FCSS_EFW_AD-7.4 FCSS - Enterprise Firewall 7.4 Administrator Questions and Answers
Refer to the exhibit, which shows a LAN interface connected from FortiGate to two FortiSwitch devices.
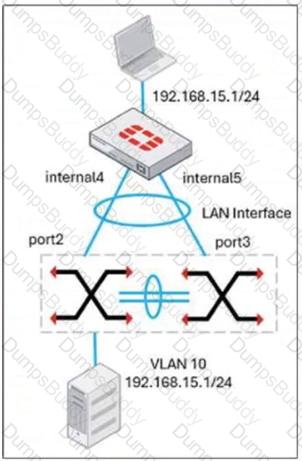
What two conclusions can you draw from the corresponding LAN interface? (Choose two.)
An administrator configured the FortiGate devices in an enterprise network to join the Fortinet Security Fabric. The administrator has a list of IP addresses that must be blocked by the data center firewall. This list is updated daily.
How can the administrator automate a firewall policy with the daily updated list?
Refer to the exhibit, which contains a partial command output.
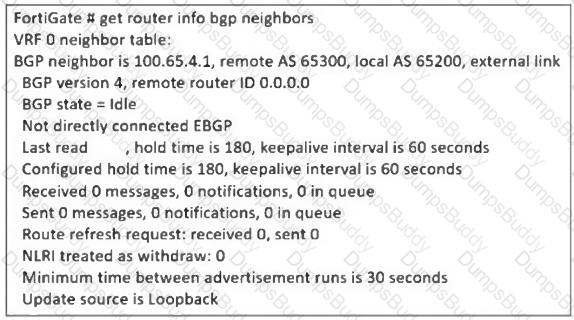
The administrator has configured BGP on FortiGate. The status of this new BGP configuration is shown in the exhibit.
What configuration must the administrator consider next?
Refer to the exhibit, which shows the packet capture output of a three-way handshake between FortiGate and FortiManager Cloud.
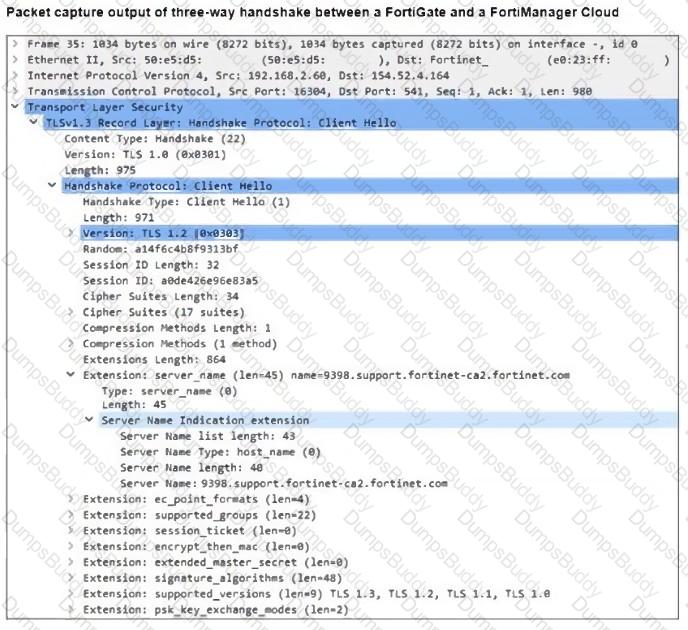
What two conclusions can you draw from the exhibit? (Choose two.)
The IT department discovered during the last network migration that all zero phase selectors in phase 2 IPsec configurations impacted network operations.
What are two valid approaches to prevent this during future migrations? (Choose two.)
Why does the ISDB block layers 3 and 4 of the OSI model when applying content filtering? (Choose two.)
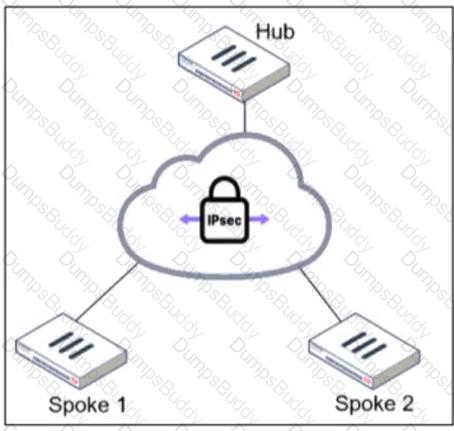
Refer to the exhibit, which shows an ADVPN network.
