The LDP session establishment process will go through the opensent status. Which state will the opensent state change to after the device receives an Initialization message and sends a Keepalive message?
Which of the following statements regarding Network Address and Port Translation (NAFT) and No Port Translation (No-PAT) is true?
Which of the following is not included in the three elements of Servermap table on the USG series firewall?
When BFD is not used, the OSPF neighbor relationship that is established through the Ethernet link is terminated after 40s upon a link fault.
For interzone packet filtering, which traffic is belong to transmitted to outbound direction?
Which of the following statements regarding data forwarding on a traditional IP network are true? (Multiple Choice)
MPLS can forward packets only after an LSP is established. Which of the following statements regarding static LSP establishment are true? (Multiple Choice)
In the MPLS VPN, RD values are added to IPv4 addresses to distinguish IPv4 prefixes with the same address space. Which of the following statements are true? (Multiple Choice)
Congestion management technology defines scheduling policies to determine the order of packet processing sequence.
MPLS is short for Multiprotocol Label Switching, so the core technology of MPLS is label switching.
When the IP address of an interface on a firewall is pinged/ ping packets are processed by the internal module of the firewall but are not forwarded,
Man-in-the-middle attacks or IP/MAC Spoofing attacks are common on intranets and will cause information leakage. Which configuration method can prevent these attacks?
Which of the port mirroring modes are supported by Huawei S series switches? (Multiple Choice)
SDN and NFV are essentially the same concept and both define network function visualization.
LR can be used on a physical interface to limit the total rate of sent packets including packets of burst traffic.
Complex traffic classification means that packets are classified based on the quintuple including the source and destination addresses, source and destination port numbers, and protocol type. It is usually deployed on the network core.
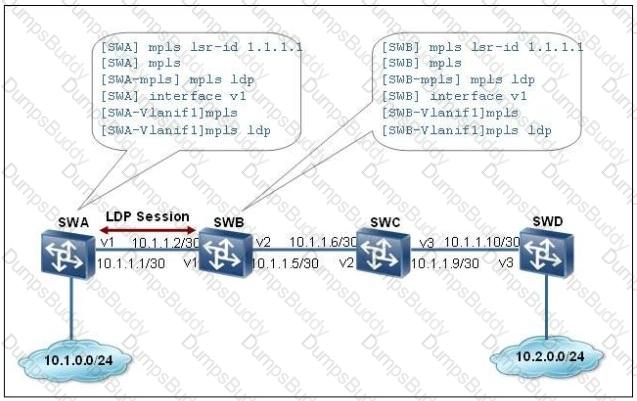
On the network shown in the following figure, a MPLS LSP is configured and a local LDP session is established between SWA and SWB. Which of the following statements is true?
Which of the following statements regarding the characteristics of HA network are true? (Multiple Choice)
MPLS forwards data packets based on labels. How is IP packets passing through the MPLS domain forwarded if they do not carry any label?
LDP is dedicated for label distribution and supports multiple message types. Which of the following messages is used to create, change, or delete label mapping messages for FECs?
Which of the following are label distribution control modes in the MPLS system? (Multiple Choice)
The traditional tail drop method is used for packet loss, which causes global TCP synchronization.
During the DHCP interaction process, the DHCP server and client exchange various types of packets. Which of the following packets is not sent from the client to the server?
To avoid global TCP synchronization, which congestion avoidance mechanisms can be used? (Multiple Choice)
Which of the following statements regarding Huawei eSight network management software is false?
Which of the following steps are required when configuring a DHCP relay agent? (Multiple Choice)
Besides resource discovery, allocation, and management, which function else does the VIM management module of NFV provide?
Which of the following items is not the disadvantage of the traditional congestion avoidance mechanism (tail drop)?
What about all outgoing labels in the label forwarding table of a MPLS-capable device for different routes with the same next hop?
Which of the following statements regarding the free mobility application scenario of the Agile Controller is false?