SC-100 Microsoft Cybersecurity Architect Questions and Answers
You need to recommend a solution to secure the MedicalHistory data in the ClaimsDetail table. The solution must meet the Contoso developer requirements.
What should you include in the recommendation?
You need to recommend a solution to resolve the virtual machine issue. What should you include in the recommendation? (Choose Two)
You need to recommend a strategy for securing the litware.com forest. The solution must meet the identity requirements. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE; Each correct selection is worth one point.
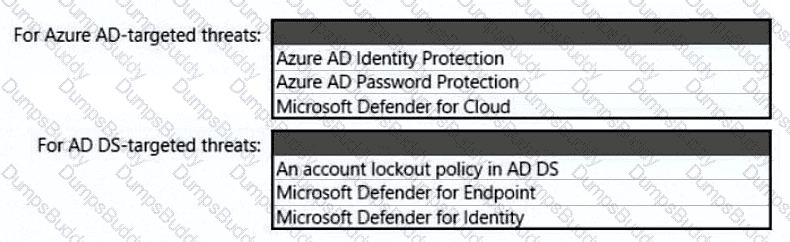
You need to recommend a multi-tenant and hybrid security solution that meets to the business requirements and the hybrid requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

You need to design a strategy for securing the SharePoint Online and Exchange Online data. The solution must meet the application security requirements.
Which two services should you leverage in the strategy? Each correct answer presents part of the solution. NOTE; Each correct selection is worth one point.
To meet the application security requirements, which two authentication methods must the applications support? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
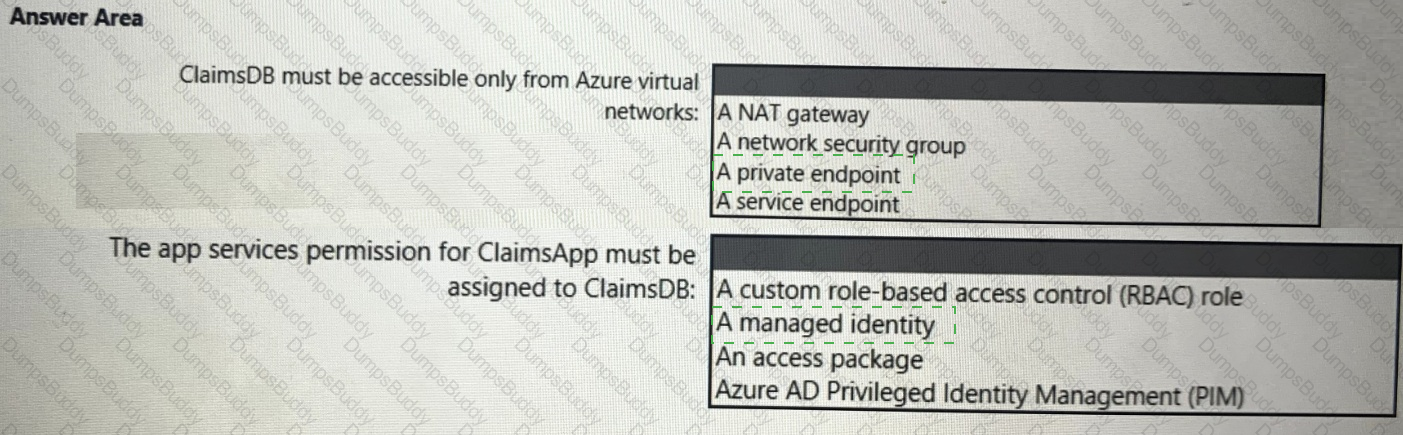
You need to recommend a solution to meet the requirements for connections to ClaimsDB.
