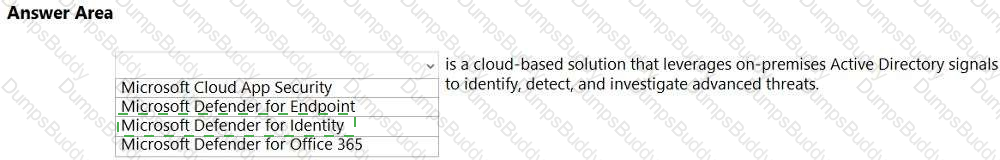
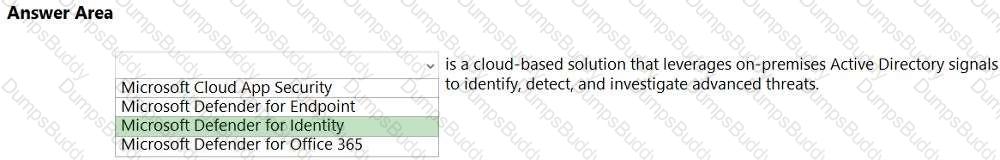
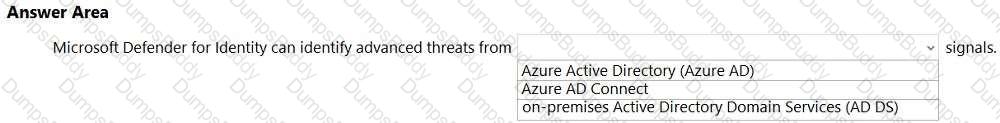
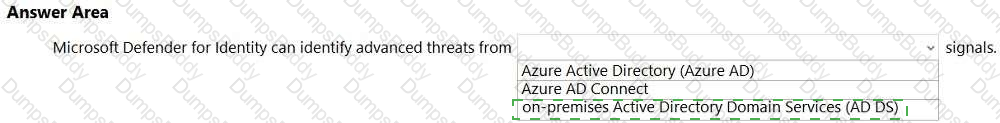
SC-900 Microsoft Security Compliance and Identity Fundamentals Questions and Answers
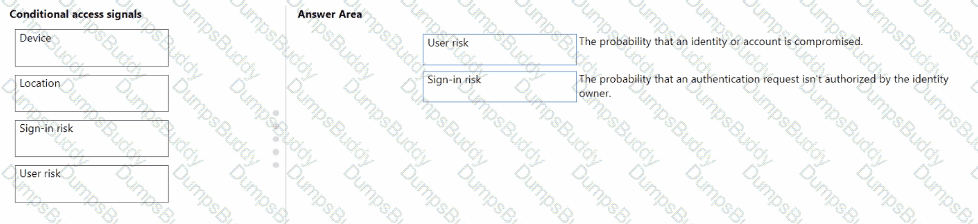
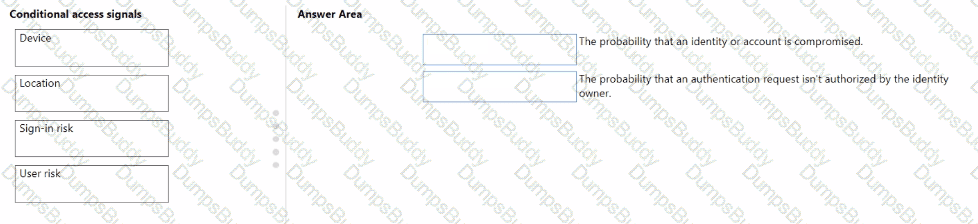
Match the types of Conditional Access signals to the appropriate definitions.
To answer, drag the appropriate Conditional Access signal type from the column on the left to its definition on the right. Each signal type may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
Which Microsoft Defender for Cloud metric displays the overall security health of an Azure subscription?
