A cloud administrator needs to implement a mechanism to monitor the expense of the company’s cloud resources.
Which of the following is the BEST option to execute this task with minimal effort?
An IaaS provider has numerous devices and services that are commissioned and decommissioned automatically on an ongoing basis. The cloud administrator needs to implement a solution that will help reduce administrative overhead.
Which of the following will accomplish this task?
A cloud administrator checked out the deployment scripts used to deploy the sandbox environment to a public cloud provider. The administrator modified the script to add an application load balancer in front of the web- based front-end application. The administrator next used the script to recreate a new sandbox environment successfully, and the application was then using the new load balancer.
The following week, a new update was required to add more front-end servers to the sandbox environment. A second administrator made the necessary changes and checked out the deployment scripts. The second administrator then ran the script, but the application load balancer was missing from the new deployment.
Which of the following is the MOST likely reason for this issue?
A cloud administrator is reviewing the authentication and authorization mechanism implemented within the cloud environment. Upon review, the administrator discovers the sales group is part of the finance group, and the sales team members can access the financial application. Single sign-on is also implemented, which makes access much easier.
Which of the following access control rules should be changed?
A systems administrator is deploying a GPU-accelerated VDI solution. Upon requests from several users, the administrator installs an older version of the OS on their virtual workstations. The majority of the VMs run the latest LTS version of the OS.
Which of the following types of drivers will MOST likely ensure compatibility will all virtual workstations?
An organization is running a database application on a SATA disk, and a customer is experiencing slow performance most of the time.
Which of the following should be implemented to improve application performance?
An OS administrator is reporting slow storage throughput on a few VMs in a private IaaS cloud. Performance graphs on the host show no increase in CPU or memory. However, performance graphs on the storage show a decrease of throughput in both IOPS and MBps but not much increase in latency. There is no increase in workload, and latency is stable on the NFS storage arrays that are used by those VMs.
Which of the following should be verified NEXT?
A systems administrator needs to modify the replication factors of an automated application container from 3 to 5. Which of the following file types should the systems administrator modify on the master controller?
A systems administrator is building a new virtualization cluster. The cluster consists of five virtual hosts, which each have flash and spinning disks. This storage is shared among all the virtual hosts, where a virtual machine running on one host may store data on another host.
This is an example of:
A DevOps administrator is building a new application slack in a private cloud. This application will store sensitive information and be accessible from the internet. Which of the following would be MOST useful in maintaining confidentiality?
A company wants to check its infrastructure and application for security issues regularly. Which of the following should the company implement?
A cloud administrator is switching hosting companies and using the same script that was previously used to deploy VMs in the new cloud. The script is returning errors that the command was not found.
Which of the following is the MOST likely cause of the script failure?
A company wants to utilize its private cloud for a new application. The private cloud resources can meet 75% of the application's resource requirements. Which of the following
scaling techniques can the cloud administrator implement to accommodate 100% of the application's requirements?
A security team is conducting an audit of the security group configurations for the Linux servers that are hosted in a public laaS. The team identifies the following rule as a potential

A cloud administrator, who is working remotely, logs in to the cloud management console and modifies the rule to set the source to "My IR" Shortly after deploying the rule, an internal developer receives the following error message when attempting to log in to the server using SSH: Network error: connection timed out. However, the administrator is able to connect successfully to the same server using SSH. Which of the following is the BEST option for both the developer and the administrator to access the
server from their locations?
A systems administrator is reviewing two CPU models for a cloud deployment. Both CPUs have the same number of cores/threads and run at the same clock speed.
Which of the following will BEST identify the CPU with more computational power?
A company has decided to get multiple compliance and security certifications for its public cloud environment. However, the company has few staff members to handle the extra workload, and it has limited knowledge of the current infrastructure.
Which of the following will help the company meet the compliance requirements as quickly as possible?
An organization has two businesses that are developing different software products. They are using a single cloud provider with multiple IaaS instances. The organization identifies that the tracking of costs for each
business are inaccurate.
Which of the following is the BEST method for resolving this issue?
A systems administrator wants to have near-real-time information on the volume of data being exchanged between an application server and its clients on the Internet.
Which of the following should the systems administrator implement to achieve this objective?
Which of the following cloud deployment models allows a company to have full control over its IT infrastructure?
A systems administrator is configuring a storage system for maximum performance and redundancy. Which of the following storage technologies should the administrator use to achieve this?