What should you recommend using for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
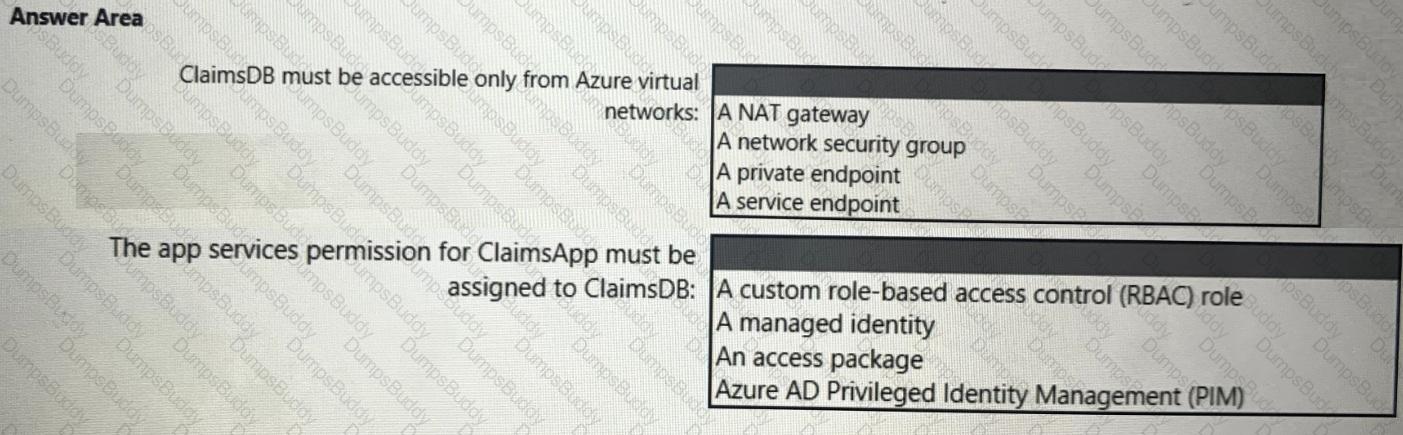
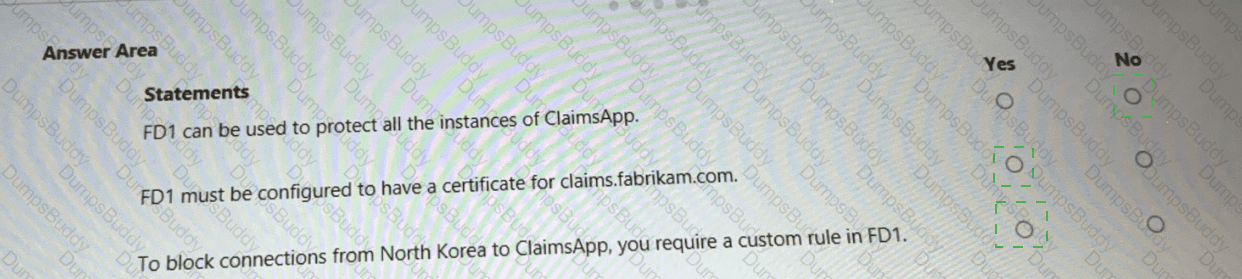
You are evaluating the security of ClaimsApp.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE; Each correct selection is worth one point.
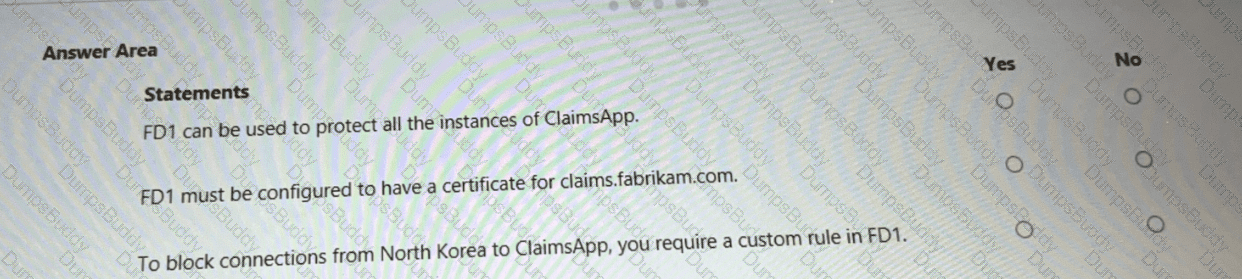
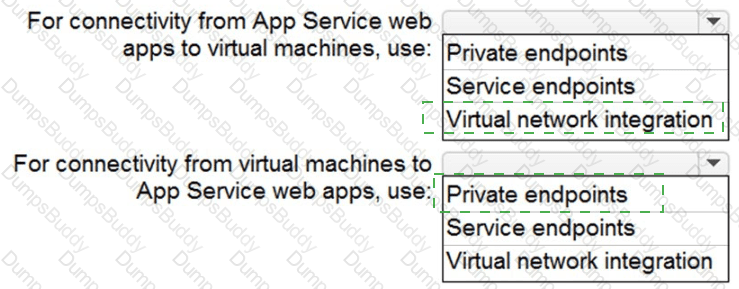
You need to recommend a strategy for App Service web app connectivity. The solution must meet the landing zone requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE Each correct selection is worth one point.
