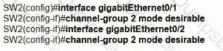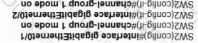200-301 Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1 Questions and Answers
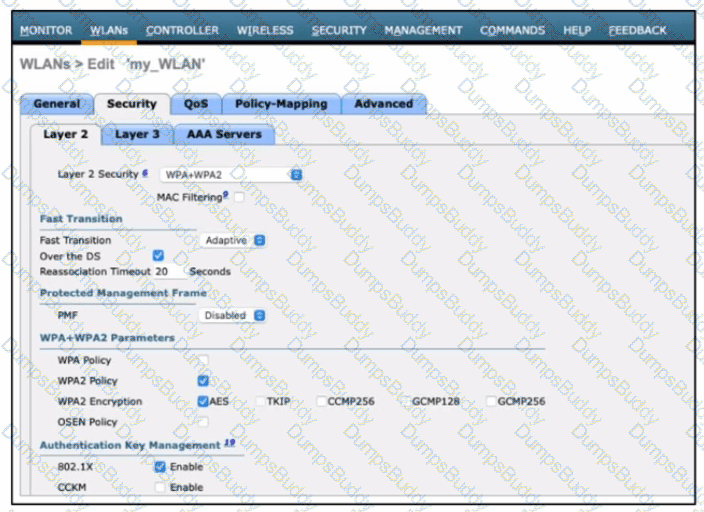
Refer to the exhibit. A network engineer is configuring a wireless LAN with Web Passthrough Layer 3 Web Policy. Which action must the engineer take to complete the configuration?
200-301 Report Card
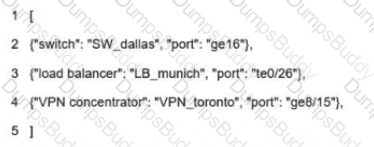
Connectivity between four routers has been established. IP connectivity must be configured in the order presented to complete the implementation. No dynamic routing protocols are included.
1. Configure static routing using host routes to establish connectivity from router R3 to the router R1 Loopback address using the source IP of 209.165.200.230.
2. Configure an IPv4 default route on router R2 destined for router R4.
3. Configure an IPv6 default router on router R2 destined for router R4.

Refer to the exhibit.
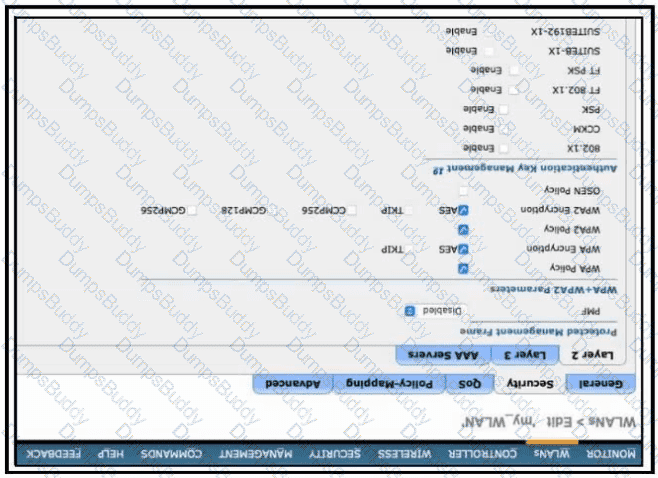
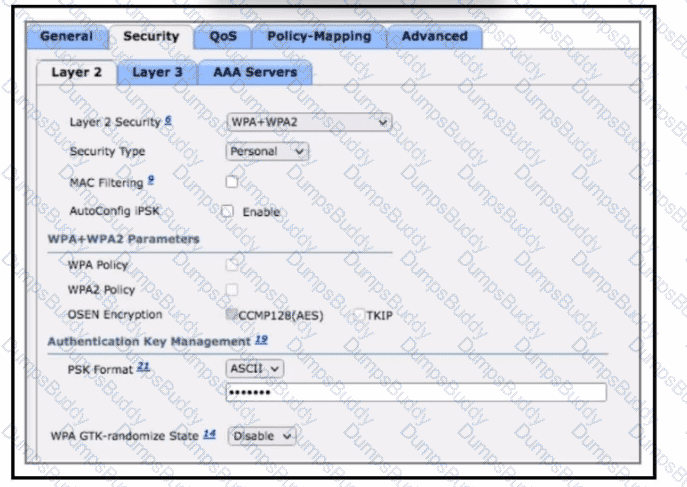
Which configuration is needed to configure a WLAN with WPA2 only and with a password that is 63 characters long?
Where are the real-time control functions processed in a split MAC architecture?
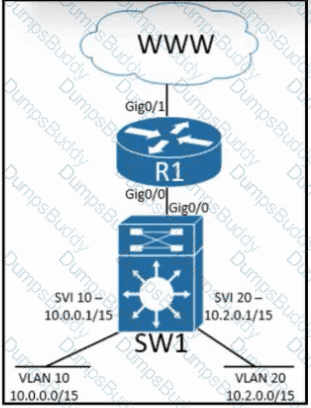
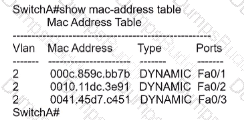
Refer to the exhibit. Inter-VLAN routing is configured on SW1. Client A is running Linux as an OS in VLAN 10 with a default gateway IP 10.0.0.1 but cannot ping client B in VLAN 20 running Windows. What action must be taken to verify that client A has the correct IP settings?
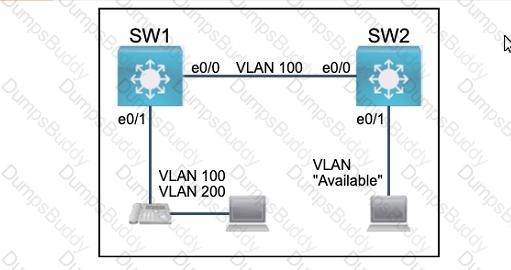
All physical cabling between the two switches is installed. Configure the network connectivity between the switches using the designated VLANs and interfaces.
1. Configure VLAN 100 named Compute and VLAN 200 named Telephony where required for each task.
2. Configure Ethernet0/1 on SW2 to use the existing VLAN named Available.
3. Configure the connection between the switches using access ports.
4. Configure Ethernet0/1 on SW1 using data and voice VLANs.
5. Configure Ethemet0/1 on SW2 so that the Cisco proprietary neighbor discovery protocol is turned off for the designated interface only.
Which combination of methods satisfies the minimum security requirements when a new multifactor authentication solution is deployed?
Which interface is used to send traffic to the destination network?
10.174.208.210/28 [110/2708] via G0/21
10.174.208.210/28 [110/25445] via G0/20
10.174.208.210/28 [120/1] via G0/12
10.174.208.210/28 [120/4] via G0/16
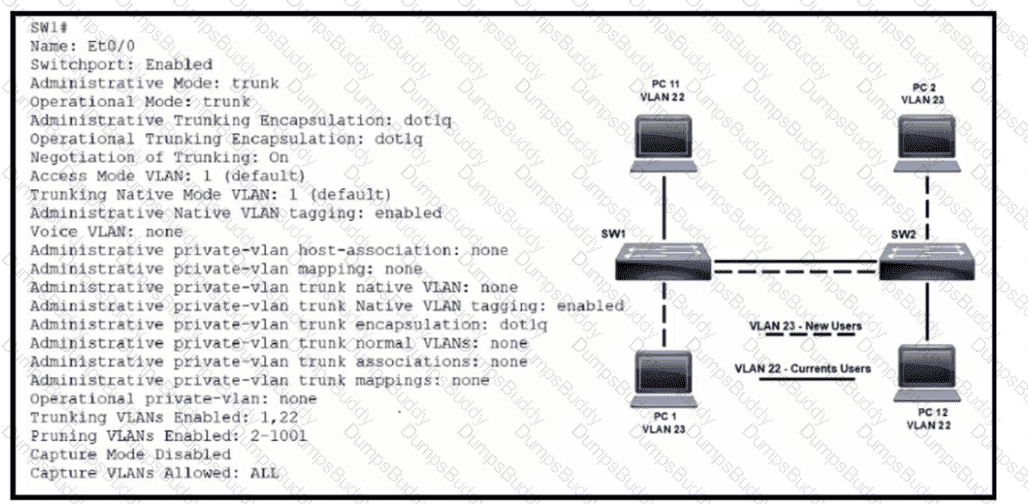
Refer to the exhibit. VLAN 23 is being implemented between SW1 and SW2. The command show interface ethernet0/0 switchport has been issued on SW1. Ethernet0/0 on SW1 is the uplink to SW2. Which command when entered on the uplink interface allows PC 1 and PC 2 to communicate without impact to the communication between PC 11 and PC 12?
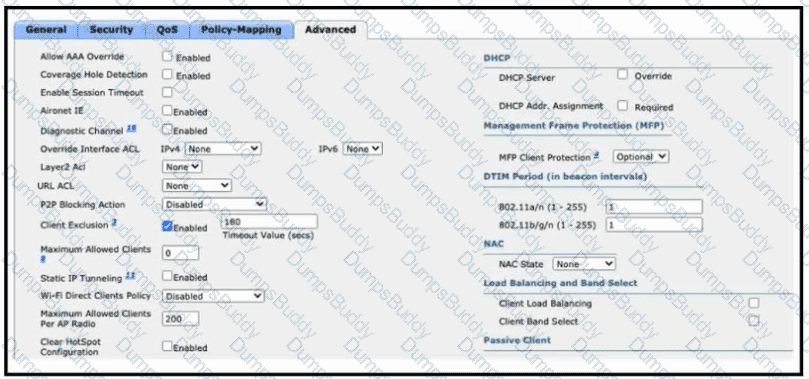
Refer to the exhibit. An administrator is configuring a new WLAN for a wireless network that has these requirements:
Dual-band clients that connect to the WLAN must be directed to the 5-GHz spectrum.
Wireless clients on this WLAN must be able to apply VLAN settings from RADIUS attributes.
Which two actions meet these requirements? (Choose two.)
Which technology allows multiple operating systems lo run a single physical server?
Which technology allows for logical Layer 3 separation on physical network equipment?
Which security element uses a combination of one-time passwords, a login name, and a personal smartphone?
Which default condition must be considered when an encrypted mobility tunnel is used between two Cisco WLCs?
All physical cabling is in place. A company plans to deploy 32 new sites.
The sites will utilize both IPv4 and IPv6 networks.
1 . Subnet 172.25.0.0/16 to meet the subnet requirements and maximize
the number of hosts
Using the second subnet
• Assign the first usable IP address to e0/0 on Sw1O1
• Assign the last usable IP address to e0/0 on Sw102
2. Subnet to meet the subnet requirements and maximize
the number of hosts
c Using the second subnet
• Assign an IPv6 GUA using a unique 64-Bit interface identifier
on e0/0 on Sw101
• Assign an IPv6 GUA using a unique 64-Bit interface identifier
on eO/O on swi02
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.

Which IP address is used when an administrator must open a web-based management session with a lightweight AP?
Which interface is used to send traffic to the destination network?
10.249.210.56/25 [90/6144] via G0/15
10.249.210.56/25 [90/45053] via G0/13
10.249.210.56/25 [110/3693] via G0/16
10.249.210.56/25 [110/360] via G0/12
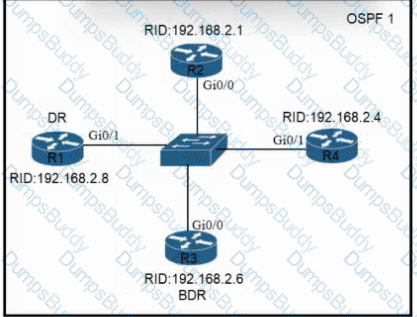
Refer to the exhibit. All routers In the network are configured. R2 must be the DR. After the engineer connected the devices, R1 was elected as the DR. Which command sequence must be configured on R2 to be elected as the DR in the network?

