NSK200 Netskope Certified Cloud Security Integrator (NCCSI) Questions and Answers
You have deployed Netskope Secure Web Gateway (SWG). Users are accessing new URLs that need to be allowed on a daily basis. As an SWG administrator, you are spending a lot of time updating Web policies. You want to automate this process without having to log into the Netskope tenant
Which solution would accomplish this task?
Recently your company implemented Zoom for collaboration purposes and you are attempting to inspect the traffic with Netskope. Your initial attempt reveals that you are not seeing traffic from the Zoom client that is used by all users. You must ensure that this traffic is visible to Netskope.
In this scenario, which two steps must be completed to satisfy this requirement? (Choose two.)
You are given an MD5 hash of a file suspected to be malware by your security incident response team. They ask you to offer insight into who has encountered this file and from where was the threat initiated. In which two Skope IT events tables would you search to find the answers to these questions? (Choose two.)
Your customer is concerned about malware in their AWS S3 buckets. What two actions would help with this scenario? (Choose two.)
Your learn is asked to Investigate which of the Netskope DLP policies are creating the most incidents. In this scenario, which two statements are true? (Choose two.)
Review the exhibit.
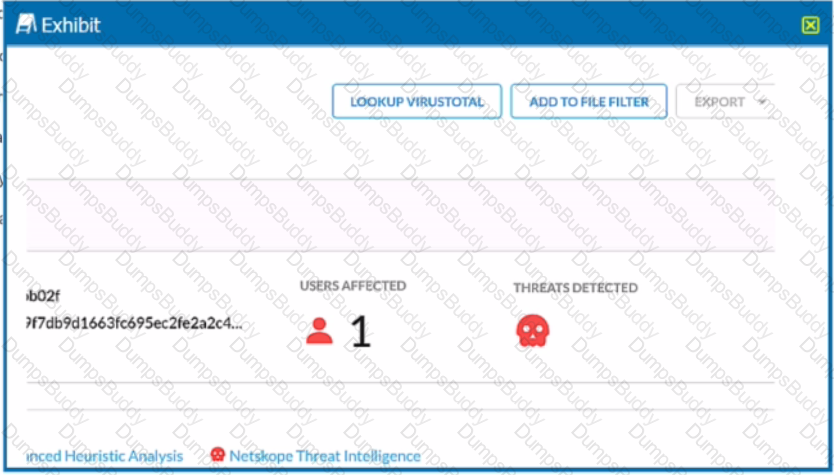
You are at the Malware Incident page. A virus was detected by the Netskope Heuristics Engine. Your security team has confirmed that the virus was a test data file You want to allow the security team to use this file
Referring to the exhibit, which two statements are correct? (Choose two.)
The risk team at your company has determined that traffic from the sales team to a custom Web application should not be inspected by Netskope. All other traffic to the Web application should continue to be inspected. In this scenario, how would you accomplish this task?
With Netskope DLP, which feature would be used to detect keywords such as "Confidential" or "Access key"?
Netskope support advised you to enable DTLS for belter performance. You added firewall rules to allow UDP port 443 traffic. These settings are part of which configuration element when enabled in the Netskope tenant?
Your company asks you to use Netskope to integrate with Endpoint Detection and Response (EDR) vendors such as CrowdStrike. In this scenario, what is a requirement for a successful Integration and sharing of threat data?
Review the exhibit.
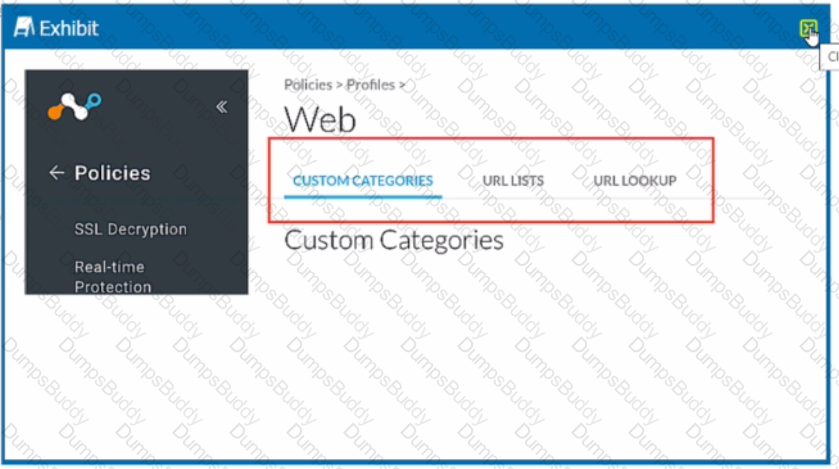
You want to create a custom URL category to apply a secure Web gateway policy combining your own list of URLs and Netskope predefined categories.
In this scenario, which task must be completed?
A customer wants to deploy the Netskope client on all their employee laptops to protect all Web traffic when users are working from home. However, users are required to work from their local offices at least one day per week. Management requests that users returning to the office be able to transparently leverage the local security stack without any user intervention.
Which two statements are correct in this scenario? (Choose two.)
You are using Skope IT to analyze and correlate a security incident. You are seeing too many events generated by API policies. You want to filter for logs generated by the Netskope client only.