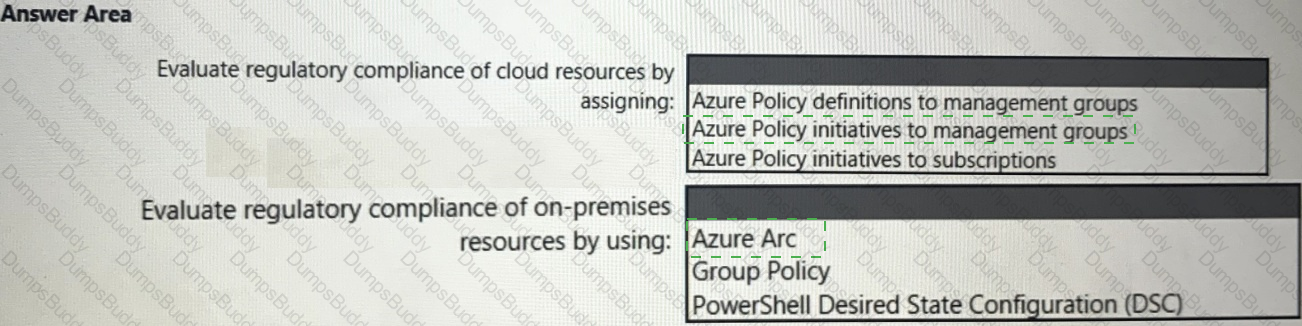
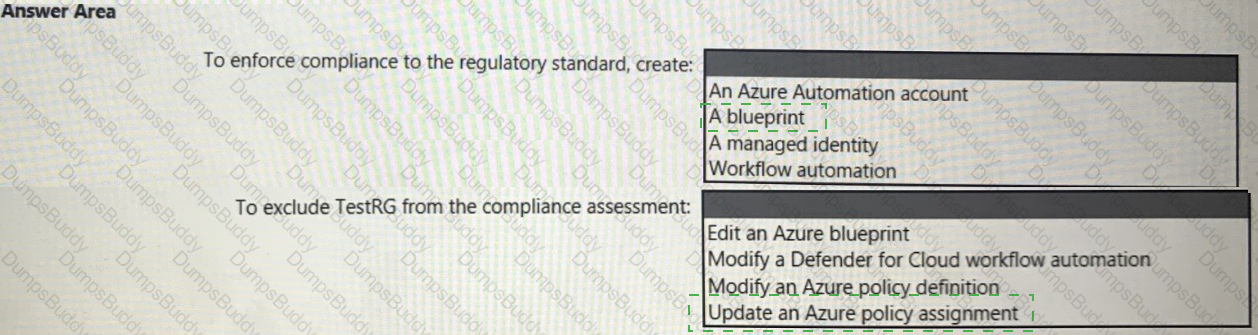
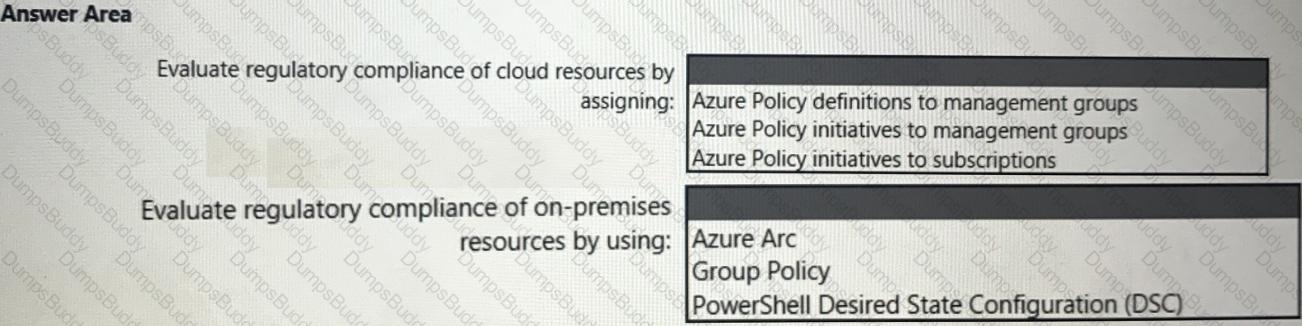
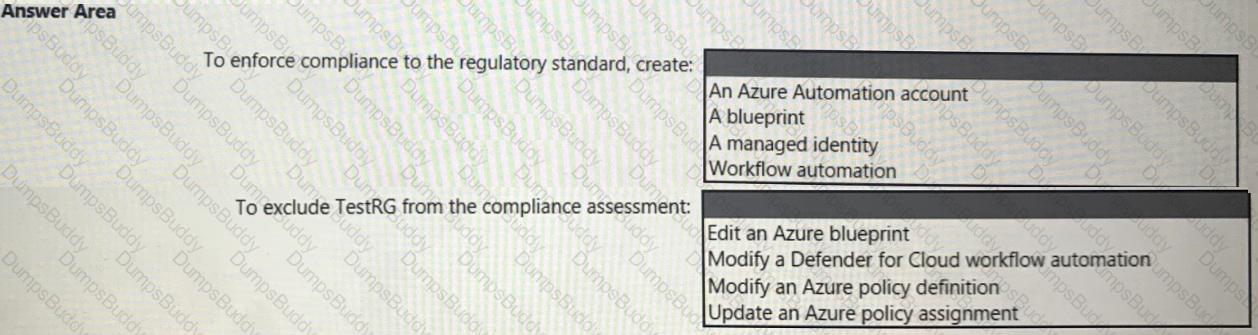
You need to recommend a solution to evaluate regulatory compliance across the entire managed environment. The solution must meet the regulatory compliance requirements and the business requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution for securing the landing zones. The solution must meet the landing zone requirements and the business requirements.
What should you configure for each landing zone?
