- Home
- MikroTik
- MTCNA - MikroTik Training
- MTCNA
- MikroTikCertified Network Associate Exam Questions and Answers
MTCNA MikroTikCertified Network Associate Exam Questions and Answers
The DoD model (also called the TCP/IP stack) has four layers. Which layer of the DoD model is equivalent to the Network layer of the OSI model?
Options:
Application
Host-to-Host
Internet
Network Access
Answer:
CExplanation:
The TCP/IP or DoD model includes the following layers:
Application
Host-to-Host
Internet
Network Access
The Internet layer in the DoD model is responsible for logical addressing and routing — matching the function of the OSI model's Layer 3 (Network Layer), which handles IP addressing and packet forwarding.
MTCNA Course Material – TCP/IP vs OSI Model:
“The Internet layer of the TCP/IP model maps directly to the OSI’s Network Layer and is responsible for logical addressing and routing.”
René Meneses MTCNA Study Guide – Layer Mapping Table:
“TCP/IP Internet Layer = OSI Network Layer. Handles IP routing, addressing.”
Other mappings:
Application = OSI Layers 5–7
Host-to-Host = OSI Layer 4 (Transport)
Network Access = OSI Layers 1–2
Final Answer: CQUESTION NO: 114 [RouterOS Introduction – ARP]
Which of the following allows a router to respond to an ARP request that is intended for a remote host?
A. Gateway DP
B. Reverse ARP (RARP)
C. Proxy ARP
D. Inverse ARP (IARP)
Answer: C
Proxy ARP allows a router to answer ARP requests on behalf of another device. It is often used in networks where hosts don't have proper default gateways but still need to communicate with devices in different subnets.
MTCNA Course Material – ARP Types:
“Proxy ARP allows a router to respond to an ARP request for an IP address that is not on the local subnet, effectively acting as a proxy.”
René Meneses MTCNA Guide – ARP Configuration:
“Proxy ARP is useful for bridging two IP networks or for clients that do not have default gateways defined.”
MikroTik Wiki – ARP Modes:
“When Proxy ARP is enabled, the router replies to ARP requests for hosts that are not on the same subnet.”
Other options:
A: Gateway DP is not a standard term or protocol.
B: RARP maps MAC to IP — outdated and not used in this context.
D: Inverse ARP is used in Frame Relay, not Ethernet/IP networks.
Final Answer: CQUESTION NO: 115 [DHCP]
You want to implement a mechanism that automates the IP configuration, including IP address, subnet mask, default gateway, and DNS information. Which protocol will you use to accomplish this?
A. SMTP
B. SNMP
C. DHCP
D. ARP
Answer: C
DHCP (Dynamic Host Configuration Protocol) is specifically designed to assign IP configuration details automatically to clients on a network, including:
IP address
Subnet mask
Default gateway
DNS servers
MTCNA Course Material – DHCP Server Function:
“DHCP is a service that dynamically assigns IP settings to clients, removing the need for manual configuration.”
René Meneses MTCNA Study Guide – DHCP Operation:
“DHCP provides automatic configuration of network parameters including IP, mask, DNS, and gateway.”
Other options:
A: SMTP is for email
B: SNMP is for monitoring
D: ARP resolves IP-to-MAC addresses
Final Answer: CQUESTION NO: 116 [DHCP]
Which of the following describe the DHCP Discover message?
It uses FF:FF:FF:FF:FF:FF as a layer 2 broadcast.
It uses UDP as the Transport layer protocol.
It uses TCP as the Transport layer protocol.
It does not use a layer 2 destination address.
A. 1 only
B. 1 and 2
C. 3 and 4
D. 4 only
Answer: B
When a client sends a DHCP Discover message:
It does not yet have an IP address, so it sends a Layer 2 broadcast (FF:FF:FF:FF:FF:FF).
DHCP uses UDP, not TCP.
Specifically, it uses UDP port 67 (server) and 68 (client).
Layer 2 destination is broadcast — it certainly does use a Layer 2 address.
MTCNA Course Material – DHCP Process:
“The client broadcasts a DHCP Discover message to FF:FF:FF:FF:FF:FF using UDP ports 67 and 68.”
René Meneses MTCNA Study Guide – DHCP Message Types:
“DHCP uses UDP. Discovery messages are Layer 2 broadcasts to locate a DHCP server.”
MikroTik Wiki – DHCP Protocol Behavior:
“The Discover message uses UDP and broadcast MAC addressing.”
Statements:
1: True (Layer 2 broadcast)
2: True (Uses UDP)
3: False (TCP not used)
4: False (Layer 2 destination address is broadcast)
────────────────────────────────────────────────────────────
Mark all packages required for PPPoE server on MikroTik RouterOS
Options:
ppp
user-manager
radius
synchronous
system
Answer:
A, EExplanation:
The PPPoE server functionality in RouterOS relies primarily on the PPP package, which includes support for protocols like PPP, PPPoE, PPTP, L2TP, SSTP, etc. The system package is also always required, as it contains the core OS components.
Option breakdown:
A.✔ppp – Required. Contains all PPP and PPPoE server/client implementations.
B.✘user-manager – Optional. Used for advanced AAA (authentication/accounting), not required for basic PPPoE.
C.✘radius – Optional. Used for external authentication, not essential unless RADIUS integration is needed.
D.✘synchronous – Used for legacy synchronous interfaces (e.g., serial or modem), not for PPPoE.
E.✔system – Required for all RouterOS functions.
Extract from Official MTCNA Course Material – RouterOS Packages:
“To enable PPPoE server functionality, you need the ppp and system packages. Radius and User Manager are optional.”
Extract from René Meneses MTCNA Study Guide – PPPoE Deployment:
“Only the ppp and system packages are strictly required. Additional features like radius are for centralized authentication.”
Extract from MikroTik Wiki – RouterOS Package Descriptions:
“ppp: required for PPP, PPTP, L2TP, PPPoE; system: required core package. user-manager and radius are optional.”
===========
What protocol does ping use?
Options:
TCP
ARP
UDP
ICMP
Answer:
DExplanation:
Ping is a network diagnostic tool used to test the reachability of a host and measure round-trip time for packets. It uses the Internet Control Message Protocol (ICMP), not TCP or UDP.
ICMP is a Layer 3 protocol designed for diagnostics and control messaging. Ping sends ICMP Echo Request packets and waits for ICMP Echo Reply packets.
Evaluation:
A. TCP → Used for reliable data transmission, not for ping.
B. ARP → Resolves MAC addresses on LANs; unrelated to ping.
C. UDP → Used for connectionless communication; ping does not use it.
D. ICMP → Correct. Protocol used by ping.✅
Extract from MTCNA Official Training Slides – Tools Section:
“Ping sends ICMP Echo Request messages to the target IP address and expects Echo Reply messages. ICMP is a protocol used for diagnostic purposes.”
René Meneses Study Guide – Diagnostic Tools:
“Ping is based on ICMP, which is part of Layer 3. It’s used for checking connectivity and response times.”
Terry Combs Notes – Common Tools:
“Ping = ICMP. Always. No TCP/UDP involved.”
===========
What is the address range of a Class B network address in binary?
Options:
01xxxxxx
0xxxxxxx
10xxxxxx
110xxxxx
Answer:
CExplanation:
IPv4 Class B addresses have their first two bits as 10 in binary. The range for Class B starts at 128.0.0.0 and goes up to 191.255.255.255, which in binary representation begins with 10xxxxxx.
MTCNA Course Material – IP Addressing and Classes:
“Class B IP addresses are identified by the first two bits being 10. This corresponds to IP addresses from 128.0.0.0 to 191.255.255.255.”
René Meneses MTCNA Study Guide – Address Classes:
“Class B: 128.0.0.0 – 191.255.255.255. Binary pattern: 10xxxxxx.”
Terry Combs MTCNA Notes – IP Addressing:
“The first octet of a Class B address starts with binary 10, followed by 6 variable bits.”
Other options:
A. 01xxxxxx: incorrect (used for experimental/reserved ranges)
B. 0xxxxxxx: represents Class A
D. 110xxxxx: indicates Class C
Final Answer: CQUESTION NO: 102 [RouterOS Introduction – Protocols]
Which of the following protocols uses both TCP and UDP?
A. FTP
B. SMTP
C. Telnet
D. DNS
Answer: D
DNS (Domain Name System) can use both UDP and TCP. Typically:
UDP port 53 is used for standard DNS queries due to its lower overhead.
TCP port 53 is used for DNS zone transfers and when DNS responses exceed the UDP packet size (e.g., DNSSEC).
MTCNA Course Material – Protocol Overview:
“DNS uses UDP port 53 for standard queries and TCP port 53 for zone transfers or large responses.”
René Meneses MTCNA Study Guide – Protocol Functions:
“DNS can operate over UDP and TCP. UDP is faster and used for most lookups. TCP is used when the payload is too large or for zone transfers.”
MikroTik Wiki – DNS Protocols:
“DNS primarily uses UDP 53. For zone transfers (AXFR), TCP 53 is used.”