Your organization has a homegrown cloud application. You are required to monitor the activities that users perform on this cloud application such as logins, views, and downloaded files. Unfortunately, it seems Netskope is unable to detect these activities by default.
How would you accomplish this goal?
You want to allow both the user identities and groups to be imported in the Netskope platform. Which two methods would satisfy this requirement? (Choose two.)
Your customer is using a virtual desktop infrastructure (VDI) for their support engineers. Multiple users will be logging into the same device, and they want to detect activities for each user.
Review the exhibit.
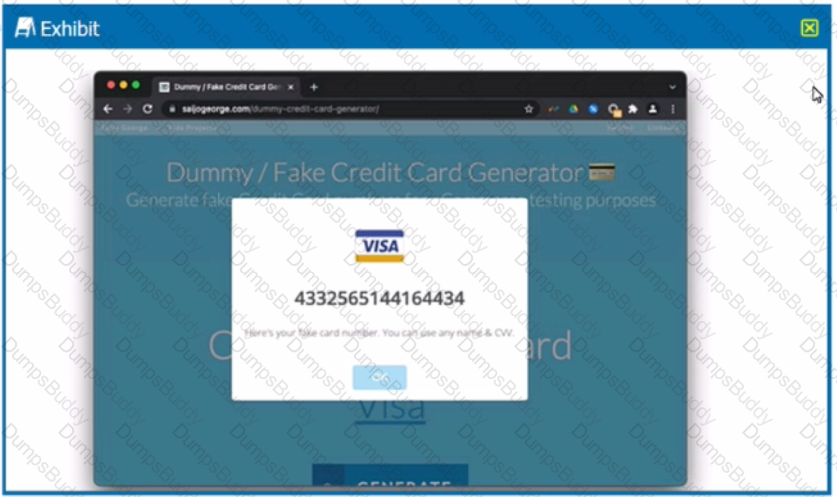
You are asked to create a DLP profile that will ensure that the data shown in the exhibit cannot be uploaded to a user's personal Google Drive.
What must be used to accomplish this task?
The director of IT asks for confirmation If your organization's Web traffic would be blocked when the Netskope client fails. In this situation, what would confirm the fail close status?
Review the exhibit.
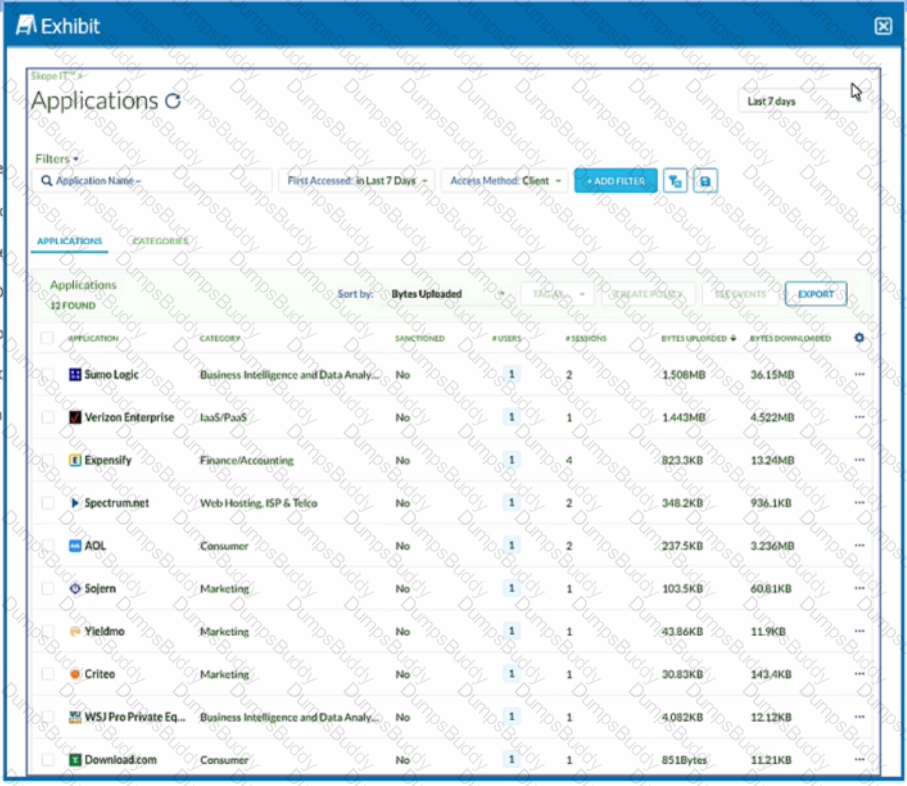
You want to discover new cloud applications in use within an organization.
Referring to the exhibit, which three methods would accomplish this task? (Choose three.)
Your IT organization is migrating its user directory services from Microsoft Active Directory to a cloud-based Identity Provider (IdP) solution, Azure AD. You are asked to adapt the Netskope user provisioning process to work with this new cloud-based IdP.
You want to reduce false positives by only triggering policies when contents of your customer database are uploaded to Dropbox. Your maximum database size is 2 MB. In this scenario, what are two ways to accomplish this task? (Choose two.)
Your company has many users that are remote and travel often. You want to provide the greatest visibility into their activities, even while traveling. Using Netskope. which deployment method would be used in this scenario?