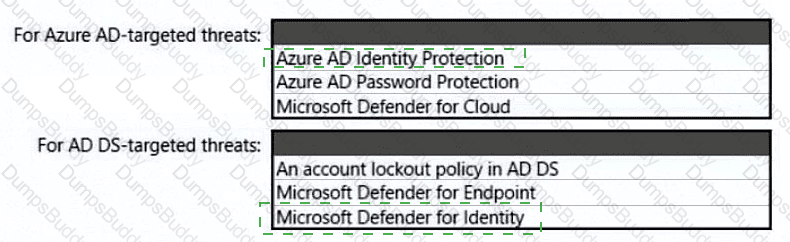
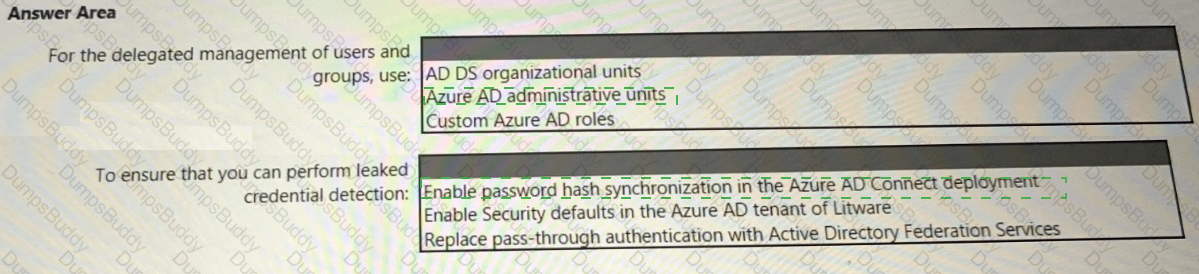
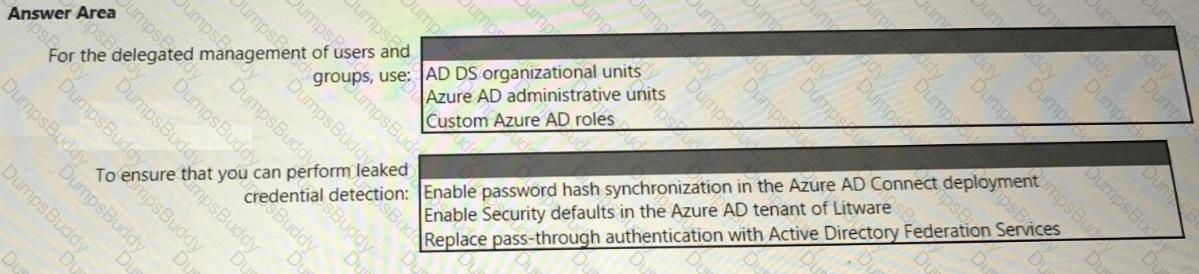
You need to recommend an identity security solution for the Azure AD tenant of Litware. The solution must meet the identity requirements and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to meet the compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to meet the security requirements for the virtual machines.
What should you include in the recommendation?
A customer follows the Zero Trust model and explicitly verifies each attempt to access its corporate applications.
The customer discovers that several endpoints are infected with malware.
The customer suspends access attempts from the infected endpoints.
The malware is removed from the end point.
Which two conditions must be met before endpoint users can access the corporate applications again? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You have an Azure subscription that is used as an Azure landing zone for an application. You need to evaluate the security posture of all the workloads in the landing zone. What should you do first?
You have an Azure subscription that contains multiple network security groups (NSGs), multiple virtual machines, and an Azure Bastion host named bastion1.
Several NSGs contain rules that allow direct RDP access to the virtual machines by bypassing bastion!
You need to ensure that the virtual machines can be accessed only by using bastion! The solution must prevent the use of NSG rules to bypass bastion1.
What should you include in the solution?
Your on-premises network contains an Active Directory Domain Services (AD DS) domain. The domain contains a group named Group1 and five servers that run Windows Server. Each server contains a standalone app. Each app is used by the members of Group1.
You have a Microsoft Entra tenant that syncs with the domain.
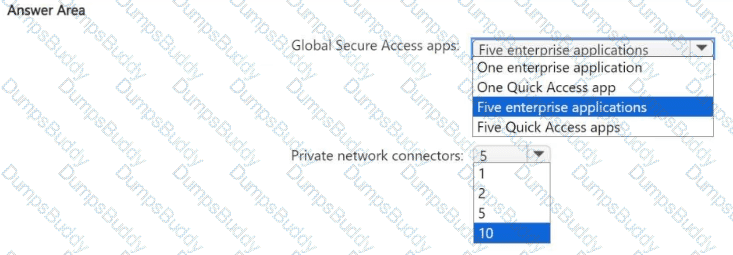
You plan to manage access to the apps by deploying Global Secure Access. You will use a Conditional Access policy to enforce security controls for all connections to the apps.
