- Home
- Forescout
- Forescout Certified Professional
- FSCP
- Forescout Certified Professional Exam Questions and Answers
FSCP Forescout Certified Professional Exam Questions and Answers
How can a specific event detected by CounterACT (such as a P2P compliance violation event) be permanently recorded with a custom message for auditing purposes?
Options:
Customize the message on the send syslog action
Increase the "Purge Inactivity Timeout" setting
Customize the message in the Reports Portal
Configure a custom SNMP trap to be sent
Customize the message in the syslog configuration in Options > Core Ext > Syslog
Answer:
AExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide and Syslog Plugin Configuration Guide, specific events detected by CounterACT can be permanently recorded with a custom message for auditing purposes by customizing the message on the send syslog action.
Send Message to Syslog Action:
According to the official documentation:
"You can send customized messages to Syslog for specific endpoints using the Forescout eyeSight Send Message to Syslog action, either manually or based on policies."
How to Configure Custom Messages:
According to the Syslog Plugin Configuration Guide:
Create or Edit a Policy - Select a policy and edit the Main Rule section
Add an Action - In the Actions section, select "Add"
Select Send Message to Syslog - From the Audit folder, select "Send Message to Syslog"
Customize the Message - Specify the custom message to send when the policy is triggered
Custom Message Configuration:
According to the documentation:
When configuring the "Send Message to Syslog" action, you specify:
Message to syslog - Type a custom message to send to the syslog server when the policy is triggered
Message Identity - Free-text field for identifying the syslog message
Syslog Server Address - The syslog server to receive the message
Syslog Server Port - Typically port 514
Syslog Server Protocol - TCP or UDP
Syslog Facility - Message facility classification
Syslog Priority - Severity level (e.g., Info)
Example Implementation for P2P Compliance Violation:
According to the configuration guide:
For a P2P compliance violation event, you would:
Create a policy that detects P2P traffic violations
Add a "Send Message to Syslog" action
Customize the message to something like: "P2P VIOLATION: Endpoint [IP] detected unauthorized P2P application traffic"
Configure the syslog server details
When the condition is triggered, CounterACT sends the custom message to syslog for permanent auditing
Permanent Recording:
According to the documentation:
The messages sent to syslog are:
Permanently recorded on the syslog server
Timestamped automatically by Forescout and/or the syslog server
Available for audit trails and compliance reports
Can be forwarded to SIEM systems like Splunk or EventTracker for further analysis
Why Other Options Are Incorrect:
B. Increase the "Purge Inactivity Timeout" setting - This relates to device timeout, not event recording or custom messages
C. Customize the message in the Reports Portal - The Reports Portal displays reports but does not customize messages for syslog events
D. Configure a custom SNMP trap - SNMP traps are for network device management, not for recording Forescout events
E. Customize the message in the syslog configuration in Options > Core Ext > Syslog - While syslog configuration is done here, the actual custom messages are configured in the "Send Message to Syslog" action within policies
Referenced Documentation:
How-To Guide: ForeScout CounterAct to forward logs to EventTracker
Audit Actions documentation
How to Work with the Syslog Plugin
Send Message to Syslog Action documentation
Which of the following actions can be performed with Remote Inspection?
Options:
Set Registry Key, Disable dual homing
Send Balloon Notification, Send email to user
Disable External Device, Start Windows Updates
Start Secure Connector, Attempt to open a browser at the endpoint
Endpoint Address ACL, Assign to VLAN
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout HPS Inspection Engine Configuration Guide Version 10.8 and the Remote Inspection and SecureConnector Feature Support documentation, the actions that can be performed with Remote Inspection include "Start Secure Connector" and "Attempt to open a browser at the endpoint".
Remote Inspection Capabilities:
According to the documentation, Remote Inspection uses WMI and other standard domain/host management protocols to query the endpoint, and to run scripts and implement remediation actions on the endpoint. Remote Inspection is agentless and does not install any applications on the endpoint.
Actions Supported by Remote Inspection:
According to the HPS Inspection Engine Configuration Guide:
The Remote Inspection Feature Support table lists numerous actions that are supported by Remote Inspection, including:
Set Registry Key -✓Supported by Remote Inspection
Start SecureConnector -✓Supported by Remote Inspection
Attempt to Open Browser -✓Supported by Remote Inspection
Send Balloon Notification -✓Supported (requires SecureConnector; can also be used with Remote Inspection)
Start Windows Updates -✓Supported by Remote Inspection
Send Email to User -✓Supported action
However, the question asks which actions appear together in one option, and Option D correctly combines two legitimate Remote Inspection actions: "Start Secure Connector" and "Attempt to open a browser at the endpoint".
Start SecureConnector Action:
According to the documentation:
"Start SecureConnector installs SecureConnector on the endpoint, enabling future management via SecureConnector"
This is a supported Remote Inspection action that can deploy SecureConnector to endpoints.
Attempt to Open Browser Action:
According to the HPS Inspection Engine guide:
"Opening a browser window" is a supported Remote Inspection action
However, there are limitations documented:
"Opening a browser window does not work on Windows Vista and Windows 7 if the HPS remote inspection is configured to work as a Scheduled Task"
"When redirected with this option checked, the browser does not open automatically and relies on the packet engine seeing this traffic"
Why Other Options Are Incorrect:
A. Set Registry Key, Disable dual homing - While Set Registry Key is supported, "Disable dual homing" is not a standard Remote Inspection action
B. Send Balloon Notification, Send email to user - Both are notification actions, but the question seeks Remote Inspection-specific endpoint actions; these are general notification actions not specific to Remote Inspection
C. Disable External Device, Start Windows Updates - While Start Windows Updates is supported by Remote Inspection, "Disable External Device" is not a Remote Inspection action; it's a network device action
E. Endpoint Address ACL, Assign to VLAN - These are Switch plugin actions, not Remote Inspection actions; they work on network device level, not endpoint level
Remote Inspection vs. SecureConnector vs. Switch Actions:
According to the documentation:
Remote Inspection Actions (on endpoints):
Set Registry Key on Windows
Start Windows Updates
Start Antivirus
Update Antivirus
Attempt to open browser at endpoint
Start SecureConnector (to deploy SecureConnector)
Switch Actions (on network devices):
Endpoint Address ACL
Access Port ACL
Assign to VLAN
Switch Block
Referenced Documentation:
Forescout CounterACT Endpoint Module HPS Inspection Engine Configuration Guide Version 10.8
Remote Inspection and SecureConnector – Feature Support documentation
Set Registry Key on Windows action documentation
Start Windows Updates action documentation
Send Balloon Notification documentation
The host property 'HTTP User Agent banner' is resolved by what function?
