NSK101 Netskope Certified Cloud Security Administrator (NCCSA) Questions and Answers
Your customer has cloud storage repositories containing sensitive files of their partners, including bank statements, consulting, and disclosure agreements. In this scenario, which feature would help them control the flow of these types of documents?
What are two primary advantages of Netskope's Secure Access Service Edge (SASE) architecture? (Choose two.
Click the Exhibit button.
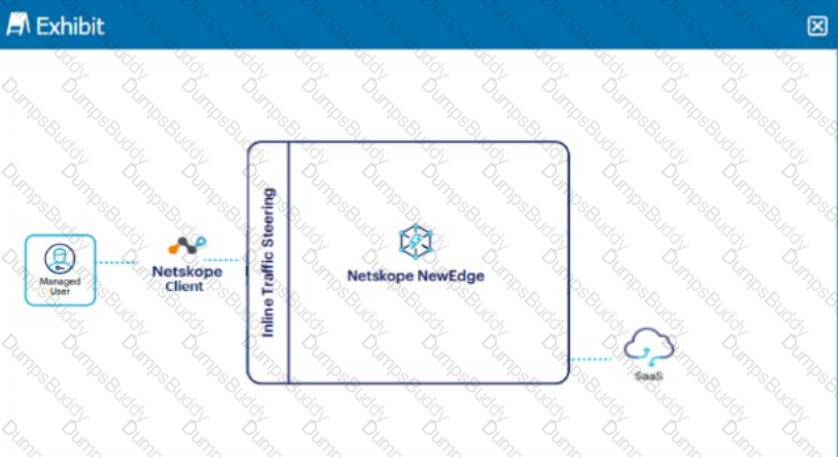
A user is connected to a SaaS application through Netskope's Next Gen SWG with SSL inspection enabled. In this scenario, what information is available in SkopeIT? (Choose three.)
Your customer asks you to secure all Web traffic as part of the initial configuration. In the Netskope platform, which statement is correct in this scenario?
Your company has implemented Netskope's Cloud Firewall and requires that all FTP connections are blocked regardless of the ports being used.
Which two statements correctly identify how to block FTP access? (Choose two.)
Which two common security frameworks are used today to assess and validate a vendor's security practices? (Choose two.)
A user has performed a bulk delete activity. In this scenario, which Netskope feature monitors potential risky users for a malicious activity that would cause data loss?
A customer asks you to create several real-time policies. Policy A generates alerts when any user downloads, uploads, or shares files on a cloud storage application. Policy B blocks users from downloading files from any operating system (OS) other than Mac or Windows for cloud storage. In this case, policy A is least restrictive and policy B is more restrictive.
Which statement is correct in this scenario?
Which three status indicators does the NPA Troubleshooter Tool provide when run? (Choose three)
You want to take into account some recent adjustments to CCI scoring that were made in your Netskope tenant.
In this scenario, which two CCI aspects in the Ul would be used in a real-time protection policy? (Choose two.)
Click the Exhibit button.
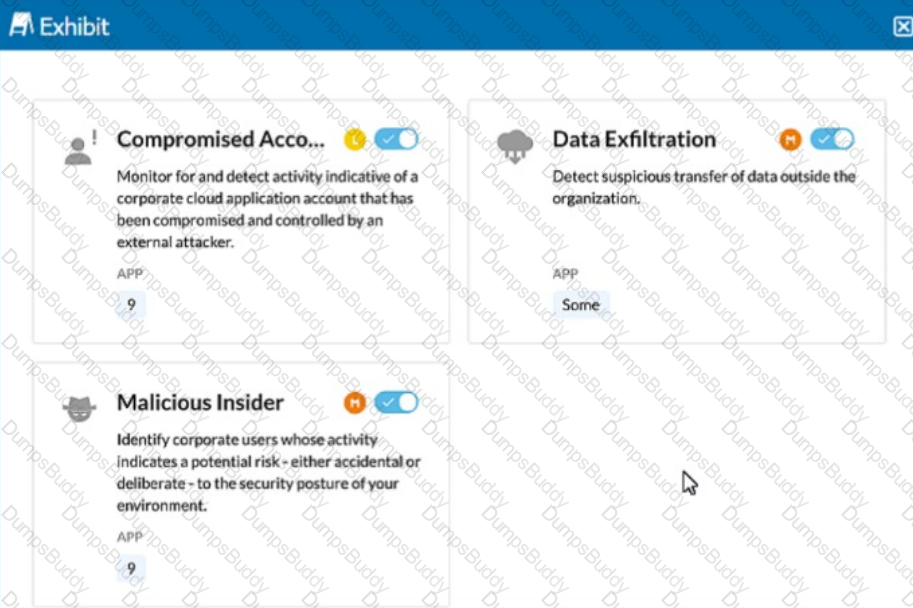
The exhibit shows security rules that are part of which component of the Netskope platform?