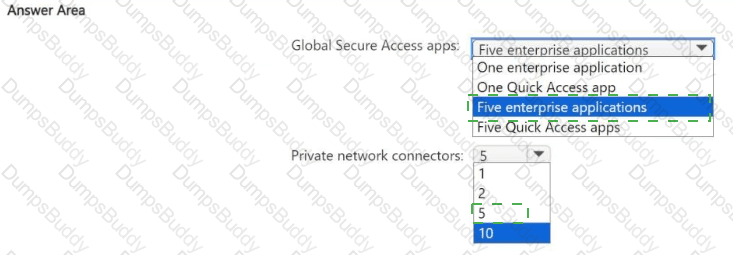
You need to recommend a Global Secure Access app and Microsoft Entra private network connector configuration for the planned deployment. The solution must minimize administrative effort and be highly available.
What is the minimum number of Global Secure Access apps and private network connectors you should recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have legacy operational technology (OT) devices and loT devices.
You need to recommend best practices for applying Zero Trust principles to the OT and loT devices based on the Microsoft Cybersecurity Reference Architectures (MCRA). The solution must minimize the risk of disrupting business operations.
Which two security methodologies should you include in the recommendation? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point
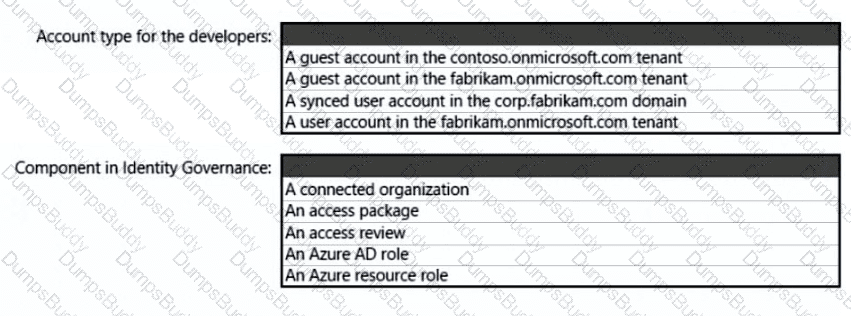
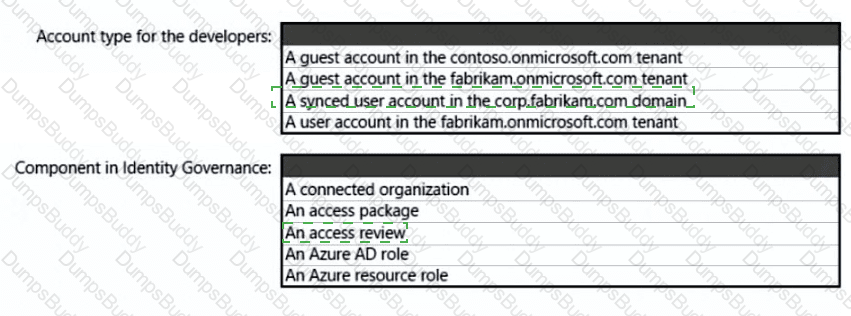
You are designing a privileged access strategy for a company named Contoso, Ltd. and its partner company named Fabrikam, Inc. Contoso has a Microsoft Entra tenant named contoso.com. Fabrikam has a Microsoft Entra tenant named fabrikam.com. Users at Fabrikam must access the resources in contoso.com.
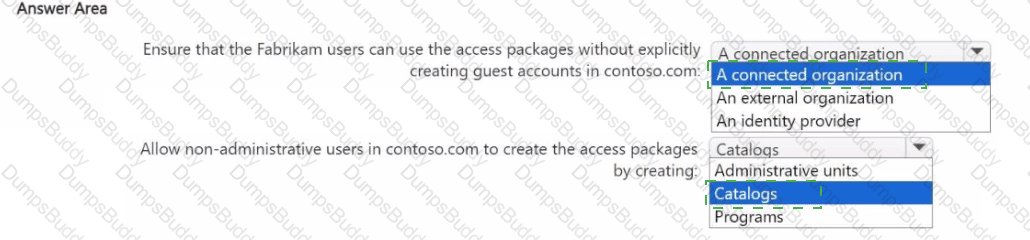
You need to provide the Fabrikam users with access to the Contoso resources by using access packages. The solution must meet the following requirements:
• Ensure that the Fabrikam users can use the Contoso access packages without explicitly creating guest accounts in contoso.com.
• Allow non-administrative users in contoso.com to create the access packages.
What should you use for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

You need to recommend a solution to scan the application code. The solution must meet the application development requirements. What should you include in the recommendation?
You have an Azure subscription.
You plan to deploy enterprise-scale landing zones based on the Microsoft Cloud Adoption Framework for Azure. The deployment will include a single-platform landing zone for all shared services and three application landing zones that will each host a different Azure application.
You need to recommend which resource to deploy to each landing zone. The solution must meet the Cloud Adoption Framework best-practice recommendations for enterprise-scale landing zones.
What should you recommend?