Options:
Device classification engine
NetFlow
NMAP scanning
Packet engine
Device profile library
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide - Advanced Classification Properties, the host property "HTTP User Agent banner" is resolved by the Packet Engine.
HTTP User Agent Banner Property:
According to the Advanced Classification Properties documentation:
The HTTP User Agent property is captured through passive network traffic analysis by the Packet Engine, which monitors and analyzes HTTP headers in network traffic.
Packet Engine Function:
According to the Packet Engine documentation:
The Packet Engine provides:
Passive Traffic Monitoring - Analyzes network packets without interfering
HTTP Header Analysis - Extracts HTTP headers from captured traffic
User Agent Detection - Identifies HTTP User Agent strings from web requests
Property Resolution - Populates device properties from observed traffic
HTTP User Agent Examples:
Common User Agent banners that identify device types and browsers:
text
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36
Mozilla/5.0 (iPhone; CPU iPhone OS 14_6 like Mac OS X) AppleWebKit/605.1.15
Mozilla/5.0 (Linux; Android 11; SM-G991B) AppleWebKit/537.36
Why Other Options Are Incorrect:
A. Device classification engine - The classification engine uses properties resolved by other components like the Packet Engine
B. NetFlow - NetFlow provides flow statistics, not application-level data like HTTP headers
C. NMAP scanning - NMAP performs active port scanning, not passive HTTP header analysis
E. Device profile library - The profile library uses properties; it doesn't resolve them
Property Resolution by Function:
According to the documentation:
Property
Packet Engine
NMAP
Device Class Engine
Profile Library
HTTP User Agent
✓Yes
✗No
✗No
✗No
Service Banner
✗No
✓Yes
✗No
✗No
OS Classification
Partial
Partial
✓Yes
✗No
Function
✗No
✗No
✓Yes
✓Yes
Referenced Documentation:
Advanced Classification Properties
About the Packet Engine
Forescout Platform Dependencies and Known Issues
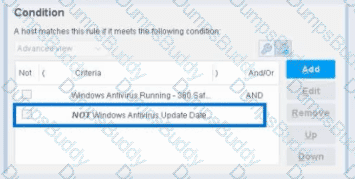
When configuring policies, which of the following statements is true regarding the indicated property?
Select one:
Options:
Irresolvable hosts would match the condition
Negates the criteria inside the property
Negates the criteria outside the property
Modifies the irresolvable condition to TRUE
Negates the "evaluate irresolvable as" setting
Answer:
BExplanation:
Based on the policy condition image provided showing the NOT checkbox on "Windows Antivirus Update Data", the correct statement is that the NOT operator negates the criteria inside the property.
Understanding the NOT Operator:
When the NOT checkbox is selected on a policy condition property, it performs a logical negation (NOT operation) on the criteria evaluation. According to the Forescout Administration Guide:
The NOT operator creates an inverted evaluation:
Without NOT: "Windows Antivirus Update Data = [value]"
Result: Matches endpoints where the property equals the specified value
With NOT (as shown in the image): "NOT (Windows Antivirus Update Data = [value])"
Result: Matches endpoints where the property does NOT equal the specified value
How the NOT Operator Works:
The NOT operator negates the criteria inside the property:
Criteria Evaluation - The property condition is evaluated normally first
Negation Applied - The result is then inverted (TRUE becomes FALSE, FALSE becomes TRUE)
Final Result - The endpoint matches only if the negated condition is true
Example from the Image:
The image shows:
First criterion: "Windows Antivirus Running - 360 Sat" (AND)
Second criterion: "NOT Windows Antivirus Update Data" (checked)
This means:
The endpoint must have Windows Antivirus Running = True (360 Sat)
AND the endpoint must NOT have the Windows Antivirus Update Data property value (whatever was specified)
The NOT negates the criteria inside the property condition
NOT vs. "Evaluate Irresolvable As":
According to the documentation, these are independent settings:
Setting
Purpose
NOT Checkbox
Negates the criteria evaluation (inverts the match logic)
Evaluate Irresolvable As
Defines how to handle unresolvable properties (when data cannot be determined)
The NOT operator works inside the property evaluation, while "Evaluate Irresolvable As" is a separate setting that determines behavior when a property cannot be resolved.
Why Other Options Are Incorrect:
A. Irresolvable hosts would match the condition - The NOT operator doesn't specifically affect how irresolvable properties are handled
C. Negates the criteria outside the property - The NOT operator is internal to the property; it negates the criteria inside, not outside
D. Modifies the irresolvable condition to TRUE - The NOT operator doesn't modify the "Evaluate Irresolvable As" setting; these are independent
E. Negates the "evaluate irresolvable as" setting - The NOT operator and "Evaluate Irresolvable As" are separate; NOT doesn't affect or negate that setting
Policy Condition Structure:
According to the Forescout Administration Guide:
A policy condition is structured as:
text
[NOT] [Property Name] [Operator] [Value]
Where:
[NOT] - Optional negation operator (what the checkbox controls)
[Property Name] - The property being evaluated
[Operator] - The comparison operator (equals, contains, greater than, etc.)
[Value] - The value to match against
When NOT is checked, it negates the entire criteria evaluation inside that property condition.
Referenced Documentation:
Forescout Administration Guide v8.3
Forescout Administration Guide v8.4
Define policy scope documentation
Forescout eyeSight policy sub-rule advanced options
Based on ForeScout's recommended troubleshooting approach, where should you start the troubleshooting process?
Options:
Run fstool tech-support
Check that requirements are met
Look at dependencies
Examine the GUI Logs
Review command line logs
Answer:
BExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout troubleshooting methodology, the recommended starting point for the troubleshooting process is to "Check that requirements are met". This foundational step must come before any detailed investigation.
