ACCESS-DEF CyberArk Defender Access (ACC-DEF) Questions and Answers
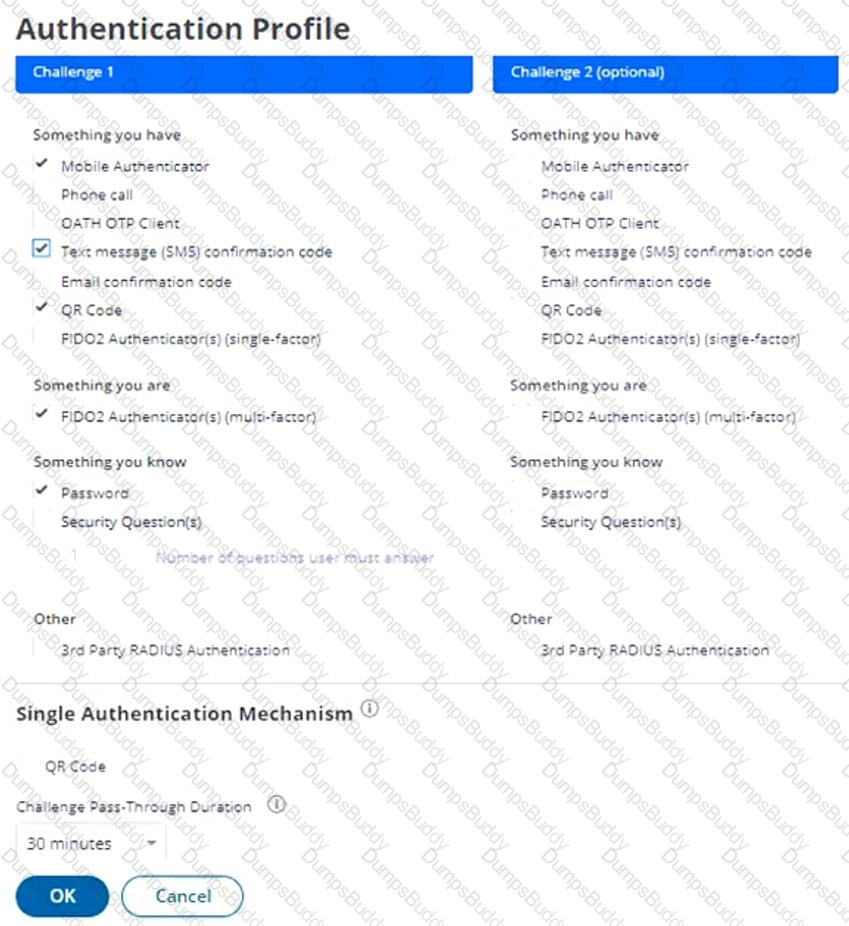
Refer to the exhibit.
How should you configure this default authentication policy to ensure users must authenticate every time they try to access the CyberArk Identity portal or web applications?
Which Custom Template app connectors are appropriate to use if a website does not require user authentication?
You want to find all events related to the user with the login ID of "ivan.helen@acme".
Which filter do you enter into the UBA portal data explorer?
Your team is deploying endpoint authentication onto the corporate endpoints within an organization. Enrollment details include when the enrollment must be completed, and the enrollment code was sent out to the users. Enrollment can be performed in the office or remotely (without the assistance of an IT support engineer). You received feedback that many users are unable to enroll into the system using the enrollment code.
What can you do to resolve this? (Choose two.)
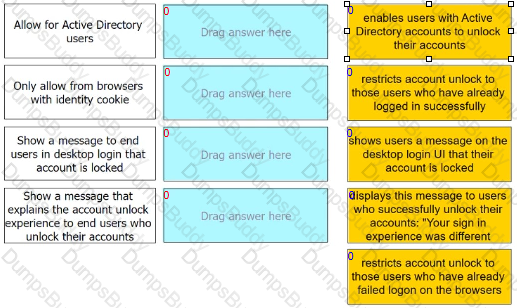
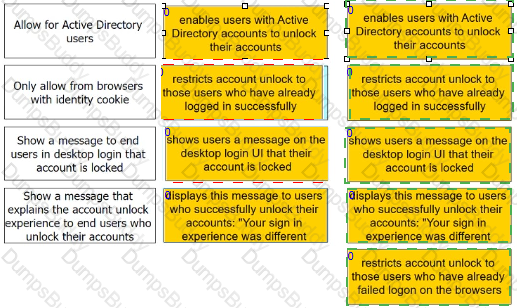
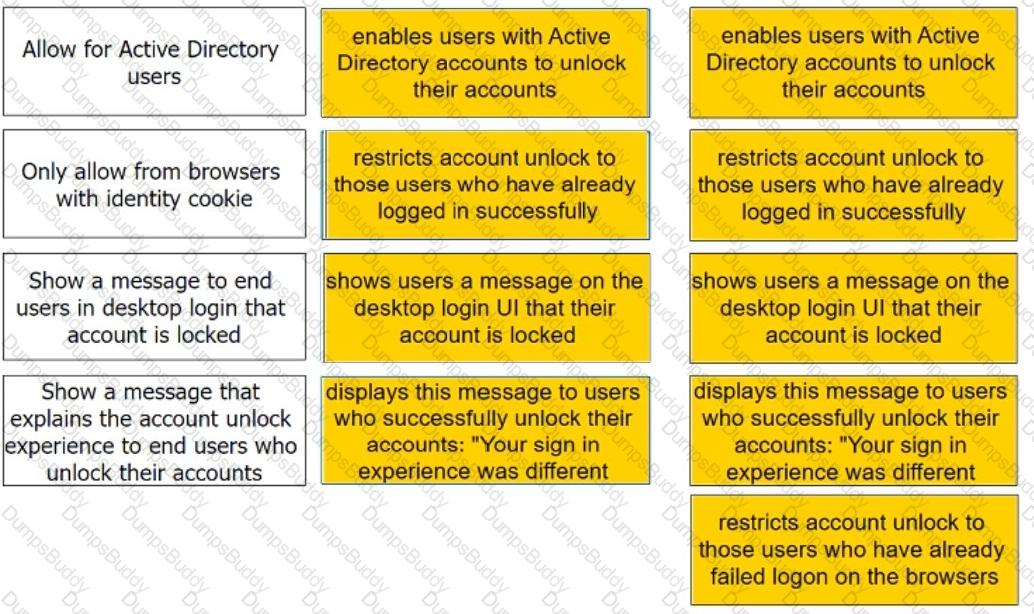
Admins can enable self-service for users to unlock their accounts. There are four options under the Admin Portal Core Services > Policies > User Security Policies > Self Service > Account Unlock options.
