CFR-410 CyberSec First Responder (CFR) Exam Questions and Answers
A company has noticed a trend of attackers gaining access to corporate mailboxes. Which of the following
would be the BEST action to take to plan for this kind of attack in the future?
Senior management has stated that antivirus software must be installed on all employee workstations. Which
of the following does this statement BEST describe?
Which two answer options correctly highlight the difference between static and dynamic binary analysis techniques? (Choose two.)
When performing a vulnerability assessment from outside the perimeter, which of the following network devices is MOST likely to skew the scan results?
When tracing an attack to the point of origin, which of the following items is critical data to map layer 2 switching?
Which of the following plans helps IT security staff detect, respond to, and recover from a cyber attack?
An employee discovered the default credentials in DB servers, which were found by using a word list of commonly used and default passwords in Hydra, the tool behind the Brute functionality. The use of the word list in Hydra is an example of what type of password cracking?
Which of the following types of attackers would be MOST likely to use multiple zero-day exploits executed against high-value, well-defended targets for the purposes of espionage and sabotage?
Which concept involves having more than one person required to complete a task?
Which common source of vulnerability should be addressed to BEST mitigate against URL redirection attacks?
Recently, a cybersecurity research lab discovered that there is a hacking group focused on hacking into the computers of financial executives in Company A to sell the exfiltrated information to Company B. Which of the
following threat motives does this MOST likely represent?
Which of the following is an automated password cracking technique that uses a combination of uppercase and lowercase letters, 0-9 numbers, and special characters?
Detailed step-by-step instructions to follow during a security incident are considered:
A system administrator pulls records from a database that only requires the use of their general user vs. domain admin account. Use of the general user account demonstrates which of the following concepts?
An incident response team is concerned with verifying the integrity of security information and event
management (SIEM) events after being written to disk. Which of the following represents the BEST option for addressing this concern?
Windows Server 2016 log files can be found in which of the following locations?
While planning a vulnerability assessment on a computer network, which of the following is essential? (Choose two.)
After a hacker obtained a shell on a Linux box, the hacker then sends the exfiltrated data via Domain Name System (DNS). This is an example of which type of data exfiltration?
During an audit, an organization's ability to establish key performance indicators for its service hosting solution is discovered to be weak. What could be the cause of this?
An administrator believes that a system on VLAN 12 is Address Resolution Protocol (ARP) poisoning clients on the network. The administrator attaches a system to VLAN 12 and uses Wireshark to capture traffic. After
reviewing the capture file, the administrator finds no evidence of ARP poisoning. Which of the following actions should the administrator take next?
During a malware-driven distributed denial of service attack, a security researcher found excessive requests to a name server referring to the same domain name and host name encoded in hexadecimal. The malware author used which type of command and control?
A first responder notices a file with a large amount of clipboard information stored in it. Which part of the MITRE ATT&CK matrix has the responder discovered?
What allows a company to restore normal business operations in a matter of minutes or seconds?
Which two answer options are the BEST reasons to conduct post-incident reviews after an incident occurs in an organization? (Choose two.)
According to Payment Card Industry Data Security Standard (PCI DSS) compliance requirements, an organization must retain logs for what length of time?
Which three tools are used for integrity verification of files? (Choose three.)
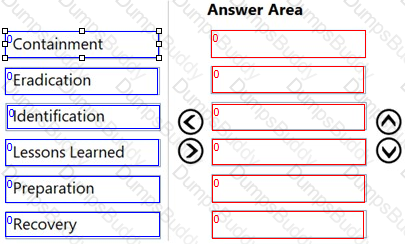
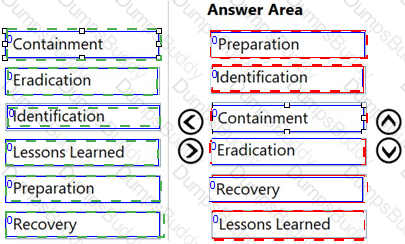
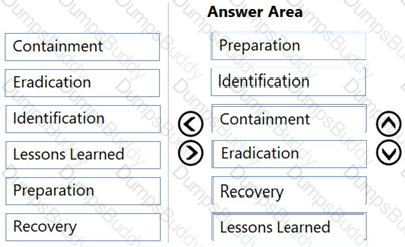
During which phase of the incident response process should an organization develop policies and procedures for incident handling?
When attempting to determine which system or user is generating excessive web traffic, analysis of which of
the following would provide the BEST results?
An incident responder discovers that the CEO logged in from their New York City office and then logged in from a location in Beijing an hour later. The incident responder suspects that the CEO’s account has been
compromised. Which of the following anomalies MOST likely contributed to the incident responder’s suspicion?
The "right to be forgotten" is considered a core tenet of which of the following privacy-focused acts or regulations?
A common formula used to calculate risk is:+ Threats + Vulnerabilities = Risk. Which of the following represents the missing factor in this formula?
After a security breach, a security consultant is hired to perform a vulnerability assessment for a company’s web application. Which of the following tools would the consultant use?
A Windows system administrator has received notification from a security analyst regarding new malware that executes under the process name of “armageddon.exe” along with a request to audit all department workstations for its presence. In the absence of GUI-based tools, what command could the administrator execute to complete this task?
A security analyst has discovered that an application has failed to run. Which of the following is the tool MOST
likely used by the analyst for the initial discovery?
An incident at a government agency has occurred and the following actions were taken:
-Users have regained access to email accounts
-Temporary VPN services have been removed
-Host-based intrusion prevention system (HIPS) and antivirus (AV) signatures have been updated
-Temporary email servers have been decommissioned
Which of the following phases of the incident response process match the actions taken?
A company that maintains a public city infrastructure was breached and information about future city projects was leaked. After the post-incident phase of the process has been completed, which of the following would be
PRIMARY focus of the incident response team?
Which three of the following are included in encryption architecture? (Choose three.)
Which of the following enables security personnel to have the BEST security incident recovery practices?
Which of the following is a cybersecurity solution for insider threats to strengthen information protection?