Salesforce-MuleSoft-Developer-II Salesforce Certified MuleSoft Developer II (Mule-Dev-301) Questions and Answers
Which statement is true when using XML SDK for creating custom message processors?
A mule application exposes and API for creating payments. An Operations team wants to ensure that the Payment API is up and running at all times in production.
Which approach should be used to test that the payment API is working in production?
Which configurations are required for HTTP Listener to enable mTLS authentication?
A developer is working on a project that requires encrypting all data before sending it to a backend application. To accomplish this, the developer will use PGP encryption in the Mule 4 Cryptography module.
What is required to encrypt the data before sending it to the backend application?
Multiple individual Mute application need to use the Mule Maven plugin to deploy to CloudHub.
The plugin configuration should .. reused where necessary and anything project, specific should be property-based.
Where should the Mule Maven details be configured?
A developer has created the first version of an API designed for business partners to work commodity prices.
What should developer do to allow more than one major version of the same API to be exposed by the implementation?
A developer deploys an API to CloudHub and applies an OAuth policy on API Manager. During testing, the API response is slow, so the developer reconfigures the API so that the out-of-the-box HTTP Caching policy is applied first, and the OAuth API policy is applied second.
What will happen when an HTTP request is received?
A Mule application defines as SSL/TLS keystore properly ‘tis,keystore.keyPassword’’ as secure.
How can this property be referenced to access its value within the application?
A Mule application deployed to a standardalone Mule runtime uses VM queues to publish messages to be consumed asynchronously by another flow.
In the case of a system failure, what will happen to in-flight messages in the VM queues that have been consumed?
A heathcare customer wants to use hospital system data, which includes code that was developed using legacy tools and methods. The customer has created reusable Java libraries in order to read the data from the system.
What is the most effective way to develop an API retrieve the data from the hospital system?
Refer to the exhibit.
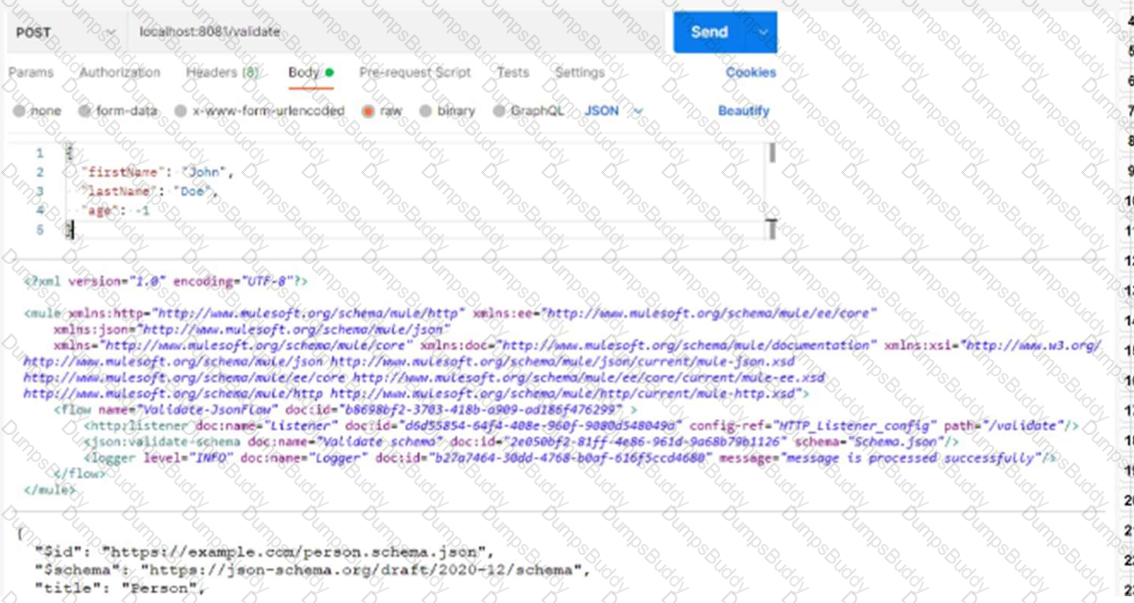
Based on the code snippet, schema,json file, and payload below, what is the outcome of the given code snippet when a request is sent with the payload?
A Mule application for processing orders must log the order ID for every log message output.
What is a best practice to enrich every log message with the order ID?
A custom policy needs to be developed to intercept all cutbound HTTP requests made by Mule applications.
Which XML element must be used to intercept outbound HTTP requests?
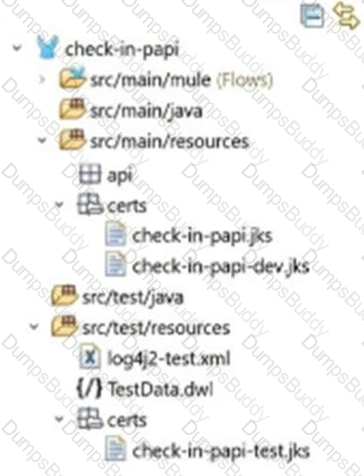
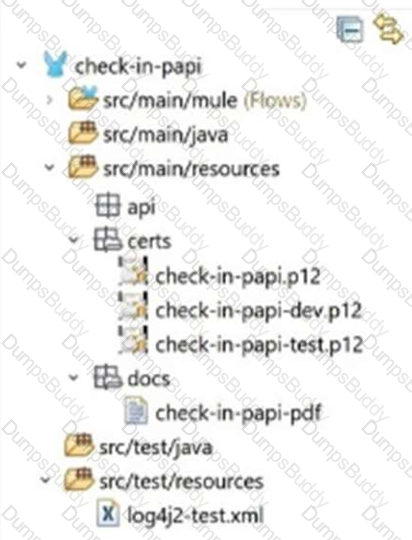
Refer to the exhibit.

A Mule application pom.xml configures the Maven Resources plugin to exclude parsing binary files in the project’s src/main/resources/certs directory.
Which configuration of this plugin achieves a successful build?
A)
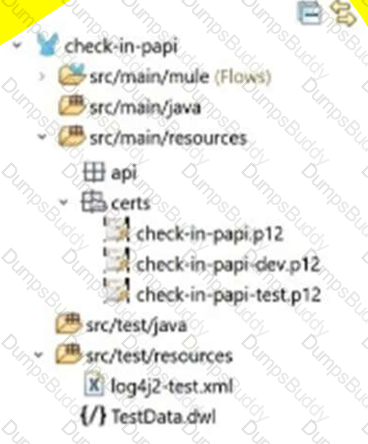
B)
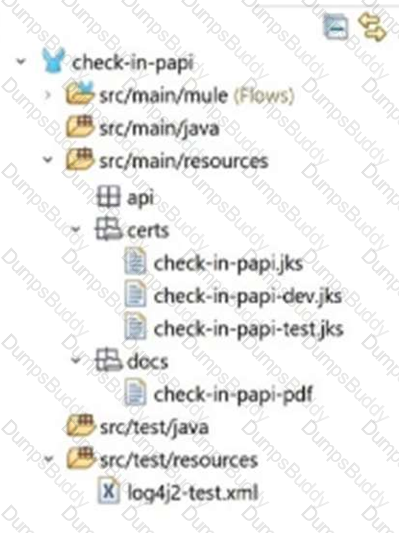
C)
D)