A company is currently running a website on site. However, because of a business requirement to reduce current RTO from 12 hours to one hour, and the RPO from one day to eight hours, the company is considering operating in a hybrid environment. The website uses mostly static files and a small relational database. Which of the following should the cloud architect implement to achieve the objective at the LOWEST cost possible?
A systems administrator is deploying a new virtualized environment. The setup is a three-server cluster with 12 VMs running on each server. While executing a vertical-scaling test of the vCPU on the VMs, the administrator gets an error. Which of the following issues is MOST likely occurring?
A company is considering consolidating a number of physical machines into a virtual infrastructure that will be located at its main office. The company has the following requirements:
High-performance VMs
More secure
Has system independence
Which of the following is the BEST platform for the company to use?
A company is migrating workloads from on premises to the cloud and would like to establish a connection between the entire data center and the cloud environment. Which of the following VPN configurations would accomplish this task?
A piece of software applies licensing fees on a socket-based model. Which of the following is the MOST important consideration when attempting to calculate the licensing costs for this software?
A financial industry services firm was the victim of an internal data breach, and the perpetrator was a member of the company's development team. During the investigation, one of the security administrators accidentally deleted the perpetrator's user data. Even though the data is recoverable, which of the following has been violated?
A security audit related to confidentiality controls found the following transactions occurring in the system:
GET http://gateway.securetransaction.com/privileged/api/v1/changeResource?id=123 &user=277
Which of the following solutions will solve the audit finding?
A systems administrator needs to deploy a solution to automate new application releases that come from the development team. The administrator is responsible for provisioning resources at the infrastructure layer without modifying any configurations in the application code. Which of the following would BEST accomplish this task?
A cloud security engineer needs to ensure authentication to the cloud pro-vider console is secure. Which of the following would BEST achieve this ob-jective?
A systems administrator is asked to implement a new three-host cluster. The cloud architect specifies this should be a testing environment, and the budget is limited. The estimated resource consumption for each application is as follows:

A cloud administrator configured a local cloud-resource pool lo offer 64GB of memory, 64 cores, and 640GB of storage. Thirty-two machines with identical resource allocations are started. but one machine is unable to handle requests. Which of the following is the MOST likely cause?
A company is switching from one cloud provider to another and needs to complete the migration as quickly as possible.
Which of the following is the MOST important consideration to ensure a seamless migration?
A security analyst is investigating incidents in which attackers are able to access sensitive data from a corporate application's database. The attacks occur periodically and usually
after the release of a new application's version. The following log confirms the compromise:
The following actions are made after every incident occurrence:
• Validation of firewall rules
• Scripted rebuild of the database and web instances
• Application deployment from a cloud code repository
Which of the following actions will MOST likely prevent future compromises?
A web-application company recently released some new marketing promotions without notifying the IT staff. The systems administrator has since been noticing twice the normal traffic consumption every two hours for the last three hours in the container environment. Which of the following should the company implement to accommodate the new traffic?
A company has two primary offices, one in the United States and one in Europe. The company uses a public laaS service that has a global data center presence to host its marketing materials. The marketing team, which is primarily based in Europe, has reported latency issues when retrieving these materials. Which of the following is the BEST option to reduce the latency issues?
A systems administrator is troubleshooting performance issues with a Windows VDI environment. Users have reported that VDI performance is very slow at the start of the workday, but the performance is fine during the rest of the day. Which of the following is the MOST likely cause of the issue? (Select TWO).
An administrator manages a file server that has a lot of users accessing and creating many files. As a result, the storage consumption is growing quickly. Which of the following would BEST control storage usage?
A systems administrator is securing a new email system for a large corporation. The administrator wants to ensure private corporate information is not emailed to external users. Which of the following would be MOST useful to accomplish this task?
An administrator needs to back up all the data from each VM daily while also saving space. Which of the following backup types will BEST fit this scenario?
A web application has been configured to use autoscaling for provisioning and deprovisioning more VMs according to the workload. The systems administrator deployed a new CI/CD tool to automate new releases of the web application. During the night, a script was deployed and configured to be executed by the VMs during bootstrapping. Now. the autoscaling configuration is creating a new VM ever\ five minutes. Which of the following actions will MOS I like y resolve the issue?
In an IaaS platform, which of the following actions would a systems administrator take FIRST to identify the scope of an incident?