A new DHCP server has been deployed in a corporate environment with lease time set to eight hours. Which CMD command on a Windows-based device allows the engineer to verify the DHCP lease expiration?
Which syslog message logging level displays interface line protocol up/down events?
Which action prevents debug messages from being sent via syslog while allowing other messages when an abnormally high number of syslog messages are generated by a device with the debug process turned on?
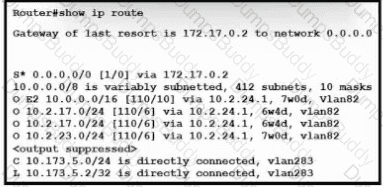
Refer to the exhibit. What is the value of the administrative distance for the default gateway?
Aswitch receives a frame with the destination MAC address 3C:5D: 7E:9F: 1A:2B.
Switch# show ethernet-frame-and-mac-address-table
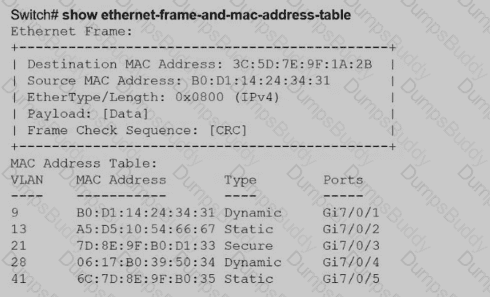
How does the switch handle the frame?
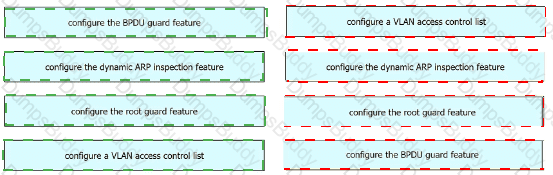
Which feature Is mandatory when configuring a new SSID for a wireless network running WPA3-Personal mode?
Refer to the exhibit.
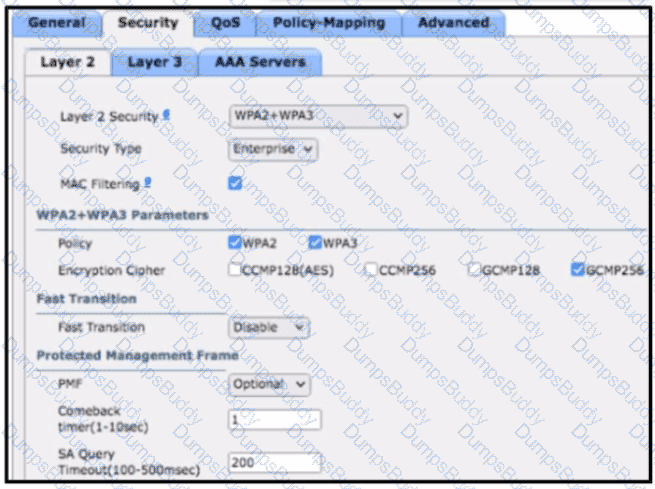
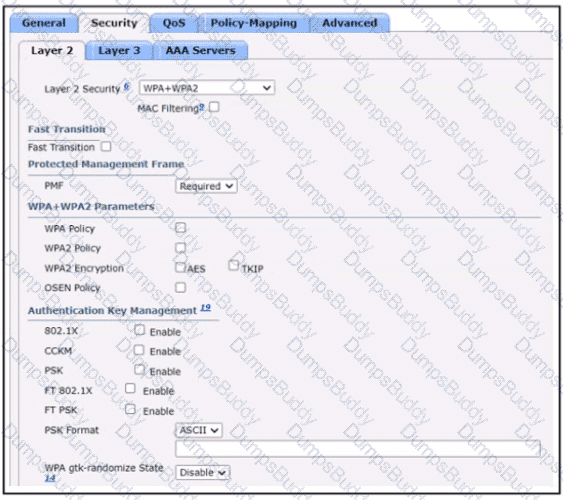
An engineer must document all Wi-Fi services on a new wireless LAN controller. The Wi-Fi SSID "Office_WLan" has Layer 2 Security. What is determined by this configuration?
Which two northbound APIs are found in a software-defined network? (Choose two.)
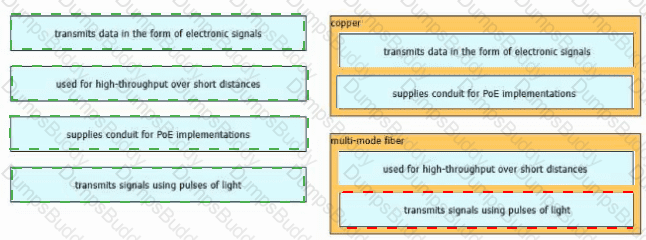
Drag and drop the characteristic from the left onto the cable type on the right.
Which interface is used to send traffic to the destination network?
O 10.76.170 161/26 |110/102] via FO/17
O 10.76.170 161/26[110/27e31] via FO/20
R 10.76.170.161/261120/15] via FO/8
R 10.76.170.161/26 [120/10] via FO/12
Which two principles must be considered when using per-hop behavior in QoS? (Choose two.)
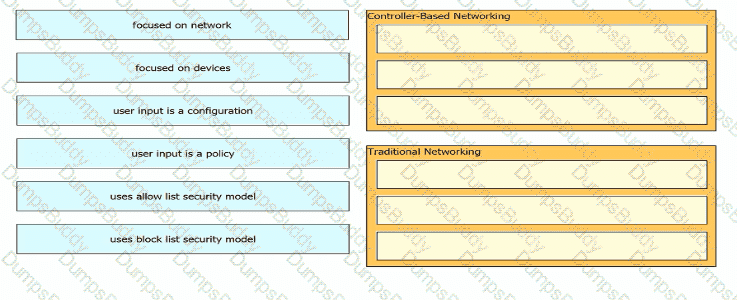
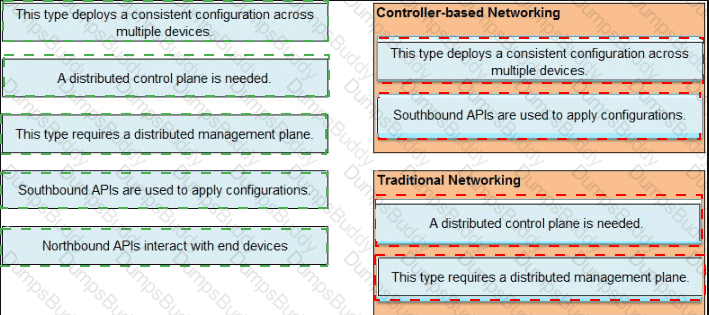
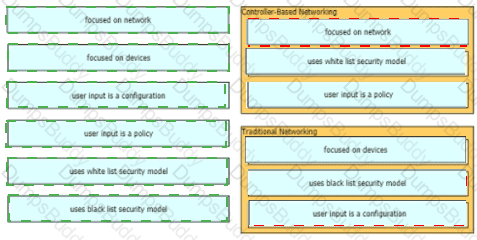
What is an advantage of using SDN versus traditional networking when it comes to security?
Which switch port configuration must be configured when connected to an AP running in FlexConnect mode, and the WLANs use flex local switching?
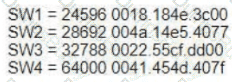
Refer to the exhibit.
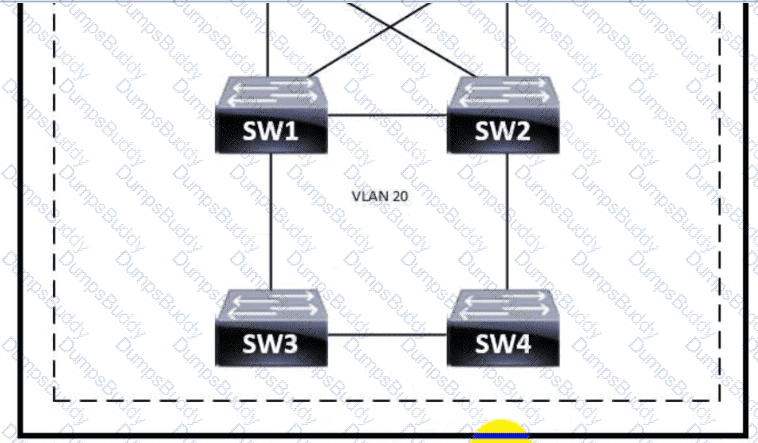
Which switch becomes the root of a spanning tree for VLAN 20 if all li links are of equal speed?
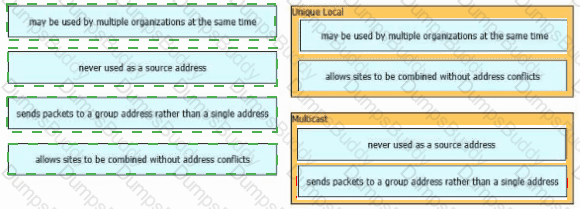
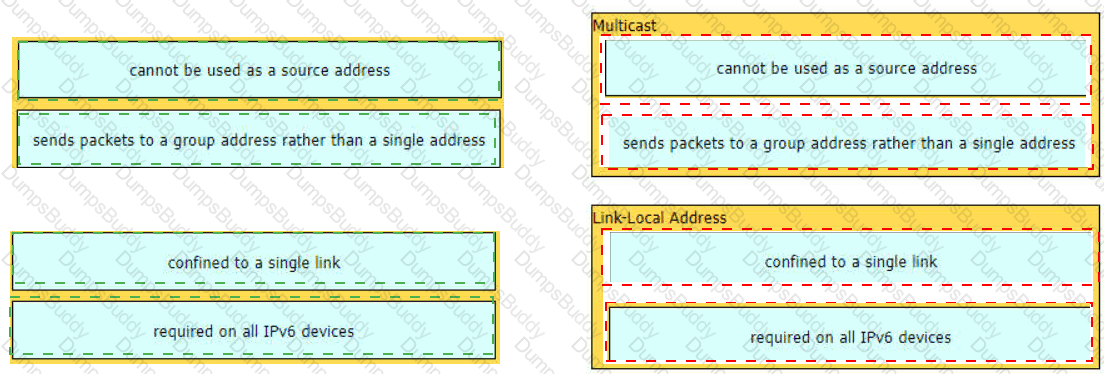
Which type of IPv6 address is similar to a unicast address but is assigned to multiple devices on the same network at the same time?
Which QoS per-hop behavior changes the value of the ToS field in the IPv4 packet header?
Refer to the exhibit.
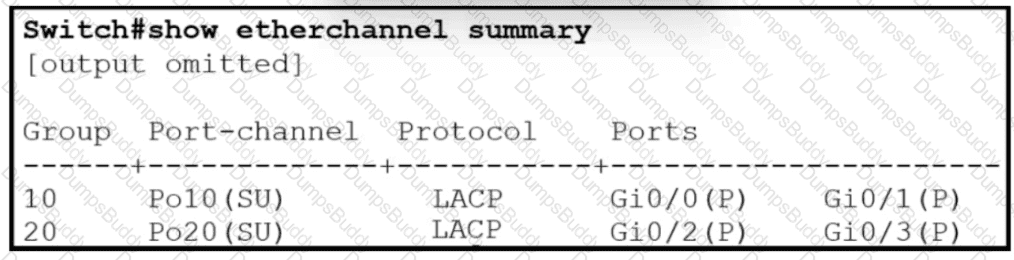
Which two commands when used together create port channel 10? (Choose two.)
A Cisco engineer must configure a single switch interface to meet these requirements
• accept untagged frames and place them in VLAN 20
• accept tagged frames in VLAN 30 when CDP detects a Cisco IP phone
Which command set must the engineer apply?
A)

B)

C)

D)

Refer to the exhibit.
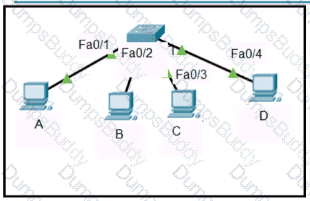
Host A sent a data frame destined for host D
What does the switch do when it receives the frame from host A?
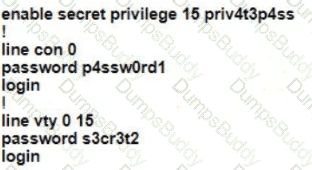
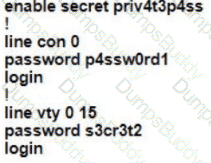
A Cisco engineer is configuring a factory-default router with these three passwords:
• The user EXEC password for console access is p4ssw0rd1
• The user EXEC password for Telnet access is s3cr3t2
• The password for privileged EXEC mode is pnv4t3p4ss Which command sequence must the engineer configured
A)
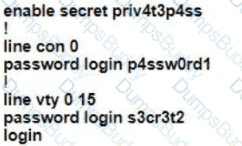
B)
C)
D)

Refer to the exhibit.
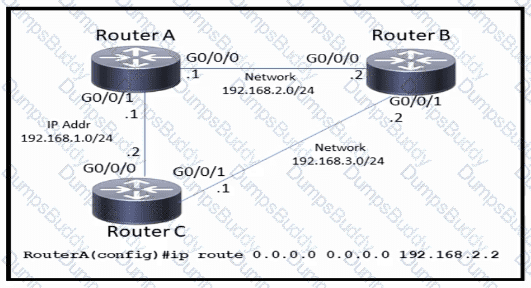
Which command must be issued to enable a floating static default route on router A?
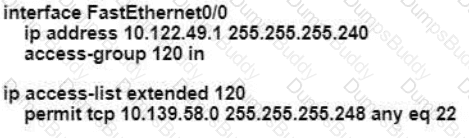
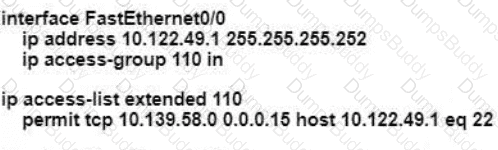
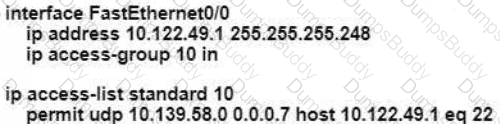
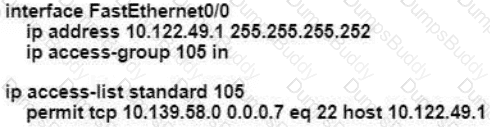
An engineer is configuring remote access to a router from IP subnet 10.139.58.0/28. The domain name, crypto keys, and SSH have been configured. Which configuration enables the traffic on the destination router?
A)
B)
C)
D)
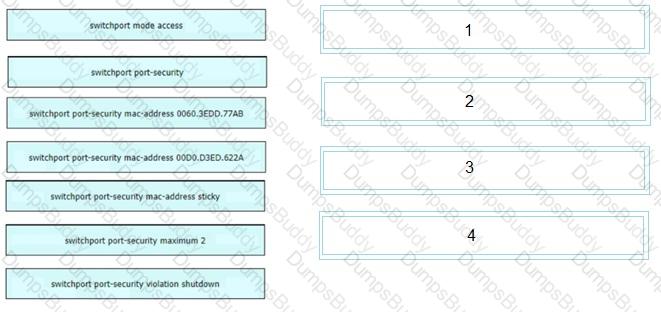
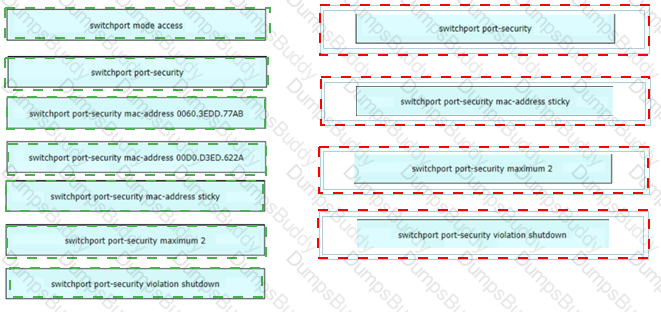
An engineer is tasked to configure a switch with port security to ensure devices that forward unicasts multicasts and broadcasts are unable to flood the port The port must be configured to permit only two random MAC addresses at a time Drag and drop the required configuration commands from the left onto the sequence on the right Not all commands are used.
Refer to the exhibit.

All VLANs are present in the VLAN database. Which command sequence must be applied to complete the configuration?
Refer to the exhibit.
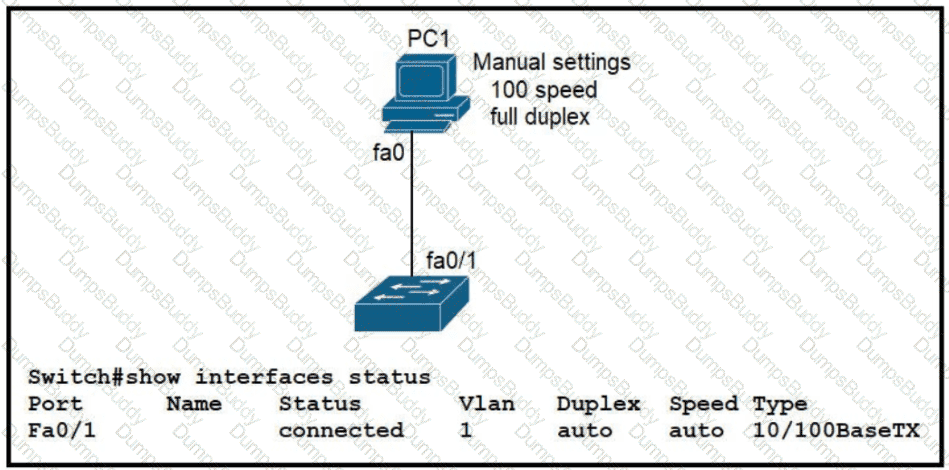
The link between PC1 and the switch is up. but it is performing poorly. Which interface condition is causing the performance problem?
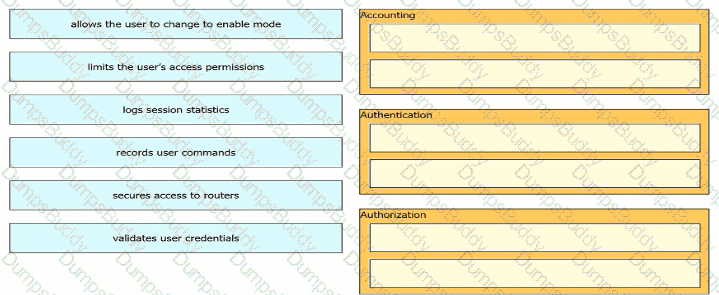
What provides centralized control of authentication and roaming In an enterprise network?
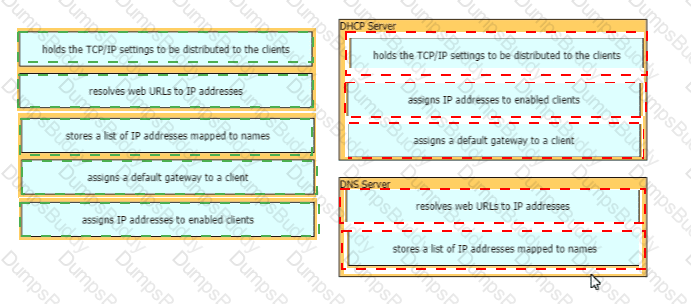
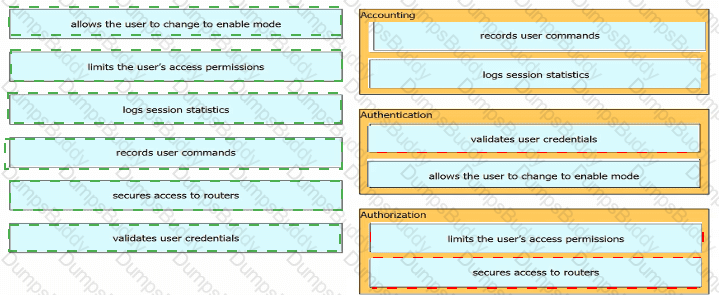
Drag and drop the descriptions of AAA services from the left onto the corresponding services on the right.
Which interface is used to send traffic to the destination network?
O 10.18.75.113/27 [110/6906] via GO/6
O 10.18.75.113/27 [110/23018] via GO/3
R 10.18.75.113/27 [120/16] via GO/16
R 10.18.75.113/27 [120/14] via GO/23
Which WLC management connection type is vulnerable to man-in-the-middle attacks?
Refer to the exhibit.
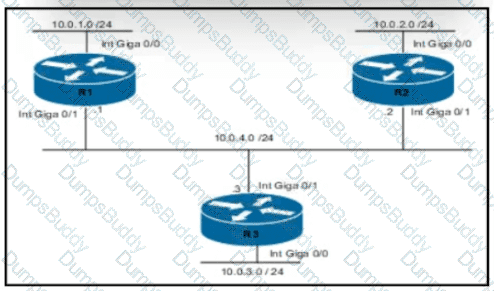
Routers R1 and R3 have the default configuration The router R2 priority is set to 99 Which commands on R3 configure it as the DR in the 10.0 4.0/24 network?
Refer to the exhibit.
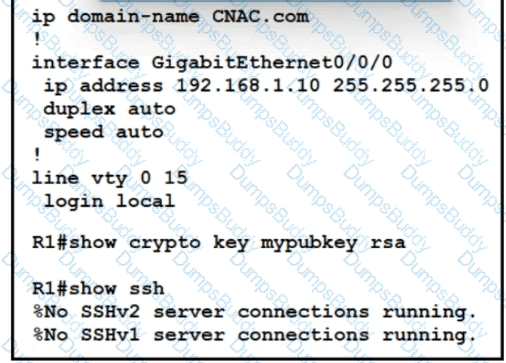
Which two commands must be added to update the configuration of router R1 so that it accepts only encrypted connections? (Choose two )
Refer to the exhibit.
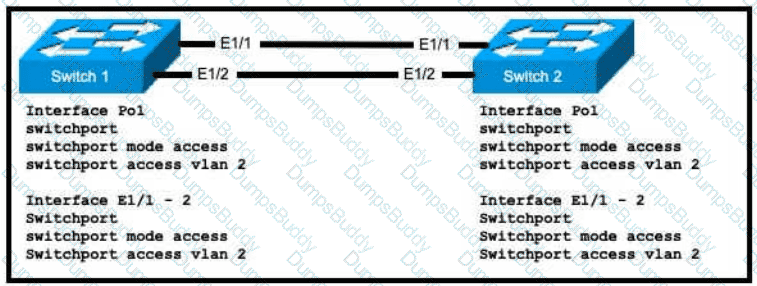
An engineer is configuring an EtherChannel using LACP between Switches 1 and 2 Which configuration must be applied so that only Switch 1 sends LACP initiation packets?
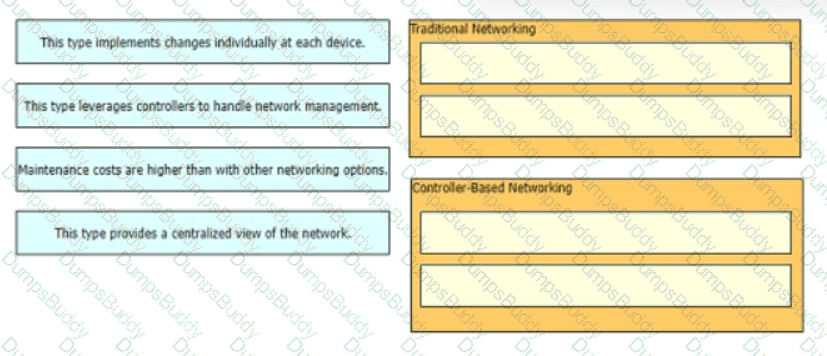
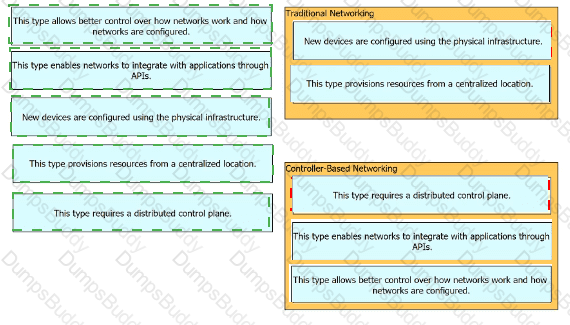
Drag and drop the statements about networking from the left onto the corresponding networking types on the right.
Which PoE mode enables powered-device detection and guarantees power when the device is detected?
Refer to the exhibit.
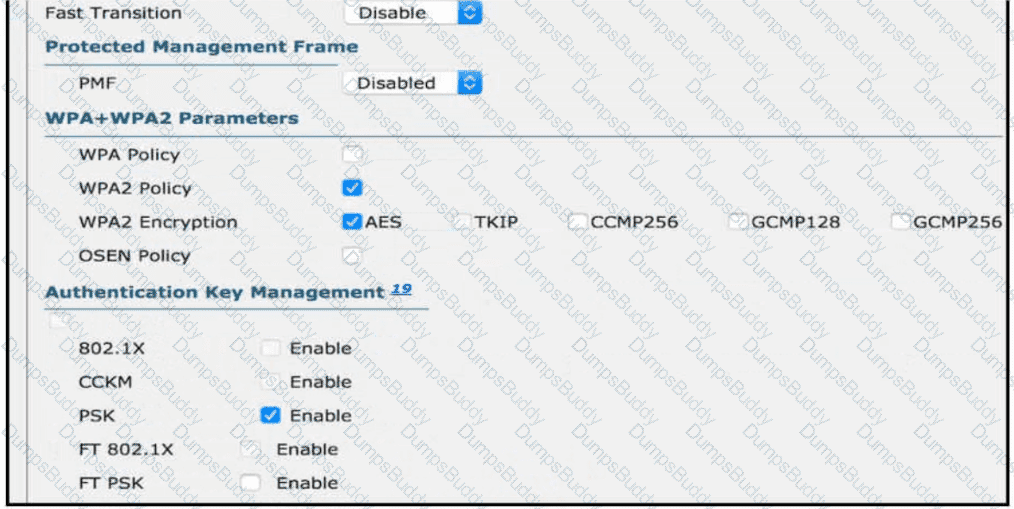
Users need to connect to the wireless network with IEEE 802. 11r-compatible devices. The connection must be maintained as users travel between floors or to other areas in the building What must be the configuration of the connection?
Refer to the exhibit.
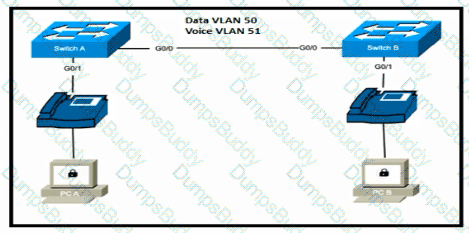
Switch A is newly configured. All VLANs are present in the VLAN database. The IP phone and PC A on Gi0/1 must be configured for the appropriate VLANs to establish connectivity between the PCs. Which command set fulfills the requirement?
A)
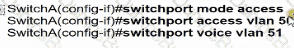
B)