Forescout Troubleshooting Approach:
The basic troubleshooting workflow consists of:
text
Step 1: CHECK THAT REQUIREMENTS ARE MET (START HERE)
├─ System requirements
├─ Software versions
├─ Network connectivity
└─ Licensing
Step 2: Look at Dependencies
├─ Network dependencies
├─ Service dependencies
└─ Appliance dependencies
Step 3: Gather Information from CounterACT
├─ GUI logs
├─ Properties
└─ Policies
Step 4: Gather Information from Command Line
├─ CLI logs
└─ Network diagnostics
Step 5: Form Hypothesis and Diagnose
├─ Analyze findings
└─ Determine root cause
Why Checking Requirements is the First Step:
According to the troubleshooting best practices:
Foundation - Verifying requirements prevents wasting time on invalid configurations
System Integrity - Ensures all prerequisites are met before investigating issues
Efficiency - Many issues stem from unmet requirements; fixing these resolves the problem immediately
Logical Flow - Without meeting requirements, no further troubleshooting will be effective
Why Other Options Are Incorrect:
A. Run fstool tech-support - This is an advanced diagnostic tool, not the starting point
C. Look at dependencies - Dependencies are examined AFTER confirming requirements are met
D. Examine the GUI Logs - Logs are reviewed AFTER requirements and dependencies are checked
E. Review command line logs - CLI logs are examined later in the process, not first
Requirements Verification Includes:
According to the methodology:
System Requirements
Supported OS versions
Memory and storage requirements
CPU specifications
Software Versions
Forescout platform version
Plugin/module compatibility
Browser versions for Console
Network Connectivity
IP address configuration
Network interfaces
Firewall rules
Licensing
Valid licenses
License not expired
License for required modules
Referenced Documentation:
Basic troubleshooting approach methodology
Which of the following logs are available from the GUI?
Options:
Host Details, Policy, Blocking, Event Viewer, Audit Trail
Switch, Policy, Blocking, Event Viewer, Audit Trail
Switch, Discovery, Threat Protection, Event Viewer, Audit Trail
HPS, Policy, Threat Protection, Event Viewer, Audit Trail
Host Details, Policy, Today Log, Threat Event Viewer, Audit Trail
Answer:
AExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Platform Administration Guide, the logs available from the GUI Console include: Host Details, Policy, Blocking, Event Viewer, and Audit Trail.
Available Logs from the Forescout Console GUI:
Host Details Log - Provides detailed information about individual endpoints discovered on the network. This log displays comprehensive host properties and status information directly accessible from the console.
Policy Log - Shows policy activity and records how specific endpoints are handled by policies. The Policy Log investigates endpoint activity, displaying information about policy matches, actions executed, and policy evaluation results.
Blocking Log - Displays all blocking events that occur on the network, including port blocks, host blocks, and external port blocks. This log provides an at-a-glance display of blocked endpoints with timestamps and reasons.
Event Viewer - A system log that displays severity, date, status, element, and event information. Administrators can search, export, and filter events using the Event Viewer.
Audit Trail - Records administrative actions and changes made to the Forescout platform configuration and policies.
How to Access Logs from the GUI:
From the Forescout Console GUI, administrators access logs through the Log menu by selecting:
Blocking Logs to view block events
Event Viewer to display system events
Policy Reports to investigate policy activity
Why Other Options Are Incorrect:
B. Switch, Policy, Blocking, Event Viewer, Audit Trail - "Switch" is not a standalone log type available from the GUI; switch data is captured through plugin logs and reports
C. Switch, Discovery, Threat Protection, Event Viewer, Audit Trail - "Discovery" and "Threat Protection" are report categories, not GUI logs in the standard log menu
D. HPS, Policy, Threat Protection, Event Viewer, Audit Trail - HPS logs are accessed through CLI, not the GUI; "Threat Protection" is a report, not a GUI log
E. Host Details, Policy, Today Log, Threat Event Viewer, Audit Trail - "Today Log" and "Threat Event Viewer" are not standard log names in the Forescout GUI
Referenced Documentation:
Forescout Platform Administration Guide - Generating Reports and Logs
Policy Reports and Logs section
Work with System Event Logs documentation
View Block Events documentation
Place the DNS Enforce control actions into the correct workflow order for endpoints which have a pending control action.
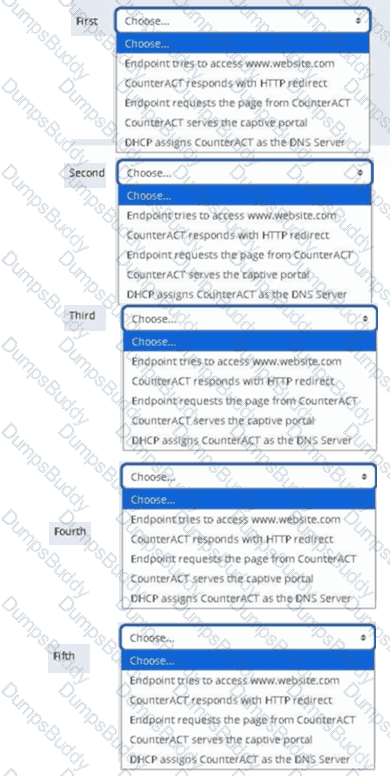
Options:
Answer:
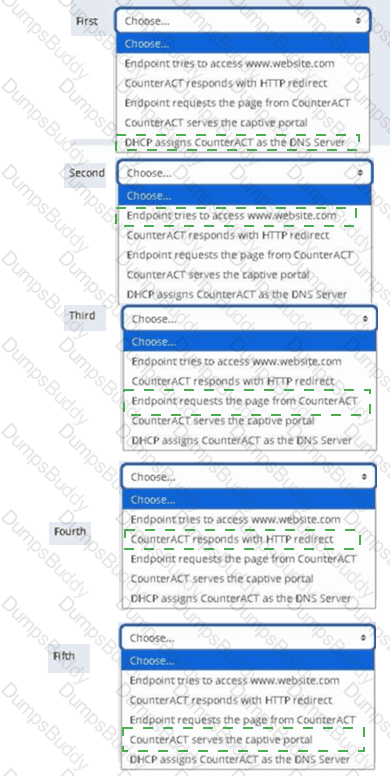
What is true of the "Use as directory" selection configured below?

Select one:
Options:
It allows resolution of User information via LDAP
It allows resolution of user information via TACACS
It allows for Guest Registration when Approvals are required
It enables HTTP authentication and resolves HTTP login status
It allows resolution of user information via RADIUS
Answer:
AExplanation:
According to the Forescout User Directory Plugin Configuration Guide and the RADIUS Plugin Configuration Guide Version 4.3, the "Use as directory" selection allows resolution of user information via LDAP. The documentation explicitly states:
"Use as directory: Select this option to use the server as a directory to retrieve user information. This option is not available for RADIUS and TACACS servers."
