FCSS_SASE_AD-25 FCSS - FortiSASE 25 Administrator Questions and Answers
Your organization is currently using FortiSASE for its cybersecurity. They have recently hired a contractor who will work from the HQ office and who needs temporary internet access in order to set up a web-based point of sale (POS) system.
What is the recommended way to provide internet access to the contractor?
Which two settings are automatically pushed from FortiSASE to FortiClient in a new FortiSASE deployment with default settings? (Choose two.)
Which information does FortiSASE use to bring network lockdown into effect on an endpoint?
In the Secure Private Access (SPA) use case, which two FortiSASE features facilitate access to corporate applications? (Choose two.)
Refer to the exhibit.
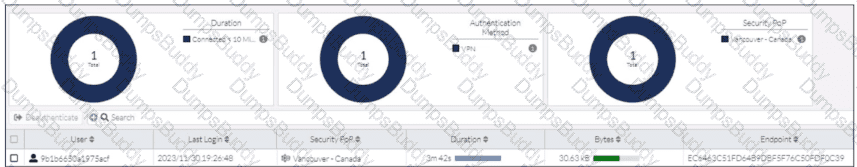
While reviewing the traffic logs, the FortiSASE administrator notices that the usernames are showing random characters.
Why are the usernames showing random characters?
Refer to the exhibit.
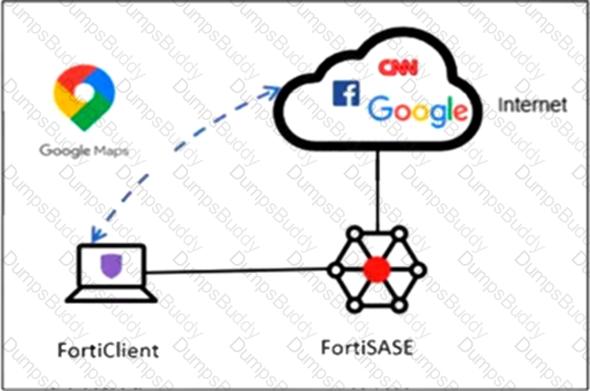
