H12-721 Huawei Certified ICT Professional - Constructing Infrastructure of Security Network Questions and Answers
The following figure shows the L2TP over IPSec application scenario. The client uses the pre-shared-key command to perform IPSec authentication. How should the IPSec security policy be configured on the LNS?
Connecting the internal network interface address from the firewall By pinging the internal network address of the peer, the IPSec tunnel can be successfully triggered. The internal PC cannot trigger the tunnel establishment. What are the possible reasons?
The NAT/ASPF log in the session log and the DPI traffic monitoring log provide a “binary” output technology for this type of log. The use of binary input output can greatly reduce the impact on system performance, but The binary form output needs to be configured with the elog log management system.
In the USG firewall, which two commands can be used to view the running status and memory/CPU usage of the device components (main control board, board, fan, power supply, etc.)?
The SSL VPN authentication login is unsuccessful and the message "Bad username or password" is displayed. Which one is wrong?
In the client-initial mode, the L2TP dialup fails. From the debug information below, it can be seen that the most likely cause is the dialup failure.
Which of the following statements is correct about the IKE main mode and the aggressive mode?
What are the scenarios in which the USG series firewall service port sends gratuitous ARPs when the following configurations are performed?
In the TCP/IP protocol, the TCP protocol provides a reliable connection service, which is implemented using a 3-way handshake. First handshake: When establishing a connection, the client sends a SYN packet (SYN=J) to the server and enters the SYN_SENT state, waiting for the server to confirm; the second handshake: the server receives the SYN packet and must send an ACK packet (ACK=1) To confirm the SYN packet of the client, and also send a SYN packet (SYN=K), that is, the SYN-ACK packet, the server enters the SYN_RCVD state; the third handshake: the client receives the SYN-ACK packet of the server. Send the acknowledgement packet ACK (SYN=2 ACK=3) to the server. After the packet is sent, the client and server enter the ESTABUSHED state and complete the handshake. Regarding the three parameters in the 3-way handshake process, which one is correct?
Virtual firewall virtualizes multiple logical firewalls on a physical firewall device and implements multiple instances?
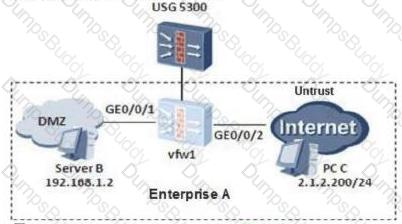
On the following virtual firewall network, the USG unified security gateway provides leased services to the enterprise. The VPN instance vfw1 is leased to enterprise A. The networking diagram is as follows. The PC C of the enterprise A external network user needs to access the intranet DMZ area server B through NAT. To achieve this requirement, what are the following key configurations?
Two USG firewalls establish an IPSec VPN through the Site to Site mode. When viewing the status of a USG A, the following is displayed: display ipsec statistics the security packet statistics: input/output security paskets: 40 input/output security bytes: 400/0 input /output dropped security packets: 0/0 By status information, what information can be obtained correctly?
L2TP is a tunneling protocol set up for transparent transmission of PPP packets between users and enterprise servers. Which of the following features are included?
In the IDC room, a USG firewall can be used to divide into several virtual firewalls, and then the root firewall administrator generates a virtual firewall administrator to manage each virtual firewall.
In the abnormal traffic cleaning solution, to ensure that the attack traffic can be imported into the cleaning center for cleaning, the VRRP is implemented in Step 12 as shown in the figure. The management center adopts the following configuration: Select Configuration-->Anti-DDoS- -> "Drainage management", create a drainage task, configure the protected IP address to 10.1.3.10/32. What kind of route will the cleaning center generate after the above steps are configured?
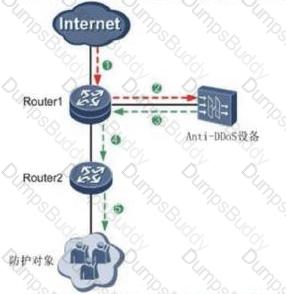
What are the drainage schemes that can be used in the scenario of bypass deployment in Huawei's abnormal traffic cleaning solution?
An enterprise network is as follows. At this time, server A cannot access server B. The administrator performs troubleshooting. It finds that server A can access firewall A, but cannot access firewall B. What is the method for administrators to use to troubleshoot problems?

In the L2TP over IPSec application scenario, the USG device encrypts the original data packet with IPSec and then encapsulates the packet with L2TP.
Which of the following protocol messages cannot be propagated in an IPSec tunnel by default?
Which of the following does the virtual firewall technical feature not include?
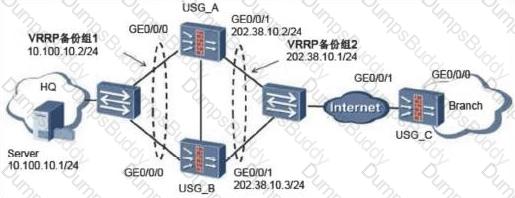
What are the correct statements about the following VRRP and VGMP protocol messages?
In the IPSec VPN, the digital certificate is used for identity authentication. If the IKE main mode is used for negotiation, the certificate verification is completed in message 5 and message 6.
87. The SSL VPN scenario under dual-system hot standby is shown in the following figure. The administrator has enabled the SSL network extension function. The following is about the configuration of the SSL VPN function.
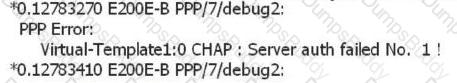
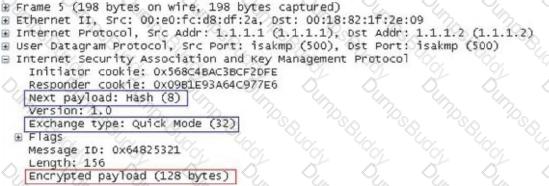
In the IKE V1 pre-shared key mode, what is the main role of the data captured in the following figure?
The administrator can create vfw1 and vfw2 on the root firewall to provide secure multi-instance services for enterprise A and enterprise B, and configure secure forwarding policies between security zones of vfw1 and vfw2.
The principle of HTTPS Flood source authentication defense is that the Anti-DDoS device replaces the SSL server with the client to complete the TCP three-way handshake. If the TCP three-way handshake is complete, the HTTPS flood source authentication check is successful.
The hot standby and IPSec functions are combined. Which of the following statements is correct?