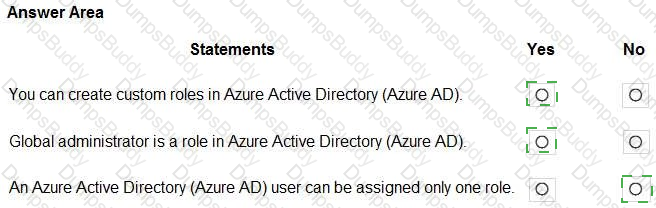
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

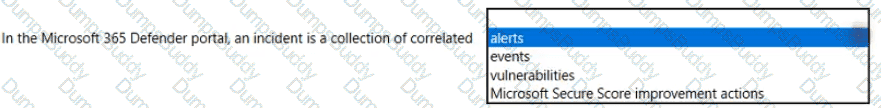
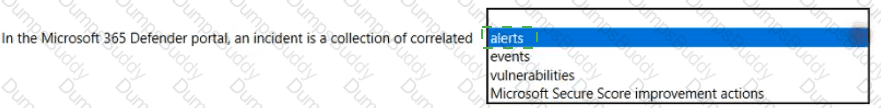
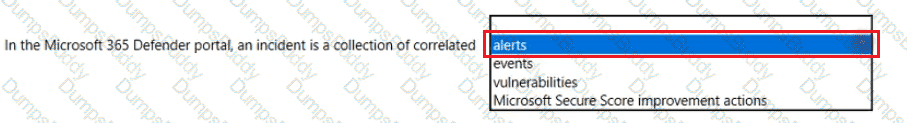
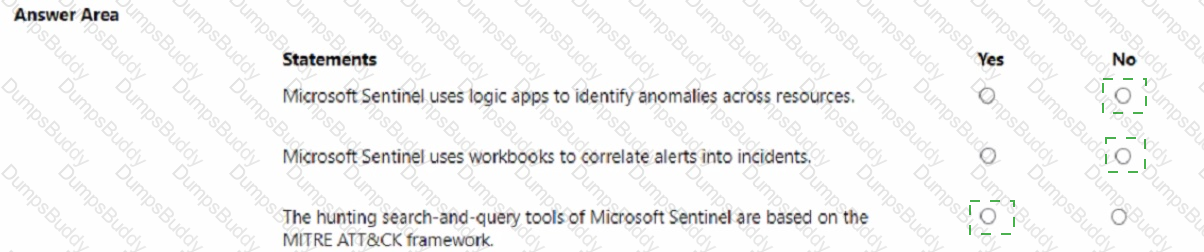
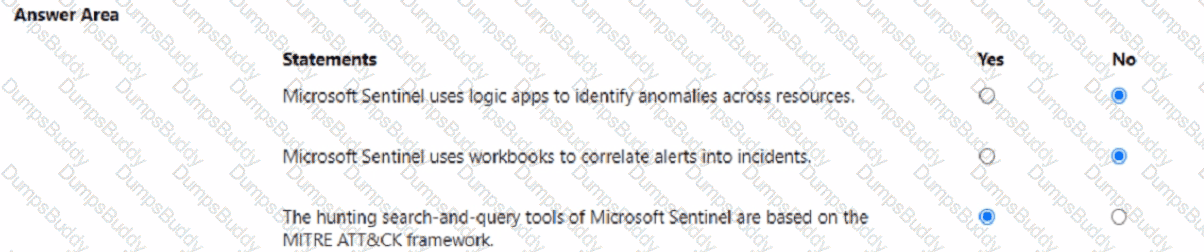
Which feature provides the extended detection and response (XDR) capability of Azure Sentinel?
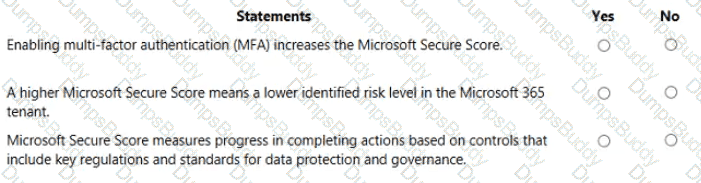
Which score measures an organization's progress in completing actions that help reduce risks associated to data protection and regulatory standards?
