An auditor is evaluating the configuration of Panorama and notices a discrepancy between the Panorama template and the local firewall configuration. When overriding the firewall configuration pushed from Panorama, what should you consider?
An engineer is monitoring an active/active high availability (HA) firewall pair.
Which HA firewall state describes the firewall that is currently processing traffic?
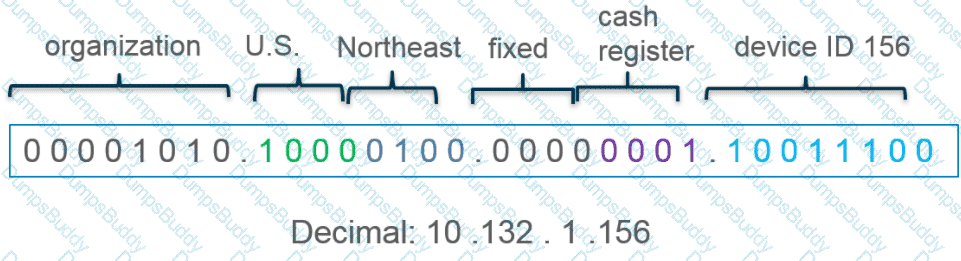
What type of address object would be useful for internal devices where the addressing structure assigns meaning to certain bits in the address, as illustrated in the diagram?
An administrator has been tasked with configuring decryption policies,
Which decryption best practice should they consider?
Based on the images below, what is the correct order in which the various rules are deployed to firewalls inside the DATACENTER_DG device group?
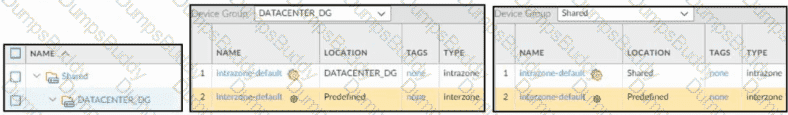
Based on the images below, what is the correct order in which the various rules are deployed to firewalls inside the DATACENTER_DG device group?
A security engineer needs to mitigate packet floods that occur on a RSF servers behind the internet facing interface of the firewall. Which Security Profile should be applied to a policy to prevent these packet floods?
What must be taken into consideration when preparing a log forwarding design for all of a customer’s deployed Palo Alto Networks firewalls?
A remote administrator needs access to the firewall on an untrust interface. Which three options would you configure on an interface Management profile to secure management access? (Choose three)
An administrator has a Palo Alto Networks NGFW. All security subscriptions and decryption are enabled and the system is running close to its resource limits.
Knowing that using decryption can be resource-intensive, how can the administrator reduce the load on the firewall?
A firewall administrator has been tasked with ensuring that all Panorama configuration is committed and pushed to the devices at the end of the day at a certain time. How can they achieve this?
‘SSL Forward Proxy decryption is configured, but the firewall uses Untrusted-CA to sign the website https://www important-website com certificate, End-users are receiving the "security certificate is no: trusted” warning, Without SSL decryption, the web browser shows chat the website certificate is trusted and signet by well-known certificate chain Well-Known-intermediate and Wako Hebe CA Security administrator who represents the customer requires the following two behaviors when SSL Forward Proxy is enabled:
1. End-users must not get the warning for the https:///www.very-import-website.com/ website.
2. End-users should get the warning for any other untrusted website.
Which approach meets the two customer requirements?
If a URL is in multiple custom URL categories with different actions, which action will take priority?
What would allow a network security administrator to authenticate and identify a user with a new BYOD-type device that is not joined to the corporate domain?
What happens when an A/P firewall pair synchronizes IPsec tunnel security associations (SAs)?
An administrator wants to use LDAP, TACACS+, and Kerberos as external authentication services for authenticating users. What should the administrator be aware of regarding the authentication sequence, based on the Authentication profile in the order Kerberos LDAP, and TACACS+?
The vulnerability protection profile of an on-premises Palo Alto Networks firewall is triggering on a common Threat ID, and it has been determined to be a false positive. The issue causes an outage of a critical service. When the vulnerability protection profile is opened to add the exception, the Threat ID is missing. Which action will most efficiently find and implement the exception?