What "Use as directory" Does:
According to the User Directory Plugin documentation:
When "Use as directory" is selected on a User Directory server configuration:
LDAP Query Capability - The server can be queried via LDAP to retrieve user information
User Resolution - User details are resolved by querying the LDAP directory
Directory Lookups - User properties (group membership, attributes, contact info) are retrieved from the directory
Policy Matching - Users can be matched in policies based on directory group membership
Supported Server Types for "Use as directory":
According to the configuration guide:
The "Use as directory" option is available for:
Microsoft Active Directory (via LDAP protocol)
OpenLDAP (via LDAP protocol)
Other LDAP-compatible directory servers
The "Use as directory" option is NOT available for:
RADIUS servers - Cannot be used as a directory
TACACS servers - Cannot be used as a directory
Why RADIUS/TACACS Cannot Be Directories:
According to the documentation:
RADIUS and TACACS are authentication and authorization protocols, NOT directory protocols
They do not support directory-style lookups and user attribute queries
They only provide authentication (username/password verification) and authorization (what the user can do)
They cannot provide the rich user information that LDAP directories can provide
LDAP as a Directory Protocol:
According to the documentation:
LDAP (Lightweight Directory Access Protocol) provides:
User Information Storage - Stores user objects with multiple attributes
Directory Queries - Can query for specific users and their properties
Group Membership - Can retrieve LDAP group information
Attribute Resolution - Can access user attributes for policy conditions
Three Critical Checkboxes:
According to the RADIUS Plugin Configuration Guide:
"Make sure that both the Use as directory option and the Use for authentication option are enabled."
This indicates that a single User Directory server can have multiple roles:
Use as directory - For LDAP queries and user information resolution
Use for authentication - For user login authentication
Use for Console Login - For access to the Forescout Console
Example Configuration:
According to the documentation:
When you have an Active Directory server:
✓ "Use as directory" is CHECKED - Enables LDAP queries for user info and group membership
✓ "Use for authentication" is CHECKED - Allows users to authenticate with their AD credentials
✓ "Use for Console Login" is CHECKED - Allows administrators to log into Forescout Console with AD credentials
Why Other Options Are Incorrect:
B. It allows resolution of user information via TACACS - Explicitly NOT available for TACACS; TACACS cannot function as a directory
C. It allows for Guest Registration when Approvals are required - This is a separate User Directory feature unrelated to "Use as directory"
D. It enables HTTP authentication and resolves HTTP login status - This is not related to directory usage; HTTP authentication is a separate feature
E. It allows resolution of user information via RADIUS - Explicitly NOT available for RADIUS; RADIUS servers cannot function as directories
Referenced Documentation:
User Directory Plugin Configuration - Define User Directory Servers
User Directory Plugin - Name and Type Step documentation
RADIUS Plugin Configuration Guide Version 4.3 - User Directory Readiness section
Which of the following plugins assists in classification for computer endpoints? (Choose two)
Options:
Switch
HPS Inspection Engine
Linux Plugin
Advanced Tools
DNS Client
Answer:
B, DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide and Base Modules documentation, the plugins that assist in classification for computer endpoints are HPS Inspection Engine (B) and Advanced Tools (D).
HPS Inspection Engine Classification:
According to the HPS Inspection Engine Configuration Guide:
"The HPS Inspection Engine powers CounterACT tools used for classifying endpoints. These tools include the classification engine that is part of HPS Inspection Engine, the Primary Classification, Asset Classification and Mobile Classification templates, the Classify actions, and Classification/Classification (Advanced) properties."
The HPS Inspection Engine provides:
Classification Engine - Determines the Network Function property
Primary Classification Template - Classifies endpoints into categories
Asset Classification Template - For asset-level classification
Mobile Classification Template - For mobile device classification
Multiple Classification Methods - Including NMAP, HTTP banner scanning, SMB analysis, passive TCP/IP fingerprinting
Advanced Tools Plugin Classification:
According to the Advanced Tools Plugin documentation:
"The Advanced Tools Plugin is used to classify endpoints based on characteristics such as operating system, hardware vendor, and application software."
The Advanced Tools Plugin provides:
Endpoint Classification - Based on OS, vendor, and applications
Device Property Resolution - Resolves device characteristics
Fingerprinting - Identifies endpoints based on behavioral patterns
Why Other Options Are Incorrect:
A. Switch - The Switch Plugin manages network devices (switches) and provides VLAN/access control, not endpoint classification
C. Linux Plugin - The Linux Plugin is a platform-specific module for managing Linux endpoints, not a general classification tool
E. DNS Client - The DNS Client Plugin resolves DNS queries but does not assist with endpoint classification
Classification Workflow:
According to the documentation:
When classifying computer endpoints, Forescout uses:
HPS Inspection Engine - Primary classification tool analyzing:
HTTP banners from web services
SMB protocol information
NMAP scans and service detection
Passive TCP/IP fingerprinting
Domain credentials analysis
Advanced Tools Plugin - Secondary classification providing:
Vendor/model information
Application detection
Operating system identification
Hardware characteristics
Together, these plugins provide comprehensive endpoint classification for computer systems.
Classification Properties Resolved:
According to the Base Modules documentation:
The HPS Inspection Engine and Advanced Tools plugins resolve:
Function (Workstation, Printer, Server, Router, etc.)
Operating System (Windows, Linux, macOS, etc.)
Vendor and Model information
Network Function (specific device role)
Application information
Referenced Documentation:
CounterACT Endpoint Module HPS Inspection Engine Configuration Guide v10.8
Forescout Platform Base Modules
About the Forescout Advanced Tools Plugin
Which of the following is a User Directory feature?
Options:
Guest authentication
Dashboard
Radius authorization
Query Switches
Assets portal
Answer:
AExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
Guest authentication is a User Directory feature. According to the Forescout Authentication Module Overview Guide and the User Directory Plugin Configuration Guide, the User Directory Plugin enables guest authentication and management through configured directory servers.
User Directory Plugin Features:
The User Directory Plugin (version 6.4+) provides the following core features:
Endpoint User Resolution - Resolves endpoint user details by querying directory servers
User Authentication - Performs user authentication via configured internal and external directory servers (Active Directory, LDAP, etc.)
