H12-891_V1.0 HCIE-Datacom V1.0 Questions and Answers
Free mobility is deployed on a campus network through iMaster NCE-Campus. During this deployment, which of the following steps are performed by administrators and which are automatically performed by iMaster NCE-Campus? Drag the administrators and iMaster NCE-Campus icons on the left to the corresponding steps on the right.
On a small- or medium-sized campus network deployed based on the Huawei CloudCampus Solution, an AR functioning as the egress gateway supports web-based network management, registration center query, and DHCP Option 148-based deployment, but does not support CLI-based deployment.
MPLS supports Forwarding Equivalence Class (FEC). Which of the following cannot be used as a FEC allocation standard?
Which of the following statements are correct about authentication points and policy enforcement points in Huawei's free mobility solution?
MACsec can provide secure services during MAC-layer data transmitting and receiving. Which of the following services isnotprovided by MACsec?
In BGP4+, what is the content of the next hop network address field carried in the MP_REACH_NLRI attribute of an Update packet?
An enterprise has three types of services. Voice and video services are key services and need to be guaranteed, and FTP services are non-key services. Which of the following scheduling modes is optimal for satisfying the service requirements?
iMaster NCE-Campus restricts RESTful APIs. If a client sends aGET requestthat invokes a RESTful API to obtain site information from iMaster NCE-Campus, which of the following fields should be included in the request header?
The Ingress VTEP performs both Layer 2 and Layer 3 table lookup for packet forwarding. The forwarding mode is ______ IRB forwarding. (Capitalize the first letter.)
Which of the following statements is incorrect about the user authentication points on the network?
In the firewall hot standby scenario, when VGMP works in load balancing mode, which of the following functions must be enabled on the firewalls to prevent the return traffic from being discarded because it does not match any session entry in the case of inconsistent forward and return paths?
SR-MPLS uses IGP extensions to advertise labels and reserve bandwidth to support high-bandwidth services.
The telemetry network model is broadly and narrowly defined. Which of the following modules are involved intelemetry in a narrow sense (device-side telemetry)?
A carrier's home broadband service requires a maximum downstream bandwidth of 100 Mbit/s during off-peak hours and a guaranteed downstream bandwidth of 50 Mbit/s during peak hours. The home broadband service includes the home IP phone service and the home Internet access service. Which of the following configurations best meets the service requirement?