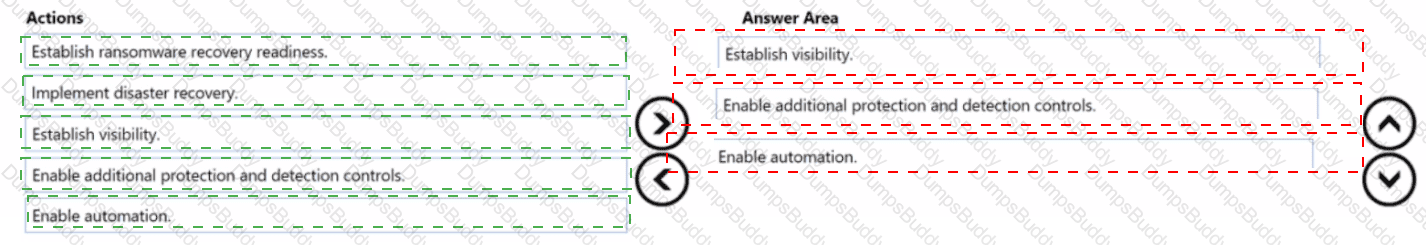
You are designing a security operations strategy based on the Zero Trust framework.
You need to increase the operational efficiency of the Microsoft Security Operations Center (SOC).
Based on the Zero Trust framework, which three deployment objectives should you prioritize in sequence? To answer, move the appropriate objectives from the list of objectives to the answer area and arrange them in the correct order.

You have an on-premises network that has several legacy applications. The applications perform LDAP queries against an existing directory service. You are migrating the on-premises infrastructure to a cloud-only infrastructure.
You need to recommend an identity solution for the infrastructure that supports the legacy applications. The solution must minimize the administrative effort to maintain the infrastructure.
Which identity service should you include in the recommendation?
You have an Azure subscription that contains multiple Azure Data Lake Storage accounts.
You need to recommend a solution to encrypt the content of the accounts by using service-side encryption and customer-managed keys. The solution must ensure that individual encryption keys are applied at the most granular level.
At which level should you recommend the encryption be applied?
You have an Azure AD tenant that syncs with an Active Directory Domain Services {AD DS) domain. Client computers run Windows and are hybrid-joined to Azure AD.
You are designing a strategy to protect endpoints against ransomware. The strategy follows Microsoft Security Best Practices.
You plan to remove all the domain accounts from the Administrators group on the Windows computers.
You need to recommend a solution that will provide users with administrative access to the Windows computers only when access is required. The solution must minimize the lateral movement of ransomware attacks if an administrator account on a computer is compromised.
What should you include in the recommendation?
You have an Azure subscription.
You plan to deploy Azure App Services apps by using Azure DevOps.
You need to recommend a solution to ensure that deployed apps maintain compliance with Microsoft cloud security benchmark (MCSB) recommendations.
What should you include in the recommendation?
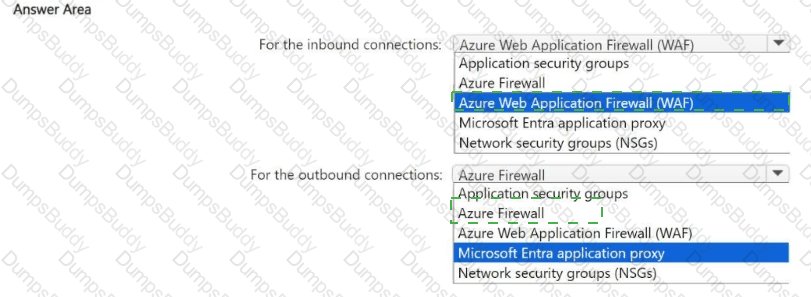
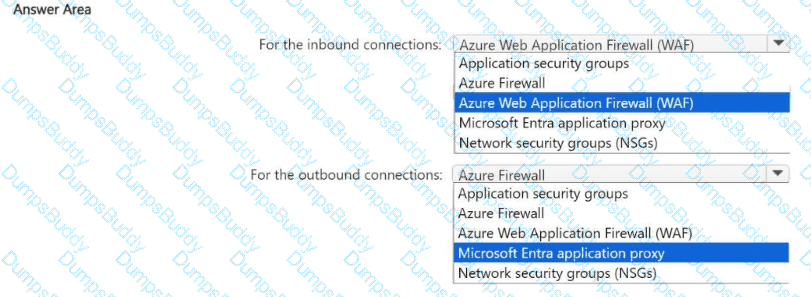
You have an Azure subscription that contains a virtual network named VNet1. VNet1 contains a 10-node virtual machine scale set that hosts a web search app named App1. Customers access App1 from the internet. The nodes establish outbound HTTP and HTTPS connections to the internet.
You need to recommend a network security solution for App1. The solution must meet the following requirements:
• Inbound connections to App1 that contain security threats specified in the Core Rule. Set (CRS) from the Open Web Application Security Project (OWASP) must be blocked.
• Outbound HTTP and HTTPS connections from the virtual machine scale set that contain security threats identified by the Microsoft Defender Threat Intelligence (Defender Tl) feed must be blocked.
What should you include in the recommendation? To answer, select the options in the answer area,
NOTE: Each correct answer is worth one point.