Guest Authentication - Enables authentication and registration of guest users on the network
Guest Sponsorship - Allows corporate employee sponsors to approve guest network access
Guest Management Portal - Provides functionality for managing guest hosts and guest portal access
Directory Server Integration - Integrates with enterprise directory servers for credential validation
Guest Management Capabilities:
The User Directory Plugin specifically enables:
Guest user registration and authentication
Guest approval workflows through sponsor groups
Guest session management
Guest password policies
Guest tag management for categorization
Why Other Options Are Incorrect:
B. Dashboard - This is a general console feature, not specific to the User Directory plugin
C. Radius authorization - This is the function of the RADIUS plugin, not the User Directory plugin (though they work together in the Authentication Module)
D. Query Switches - This is a function of the Switch plugin, not the User Directory plugin
E. Assets portal - This is a general Forescout platform feature, not specific to the User Directory plugin
Authentication Module Structure:
According to the documentation, the Authentication Module consists of two plugins:
RADIUS Plugin - Handles 802.1X authentication, authorization, and accounting
User Directory Plugin - Handles user resolution, authentication, and guest management
These work together but have distinct responsibilities. The User Directory Plugin specifically handles guest authentication among its feature set.
Referenced Documentation:
Forescout Authentication Module Overview Guide Version 1.1
About the User Directory Plugin documentation
User Directory Plugin Server and Guest Management Configuration Guide
When an admission event is seen, how are main rules and sub-rules processed?
Options:
Main rules process concurrently, sub-rules process sequentially.
Main rules process in parallel, sub-rules process concurrently.
Main rules process concurrently, sub-rules process in parallel.
Main rules process sequentially, sub-rules process concurrently.
Main rules process sequentially, sub-rules process in parallel.
Answer:
AExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide - Policy Processing, when an admission event occurs, "Main rules process concurrently, sub-rules process sequentially".
Policy Processing Flow:
According to the Main Rule Advanced Options documentation:
When an admission event triggers policy evaluation:
Main Rules - Process concurrently/in parallel
All main rules are evaluated simultaneously
No ordering or sequencing
Each main rule evaluates independently
Sub-Rules - Process sequentially/in order
Sub-rules within each main rule execute one after another
First match wins - stops evaluating subsequent sub-rules
Order matters for sub-rule execution
Main Rule Concurrent Processing:
According to the documentation:
"Main rules are evaluated independently and concurrently. Multiple main rules can be processed simultaneously for the same endpoint."
Sub-Rule Sequential Processing:
According to the Defining Policy Sub-Rules documentation:
"Sub-rules are evaluated sequentially in the order defined. When an endpoint matches a sub-rule, that sub-rule's actions are taken and subsequent sub-rules are not evaluated."
Example Processing:
When admission event triggers:
text
CONCURRENT (Main Rules):
├─ Main Rule 1 evaluation → Sub-rule processing (sequential)
├─ Main Rule 2 evaluation → Sub-rule processing (sequential)
└─ Main Rule 3 evaluation → Sub-rule processing (sequential)
(All main rules evaluate at the same time)
Why Other Options Are Incorrect:
B. Parallel/Concurrently - "Concurrent" and "parallel" mean the same thing; sub-rules don't process concurrently
C. Concurrent/Parallel - Sub-rules don't process in parallel; they're sequential
D. Sequential/Concurrently - Main rules don't process sequentially; they're concurrent
E. Sequential/Parallel - Main rules don't process sequentially; they're concurrent
Referenced Documentation:
Main Rule Advanced Options
Defining Policy Sub-Rules
Which setting is NOT available when initially adding a server to the User Directory Plugin?
Options:
Test
Domain
Domain Aliases
Advanced
Replica
Answer:
EExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout User Directory Plugin Configuration Guide and supported integration documentation, Replica is NOT available when initially adding a server to the User Directory Plugin. Replicas are configured after the initial server setup is complete.
User Directory Server Initial Setup Process:
When initially adding a User Directory server, the following settings are available:
Server Name - The name to identify the server in Forescout
Address - The IP address or FQDN of the User Directory server
Port - The port number (typically 389 for LDAP, 636 for secure LDAP)
Domain - The domain name associated with the User Directory
Test - Option to test the connection and credentials
Advanced - Advanced configuration options
Replica Configuration - Post-Initial Setup:
According to the documentation:
"After configuring server settings, you can configure server tests and replicas."
The Replica settings are NOT available during the initial server addition. Instead, replicas are configured as a separate step after the primary server configuration is complete.
Replica Setup Workflow:
According to the User Directory Plugin configuration process:
Step 1: Add Server - Configure the primary server with Name, Address, Port, Domain
Step 2: Test Connection - Use the Test option to verify connectivity
Step 3: Configure Replicas - After the primary server is fully configured, then add replica servers
The documentation explicitly states:
"Refer to the following sections for server configuration details. After configuring server settings, you can configure server tests and replicas."
Why Other Options Are Available Initially:
A. Test -✓Available initially; allows testing of server credentials and connectivity before completion
B. Domain -✓Available initially; domain name is required during server setup
C. Domain Aliases -✓Available initially; additional domain aliases can be specified for the server
D. Advanced -✓Available initially; advanced options like authentication types, TLS, etc. are available during setup
Replica Purpose:
Replicas are used to provide redundancy and failover capability. According to the documentation:
When replica servers are configured:
If the primary User Directory server becomes unavailable, the Forescout platform can failover to a replica server
Multiple replicas can be specified for increased fault tolerance
Referenced Documentation:
Forescout User Directory Plugin Configuration - Server Setup documentation
Configure server settings - After configuring server settings section
User Directory Plugin configuration videos and tutorials showing initial setup flow
Which of the following is true regarding how CounterACT restores a quarantined endpoint to its original production VLAN after the "Assign to VLAN Action" is removed?
Options:
This happens automatically because CounterACT compares the running and startup configs
This happens automatically as long as configuration changes to the switchport access VLAN of affected ports are not changed in the switch running config
This happens automatically as long as no configuration changes to the switch are made to the running config
This happens automatically as long as configuration changes to the switchport access VLAN of affected ports are not saved in the startup config
A policy is required to ensure this happens correctly.
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Switch Plugin Configuration Guide Version 8.12 and 8.14.2, CounterACT restores a quarantined endpoint to its original production VLAN automatically as long as configuration changes to the switchport access VLAN of affected ports are not saved in the startup config.
VLAN Restoration Mechanism:
According to the Switch Plugin documentation:
When the "Assign to VLAN" action is removed or expires, CounterACT can restore the original VLAN configuration by comparing the running configuration with the startup configuration on the switch.
