H12-724 HCIP-Security (Fast track) V1.0 Questions and Answers
Which of the following equipment is suitable for use MAC Authentication access network?
The application behavior control configuration file takes effect immediately after being referenced, without configuration submission.
In the campus network, employees can use 802.1X, Portal,MAC Address or SACG Way to access. Use different access methods according to different needs to achieve the purpose of user access control.
Which of the following descriptions about the black and white lists in spam filtering is wrong? c
Fage attack means that the original address and target address of TOP are both set to the IP address of a certain victim. This behavior will cause the victim to report to it.
SYN-ACK message is sent from the address, and this address sends back an ACK message and creates an empty connection, which causes the system resource board to occupy or target
The host crashed.
Free mobility is a special access control method, according to the user’s access location, access time, access method and terminal authorization instructions. Set permissions, as long as the user’s access conditions remain unchanged, the permissions and network experience after accessing the network--To q
Which of the following technology, administrators can according to business requirements, to scale to achieve load sharing of business flow?
The whitelist rule of the firewall anti-virus module is configured as ("*example*, which of the following matching methods is used in this configuration?
Regarding the statement of the mail protocol, which of the following is correct? (multiple choice)
When configuring the URL filtering configuration file, www.bt.com is configured in the URL blacklist-item: At the same time, set it in the custom URL category.
A URL is set as bt.com, and the action of customizing URL classification is a warning. Regarding the above configuration, which of the following statements are correct? (More
select)
Deploying on Windows platform, using SQL Server database About the HA function of Agile Cotoller-Campus, which of the following descriptions Is it correct? (multiple choice)
For the convenience of visitors, different authentication and master pages can be distributed for different visitors. When configuring the push page strategy, different matching conditions need to be defined, so which of the following options can be used as the limited matching conditions? (Multiple choice)
On WIDS functional WLAN Regarding the judgment of illegal devices in the network, which of the following statements are correct? (Multiple choice)
The terminal host access control function does not take effect, the following is SACG View information on:
Advanced ACL 3099 ,25 rules,not bingding with vpn-instance Ad's step is 1
rule 1000 permit ip (1280 times matched)
rule 1001 permit ip destination 172.18.11.2210 (581 times matched)
rule 1002 permit ip destination 172:18.11.2230 (77 times matched)
rule 1003 permit ip destination 172.19.0.0 0.0 255.255 (355 Book times matched)
rule 1004 deny ip (507759 times matched)
Which of the following statements is correct?
Intrusion detection is a network security technology used to detect any damage or attempt to damage the confidentiality, integrity or availability of the system. Which of the following
What is the content of the intrusion detection knowledge base?
The analysis and processing capabilities of traditional firewalls at the application layer are weak, and they cannot correctly analyze malicious codes that are mixed in the flow of allowed application teaching: many Attacks or malicious behaviors often use the firewall's open application data flow to cause damage, causing application layer threats to penetrate the firewall
A True
B. False
With regard to APT attacks, the attacker often lurks for a long time and launches a formal attack on the enterprise at the key point of the incident.
Generally, APT attacks can be summarized into four stages:
1. Collecting Information & Intrusion
2. Long-term lurking & mining
3. Data breach
4. Remote control and penetration
Regarding the order of these four stages, which of the following options is correct?
In the big data intelligent security analysis platform, it is necessary to collect data from data sources, and then complete a series of actions such as data processing, detection and analysis, etc.
do. Which of the following options does not belong to the action that needs to be completed in the data processing part?
155955cc-666171a2-20fac832-0c042c0422
Regarding the file source set in the software management, which of the following descriptions is correct?
When a guest needs to access the network through an account, which of the following methods can be used to access? (Multiple choice)
The following figure is a schematic diagram of the detection file of the firewall and the sandbox system linkage.
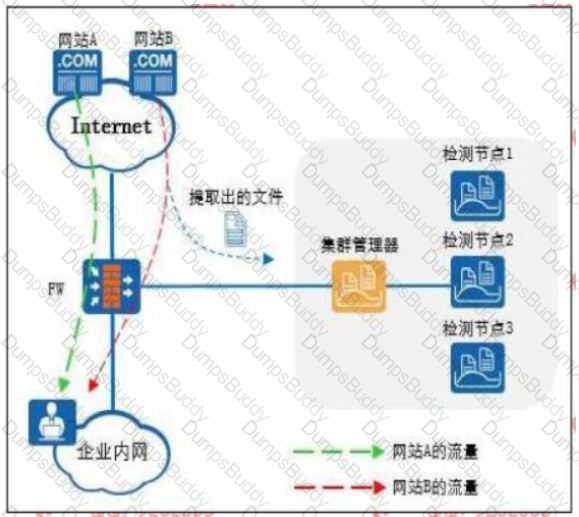
The Web reputation function is enabled on the firewall, and website A is set as a trusted website and website B is set as a suspicious website.