Other options:
A. FTP uses TCP (ports 20/21)
B. SMTP uses TCP (port 25)
C. Telnet uses TCP (port 23)
Only DNS uses both TCP and UDP.
Final Answer: DQUESTION NO: 103 [RouterOS Introduction – IP Fundamentals]
What protocol is used to find the hardware address of a local device?
A. RARP
B. ARP
C. IP
D. ICMP
Answer: B
ARP (Address Resolution Protocol) is used to resolve IP addresses to MAC (hardware) addresses on a local network.
MTCNA Course Material – ARP & Layer 2 Communication:
“ARP translates an IP address to a MAC address on local networks. It is necessary for IP communication within a broadcast domain.”
René Meneses MTCNA Study Guide – ARP Explanation:
“When sending to a local IP, the host first uses ARP to determine the hardware address. This is done through broadcast ARP requests.”
MikroTik Wiki – ARP Functionality:
“RouterOS uses ARP to associate IP addresses with hardware (MAC) addresses in the LAN.”
Other options:
A. RARP is Reverse ARP, outdated and rarely used.
C. IP is the higher-layer addressing protocol.
D. ICMP is used for ping and diagnostics.
Only ARP (Option B) is correct.
Final Answer: BQUESTION NO: 104 [RouterOS Introduction]
Which of the following are TCP/IP protocols used at the Application layer of the OSI model?
IP
TCP
Telnet
FTP
TFTP
A. 1 and 3
B. 1, 3 and 5
C. 3, 4 and 5
D. All of the above
Answer: C
In the OSI model:
Application layer protocols include Telnet, FTP, and TFTP.
IP is a Network Layer (Layer 3) protocol.
TCP is a Transport Layer (Layer 4) protocol.
MTCNA Course Material – OSI Model and Protocols:
“Application layer protocols provide services to user applications. Examples include FTP, TFTP, Telnet. TCP and IP operate at lower layers.”
René Meneses MTCNA Study Guide – TCP/IP Stack:
“Telnet, FTP, and TFTP are Application layer protocols. IP belongs to Layer 3. TCP is at Layer 4.”
Terry Combs MTCNA Notes – OSI Reference Model:
“Layer 7 (Application): FTP, HTTP, Telnet, TFTP.
Layer 4: TCP, UDP
Layer 3: IP”
Only Options 3 (Telnet), 4 (FTP), and 5 (TFTP) are Application layer protocols.
────────────────────────────────────────────────────────────
Using wireless connect-list it’s possible to prioritize connection to one Access Point over another Access Point by changing the order of the entries.
Options:
False
True
Answer:
BExplanation:
The connect-list in RouterOS is used to define rules for wireless client behavior when connecting to available Access Points. You can define multiple entries in the connect-list, and RouterOS processes them in top-down order. This allows prioritization of APs based on criteria such as SSID, signal strength, and MAC address.
MTCNA Course Material – Wireless Client Settings:
“The connect-list determines the order in which the wireless client will try to associate with Access Points. Entries are processed from top to bottom, allowing prioritized connection attempts.”
René Meneses MTCNA Study Guide – Wireless & Connect-List Section:
“By placing the most preferred AP at the top of the connect-list, you ensure it is attempted first. Reordering entries is used to manage roaming behavior and priority.”
MikroTik Wiki – Wireless Client & Connect List:
“The client will attempt to connect to the first matching entry in the connect list. This means the connect list can be used to define AP priorities.”
Therefore, the statement is true.
Final Answer: BQUESTION NO: 98 [Hotspot]
What configuration is added by /ip Hot-Spot setup command? (Select all that apply)
A. /ip service
B. /ip Hot-Spot user
C. /ip Hot-Spot walled-garden
D. /ip dhcp-server
E. /queue tree
Answer: B, C, D
The /ip hotspot setup command is a wizard used to quickly deploy a HotSpot service on a selected interface. It automatically creates several configurations necessary for a functional HotSpot environment:
Creates a default user in /ip hotspot user
Adds entries in /ip hotspot walled-garden to allow access to login page
Configures a DHCP server on the selected interface if not present
MTCNA Course Material – HotSpot Setup Wizard:
“The hotspot setup creates a user, configures a DHCP server, and sets up walled garden entries. It does not touch system services or create queue trees by default.”
René Meneses MTCNA Guide – HotSpot Setup Section:
“After running hotspot setup, you will find new configurations in /ip hotspot user, /ip hotspot walled-garden, and /ip dhcp-server. The system automatically assigns IP pools and login pages.”
MikroTik Wiki – HotSpot Setup Overview:
“The setup creates a DHCP server, login page, user entry, and basic NAT and walled garden rules.”
Option A: /ip service is unrelated
Option E: /queue tree is not configured by the setup wizard
Final Answer: B, C, DQUESTION NO: 99 [PPP]
What kind of users are listed in the Secrets window of the PPP menu?
A. Hot-Spot users
B. wireless users
C. l2tp users
D. pptp users
E. pppoe users
F. winbox users
Answer: C, D, E
The /ppp secret menu is used in RouterOS to manage usernames and passwords for Point-to-Point Protocol (PPP) based services, including:
PPPoE (Point-to-Point Protocol over Ethernet)
PPTP (Point-to-Point Tunneling Protocol)
L2TP (Layer 2 Tunneling Protocol)
It does not include HotSpot users, wireless clients, or Winbox users.
MTCNA Course Material – PPP User Authentication:
“The PPP secret database stores credentials for services like PPPoE, PPTP, and L2TP.”
René Meneses MTCNA Study Guide – PPP Configuration Section:
“Users for PPP-based protocols are configured under PPP → Secrets. This includes PPPoE, PPTP, and L2TP.”
MikroTik Wiki – PPP Secrets Window:
“Secrets are used to authenticate users for all PPP interfaces. HotSpot users are managed separately under /ip hotspot user.”
Option A: HotSpot users → /ip hotspot user
Option B: Wireless users connect via WPA/802.11 — not listed in PPP
Option F: Winbox users refer to /user under system user management
Final Answer: C, D, EQUESTION NO: 100 [RouterOS Introduction]
Select valid MAC-address:
A. G2:60:CF:21:99:H0
B. 00:00:5E:80:EE:B0
C. AEC8:21F1:AA44:54FF:1111:DDAE:0212:1201
D. 192.168.0.0/16
Answer: B
A valid MAC address must meet the following criteria:
Be 6 bytes (48 bits) in length
Consist of only hexadecimal digits (0–9, A–F)
Written in six groups separated by colons or hyphens (e.g., 00:1A:2B:3C:4D:5E)
MTCNA Course Material – RouterOS MAC Address Basics:
“MAC addresses are 48-bit identifiers written as six pairs of hexadecimal digits. Invalid characters or incorrect length disqualifies an address.”
René Meneses MTCNA Guide – MAC Addressing Section:
“Each MAC is made up of 12 hexadecimal characters (6 octets). If a character like ‘G’ appears, or if it’s longer than 6 bytes, it is invalid.”
MikroTik Wiki – MAC Addressing Rules:
“Valid MAC format: XX:XX:XX:XX:XX:XX using only 0-9 and A-F. 192.168.0.0/16 is an IP subnet, not a MAC.”
Option A: Invalid — “G” and “H” are not hexadecimal characters
Option B: Valid — proper format and hex content
Option C: Invalid — Too long (appears to be IPv6 or malformed)
Option D: Invalid — this is an IP network (CIDR notation), not a MAC
Only Option B is correct.
What does this simple queue do (check the image)?
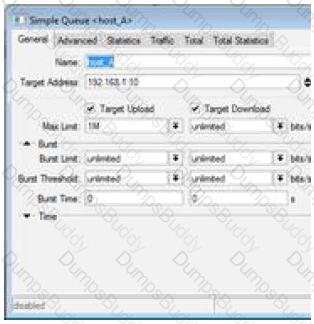
The screenshot shows a Simple Queue named "host_A" with:
Target Address: 192.168.1.10
Target Upload: Checked
Target Download: Checked
Max Limit: 1M (upload), unlimited (download)
Options:
Queue guarantees upload data rate of one megabit per second for host 192.168.1.10
Queue limits host 192.168.1.10 download data rate to one megabit per second.
Queue limits host 192.168.1.10 upload data rate to one megabit per second.
Queue guarantees download data rate of one megabit per second for host 192.168.1.10
Answer:
CExplanation:
The “Max Limit” value in MikroTik Simple Queues defines the maximum allowed bandwidth. In this case:
Target Address: 192.168.1.10
Target Upload = 1M → The host can upload at a maximum of 1 Mbps
Target Download = unlimited → No restriction on download
This does not “guarantee” bandwidth — it enforces a ceiling. A guaranteed rate would require "Limit-at" to be set.
Evaluation:
A.❌This queue limits, it does not guarantee a minimum bandwidth.
B.❌Download is set to unlimited — no limitation.
C.✅Upload is limited to 1 Mbps — correct.
D.❌Download rate is unlimited — no guarantee or limit.
MTCNA Course Manual – Simple Queue Explanation:
“Max-limit sets the maximum throughput for upload/download. It’s a ceiling, not a guarantee.”
