RH033 Red Hat Linux Essentials Questions and Answers
You work as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. You want to view the status of the current processes running on a Linux computer. You also want to save the output to the ProStat.txt file. Which of the following commands will you use to accomplish the task?
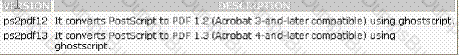
You work as the Network administrator for McNeil Inc. The company has a Linux-based network. You are working as a root user on the Linux operating system. You have created a PostScript file on your system. You want to convert this file to a PDF file. Which of the following commands should you use to accomplish the task?
Which of the following cp command parameters copies only when the source file is newer than the destination file or when the destination file is missing?
Which of the following key-combinations is used to redo a change undone by a u command in vim?
You work as a Network Administrator for Net Perfect Inc. The company has a Linux-based network.
You have created a folder named Report.
You have made David the owner of the folder. The members of a group named JAdmin can access the folder and have Read, Write, and
Execute permissions. No other user can access the folder. You want to ensure that the members of
the JAdmin group do not have Write permission on the folder. Also, you want other users to have Read permission on the Report folder.
Whizh of the following commands will you use to accomplish the task?
Which of the following commands can be used to delete all jobs queued in a printer?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following commands is used to set down the interface and flush all its addresses?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He wants to change the group membership of the file foo to group bar. Which of the following commands will he use to accomplish the task?
All network interface settings are stored in /etc/sysconfig/network-scripts/ directory. Which of the following tools are used to read the interface configuration files?
Each correct answer represents a complete solution. Choose all that apply.
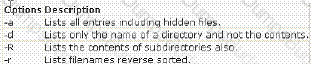
You work as a Network Administrator for McNeil Inc. The company has a Linux-based network. You are a root user on the Red Hat operating system. You want to see all directories and files, including hidden files of your home directory in long listing format. Which of the following command-line utilities would you use to accomplish this task?
You run the wc -c file1.txt command. If this command displays any error message, you want to store the error message in the error.txt file. Which of the following commands will you use to accomplish the task?
You work as the Network Administrator for McNeil Inc. The company has a Linux- based network.
You are working as a root user on the Red Hat operating system. Joe is a user in your company. You want to remove Joe's tmp files that are 3 days older. Which of the following command syntaxes should you use to accomplish the task?
Which of the following statements are true about open source software?
Each correct answer represents a complete solution. Choose two.
Which of the following is NOT true about the inode table in the Linux operating system?
Which of the following network diagnostic tools is NOT used in the Linux operating system?
You work as a Network Administrator for Maverick Inc. The company has a Linux-based network.
You are working on a Linux computer. You want to see the environment variables that are set on your computer. Which of the following commands will you use?
Fill in the blank with appropriate word. The------------ command copies files between hosts on a network. It uses ssh for data transfer, and uses the same authentication and provides the same security as ssh. It will ask for passwords or passphrases if they are needed for authentication.
You work as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. You want to modify a configuration file in a Linux server. Which of the following utilities will you use to accomplish the task?