In the Huawei SD-WAN Solution, which of the following routing protocols is used to advertise VPN routes between CPEs?
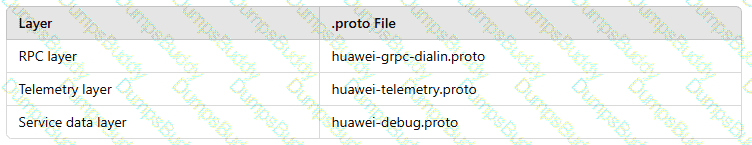
In the gRPC-based telemetry protocol, the data model layer consists of theRPC layer,telemetry layer, andservice data layer. Drag the.proto fileto the layer where the file should be located.
Which of the following inter-AS MPLS L3VPN solutions need VPN user data packets to carry MPLS labels when being forwarded between ASs?
Refer to the following command output on the router R3. Which of the following statements are correct?
Tunnel0/0/0 current state : UP
Line protocol current state : UP
Last line protocol up time : 15:21:26 UTC-08:00
Description: HUAWEI, AR Series, Tunnel0/0/0 Interface
Route Port, The Maximum Transmit Unit is 1500
Internet Address is 20.1.1.2/24
Encapsulation is TUNNEL, loopback not set
Tunnel source 10.0.3.3 (LoopBack0), destination 10.0.1.1
Tunnel protocol/transport GRE/IP, key disabled
keepalive disabled
Checksumming of packets disabled
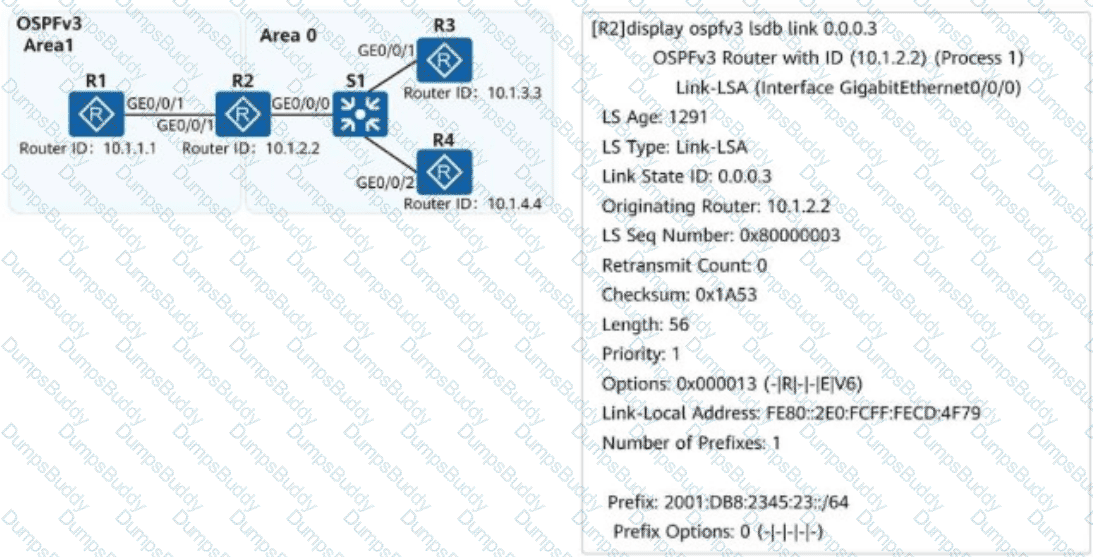
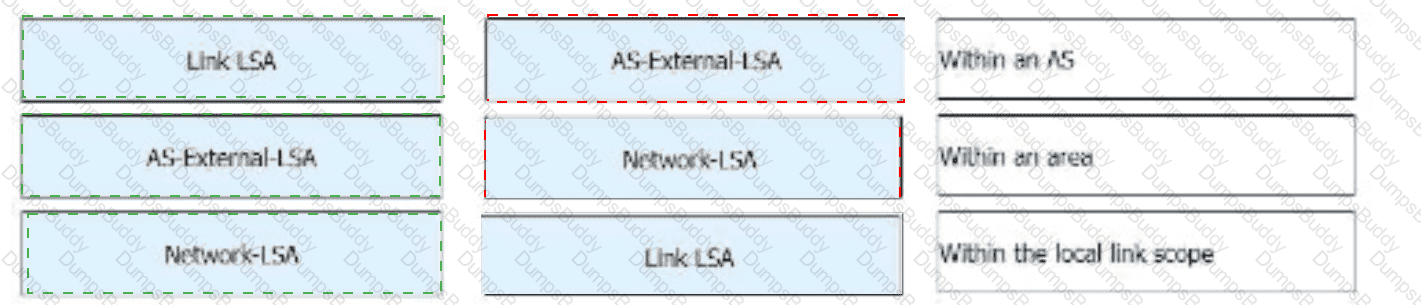
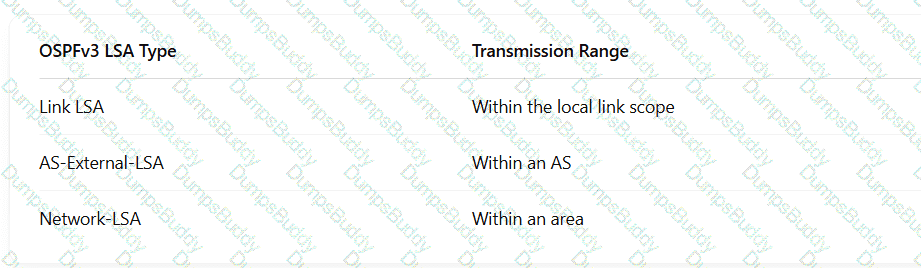
On the campus network shown, IPv6 is deployed for service tests. Four routers are deployed on the network, and OSPFv3 is used for IPv6 network connectivity. An engineer checks the LSDB of R2 and obtains a Link-LSA. Which of the following statements about the LSA are correct?
Which of the following can be used to transmit traffic to a VXLAN network and implement intra-subnet communication on the same VXLAN network?
Which of the following statements about the multicast address used by OSPFv3 are correct?
On a VXLAN-based virtualized campus network, BGP EVPN can be used as the control plane protocol. Which of the following EVPN route types are not used in the virtualized campus network scenario?
In 6PE networking, the shared explicit null label function can be enabled on routers to reduce the number of required MPLS labels. With this function, a router assigns a label with the value (enter only digits) to all 6PE routes.
The channelized sub-interface and FlexE technologies both can be used to implement network slicing, but the application scenarios of the two technologies are slightly different. Which of the following statements about the two technologies are correct?
If ISIS is used to transmit SIDs on an SR network, the node SIDs advertised by a Level-2 router are transmitted only within the same area.
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, which of the following BGP EVPN routes is used to advertise MAC addresses, ARP entries, and IRB routes?
Which of the following protocols is used in the Huawei SD-WAN Solution to report device performance data?
Refer to the following command output on the router R1. Which of the following statements isincorrect?