René Meneses Guide – Simple Queues Explained:
“In this case, upload is capped at 1M. No burst or download limit is applied.”
Terry Combs Notes – Queue Properties:
“Always distinguish between 'limit-at' (minimum guarantee) and 'max-limit' (maximum cap).”
Action=redirect is applied in:
Options:
chain=srcnat
chain=forward
chain=dstnat
Answer:
CExplanation:
The redirect action is only valid in the dstnat chain. It is used to redirect traffic to a service running on the router itself (e.g., redirecting HTTP to a local proxy server).
A.✘srcnat – Not compatible with redirect
B.✘forward – Redirect doesn’t apply in this chain
C.✔dstnat – This is the correct and only supported chain for action=redirect
Extract from Official MTCNA Course Material – NAT Actions:
“The redirect action is used within the dstnat chain to forward packets to the router’s local services.”
Extract from MikroTik Wiki – NAT Rule Actions:
“Redirect is used in dstnat chain and changes destination address to a local router IP and port.”
===========
What is the default protocol/port of (secure) winbox?
Options:
UDP/5678
TCP/22
TCP/8291
TCP/8080
Answer:
CExplanation:
Winbox is the graphical configuration utility for MikroTik routers. By default, Winbox connects to RouterOS over TCP port 8291.
A.✘UDP/5678 – Used for Winbox neighbor discovery, not for connecting.
B.✘TCP/22 – SSH service.
C.✔TCP/8291 – Default and official port for Winbox connections.
D.✘TCP/8080 – Often used for HTTP proxy; unrelated to Winbox.
Extract from MTCNA Course Material – RouterOS Access Methods:
“Winbox uses TCP port 8291 to establish connections to RouterOS.”
Extract from René Meneses MTCNA Study Guide – Access Tools:
“Winbox connects via TCP 8291. Neighbor discovery uses UDP 5678.”
Extract from MikroTik Wiki – Winbox Port Info:
“TCP/8291 is the default port for Winbox. Ensure it is not blocked by firewall.”
Evaluate the following information:
Access Point configuration:
-- wlan1 is in 'AP-Bridge' mode
-- Bridge1 has wlan1 and ether1 as ports
CPE configuration:
-- wlan1 is in 'Station-Bridge' mode
-- Bridge1 has wlan1 and ether1 as ports
Select protocols that will pass from ether1 on the CPE to ether1 on the Access Point:
Options:
IPv4
ARP
USB
BGP
Firewire
IPv6
DHCP
Answer:
A, B, D, F, G, HExplanation:
In this configuration, the wireless interface (wlan1) on the AP is in ap-bridge mode, and on the CPE it's in station-bridge mode. This mode allows full Layer 2 bridging over wireless, supporting all Ethernet-based protocols and services, including:
IPv4, IPv6, DHCP, ARP, PPPoE, and routing protocols like BGP (which use TCP/IP).
Protocols like USB or Firewire are hardware-level or local bus protocols and cannot be transmitted over Ethernet frames or wireless.
Option Review:
A.✔IPv4 – supported
B.✔ARP – Layer 2 protocol, supported
C.✘USB – not a network protocol, not transmitted over bridges
D.✔BGP – Layer 3 protocol, supported over bridged links
E.✘Firewire – not a Layer 2 or network protocol
F.✔IPv6 – fully supported
G.✔DHCP – Layer 3 broadcast protocol, works over bridges
H.✔PPPoE – Ethernet-based protocol, passes over Layer 2 bridge
Extract from Official MTCNA Course Material – Wireless Bridging:
“station-bridge mode allows transparent Layer 2 bridging, supporting all Ethernet protocols including IPv4, IPv6, ARP, DHCP, PPPoE, and more.”
Extract from René Meneses MTCNA Study Guide – Wireless Modes:
“Use station-bridge with ap-bridge to pass full Layer 2 traffic. This allows DHCP, PPPoE, and other protocols to work transparently.”
Extract from MikroTik Wiki – Station Bridge:
“station-bridge mode is used with MikroTik-only links and allows full Layer 2 protocol support, including dynamic IP assignments and bridging.”
Which firewall chain would be used to block a client's MSN traffic on a router?
Options:
static
forward
output
input
Answer:
BExplanation:
To block a client’s application traffic (like MSN Messenger) that is passing through the router (from LAN to WAN or vice versa), the forward chain must be used. This chain processes packets that are routed through the router.
Evaluation:
A. static →❌Not a valid firewall chain.
B.✅forward → Correct – used to filter traffic that passes through the router.
C.❌output → Filters traffic originating from the router itself.
D.❌input → Filters traffic destined for the router itself.
MTCNA Firewall Section – Chain Descriptions:
“forward – Used for filtering transit traffic (client to internet or internet to client).”
René Meneses Guide – Firewall Chains:
“To block client application traffic, use the forward chain. Input/output are for local router access.”
Terry Combs Notes – Chain Matching:
“forward = traffic passing through router, like client web or chat traffic.”
Answer: BQUESTION NO: 71 [Routing]
There are two routes in the routing table:
0 dst-addr=10.1.1.0/24 gateway=5.5.5.5
1 dst-addr=10.1.1.4/30 gateway=5.6.6.6
Which gateway will be used to get to the IP address 10.1.1.6?
A. both – half of the traffic will be routed through one gateway, half through the other
B. 5.5.5.5
C. the required route is not in the routing table
D. 5.6.6.6
Answer: D
Routing decisions are made based on the longest prefix match (most specific route).
10.1.1.6 falls within:→ 10.1.1.0/24 → range: 10.1.1.0 – 10.1.1.255 (prefix length: 24)→ 10.1.1.4/30 → range: 10.1.1.4 – 10.1.1.7 (prefix length: 30)
Because /30 is more specific than /24, it will be selected for routing the packet.
MTCNA Routing Module – Prefix Length Decision:
“Router chooses the route with the longest subnet mask (most specific match).”
René Meneses Study Guide – Longest Match Principle:
“10.1.1.6 falls within 10.1.1.4/30 → use gateway 5.6.6.6.”
Terry Combs Notes – Routing Table Resolution:
“Always check if multiple routes match. Use the one with the longest prefix.”
Answer: DQUESTION NO: 72 [Wireless Security]
In order to use dynamic keys in your wireless security profile for an AP, you MUST set up the DHCP server to provide the dynamic keys.
A. true
B. false
Answer: B
MikroTik RouterOS supports dynamic key exchange for wireless networks using WPA/WPA2 (with PSK or EAP). These dynamic keys are not provided by the DHCP server but are instead part of the wireless security profile configured under /interface wireless security-profiles.
DHCP only assigns IP addresses and other network configuration parameters — it does not provide encryption keys.
MTCNA Wireless Security Module – WPA/WPA2 Explained:
“Dynamic keys are negotiated during the WPA/WPA2 authentication process, not via DHCP.”
René Meneses Guide – Wireless Authentication:
“Security profiles define pre-shared or dynamic key exchange (WPA-EAP). DHCP is unrelated.”
Terry Combs Notes – Misconceptions in Wireless Setup:
“DHCP and wireless encryption are separate layers. Keys are not assigned through DHCP.”
Answer: BQUESTION NO: 73 [Firewall / Security]
Which firewall chain should you use to filter SSH access to the router itself?
A. output
B. input
C. prerouting
D. forward
Answer: B
SSH access to the router targets the router itself. Therefore, any packets destined for the router (for example, to TCP port 22) are evaluated in the input chain of the firewall.
Evaluation:
A. output →❌For packets originating from the router, not to it.
B.✅input → Correct – handles traffic destined for the router (like SSH, Winbox, etc.)
C.❌prerouting → Used for NAT and mangle operations, not filtering
D.❌forward → Used for traffic routed through the router (not for router itself)
MTCNA Firewall Section – Chain Functions:
“SSH access to the router is incoming traffic. Use input chain to filter or allow it.”
René Meneses Guide – Access Protection:
“input chain is responsible for traffic to the router’s IP – block/allow SSH, Winbox, etc.”
Terry Combs Notes – Firewall Management:
“Always use input chain for filtering incoming management protocols like SSH.”
A client uses a RouterBOARD1000. The clock is configured in '/system clock'. The clock resets to default after each reboot.
Select the best solution for the problem.
Options:
Write a script in '/system script' to set the clock
Configure '/system ntp server' and set a valid and reachable NTP client address
Configure '/system ntp client' and set a valid and reachable NTP server address
Open the router and ensure the CMOS battery is fine
Answer:
CExplanation:
RouterBOARD devices (such as RB1000) typically do not have a battery-backed hardware clock (RTC). This means the system time resets after each reboot. To keep time accurate, you must configure the router to synchronize with an external NTP (Network Time Protocol) server.
A.✘Inefficient and non-scalable solution.
B.✘The /system ntp server is used to act as an NTP server for others — not for receiving time.
C.✔Correct – You must enable /system ntp client and point to a reachable NTP server to get the correct time on boot.
D.✘Irrelevant – RouterBOARDs do not have CMOS batteries for timekeeping like traditional PCs.