The Key Requirement:
According to the documentation:
The restoration process works as follows:
Assign to VLAN Action Applied - Endpoint is moved to quarantine VLAN (switch running config is updated)
Assign to VLAN Action Removed - CounterACT wants to restore the original VLAN
Running vs. Startup Config Comparison - CounterACT compares running config to startup config
Restoration - The port is returned to its original VLAN as defined in the startup configuration
Critical Condition:
According to the documentation:
"This happens automatically as long as configuration changes to the switchport access VLAN of affected ports are not saved in the startup config"
This is critical because:
If manual changes are saved to the startup config, CounterACT cannot determine what the "original" VLAN should be
The startup config must remain unchanged for CounterACT to restore the correct VLAN
The running config changes are temporary and revert to startup config values
Why Other Options Are Incorrect:
A. CounterACT compares the running and startup configs - While true that comparison occurs, the condition is about whether changes are saved to startup, not just comparing
B. Configuration changes...are not changed in the switch running config - Too broad; there can be other running config changes; the specific requirement is about VLAN configuration being saved to startup
C. No configuration changes to the switch are made to the running config - Too strict; other changes can be made; only VLAN switchport access configuration matters
E. A policy is required - Incorrect; this is automatic behavior, not policy-dependent
Default VLAN Feature:
According to the Switch Plugin Configuration Guide:
The Default VLAN feature ensures that ports are automatically assigned to a default VLAN unless specifically configured otherwise. When the "Assign to VLAN" action is removed, the port returns to the default VLAN (as defined in the startup configuration).
Referenced Documentation:
Forescout CounterACT Switch Plugin Configuration Guide Version 8.12
Switch Plugin Configuration Guide v8.14.2
Global Configuration Options for the Switch Plugin
Which of the following statements is true regarding Layer-2 channel?
Options:
Recommended when there are a large number of VLANs
Response interface is a VLAN trunk
Monitor interface is a trunk
Utilizes two interfaces
Appliance monitor interface must be connected to an access layer switch
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Installation Guide and Working with Appliance Channel Assignments documentation, a Layer-2 channel "Utilizes two interfaces" - one monitor interface and one response interface.
Layer-2 Channel Structure:
According to the documentation:
"A channel defines a pair of interfaces used by the Appliance to protect your network. In general, one interface monitors traffic going through the network (the monitor interface), and the other responds to traffic on the network (the response interface)."
Two Interface Components:
According to the Installation Guide:
Monitor Interface:
Monitors and tracks network traffic
Traffic is mirrored from switch ports
No IP address required
Can be any available interface
Response Interface:
Responds to monitored traffic
Used for policy actions and protections
Configuration depends on VLAN tagging
Can be same VLAN or trunk configuration
Layer-2 vs. Layer-3 Channel:
According to the documentation:
Layer-2 Channel - Two interfaces (monitor and response)
Layer-3 Channel - Uses IP layer for response
Why Other Options Are Incorrect:
A. Recommended for large number of VLANs - Actually, Layer-2 channels with VLAN tagging are recommended for multiple VLANs, but this doesn't define what a Layer-2 channel is
B. Response interface is a VLAN trunk - While response interface CAN be a trunk for multiple VLANs, it's not required for all configurations
C. Monitor interface is a trunk - The monitor interface receives mirrored traffic; trunk configuration depends on VLAN setup
E. Must be connected to access layer switch - The appliance can connect to various switch types; not specifically limited to access layer
Referenced Documentation:
Working with Appliance Channel Assignments
Quick Installation Guide v8.4
Quick Installation Guide v8.2
Add Channels
Monitor Interface
Set up the Forescout Platform Network
Main rules are executed independently of each other. However, one policy may be set to run first by configuring which of the following?
Options:
There is no way to cause one policy to run first
Setting the Main Rule condition to utilize primary classification
Categorizing the Policy as an assessment policy
Categorizing the Policy as a classifier
Using Irresolvable criteria
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide, one policy can be set to run first by categorizing the Policy as a classifier. Classifier policies run before other policy types.
Policy Categorization and Execution Order:
According to the Forescout Administration Guide:
Forescout supports different policy categories, and these categories determine execution order:
Classifier Policies - Run FIRST
Used for initial device classification
Establish basic device properties (OS, Function, Network Function)
Must complete before other policies can evaluate classification properties
Assessment Policies - Run AFTER classifiers
Assess compliance based on classified properties
Depend on classifier output
Control/Action Policies - Run LAST
Apply remediation actions
Depend on assessment results
How Classifier Policies Run First:
According to the documentation:
"When you categorize a policy as a classifier, it runs before assessment and action policies. This allows the classified properties to be established before other policies attempt to evaluate them."
Reason for Classifier Priority:
According to the policy execution guidelines:
Classifier policies must run first because:
Dependency Resolution - Other policies depend on classification properties
Property Population - Classifiers populate device properties used by other policies
Execution Efficiency - Classifiers determine what type of device is being evaluated
Logical Flow - You must know what a device is before assessing or controlling it
Why Other Options Are Incorrect:
A. There is no way to cause one policy to run first - Incorrect; categorization determines execution order
B. Setting Main Rule condition to utilize primary classification - While main rule conditions can reference classification, this doesn't change policy execution order
C. Categorizing the Policy as an assessment policy - Assessment policies run AFTER classifier policies, not first
E. Using Irresolvable criteria - Irresolvable criteria handling doesn't affect policy execution order
Policy Categorization Example:
According to the documentation:
text
Policy Execution Order:
1. CLASSIFIER Policies (Run First)
- "Device Classification Policy" (categorized as Classifier)
- Resolves: OS, Function, Network Function
2. ASSESSMENT Policies (Run Second)
- "Windows Compliance Policy" (categorized as Assessment)
- Depends on classification from step 1
3. ACTION Policies (Run Last)
- "Remediate Non-Compliant Devices" (categorized as Control)
- Depends on assessment from step 2
In this workflow, because "Device Classification Policy" is categorized as a Classifier, it executes first, populating device properties that the subsequent Assessment and Action policies need.
Referenced Documentation:
ForeScout CounterACT Administration Guide - Policy Categorization
Categorize Endpoint Authorizations - Policy Categories and Execution
Which of the following are endpoint attributes learned from the Switch plugin?
Options:
Host Name, Mac table, Switch IP, Port Description, Host Table, Switch Version
Port VLAN, Switch Version, Mac address, Host name, Port Description, ARP Table, Switch Version
Mac address, Host name, Port VLAN, Port Description, Switch OS, Switch Version
Switch Version, Mac address, Switch OS, Port VLAN, Host Name, ARP Table
Mac address, Switch IP and Port name, ARP Table, Switch Port Information
Answer:
CExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Switch Plugin documentation and Switch Properties, the endpoint attributes learned from the Switch plugin are: Mac address, Host name, Port VLAN, Port Description, Switch OS, and Switch Version.