C)

D)

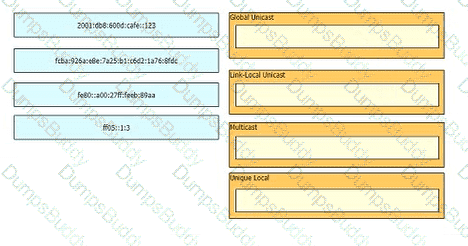
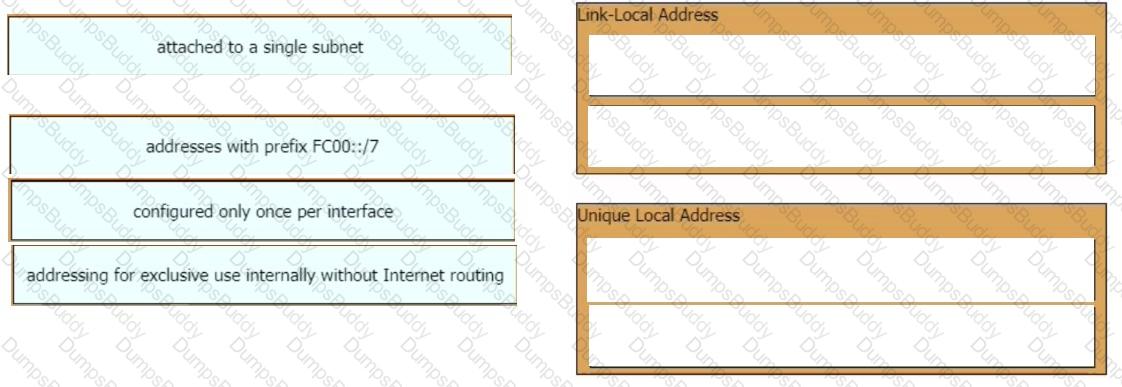
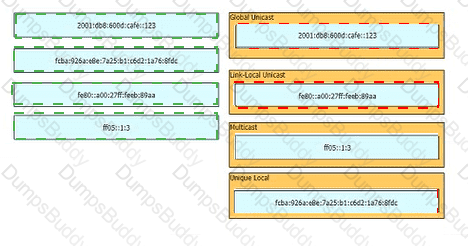
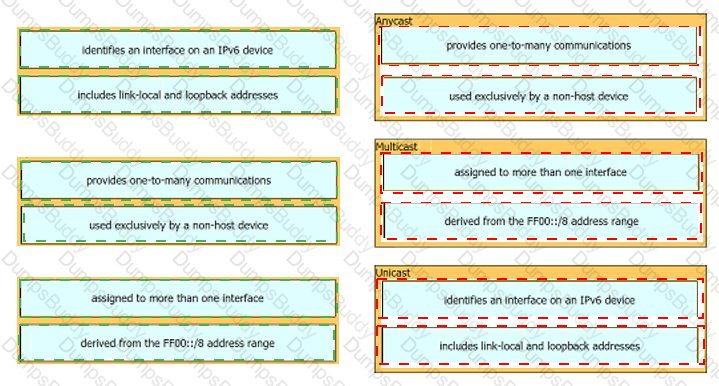
Drag and drop the IPv6 addresses from the left onto the corresponding address types on the right.
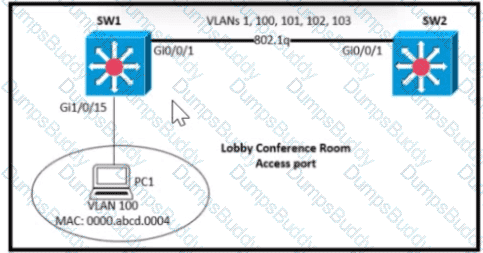
SW1 supports connectivity for a lobby conference room and must be secured. The engineer must limit the connectivity from PCI lo ma SW1 and SW2 network. The MAC addresses allowed must be Limited to two. Which configuration secures the conference room connectivity?
A)

B)

C)
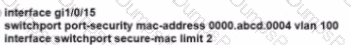
D)

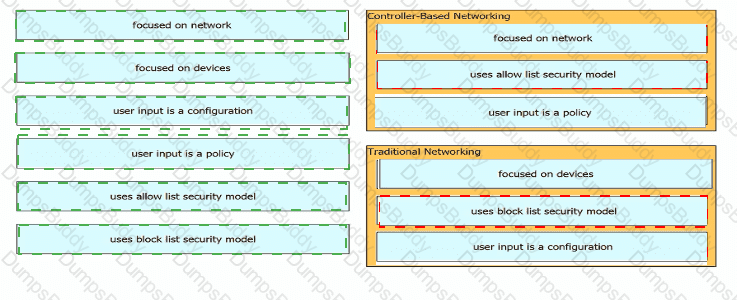
Drag and drop the characteristics of networking from the left onto the networking types on the right.
Refer to the exhibit.
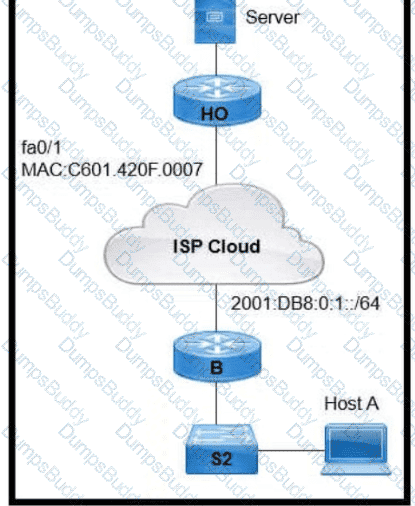
An engineer is configuring the HO router. Which IPv6 address configuration must be applied to the router fa0'1 interface for the router to assign a unique 64-brt IPv6 address to Itself?
Refer to the exhibit.
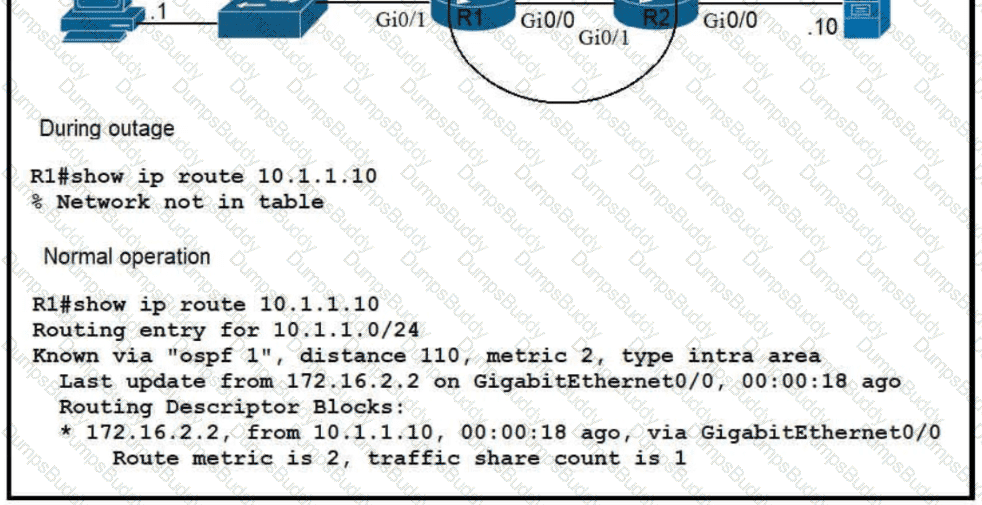
Which route must be configured on R1 so that OSPF routing is used when OSPF is up. but the server is still reachable when OSPF goes down?
Which interface mode must be configured to connect the lightweight APs in a centralized architecture?
Which characteristic differentiates the concept of authentication from authorization and accounting?
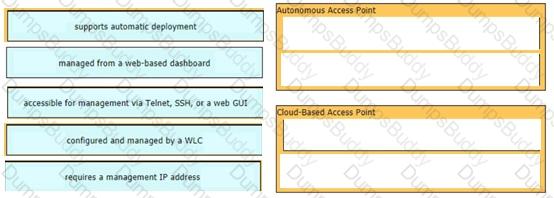
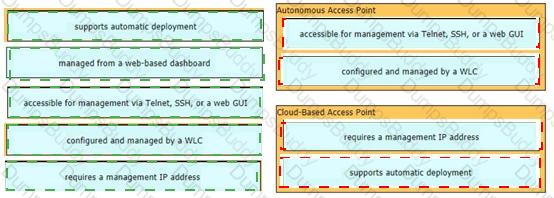
Drag and drop the facts about wireless architectures from the left onto the types of access point on the right. Not all options are used.
Refer to the exhibit.
The DHCP server and clients are connected to the same switch. What is the next step to complete the DHCP configuration to allow clients on VLAN 1 to receive addresses from the DHCP server?
Drag and drop the threat-mitigation techniques from the left onto the types of threat or attack they mitigate on the right.
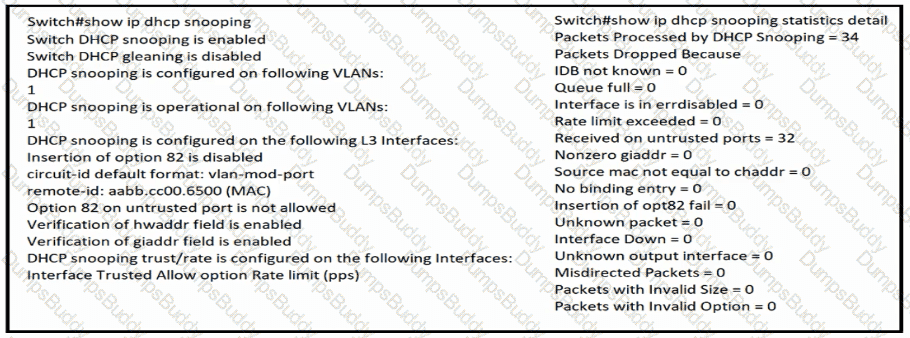
Refer to the exhibit.
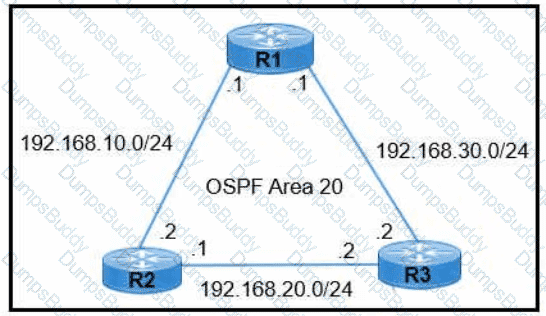
R1 learns all routes via OSPF Which command configures a backup static route on R1 to reach the 192 168.20.0/24 network via R3?
Refer to the exhibit.
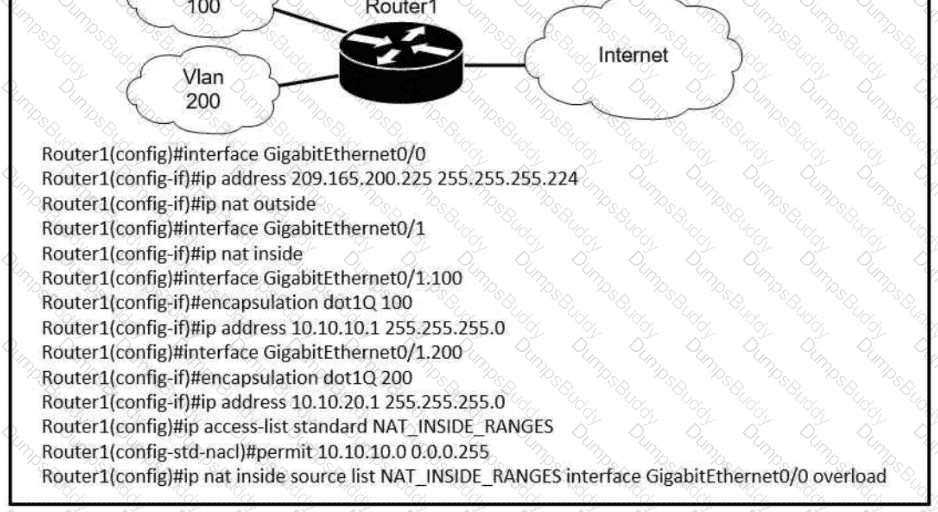
Users on existing VLAN 100 can reach sites on the Internet. Which action must the administrator take to establish connectivity to the Internet for users in VLAN 200?
Refer to the exhibit.
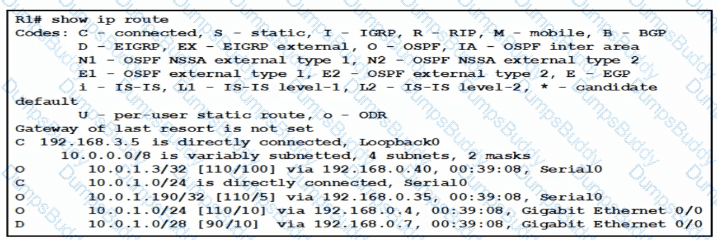
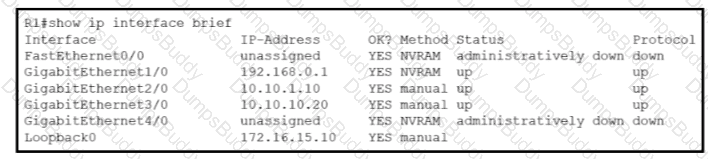
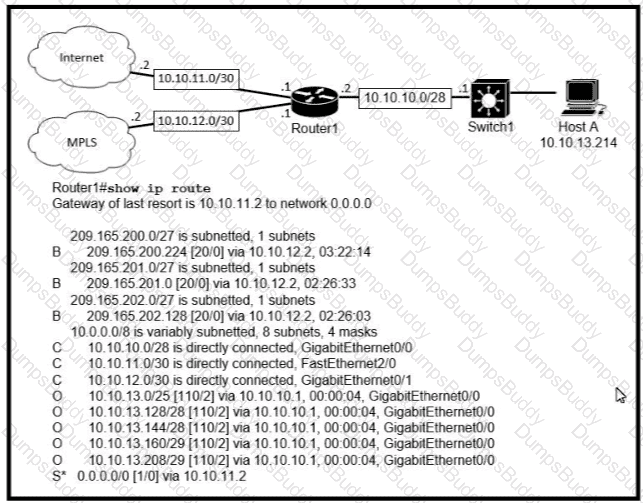
Traffic sourced from the loopback0 Interface is trying to connect via ssh to the host at 10.0.1.15. What Is the next hop to the destination address?
Refer to the exhibit.

