SECRET-SEN CyberArk Sentry Secrets Manager Questions and Answers
A customer wants to ensure applications can retrieve secrets from Conjur in three different data centers if the Conjur Leader becomes unavailable. Conjur Followers are already deployed in each of these data centers.
How should you architect the solution to support this requirement?
An application is having authentication issues when trying to securely retrieve credential’s from the Vault using the CCP webservices RESTAPI. CyberArk Support advised that further debugging should be enabled on the CCP server to output a trace file to review detailed logs to help isolate the problem.
What best describes how to enable debug for CCP?
You have a request to protect all the properties around a credential object. When configuring the credential in the Vault, you specified the address, user and password for the credential.
How do you configure the Vault Conjur Synchronizer to properly sync all properties?
A Kubernetes application attempting to authenticate to the Follower load balancer receives this error:
ERROR: 2024/10/30 06:07:08 authenticator.go:139: CAKC029E Received invalid response to certificate signing request. Reason: status code 401
When checking the logs, you see this message:
authn-k8s/prd-cluster-01 is not enabled
How do you remediate the issue?
While retrieving a secret through REST, the secret retrieval fails to find a matching secret. You know the secret onboarding process was completed, the secret is in the expected safe with the expected object name, and the CCP is able to provide secrets to other applications.
What is the most likely cause for this issue?
In the event of a failover of the Vault server from the primary to the DR, which configuration option ensures that a CP will continue being able to refresh its cache?
While installing the first CP in an environment, errors that occurred when the environment was created are displayed; however, the installation procedure continued and finished successfully.
What should you do?
After manually failing over to your disaster recovery site (Site B) for testing purposes, you need to failback to your primary site (Site A).
Which step is required?
You start up a Follower and try to connect to it with a REST call using the server certificate, but you get an SSL connection refused error.
What could be the problem and how should you fix it?
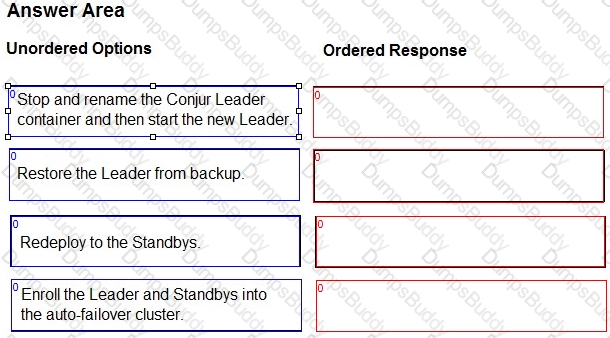
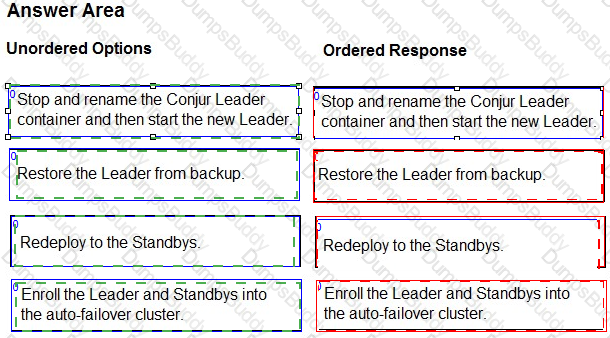
You are upgrading an HA Conjur cluster consisting of 1x Leader, 2x Standbys & 1x Follower. You stopped replication on the Standbys and Followers and took a backup of the Leader.
Arrange the steps to accomplish this in the correct sequence.