D-ISM-FN-23 Dell Information Storage and Management Foundations 2023 Exam Questions and Answers
What is a benefit of using a Scale-Out NAS system vs. general purpose file servers?
An organization is planning to adopt pre integrated systems to deploy compute, network, storage, and management functions as a single engineered solution.
Which approach should the organization adopt?
An organization is planning to adopt pre-integrated systems to deploy compute, network, storage, and management functions as a single engineered solution.
Which approach should the organization adopt?
Which block storage device protocol achieves the optimal cost-effective balance between I/O performance and high storage capacity for midrange storage applications?
What is an advantage of performing incremental backups compared to cumulative backups for the same data?
Which block storage volume allocates all of the physical storage specified at the time it is created?
An organization is interested in a cloud service that provides middleware, development tools, and database management systems for application development and deployment.
Which cloud service model meets these requirements?
An organization wants to consume compute, network, and storage resources through self-service portal.
Which cloud service model provides this capability?
Which data deduplication method increases the probability of identifying duplicate data even when there is only a minor difference between two documents?
Which loT architecture component provides the connection to monitor and control user devices? (First Choose Correct option and give detailed explanation delltechnologies.com)
Which type of machine learning algorithm produces results using a reward and feedback mechanism?
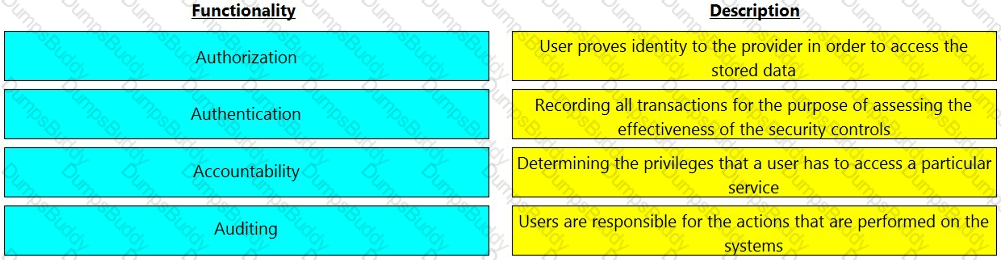
What is an accurate statement about Challenge Handshake Authentication Protocol (CHAP) control?
An Ethernet switch has eight ports and all ports must be operational for 24 hours from Monday through Friday. However, failures of Port 6 occur within the week as follows:
Tuesday = 6 AM to 8 AM
Thursday = 5 PM to 10 PM
Friday = 7 AM to 9 AM
What is the MTBF of Port 6?
In a RAID 6 array with four disks, what is the total usable data storage capacity on the array if the disk size is 200 GB?
A Fibre Channel switch has eight ports and all ports must be operational from 6 AM to 6 PM, Monday through Friday.
However, a failure of Port 4 occurs with the week as follows:
Monday= 11 AM to 1 PM
Wednesday= 5 PM to 10 PM
Thursday= 7 AM to 10 AM
Saturday= 11 AM to 1 PM
What is the availability of Port 4 in that week?
What set of factors are used to calculate the disk service time of a hard disk drive?
A company finance department needs 250 GB of storage for their business applications. A LUN is created with 250 GB, and RAID 1 protection. The LUN is configured to support application I/O performance.
If storage cost is $2 per GB, what is the chargeback amount to the department for application storage?
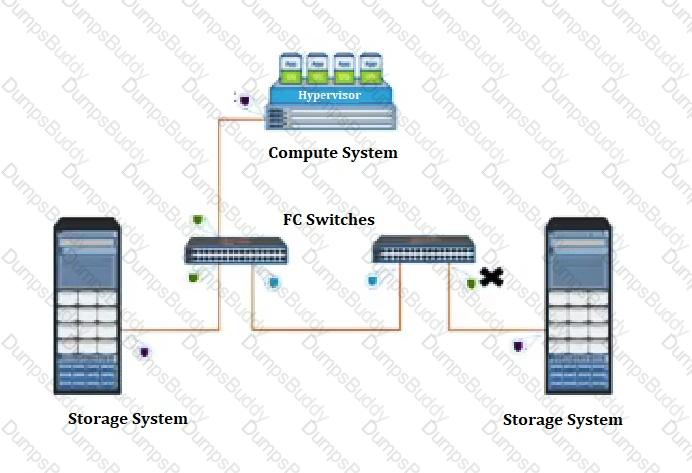
In a modern data center environment, which mechanism secures internal assets while allowing Internet-based access to selected resources?