An engineer is monitoring an active/active high availability (HA) firewall pair.
Which HA firewall state describes the firewall that is experiencing a failure of a monitored path?
An administrator wants to add User-ID information for their Citrix MetaFrame Presentation Server (MPS) users.
Which option should the administrator use?
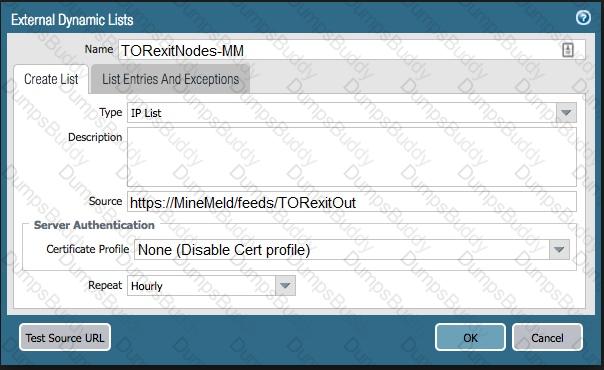
The firewall is not downloading IP addresses from MineMeld. Based, on the image, what most likely is wrong?
Which two profiles should be configured when sharing tags from threat logs with a remote User-ID agent? (Choose two.)
An administrator is informed that the engineer who previously managed all the VPNs has left the company. According to company policies the administrator must update all the IPSec VPNs with new pre-shared keys Where are the pre-shared keys located on the firewall?
A security engineer needs firewall management access on a trusted interface.
Which three settings are required on an SSL/TLS Service Profile to provide secure Web UI authentication? (Choose three.)
An engineer reviews high availability (HA) settings to understand a recent HA failover event. Review the screenshot below.
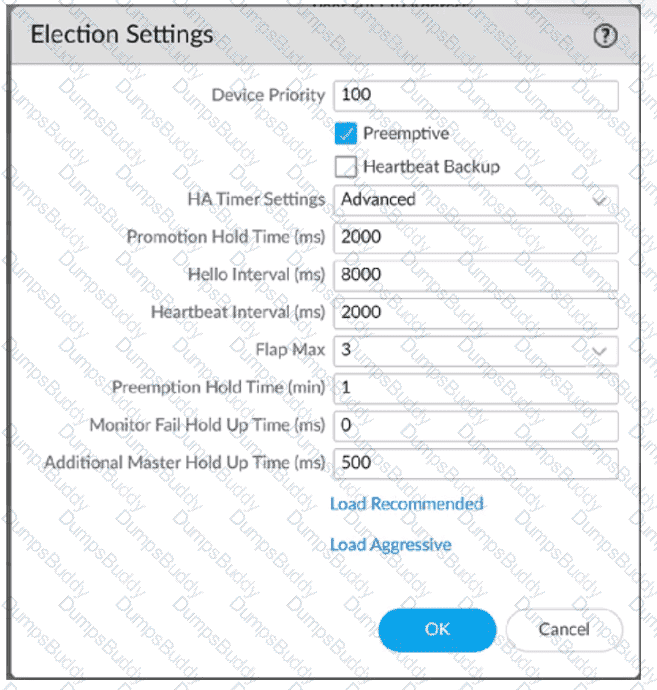
Which timer determines the frequency at which the HA peers exchange messages in the form of an ICMP (ping)
What can the Log Forwarding built-in action with tagging be used to accomplish?
A firewall engineer is managing a Palo Alto Networks NGFW that does not have the DHCP server on DHCP agent configuration. Which interface mode can the broadcast DHCP traffic?
Which tool will allow review of the policy creation logic to verify that unwanted traffic is not allowed?
An administrator needs to validate that policies that will be deployed will match the appropriate rules in the device-group hierarchy. Which tool can the administrator use to review the policy creation logic and verify that unwanted traffic is not allowed?
A firewall engineer is configuring quality of service (OoS) policy for the IP address of a specific server in an effort to limit the bandwidth consumed by frequent downloads of large files from the internet.
Which combination of pre-NAT and / or post-NAT information should be used in the QoS rule?
Users have reported an issue when they are trying to access a server on your network. The requests aren’t taking the expected route. You discover that there are two different static routes on the firewall for the server. What is used to determine which route has priority?
