Which license is required to use the Palo Alto Networks built-in IP address EDLs?
Which three types of Source NAT are available to users inside a NGFW? (Choose three.)
Which information is included in device state other than the local configuration?
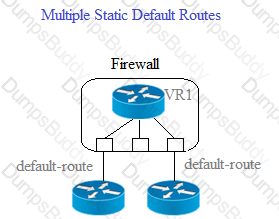
Given the scenario, which two statements are correct regarding multiple static default routes? (Choose two.)
An administrator has an IP address range in the external dynamic list and wants to create an exception for one specific IP address in this address range.
Which steps should the administrator take?
You receive notification about new malware that infects hosts through malicious files transferred by FTP.
Which Security profile detects and protects your internal networks from this threat after you update your firewall’s threat signature database?
Which two options does the firewall use to dynamically populate address group members? (Choose two.)
A network administrator creates an intrazone security policy rule on a NGFW. The source zones are set to IT. Finance, and HR.
To which two types of traffic will the rule apply? (Choose two.)
Which two rule types allow the administrator to modify the destination zone? (Choose two )
Which type of profile must be applied to the Security policy rule to protect against buffer overflows illegal code execution and other attempts to exploit system flaws?
How would a Security policy need to be written to allow outbound traffic using Secure Shell (SSH) to destination ports tcp/22 and tcp/4422?
After making multiple changes to the candidate configuration of a firewall, the administrator would like to start over with a candidate configuration that matches the running configuration.
Which command in Device > Setup > Operations would provide the most operationally efficient way to accomplish this?
Which type security policy rule would match traffic flowing between the inside zone and outside zone within the inside zone and within the outside zone?
Which URL profiling action does not generate a log entry when a user attempts to access that URL?
What allows a security administrator to preview the Security policy rules that match new application signatures?
Which administrative management services can be configured to access a management interface?
Prior to a maintenance-window activity, the administrator would like to make a backup of only the running configuration to an external location.
What command in Device > Setup > Operations would provide the most operationally efficient way to achieve this outcome?
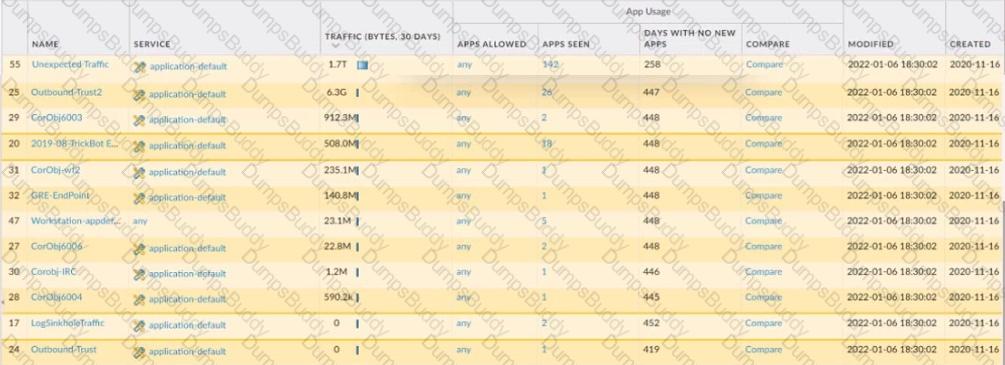
An administrator is updating Security policy to align with best practices.
Which Policy Optimizer feature is shown in the screenshot below?
An administrator creates a new Security policy rule to allow DNS traffic from the LAN to the DMZ zones. The administrator does not change the rule type from its default value.
What type of Security policy rule is created?
What must be configured for the firewall to access multiple authentication profiles for external services to authenticate a non-local account?
Which built-in IP address EDL would be useful for preventing traffic from IP addresses that are verified as unsafe based on WildFire analysis Unit 42 research and data gathered from telemetry?
What is the default action for the SYN Flood option within the DoS Protection profile?