A cloud engineer has deployed a virtual storage appliance into a public cloud environment. The storage appliance has a NAT to a public IP address. An administrator later notices there are some strange files on the storage appliance and a large spike in network traffic on the machine. Which of the following is the MOST likely cause?
A local bank has all of its infrastructure in the cloud. An update was applied to the main database server at 5:00 a.m. on Monday morning, and the database was then corrupted and unusable. It had to be restored from backup. The last backup was taken the night before at 10:00 p.m. The database was then restored successfully, but seven hours' worth of data was lost, which is deemed unacceptable. Which of the following needs to be updated in the DR plan?
A systems administrator is trying to reduce storage consumption. Which of the following file types would benefit the MOST from compression?
A cloud administrator is planning to migrate a globally accessed application to the cloud.
Which of the following should the cloud administrator implement to BEST reduce latency for all users?
A company is using a method of tests and upgrades in which a small set of end users are exposed to new services before the majority of other users. Which of the following deployment methods is being used?
A systems administrator is planning a penetration test for company resources that are hosted in a public cloud. Which of the following must the systems administrator do FIRST?
A cloud administrator is responsible for managing a VDI environment that provides end users with access to limited applications. Which of the following should the administrator make changes to when a new application needs to be provided?
A cloud architect is deploying a web application that contains many large images and will be accessed on two continents. Which of the following will MOST improve the user experience while keeping costs low?
A cloud engineer, who manages workloads in a public cloud environment, uses autoscaling to maintain availability of a critical application. During a recent burst in demands, the engineer received the following error alert:
LimitedlnstanceCapacity
Which of the following is MOST likely cause of the error?
A storage administrator is reviewing the storage consumption of a SAN appliance that is running a VDI environment. Which of the following features should the administrator implement to BEST reduce the storage consumption of the SAN?
A company needs to migrate the storage system and batch jobs from the local storage system to a public cloud provider. Which of the following accounts will MOST likely be created to run the batch processes?
A development team recently completed testing changes to a company's web-based CMS in the sandbox environment. The cloud administrator deployed these CMS application changes to the staging environment as part of the next phase in the release life cycle. The deployment was successful, but after deploying the CMS application, the web page displays an error message stating the application is unavailable. After reviewing the application logs, the administrator sees an error message that the CMS is unable to connect to the database. Which of the following is the BEST action for the cloud administrator to perform to resolve the issue?
A cloud security analyst needs to ensure the web servers in the public subnet allow only secure communications and must remediate any possible issue. The stateful configuration for the public web servers is as follows:

Which of the following actions should the analyst take to accomplish the objective?
An organization is using multiple SaaS-based business applications, and the systems administrator is unable to monitor and control the use of these subscriptions. The administrator needs to implement a solution that will help the organization apply security policies and monitor each individual SaaS subscription. Which of the following should be deployed to achieve these requirements?
A systems administrator is using a configuration management tool to perform maintenance tasks in a system. The tool is leveraging the target system's API to perform these maintenance tasks After a number of features and security updates are applied to the target system, the configuration management tool no longer works as expected. Which of the following is the MOST likely cause of the issue?
A systems administrator adds servers to a round-robin, load-balanced pool, and then starts receiving reports of the website being intermittently unavailable. Which of the following is the MOST likely cause of the issue?
A DevOps administrator is automating an existing software development workflow. The administrator wants to ensure that prior to any new code going into production, tests confirm the new code does not negatively impact existing automation activities.
Which of the following testing techniques would be BEST to use?
An administrator is performing an in-place upgrade on a quest VM operating system.
Which of the following can be performed as a quick method to roll back to an earlier state, if necessary?
A cloud administrator set up a link between the private and public cloud through a VPN tunnel. As part of the migration, a large set of files will be copied. Which of the following network ports are required from a security perspective?
A cloud solutions architect needs to determine the best strategy to deploy an application environment in production, given the following requirements:
No downtime
Instant switch to a new version using traffic control for all users
Which of the following deployment strategies would be the BEST solution?
A resource pool in a cloud tenant has 90 GB of memory and 120 cores. The cloud administrator needs to maintain a 30% buffer for resources for optimal performance of the hypervisor. Which of the following would all ow for the maximum number of two-core machines with equal memory?
A systems administrator is performing upgrades to all the hypervisors in the environment. Which of the following components of the hypervisors should be upgraded? (Choose two.)