What does the User-ID agent use to find login and logout events in syslog messages?
What are three prerequisites to enable Credential Phishing Prevention over SSL? (Choose three
Which DoS Protection Profile detects and prevents session exhaustion attacks against specific destinations?
An administrator pushes a new configuration from Panorama to a pair of firewalls that are configured as an active/passive HA pair. Which NGFW receives the configuration from Panorama?
When you troubleshoot an SSL Decryption issue, which PAN-OS CL1 command do you use to check the details of the Forward Trust certificate. Forward Untrust certificate, and SSL Inbound Inspection certificate?
After configuring an IPSec tunnel, how should a firewall administrator initiate the IKE phase 1 to see if it will come up?
Which two components are required to configure certificate-based authentication to the web UI when firewall access is needed on a trusted interface? (Choose two.)
An engineer is configuring a template in Panorama which will contain settings that need to be applied to all firewalls in production.
Which three parts of a template an engineer can configure? (Choose three.)
A firewall administrator is changing a packet capture filter to troubleshoot a specific traffic flow. Upon opening the newly created packet capture, the administrator still sees traffic for the previous filter.
What can the administrator do to limit the captured traffic to the newly configured filter?
For company compliance purposes, three new contractors will be working with different device-groups in their hierarchy to deploy policies and objects.
Which type of role-based access is most appropriate for this project?
An engineer is deploying multiple firewalls with common configuration in Panorama.
What are two benefits of using nested device groups? (Choose two.)
A network security engineer needs to enable Zone Protection in an environment that makes use of Cisco TrustSec Layer 2 protections
What should the engineer configure within a Zone Protection profile to ensure that the TrustSec packets are identified and actions are taken upon them?
An administrator needs to build Security rules in a Device Group that allow traffic to specific users and groups defined in Active Directory.
What must be configured in order to select users and groups for those rules from Panorama?
An administrator is receiving complaints about application performance degradation. After checking the ACC, the administrator observes that there is an excessive amount of VoIP traffic.
Which three elements should the administrator configure to address this issue? (Choose three.)
An administrator has purchased WildFire subscriptions for 90 firewalls globally.
What should the administrator consider with regards to the WildFire infra-structure?
Which three options does Panorama offer for deploying dynamic updates to its managed devices? (Choose three.)
A firewall administrator to have visibility on one segment of the company network. The traffic on the segment is routed on the Backbone switch. The administrator is planning to apply security rules on segment X after getting the visibility. There is already a PAN-OS firewall used in L3 mode as an internet gateway, and there are enough system resources to get extra traffic on the firewall. The administrator needs to complete this operation with minimum service interruptions and without making any IP changes. What is the best option for the administrator to take?
How can Panorama help with troubleshooting problems such as high CPU or resource exhaustion on a managed firewall?
Which Panorama mode should be used so that all logs are sent to. and only stored in. Cortex Data Lake?
An administrator is required to create an application-based Security policy rule to allow Evernote. The Evernote application implicitly uses SSL and web browsing.
What is the minimum the administrator needs to configure in the Security rule to allow only Evernote?
When an engineer configures an active/active high availability pair, which two links can they use? (Choose two)
When you import the configuration of an HA pair into Panorama, how do you prevent the import from affecting ongoing traffic?
An engineer troubleshooting a VPN issue needs to manually initiate a VPN tunnel from the CLI Which CLI command can the engineer use?
Exhibit.
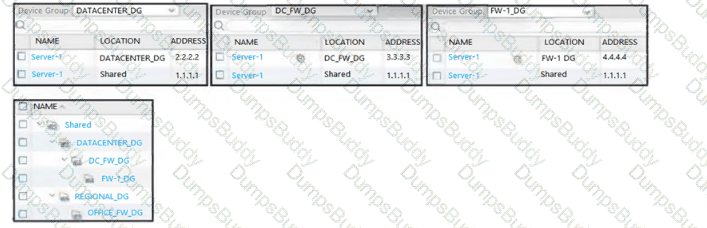
Review the screenshots and consider the following information
1. FW-1is assigned to the FW-1_DG device group, and FW-2 is assigned to OFFICE_FW_DC
2. There are no objects configured in REGIONAL_DG and OFFICE_FW_DG device groups
Which IP address will be pushed to the firewalls inside Address Object Server-1?