Extract from MTCNA Course Material – Time Synchronization:
“To maintain correct system time, configure NTP client to sync with a public or internal time server after reboot.”
Extract from René Meneses Study Guide – Clock and Scheduler:
“RouterBOARD devices don’t have battery-backed RTC. Use the NTP client to update time after reboot.”
Extract from MikroTik Wiki – NTP Setup:
“Use /system ntp client to sync time. /system clock alone will reset on reboot without NTP.”
===========
Consider the following diagram. We want to communicate from a device on LAN1 (192.168.0.0/24) to a device on LAN2 (192.168.1.0/24). Assuming that all necessary configurations are already included on R2, which of the following configurations in R1 would enable this communication?

Options:
/ip route add dst-address=192.168.1.0/24 src-address=192.168.0.0/24 gateway=192.168.99.2
/ip route add dst-address=0.0.0.0/0 gateway=Ether1
/ip route add dst-address=192.168.0.0/24 gateway=192.168.0.1
/ip route add dst-address=192.168.1.0/24 gateway=192.168.99.2
/ip route add dst-address=0.0.0.0/0 gateway=192.168.99.2
Answer:
DExplanation:
To route traffic from LAN1 (192.168.0.0/24) behind R1 to LAN2 (192.168.1.0/24) behind R2, R1 must know how to reach the destination network 192.168.1.0/24. The proper way is to add a static route on R1 pointing to the next hop IP address of R2’s interface (192.168.99.2) connected via their shared transit network (192.168.99.0/24).
According to:
René Meneses MTCNA Study Guide – Routing Section:
“A static route requires the destination prefix and the gateway (next-hop) IP address. The gateway should be reachable through a directly connected network interface.”
Terry Combs MTCNA Notes – Static Routing Example:
“To route packets to a remote network, configure a static route specifying the destination network (e.g., 192.168.50.0/24) and the gateway IP (e.g., 10.0.0.2). Ensure that the gateway is reachable via a locally connected interface.”
MikroTik Wiki – Static Routing:
“The most common usage of static routes is to forward packets for destination networks that are not directly connected. You must use the IP address of a reachable next-hop router.”
Option A incorrectly includes src-address, which is not part of a standard /ip route syntax.
Option B uses “Ether1” as a gateway, which is syntactically invalid unless using recursive routing, which this situation does not require.
Option C adds a route back to the local network — unnecessary and incorrect.
Option E routes all traffic to R2, which is inefficient and not specific.
Thus, only Option D adds the correct static route:
/ip route add dst-address=192.168.1.0/24 gateway=192.168.99.2
Final Answer: DQUESTION NO: 83 [Bridging]
For a Simple Queue to apply bandwidth restrictions on a bridged interface, the following must be done:
A. Configure an IP address on the bridge interface
B. Use mangle to mark the connections
C. Associate the Simple Queue to the bridge interface
D. Enable 'Use IP Firewall' in bridge settings
Answer: D
By default, RouterOS does not pass traffic on a bridge interface through the firewall or queue system. If you want to apply queueing (Simple Queues or other policies) on a bridge interface, you must enable the bridge to use the IP Firewall.
MTCNA Official Course Material – Bridging & IP Firewall Integration:
“If you want to apply queues or firewall rules to traffic flowing through a bridge, you must enable ‘use-ip-firewall’ under the bridge settings.”
René Meneses MTCNA Guide – Bridge Queuing Section:
“Simple Queues do not affect bridged traffic unless you activate the ‘Use IP Firewall’ setting in bridge configuration. This pushes the packets through the normal firewall and queueing engine.”
MikroTik Wiki – Bridge Settings:
“If use-ip-firewall is enabled, then all bridged traffic is also processed by firewall and queues.”
Options A and C are incorrect because assigning an IP or linking the queue alone does not enforce restrictions at Layer 2.
Option B refers to advanced queueing with mangle + Queue Trees, not Simple Queues.
Final Answer: DQUESTION NO: 84 [QoS (Simple Queues)]
In RouterOS queue configurations the word "total" usually represents:
A. download - upload
B. upload
C. upload + download
D. download
Answer: C
In Simple Queues, MikroTik uses the term “total” to refer to the sum of the incoming and outgoing traffic for a particular target. This includes both upload (TX) and download (RX) traffic.
MTCNA Course Material – Queues Overview:
“Total limit represents the combined limit of upload and download traffic. If both target-upload and target-download are defined, total-limit should be equal or higher.”
René Meneses MTCNA Study Guide – Queues Chapter:
“In Simple Queues, ‘max-limit’ and ‘limit-at’ can be set individually for upload and download, or together as ‘total’ which combines both directions.”
Terry Combs Notes – Queue Definitions:
“Total in RouterOS queues means sum of upload and download. Always consider total bandwidth used in both directions when using ‘total-limit’.”
Therefore, the correct and verified answer is C: upload + download.
If ARP=reply-only is configured on an interface, this interface will:
Options:
accept all MAC-addresses listed in '/ip arp' as static entries
accept IP and MAC address combinations listed in '/ip arp' list
add new MAC addresses in '/ip arp' list
add new IP addresses in '/ip arp' list
accept all IP addresses listed in '/ip arp' as static entries
Answer:
BExplanation:
When ARP is set to reply-only on a MikroTik interface, the router will not respond to any ARP requests unless a matching static entry exists in the /ip arp list. It will also not learn new dynamic entries — only pre-defined static IP-MAC pairs will be accepted and responded to.
Option breakdown:
A.✘Incorrect – The router doesn't operate solely based on MAC, but on IP-MAC pairings.
B.✔Correct – Only combinations that match entries in /ip arp are accepted.
C.✘Incorrect – reply-only mode disables dynamic ARP learning.
D.✘Incorrect – Again, no new IPs are dynamically added.
E.✘Incorrect – Static ARP is enforced by IP-MAC pairs, not just IP.
Extract from MTCNA Course Material – ARP Modes:
“Reply-only mode will respond to ARP requests only if a matching static ARP entry exists. No dynamic learning occurs.”
Extract from René Meneses Study Guide – ARP Explanation:
“Use ARP=reply-only to force strict IP-MAC pairing. It prevents spoofing but requires all valid pairs to be preconfigured.”
Extract from MikroTik Wiki – ARP Settings:
“reply-only: Only respond to ARP requests if the requester matches a static /ip arp entry. New dynamic entries are not created.”
===========
What is the minimal possible wireless configuration to create an Access Point?
Options:
radio name
scan-list
frequency
band
ssid
DFS mode
WDS
Answer:
C, D, E, HExplanation:
To configure a MikroTik wireless interface as a basic access point (AP), the minimum required parameters are:
Mode → Must be set to ap-bridge or bridge
SSID → Defines the wireless network name to broadcast
Band → Determines which frequency ranges are used (e.g., 2.4GHz b/g/n or 5GHz a/n/ac)
Frequency → Specifies the actual channel used for broadcasting
Options reviewed:
A. radio name →✘Optional. A cosmetic label used to identify the radio in Winbox.
B. scan-list →✘Optional. Used to define which frequencies the interface should scan.
C.✔Required
D.✔Required
E.✔Required
F. DFS mode →✘Optional and auto-configured based on regulatory domain.
G. WDS →✘Only needed for bridging or extending networks.
Extract from Official MTCNA Course Material – Wireless Configuration:
“The minimal settings to enable an Access Point include: mode, SSID, band, and frequency. Without these, the interface won’t broadcast.”
Extract from René Meneses Study Guide – Wireless Basics:
“To turn on an AP: Set the mode to ap-bridge, define SSID, band, and frequency. Other settings are optional or advanced.”
Extract from Terry Combs Notes – Wireless Setup:
“Essential: mode, frequency, SSID, band. Others like WDS and DFS are situational.”
===========
Mark all the features that can be used for limiting client registrations to your access point:
Options:
access-list
wpa
WDS
registration-table
Answer:
A, BExplanation:
MikroTik allows you to control which clients can connect to your access point through:
WPA/WPA2 security – prevents unauthorized devices from authenticating.
Access List – filters by MAC address and signal strength.
Option breakdown:
A.✔access-list – Used to accept/reject client MACs and customize access settings.
B.✔wpa – WPA/WPA2 passphrase restricts who can join the network.
C.✘WDS – Wireless Distribution System, used for bridging, not access control.
D.✘registration-table – A monitoring tool showing currently connected clients; it doesn’t restrict connections.
Extract from Official MTCNA Course Material – Wireless Access Control:
“Use WPA/WPA2 for secure authentication. Access List lets you accept or reject clients based on MAC or signal level.”
Extract from René Meneses MTCNA Study Guide – Wireless Security & Filtering:
“You can limit client access using WPA security and Access List. Registration Table only shows connected users.”
Extract from Terry Combs Notes – Wireless Configuration:
“Access control = WPA + Access List. WDS is for bridging, and registration-table is read-only.”
Domain Name System (DNS) requests can use protocol/port:
Options:
UDP
TCP port 53
Answer:
A, BExplanation:
DNS primarily uses UDP port 53 for most query/response operations. However, TCP port 53 is also used, particularly for larger responses (such as DNS zone transfers or DNSSEC).
A.✔UDP – Used for standard DNS queries due to lower overhead.
B.✔TCP port 53 – Used when UDP is insufficient, especially for zone transfers (AXFR/IXFR).
Extract from MTCNA Course Material – DNS and Networking Services:
“DNS typically uses UDP/53, but falls back to TCP/53 for larger queries or zone transfers.”
Extract from MikroTik Wiki – DNS Settings:
“DNS uses UDP for general queries. TCP is used when UDP cannot accommodate the size of the response.”
===========
You have 10 users plugged into a hub running 10 Mbps half-duplex. There is a server connected to the switch running 10 Mbps half-duplex as well. How much bandwidth does each host have to the server?
Options:
100 kbps
1 Mbps
2 Mbps
10 Mbps
Answer:
DExplanation:
When using a hub, all connected devices share the total bandwidth. Since it’s a 10 Mbps half-duplex hub, all 10 users share the same collision domain and 10 Mbps. However, when calculating potential access to the server from any single host, each host can use the full 10 Mbps — as long as no other users are transmitting simultaneously.
More importantly, the connection to the server is also 10 Mbps half-duplex, so regardless of the internal collisions, each client could use the full 10 Mbps to the server — just not concurrently with others.
Cisco CCNA Curriculum – Hubs and Bandwidth Sharing:
“In a hub, all ports share bandwidth. However, each host is capable of utilizing the full bandwidth if no contention exists.”
René Meneses MTCNA Study Guide – Hub Limitations:
“A hub provides shared bandwidth, but each device can use the full rate momentarily, assuming no collisions.”
Hence, the correct answer is based on potential — not divided bandwidth.
Final Answer: DQUESTION NO: 146 [Cisco IOS – Configuration Management]
What command is used to create a backup configuration?
A. copy running backup
B. copy running-config startup-config
C. config mem
D. wr mem
Answer: B
The command copy running-config startup-config saves the current active configuration in RAM (running-config) to NVRAM (startup-config). This ensures that the configuration persists after a reboot.
Cisco IOS Configuration Guide – Saving Configs:
“To save the active configuration, use: copy running-config startup-config.”
René Meneses MTCNA Study Guide – IOS Management:
“Saving configuration ensures the device boots with the same settings. Use copy running-config startup-config or its shortcut: wr.”
Breakdown:
A: Invalid syntax — no such keyword as “backup”
C: config mem is outdated and not used in modern IOS
D: wr mem is a shortcut for “write memory” — still valid but less commonly used
Final Answer: BQUESTION NO: 147 [Cisco IOS – Access Control Lists]
What are the two main types of access control lists (ACLs)?
Standard
IEEE
Extended
Specialized
A. 1 and 3
B. 2 and 4
C. 3 and 4
D. 1 and 2
Answer: A
Cisco IOS supports two primary types of ACLs:
Standard ACLs: Filter traffic based only on source IP address
Extended ACLs: Filter traffic based on source, destination IP, protocol type, and port numbers
Cisco IOS Security Guide – ACL Fundamentals:
“Standard ACLs use only source IP for filtering. Extended ACLs can match based on source, destination, ports, and protocols.”
René Meneses MTCNA Study Guide – ACL Types:
“Two types of IP ACLs: standard and extended. IEEE or specialized ACLs do not exist in Cisco terminology.”
Other options:
IEEE: Refers to Ethernet or wireless standards, not ACLs
Specialized: Not a defined ACL type
MAC layer by OSI model is also known as
Options:
Layer 2
Layer 1
Layer 6
Layer 7
Layer 3
Answer:
AIf a packet comes to a router and starts a new, previously unseen connection, which connection state would be applied to it?
Options:
no connection state would be applied to such packet
new
unknown
invalid
established
Answer:
BExplanation:
MikroTik uses connection tracking to assign states to packets that pass through the router’s firewall. When a packet initiates a connection that is not previously tracked, it is marked as new.
Connection states:
new: First packet of a new connection
established: Part of an existing tracked connection
related: New connection related to an existing one (e.g., FTP data channel)
invalid: Unrecognized or malformed connection
unknown: Used in very specific or rare circumstances (not common in IP-based networks)
Therefore:
A.✘Incorrect – All packets entering the firewall are tracked
B.✔Correct – This is a new connection
C.✘Incorrect – "unknown" is not used for typical traffic
D.✘Incorrect – Not invalid unless malformed or contextless
E.✘Incorrect – This is not an existing connection
Extract from Official MTCNA Course Material – Firewall Connection States:
“A packet that begins a new connection is marked as ‘new’. Connection tracking then continues monitoring that session.”
Extract from René Meneses MTCNA Study Guide – Connection Tracking:
“New connections receive the 'new' state. Firewall rules often start by permitting or blocking 'new' and 'established' states.”
Extract from MikroTik Wiki – Firewall and Connection States:
“State=new is assigned when no existing connection entry matches the incoming packet.”
===========
PPPoE server only works within one Ethernet broadcast domain that it is connected to. If there is a router between server and end-user host, it will not be able to create PPPoE tunnel to that PPPoE server.
Options:
False
True
Answer:
BExplanation:
PPPoE (Point-to-Point Protocol over Ethernet) relies on Ethernet broadcast and discovery mechanisms. It uses a discovery stage (PPPoE Active Discovery Initiation – PADI) which is sent as a broadcast. Therefore, PPPoE only works within the same Layer 2 broadcast domain.
If a router (Layer 3 device) exists between the client and PPPoE server, it breaks the Layer 2 broadcast domain, making it impossible for the client to reach the server.
A.✘False – Routers break the broadcast domain; PPPoE will fail.
B.✔True – PPPoE requires L2 adjacency.
Extract from Official MTCNA Course Material – PPPoE Concepts:
“PPPoE operates only over Ethernet broadcast domains. If routed, PADI packets will not reach the PPPoE server.”
Extract from René Meneses MTCNA Study Guide – PPPoE:
“PPPoE discovery is broadcast-based and does not traverse routers.”
Extract from MikroTik Wiki – PPPoE Limitations:
“PPPoE cannot function over routed networks. Server and client must be in the same broadcast domain.”
===========
Is action=masquerade allowed in chain=dstnat?
Options:
yes, but only if dst-addr is specified
yes
yes, but it works only for incoming connections
no
Answer:
DExplanation:
The action=masquerade is used exclusively in the srcnat chain. It dynamically hides internal IP addresses behind the router's public IP. It cannot be used in the dstnat chain.
A.✘Incorrect – masquerade is not allowed in dstnat regardless of parameters.
B.✘Incorrect – masquerade is not valid in the dstnat chain.
C.✘Incorrect – masquerade does not operate in dstnat, direction does not change this.
D.✔Correct – masquerade must only be used in chain=srcnat.
Extract from MTCNA Course Material – NAT Concepts:
“Masquerade is a special type of source NAT used only in the srcnat chain. It is invalid in dstnat.”
Extract from René Meneses Study Guide – NAT Actions:
“Use action=masquerade in chain=srcnat. RouterOS will not accept it in dstnat.”
Extract from MikroTik Wiki – NAT Rules:
“action=masquerade is not allowed in dstnat chain and will result in error if applied.”
===========
Which default route will be active?
/ip route
add disabled=no distance=10 dst-address=0.0.0.0/0 gateway=1.1.1.1
add disabled=no distance=5 dst-address=0.0.0.0/0 gateway=2.2.2.2
Options:
Route via gateway 2.2.2.2
Route via gateway 1.1.1.1
Answer:
AExplanation:
In MikroTik RouterOS (and in routing in general), the "distance" value determines the priority of a route. The route with the lowest distance will be preferred.
Here:
Route to 0.0.0.0/0 via 1.1.1.1 has distance = 10
Route to 0.0.0.0/0 via 2.2.2.2 has distance = 5 → lower, so preferred✅
Unless the lower-distance route is invalid or unreachable, it will always be selected.
MTCNA Course Manual – Static Routing:
“The lower the distance value, the higher the route’s priority. Routes are selected based on administrative distance first.”
René Meneses Study Guide – Route Distance:
“A route with distance 1 is preferred over a route with distance 2. It does not matter which was added first.”
Terry Combs Notes – Routing Behavior:
“RouterOS evaluates the distance (priority) before anything else. Smallest value wins.”
Answer: AQUESTION NO: 44 [Firewall]
What does the firewall action "Redirect" do? Select all true statements.
A. Redirects a packet to a specified port on the router
B. Redirects a packet to a specified IP
C. Redirects a packet to the router
D. Redirects a packet to a specified port on a host in the network
Answer: A, C
The redirect action in MikroTik’s NAT firewall rules is used to force traffic (usually from LAN clients) to a local service on the router — for example, redirecting all DNS queries to the router’s DNS server, or forcing web traffic to a proxy.
Details:
It changes the destination IP to the router's IP automatically (without needing to specify it)
It also allows port redirection (e.g., dst-port=80 → to 3128 for proxy)
Evaluation:
A.✅True — You can redirect to a specific port on the router
B.❌False — Redirect does not change destination IP to an arbitrary host; for that, use dst-nat
C.✅True — Redirect forces traffic to the router itself
D.❌False — dst-nat is used to forward packets to internal hosts, not redirect
MTCNA Course Manual – NAT Actions:
“Redirect action changes destination to the router itself. This is useful for forcing traffic through router services.”
René Meneses Guide – NAT Behavior:
“Redirect = router-local services like DNS or proxy. Use dst-nat for remote hosts.”
Terry Combs Notes – Firewall Actions:
“Use redirect when you want to intercept traffic and handle it locally on the router.”
Answer: A, CQUESTION NO: 45 [PPP / Tunnels]
Which port does PPTP use by default?
A. TCP 1721
B. UDP 1723
C. TCP 1723
D. UDP 1721
Answer: C
PPTP (Point-to-Point Tunneling Protocol) uses:
TCP port 1723 for control and session initiation
GRE (Generic Routing Encapsulation) protocol (protocol number 47) for tunneling
No UDP port is used by PPTP.
Evaluation:
A. TCP 1721 →❌Invalid port
B. UDP 1723 →❌Incorrect protocol (TCP is used, not UDP)
C.✅TCP 1723 → Correct
D.❌Invalid (wrong protocol and port)
MTCNA Tunneling Section – PPTP Overview:
“PPTP uses TCP port 1723 for control and GRE protocol for tunneling traffic.”
René Meneses MTCNA Guide – PPTP Characteristics:
“PPTP = TCP/1723 + GRE (not a port, but a protocol). Allow both on firewall.”
Terry Combs Notes – VPN Protocol Reference:
“PPTP: TCP 1723. GRE must be permitted for tunnel data.”
Answer: CQUESTION NO: 46 [Firewall]
Which firewall chain should you use to filter ICMP packets from the router itself?
A. input
B. postrouting
C. forward
D. output
Answer: D
MikroTik RouterOS uses firewall chains to process packets based on direction:
input: For packets destined to the router itself (from outside)
output: For packets originating from the router (e.g., router pings)
forward: For packets passing through the router between interfaces
postrouting: Used for NAT and marking, not filtering
Therefore:
To block/allow ICMP (ping) generated by the router (e.g., netwatch, DNS probes), use the output chain
To block incoming pings to the router, use input
To block pings between LAN and WAN, use forward
MTCNA Firewall Module – Chain Responsibilities:
“To control traffic originating from the router itself, use the output chain. For example, when the router itself sends ICMP requests.”
René Meneses Guide – Firewall Chains Explained:
“output is for locally generated traffic. input is for inbound traffic to the router.”
Terry Combs Notes – Chain Use Cases:
“Ping from router = output. Ping to router = input. Ping between networks = forward.”
Destination NAT (chain dstnat, action dst-nat) can be used to:
Options:
Change destination port
Direct users from the Internet to a server within your local network
Change source port
Hide your local network from the Internet
Answer:
A, BExplanation:
Destination NAT (dst-nat) is used to redirect packets arriving at the router to a different internal destination. It is most commonly used to allow public access to internal services such as web servers or mail servers.
You can:
Change the destination IP address (redirect to an internal host)
Change the destination port (e.g., port 8080 to port 80)
But:
C. Changing the source port is a function of src-nat, not dst-nat →❌
D. Hiding the local network from the Internet is done via masquerade or src-nat →❌
MTCNA Course Manual – NAT Section:
“Use dst-nat to forward traffic to a private host. Port translation can also be applied (e.g., from 81 to 80).”
René Meneses Study Guide – NAT Configuration:
“dst-nat changes the destination IP/port of packets arriving on a specific interface. Common use case: access to LAN services from WAN.”
Terry Combs Notes – NAT Rule Summary:
“dst-nat = port forwarding. src-nat/masquerade = hide internal addresses.”
Answer: A, BQUESTION NO: 48 [RouterOS Introduction]
Which is the default port of IP-Winbox?
A. UDP 8291
B. TCP 80
C. TCP 8291
D. TCP 8192
Answer: C
Winbox is MikroTik’s GUI-based configuration tool. It communicates with RouterOS over TCP port 8291 by default. This port is used for both IP-based Winbox connections and MAC-based sessions (in combination with layer-2 discovery protocol).
Evaluation:
A. UDP 8291 →❌Wrong protocol
B. TCP 80 →❌Used for HTTP (WebFig)
C. TCP 8291 →✅Correct default Winbox port
D. TCP 8192 →❌Invalid / non-standard
MTCNA Course Manual – RouterOS Management Tools:
“Winbox uses TCP port 8291 by default. It is possible to change this port in the /ip service settings.”
René Meneses MTCNA Guide – Winbox Access:
“Default access via TCP 8291. Check firewall filters to ensure it’s not blocked.”
Terry Combs Notes – Remote Management:
“Winbox = TCP/8291. WebFig = TCP/80 or 443.”
Answer: CQUESTION NO: 49 [PPP]
It is possible to create an encrypted PPPoE tunnel in RouterOS:
A. true
B. false
Answer: B
PPPoE (Point-to-Point Protocol over Ethernet) does not include encryption by default. It can authenticate users using PAP or CHAP, but the data payload is transmitted in cleartext unless another secure tunneling protocol (e.g., IPSec) is layered on top.
MikroTik supports encryption in other tunneling protocols, such as:
SSTP (uses SSL)
L2TP with IPSec
OpenVPN (SSL-based)
IPsec itself (for IP layer encryption)
MTCNA Tunneling Chapter – PPP Protocol Features:
“PPPoE offers authentication, compression, but no native encryption. Use IPSec if encryption is needed.”
René Meneses Guide – Tunnel Comparison Table:
“PPPoE is not encrypted. SSTP and L2TP/IPSec are alternatives when encryption is a requirement.”
Terry Combs Notes – PPP Family Summary:
“PPPoE: Authentication = Yes, Encryption = No. Use with caution over untrusted networks.”
Answer: BQUESTION NO: 50 [Wireless]
Why is it useful to set a Radio Name on the radio interface?
A. To identify a station in a list of connected clients
B. To identify a station in Neighbor discovery
C. To identify a station in the Access List
Answer: A
The Radio Name is a human-readable identifier assigned to a wireless interface. It becomes visible in the Registration Table (i.e., the list of connected clients) on an access point. It helps network administrators distinguish between multiple connected devices.
Evaluation:
A.✅Correct — Radio Name is shown in the Registration Table (list of connected clients)
B.❌Neighbor discovery uses MAC and device identity, not radio name
C.❌Access List uses MAC addresses, not radio name, for matching
MTCNA Wireless Module – Interface Settings:
“Radio Name is shown in the registration table on the AP. It helps in client identification.”
René Meneses Guide – Wireless Monitoring:
“The AP uses the client’s Radio Name to label them in the list of associated stations.”
Terry Combs Notes – Best Practice:
“Set radio-name so you can easily tell which device is which in the registration list.”
Answer: A
Which router command allows you to view the entire contents of all access lists?
Options:
show all access-lists
show access-lists
show ip interface
show interface
Answer:
BExplanation:
The show access-lists command in Cisco IOS is used to display all configured access control entries (ACEs) in every access list, both named and numbered. This command shows the complete content, including rules and hit counters.
Cisco IOS Command Reference – Access List Monitoring:
“Use show access-lists to view the complete list of all access control entries. This includes both standard and extended lists.”
Other options:
A: Invalid command syntax
C: show ip interface shows interface-level IP settings and ACL applications, but not full ACL content
D: show interface shows status and statistics, not ACL rules
Final Answer: BQUESTION NO: 134 [Cisco IOS – Console Access Configuration]
What does the command routerA(config)#line cons 0 allow you to perform next?
A. Set the Telnet password.
B. Shut down the router.
C. Set your console password.
D. Disable console connections.
Answer: C
The command line cons 0 enters the console line configuration mode. This is used to apply settings specific to the physical console line, such as setting a login password (via password and login commands).
Cisco IOS Configuration Guide – Line Console Mode:
“Use line console 0 to configure settings for the console line, including timeouts, password security, and logging behavior.”
René Meneses Study Guide – Device Access:
“Console access configuration begins with line console 0. It is followed by login and password commands.”
Other options:
A: Telnet is configured under line vty, not console
B: Router shutdown is done with reload or shutdown commands (not here)
D: Console cannot be disabled from line cons 0
Final Answer: CQUESTION NO: 135 [Switching – Spanning Tree Protocol]
How often are BPDUs sent from a Layer 2 device?
A. Never
B. Every 2 seconds
C. Every 10 minutes
D. Every 30 seconds
Answer: B
BPDU (Bridge Protocol Data Units) are messages exchanged by switches in a Spanning Tree Protocol (STP) topology to maintain loop-free Layer 2 networks. By default, switches send BPDUs every 2 seconds.
MTCNA Course Material – STP Operation:
“Switches send BPDUs to maintain spanning tree and detect topology changes. The default transmission interval is 2 seconds.”
Cisco STP Documentation:
“BPDUs are transmitted by the root bridge and propagated every 2 seconds by default, controlled by the hello-time timer.”
Other options:
A: Incorrect — BPDUs are essential for loop prevention
C & D: Not correct — default is 2 seconds, not minutes
Final Answer: BQUESTION NO: 136 [Routing Protocols – Passive Interface Behavior]
What does the passive command provide to dynamic routing protocols?
A. Stops an interface from sending or receiving periodic dynamic updates.
B. Stops an interface from sending periodic dynamic updates but not from receiving updates.
C. Stops the router from receiving any dynamic updates.
D. Stops the router from sending any dynamic updates.
Answer: B
In dynamic routing (e.g., RIP, OSPF, EIGRP), the passive-interface command stops routingadvertisements (outgoing updates) from being sent through the specified interface. However, the router still listens for incoming routing updates.
Cisco IOS Configuration Guide – Passive Interface:
“The passive-interface command prevents routing updates from being sent on an interface, while still allowing updates to be received.”
René Meneses MTCNA Guide – Passive Mode:
“It suppresses sending routing advertisements but does not block receiving updates on that interface.”
Other options:
A: Incorrect — it does not block receiving
C: Incorrect — it applies to interfaces, not globally
D: Also incorrect — it does not block all updates
Final Answer: B
────────────────────────────────────────────────────────────
To block communications between wireless clients connected to the same access point interface, you should set:
Options:
'default-forwarding=no'
'max-station-count=1'
'default-authentication=no'
'default-authentication=no' and 'default-forwarding=no'
Answer:
AExplanation:
The setting default-forwarding=no prevents wireless clients from communicating with each other over the same access point interface. This enables client isolation — each device can only reach the gateway (router), not other wireless clients.
A.✔Correct – This enables client isolation by blocking inter-client communication.
B.✘Incorrect – This limits how many clients can connect, not their ability to talk to each other.
C.✘Incorrect – Prevents new clients from associating, unrelated to inter-client traffic.
D.✘Incorrect – Only default-forwarding affects client-to-client visibility.
Extract from MTCNA Course Material – Wireless Security and Isolation:
“default-forwarding=no prevents wireless clients from communicating with each other on the same AP interface.”
Extract from René Meneses Study Guide – Wireless Interface Settings:
“To isolate wireless clients, use default-forwarding=no. This ensures clients can’t ping or access one another.”
Extract from MikroTik Wiki – Wireless Interface Options:
“default-forwarding=no stops traffic between clients. Only traffic to the AP is allowed.”
What wireless card can we use to achieve 100 Mbps actual wireless throughput?
Options:
802.11 b/g
802.11 a/b/g
802.11 a
802.11 a/n
802.11 a/b/g/n
Answer:
DExplanation:
To achieve actual throughput of 100 Mbps, you must use 802.11n, which supports higher data rates through technologies such as MIMO (Multiple Input, Multiple Output) and channel bonding. 802.11n provides theoretical speeds up to 150 Mbps per stream and actual throughput above 100 Mbps under good conditions.
802.11a/b/g maxes out around 20–25 Mbps real throughput
802.11n (especially in 5 GHz band via 802.11a/n) is required to exceed 100 Mbps actual throughput
MTCNA Course Material – Wireless Standards and Data Rates:
“802.11n with proper channel width and MIMO can achieve over 100 Mbps of real throughput.”
René Meneses MTCNA Study Guide – Wireless Performance:
“Only 802.11n can reach 100+ Mbps in practical use. Legacy modes (a/b/g) fall short due to modulation limits.”
Breakdown:
A/B/C: Do not support 100 Mbps throughput
D:✔802.11a/n supports 100+ Mbps
E: While also valid, D is more precise for the specific requirement (focused on a/n only)
Final Answer: DQUESTION NO: 156 [Firewall – Mangle Chains]
It is possible to add user-defined chains in ip firewall mangle.
A. True
B. False
Answer: A
RouterOS allows users to define custom chains in the mangle table, giving more flexibility for organizing and managing rules. This is particularly useful in complex routing and QoS configurations.
MikroTik Wiki – Firewall Mangle:
“Custom chains can be created using the add chain=your_chain_name command. Then you can jump to them from built-in chains.”
MTCNA Course Material – Mangle & Packet Flow:
“User-defined chains help separate logic and simplify processing. You can jump into them from prerouting, forward, or postrouting.”
Final Answer: AQUESTION NO: 157 [Firewall – NAT and Redirect Actions]
Action=redirect allows you to make:
A. Transparent DNS Cache
B. Forward DNS to another device IP address
C. Enable Local Service
D. Transparent HTTP Proxy
Answer: D
In RouterOS, action=redirect is used in NAT rules to redirect traffic destined for specific ports to local services. This is often used for:
Transparent web proxy (redirect port 80 to a local proxy service)
Transparent DNS interception (if RouterOS is the DNS server)
In most practical MikroTik use cases, redirect is associated with Transparent HTTP Proxy.
MTCNA Course Material – NAT Configuration:
“action=redirect rewrites the destination address to the router’s own IP. It is commonly used to create transparent web proxies.”
MikroTik Wiki – NAT Redirect:
“Redirect is used for redirecting traffic to local services like web proxy or DNS cache on the router.”
Breakdown:
A: Possible, but limited use; DNS cache works better with dst-nat
B: Incorrect — to forward to another IP, use dst-nat
C: Misleading — enabling local services doesn't require redirect
D:✔Correct—redirect enables transparent proxy setup
Final Answer: DQUESTION NO: 158 [Routing – Automatically Created Routes]
What letters appear next to a route, which is automatically created by RouterOS when user adds a valid address to an active interface?
A. I
B. D
C. A
D. S
E. C
Answer: E
In RouterOS, when an IP address is assigned to an interface, a connected route is automatically created. These routes are marked with the letter “C” in the routing table, denoting “Connected.”
MikroTik Wiki – Routing Table Flags:
“C – directly connected routes (assigned via /ip address), added automatically when interface is active.”
MTCNA Course Material – Static vs Dynamic Routes:
“Connected (C) routes are added automatically when IP is assigned to an interface.”
Flag meanings:
C:✔Connected
S: Static
D: Dynamic
A: Active (not a route type)
I: Invalid or intermediate (not shown for connected)
How long is level 1 (demo) license valid?
Options:
24 hours
Infinite time
1 month
1 year
Answer:
BExplanation:
RouterOS Level 1 license is the demo license that comes with all RouterOS installations (particularly on x86 or CHR before activation). It is unrestricted in time, meaning it never expires, but functionality is extremely limited.
A. 24 hours → Incorrect. There is no such time-limited restriction.
B. Infinite time → Correct. Level 1 license is perpetual but has limited features.
C. 1 month → Incorrect. MikroTik does not impose monthly timeouts on license levels.
D. 1 year → Incorrect. No temporary time-bound license is assigned by default.
Extract from Official MTCNA Course Material – Licensing Section:
“Level 1 (demo) license is unlimited in time but has very limited functionality. It is designed for testing purposes only.”
Extract from René Meneses MTCNA Study Guide – RouterOS Licensing:
“The Level 1 license is not time-limited, but it cannot be used in production due to its lack of key features.”
Extract from MikroTik Wiki – Licensing Model:
“License level 1 is a free demo license that does not expire.”
===========
What is the term for the hardware coded address found on an interface?
Options:
FQDN Address
IP Address
Interface Address
MAC Address
Answer:
DExplanation:
The hardware-coded address that uniquely identifies a device's network interface card (NIC) on the local network is called a MAC address. It is “burned in” by the hardware manufacturer and remains constant unless manually overridden.
MAC stands for Media Access Control, and it operates at Layer 2 of the OSI model. It is used to identify devices on a local area network.
A. FQDN (Fully Qualified Domain Name) refers to a human-readable name used in DNS.
B. IP Address is a logical address used for routing at Layer 3.
C. Interface Address is a generic term and not a standard identifier.
D. MAC Address is correct and refers to the physical, hardware-encoded address on an interface.
Extract from MTCNA Course Manual – RouterBOARD Overview:
“A MAC address is a globally unique hardware identifier assigned to each Ethernet or wireless interface. It is used by Layer 2 to ensure local delivery.”
René Meneses Study Guide – MAC & OSI Layering:
“The MAC address is a 48-bit physical identifier, hardcoded by the device vendor and located in the NIC chip.”
Terry Combs MTCNA Notes – Layer 2 Concepts:
“MAC = Physical Address = Layer 2 Identifier. It’s what switches use to forward Ethernet frames.”
===========
You have a DHCP server on your MikroTik router. The IP addresses 10.1.2.2–10.2.2.20 are distributed in the DHCP network. Additionally, 3 static IP addresses are defined for your servers: 10.1.2.31–10.1.2.33.
After a while, 20 more IP addresses need to be distributed in the network. It is possible to distribute the extra IP addresses without adding another DHCP Server:
Options:
True
False
Answer:
AExplanation:
MikroTik RouterOS allows DHCP administrators to modify the DHCP address pool without creating an additional DHCP server. You can simply edit or extend the address pool range, and the DHCP server will start offering those new IPs.