As an administrator, you need to configure the Netskope Admin UI to be accessible by specific IP addresses and to display a custom message after the admin users have been authenticated.
Which two statements are correct in this scenario? (Choose two.)
All users are going through Netskope's Next Gen SWG. Your CISO requests a monthly report of all users who are accessing cloud applications with a "Low" or a "Poor" CCL, where the activity is either "Edit" or "Upload".
Using the Advanced Analytics interface, which two statements describe which actions must be performed in this scenario? (Choose two.)
A customer changes CCI scoring from the default objective score to another score. In this scenario, what would be a valid reason for making this change?
Your organization has recently implemented Netskope Private Access. During an investigation, your security team has asked you to provide a list of all hosts including domains and IP addresses that a user accessed through Netskope Private Access for the past seven days.
Which two locations in the Netskope Web UI would allow you to obtain and export the requested data? (Choose two.)
You are attempting to allow access to an application using NPA. Private Apps steering is already enabled for all users.
In this scenario, which two actions are required to accomplish this task? (Choose two.)
What are two valid use cases for the Cloud Confidence Index (CCI)? (Choose two.)
Click the Exhibit button.
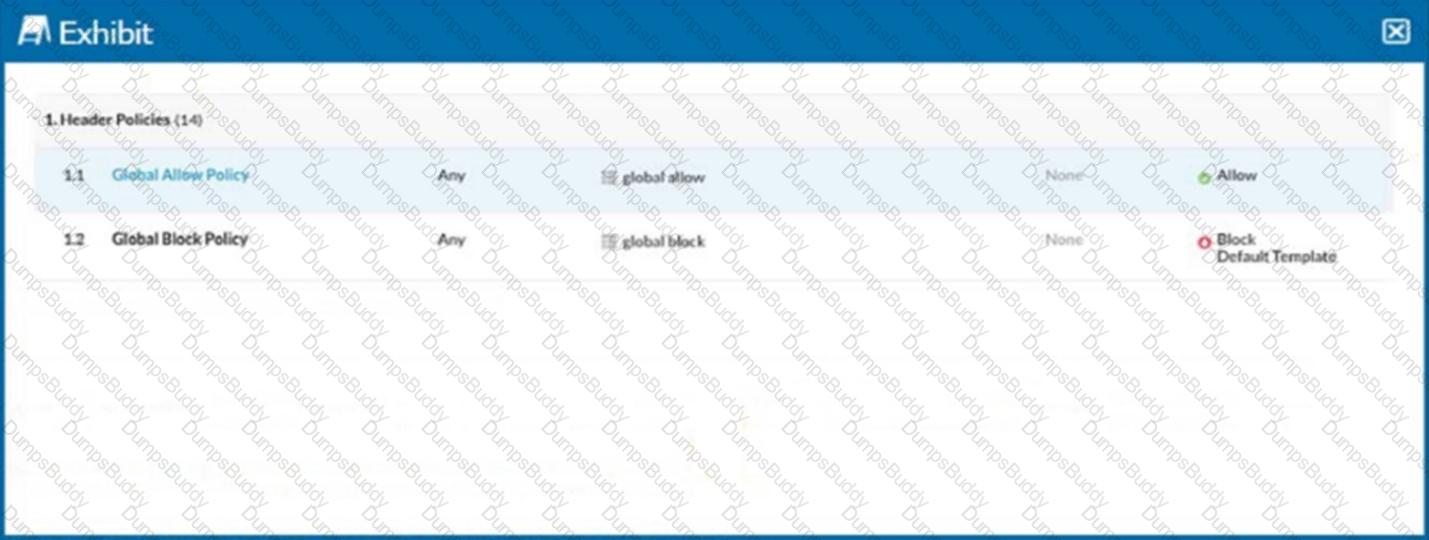
Referring to the exhibit, you have a user reporting that a blocked website is needed for legitimate business reasons. Upon review, you determine that the user has been blocked by the Global Block policy. You need to create an exception forthat domain. You create a custom URL list that includes the domain.