An administrator pushes a new configuration from Panorama to a par of firewalls that are configured as an active/passive HA pair. Which NGFW receives the from Panorama?
Exhibit.
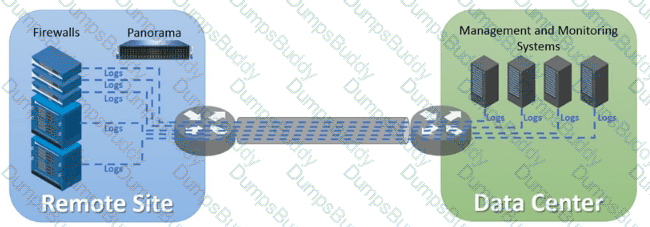
An organization has Palo Alto Networks NGFWs that send logs to remote monitoring and security management platforms The network team has reported excessive traffic on the corporate WAN How could the Palo Alto Networks NGFW administrator reduce WAN traffic while maintaining support for all the existing monitoring/security platforms?
The decision to upgrade PAN-OS has been approved. The engineer begins the process by upgrading the Panorama servers, but gets an error when attempting the install.
When performing an upgrade on Panorama to PAN-OS. what is the potential cause of a failed install?
An administrator configures a preemptive active-passive high availability (HA) pair of firewalls and configures the HA election settings on firewall-02 with a device priority value of 100, and firewall-01 with a device priority value of 90.
When firewall-01 is rebooted, is there any action taken by the firewalls?
What does SSL decryption require to establish a firewall as a trusted third party and to establish trust between a client and server to secure an SSL/TLS connection'?
For company compliance purposes, three new contractors will be working with different device groups in their hierarchy to deploy policies and objects. Which type of role-based access is most appropriate for this project?
A customer would like to support Apple Bonjour in their environment for ease of configuration.
Which type of interface in needed on their PA-3200 Series firewall to enable Bonjour Reflector in a segmented network?
An administrator is troubleshooting intermittent connectivity problems with a user's GlobalProtect connection. Packet captures at the firewall reveal missing UDP packets, suggesting potential packet loss on the connection. The administrator aims to resolve the issue by enforcing an SSL tunnel over TCP specifically for this user.
What configuration change is necessary to implement this troubleshooting solution for the user?
A company wants to use GlobalProtect as its remote access VPN solution.
Which GlobalProtect features require a Gateway license?
A company wants to deploy IPv6 on its network which requires that all company Palo Alto Networks firewalls process IPv6 traffic and to be configured with IPv6 addresses. Which consideration should the engineers take into account when planning to enable IPv6?
An administrator is troubleshooting why video traffic is not being properly classified.
If this traffic does not match any QoS classes, what default class is assigned?
To ensure that a Security policy has the highest priority, how should an administrator configure a Security policy in the device group hierarchy?
Which action can be taken to immediately remediate the issue of application traffic with a valid use case triggering the decryption log message, "Received fatal alert UnknownCA from client"?
Which three actions can Panorama perform when deploying PAN-OS images to its managed devices? (Choose three.)
A network security administrator has been tasked with deploying User-ID in their organization.
What are three valid methods of collecting User-ID information in a network? (Choose three.)
Which administrative authentication method supports authorization by an external service?
Information Security is enforcing group-based policies by using security-event monitoring on Windows User-ID agents for IP-to-User mapping in the network. During the rollout, Information Security identified a gap for users authenticating to their VPN and wireless networks.
Root cause analysis showed that users were authenticating via RADIUS and that authentication events were not captured on the domain controllers that were being monitored Information Security found that authentication events existed on the Identity Management solution (IDM). There did not appear to be direct integration between PAN-OS and the IDM solution
How can Information Security extract and learn iP-to-user mapping information from authentication events for VPN and wireless users?
An administrator plans to deploy 15 firewalls to act as GlobalProtect gateways around the world. Panorama will manage the firewalls.
The firewalls will provide access to mobile users and act as edge locations to on-premises infrastructure. The administrator wants to scale the configuration out quickly and wants all of the firewalls to use the same template configuration.