You have a Microsoft 365 tenant that contains two groups named Group1 and Group2.
You use Microsoft Defender XDR to manage the tenants of your company's customers.
You need to ensure that the users in Group1 can perform security tasks in the tenant of each customer. The solution must meet the following requirements:
The Group1 users must only be assigned the Security Operator role for the customer tenants.
The users in Group2 must be able to assign the Security Operators role to the Group1 users for the customer tenants.
The use of guest accounts must be minimized.
Administrative effort must be minimized.
What should you include in the solution?
Your company has a main office and 10 branch offices. Each branch office contains an on-premises file server that runs Windows Server and multiple devices that run either Windows 11 or macOS. The devices are enrolled in Microsoft Intune.
You have a Microsoft Entra tenant.
You need to deploy Global Secure Access to implement web filtering for device traffic to the internet The solution must ensure that all the web traffic from the devices in the branch offices is controlled by using Global Secure Access.
What should you do first in each branch office?
You have a hybrid Azure AD tenant that has pass-through authentication enabled.
You are designing an identity security strategy.
You need to minimize the impact of brute force password attacks and leaked credentials of hybrid identities.
What should you include in the design? To answer, drag the appropriate features to the correct requirements. Each feature may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

You have an Azure subscription that contains a Microsoft Sentinel workspace named WS1.
You need to configure WS1 to meet the following requirements:
• Create custom dashboards to visualize the workload of security analysts that use Microsoft Sentinel.
• Enable automated responses for the security alerts generated by Microsoft Sentinel analytics rules.
What should you use for each requirement? To answer, select the options in the answer area.
NOTE: Each correct answer is worth one point.

You have Windows 11 devices and Microsoft 365 E5 licenses.
You need to recommend a solution to prevent users from accessing websites that contain adult content such as gambling sites. What should you include in the recommendation?
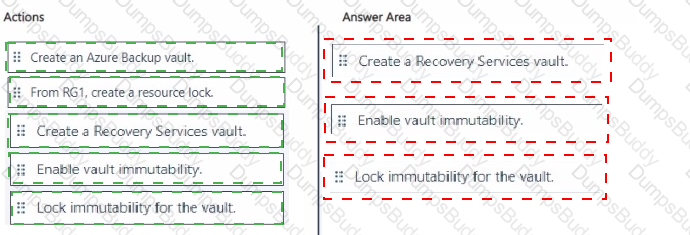
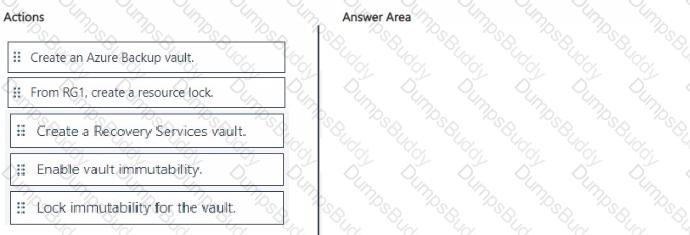
You have an Azure subscription that contains a resources group named RG1. RG1 contains multiple Azure Files shares.
You need to recommend a solution to deploy a backup solution for the shares. The solution must meet the following requirements:
• Prevent the deletion of backups and the vault used to store the backups.
• Prevent privilege escalation attacks against the backup solution.
• Prevent the modification of the backup retention period.
Which three actions should you recommend be performed in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled.
The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019.
You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application.
Which security control should you recommend?
You plan to deploy 20 Azure Kubernetes Service (AKS) clusters. The cluster configuration will be managed declaratively by using Kubernetes manifest files stored in Azure Repos.
You need to recommend a solution to ensure that the configuration of all the clusters remains consistent by using the manifest files stored in Azure Repos.
What should you include in the recommendation?
