H12-725_V4.0 HCIP-Security V4.0 Exam Questions and Answers
Predefined URL categories on Huawei firewalls reside in the URL category database delivered with the device and do not need to be manually loaded.
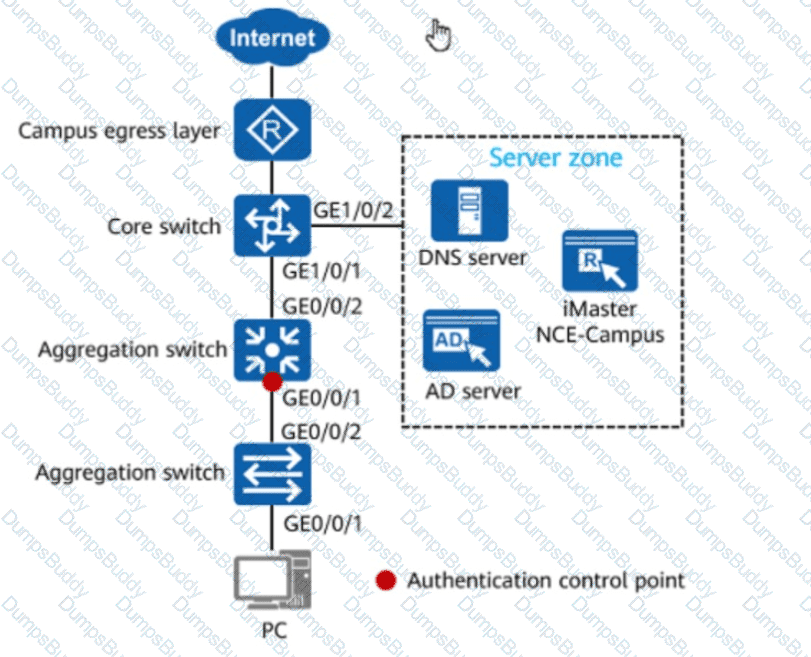
In the figure, if 802.1X authentication is used for wired users on the network, the network admission device and terminals must be connected through a Layer 2 network.
Options:
If a Portal authentication user goes offline but neither the access device nor the RADIUS server detects this event, many problems may occur. To prevent this from occurring, the access device needs to detect a user logout immediately, delete the user entry, and instruct the RADIUS server to stop accounting. Which of the following can trigger a Portal user logout?(Select All that Apply)
Before configuring DDoS attack defense, you must configure different thresholds for defense against different types of attacks. Each threshold can be considered an upper limit for normal network traffic. When the rate of traffic exceeds the pre-configured threshold, the firewall considers it to be attack traffic and takes a corresponding action to defend against it.
Which of the following operations can be performed to harden the Windows operating system?(Select All that Apply)
Trojan horses may disclose sensitive information of victims or even remotely manipulate victims' hosts, causing serious harm. Which of the following are the transmission modes of Trojan horses?(Select All that Apply)
*In the data filtering profile on the firewall, keyword group "Keyword" is invoked in the upload direction of HTTP applications, the action is block, and the keyword group is invoked in the security policy. Given this, if the regular expression "b.d" is configured in the keyword group "Keyword,” which of the following texts can be posted by internal employees on the forum?
Which of the following technologies does not belong to outbound intelligent uplink selection?
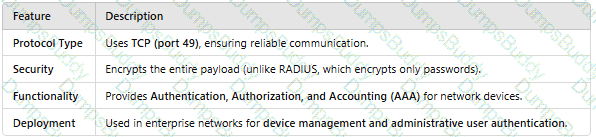
HWTACACS is a centralized information exchange protocol based on the client/server structure. It uses UDP for transmission and performs authentication, authorization, and accounting for users accessing the Internet through Point-to-Point Protocol (PPP) or Virtual Private Dial-up Network (VPDN) and administrative users logging in to devices.
When gateways are connected using GRE over IPsec, the IPsec encapsulation mode must be tunnel mode.
During deployment of Portal authentication, an authentication-free rule profile needs to be configured to ensure Portal pages can be opened on authentication terminals. To achieve this purpose, the following traffic needs to be permitted in the authentication-free rule profile: DNS resolution traffic of user terminals, traffic from user terminals for accessing Portal pages, and traffic from user terminals to the RADIUS server.
Which of the following protocols can be encapsulated through GRE over IPsec?(Select All that Apply)


 A screenshot of a computer
AI-generated content may be incorrect.
A screenshot of a computer
AI-generated content may be incorrect.

