NSE6_FML-7.2 Fortinet NSE 6 - FortiMail 7.2 Questions and Answers
Refer to the exhibit, which shows an inbound recipient policy.
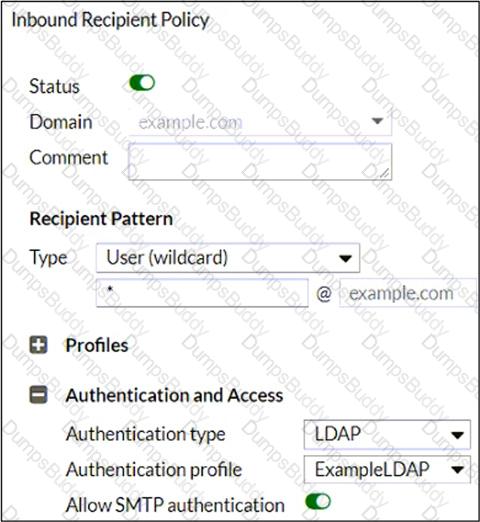
After creating the policy shown in the exhibit, an administrator discovers that clients can send unauthenticated emails using SMTP.
What must the administrator do to enforce authentication?
Refer to the exhibit, which shows a few lines of FortiMail logs.
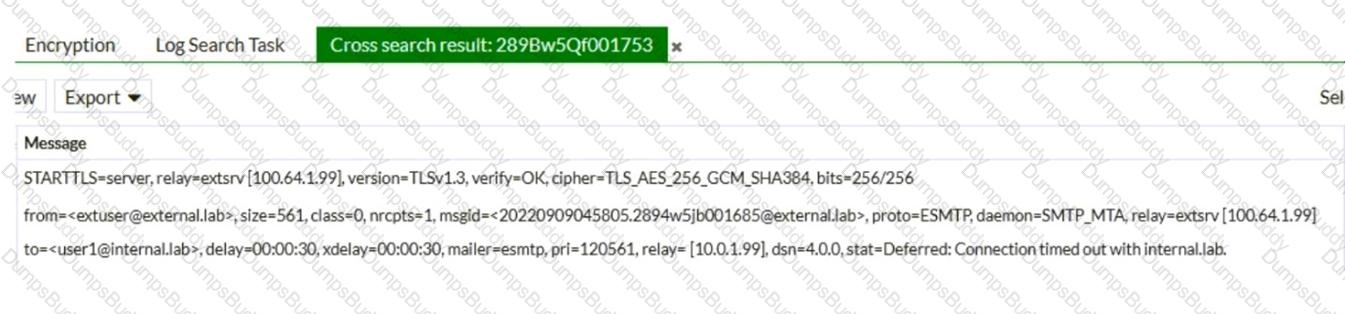
Based on these log entries, which two statements correctly describe the operational status of this FortiMail device? (Choose two.)
A FortiMail device is configured with the protected domain example.com.
If none of the senders is authenticated, which two envelope addresses will require an access receive rule? (Choose two.)
Refer to the exhibit which shows a detailed history log view.