Which of the following statements is correct
Among the following options, which attack is a malformed packet attack based on the TCR protocol?
The core technology of content security lies in anomaly detection, and the concept of defense lies in continuous monitoring and analysis.
Anti DDoS seven-layer defense can work from the dimensions of interface-based defense, global defense and defense object-based defense.
Server Fault information collection tool Server Collector, which of the following does collected information items not include?
Import the user information of the AD server on the Agile Controller-Campus to realize the user's access authentication. If the user is in the Agile.
The user information is not found on the Controller-Campus. Which of the following actions will be performed in the next step?
For the description of the principles of HTTP Flood and HTTPS Flood blow defense, which of the following options are correct? (multiple choice)
Which of the following options does not belong to the basic DDoS attack prevention configuration process?
Which of the following options belong to the keyword matching mode? (multiple choice)
Viruses can damage computer systems. v Change and damage business data: spyware collects, uses, and disperses sensitive information of corporate employees.
These malicious pastoral software seriously disturb the normal business of the enterprise. Desktop anti-disease software can solve the problem of central virus and indirect software from the overall situation.
In the construction of information security, the intrusion detection system plays the role of a monitor. It monitors the flow of key nodes in the information system.
In-depth analysis to discover security incidents that are occurring. Which of the following are its characteristics?. c0O
URL filtering technology can perform URL access control on users according to different time objects and address objects to achieve precise management of users.
The purpose of the Internet behavior.
Web Standards that come with the client and operating system 8021 The instrument client only has the function of identity authentication: It does not support the execution of inspection strategies and monitoring strategies. Any Office The client supports all inspection strategies and monitoring strategies.
The administrator issues notices to users in the form of announcements, such as the latest software and patch installation notices. Which of the following options of the announcement is incorrect?
Regarding the definition of WIPS/WIDS, which of the following statements is correct?
If the processing strategy for SMTP virus files is set to alert, which of the following options is correct?
For SYIN Flood attacks, TCP source authentication and TCP proxy can be used for defense. Which of the following descriptions is correct?
Since the sandbox can provide a virtual execution environment to detect files in the network, the sandbox can be substituted when deploying security equipment
Anti-Virus, IPS, spam detection and other equipment.
According to different reliability requirements, centralized networking can provide different reliability networking solutions. Regarding these solutions, which of the following descriptions are correct? (Multiple choice)
Regarding the application scenarios of Agile Controller-Campus centralized deployment and distributed deployment, which of the following options are correct? (Multiple select)
Based on the anti-virus gateway of streaming scan, which of the following descriptions is wrong?
Content filtering is a security mechanism for filtering the content of files or applications through Huawei USCG00 products. Focus on the flow through deep recognition
Contains content, the device can block or alert traffic containing specific keywords.
There are several steps in a stored XSS attack
①The attacker hijacks the user session
②The attacker submits an issue containing known JavaScript
③User login
④The user requests the attacker's question 5
⑤The server responds to the attacker’s JavaScript
⑥ The user's browser sends a session token to the attacker
⑦The attacker's JavaScript is executed in the user's browser
For the ordering of these steps, which of the following options is correct?
Which of the following options is correct for the description of the Anti DDoS system configuration?
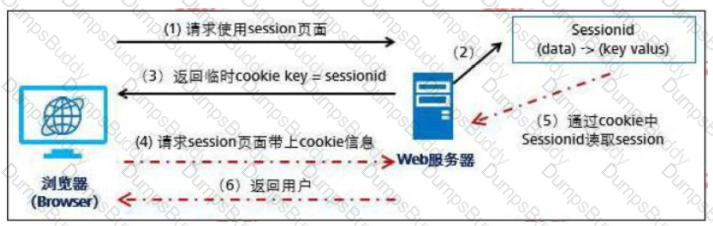
The process of a browser carrying a cookie to request resources from a server is shown in the following figure. Which of the following steps contains SessionID information in the message?
Which of the following options is about Portal The description of the certification process is correct?
Regarding the policy for checking account security, which of the following descriptions are correct? (Multiple choice)
An enterprise has 3 server, which is the most reasonable plan when deploy Policy Center system
planning?