The following must be considered:
• SW1 is fully configured for all traffic
• The SW4 and SW9 links to SW1 have been configured
• The SW4 interface Gi0/1 and Gi0/0 on SW9 have been configured
• The remaining switches have had all VLANs adde d to their VLAN database
Which configuration establishes a successful ping from PC2 to PC7 without interruption to traffic flow between other PCs?
A)
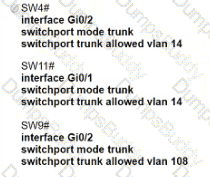
B)
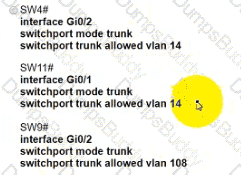
C)

D)

An engineer must configure R1 for a new user account. The account must meet these requirements:
* It must be configured in the local database.
* The username is engineer.
* It must use the strongest password configurable. Which command must the engineer configure on the router?
Which Layer 2 switch function encapsulates packets for different VLANs so that the packets traverse the same port and maintain traffic separation between the VLANs?
Refer to the exhibit.
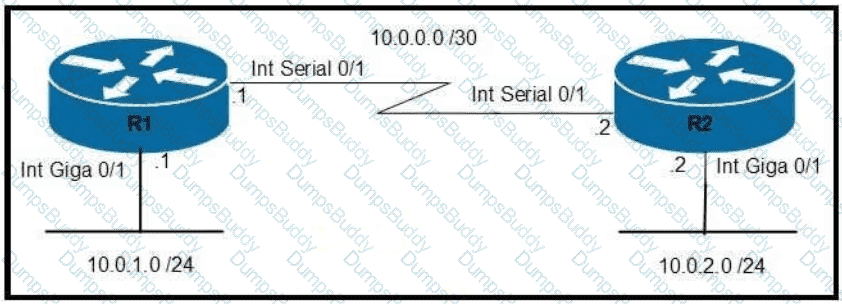
Which command configures OSPF on the point-to-point link between routers R1 and R2?
Refer to the exhibit.
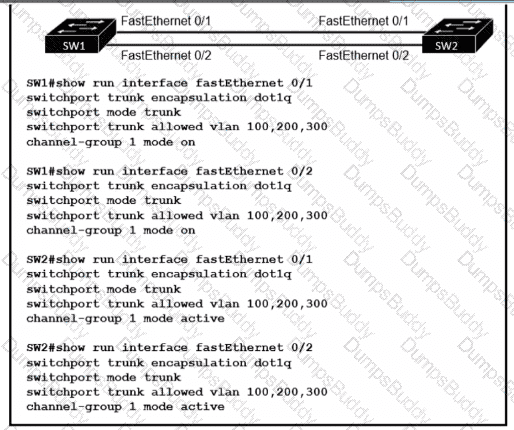
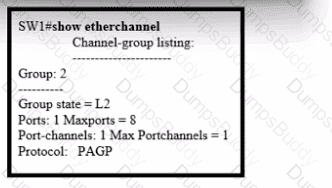
An engineer built a new L2 LACP EtherChannel between SW1 and SW2 and executed these show commands to verify the work. Which additional task allows the two switches to establish an LACP port channel?
Which action implements physical access control as part of the security program of an organization?
Refer to the exhibit.
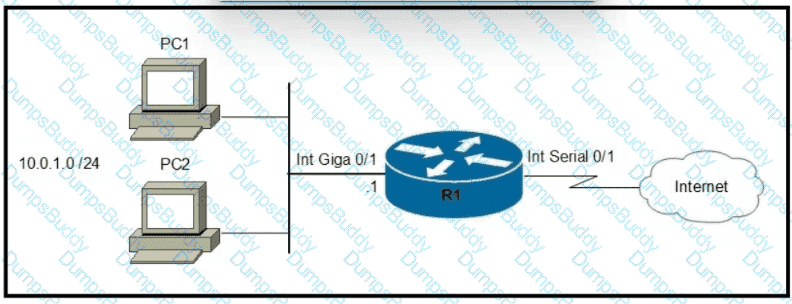
Which two commands must be configured on router R1 to enable the router to accept secure remote-access connections? (Choose two)
Refer to the exhibit.
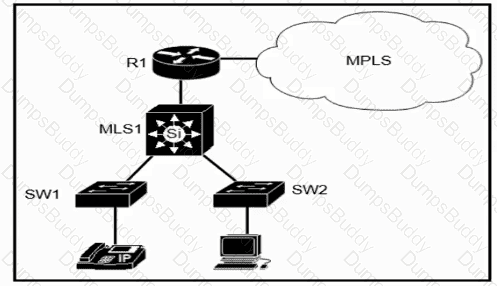
Which plan must be Implemented to ensure optimal QoS marking practices on this network?
Refer to the exhibit.
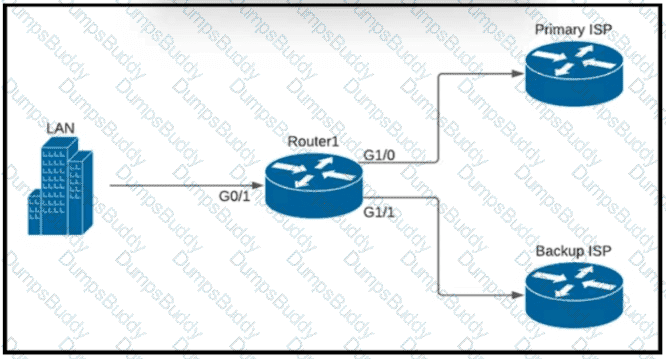
A company is configuring a failover plan and must implement the default routes in such a way that a floating static route will assume traffic forwarding when the primary link goes down. Which primary route configuration must be used?
Refer to the exhibit.
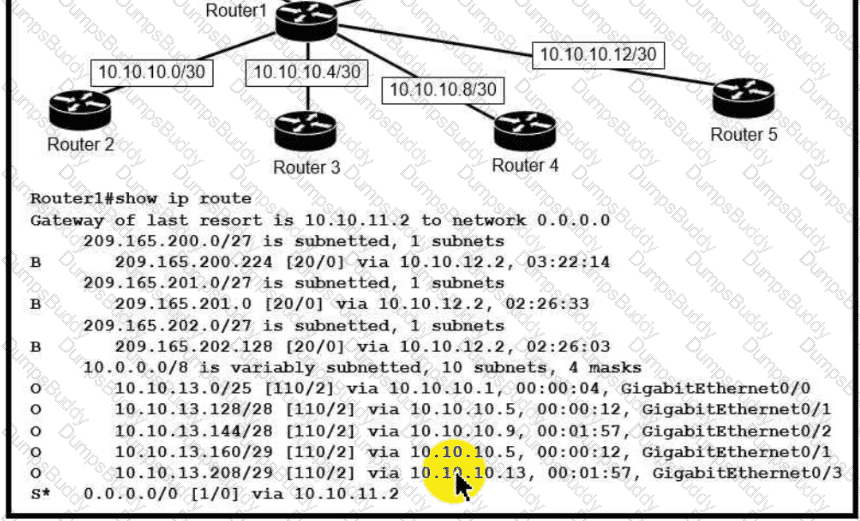
Which next-hop IP address does Routed use for packets destined to host 10 10.13.158?
Refer to the exhibit.
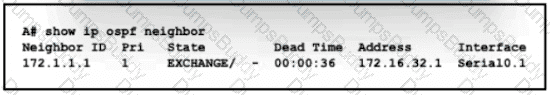
An engineer assumes a configuration task from a peer Router A must establish an OSPF neighbor relationship with neighbor 172 1 1 1 The output displays the status of the adjacency after 2 hours. What is the next step in the configuration process for the routers to establish an adjacency?
Refer to the exhibit.
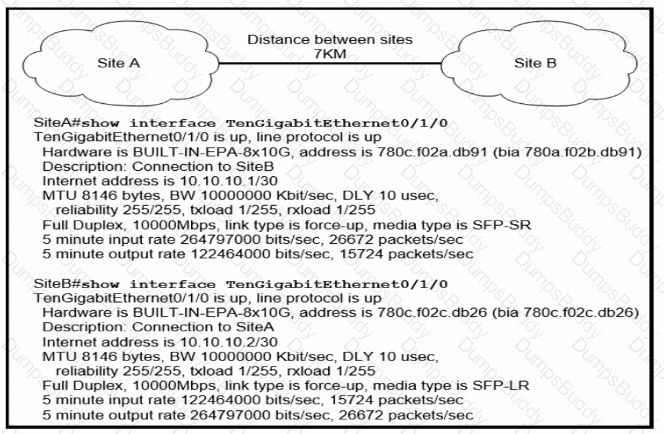
Site A was recently connected to site B over a new single-mode fiber path. Users at site A report Intermittent connectivity Issues with applications hosted at site B. What is the reason for the problem?
Which type of network attack overwhelms the target server by sending multiple packets to a port until the half-open TCP resources of the target are exhausted?
Which two spanning-tree states are bypassed on an interface running PortFast? (Choose two.)
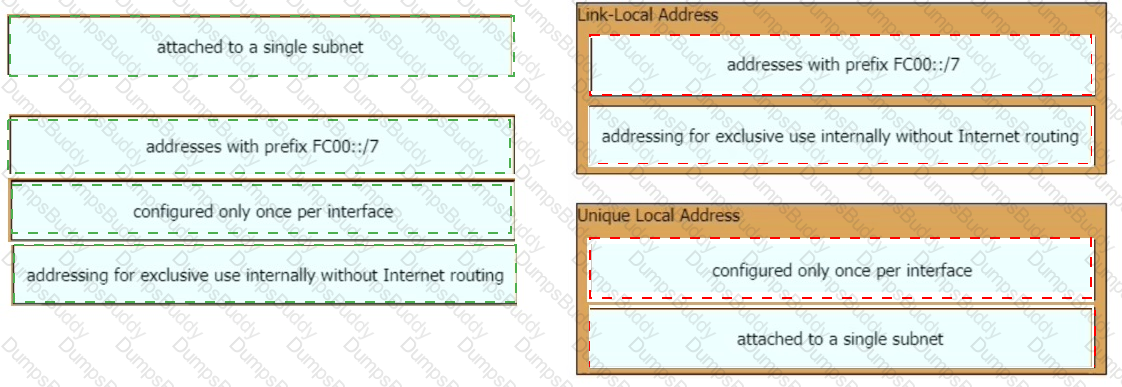
A network engineer is installing an IPv6-only capable device. The client has requested that the device IP address be reachable only from the internal network. Which type of IPv6 address must the engineer assign?
Which QoS traffic handling technique retains excess packets in a queue and reschedules these packets for later transmission when the configured maximum bandwidth has been surpassed?
Refer to the exhibit.
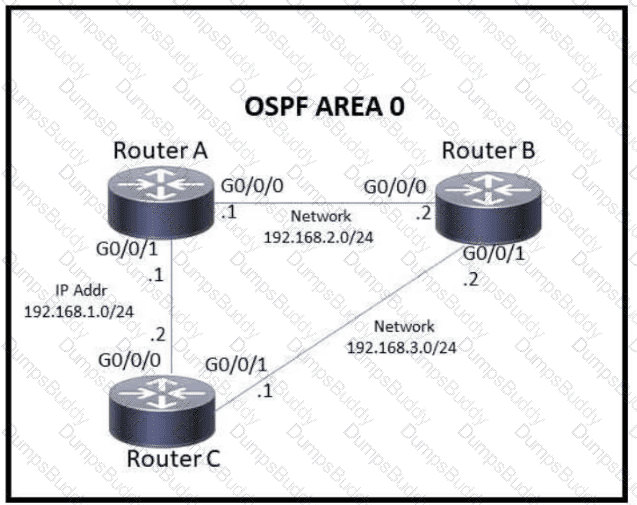
Which action must be taken to ensure that router A is elected as the DR for OSPF area 0?
Refer to the exhibit.
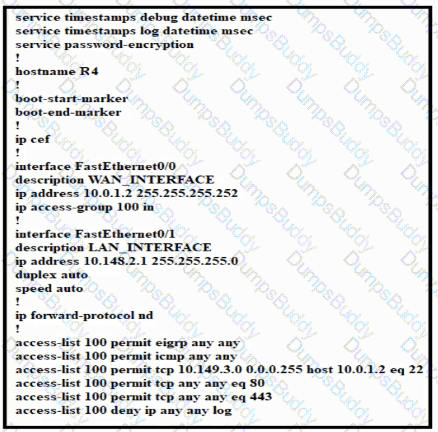
Which configuration enables DHCP addressing for hosts connected to interface FastEthernetO/1 on router R4?
Refer to the exhibit.
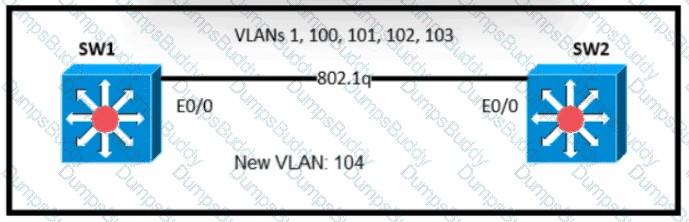
An engineer is asked to insert the new VLAN into the existing trunk without modifying anything previously configured Which command accomplishes this task?
Refer to the exhibit.
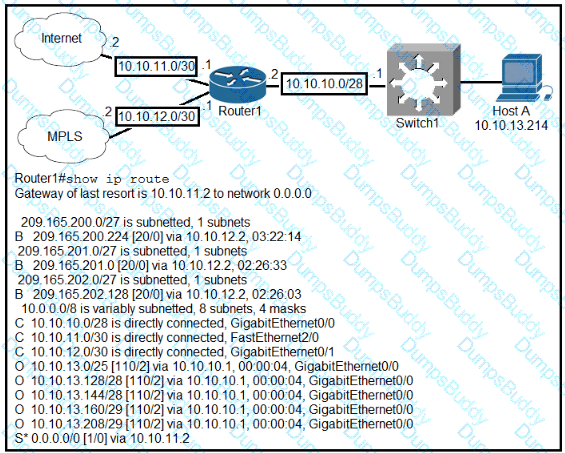
What is the subnet mask of the route to the 10.10.13.160 prefix?
Which feature, when used on a WLC, allows it to bundle its distribution system ports into one 802.3ad group?
When a WPA2-PSK WLAN is configured in the Wireless LAN Controller, what is the minimum number of characters that is required in ASCII format?
Which IPv6 address range is suitable for anycast addresses for distributed services such DHCP or DNS?
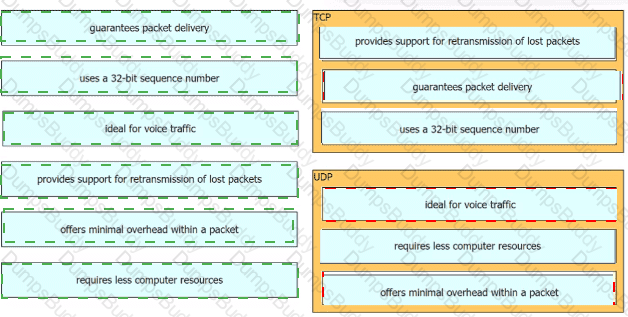
Why is TCP desired over UDP for application that require extensive error checking, such as HTTPS?
Exhibit.