Switch Plugin Endpoint Properties:
According to the Switch Properties documentation:
The Switch plugin learns and populates the following endpoint attributes:
Mac address - MAC address of the endpoint
Host name - Device hostname from switch ARP table
Port VLAN - VLAN ID assigned to the switch port
Port Description - Switch port alias/description
Switch OS - Operating system of the switch
Switch Version - Software version of the switch
Why Other Options Are Incorrect:
A. Includes "Mac table" and "Host Table" - These are switch resources, not endpoint attributes
B. Lists "ARP Table" and duplicates "Switch Version" - ARP table is not an endpoint attribute
D. Includes "ARP Table" - ARP table is a switch resource, not an endpoint attribute
**E. "Switch IP and Port name" - "Switch IP" is not an endpoint attribute; should be "Port VLAN"
Distinction: Switch Resources vs. Endpoint Attributes:
According to the documentation:
Endpoint Attributes (learned about the endpoint):
Mac address
Host name
Port VLAN
Port Description
Switch OS
Switch Version
Switch Resources (infrastructure information):
Mac table
ARP table
Host table
Referenced Documentation:
Switch Properties - v8.4.4
Switch Properties - v8.16.h
Switch Properties - v8.1.x
What is the best practice to pass an endpoint from one policy to another?
Options:
Use operating system property
Use sub rules
Use function property
Use groups
Use policy condition
Answer:
BExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Platform Administration and Deployment Documentation, the best practice to pass an endpoint from one policy to another is to use SUB-RULES.
Sub-Rules and Policy Routing:
Sub-rules are conditional branches within a Forescout policy that allow for sophisticated endpoint routing and handling. When an endpoint matches a sub-rule condition, it can be directed to perform specific actions or be passed to another policy group for further evaluation.
Key Advantages of Using Sub-Rules:
Granular Control - Sub-rules enable precise segmentation of endpoints based on multiple properties and conditions
Hierarchical Processing - Once an endpoint matches a sub-rule, it proceeds down the sub-rule branch; later sub-rules of the policy are not evaluated for that endpoint
Efficient Endpoint Routing - Sub-rules allow endpoints to be efficiently routed to appropriate policy handlers without evaluating unnecessary conditions
Policy Chaining - Sub-rules facilitate the logical flow and routing of endpoints through multiple policy layers
Best Practice Implementation:
The documentation emphasizes that when designing policies for endpoint management, administrators should:
Use sub-rules to create conditional branches that evaluate endpoints against multiple criteria
Route endpoints to appropriate policy handlers based on their properties and compliance status
Avoid using simple property-based routing when complex multi-step evaluation is needed
Why Other Options Are Incorrect:
A. Use operating system property - While OS properties can be used in conditions, they are not the mechanism for passing endpoints between policies
C. Use function property - Function properties are not used for inter-policy endpoint routing
D. Use groups - While groups are useful for organizing endpoints, they are not the primary best practice for passing endpoints between policies
E. Use policy condition - Policy conditions define what endpoints should be evaluated, but sub-rules provide the actual routing mechanism
Referenced Documentation:
Forescout Platform Administration Guide - Defining Policy Sub-Rules
"Defining Forescout Platform Policy Sub-Rules" - Best Practice section
Sub-Rule Advanced Options documentation
Which of the following is true regarding Failover Clustering module configuration?
Options:
Once appliances are configured, then press the Apply button.
Segments should be assigned to appliance folders and NOT to the individual appliances.
You can see the status of failover by selecting IP Assignments and failover tab.
Configure the second HA on the Secondary node.
Place only the EM to participate in failover in the folder.
Answer:
BExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Resiliency Solutions User Guide and Failover Clustering configuration documentation, the correct statement is: "Segments should be assigned to appliance folders and NOT to the individual appliances".
Failover Clustering Folder Structure:
According to the Resiliency Solutions User Guide:
"When configuring failover: Identify segments of the CounterACT Internal Network that should participate in failover, and assign these segments to the folder."
Key requirement:
"Clear statically assigned segments from Appliances in the failover cluster folder. Appliances in the failover cluster support only the network segments assigned to the folder. They cannot support individually assigned segments."
Segment Assignment Rules:
According to the documentation:
text
Correct Configuration:
├─ Failover Cluster Folder
│ ├─ Assigned Segments: Segment1, Segment2, Segment3
│ ├─ Appliance A (no individual segments)
│ ├─ Appliance B (no individual segments)
│ └─ Appliance C (no individual segments)
NOT this way:
text
Incorrect Configuration:
├─ Failover Cluster Folder
│ ├─ Appliance A: Segment1
│ ├─ Appliance B: Segment2
│ └─ Appliance C: Segment3
Configuration Steps:
According to the official procedure:
Create or select an appliance folder
Place appliances in the folder
Assign segments to the FOLDER (not individual appliances)
Clear any statically assigned segments from individual appliances
Configure the folder as a failover cluster
Why Other Options Are Incorrect:
A. Once appliances are configured, then press the Apply button - Failover uses "Configure Failover" button, not "Apply"
C. See failover status by selecting IP Assignments and failover tab - It's the "IP Assignment and Failover pane," not a separate tab
D. Configure the second HA on the Secondary node - Incorrect; failover clustering is configured at the folder level, not on individual nodes
E. Place only the EM to participate in failover - Incorrect; member appliances participate; EM has separate HA
Referenced Documentation:
ForeScout CounterACT Resiliency Solutions User Guide - Failover Clustering section
Define a Forescout Platform failover cluster
Forescout Platform Failover Clustering
Work with Appliance Folders
Which of the following is true regarding CounterACT 8 FLEXX Licensing?
Options:
CounterACT 8 can be installed on all CTxx and 51xx models.
Disaster Recovery is used for member appliances.
For member appliances, HA and Failover Clustering are part of Resiliency licensing.
Changing the licensing of the deployment from Per Appliance Licensing to FLEXX Licensing can be done through the Customer Portal.
Failover Clustering is used with EM and RM.
Answer:
CExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Licensing and Sizing Guide and Failover Clustering Licensing Requirements documentation, the correct statement is: For member appliances, HA and Failover Clustering are part of Resiliency licensing.
Resiliency Licensing for Member Appliances:
According to the Failover Clustering Licensing Requirements documentation:
"To begin working with Failover Clustering, you need a license for the feature. The license required depends on which licensing mode your deployment is using."