In this scenario, which two actions would allow this access? (Choose two.)
You are working with a large retail chain and have concerns about their customer data. You want to protect customer credit card data so that it is never exposed in transit or at rest. In this scenario, which regulatory compliance standard should be used to govern this data?
You are setting up a real-time threat protection policy for patient zero to block previously unseen files until a benign verdict is produced by the Netskope Threat Protection Service. In this scenario, which two policy parameters must you configure? (Choose two)
You added a new private app definition and created a Real-time Protection policy to allow access for all users. You have a user who reports that they are unable to access the application but all other applications work fine.
Which statement correctly describes how to troubleshoot this issue using the Netskope Web UI?
You want to block access to sites that use self-signed certificates. Which statement is true in this scenario?
You are required to mitigate malicious scripts from being downloaded into your corporate devices every time a user goes to a website. Users need to access websites from a variety of categories, including new websites.
Which two actions would help you accomplish this task while allowing the user to work? (Choose two.)
You are adding a new tenant administrator in the Admins page. Which additional security measure would you be able to enable for only this new account?
Which Netskope platform component uses NewEdge Traffic Management for traffic steering?
A customer wants to detect misconfigurations in their AWS cloud instances.
In this scenario, which Netskope feature would you recommend to the customer?
When accessing an encrypted website (HTTPS), what is a reason why you might receive a "certificate not trusted" browser message?
As an administrator, you are asked to monitor the status of your IPsec and GRE tunnels.
In the Netskope Admin UI, which two sections would you use in this scenario? (Choose two.)
Exhibit
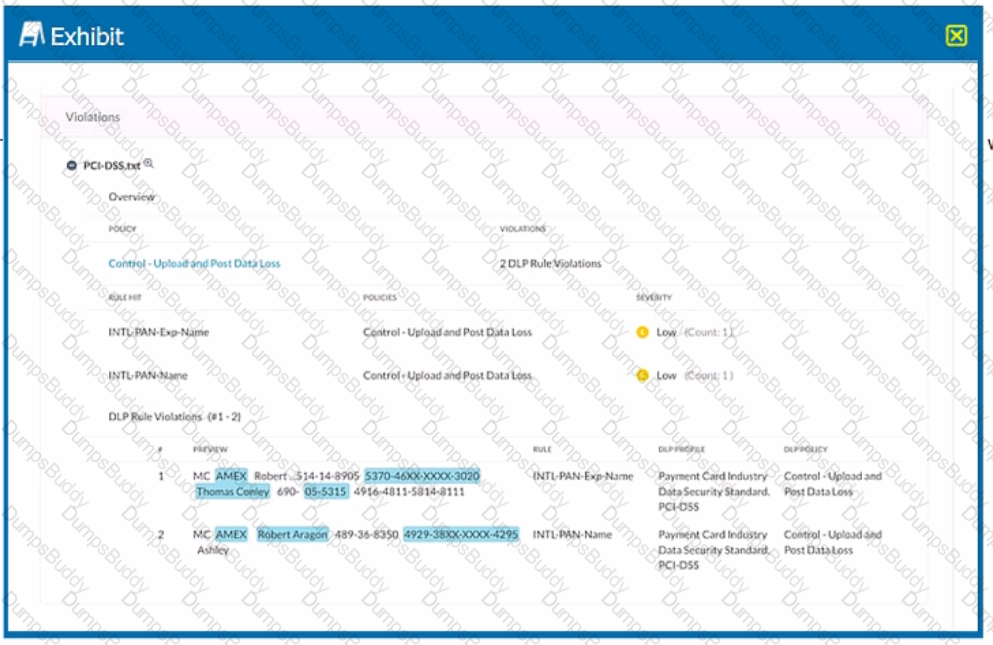
Which portion of the interface shown in the exhibit allows an administrator to set severity, assign ownership, track progress, and perform forensic analysis with excerpts of violating content?
You just deployed the Netskope client in Web mode and several users mention that their messenger application is no longer working. Although you have a specific real-time policy that allows this application, upon further investigation you discover that it is using proprietary encryption. You need to permit access to all the users and maintain some visibility.
In this scenario, which configuration change would accomplish this task?