The switches are connected via a Cat5 Ethernet cable that was successfully tested. The Interfaces are configured as access ports and are both in a 'down" status. What is the cause of this issue?
Refer to the exhibit.
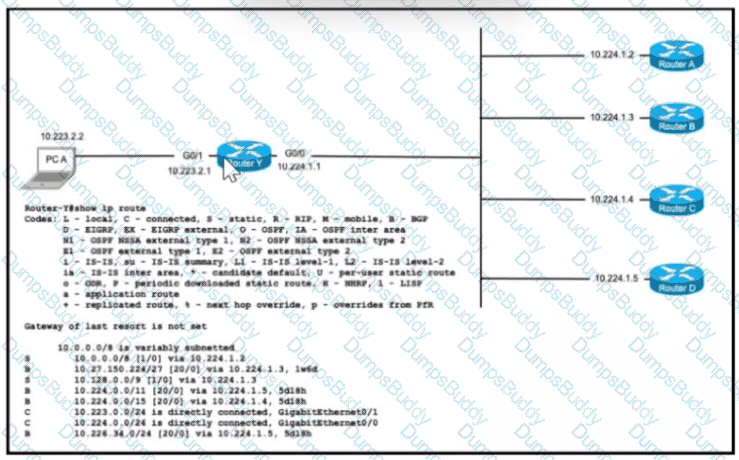
PC A is communicating with another device at IP address 10.227.225.255. Through which router does router Y route the traffic?
Refer to the exhibit.
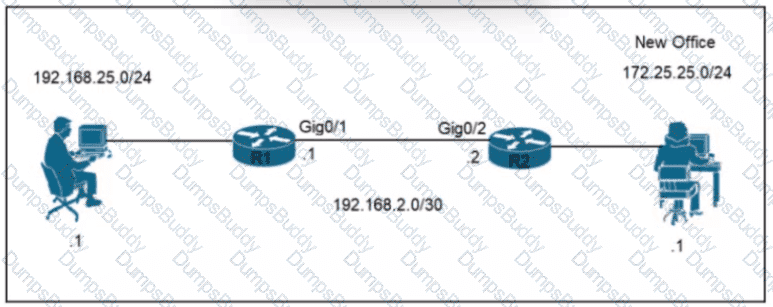
A network engineer is updating the configuration on router R1 to connect a new branch office to the company network R2 has been configured correctly. Which command must the engineer configure so that devices at the new site communicate with the main office?
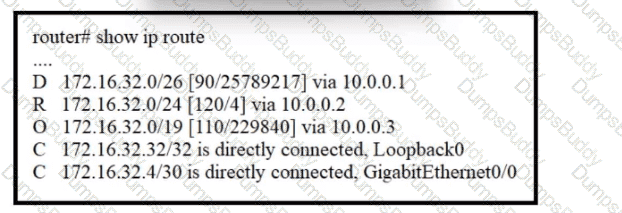
Refer to the exhibit. A packet sourced from 172.16.32.254 is destined for 172.16.32.8. What is the subnet mask of the preferred destination route?
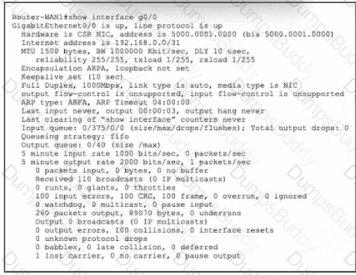
Refer to the exhibit. Router-WAN1 has a new connection via Gi0/0 to the ISP. Users running the web applications indicate that connectivity is unstable to the internet. What is causing the interface issue?
Refer to the exhibit.
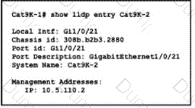
The network administrator must prevent the switch Cat9K-2 IP address from being visible in LLDP without disabling the protocol. Which action must be taken must be taken to complete the task?

Refer to the exhibit. An engineer must translate the PC1 IP address to 10.199.77.100 and permit PC1 to ping the loopback 0 on router R2. What command set must be used?
A)
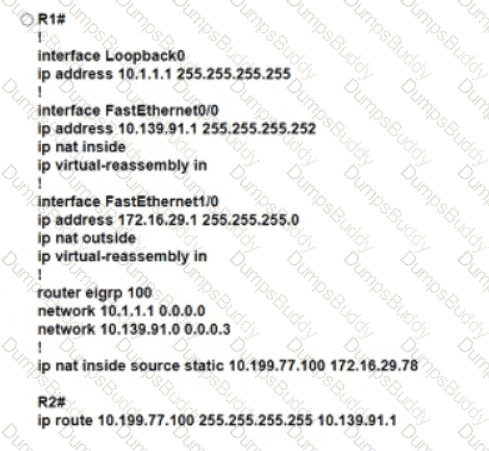
B)
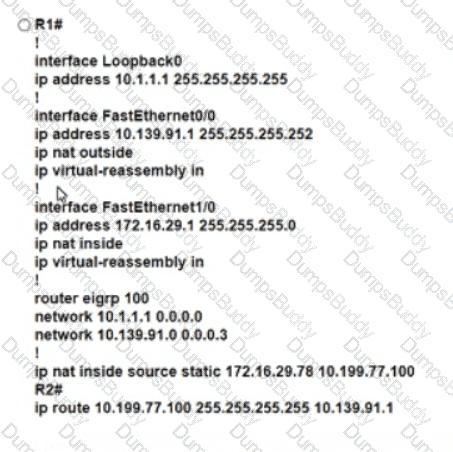
C)
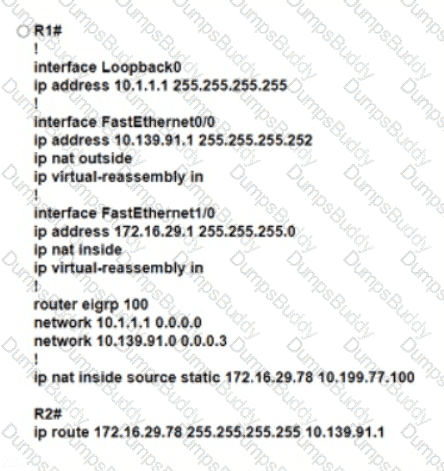
D)
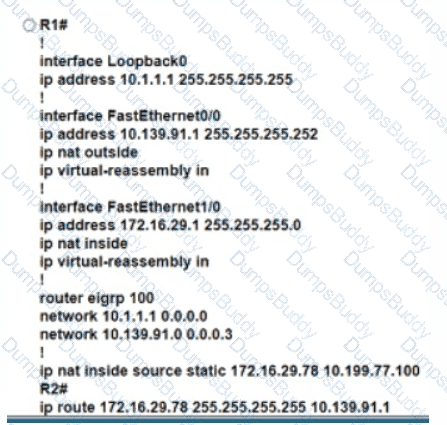
Drag and drop the IPv6 address details from the left onto the corresponding types on the right.
What is the operating mode and role of a backup port on a shared LAN segment in Rapid PVST+?
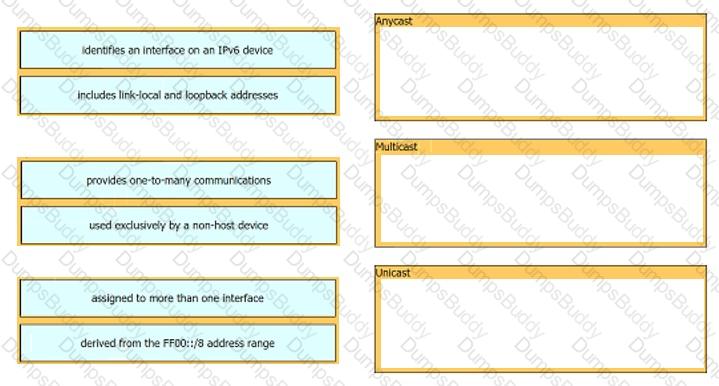
Drag and drop the IPv6 address description from the left onto the IPv6 address types on the right. Not all options are used.
A packet from a company s branch office is destined to host 172.31.0.1 at headquarters. The sending router has three possible matches in its routing table for the packet prefixes: 172. 31.0 .0/16.72.31.0.0724. and 172.31 0 0/25. How does the router handle the packet?
Refer to the exhibit. A network engineer updates the existing configuration on interface fastethernet1/1 switch SW1. It must establish an EtherChannel by using the same group designation with another vendor switch. Which configuration must be performed to complete the process?
Company has decided to require multifactor authentication for all systems. Which set of parameters meets the requirement?
In which circumstance would a network architect decide to implement a global unicast subnet instead of a unique local unicast subnet?
A network engineer must migrate a router loopback interface to the IPv6 address space. If the current IPv4 address of the interface is 10.54.73.1/32, and the engineer configures IPv6 address 0.0.0.0.0:ffff:a36:4901, which prefix length must be used?
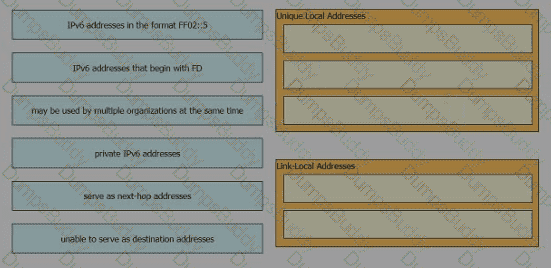
Drag and drop the IPv6 address description from the left onto the IPv6 address types on the right. Not all options are used.

Refer to the exhibit.
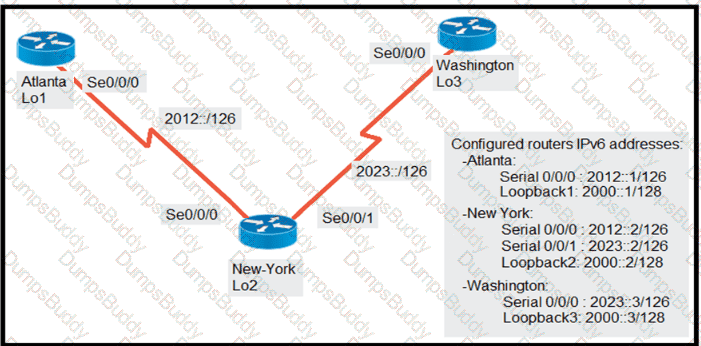
The New York router is configured with static routes pointing to the Atlanta and Washington sites. Which two tasks must be performed so that the Se0/0/0 interfaces on the Atlanta and Washington routers reach one another? (Choose two.)
Refer to the exhibit.

The router has been configured with a subnet to accommodate the requirement for 380 users on a subnet. The requirement already considers 30% future growth. Which configuration verifies the IP subnet on router R4?

SW1 supports connectivity for a lobby conference room and must be secured. The engineer must limit the connectivity from PCI lo ma SW1 and SW2 network. The MAC addresses allowed must be Limited to two. Which configuration secures the conference room connectivity?
A)

B)

C)
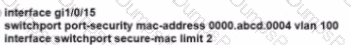
D)

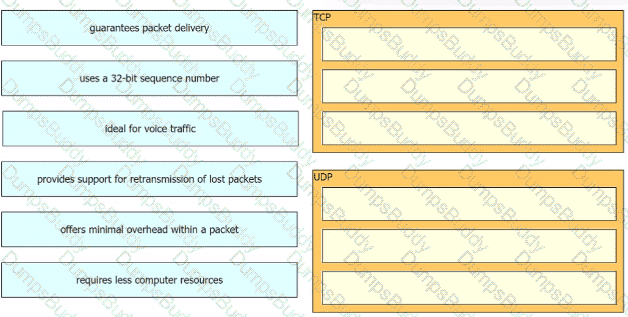
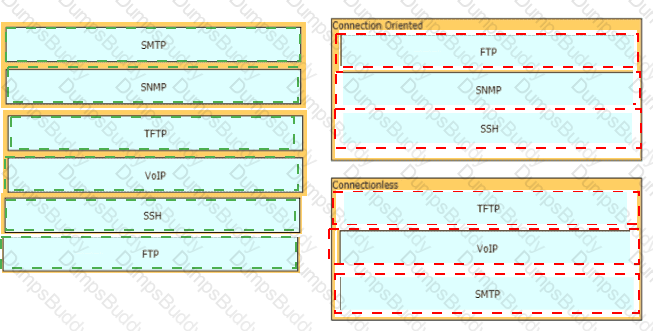
Drag and drop the characteristics of transport layer protocols from the left onto the corresponding protocols on the right.
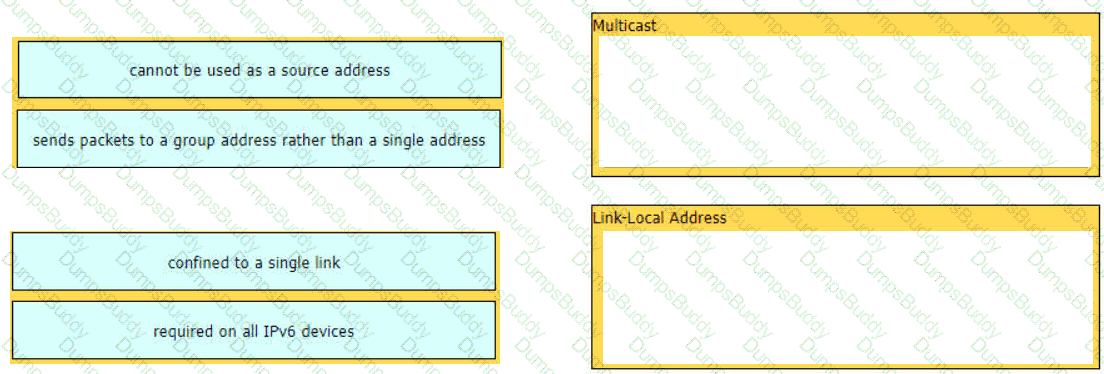
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
A network engineer must migrate a router loopback interface to the IPv6 address space. If the current IPv4 address of the interface is 10.54.73.1/32, and the engineer configures IPv6 address 0.0.0.0.0:ffff:a36:4901, which prefix length must be used?
Which cable type must be used to interconnect one switch using 1000 BASE-SX GBiC modules and another switch using 1000 BASE-SX SFP modules?
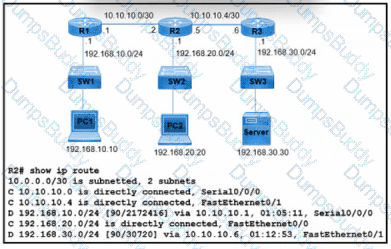
Refer to the exhibit. What is the next-hop IP address for R2 so that PC2 reaches the application server via EIGRP?
Refer to the exhibit. Company A wants to use a RADIUS server to service all user and device authentication attempts with a more secure and granular authentication approach. Not all client devices support dot1x authentication. Which two configuration changes must be made to accomplish the task? (Choose two.)
Drag and drop the statements about networking from me left onto the corresponding networking types on the right
What is the purpose of using First Hop Redundancy Protocol on a specific subnet?
Refer to the exhibit.
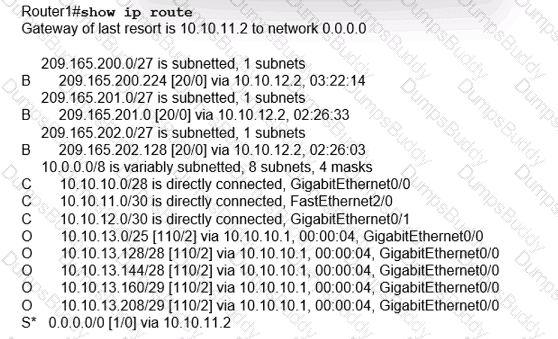
What is the subnet mask of the route to the 10.10.13.160 prefix?

Refer to the exhibit. A network engineer updates the existing configuration on interface fastethernet1/1 switch SW1. It must establish an EtherChannel by using the same group designation with another vendor switch. Which configuration must be performed to complete the process?
Refer to the exhibit.
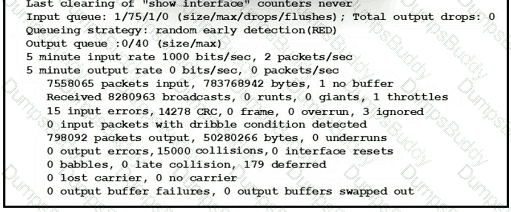
An administrator received a call from a branch office regarding poor application performance hosted at the headquarters. Ethernet 1 is connected between Router1 and the LAN switch. What identifies the issue?

Refer to the exhibit. An engineer must translate the PC1 IP address to 10.199.77.100 and permit PC1 to ping the loopback 0 on router R2. What command set must be used?
A)

B)

C)

D)

Refer to the exhibit.
All interfaces are in the same VLAN. All switches are configured with the default STP priorities. During the STP electronics, which switch becomes the root bridge?
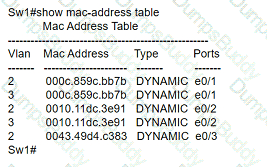
By default, how long will the switch continue to know a workstation MAC address after the workstation stops sending traffic?
When the LAG configuration is updated on a Cisco WLC which additional task must be performed when changes are complete?
Which command do you enter so that a switch configured with Rapid PVST + listens and learns for a specific time period?
Refer to the exhibit An IPv6 address must be obtained automatically on the LAN interface on R1 Which command must be implemented to accomplish the task?
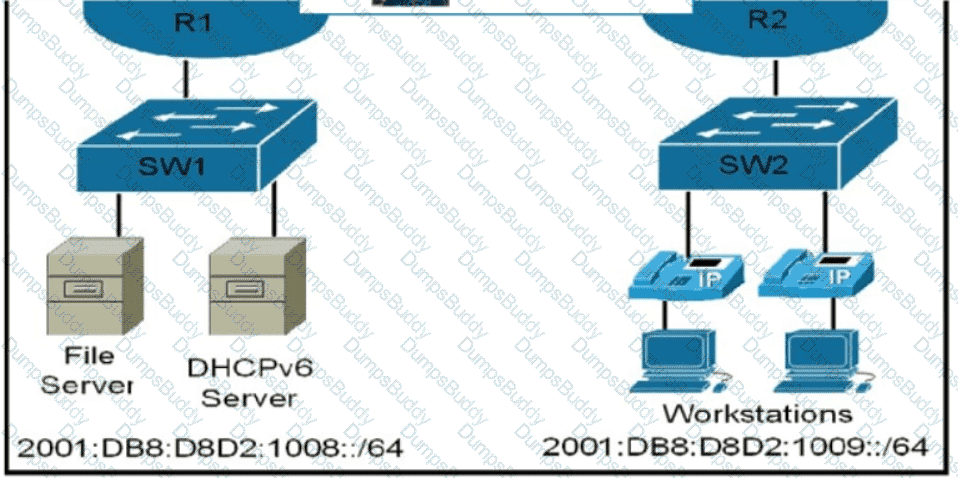
Refer to the exhibit.