What is a key benefit for deploying a remote data protection and recovery solution in a data center environment?
Which network file sharing protocol provides cloud-based file sharing through a REST API interface?
Which interface does an SCM device use to connect to intelligent storage system controllers?
A company's assets are continuously under attack.
To deploy a security control mechanism to protect these assets, what should be considered?
If the erasure coding technique used divides data into 12 data segments and 5 coding segments, what is the maximum number of disk drive failures against which data is protected by the configuration?
In a software-defined networking architecture, which layer is responsible for handling data packet forwarding or dropping?
What is a function of the metadata service in an object-based storage device (OSD)?
How should vulnerabilities be managed in a data center environment? (Verify the Correct answer from Associate - Information Storage and Management Study Manual from dellemc.com)
A Fibre Channel switch has eight ports and all ports must be operational from 8 AM to 8 PM, Monday through Friday. However, a failure of Port 7 occurs in the week as follows:
Monday = 11 AM to 12 PM
Wednesday = 4 PM to 9 PM
Thursday = 4 AM to 9 AM
Friday = 2 PM to6 PM
Saturday = 9 AM to 1 PM
What is the availability of Port 7 in that week?
What is true about scale-out NAS storage architecture? (First Choose Correct option and give detailed explanation delltechnologies.com)
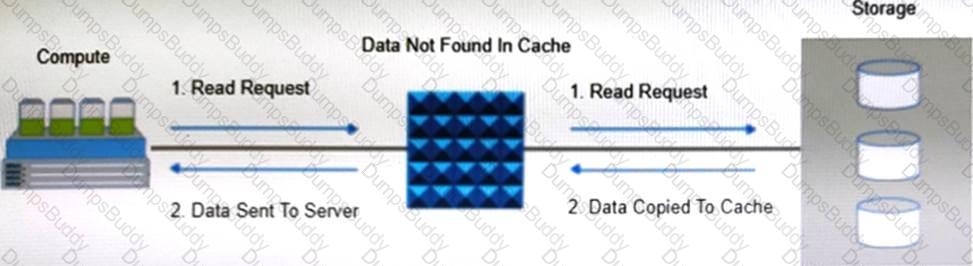
What is an advantage of deploying intelligent storage systems in the data center?
What is the maximum number of VLANs that can be supported with one VLAN tag field?
Which management monitoring parameter involves examining the amount of infrastructure resources used?
What is the functionality of the application server in a Mobile Device Management?
An organization wants to deploy a VM storage migration solution into their data center environment.
What is the result of deploying this type of solution?
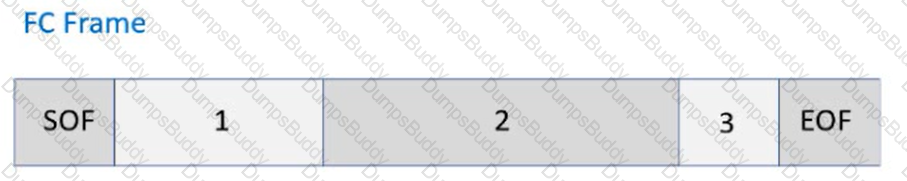
Which layer of the OSI reference model provides logical end-to-end connections, sequencing, and integrity?
What type of technology is used in SSD devices to provide non-volatile data storage?
What is determined by the amount of space configured for the journal in continuous data protection (CDP) replication?