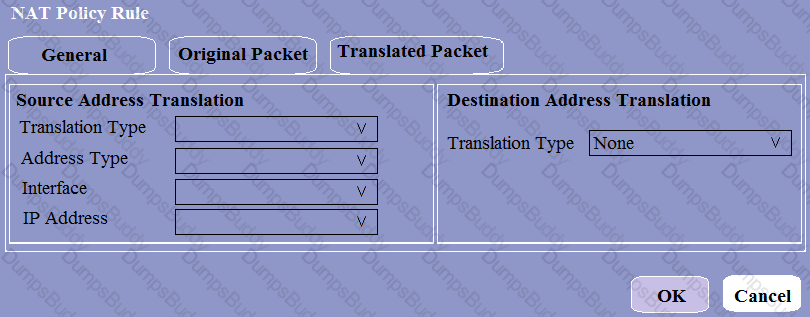
What does an administrator use to validate whether a session is matching an expected NAT policy?
When creating a Source NAT policy, which entry in the Translated Packet tab will display the options Dynamic IP and Port, Dynamic, Static IP, and None?
Which Security profile should be applied in order to protect against illegal code execution?
For the firewall to use Active Directory to authenticate users, which Server Profile is required in the Authentication Profile?
Which action can be set in a URL Filtering Security profile to provide users temporary access to all websites in a given category using a provided password?
An administrator configured a Security policy rule where the matching condition includes a single application and the action is set to deny. What deny action will the firewall perform?
Starting with PAN-OS version 9.1, application dependency information is now reported in which two locations? (Choose two.)
In which two Security Profiles can an action equal to the block IP feature be configured? (Choose two.)
What can be achieved by selecting a policy target prior to pushing policy rules from Panorama?
In order to attach an Antivirus, Anti-Spyware and Vulnerability Protection security profile to your Security Policy rules, which setting must be selected?
Which path is used to save and load a configuration with a Palo Alto Networks firewall?
An administrator wants to prevent access to media content websites that are risky
Which two URL categories should be combined in a custom URL category to accomplish this goal? (Choose two)
The PowerBall Lottery has reached a high payout amount and a company has decided to help employee morale by allowing employees to check the number, but doesn’t want to unblock the gambling URL category.
Which two methods will allow the employees to get to the PowerBall Lottery site without the company unlocking the gambling URL category? (Choose two.)
URL categories can be used as match criteria on which two policy types? (Choose two.)
Which action results in the firewall blocking network traffic with out notifying the sender?
Which three types of entries can be excluded from an external dynamic list (EDL)? (Choose three.)
A server-admin in the USERS-zone requires SSH-access to all possible servers in all current and future Public Cloud environments. All other required connections have already been enabled between the USERS- and the OUTSIDE-zone. What configuration-changes should the Firewall-admin make?
What are three valid source or D=destination conditions available as Security policy qualifiers? (Choose three.)
Which object would an administrator create to enable access to all applications in the office-programs subcategory?
Which user mapping method could be used to discover user IDs in an environment with multiple Windows domain controllers?
Which three interface deployment methods can be used to block traffic flowing through the Palo Alto Networks firewall? (Choose three.)
All users from the internal zone must be allowed only HTTP access to a server in the DMZ zone.
Complete the empty field in the Security policy using an application object to permit only this type of access.
Source Zone: Internal -
Destination Zone: DMZ Zone -
Application: __________
Service: application-default -
Action: allow
Which option lists the attributes that are selectable when setting up an Application filters?
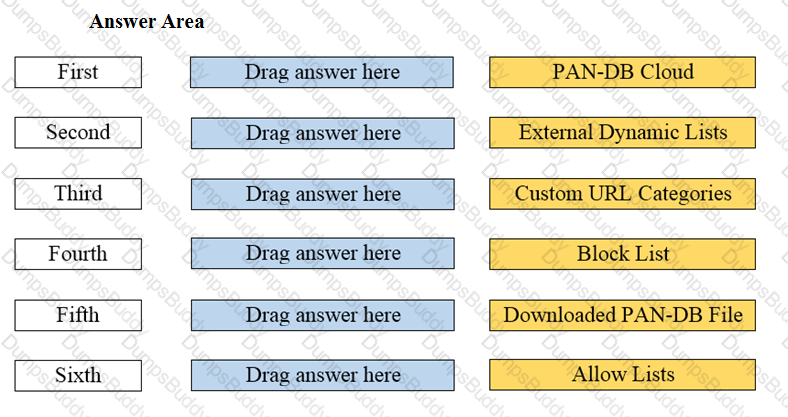
Arrange the correct order that the URL classifications are processed within the system.