An organization must inspect all the endpoint internet traffic on FortiSASE, and exclude Google Maps traffic from the FortiSASE VPN tunnel and redirect it to the endpoint physical interface.
Which configuration must you apply to achieve this requirement?
Refer to the exhibits.
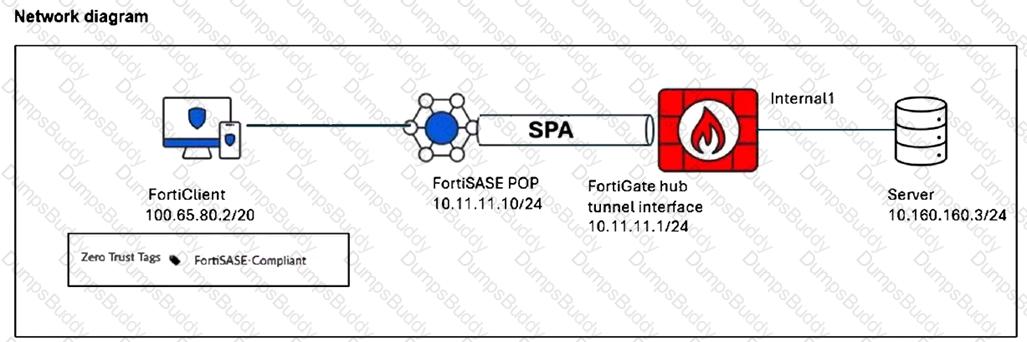
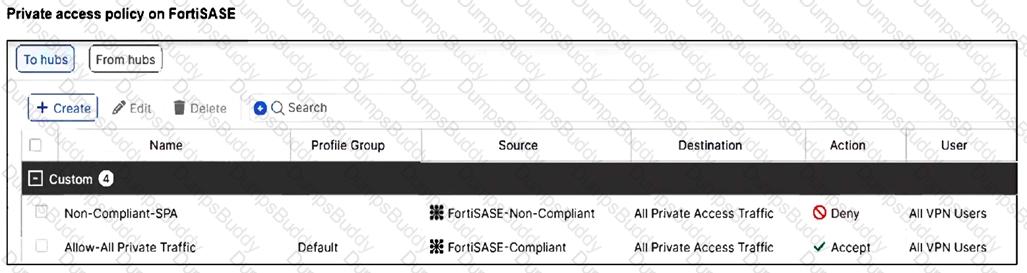
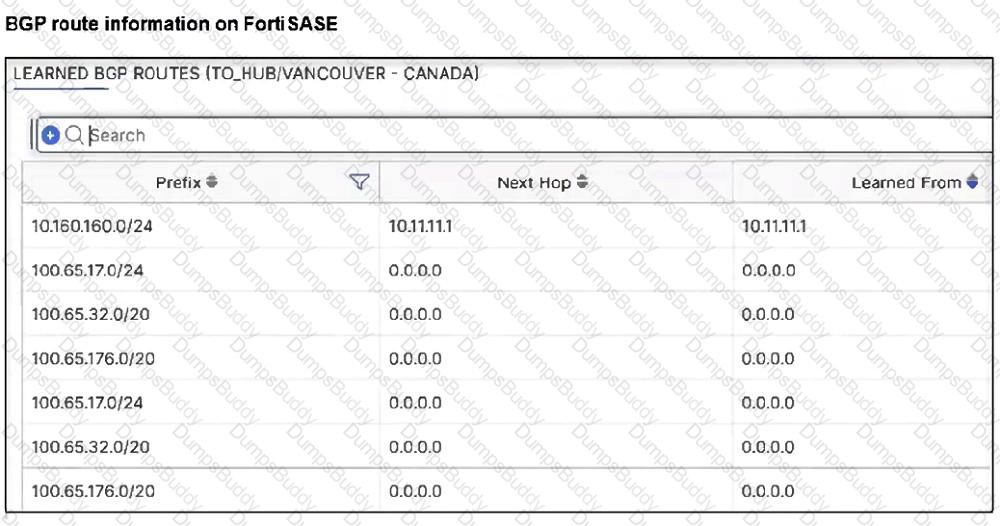
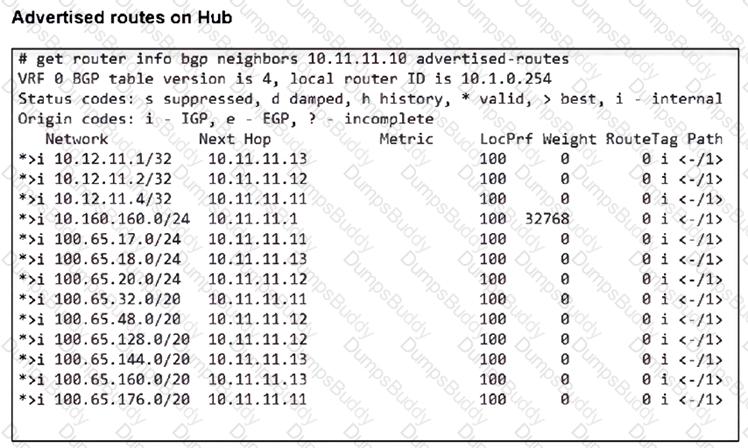
A FortiSASE administrator has configured FortiSASE as a spoke to a FortiGate hub. The tunnel is up to the FortiGate hub. However, the remote FortiClient is not able to access the web server hosted behind the FortiGate hub.
Based on the exhibits, what is the reason for the access failure?
An organization must block user attempts to log in to non-company resources while using Microsoft Office 365 to prevent users from accessing unapproved cloud resources.
Which FortiSASE feature can you implement to meet this requirement?
What happens to the logs on FortiSASE that are older than the configured log retention period?
When accessing the FortiSASE portal for the first time, an administrator must select data center locations for which three FortiSASE components? (Choose three.)


