FCP_FML_AD-7.4 FCP - FortiMail 7.4 Administrator Questions and Answers
Refer to the exhibit which displays a topology diagram.
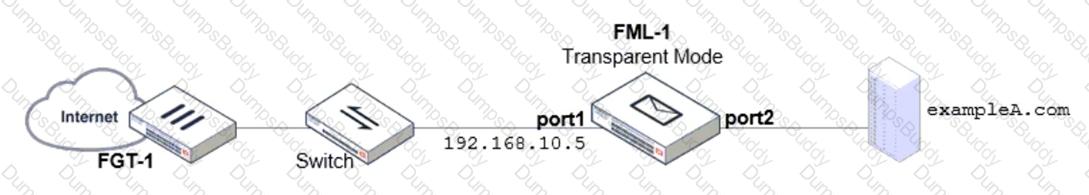
Which two statements describe the built-in bridge functionality on a transparent mode FortiMail? (Choose two.)
Exhibit.
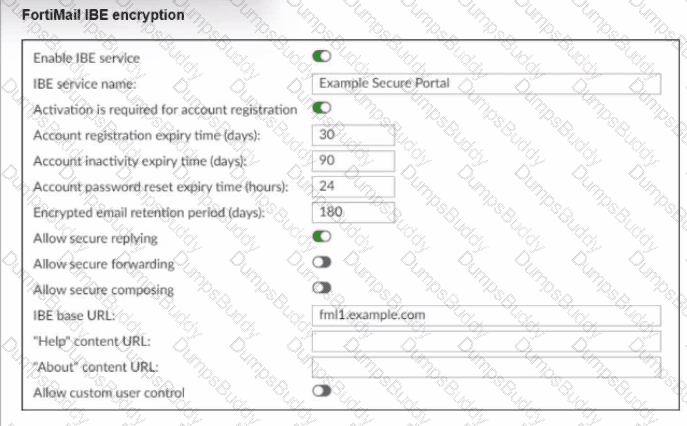
Reter to the exhibit, which shows the IBE Encryption page of a FortiMail device. Which user account behavior can you expect from these IBE settings?
Exhibit.
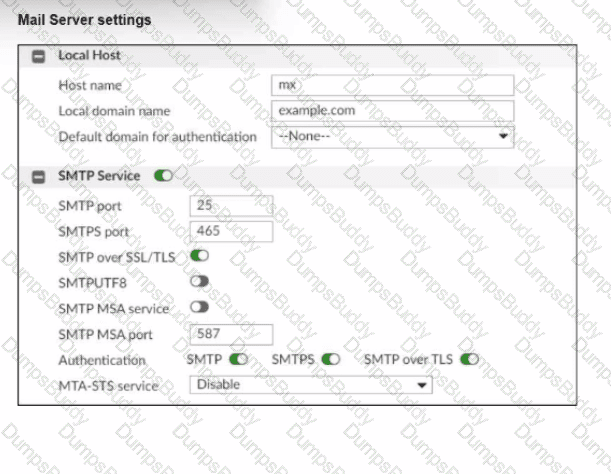
Refer to the exhibit, which shows the mail server settings of a FortiMail device. What are two ways this FortiMail device will handle connections? (Choose two.)
A FortiMail device is configured with the protected domain example. com.
It senders are not authenticated, which two envelope addresses will require an access receive rule? (Choose two.)
Which three configuration steps must you set to enable DKIM signing for outbound messages on FortiMail? (Choose three.}
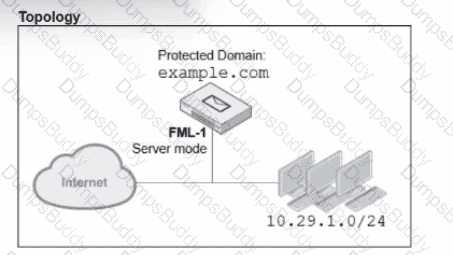
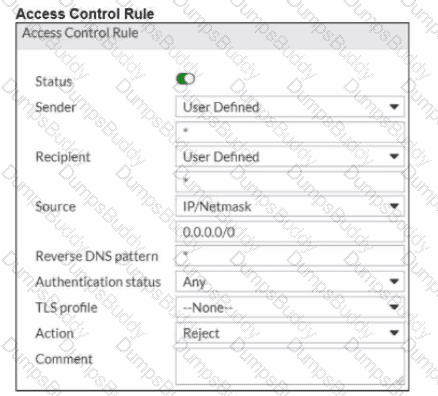
Refer to the exhibits, which show a topology diagram (Topology) and a configurationelement (Access Control Rule.)
An administrator wants to configure an access receive rule to matchauthentication status on FML-1 for all outbound email from the example. co- domain.
Which two access receive rule settings must the administrator configure? (Choose two.)
A FortiMail administrator is investigating a sudden increase in DSNs being delivered to their protected domain. After searching the logs, the administrator identifies that the DSNs werenotgenerated because of any outbound email sent from their organization.
Which FortiMail antispam technique can the administrator use to prevent this scenario?
Refer to the exhibit, which displays an access control rule.