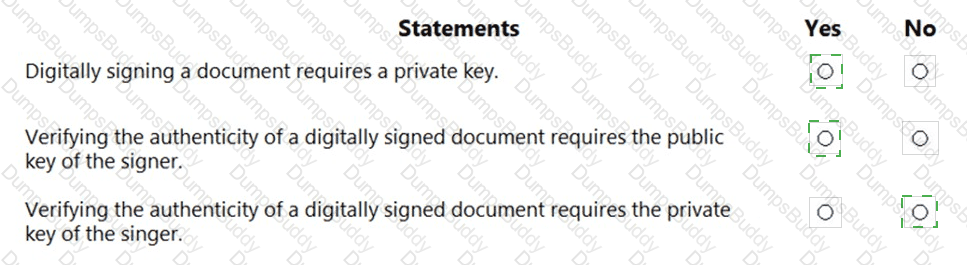
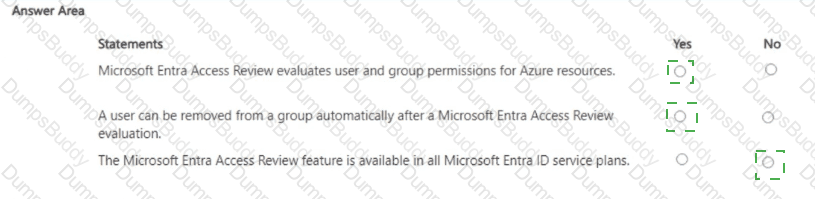
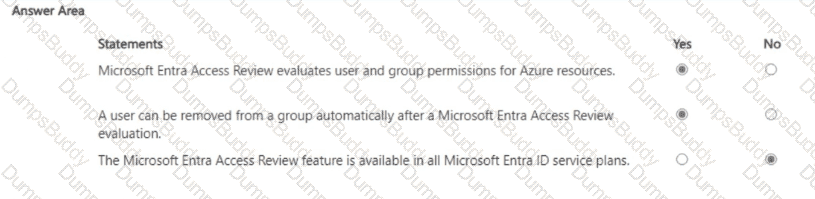
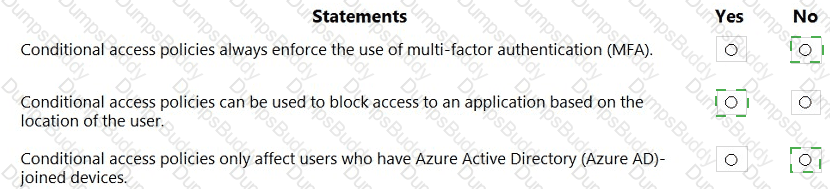
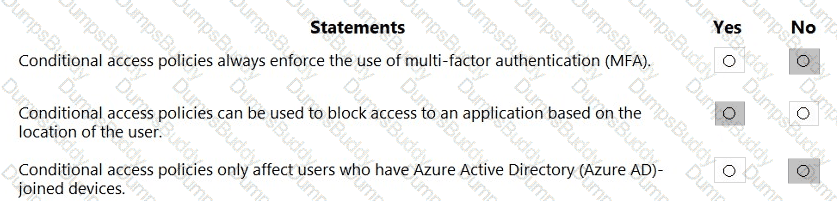
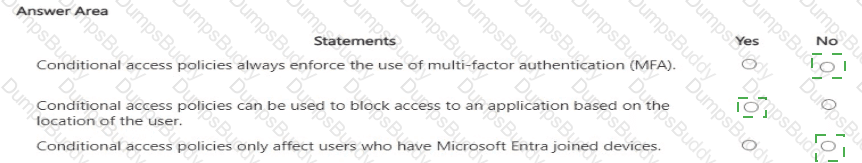
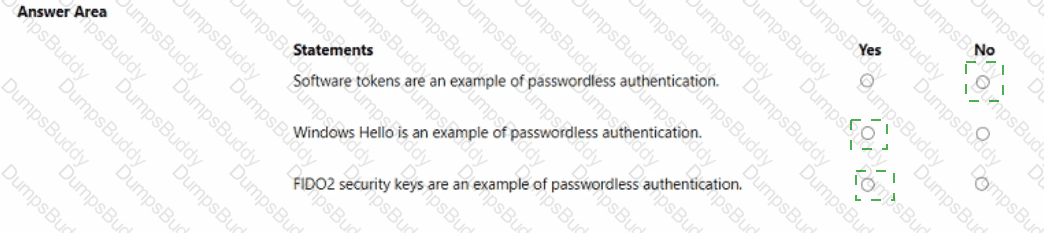
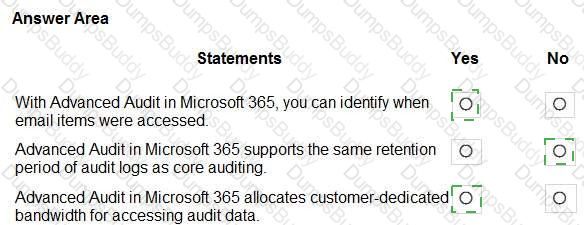
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
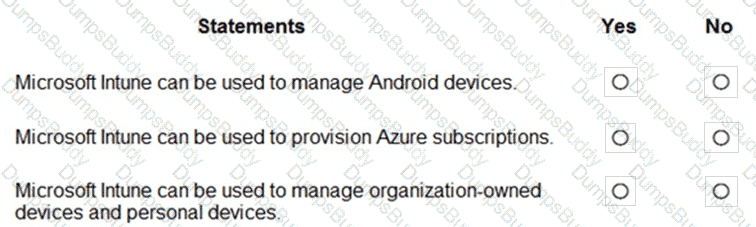
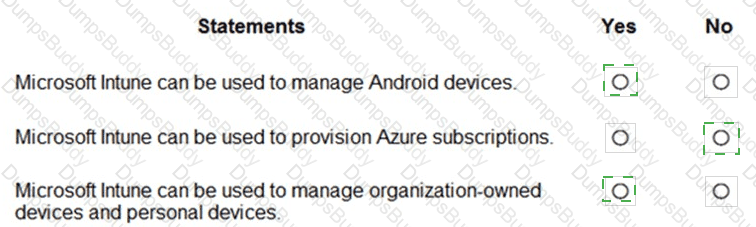
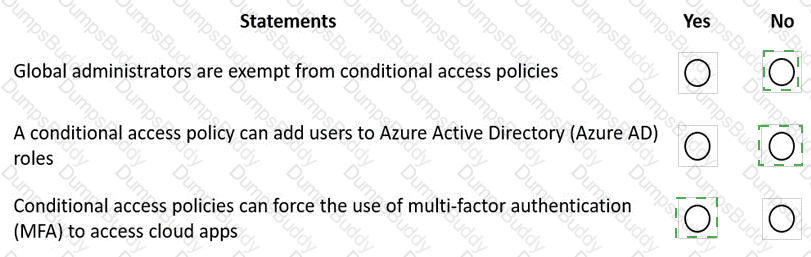
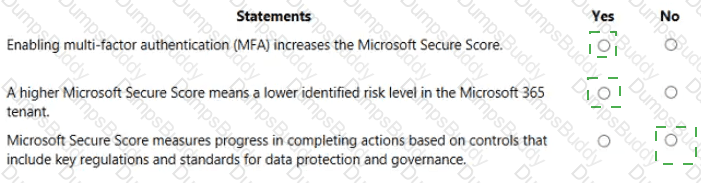
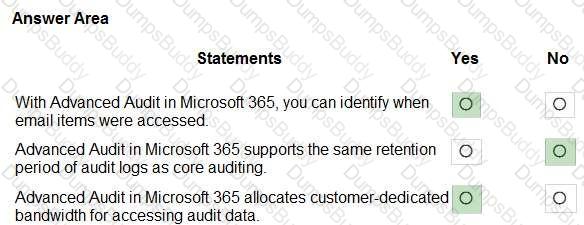
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

