A network administrator needs to resolve connectivity issues in a hybrid cloud setup. Workstations and VMs are not able to access Application A. Workstations are able to access Server B.
INSTRUCTIONS
Click on workstations, VMs, firewalls, and NSGs to troubleshoot and gather information. Type help in the terminal to view a list of available commands.
Select the appropriate device(s) requiring remediation and identify the associated issue(s).
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.












A company hosts a cloud-based e-commerce application and only wants the application accessed from certain locations. The network team configures a cloud firewall with WAF enabled, but users can access the application globally. Which of the following should the network team do?
A network engineer identified several failed log-in attempts to the VPN from a user's account. When the engineer inquired, the user mentioned the IT help desk called and asked them to change their password. Which of the following types of attacks occurred?
An organization with an on-premises data center is adopting additional cloud-based solutions. The organization wants to keep communication secure between remote employees' devices and workloads. Which of the following ZTA features best achieves this goal?
A company has a 40Gbps network that uses a network tap to inspect the traffic using an IDS. The IDS usually performs normally except when the servers are downloading patches from their local update repository 10.10.10.139 using HTTPS. During the patch windows, the IDS cannothandle the extra load and drops a significant number of packets. Which of the following would allow a network engineer to prevent this issue without compromising the network visibility?
A network engineer is installing new switches in the data center to replace existing infrastructure. The previous network hardware had administrative interfaces that were plugged into the existing network along with all other server hardware on the same subnet. Which of the following should the engineer do to better secure these administrative interfaces?
A network architect needs to design a new network to connect multiple private data centers. The network must:
Provide privacy for all traffic between locations
Use preexisting internet connections
Use intelligent steering of application traffic over the best path
Which of the following best meets these requirements?
A network architect is working on a new network design to better support remote and on-campus workers. Traffic needs to be decrypted for inspection in the cloud but is not required to go through the company's data center. Which of the following technologies best meets these requirements?
A network administrator is troubleshooting a user's workstation that is unable to connect to the company network. The results of ipconfig and arp -a are shown. The user’s workstation:

A router on the same network shows the following output:

Has an IP address of 10.21.12.8
Has subnet mask 255.255.255.0
Default gateway is 10.21.12.254
ARP table shows 10.21.12.8 mapped to 1A-21-11-31-74-4C (a different MAC address than the local adapter)
An outage occurred after a software upgrade on core switching. A network administrator thinks that the firmware installed had a bug. Which of the following should the network administrator do next?
A company's IT department is expected to grow from 100 to 200 employees, and the sales department is expected to grow from 1,000 to a maximum of 2,000 employees. Each employee owns a single laptop with a single IP allocated. The network architect wants to deploy network segmentation using the IP range 10.0.0.0/8. Which of the following is the best solution?
A developer reports errors when trying to access a web application. The developer uses Postman to troubleshoot and receives the following error:
HTTP Status: 403 Forbidden
Headers include authentication-related variables such as access_key, signature, salt, and timestamp
The request is a GET request to a payment methods API

Which of the following is the cause of the issue?
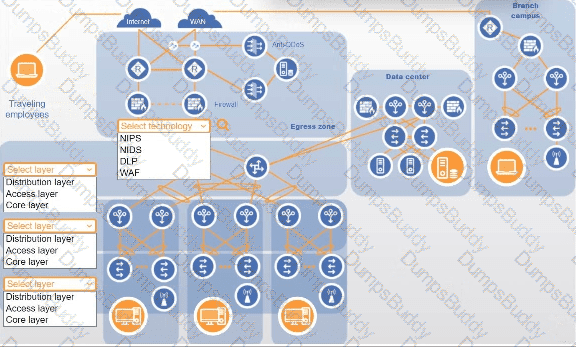
You are designing a campus network with a three-tier hierarchy and need to ensure secure connectivity between locations and traveling employees.
INSTRUCTIONS
Review the command output by clicking on the server, laptops, and workstations on the network.
Use the drop-down menus to determine the appropriate technology and label for each layer on the diagram. Options may only be used once.
Click on the magnifying glass to make additional configuration changes.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Security policy states that all inbound traffic to the environment needs to be restricted, but all external outbound traffic is allowed within the hybrid cloud environment. A new application server was recently set up in the cloud. Which of the following would most likely need to be configured so that the server has the appropriate access set up? (Choose two.)
A network security administrator needs to set up a solution to:
Gather all data from log files in a single location.
Correlate the data to generate alerts.
Which of the following should the administrator implement?
An architecture team needs to unify all logging and performance monitoring used by global applications across the enterprise to perform decision-making analytics. Which of the following technologies is the best way to fulfill this purpose?
An administrator must ensure that credit card numbers are not contained in any outside messaging or file transfers from the organization. Which of the following controls meets this requirement?
A network architect is designing a solution to place network core equipment in a rack inside a data center. This equipment is crucial to the enterprise and must be as secure as possible to minimize the chance that anyone could connect directly to the network core. The current security setup is:
In a locked building that requires sign in with a guard and identification check.
In a locked data center accessible by a proximity badge and fingerprint scanner.
In a locked cabinet that requires the security guard to call the Chief Information Security Officer (CISO) to get permission to provide the key.
Which of the following additional measures should the architect recommend to make this equipment more secure?
An organization has centralized logging capability at the on-premises data center and wants a solution that can consolidate logging from deployed cloud workloads. The organization would like to automate the detection and alerting mechanism. Which of the following best meets the requirements?
A network administrator is configuring firewall rules to lock down the network from outside attacks. Which of the following should the administrator configure to create the most strict set of rules?
A network architect is designing an expansion solution for the branch office network and requires the following business outcomes:
Maximize cost savings with reduced administration overhead
Easily expand connectivity to the cloud
Use cloud-based services to the branch offices
Which of the following should the architect do to best meet the requirements?
A company hosts its applications on the cloud and is expanding its business to Europe. Thecompany must comply with General Data Protection Regulation (GDPR) to limit European customers' access to data. The network team configures the firewall rules but finds that some customers in the United States can access data hosted in Europe. Which of the following is the best option for the network team to configure?