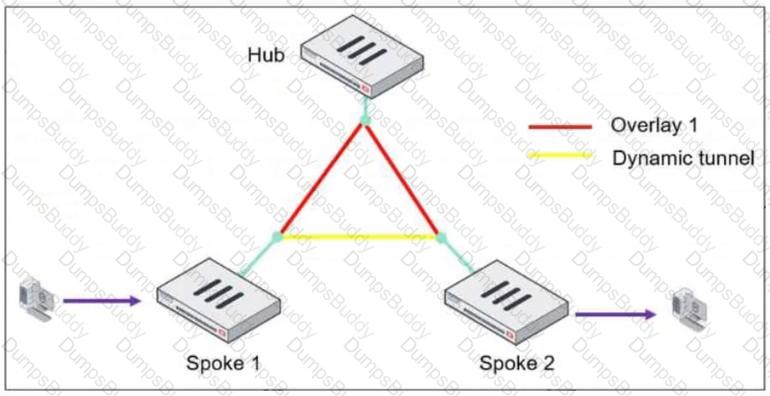
The client behind Spoke-1 generates traffic to the device located behind Spoke-2.
What is the first message that the hub sends to Spoke-1 to bring up the dynamic tunnel?
Refer to the exhibit.
An administrator is deploying a hub and spokes network and using OSPF as dynamic protocol.
Which configuration is mandatory for neighbor adjacency?
An administrator is designing an ADVPN network for a large enterprise with spokes that have varying numbers of internet links. They want to avoid a high number of routes and peer connections at the hub.
Which method should be used to simplify routing and peer management?
A vulnerability scan report has revealed that a user has generated traffic to the website example.com (10.10.10.10) using a weak SSL/TLS version supported by the HTTPS web server.
What can the firewall administrator do to block all outdated SSL/TLS versions on any HTTPS web server to prevent possible attacks on user traffic?
Refer to the exhibit, which shows a partial troubleshooting command output.
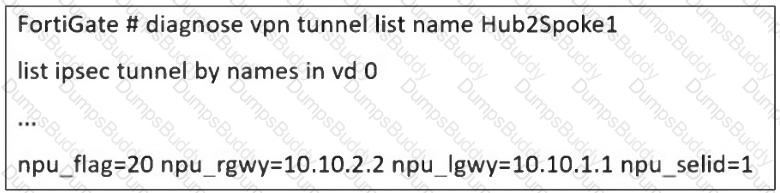
An administrator is extensively using IPsec on FortiGate. Many tunnels show information similar to the output shown in the exhibit.
What can the administrator conclude?
An administrator must minimize CPU and RAM use on a FortiGate firewall while also enabling essential security features, such as web filtering and application control for HTTPS traffic.
Which SSL inspection setting helps reduce system load while also enabling security features, such as web filtering and application control for encrypted HTTPS traffic?
Refer to the exhibit, which shows the HA status of an active-passive cluster.
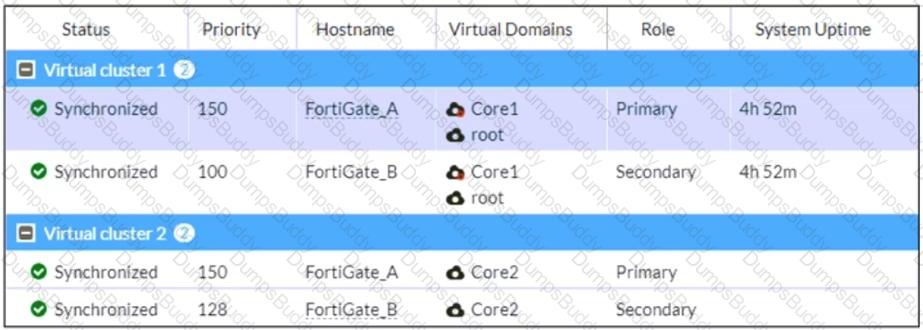
An administrator wants FortiGate_B to handle the Core2 VDOM traffic.
Which modification must the administrator apply to achieve this?
An administrator is checking an enterprise network and sees a suspicious packet with the MAC address e0:23:ff:fc:00:86.
What two conclusions can the administrator draw? (Choose two.)
 A client behindSpoke-1sends traffic to a device behindSpoke-2.
A client behindSpoke-1sends traffic to a device behindSpoke-2. The traffic initially flows through thehub, following the pre-established overlay tunnel.
The traffic initially flows through thehub, following the pre-established overlay tunnel. Thehubdetects that Spoke-1 is communicating with Spoke-2 and determines that adirect shortcut tunnelbetween the spokes can optimize the connection.
Thehubdetects that Spoke-1 is communicating with Spoke-2 and determines that adirect shortcut tunnelbetween the spokes can optimize the connection. Thehub sends a "Shortcut Offer"message to Spoke-1, informing it that a directdynamic tunnelto Spoke-2 is possible.
Thehub sends a "Shortcut Offer"message to Spoke-1, informing it that a directdynamic tunnelto Spoke-2 is possible. Spoke-1 and Spoke-2 then negotiate and establish a directIPsec tunnelfor communication.
Spoke-1 and Spoke-2 then negotiate and establish a directIPsec tunnelfor communication.