Which two solutions can the administrator use to scale this configuration? (Choose two.)
After implementing a new NGFW, a firewall engineer sees a VoIP traffic issue going through the firewall After troubleshooting the engineer finds that the firewall performs NAT on the voice packets payload and opens dynamic pinholes for media ports
What can the engineer do to solve the VoIP traffic issue?
An administrator wants to configure the Palo Alto Networks Windows User-D agent to map IP addresses to u: ‘The company uses four Microsoft Active ‘servers and two Microsoft Exchange servers, which can provide logs for login events. All six servers have IP addresses assigned from the following subnet: 192.168.28.32/27. The Microsoft Active Directory in 192.168.28.22/128, and the Microsoft Exchange reside in 192,168.28 48/28. What the 0 the User
If a template stack is assigned to a device and the stack includes three templates with overlapping settings, which settings are published to the device when the template stack is pushed?
An administrator plans to install the Windows-Based User-ID Agent.
What type of Active Directory (AD) service account should the administrator use?
Which translated port number should be used when configuring a NAT rule for a transparent proxy?
Based on the images below, and with no configuration inside the Template Stack itself, what access will the device permit on its management port?
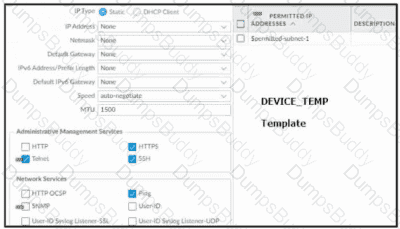
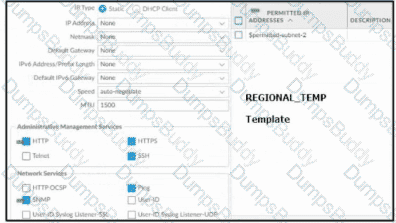

Refer to the exhibit.
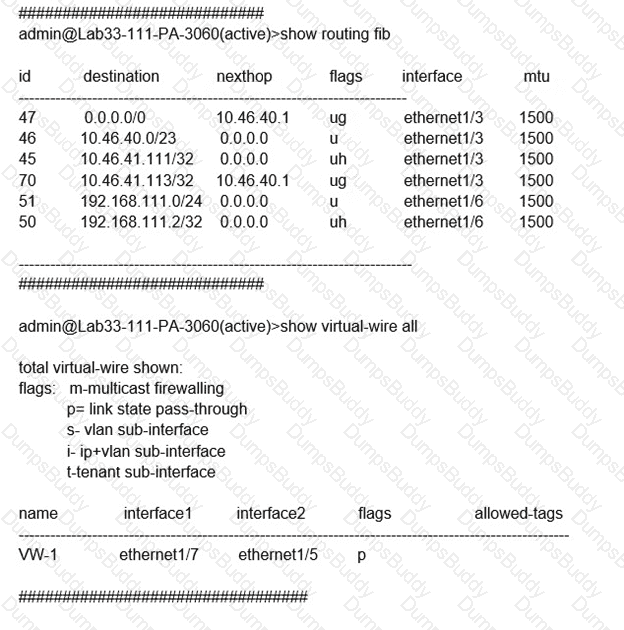
Which will be the egress interface if the traffic's ingress interface is ethernet1/7 sourcing from 192.168.111.3 and to the destination 10.46.41.113?
A standalone firewall with local objects and policies needs to be migrated into Panorama. What procedure should you use so Panorama is fully managing the firewall?
As a best practice, which URL category should you target first for SSL decryption?
In which two scenarios is it necessary to use Proxy IDs when configuring site-to-site VPN tunnels? (Choose two.)
SSL Forward Proxy decryption is configured, but the firewall uses Untrusted-CA to sign the website https://www.important-website.com certificate. End-users are receiving the "security certificate is not trusted" warning. Without SSL decryption, the web browser shows that the website certificate is trusted and signed by a well-known certificate chain Well-Known-Intermediate and Well-Known-Root-CA. The network security administrator who represents the customer requires the following two behaviors when SSL Forward Proxy is enabled:
End-users must not get the warning for the https://www.very-important-website.com/ website
End-users should get the warning for any other untrusted websiteWhich approach meets the two customer requirements?