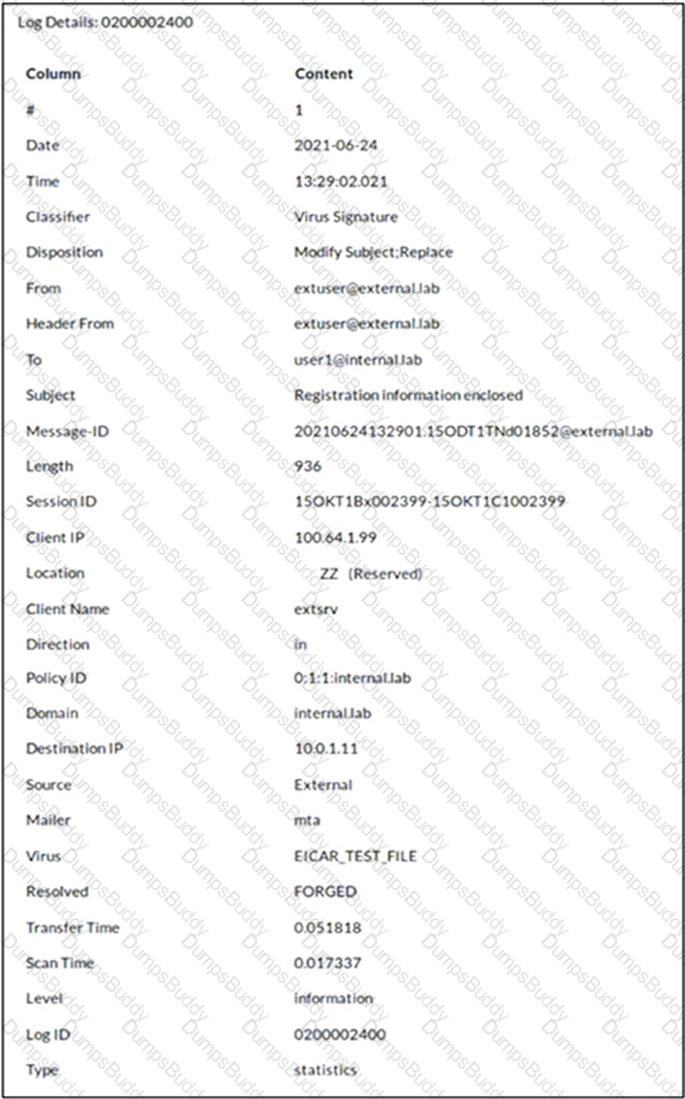
Which two actions did FortiMail take on this email message? (Choose two.)
Which two FortiMail antispam techniques can you use to combat zero-day spam? (Choose two.)
Refer to the exhibits which show a topology diagram (Topology), and a configuration element (Access Control Rule).
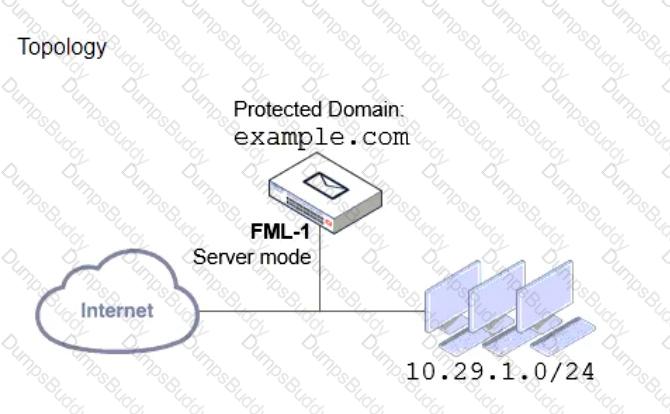
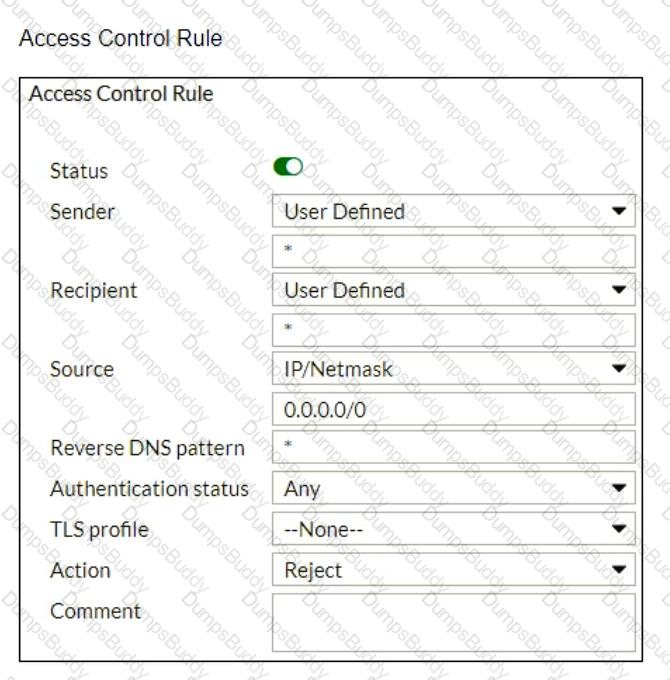
An administrator must enforce authentication on FML-1 for all outbound email from the example.com domain.
Which two settings should be used to configure the access receive rule? (Choose two.)