Which CLI command will help confirm if FQDN objects are resolved in the event there is a shadow rule?
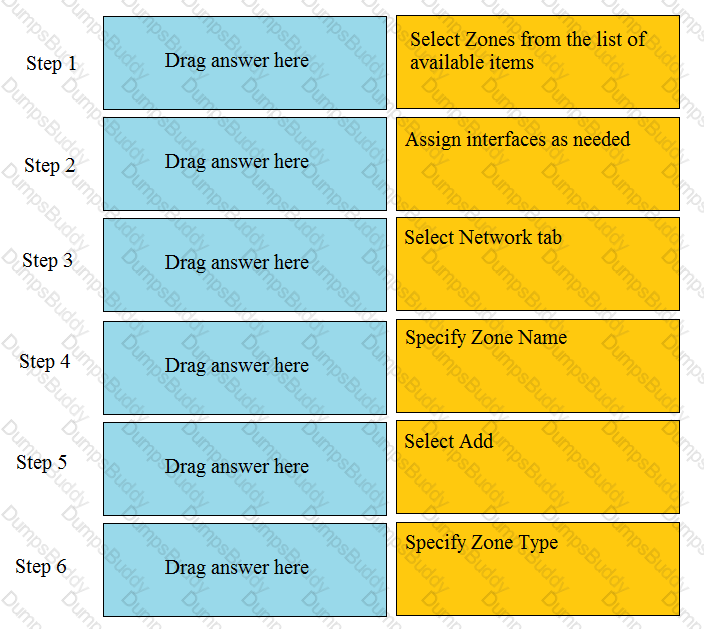
Order the steps needed to create a new security zone with a Palo Alto Networks firewall.
When HTTPS for management and GlobalProtect are enabled on the same data plane interface, which TCP port is used for management access?
An administrator needs to allow users to use their own office applications. How should the administrator configure the firewall to allow multiple applications in a dynamic environment?
A website is unexpectedly allowed due to miscategorization.
What are two way-s to resolve this issue for a proper response? (Choose two.)
Which Security profile must be added to Security policies to enable DNS Signatures to be checked?
A network has 10 domain controllers, multiple WAN links, and a network infrastructure with bandwidth needed to support mission-critical applications. Given the scenario, which type of User-ID agent is considered a best practice by Palo Alto Networks?
When a security rule is configured as Intrazone, which field cannot be changed?
What is considered best practice with regards to committing configuration changes?
Which table for NAT and NPTv6 (IPv6-to-IPv6 Network Prefix Translation) settings is available only on Panorama?
Actions can be set for which two items in a URL filtering security profile? (Choose two.)
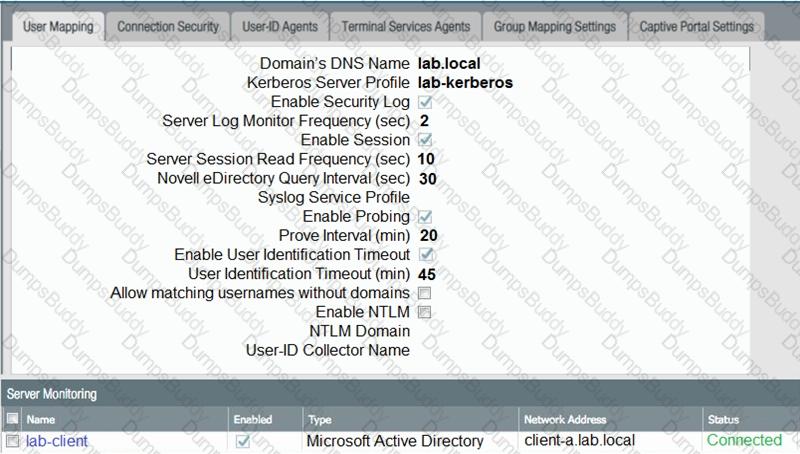
Based on the graphic which statement accurately describes the output shown in the server monitoring panel?
A network administrator is required to use a dynamic routing protocol for network connectivity.
Which three dynamic routing protocols are supported by the NGFW Virtual Router for this purpose? (Choose three.)
In a security policy what is the quickest way to rest all policy rule hit counters to zero?