Tunnel0/0/0 current state : UP
Line protocol current state : UP
Last line protocol up time : 15:21:23 UTC-08:00
Description: ! 0.0.3.3
Route Port, The Maximum Transmit Unit is 1500
Internet Address is 20.1.1.1/24
Encapsulation is TUNNEL, loopback not set
Tunnel source 10.0.1.1 (LoopBack0), destination 10.0.3.3
Tunnel protocol/transport GRE/IP, key disabled
keepalive disabled
Checksumming of packets disabled
Current system time: 15:21:37-08:00
300 seconds input rate 0 bits/sec, 0 packets/sec
300 seconds output rate 0 bits/sec, 0 packets/sec
13 seconds input rate 0 bits/sec, 0 packets/sec
13 seconds output rate 448 bits/sec, 0 packets/sec
9 packets output, 824 bytes
0 output error
Input bandwidth utilization : -
Output bandwidth utilization : -
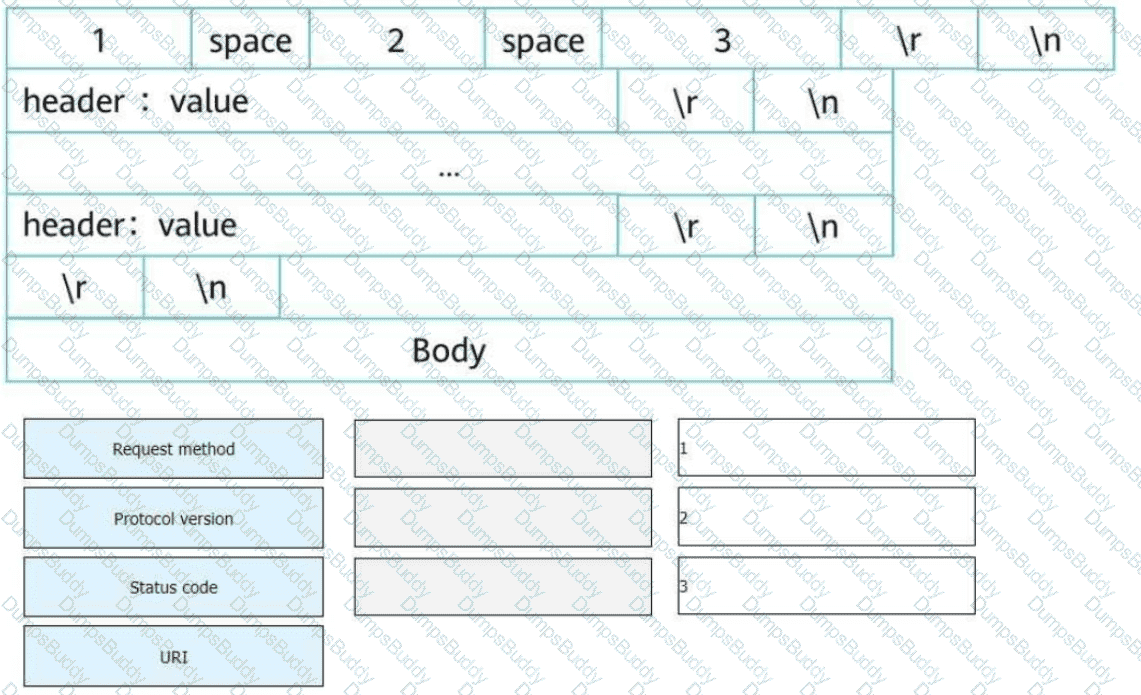
An HTTP request line consists of three fields. Select the fields to form a complete HTTP request message.
The naming of SRv6 instructions complies with certain rules. You can quickly determine the function of an instruction based on the instruction name. Which of the following statements about the keywords in SRv6 instruction names are correct?
MPLS implements data forwarding based on two different planes. Which of the following statements regarding the forwarding mechanism are correct?
To obtain the token ID of iMaster NCE, you need to send an HTTP request message that includes the following Python code to invoke an iMaster NCE RESTful API.
Which of the following statements is incorrect?
import requests
nbi_name = "demo13@north.com"
nbi_pwd = "CgocVcVe1@"
host = "139.9.213.72"
port = "18002"
URI = "/controller/v2/tokens"
post_token_url = "https:// " + host + ":" + port + URI
headers_post = {"Content-Type": "application/json", "Accept": "application/json"}
r = requests.post(post_token_url, headers=headers_post, json={"userName": nbi_name, "password": nbi_pwd}, verify=False)
Telemetry is a technology that remotely collects data from physical or virtual devices at high speed, and has a layered protocol stack. Which of the following layers isnotincluded in the telemetry protocol stack?
When you configure a virtualized campus network on iMaster NCE-Campus and enable external networks to connect to the Internet, iMaster NCE-Campus will automatically deliver a specific route to direct traffic to the corresponding external network.
How long is an IPv6 prefix assigned to a host when an IPv6 address is configured for the host in SLAAC mode?