Host A switch interface is configured in VLAN 2. Host D sends a unicast packet destined for the IP address of host A.
What does the switch do when it receives the frame from host D?
Which group of channels in the 802.1ib/g/n/ac/ax 2.4 GHz frequency Bands are nonoverlapping channels?
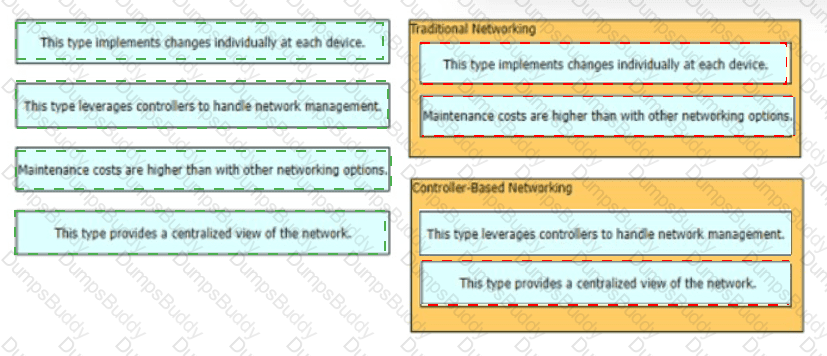
What is the function of "off-the-shell" switches in a controller-based network?
What is the difference between an IPv6 link-local address and a unique local address?
A switch is a forwarding a frame out of an interfaces except the interface that received the frame. What is the technical term for this process?
An engineer is configuring switch SW1 to act an NTP server when all upstream NTP server connectivity fails. Which configuration must be used?
A)
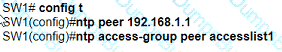
B)
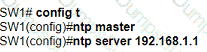
C)
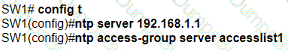
D)
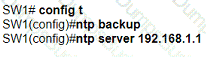
What should a network administrator consider when deciding to implement automation?
Refer to the exhibit An IPv6 address must be obtained automatically on the LAN interface on R1 Which command must be implemented to accomplish the task?

Refer to the exhibit.
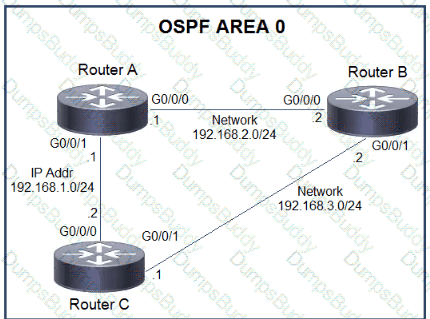
Which action must be taken to ensure that router A is elected as the DR for OSPF area 0?
Refer to the exhibit.
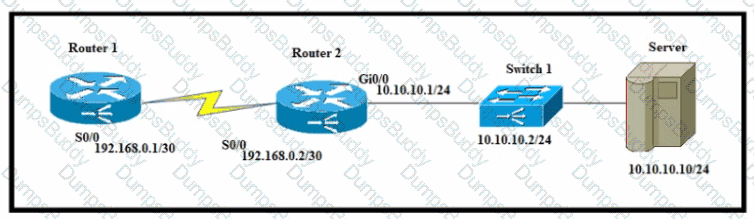
A network engineer must configure router R1 with a host route to the server. Which command must the engineer configure?
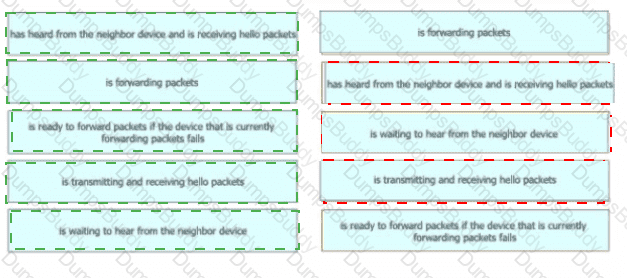
Drag and drop the device behaviors from the left onto the matching HSRP slate on the right.

Which two practices are recommended for an acceptable security posture in a network? (Choose two)
Drag and drop the statements about networking from the left onto the corresponding networking types on the right. Not all statements are used.
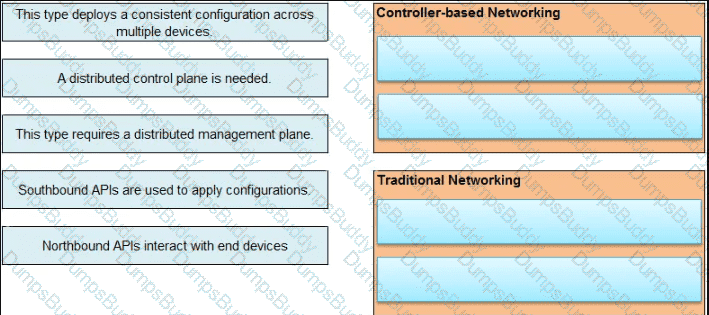
What are two differences between WPA2 and WPA3 wireless security? (Choose two.)
An engineer must configure a WLAN using the strongest encryption type for WPA2- PSK. Which cipher fulfills the configuration requirement?
A user configured OSPF in a single area between two routers A serial interface connecting R1 and R2 is running encapsulation PPP By default which OSPF network type is seen on this interface when the user types show ip ospf interface on R1 or R2?
Refer to Exhibit.
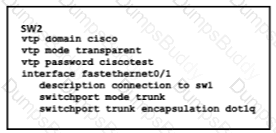
How does SW2 interact with other switches in this VTP domain?
When a client and server are not on the same physical network, which device is used to forward requests and replies between client and server for DHCP?
Refer to the exhibit.
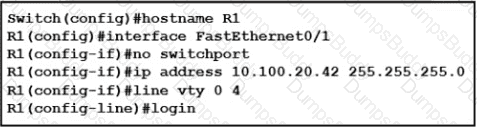
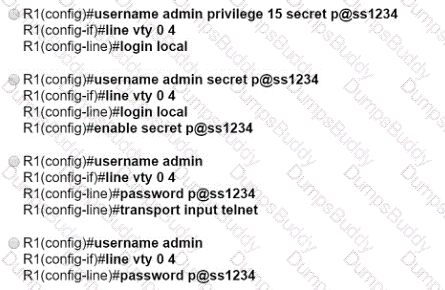
An engineer booted a new switch and applied this configuration via the console port. Which additional configuration must be applied to allow administrators to authenticate directly to enable privilege mode via Telnet using a local username and password?
Which IPv6 address type provides communication between subnets and is unable to route on the Internet?
Refer to the exhibit.
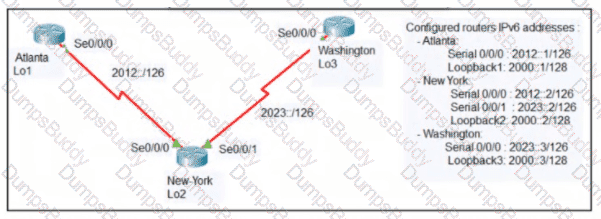
An engineer configured the New York router with state routes that point to the Atlanta and Washington sites. When command must be configured on the Atlanta and Washington routers so that both sites are able to reach the loopback2 interface on the New York router?
A network engineer must configure the router R1 GigabitEthernet1/1 interface to connect to the router R2 GigabitEthernet1/1 interface. For the configuration to be applied the engineer must compress the address 2001:0db8:0000:0000:0500:000a:400F:583B. Which command must be issued on the interface?
An organization secures its network with multi-factor authentication using an authenticator app on employee smartphone. How is the application secured in the case of a user’s smartphone being lost or stolen?
An administrator must secure the WLC from receiving spoofed association requests. Which steps must be taken to configure the WLC to restrict the requests and force the user to wait 10 ms to retry an association request?
Refer to the exhibit.
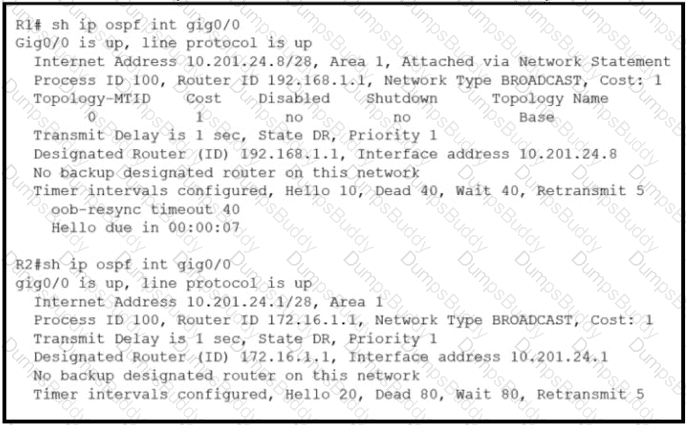
What action establishes the OSPF neighbor relationship without forming an adjacency?
When the active router in an HSRP group fails, what router assumes the role and forwards packets?
Which header must be included in a REST request from an application that requires JSON-formatted content?
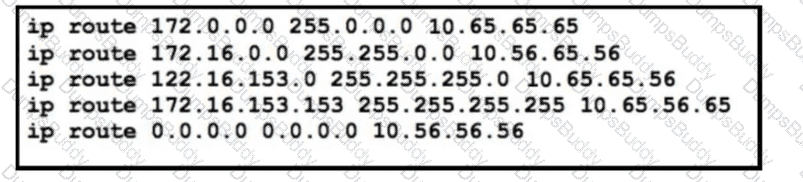
Refer to the exhibit. The static routes were implemented on the border router. What is the next hop IP address for a ping sent to 172.16.153.154 from the border router?
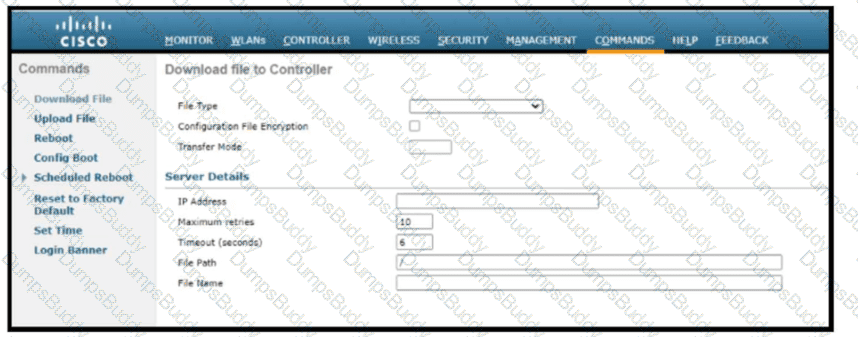
Refer to the exhibit. Which tasks must be performed on the Download File tab to install new software using TCP port 22?)
The SW1 interface g0/1 is in the down/down state. Which two configurations are valid reasons for the interface conditions?(choose two)
Which unified access point mode continues to serve wireless clients after losing connectivity to the Cisco Wireless LAN Controller?
If a switch port receives a new frame while it is actively transmitting a previous frame, how does it process the frames?
Drag and drop to the characteristics of networking from the left onto the correct networking types on the right.
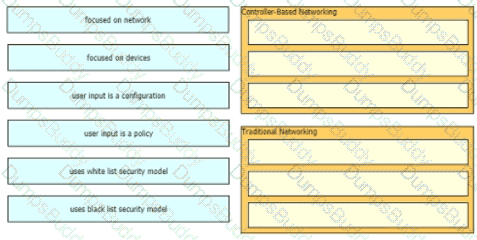
How do traditional campus device management and Cisco DNA Center device management differ in regards to deployment?
Which two tasks must be performed to configure NTP to a trusted server in client mode on a single network device? (Choose two)
Which type of API allows SDN controllers to dynamically make changes to the network?
When a site-to-site VPN is used, which protocol is responsible for the transport of user data?
Which statement correctly compares traditional networks and controller-based networks?
Refer to the exhibit.
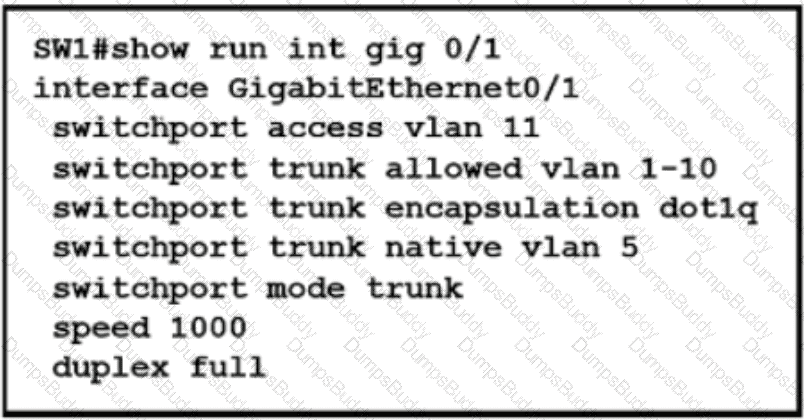
Which action is expected from SW1 when the untagged frame is received on the GigabitEthernet0/1 interface?
A user configured OSPF and advertised the Gigabit Ethernet interface in OSPF By default, which type of OSPF network does this interface belong to?
Refer to the exhibit.
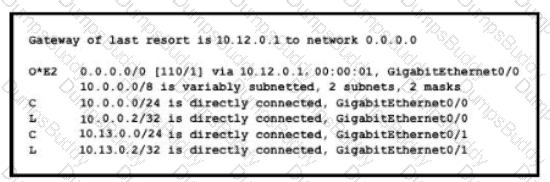
If configuring a static default route on the router with the ip route 0.0.0.0 0.0.0.0 10.13.0.1 120 command how does the router respond?
Which statement about Link Aggregation when implemented on a Cisco Wireless LAN Controller is true?
Which two must be met before SSH can operate normally on a Cisco IOS switch? (Choose two)
Using direct sequence spread spectrum, which three 2.4-GHz channels are used to limit collisions?
What are two reasons for an engineer to configure a floating state route? (Choose two)
Refer to Exhibit.
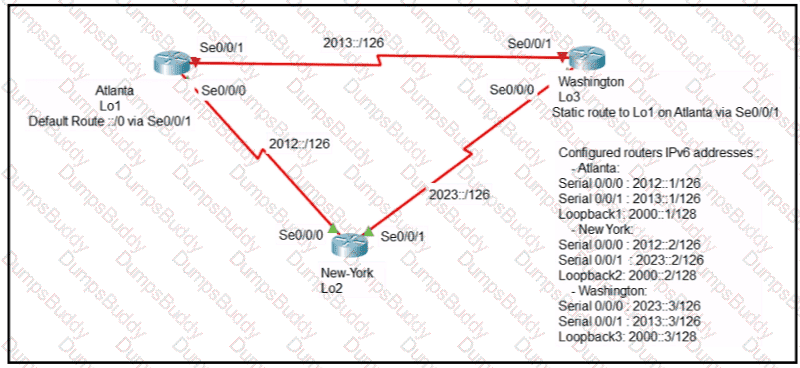
An engineer is configuring the NEW York router to reach the Lo1 interface of the Atlanta router using interface Se0/0/0 as the primary path. Which two commands must be configured on the New York router so that it can reach the Lo1 interface of the Atlanta router via Washington when the link between New York and Atlanta goes down? (Choose two)
Refer to the exhibit.
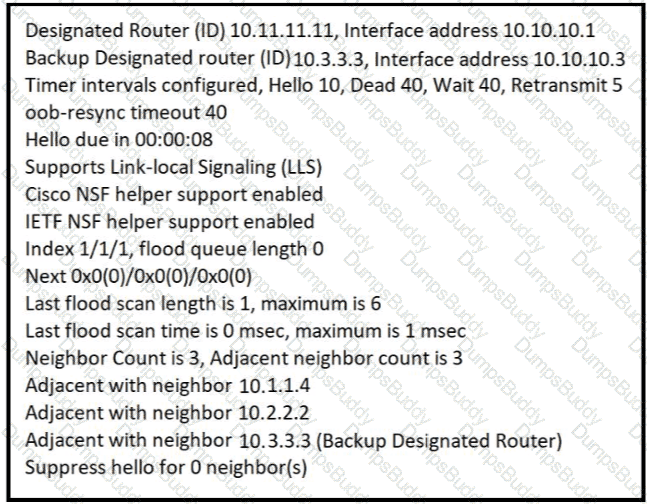
The show ip ospf interface command has been executed on R1 How is OSPF configured?
Refer to the exhibit.
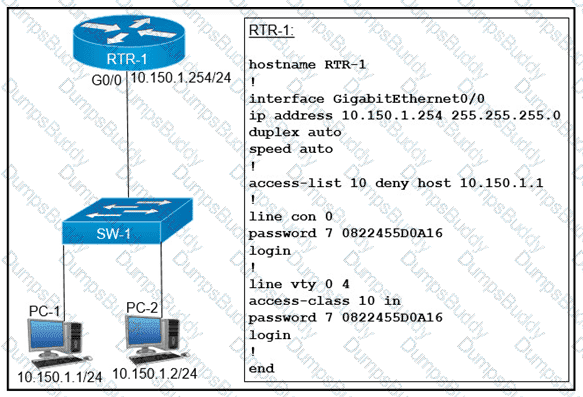
An access list is created to deny Telnet access from host PC-1 to RTR-1 and allow access from all other hosts A Telnet attempt from PC-2 gives this message:"% Connection refused by remote host" Without allowing Telnet access from PC-1, which action must be taken to permit the traffic?
A network administrator enabled port security on a switch interface connected to a printer. What is the next configuration action in order to allow the port to learn the MAC address of the printer and insert it into the table automatically?
Which configuration management mechanism uses TCP port 22 by default when communicating with managed nodes?
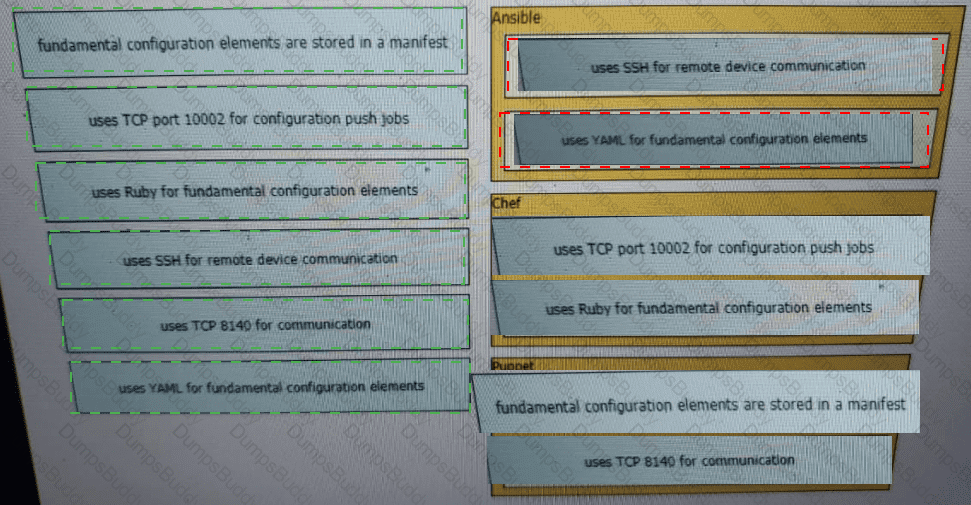
Drag and drop the descriptions from the left onto the configuration-management technologies on the right.