Match each option to the correct description.
Your Chief Executive Officer lost his phone and cannot perform MFA to log in to work.
How can you enable him to bypass MFA right away and not delay his work?
As part of compliance regulation, ACME Corporation is enforcing MFA for its critical business web-based application. To increase security and MFA compliance, CyberArk recommends selecting mechanisms from different categories. Within the authentication policy, ACME Corporation made the requirement to configure an authentication mechanism with "Something you know".
Which authentication mechanism meets this requirement?
You get the following error: "Not Authorized. You do not have permission to access this feature".
What is most likely the cause of the error?
Cindy just joined a company's IT Audit Department and needs CyberArk Identity access to perform her daily job activities.
Which administrative right(s) should she be assigned to match her job requirement?
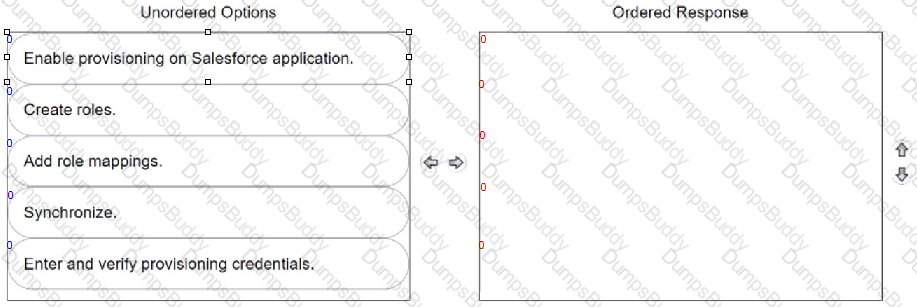
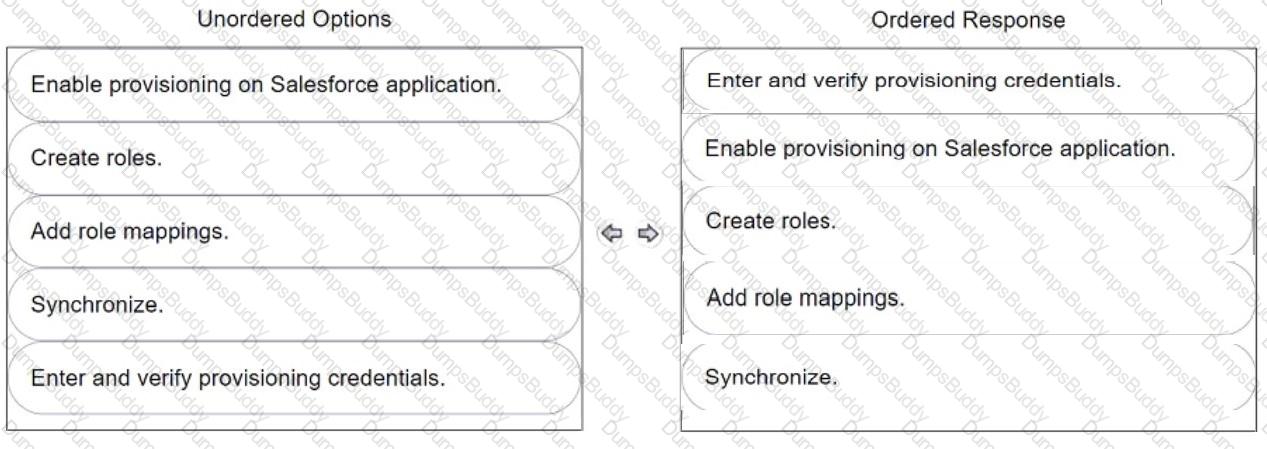
Your organization wants to automatically create user accounts with different Salesforce licenses (e.g., Salesforce, Identity, Chatter External).
In CyberArk Identity, arrange the steps to achieve this in the correct sequence.
 C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg
C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg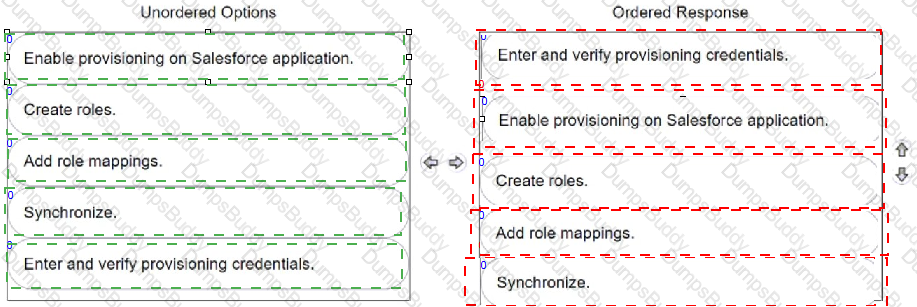
 C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg
C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg

