Which of the following devices should Jeff, an administrator, connect to a protocol analyzer in order to collect all of the traffic on a LAN segment?
Users are reporting that external web pages load slowly. The network administrator determines that the Internet connection is saturated. Which of the following is BEST used to decrease the impact of web surfing?
A computer has lost network connectivity. The network technician determines the network cable and the cable drop are both good. Which of the following would the technician use to test the computer’s NIC?
A web server that provides shopping cart capabilities for external end users will likely function with which of the following protocols?
A company would like their technicians to be able to connect to employee desktops remotely via RDP. Which of the following default port numbers need to be opened on the firewall to support this?
Which of the following protocols could the below packet capture be from?
Port: 161
msgVersion:
msgUsername:
msgAuthenticationParameters:
msgPrivacyParameters:
msgData:
data: get-request
request-id:
error-status: noError (0)
error-index: 0
variable-bindings: 0 items
Which of the following ports should be allowed through a firewall to allow DNS resolution to occur to an outside DNS server?
The MAC address of a network device is used to communicate at which of the following OSI layers?
At which of the following layers of the OSI model does an unmanaged switch operate?
Which of the following subnet masks would allow for 192.168.0.3 and 192.168.0.240 to be in the same subnet?
A CAT5e network cable run needs to be installed over fluorescent lighting arrays in an office building. Which of the following cable types would be BEST suited for such an installation?
A client’s computer is unable to access any network resources. Which of the following utilities can a technician use to determine the IP address of the client’s machine?
A consultant is installing new WAPs for an office using wall mounts. Which of the following is the BEST location for the new boxes for signal strength and coverage?
Which of the following is used to create a secure connection between a client and a host?
A network technician is doing a wireless audit and finds an SSID that does not match the company’s SSID. The company uses the SSID of ABC123, and the SSID the technician found is Default. Which of the following threats did the network technician find?
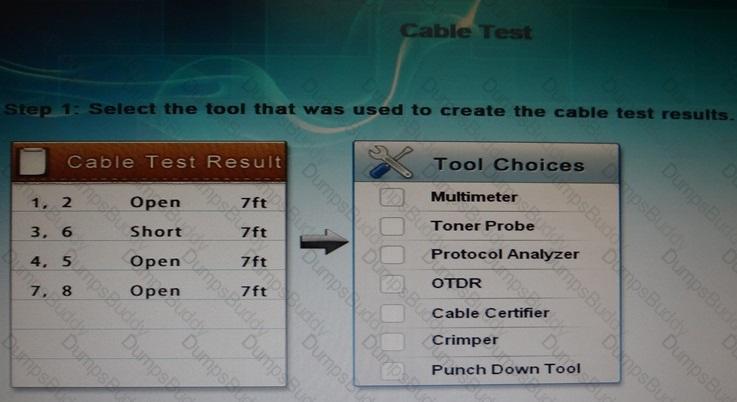
You have been tasked with testing a CAT5 cable. A summary of the test results can be found on the screen.
Step 1: Select the tool that was used to create the cable test results.
Step 2: Interpret the best results and select the options that explains the results.

During business hours, users at a small office are reporting that all of a sudden they are unable to reach any host on the Internet, but they can still use the network shares to transfer files within the office. Which of the following is the MOST likely cause of the outage?
A recent flood in the office caused a lot of equipment to be damaged and the manager of the IT department would like a way to prevent such an incident in the future. Which of the following is the BEST way to mitigate such an equipment failure?
A company has attempted to introduce a new major network segment to allow growth in capacity. On the core switch, a GBIC was used to interconnect with a newly placed downstream distribution switch for the first time. Soon after this implementation, a network flood and an outage occurred between the core and new distribution network modules. Which of the following should the network administrator troubleshoot FIRST in order to rectify the issue?
Which of the following authentication solutions use tickets that include valid credentials to access additional network resources?
Ann, a home user, wishes to confine a wireless network to devices ONLY inside of her house. Which of the following will accomplish this?
A company wants to only allow incoming HTTP and HTTPS traffic on their public wireless network. Which of the following port numbers should be the only allowed open ports on the firewall to accomplish this? (Select TWO).
A SOHO had their wireless network breached on several occasions. The user turned off the SSID and enabled WEP encryption, but breaches are still occurring. Which of the following will improve security and MOST likely prevent future breaches?
Which of the following BEST describes a firewall that can be installed via Add/Remove programs on a Windows computer?
An organization recently installed a firewall on the network. Employees must be able to send and receive email from a POP3 server. In which of the following ways should the firewall be configured? (Select TWO).
A user is connecting to the Internet at an airport through an ad-hoc connection. Which of the following is the MOST likely security threat?