A cloud administrator wants to have a central repository for all the logs in the company’s private cloud. Which of the following should be implemented to BEST meet this requirement?
An administrator recently provisioned a file server in the cloud. Based on financial considerations, the administrator has a limited amount of disk space. Which of the following will help control the amount of space that is being used?
A cloud administrator would like to deploy a cloud solution to its provider using automation techniques. Which of the following must be used? (Choose two.)
A cloud administrator is building a new VM for machine-learning training. The developer requesting the VM has stated that the machine will need a full GPU dedicated to it.
Which of the following configuration options would BEST meet this requirement?
A company is planning to migrate applications to a public cloud, and the Chief Information Officer (CIO) would like to know the cost per business unit for the applications in the cloud. Before the migration, which of the following should the administrator implement FIRST to assist with reporting the cost for each business unit?
A cloud administrator has been using a custom VM deployment script. After three months of use, the script no longer joins the LDAP domain. The cloud administrator verifies the account has the correct permissions. Which of the following is the MOST likely cause of the failure?
A technician just received the lessons learned from some recent data that was lost due to an on-premises file-server crash. The action point is to change the backup strategy to minimize manual intervention. Which of the following is the BEST approach for the technician to implement?
A technician is trying to delete six decommissioned VMs. Four VMs were deleted without issue. However, two of the VMs cannot be deleted due to an error. Which of the following would MOST likely enable the technician to delete the VMs?
A company wants to move its environment from on premises to the cloud without vendor lock-in. Which of the following would BEST meet this requirement?
A Chief Information Security Officer (CISO) is evaluating the company’s security management program. The CISO needs to locate all the assets with identified deviations and mitigation measures. Which of the following would help the CISO with these requirements?
An organization is developing a new solution for hosting an external website. The systems administrator needs the ability to manage the OS. Which of the following methods would be MOST suitable to achieve this objective?
A systems administrator is troubleshooting a performance issue with a virtual database server. The administrator has identified the issue as being disk related and believes the cause is a lack of IOPS on the existing spinning disk storage. Which of the following should the administrator do NEXT to resolve this issue?
A systems administrator needs to implement a way for users to verify software integrity. Which of the following tools would BEST meet the administrator's needs?
A systems administrator has migrated a web application to the cloud with a synchronous uplink speed of 100Mbps. After the migration, the administrator receives reports of slow connectivity to the web application. The administrator logs into the firewall and notices the WAN port is transmitting at a constant 12.5MBps. Which of the following BEST explains the reason for the issue?
Some VMs that are hosted on a dedicated host server have each been allocated with 32GB of memory. Some of VMs are not utilizing more than 30% of the allocation. Which of the following should be enabled to optimize the memory utilization?
A technician needs to deploy two virtual machines in preparation for the configuration of a financial application next week. Which of the following cloud deployment models should the technician use?
All of a company's servers are currently hosted in one cloud MSP. The company created a new cloud environment with a different MSP. A cloud engineer is now tasked with preparing for server migrations and establishing connectivity between clouds. Which of the following should the engineer perform FIRST?
A cloud administrator who is troubleshooting DNS issues discovers zone transfers are not occurring between the primary and secondary name servers due to an error in the serial numbers. Which of the following records should the administrator query for the serial number?
A systems administrator wants to be notified every time an application's configuration files are updated. Which of the following should the administrator implement to achieve the objective?
A company is doing a cloud-to-cloud migration to lower costs. A systems administrator has to plan the migration accordingly.
Which of the following considerations is MOST important for a successful, future-proof, and low-cost migration?
A systems administrator deployed a new web application in a public cloud and would like to test it, but the company's network firewall is only allowing outside connections to the cloud provider network using TCP port 22. While waiting for the network administrator to open the required ports, which of the following actions should the systems administrator take to test the new application? (Select two).
A company has a web application running in an on-premises environment that needs to be migrated to the cloud. The company wants to implement a solution that maximizes scalability, availability, and security, while requiring no infrastructure administration. Which of the following services would be BEST to meet this goal?
A cloud administrator created a developer desktop image and added it to the VDI farm in a private cloud environment. One of the developers opened a VDI session and noticed that compiling the code was taking up to one hour to complete. However, when the developer compiles the code on a local machine, the job completes in less than five minutes. Which of the following sizing techniques would be best to use to improve the performance of the compile job?