A network administrator must to configure SSH for remote access to router R1 The requirement is to use a public and private key pair to encrypt management traffic to and from the connecting client.
Which configuration, when applied, meets the requirements?

Refer to the exhibit.
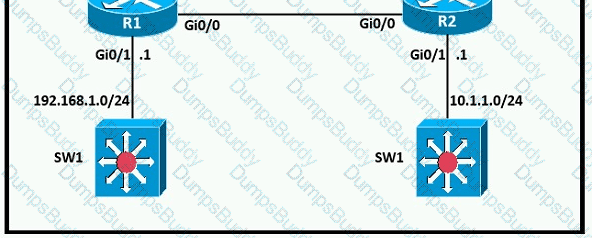
A network engineer is in the process of establishing IP connectivity between two sites. Routers R1 and R2 are partially configured with IP addressing. Both routers have the ability to access devices on their respective LANs. Which command set configures the IP connectivity between devices located on both LANs in each site?
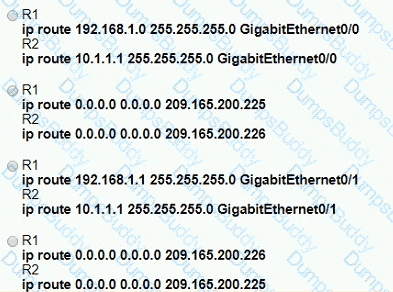
A Cisco IP phone receive untagged data traffic from an attached PC. Which action is taken by the phone?
Refer to the exhibit.
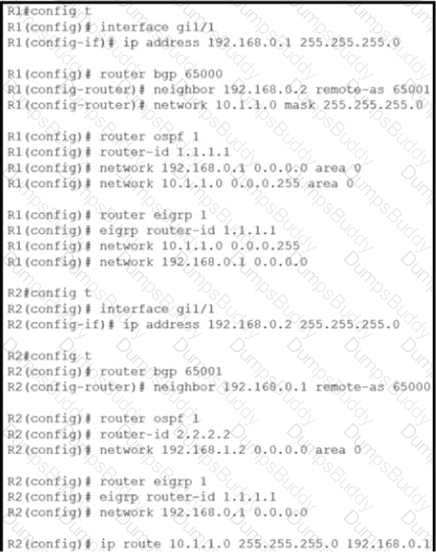
Router R2 is configured with multiple routes to reach network 10 1.1 0/24 from router R1. What protocol is chosen by router R2 to reach the destination network 10.1 1 0/24?
An engineer must configure an OSPF neighbor relationship between router R1 and R3 The authentication configuration has been configured and the connecting interfaces are in the same 192.168 1.0/30 sublet. What are the next two steps to complete the configuration? (Choose two.)
Refer to the exhibit.
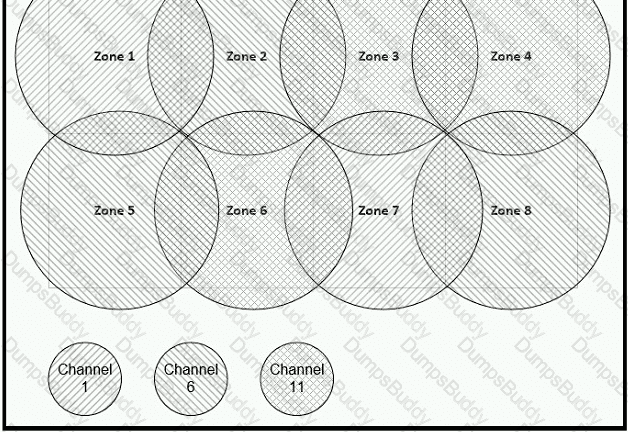
Between which zones do wireless users expect to experience intermittent connectivity?
Refer to the exhibit.
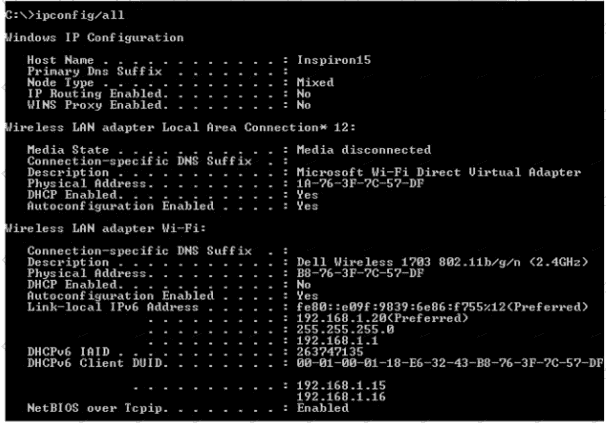
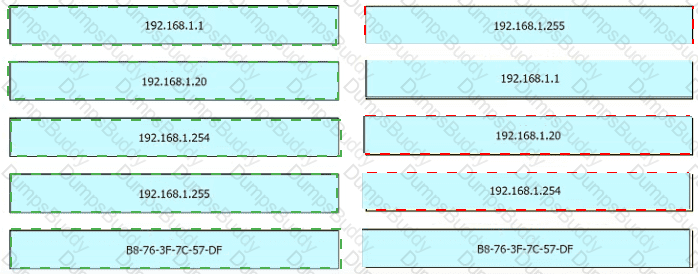
An engineer is tasked with verifying network configuration parameters on a client workstation to report back to the team lead. Drag and drop the node identifiers from the left onto the network parameters on the right.
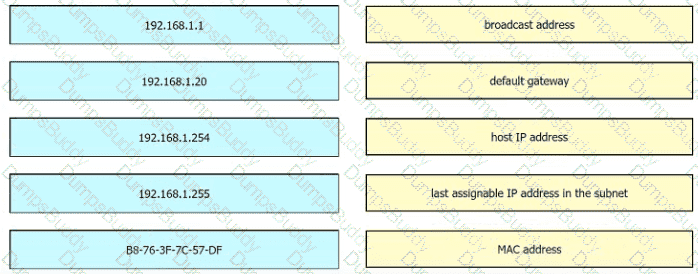
What benefit does controller-based networking provide versus traditional networking?
With REST API, which standard HTTP header tells a server which media type is expected by the client?
A corporate office uses four floors in a building
• Floor 1 has 24 users
• Floor 2 has 29 users
• Floor 3 has 28 users
•Floor 4 has 22 users
Which subnet summarizes and gives the most efficient distribution of IP addresses for the router configuration?
Refer to the exhibit.
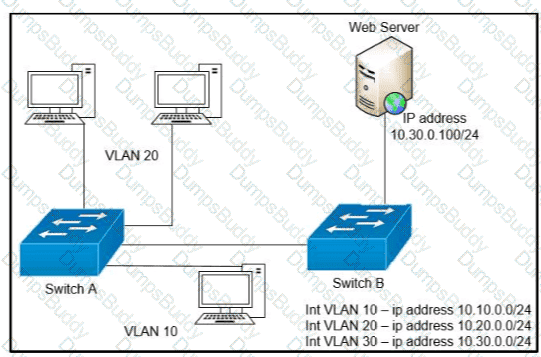
A network engineer must block access for all computers on VLAN 20 to the web server via HTTP All other computers must be able to access the web server Which configuration when applied to switch A accomplishes this task?

Refer to the exhibit.
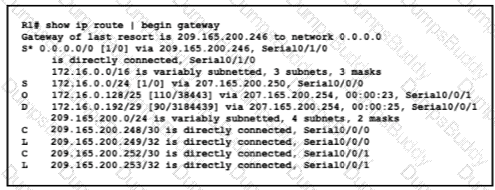
With which metric was the route to host 172.16.0.202 learned?
Which type of IPv6 address is publicly routable in the same way as IPv4 public address?
R1 has learned route 10.10.10.0/24 via numerous routing protocols. Which route is installed?
Router R1 must send all traffic without a matching routing-table entry to 192.168.1.1. Which configuration accomplishes this task?
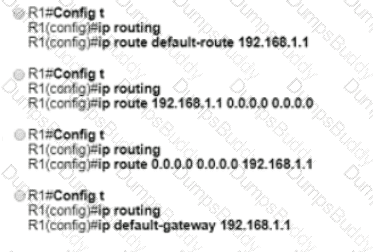
Refer to the exhibit.

Which two prefixes are included in this routing table entry? (Choose two.)
Refer to the exhibit.
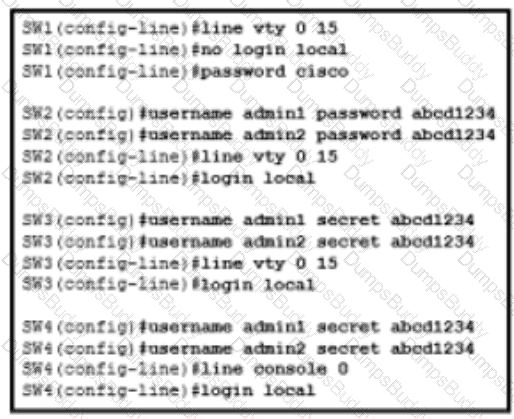
An administrator configures four switches for local authentication using passwords that are stored in a cryptographic hash. The four switches must also support SSH access for administrators to manage the network infrastructure. Which switch is configured correctly to meet these requirements?