When using FLEXX licensing with member appliances:
High Availability (HA) - Part of Resiliency licensing
Failover Clustering - Part of Resiliency licensing (called "eyeRecover License")
Disaster Recovery - Separate from member appliance resiliency
Resiliency License Components:
According to the documentation:
"When using Flexx licensing, Failover Clustering functionality is supported by the Forescout Platform eyeRecover license (Forescout CounterACT Resiliency license)."
The Resiliency license covers:
For Member Appliances:
High Availability (HA) Pairing
Failover Clustering
For Enterprise Manager:
HA Pairing for EM
FLEXX Licensing Model:
According to the Licensing and Sizing Guide:
"Flexx Licensing: Licenses are independent of hardware appliances, providing an intuitive and flexible way to license, deploy and manage Forescout products across your extended enterprise."
Why Other Options Are Incorrect:
A. Can be installed on all CTxx and 51xx models - FLEXX is for 5100/4100 series and later; CT series supports per-appliance licensing only
B. Disaster Recovery is used for member appliances - Disaster Recovery is separate; member appliances use HA/Failover Clustering from Resiliency license
D. Changing via Customer Portal - Changes from per-appliance to FLEXX must be done through official Forescout channels, not self-service Customer Portal
E. Failover Clustering is used with EM and RM - Failover Clustering is for member appliances; EM has separate HA capability
Referenced Documentation:
Failover Clustering Licensing Requirements v8.4.4 and v9.1.2
Forescout Licensing and Sizing Guide
Switch from Per-Appliance to Flexx Licensing
What is the automated safety feature to prevent network wide outages/blocks?
Options:
Stop all policies
Disable policy
Disable Policy Action
Action Thresholds
Send an Email Alert
Answer:
DExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
Action Thresholds is the automated safety feature designed to prevent network-wide outages and blocks. According to the Forescout Platform Administration Guide, Action Thresholds are specifically designed to automatically implement safeguards when rolling out sanctions (blocking actions) across your network.
Purpose of Action Thresholds:
Action thresholds work as an automated circuit breaker mechanism that prevents catastrophic network-wide outages. The feature establishes maximum percentage limits for specific action types on a single appliance. When these limits are reached, the policy automatically stops executing further blocking actions to prevent mass network disruption.
How Action Thresholds Prevent Outages:
Consider a scenario where a policy is misconfigured and would block 90% of all endpoints on the network due to a false condition match. Without Action Thresholds, this could cause a network-wide outage. With Action Thresholds configured:
Limit Definition - An administrator sets an action threshold (e.g., 20% of endpoints can be blocked by Switch action type)
Automatic Enforcement - When this percentage threshold is reached, the policy automatically stops executing the blocking action for any additional endpoints
Alert Generation - The system generates alerts to notify administrators when a threshold has been reached
Protection - This prevents the policy from cascading failures that could affect the entire network
Action Threshold Configuration:
Each action type (e.g., Switch blocking, Port blocking, External port blocking) can be configured with its own threshold percentage. This allows granular control over the maximum impact any single policy can have on the network.
Why Other Options Are Incorrect:
A. Stop all policies - This is a manual intervention, not an automated safety feature; also, it's too drastic and would disable legitimate policies
B. Disable policy - This is a manual action, not an automated safety mechanism
C. Disable Policy Action - While you can disable individual actions, this is not an automated threshold-based safeguard
E. Send an Email Alert - Alerts notify administrators but do not automatically prevent outages; they require manual intervention
Referenced Documentation:
Forescout Platform Administration Guide - Working with Action Thresholds
Forescout Platform Administration Guide - Policy Safety Features
Section: "Action Thresholds are designed to automatically implement safeguards when rolling out such sanctions across your network"
Which of the following best describes why PXE boot endpoints should be exempt from Assessment policies?
Options:
Because they will not be subject to the Acceptable Use Policy
They have already been deployed and should immediately be subject to Assessment policies
Because they are not yet manageable and may not have all the required software and services installed
Because they will never be manageable or have the required software and services
Because they are special endpoints playing a specific role in the network
Answer:
CExplanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
PXE (Preboot Execution Environment) boot endpoints should be exempt from Assessment policies because they are not yet manageable and may not have all the required software and services installed. According to the Forescout Administration Guide, endpoints in the early stages of deployment, such as those booting via PXE, are temporary in nature and lack the necessary management capabilities and required software components.
PXE Boot Endpoints Characteristics:
PXE boot endpoints represent machines in a temporary state during the deployment process:
Not Yet Fully Deployed - PXE boot is used during initial OS installation and deployment
Lack Required Services - The endpoint does not yet have installed:
SecureConnector (if required for management)
Endpoint agents
Required security software
Management services
Limited Configuration - The endpoint may not have completed network configuration
Temporary State - PXE boot endpoints are in a transient state, not their final operational state
Policy Endpoint Exceptions:
According to the documentation, administrators can "select endpoints in the Detections pane and exempt them from further inspection for the policy that detected them". This is particularly important for PXE boot endpoints because:
False Positives - Assessment policies might flag PXE boot endpoints as non-compliant due to missing software that hasn't been installed yet
Blocked Deployment - If blocking actions are applied, they could interfere with the deployment process
Temporary Assessment - Once the endpoint is fully deployed and manageable, it can be added back to Assessment policies
Operational Efficiency - Exempting PXE boot endpoints prevents unnecessary policy violations during the deployment window
Manageable vs. Unmanageable Endpoints:
According to the documentation:
"Endpoints are generally unmanageable if their remote registry and file system cannot be accessed by Forescout. Unmanageable hosts can be included in your policy."
PXE boot endpoints specifically fall into this category because:
Remote management is not yet available
Required agents are not installed
File system access is not established
Why Other Options Are Incorrect:
A. Because they will not be subject to the Acceptable Use Policy - Not the primary reason; Assessment policies differ from Acceptable Use policies
B. They have already been deployed and should immediately be subject to Assessment policies - Contradicts the purpose; PXE boot endpoints are NOT yet deployed
D. Because they will never be manageable or have the required software and services - Incorrect; once deployed, they WILL become manageable
E. Because they are special endpoints playing a specific role in the network - While true in context, this doesn't explain why they need exemption
Referenced Documentation:
Forescout Administration Guide - Create Policy Endpoint Exceptions
Restricting Endpoint Inspection documentation
Manage Actions - Unmanageable hosts section