A cloud administrator received a request to provision a set of cloud resources in an effort to switch to infrastructure as code to automate and optimize operations. The administrator decides to try to run some tests with the following definition:

Which of the following is the most likely cause of the issue?
An organization deployed an application using a cloud provider's internal managed certificates. Developers are unable to retrieve data when calling the API from any machine.
The following error message is in the log:
12-04-2023-10:05:25, SSL Negotiation Error
12-04-2023-10:05:28,Invalid Certificate
12-04-2023-10:05:29, TLS Handshake Failed
12-04-2023-10:05:30,Connection Closed
Which of the following is the most likely cause of the error?
A company has entered into a business relationship with another organization and needs to provide access to internal resources through directory services. Which of the following should a systems administrator implement?
A company is concerned it will run out of VLANs on its private cloud platform in the next couple months, and the product currently offered to customers requires the company to allocate three dedicated, segmented tiers. Which of the following can the company implement to continue adding new customers and to maintain the required level of isolation from other tenants?
A cloud administrator created four VLANs to autoscale the container environment. Two of the VLANs are on premises, while two VLANs are on a public cloud provider with a direct link between them. Firewalls are between the links with an additional subnet for communication, which is 192.168.5.0/24.
The on-premises gateways are:
192.168.1.1/24
192.168.2.1/24
The cloud gateways are:
192.168.3.1/24
192.168.4.1/24
The orchestrator is unable to communicate with the cloud subnets. Which Of the following should the administrator do to resolve the issue?
A company is comparing an application environment to be hosted on site versus a SaaS model of the same application. Which of the following SaaS-based licensing models should the administrator consider?
An integration application that communicates between different application and database servers is currently hosted on a physical machine. A P2V migration needs to be done to reduce the hardware footprint. Which of the following should be considered to maintain the same level of network throughput and latency in the virtual server?
A systems administrator is implementing a new version of a company's primary human-resources application. An upgrade will be performed on the production server, as there is no development environment. The administrator needs to have a
plan in case something goes wrong with the upgrade. Which of the following will work best to ensure a quick rollback in case an issue arises?
A cloud solutions architect has an environment that must only be accessed during work hours. Which of the following processes should be automated to best reduce cost?
Based on the shared responsibility model, which of the following solutions passes the responsibility of patching the OS to the customer?
An organization is conducting a performance test of a public application. The following actions have already been completed:
• The baseline performance has been established.
• A load test has passed.
• A benchmark report has been generated.
Which of the following needs to be done to conclude the performance test?
A cloud administrator has deployed a website and needs to improve the site security to meet requirements. The website architecture is designed to have a DBaaS in the back end and autoscaling instances in the front end using a load balancer to distribute the request. Which of the following will the cloud administrator most likely use?
A systems administrator is implementing a new file storage service that has been deployed in the company's private cloud instance. The key requirement is fast read/write times for the targeted users, and the budget for this project is not a concern. Which of the following storage types should the administrator deploy?
A web consultancy group currently works in an isolated development environment. The group uses this environment for the creation of the final solution, but also for showcasing it to customers, before commissioning the sites in production. Recently, customers of newly commissioned sites have reported they are not receiving the final product shown by the group, and the website is performing in unexpected ways. Which of the following additional environments should the group adopt and include in its process?
A systems administrator is trying to connect to a remote KVM host. The command line appears as follows:

After logging in to the remote server, the administrator verifies the daemon is running. Which of the following should the administrator try NEXT?
An application deployment team has observed delays in deployments and has asked the cloud administrator to evaluate the issue. Below is the result of a latency test that was conducted by the cloud administrator from offices located in the following regions:
• Asia-Pacific (APAC)
• Europe, the Middle East, and Africa (EMEA)
• Americas
Tests were conducted from each location, and the results are shown below:

Which of the following locations needs to be investigated further?
A systems administrator receives a ticket stating the following:
“The programming team received an error during the process deploying applications to the container platform. The error after the containerized applications were created”
Which the following should the administrator Check FIRST?
A systems administrator notices the host filesystem is running out of storage space. Which of the following will best reduce the storage space on the system?
A company plans to publish a new application and must conform with security standards. Which of the following types of testing are most important for the systems administrator to run to assure the security and compliance of the application before publishing? (Select two).
A company would like to move all its on-premises platforms to the cloud. The company has enough skilled Linux and web-server engineers but only a couple of skilled database administrators. It also has little expertise in managing email services. Which of the following solutions would BEST match the skill sets of available personnel?
