D-PCR-DY-01 Dell PowerProtect Cyber Recovery Deploy v2 Exam Questions and Answers
Which common cyber-attack overwhelms the resources of the system with excessive requests that consume all the resources to bring it down?
What is the purpose of the command crsetup. sh --install in the context of Dell PowerProtect Cyber Recovery software?
What component orchestrates synchronization, locking, and recovery operations in the vault environment?
What is a pre-requisite for performing Automated Recovery of Dell PowerProtect Data Manager?
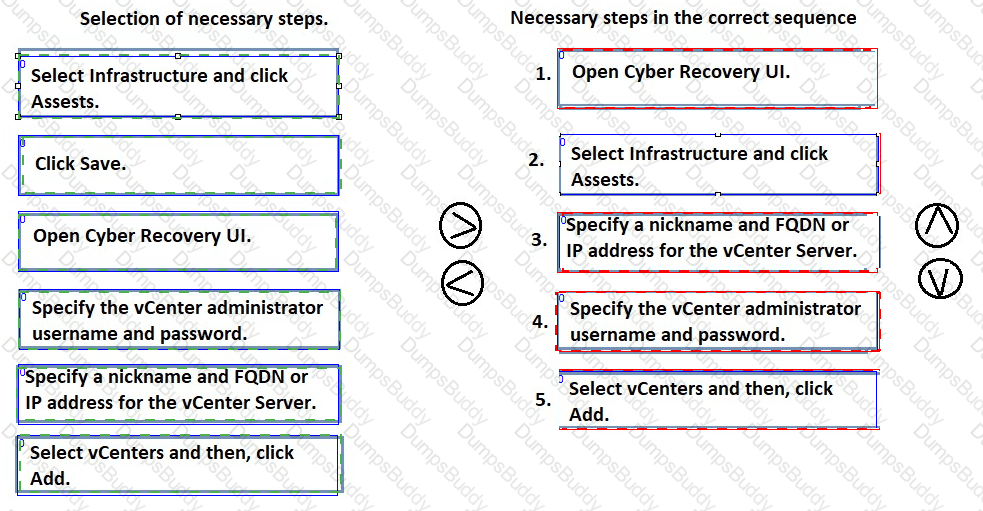
DRAG DROP
When you install a vCenter Server in an on-premises Dell PowerProtect Cyber Recovery vault, you must register it with the PowerProtect Cyber Recovery software. Arrange the necessary steps in chronological order.
Which describes the best use of Dell PowerProtect Data Domain in an isolated clean room?
After successfully completing the PoC for the Dell PowerProtect Cyber Recovery solution with Dell APEX Protection Storage All-Flash, the customer decided to purchase a license for the further use in the production environment.
Which information is required to generate the License Authorization Code (LAC) for the Dell APEX Protection Storage instance?
Which is the best practice when securing PowerProtect Data Domain in Dell PowerProtect Cyber Recovery vault?