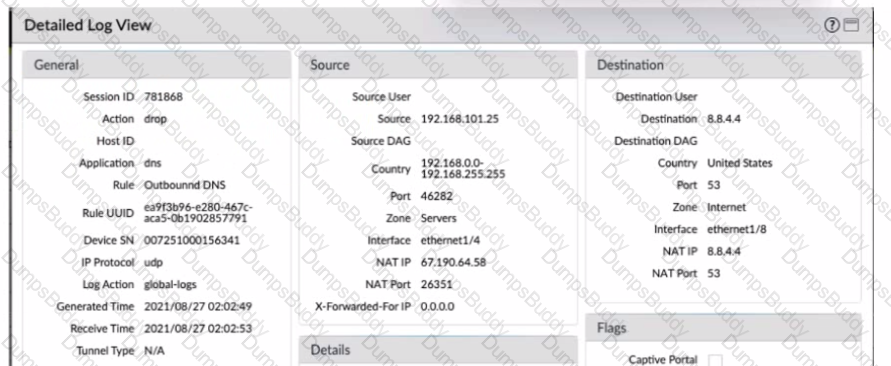
Given the detailed log information above, what was the result of the firewall traffic inspection?
What must first be created on the firewall for SAML authentication to be configured?
In the PAN-OS Web Interface, which is a session distribution method offered under NAT Translated Packet Tab to choose how the firewall assigns sessions?
Which three statement describe the operation of Security Policy rules or Security Profiles? (Choose three)
Which feature would be useful for preventing traffic from hosting providers that place few restrictions on content, whose services are frequently used by attackers to distribute illegal or unethical material?
Which User-ID mapping method should be used for an environment with clients that do not authenticate to Windows Active Directory?
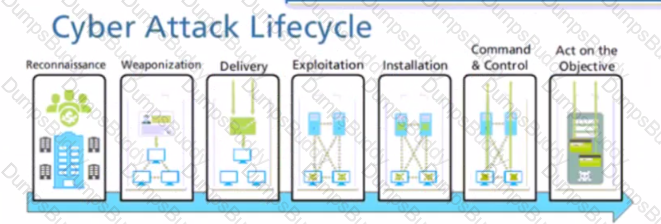
At which stage of the cyber-attack lifecycle would the attacker attach an infected PDF file to an email?
What is the minimum timeframe that can be set on the firewall to check for new WildFire signatures?
Why should a company have a File Blocking profile that is attached to a Security policy?
You receive notification about a new malware that infects hosts An infection results in the infected host attempting to contact a command-and-control server Which Security Profile when applied to outbound Security policy rules detects and prevents this threat from establishing a command-and-control connection?
Which action would an administrator take to ensure that a service object will be available only to the selected device group?
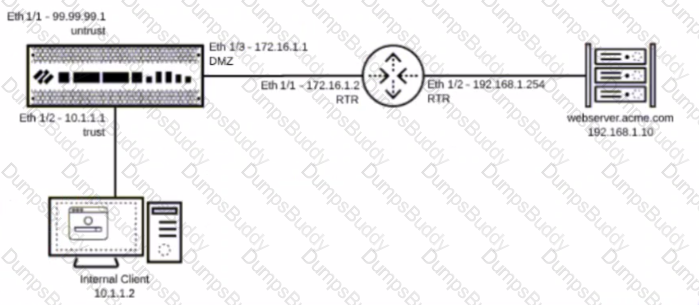
You have been tasked to configure access to a new web server located in the DMZ
Based on the diagram what configuration changes are required in the NGFW virtual router to route traffic from the 10 1 1 0/24 network to 192 168 1 0/24?
Which two firewall components enable you to configure SYN flood protection thresholds? (Choose two.)
Starting with PAN_OS version 9.1 which new type of object is supported for use within the user field of a security policy rule?
You receive notification about new malware that is being used to attack hosts The malware exploits a software bug in a common application
Which Security Profile detects and blocks access to this threat after you update the firewall's threat signature database?
Users from the internal zone need to be allowed to Telnet into a server in the DMZ zone.
Complete the security policy to ensure only Telnet is allowed.
Security Policy: Source Zone: Internal to DMZ Zone __________services “Application defaults”, and action = Allow
What are three characteristics of the Palo Alto Networks DNS Security service? (Choose three.)