A user enters a password into a logon box on a PC. The server and the PC then compare one-way hashes to validate the password. Which of the following methods uses this process?
A network administrator must ensure that both the server and the client are authenticated to the wireless system before access is granted. Which of the following should be implemented to meet this requirement?
A user does not have network connectivity. While testing the cable the technician receives the below reading on the cable tester:
1-----------1
2-----------2
3-----------3
4-----------4
5-----------5
6-----------6
7-----------7
8-----------8
Which of the following should the technician do NEXT?
A large corporate office is looking to place smaller network closets around campus to handle switching for remote workstations. To which of the following is this referring?
Lisa, a network technician, has determined that the initial theory of probable cause was incorrect. Which of the following would be the NEXT step in the troubleshooting process?
A company has only three laptops that connect to their wireless network. The company is currently using WEP encryption on their wireless network. They have noticed unauthorized connections on their WAP and want to secure their wireless connection to prevent this. Which of the following security measures would BEST secure their wireless network? (Select TWO).
Which of the following would be the BEST solution for an IDS to monitor known attacks?
Which of the following protocols would Lisa, a technician, use to disable switch ports automatically to prevent switching loops?
The process of restricting internal web traffic to an employee-only website based upon Layer 3 addresses is known as which of the following?
MIMO technology in the 802.11n standard provides for which of the following benefits?
An administrator determines that an attack is taking place on the email server from a group of users on the same ISP. Which of the following is the BEST way to mitigate an attack on the network?
A network administrator is responding to a statement of direction made by senior management to implement network protection that will inspect packets as they enter the network. Which of the following technologies would be used?
Joe, a network administrator, needs to forward HTTP traffic from a SOHO firewall public IP to the internal web server’s private IP. Which of the following can Joe implement?
A user receives a phone call at home from someone claiming to be from their company’s IT help desk. The help desk person wants to verify their username and password to ensure that the user’s account has not been compromised. Which of the following attacks has just occurred?
Lisa, an administrator, believes that the network has been attacked and there is no known definition or prevention method to help avoid this attack. Which of the following BEST describes this scenario?
Which of the following wireless security measures, although widely implemented, does not provide strong security?
A network technician has recently discovered rogue devices on their network and wishes to implement a security feature that will prevent this from occurring. Which of the following will prevent unauthorized devices from connecting to a network switch?
The company is setting up a new website that will be requiring a lot of interaction with external users. The website needs to be accessible both externally and internally but without allowing access to internal resources. Which of the following would MOST likely be configured on the firewall?
An administrator determines there are an excessive number of packets being sent to a web server repeatedly by a small number of external IP addresses. This is an example of which of the following attacks?
Network upgrades have been completed and the WINS server was shutdown. It was decided that NetBIOS network traffic will no longer be permitted. Which of the following will accomplish this objective?
Which of the following authentication solutions also provides AAA and uses TCP?
A technician tests a cable going to the patch panel and notices the following output from the cable tester:
1------------------1
2------------------2
3------------------3
4------------------4
5------------------5
6------------------6
7------------------7
8-- --8
On a T568A standard CAT5e cable, which of the following wire strands is the cause of this connectivity issue?
A technician is terminating a new run of network cables to a 110 block. Which of the following tools would the technician use?
Zach, a technician, is checking newly installed CAT5e cabling, and suspects that some of the ends were not properly terminated. Which of the following tools will verify this?
A company wants to simplify network authentication for their users. Which of the following would be used to implement wireless security with single sign-on?
A network technician has a RADIUS server IP address that must be included as part of the security settings for a WAP. Which of the following encryption types should the technician select?
Which of the following wiring components is used as a central point of termination for all network jacks through a building area?
Which of the following protocols provides a secure connection between two networks?
The network administrator just upgraded all of the WAPs to new ones with 2.4 GHz b/g/n support. The new WAPs reuse the same location and channel as the previous one and with no new external interference detected. However, performance issues are now occurring that did not exist before. Which of the following would correct the issue?
Which of the following protocols are used for accessing a command line terminal session for management purposes? (Select TWO).
Which of the following copper cable types should be chosen to run gigabit speeds through a dropped ceiling that returns airflow?
When installing new WAPs in a small office, which of the following is the BEST way to physically mitigate the threats from war driving?
A technician is setting up a firewall on the network that would show a public IP address out to the Internet and assign private IP addresses to users inside the network. Which of the following processes should be set up?
Which of the following is a fiber connector that is slightly smaller than a standard copper network cable connector?
Which of the following defines an IP address that is NOT routed on the Internet?
A technician has resolved a ticket to fix a user’s printer and has verified that the user is able to print with no issues. Which of the following action steps should the technician perform FIRST?
Lisa, a network technician, is attempting to map a FQDN to an internal server at the address of 10.0.0.15 without NAT/PAT. Which of the following is the reason this will ultimately not work?