On a virtualized network deployed using iMaster NCE-Campus, after creating VNs, you need to configure inter-VN communication. Which of the following configurations is used to achieve VN communication?
Which of the following statements aboutprefix segments and adjacency segmentsare correct?
Which of the following statements about the SP scheduling algorithm isincorrect?
On a campus network, which of the following problems may occur when you manually create a static VXLAN tunnel?
During WLAN planning and design, channels 1, 6, and 11 are recommended on the 2.4 GHz frequency band, and channels 1, 5, 9, and 13 are recommended in high-density scenarios. On the 5 GHz frequency band, it is recommended thathigh-frequency and low-frequency channels of adjacent APs be staggered to prevent overlapping.
The BGP ORF function can be used to control the maximum number of routes that can be sent by a BGP peer. To achieve this, which of the following tools is used to send such a route list to BGP peers?
Which of the following factors does not need to be considered during the selection of core devices for the enterprise bearer WAN?
Among NETCONF operations, the
The free mobility function is deployed on the iMaster NCE-Campus on a campus network. Which of the following information should an administrator pay attention to?
By default, the domain ID of an OSPF process is the same as the process ID. You can run the domain-id command in the OSPF process view to change a domain ID.
Which of the following statements aboutSR-MPLS Policy path planningare correct?
When configuring a static VXLAN tunnel, you need to manually configure the _____, VTEP IP address, and ingress replication list. (Enter only uppercase letters.)
O&M personnel for a large-scale event center receive feedback about Wi-Fi access failures. iMaster NCE-CampusInsight provides the function for personnel to view packet exchange processes and locate the root cause. It is found that IP addresses in the DHCP address pool are exhausted, preventing IP addresses from being assigned to mobile terminals. Which of the following functions is used by O&M personnel in this scenario?
Which of the following methods can be used to establish IPsec SAs? (Select All that Apply)
In the admission design for large- and medium-sized campus networks, which of the following authentication modes can be used for PCs connected to IP phones?
On a CloudCampus virtualized campus network, service data enters different VNs from physical networks through edge nodes, and the VN that the data will enter is determined by the VLANs to which users belong. Which of the following statements about dynamic VLAN authorization is incorrect?
 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.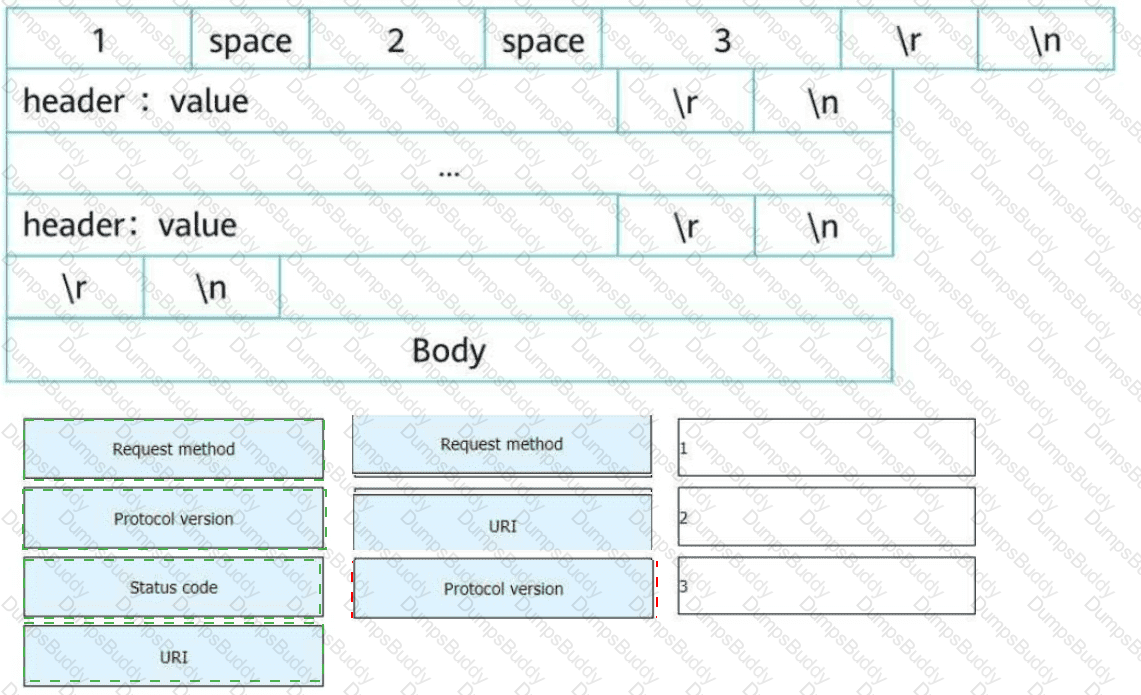

 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.