Therefore, it is completely possible to:
Extend the existing address pool
Exclude statically assigned IPs
Continue using the same DHCP Server instance
You do NOT need to create a second DHCP server on the same interface.
MTCNA Course Manual – DHCP Configuration:
“It is possible to expand the address-pool dynamically without adding additional DHCP servers. Just add more IPs to the pool.”
René Meneses Study Guide – DHCP Pools Section:
“You can edit the address pool associated with the DHCP server anytime to include more addresses. No need to create another server.”
Terry Combs Notes – DHCP Tips:
“Keep one DHCP server per subnet. Extend pools via IP > Pool if more IPs are needed.”
Answer: AQUESTION NO: 25 [Wireless]
In which order are the entries in Access List and Connect List processed?
A. By Signal Strength Range
B. By interface name
C. In sequence order
D. In a random order
Answer: C
MikroTik processes the entries in the Access List and Connect List in a top-down fashion —meaning that the first matching entry is the one applied. This is known as sequence order (from top to bottom).
Each rule is checked in the order it appears in the list, and once a match is found, the rest of the list is ignored for that client.
Incorrect options:
A. Signal strength is only a condition, not a sorting method
B. Interface names are part of rule conditions
D. Not random — rules are processed sequentially
MTCNA Official Training Manual – Wireless Access & Connect List:
“Rules in access-list and connect-list are checked in the order they are listed. Once a match is found, further rules are ignored.”
René Meneses Guide – Wireless Access Rules:
“Access-list is evaluated top-down. Sequence matters.”
Terry Combs MTCNA Notes – Wireless Filtering:
“Be careful with order. The first matching rule is applied — no exceptions.”
Answer: CQUESTION NO: 26 [Wireless]
During a scan, in order to see all the available wireless frequencies that are supported by the card, the following option must be selected in the wireless card's "Frequency Mode":
A. superchannel
B. regulatory domain
C. manual txpower
Answer: A
In MikroTik RouterOS, enabling the "superchannel" frequency mode allows access to all frequencies supported by the wireless chip, including those that may be outside of country-specific regulatory limits. This mode is typically used in lab testing or in regions where regulations permit.
A. superchannel →✅Correct. Enables full frequency range
B. regulatory domain → Restricts visible frequencies to region’s law
C. manual txpower → Controls power output, not frequency scanning
MTCNA Course Material – Wireless Configuration Options:
“To unlock all available wireless frequencies for scanning or connection, enable the 'superchannel' frequency mode.”
René Meneses Study Guide – Wireless Advanced Config:
“Superchannel mode shows all channels supported by the hardware. Use with caution — may violate regulations.”
Terry Combs Notes – Wireless Modes:
“Want to see hidden or extended frequencies? Use superchannel mode. Not legal in every region.”
Answer: AQUESTION NO: 27 [NAT]
It is required to make a web server on a private LAN visible on the public internet. Only the web server port should be visible to the public. Which of the following configuration steps must be met? (Select all that apply)
A. Public IP address of the web server must be installed on the NAT Router
B. In IP firewall NAT, there should be a dst-nat between the public IP of the router and the private IP of the web server
C. Connection Tracking must be enabled on NAT router
D. A route between the NAT router and the web server must exist
E. LAN address of the web server should be routable on the internet
Answer: B, C, D
To expose a web server behind a MikroTik router to the public, the following steps must be met:
B. dst-nat rule must be created to forward incoming requests (e.g., TCP port 80) to the internal web server IP →✅Required
C. Connection Tracking must be enabled, otherwise NAT rules won’t function →✅Required
D. A route between the NAT router and the web server must exist (usually a directly connected subnet) →✅Required
Incorrect Options:
A. The public IP does not need to be installed on the web server — it remains private →❌
E. Private LAN IP (like 192.168.x.x) does not need to be routable on the internet →❌
MTCNA Course Manual – NAT and Port Forwarding Section:
“To expose internal services to the public internet, use dst-nat. Ensure connection tracking is active and the server is reachable through routing.”
René Meneses Guide – NAT Configuration:
“DST-NAT forwards specific ports to internal IPs. Connection tracking is a prerequisite. LAN IPs remain private.”
Terry Combs Notes – Web Server NAT Rules:
“No need to assign public IP to server. Just configure a proper NAT rule and ensure routing exists internally.”
════════════════════════════════════════════
How many layers does the Open Systems Interconnection model have?
Options:
6
9
5
7
12
Answer:
DExplanation:
The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of a communication system into seven distinct layers. It is used to understand and design computer networking systems.
The seven layers of the OSI model are:
Application
Presentation
Session
Transport
Network
Data Link
Physical
Each layer has its own specific purpose and interacts with adjacent layers to perform data transmission functions.
MTCNA Official Course Material – OSI Model Chapter:
“The OSI model consists of 7 layers. Understanding these layers is critical for troubleshooting and protocol analysis.”
René Meneses MTCNA Study Guide – OSI Model Section:
“There are exactly seven OSI layers. They range from the Physical Layer (Layer 1) to the Application Layer (Layer 7).”
Terry Combs Notes – OSI Summary Page:
“OSI = 7 Layers. The most important ones for network engineers are Layer 1 through Layer 4.”
Answer: DQUESTION NO: 13 [Routing]
How many usable IP addresses are there in a 20-bit subnet?
A. 4096
B. 4094
C. 2046
D. 2048
E. 2047
Answer: B
A /20 subnet means that 20 bits are used for the network portion, and 12 bits are left for host addresses. The total number of IP addresses available in such a subnet is:
2^12 = 4096 (total addresses)
Usable IP addresses = 4096 - 2 = 4094
→ (1 address is reserved for the network ID, and 1 for the broadcast address)
MTCNA Course Manual – Subnetting and IP Allocation:
“A subnet with n host bits gives 2^n total addresses. Always subtract 2 to account for network and broadcast addresses.”
René Meneses Study Guide – Subnet Calculations:
“/20 = 12 host bits → 4096 total IPs. Usable = 4094. Remember to subtract 2.”
Terry Combs MTCNA Notes – Addressing Math:
“20-bit subnet = 4094 usable IPs. Know how to compute 2^x and subtract 2.”
Answer: BQUESTION NO: 14 [Routing]
You have a router with configuration
Public IP: 202.168.125.45/24
Default gateway: 202.168.125.1
DNS server: 248.115.148.136, 248.115.148.137
Local IP: 192.168.2.1/24
Mark the correct configuration on client PC to access the Internet:
A. IP: 192.168.0.1/24, gateway: 192.168.2.1
B. IP: 192.168.2.253/24, gateway: 202.168.0.1
C. IP: 192.168.2.115/24, gateway: 192.168.2.1
D. IP: 192.168.2.2/24, gateway: 202.168.125.45
E. IP: 192.168.1.223/24, gateway: 248.115.148.136
Answer: C
To correctly configure a host in a private network behind a router:
The IP must match the local subnet (192.168.2.0/24)
The gateway must be the router’s local IP (192.168.2.1)
DNS settings can be default or custom, but IP and gateway must be valid
Let’s evaluate:
A. 192.168.0.1 → Wrong subnet (192.168.0.0/24 ≠ 192.168.2.0/24)❌
B. Gateway 202.168.0.1 → Invalid internal gateway❌
C. IP 192.168.2.115 with gateway 192.168.2.1 →✅Correct subnet and correct gateway
D. Gateway 202.168.125.45 → This is router’s public IP, not the correct gateway for LAN❌
E. IP 192.168.1.223 → Wrong subnet; also, gateway is DNS IP❌
MTCNA NAT Section – Network Configuration:
“Clients should be in the same subnet as the router’s local IP and must use that local IP as their gateway to reach outside networks.”
René Meneses Guide – Gateway and Addressing:
“The client’s IP should belong to the same subnet as the local router interface. Always verify gateway IP points to the internal address.”
Terry Combs Notes – Default Gateway Setup:
“The default gateway for local clients must be the internal router IP — not the public or DNS IP.”
Answer: CQUESTION NO: 15 [RouterBOARD Hardware]
Collisions are possible in full-duplex Ethernet networks:
A. true
B. false
Answer: B
In full-duplex Ethernet, devices can transmit and receive simultaneously on separate physical or logical channels. This eliminates the possibility of collisions because there is no need for devices to listen before transmitting — unlike half-duplex Ethernet, which uses CSMA/CD to manage potential collisions.
Full-duplex connections are the standard in modern switching environments and are always collision-free.
MTCNA Official Course Material – Ethernet & Duplex Modes:
“In full-duplex Ethernet, there are separate transmit and receive paths, and therefore, collisions cannot occur.”
René Meneses Study Guide – Ethernet Basics:
“Full-duplex = simultaneous send/receive = no collisions. Collisions are a legacy issue from half-duplex Ethernet.”
Terry Combs MTCNA Notes – CSMA/CD and Ethernet:
“Collision Detection (CD) is not used in full-duplex. Only half-duplex environments use CSMA/CD to manage access.”