Refer to the exhibit. After the configuration is applied, the two routers fail to establish an OSPF neighbor relationship. what is the reason for the problem?
A network engineer must back up 20 network router configurations globally within a customer environment. Which protocol allows the engineer to perform this function using the Cisco IOS MIB?
When using Rapid PVST+, which command guarantees the switch is always the root bridge for VLAN 200?
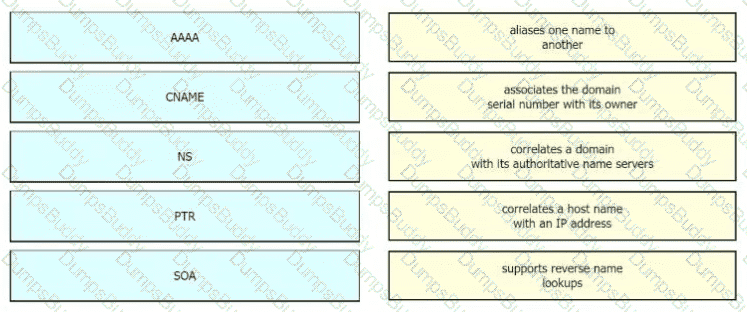
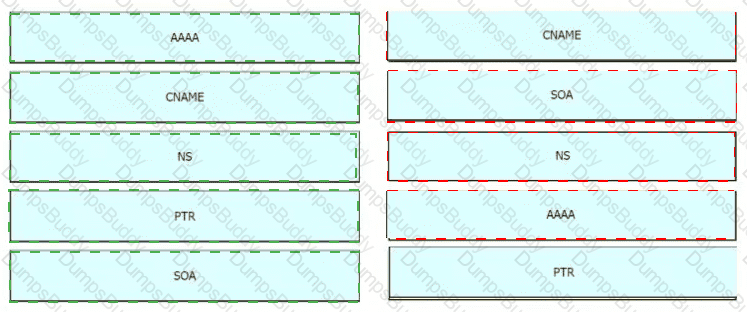
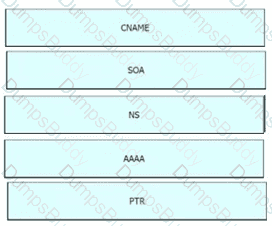
Drag the IPv6 DNS record types from the left onto the description on the right.
Refer to the exhibit.
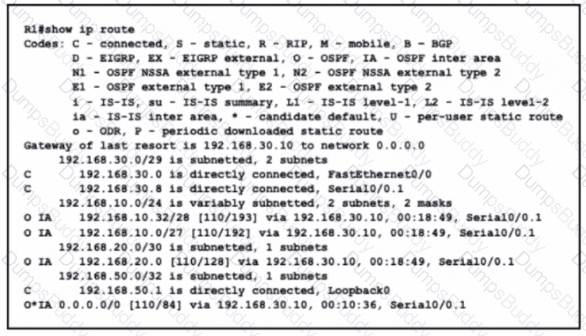
What is the metric of the route to the 192.168.10.33/28 subnet?
in Which way does a spine and-leaf architecture allow for scalability in a network when additional access ports are required?
Which attribute does a router use to select the best path when two or more different routes to the same destination exist from two different routing protocols.
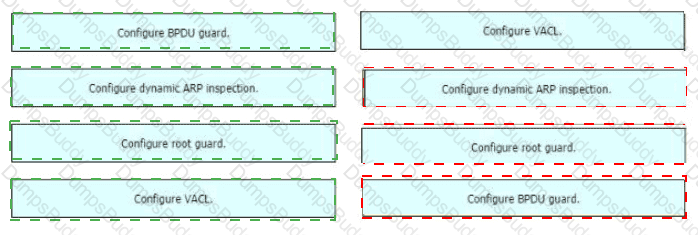
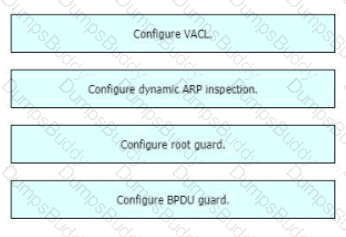
Drag and drop the attack-mitigation techniques from the left onto the Types of attack that they mitigate on the right.
Which resource is able to be shared among virtual machines deployed on the same physical server?
Which mode must be used to configure EtherChannel between two switches without using a negotiation protocol?
Which command prevents passwords from being stored in the configuration as plain text on a router or switch?
Drag and drop the network protocols from the left onto the correct transport services on the right.
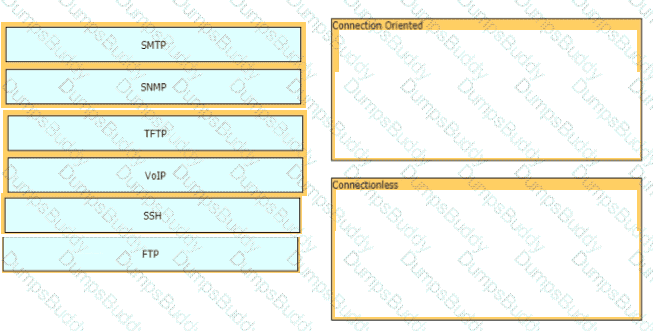
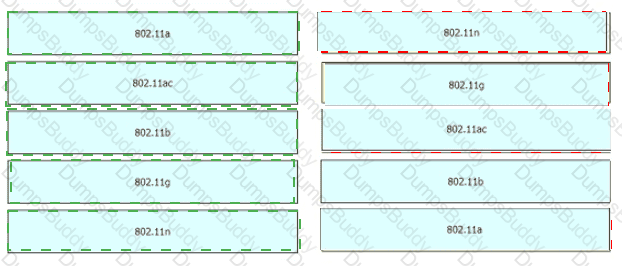
Drag and drop the 802.11 wireless standards from the left onto the matching statements on the right
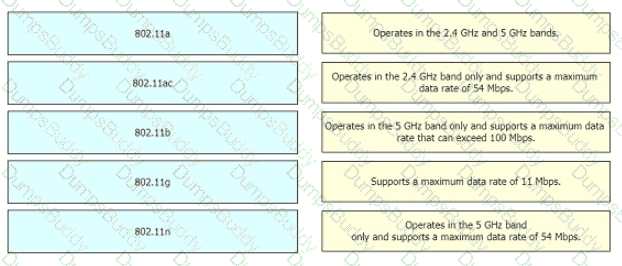
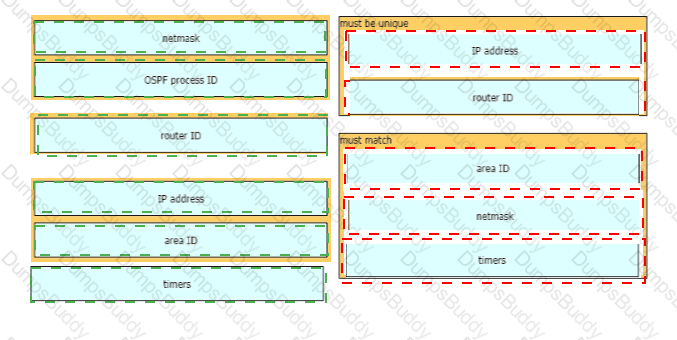
A network engineer is configuring an OSPFv2 neighbor adjacency Drag and drop the parameters from the left onto their required categories on the right. Not all parameters are used
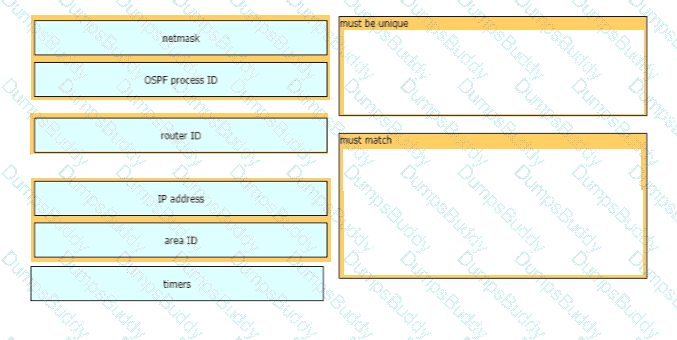
What is the purpose of using First Hop Redundancy Protocol in a specific subnet?
Which security program element involves installing badge readers on data-center doors to allow workers to enter and exit based on their job roles?
An email user has been lured into clicking a link in an email sent by their company's security organization. The webpage that opens reports that it was safe but the link could have contained malicious code. Which type of security program is in place?
Refer to the exhibit.
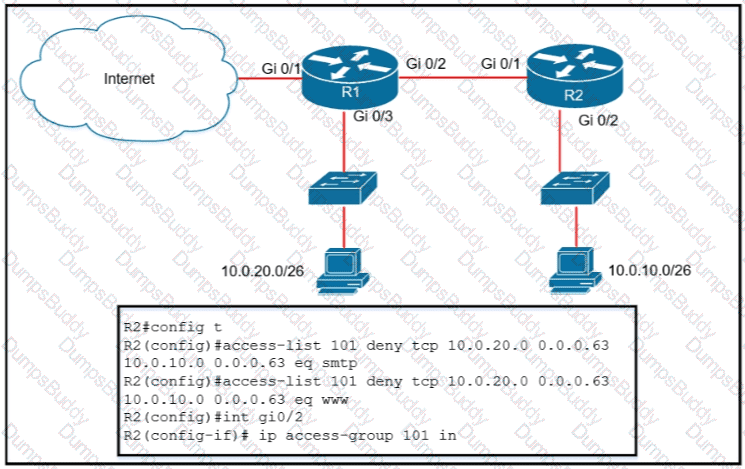
An extended ACL has been configured and applied to router R2 The configuration failed to work as intended Which two
changes stop outbound traffic on TCP ports 25 and 80 to 10.0.20 0 26 from the 10.0.10 0/26 subnet while still allowing all other traffic? (Choose
two )
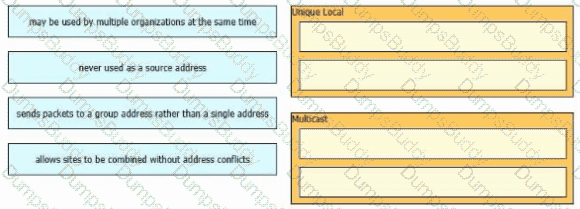
Which IPv6 address block sends packets to a group address rather than a single address?
Which API is used in controller-based architectures to interact with edge devices?
Which switch technology establishes a network connection immediately when it is plugged in?
Refer to exhibit.
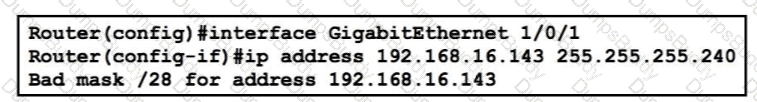
Which statement explains the configuration error message that is received?
Refer to the exhibit.
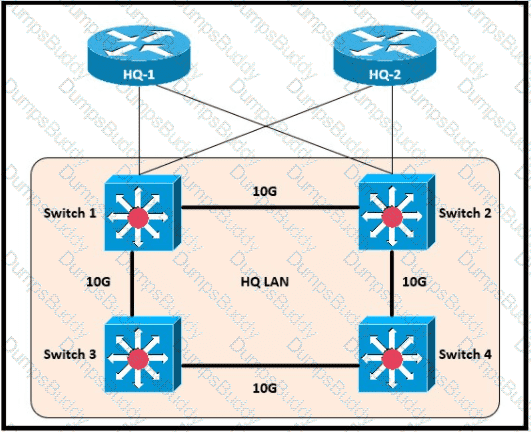
Which switch becomes the root of the spanning tree for VLAN 110?

Which QoS Profile is selected in the GUI when configuring a voice over WLAN deployment?
Which two capacities of Cisco DNA Center make it more extensible as compared to traditional campus device management? (Choose two)
Drag and drop the descriptions of file-transfer protocols from the left onto the correct protocols on the right.
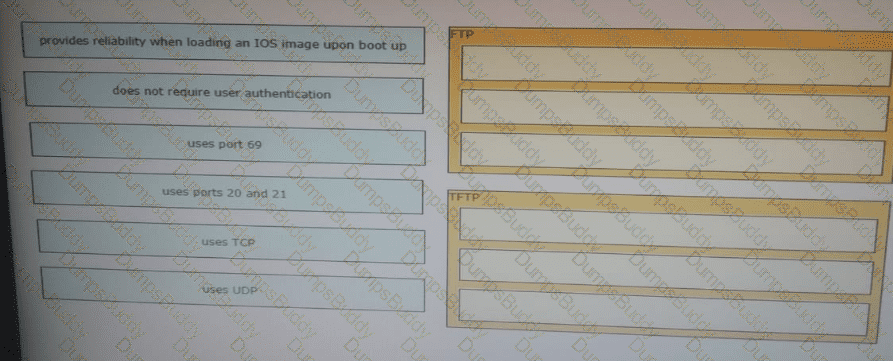
What are two roles of the Dynamic Host Configuration Protocol (DHCP)? (Choose two)
An organization has decided to start using cloud-provided services. Which cloud service allows the organization to install its own operating system on a virtual machine?
What is the difference regarding reliability and communication type between TCP and UDP?
Refer to the exhibit.
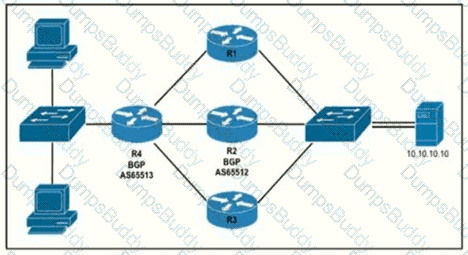
Router R4 is dynamically learning the path to the server. If R4 is connected to R1 via OSPF Area 20, to R2 v2ia R2 BGP, and to R3 via EIGRP 777, which path is installed in the routing table of R4?
Refer to the exhibit.

How must router A be configured so that it only sends Cisco Discovery Protocol Information to router C?
A network analyst is tasked with configured the date and time on a router using EXEC mode. The date must be set to 12:00am. Which command should be used?
Which two WAN architecture options help a business scalability and reliability for the network? (Choose two)
Drag and drop the IPv6 address type characteristics from the left to the right.
Which 802.11 management frame type is sent when a client roams between access points on the same SSID?
Two switches are connected and using Cisco Dynamic Trunking Protocol SW1 is set to Dynamic Desirable
What is the result of this configuration?
What is an advantage of Cisco DNA Center versus traditional campus device management?
Which technology allows for multiple operating systems to be run on a single host computer?
Which command automatically generates an IPv6 address from a specified IPv6 prefix and MAC address of an interface?
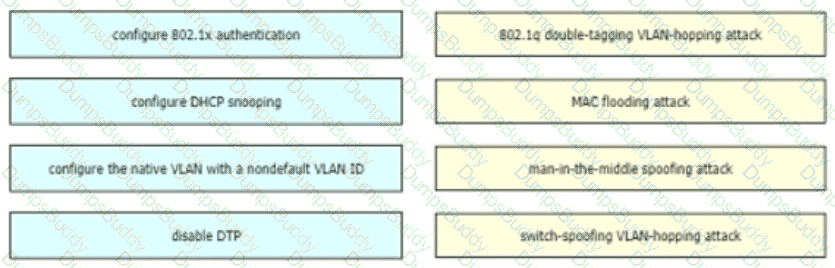
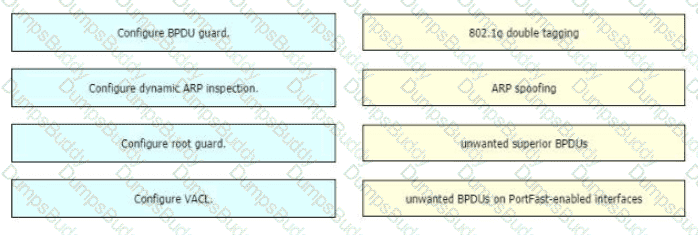
Drag and drop the threat-mitigation techniques from the left onto the types of threat or attack they mitigate on the right.
Aside from discarding, which two states does the switch port transition through while using RSTP (802.1w)? (Choose two)
Drag and drop the functions from the left onto the correct network components on the right

In which two ways does a password manager reduce the chance of a hacker stealing a users password? (Choose two.)
Refer to the exhibit.
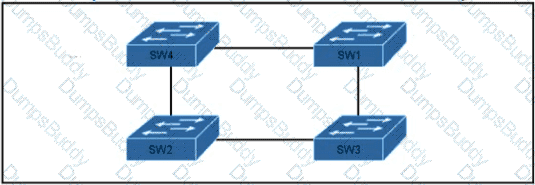
Which switch in this configuration will be elected as the root bridge?
What is a network appliance that checks the state of a packet to determine whether the packet is legitimate?
What mechanism carries multicast traffic between remote sites and supports encryption?
Which implementation provides the strongest encryption combination for the wireless environment?
Refer to the exhibit.
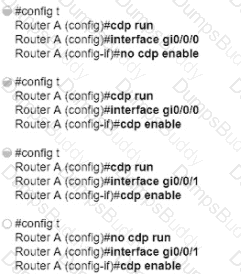
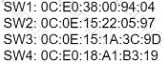
An administrator must turn off the Cisco Discovery Protocol on the port configured with address last usable address in the 10.0.0.0/30 subnet. Which command set meets the requirement?
Refer to the exhibit.
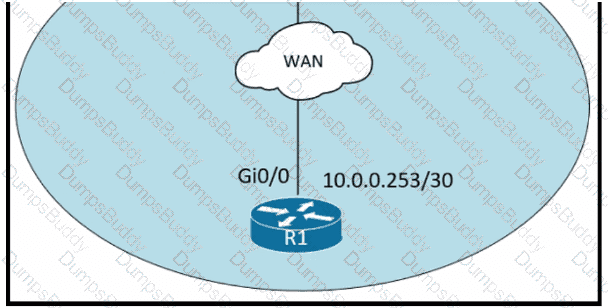
Which configuration on RTR-1 denies SSH access from PC-1 to any RTR-1 interface and allows all other traffic?
Which WAN access technology is preferred for a small office / home office architecture?
Refer to the exhibit.
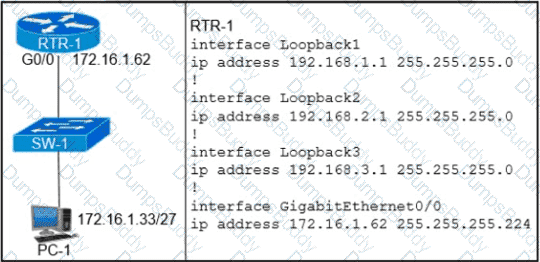
An engineer configured NAT translations and has verified that the configuration is correct.
Which IP address is the source IP?
An engineer needs to add an old switch back into a network. To prevent the switch from corrupting the VLAN database which action must be taken?
Which two actions are performed by the Weighted Random Early Detection mechanism? (Choose two)
Which feature of Digest Authentication prevents credentials from being sent in plaintext?
An organization developed new security policies and decided to print the policies and distribute them to all personnel so that employees review and apply the policies. Which element of a security program is the organization implementing?
Refer to the exhibit.
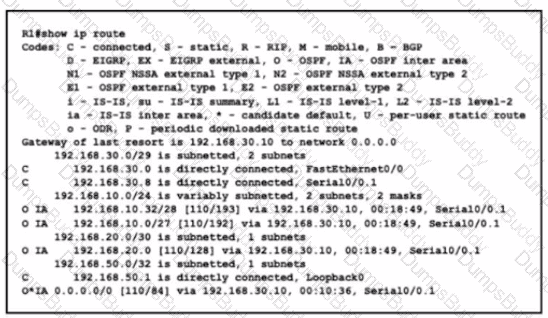
What is the metric for the route to the 192.168.10.33 host?

Refer to the exhibit. An administrator must connect SW_1 and the printer to the network. SW_2 requires DTP to be used for the connection to SW_1. The printer is configured as an access port with VLAN 5. Which set of commands completes the connectivity?

Refer to the exhibit. Which configuration enables SW2 to establish an LACP EtherChannel?
Drag and drop the characteristic from the left onto the IPv6 address type on the right.


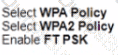
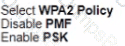


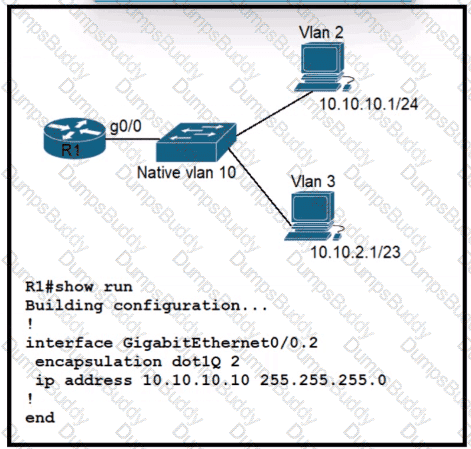






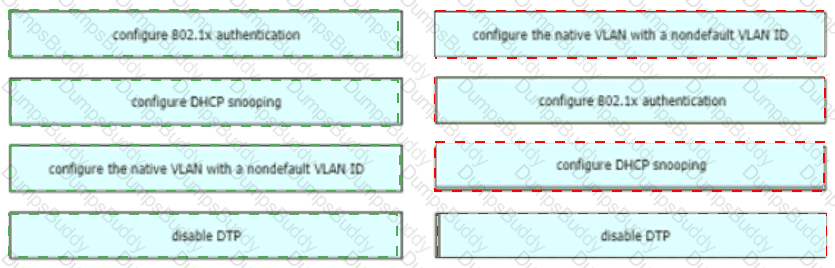

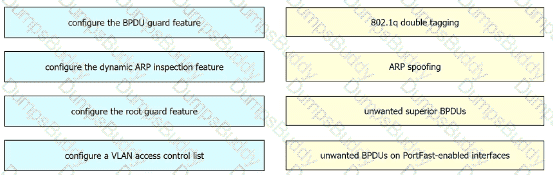
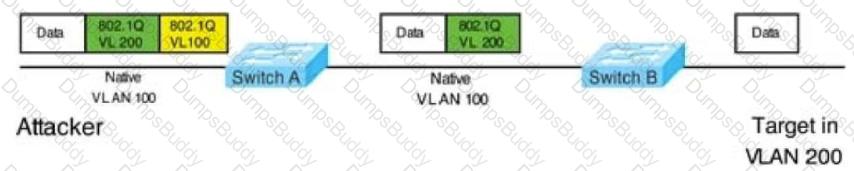 In this attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).
In this attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).