What are two reasons to deploy multiple virtual networks instead of using just one virtual network? Each correct answer presents a complete solution.
NOTE; Each correct selection is worth one point.
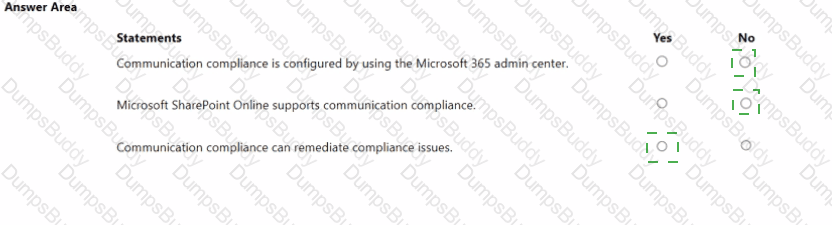
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
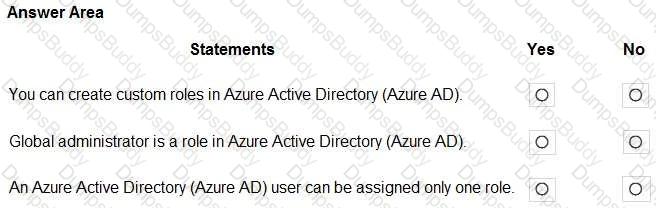
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point
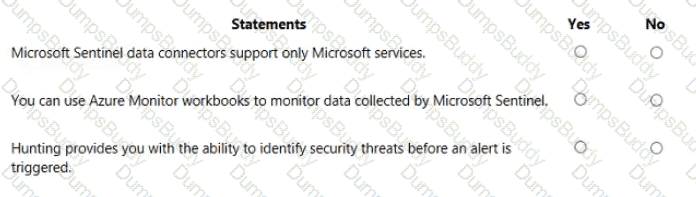
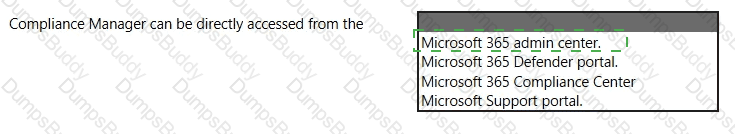
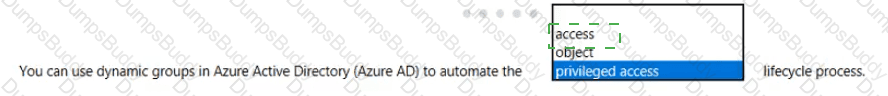
Which Microsoft portal provides information about how Microsoft manages privacy, compliance, and security?
