FCP_FWB_AD-7.4 FCP - FortiWeb 7.4 Administrator Questions and Answers
Refer to the exhibit.
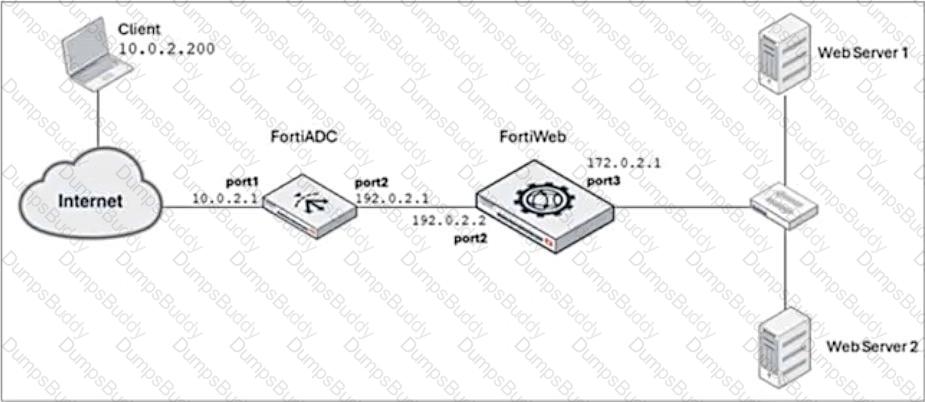
FortiADC is applying SNAT to all inbound traffic going to the servers.
When an attack occurs, FortiWeb blocks traffic based on the192.0.2.1source IP address, which belongs to FortiADC. This setup is breaking all connectivity and genuine clients are not able to access the servers.
What can the administrator do to avoid this problem? (Choose two.)
Refer to the exhibit.
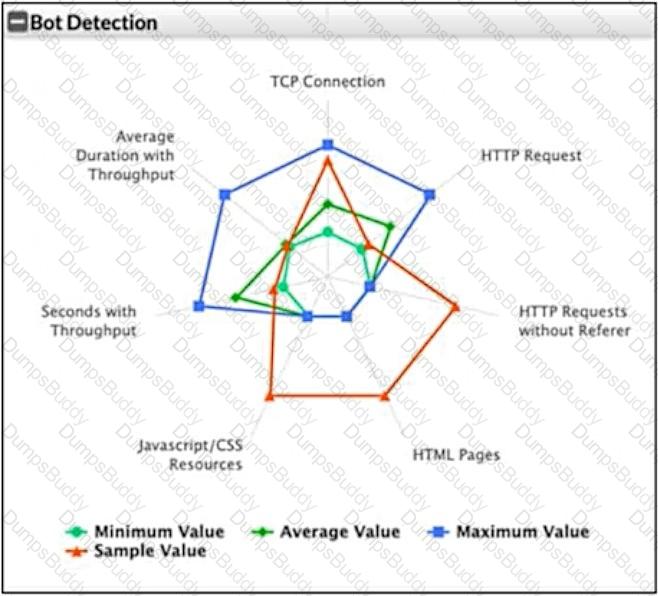
What can you conclude from this support vector machine (SVM) plot of a potential bot connection?
Refer to the exhibits.
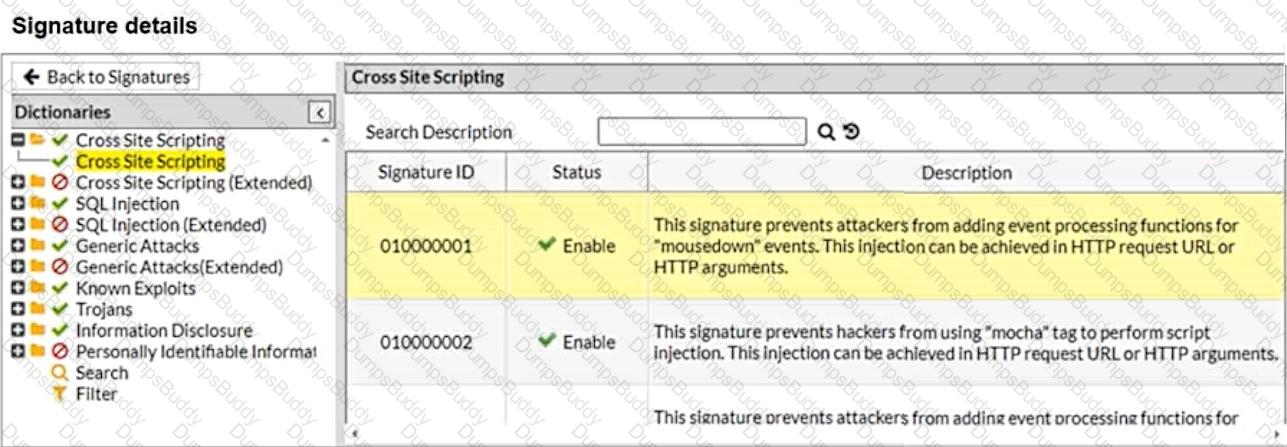
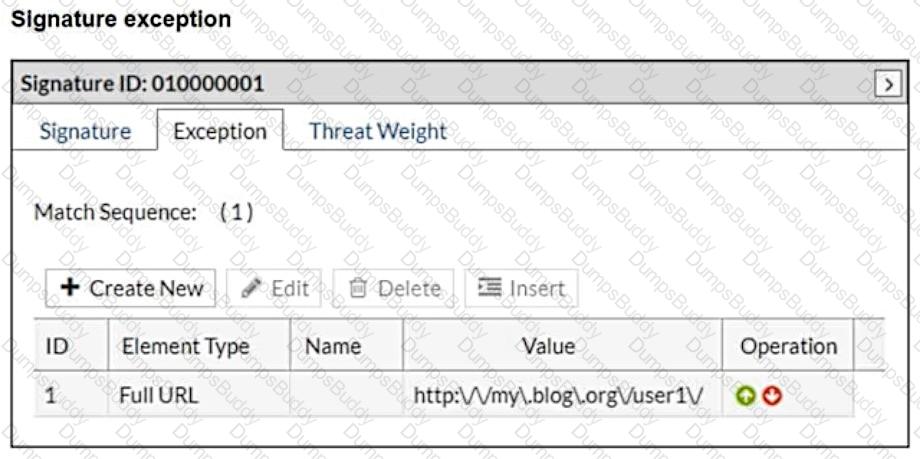
What will happen when a client attempts a mousedown cross-site scripting (XSS) attack against the sitehttp://my.blog.org/userl1/blog.php and FortiWeb is enforcing the highlighted signature?
Which two functions does the first layer of the FortiWeb anomaly machine learning (ML) analysis mechanism perform? (Choose two.)