Refer to the exhibit.
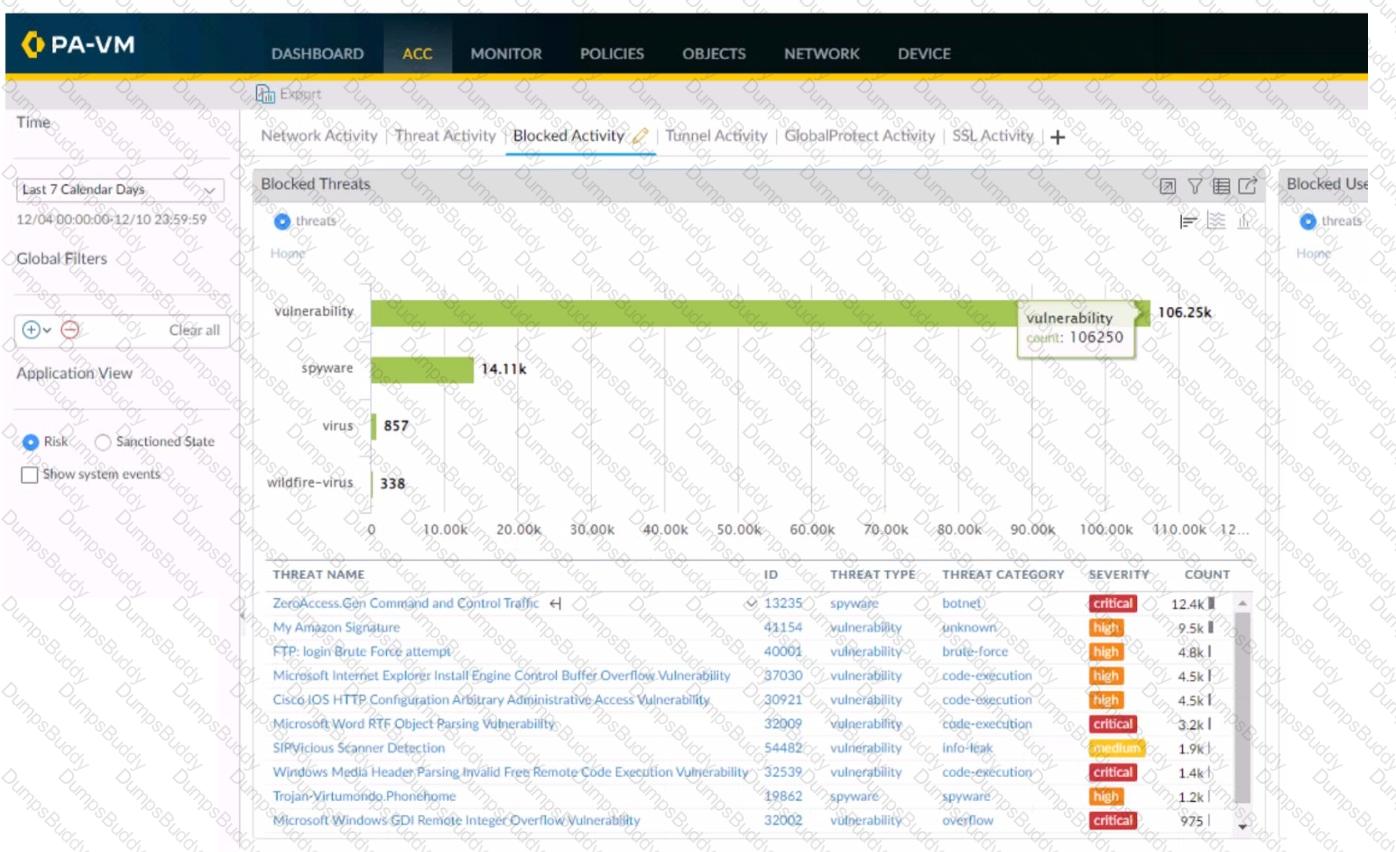
Using the above screenshot of the ACC, what is the best method to set a global filter, narrow down Blocked User Activity, and locate the user(s) that could be compromised by a botnet?