Following the deployment of a new VM, a cloud engineer notices the backup platform has not added the machine to the appropriate job. The backup platform uses a text-based variable for job configuration. This variable is based on the RPO requirements for the workload. Which of the following did the cloud engineer forget to configure when deploying the virtual machine?
A VDI administrator is deploying 512 desktops for remote workers. Which of the following would meet the minimum number of IP addresses needed for the desktops?
A VDI administrator is enhancing the existing environment with a feature to allow users to connect devices to virtual workstations. Which of the following types of devices are most likely to be allowed in the upgrade? (Select two).
An organization hosts an ERP database in on-premises infrastructure. A recommendation has been made to migrate the ERP solution to reduce operational overhead in the maintenance of the data center. Which of the following should be considered when migrating this on-premises database to DBaaS?
• Database IOPS values
• Database storage utilization
• Physical database server DAS type
• Physical database server network I/O
• Database total number of tables
• Database total number of storage procedures
• Physical database server memory configuration
• Physical database server CPU frequency
An organization located in Asia connects to a cloud infrastructure hosted in North America and Europe. Sporadic slowness has been observed when using the PaaS and laaS components. A diagnostic using the following commands was run, and the following results were collected:
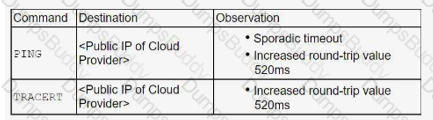
Which of the following is the most likely reason for the latency?
A web consultancy group currently works in an isolated development environment. The group uses this environment for the creation of the final solution, but also for showcasing it to customers, before commissioning the sites in production. Recently, customers of newly commissioned sites have reported they are not receiving the final product shown by the group, and
the website is performing in unexpected ways. Which of the following additional environments should the group adopt and include in its process?
A systems administrator is troubleshooting performance issues with a Windows VDI environment. Users have reported that VDI performance is very slow at the start of the workday, but the performance is fine during the rest of the day. Which of the following is the MOST likely cause of the issue? (Choose two.)
A systems administrator has migrated an internal application to a public cloud. The new web server is running under a TLS connection and has the same TLS certificate as the internal application that is deployed. However, the IT department reports that only internal users who are using new versions of the OSs are able to load the application home page.
Which of the following is the MOST likely cause of the issue?
A company has decided to scale its e-commerce application from its corporate datacenter to a commercial cloud provider to meet an anticipated increase in demand during an upcoming holiday.
The majority of the application load takes place on the application server under normal conditions. For this reason, the company decides to deploy additional application servers into a commercial cloud provider using the on-premises orchestration engine that installs and configures common software and network configurations.
The remote computing environment is connected to the on-premises datacenter via a site-to-site IPSec tunnel. The external DNS provider has been configured to use weighted round-robin routing to load balance connections from the Internet.
During testing, the company discovers that only 20% of connections completed successfully.
INSTRUCTIONS
Review the network architecture and supporting documents and fulfill these requirements:
Part 1:
 Analyze the configuration of the following components: DNS, Firewall 1, Firewall 2, Router 1, Router 2, VPN and Orchestrator Server.
Analyze the configuration of the following components: DNS, Firewall 1, Firewall 2, Router 1, Router 2, VPN and Orchestrator Server.
 Identify the problematic device(s).
Identify the problematic device(s).
Part 2:
 Identify the correct options to provide adequate configuration for hybrid cloud architecture.
Identify the correct options to provide adequate configuration for hybrid cloud architecture.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Part 1:
Cloud Hybrid Network Diagram








Part 2:
Only select a maximum of TWO options from the multiple choice question

A systems administrator wants the VMs on the hypervisor to share CPU resources on the same core when feasible.
Which of the following will BEST achieve this goal?
A systems administrator for an e-commerce company will be migrating the company’s main website to a cloud provider. The principal requirement is that the website must be highly available.
Which of the following will BEST address this requirement?
A cloud architect wants to minimize the risk of having systems administrators in an IaaS compute instance perform application code changes. The development group should be the only group allowed to modify files in the directory.
Which of the following will accomplish the desired objective?
A cloud administrator recently deployed an update to the network drivers of several servers. Following the update, one of the servers no longer responds to remote login requests. The cloud administrator investigates the issue and gathers the following information:
Which of the following is the MOST likely cause of the server being unavailable?