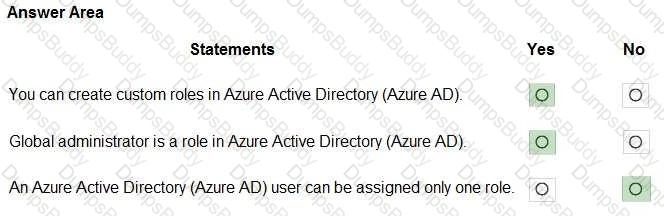
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

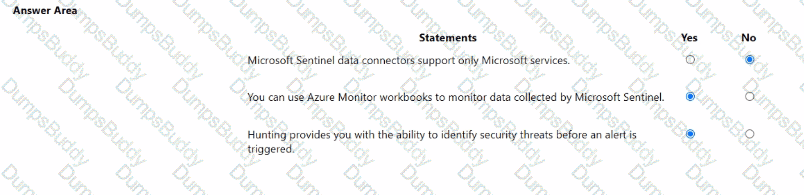
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
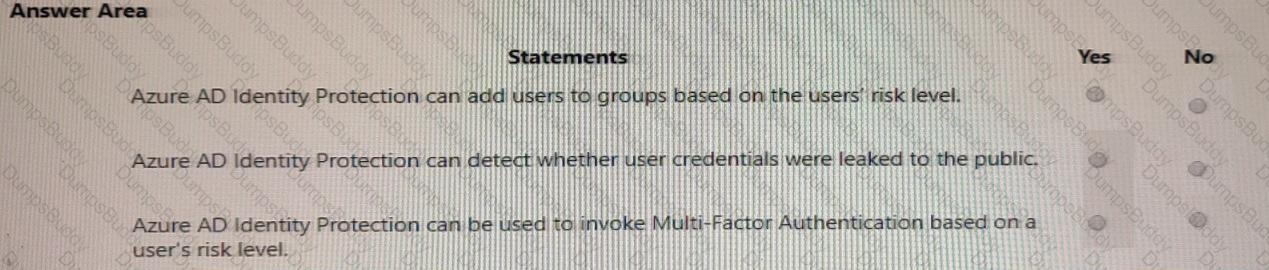
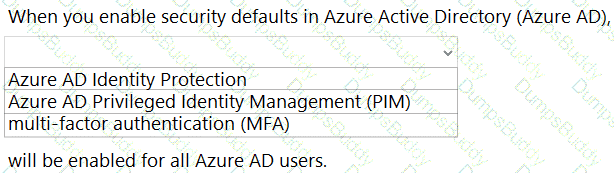
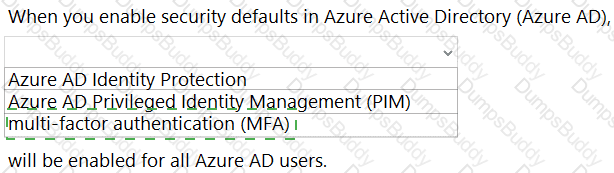
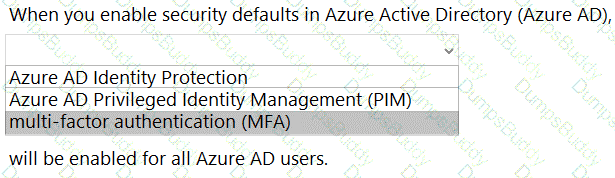
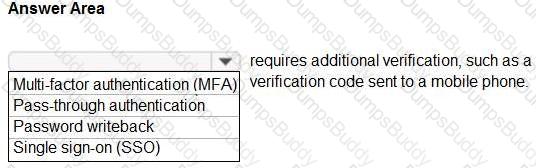
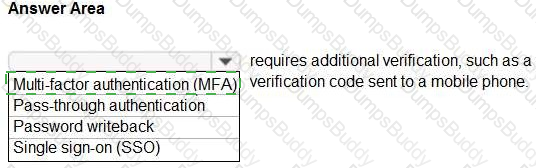
When security defaults are enabled for an Azure Active Directory (Azure AD) tenant, which two requirements are enforced? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
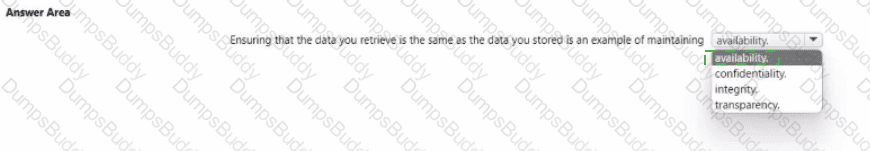
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
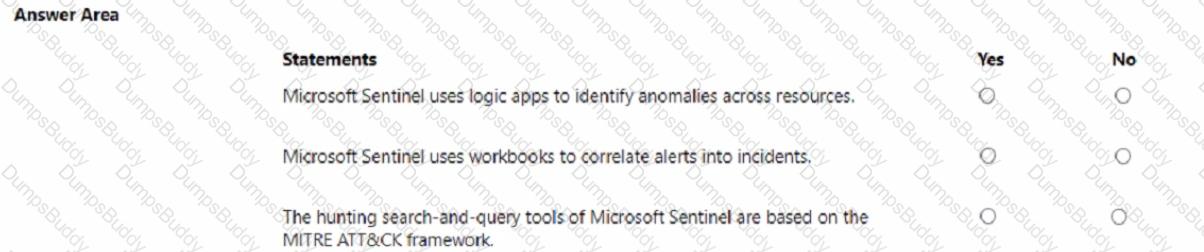
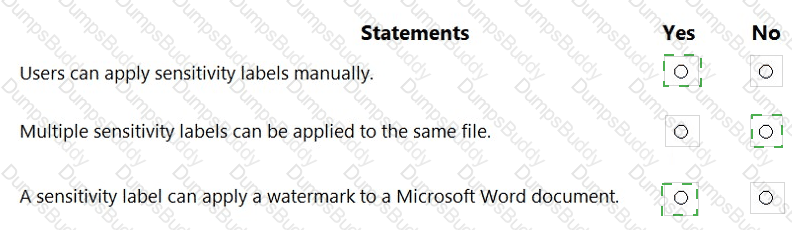
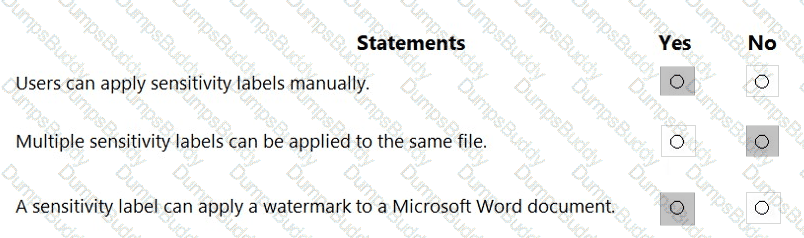
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Which three authentication methods does Windows Hello for Business support? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
What are three uses of Microsoft Cloud App Security? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Which two types of resources can be protected by using Azure Firewall? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
You need to connect to an Azure virtual machine by using Azure Bastion. What should you use?
Microsoft 365 Endpoint data loss prevention (Endpoint DLP) can be used on which operating systems?
Which Microsoft 365 compliance feature can you use to encrypt content automatically based on specific conditions?