An administrator wants to enable WildFire inline machine learning. Which three file types does WildFire inline ML analyze? (Choose three.)
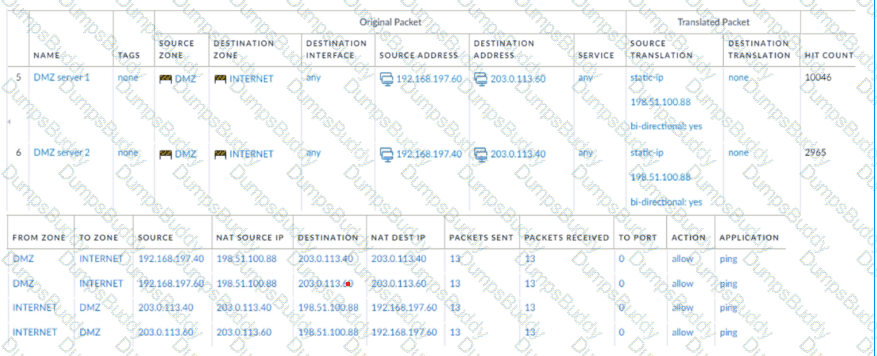
A new application server 192.168.197.40 has been deployed in the DMZ. There are no public IP addresses available resulting in the server sharing MAT IP 198 51 100 B8 with another OMZ serve that uses IP address 192 168 19? 60 Firewall security and NAT rules have been configured The application team has confirmed mat the new server is able to establish a secure connection to an external database with IP address 203.0.113.40. The database team reports that they are unable to establish a secure connection to 196 51 100 88 from 203.0.113.40 However it confirm a successful prig test to 198 51 100 88 Referring to the MAT configuration and traffic logs provided how can the firewall engineer resolve the situation and ensure inbound and outbound connections work concurrently for both DMZ servers?
A firewall administrator is changing a packet capture filter to troubleshoot a specific traffic flow Upon opening the newly created packet capture, the administrator still sees traffic for the previous fitter What can the administrator do to limit the captured traffic to the newly configured filter?
A company has configured a URL Filtering profile with override action on their firewall. Which two profiles are needed to complete the configuration? (Choose two)
A firewall engineer creates a NAT rule to translate IP address 1.1.1.10 to 192.168.1.10. The engineer also plans to enable DNS rewrite so that the firewall rewrites the IPv4 address in a DNS response based on the original destination IP address and translated destination IP address configured for the rule. The engineer wants the firewall to rewrite a DNS response of 1.1.1.10 to 192.168.1.10.
What should the engineer do to complete the configuration?
Forwarding of which two log types is configured in Device > Log Settings? (Choose two.)
Which two virtualization platforms officially support the deployment of Palo Alto Networks VM-Series firewalls? (Choose two.)
When configuring a GlobalProtect Portal, what is the purpose of specifying an Authentication Profile?
When creating a Policy-Based Forwarding (PBF) rule, which two components can be used? (Choose two.)
Which two actions can the administrative role called "vsysadmin" perform? (Choose two)
An engineer configures a specific service route in an environment with multiple virtual systems instead of using the inherited global service route configuration.
What type of service route can be used for this configuration?
Which type of zone will allow different virtual systems to communicate with each other?
An administrator is using Panorama to manage multiple firewalls. After upgrading all devices to the latest PAN-OS software, the administrator enables log forwarding from the firewalls to Panorama.
However, pre-existing logs from the firewalls are not appearing in Panorama.
Which action should be taken to enable the firewalls to send their pre-existing logs to Panorama?
An engineer needs to permit XML API access to a firewall for automation on a network segment that is routed through a Layer 3 sub-interface on a Palo Alto Networks firewall. However, this network segment cannot access the dedicated management interface due to the Security policy.
Without changing the existing access to the management interface, how can the engineer fulfill this request?
Which three external authentication services can the firewall use to authenticate admins into the Palo Alto Networks NGFW without creating administrator account on the firewall? (Choose three.)
An engineer needs to collect User-ID mappings from the company’s existing proxies. What two methods can be used to pull this data from third-party proxies? (Choose two)