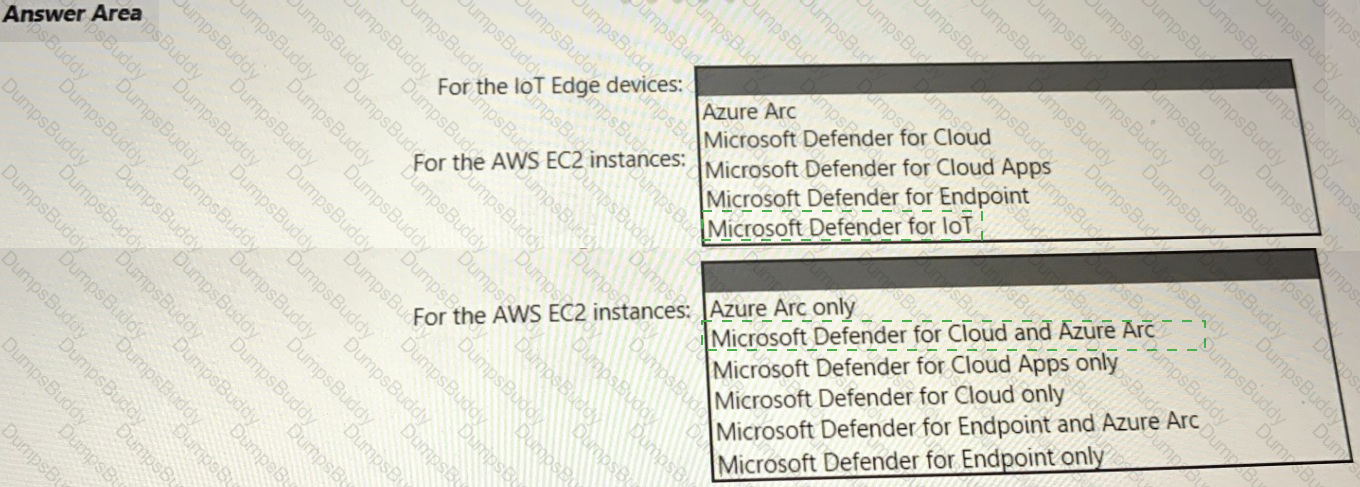
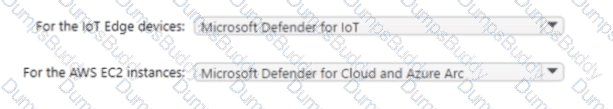
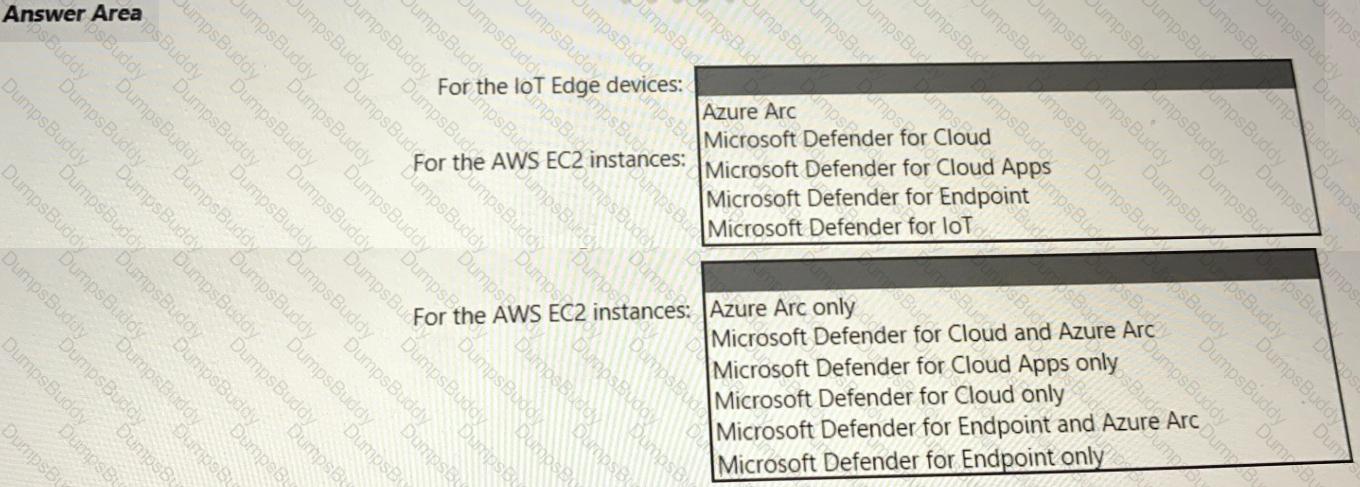
Your company has a multi-cloud environment that contains a Microsoft 365 subscription, an Azure subscription, and Amazon Web Services (AWS) implementation. You need to recommend a security posture management solution for the following components:
• Azure loT Edge devices
• AWS EC2 instances
Which services should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
A customer has a hybrid cloud infrastructure that contains a Microsoft 365 E5 subscription and an Azure subscription.
All the on-premises servers in the perimeter network are prevented from connecting directly to the internet.
The customer recently recovered from a ransomware attack.
The customer plans to deploy Microsoft Sentinel.
You need to recommend configurations to meet the following requirements:
• Ensure that the security operations team can access the security logs and the operation logs.
• Ensure that the IT operations team can access only the operations logs, including the event logs of the servers in the perimeter network.
Which two configurations can you include in the recommendation? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
You have an Azure subscription.
You have a DNS domain named contoso.com that is hosted by a third-party DNS registrar.
Developers use Azure DevOps to deploy web apps to App Service Environments- When a new app is deployed, a CNAME record for the app is registered in contoso.com.
You need to recommend a solution to secure the DNS record tor each web app. The solution must meet the following requirements:
• Ensure that when an app is deleted, the CNAME record for the app is removed also
• Minimize administrative effort.
What should you include in the recommendation?
Azure subscription that uses Azure Storage.
The company plans to share specific blobs with vendors. You need to recommend a solution to provide the vendors with secure access to specific blobs without exposing the blobs publicly. The access must be t\me-Vim\ted. What should you include in the recommendation?