What can you use to protect against malicious links sent in email messages, chat messages, and channels?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
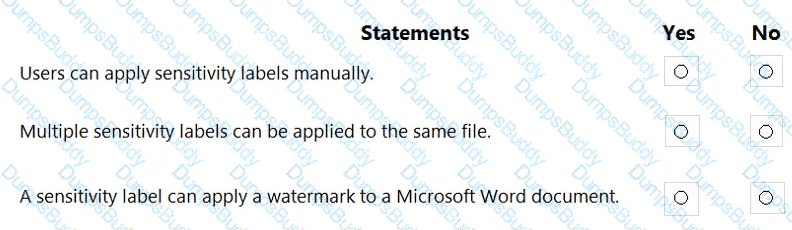
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
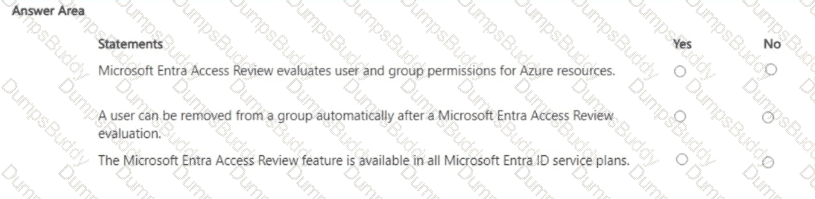
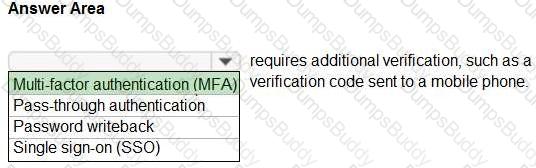
Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
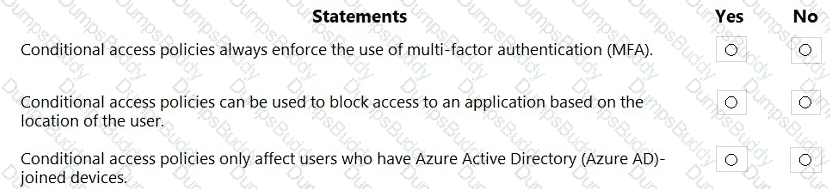
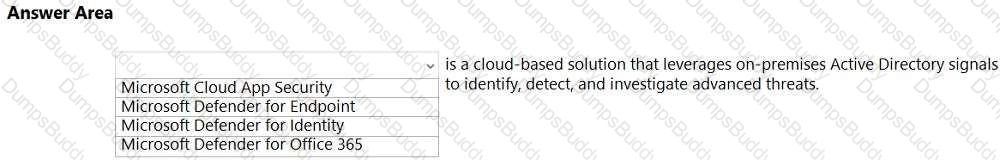
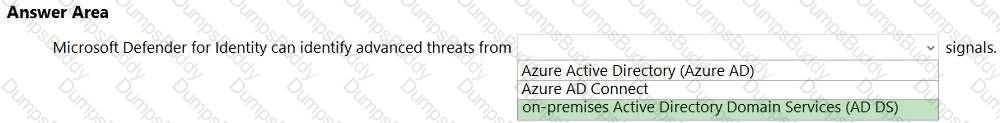
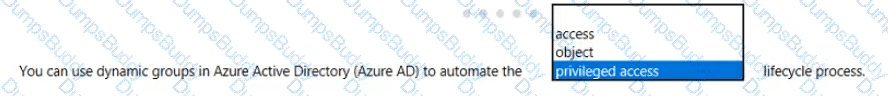
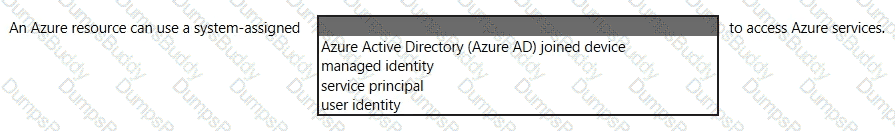
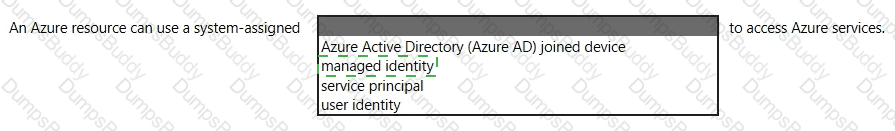
In a hybrid identity model, what can you use to sync identities between Active Directory Domain Services (AD DS) and Azure Active Directory (Azure AD)?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

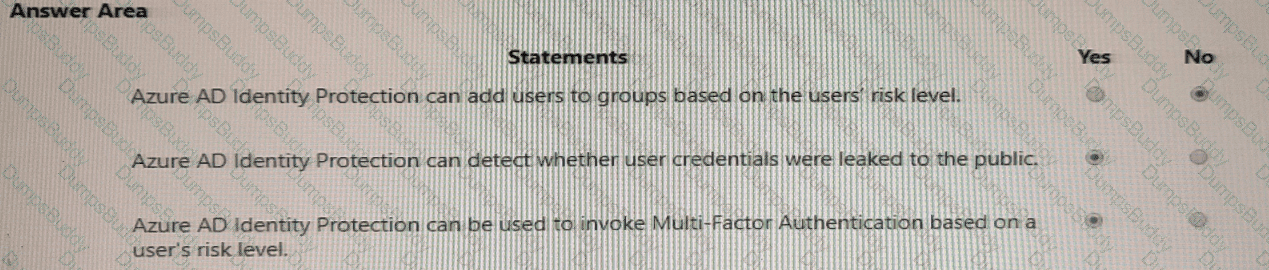
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point
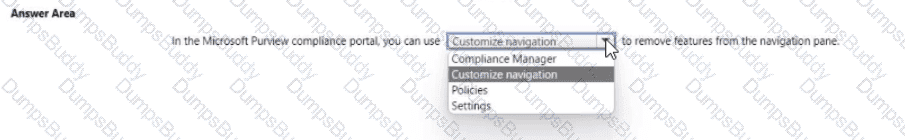
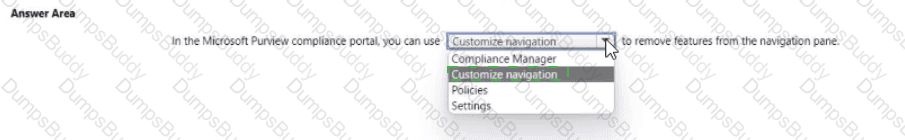
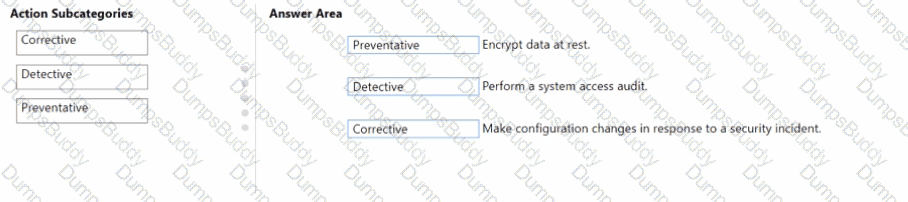