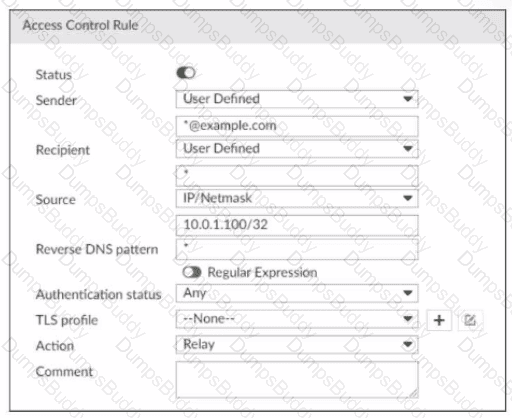
What are two expected behaviors for this access control rule? (Choose two.)
What are two disadvantages of configuring the dictionary and DLP scan rule aggressiveness too high? (Choose two.)
Refer to the exhibit which shows a detailed history log view.
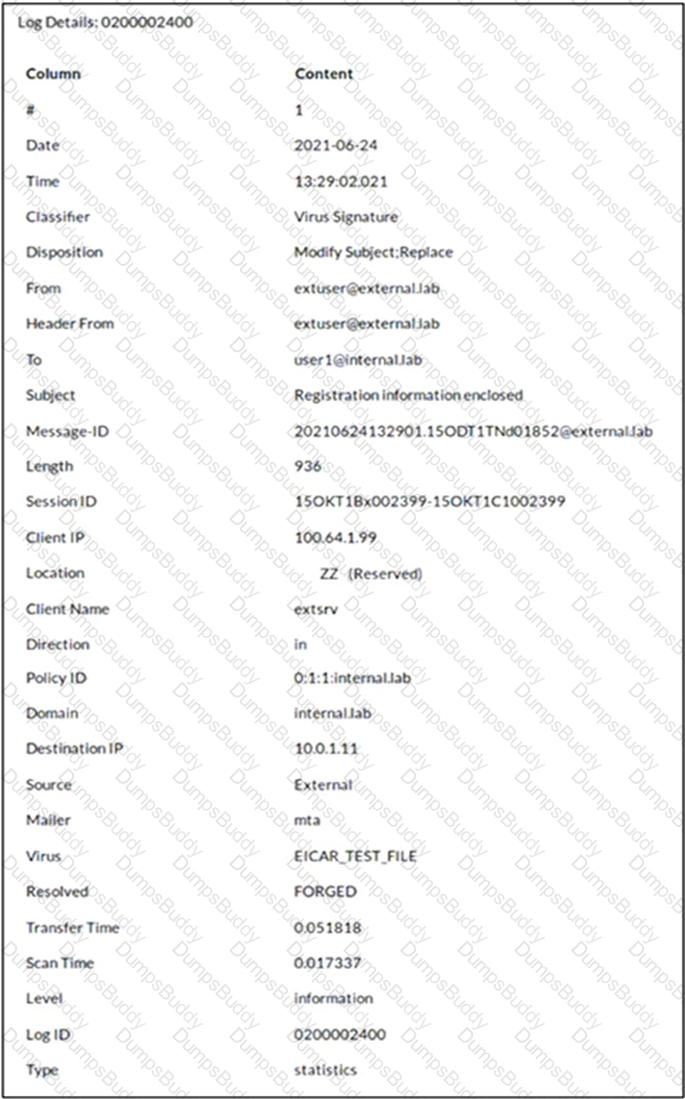
Which two actions did FortiMail take on this email message? (Choose two.)
Refer to the exhibit which shows annslookupoutput of MX records of theexample.comdomain.
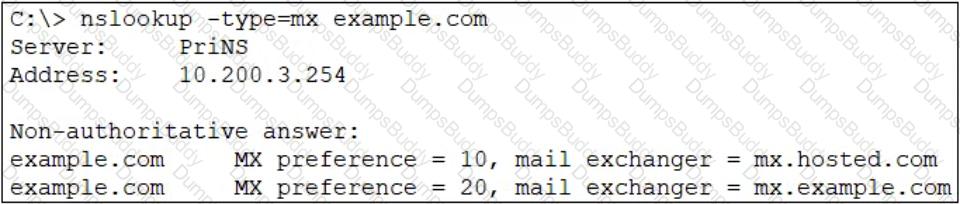
Which two MTA selection behaviors for theexample.comdomain are correct? (Choose two.)
Refer to the exhibit, which displays an encryption profile configuration.
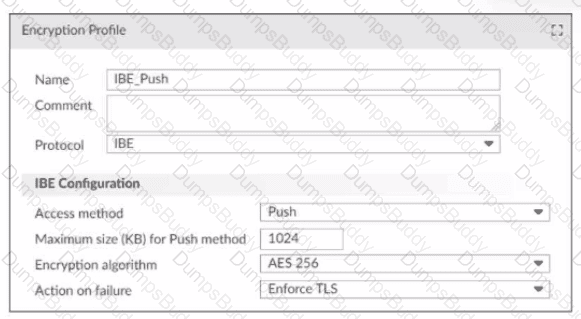
What happens if the attachment size of an IBE email exceeds 1024 KB?