Which of the following OSI layers performs error detection using a Frame Check Sequence?
Standards such as JPEG and ASCII operate at which of the following OSI model layers?
Which of the following services do TCP connections provide to application layer protocols? (Select TWO).
Joe, a technician, has identified a problem, established and confirmed a theory, and has attempted to resolve the problem. Joe, however, does not appear to have the rights to make the needed changes. Which of the following should he do NEXT?
A network consultant arrives at a customer’s site to troubleshoot their email server. The server is running a Linux operating system, but the consultant is only familiar with Windows operating systems. Which of the following troubleshooting steps should the consultant take?
A user reports intermittent network connectivity from their desktop PC. A technician determines the cause to be a bad wall jack and fixes the jack. Which of the following should the technician do NEXT?
After a new firewall is installed, users report that they do not have connectivity to the Internet. The output of the ipconfig command shows an IP address of 169.254.0.101. Which of the following ports would need to be opened on the firewall to allow the users to obtain an IP address? (Select TWO).
A crossover cable is MOST commonly associated with which of the following layers of the OSI model?
Users report that their Internet connection is slow. Zach, the network technician, has a suspicion that users are streaming video and music. Which of the following would BEST confirm Zach’s theory?
Which of the following network performance optimization methods allows for frequently accessed sites to be housed locally, thereby reducing bandwidth requirements?
Which of the following network scanners detects and sends out alerts for malicious network activity?
Which of the following utilities would Karen, a technician, use to resolve the FQDN of a web server to its IP address?
Which of the following would Karen, a technician, do to monitor remote traffic through an access point?
Sandy, a network technician, is troubleshooting connectivity to a server at a remote office. Which of the following utilities should be used to locate the network issue?
Lisa, an administrator, is experiencing availability issues on a Linux server. She decides to check the server for an IP address conflict on the server. Which of the following commands should Lisa use?
A technician is troubleshooting a computer that will not connect to the Internet. The PC is connected to the network. Which of the following tools should the technician use FIRST to understand the NIC configuration?
Which of the following should Kim, a technician, update when new computers are purchased?
An IT manager is looking for a solution that can easily trace back suspicious Internet browsing to particular users at a company. Which of the following can BEST provide this functionality?
Which of the following is used to explain guidelines for users while using network resources?
Lisa, an administrator, wants to limit the wireless guest network traffic to 100Kbps so that utilization issues do not occur on the company’s T1 Internet access network. Which of the following optimizations should Lisa implement?
Which of the following regulates the amount of network traffic a single node receives in a server cluster?
Due to a recent change in company policy, all users managing network infrastructure devices must use SSH v2 and all administrative activity must be collected on a central store. Which of the following should the network administrator deploy to comply with the new collection requirements?
A network technician is trying to run a protocol analyzer and is instructed to record the chimney offload state of TCP. Which of the following utilities did the technician use to check this parameter with the output listed below?
Querying active state...
TCP Global Parameters
----------------------------------------------
Receive-Side Scaling State : enabled
Chimney Offload State : disabled
Receive Window Auto-Tuning Level : normal
Add-On Congestion Control Provider : ctcp
ECN Capability : disabled
RFC 1323 Timestamps : disabled
Karen, a network technician, is troubleshooting in a wiring closet in 2011. The cabling to all the equipment does not match the documentation from 2007. Which of the following configuration management methods has been overlooked?
Users are reporting wired connectivity drops in a new office with brand new CAT6 infrastructure. Which of the following tools should a technician use to BEST troubleshoot this issue?
Which of the following are standard fiber cable connector types? (Select TWO).
In the 2.4GHz range, which of the following channel combinations are non-overlapping?
Which of the following connector types would Sandy, a network technician, use to connect a serial cable?
A network administrator tests a multimode fiber cable from end-to-end on a new link that is down and notices that the dB loss is -.09. Which of the following is the MOST likely cause?
Users notice a problem with their network connectivity when additional lights are turned on. Which of the following would be the cause for this problem?
Sandy, an administrator, needs to install a wireless network that will allow legacy devices to connect to the network and also offer both 5GHz and 2.4GHz frequencies. Which of the following would BEST describe the type of WAP needed?
Which of the following defines the pinout of an 8P8C eight pin modular jack for a CAT6a cable?
Which of the following are standard fiber cable connector types? (Select TWO).
When examining a suspected faulty copper network cable, Kim, the administrator, notices that some of the pairs are untwisted too much. This is MOST likely causing which of the following?
Lisa, an administrator, has been tasked with running cables from one office to another neighboring office by running cables over the light fixtures in the ceiling that connects them. To prevent interference, which of the following cable types should Lisa use?