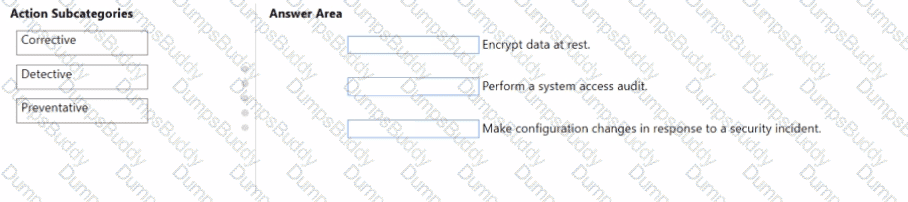
You are evaluating the compliance score in Microsoft Purview Compliance Manager.
Match the compliance score action subcategories to the appropriate actions.
To answer, drag the appropriate action subcategory from the column on the left to its action on the right. Each action subcategory may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
You have an Azure subscription.
You need to implement approval-based time-bound role activation.
What should you use?
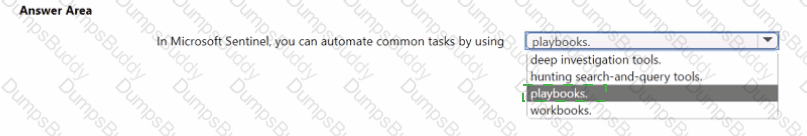
What do you use to provide real-time integration between Azure Sentinel and another security source?
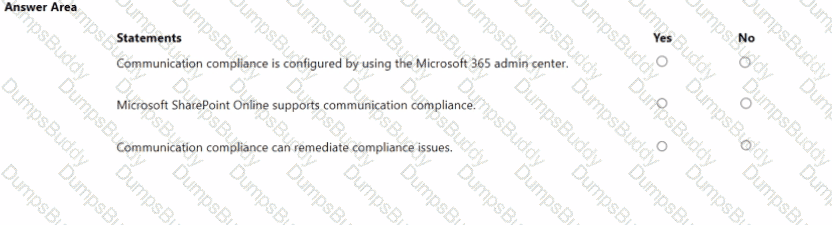
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
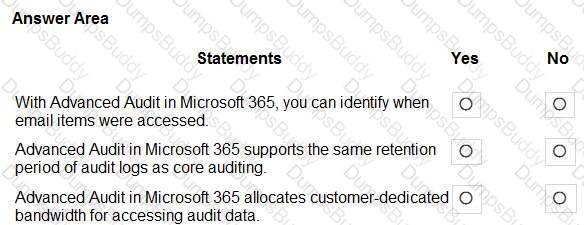
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
What should you use in the Microsoft Defender portal to view security trends and track the protection status of identities?
You have an Azure subscription that contains a Log Analytics workspace.
You need to onboard Microsoft Sentinel.
What should you do first?