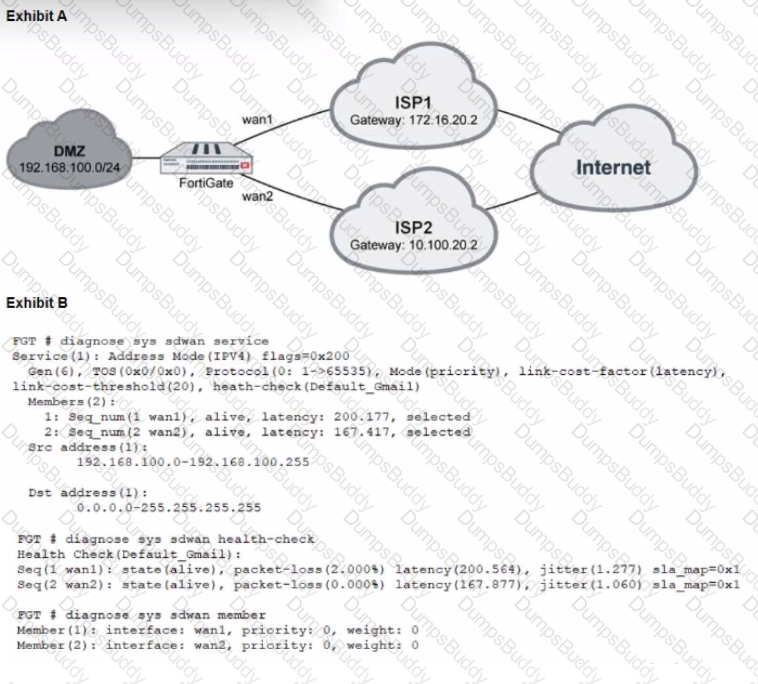
Which two statements about the path resolution are true? (Choose two.)