100-160 Cisco Certified Support Technician (CCST) Cybersecurity Questions and Answers
Which wireless security protocol provides the strongest protection for a home or small business network?
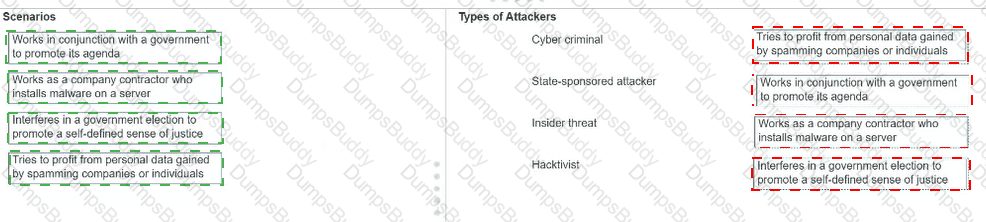
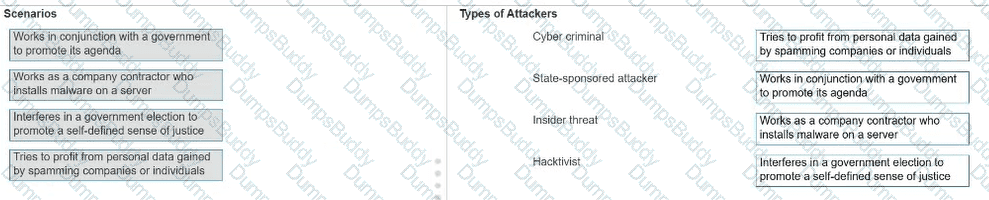
Move each scenario from the list on the left to the correct type of attacker on the right.
Note: You will receive partial credit for each correct answer.
During an incident response, the security team needs to isolate a compromised server from the rest of the network but still allow forensic analysis. Which action should they take?
Move each NIST Incident Response Lifecycle phase from the list on the left to the correct description on the right.
Note: You will receive partial credit for each correct answer.

You are collecting data after a suspected intrusion on the local LAN.
You need to capture incoming IP packets to a file for an investigator to analyze.
Which two tools should you use?(Choose 2.)
What is the main purpose of a disaster recovery plan as compared to a business continuity plan?
You need to design your company’s password policy to adhere to the National Institute of Standards and Technology (NIST) guidelines for user password security.
What is the minimum password length that you should require to be consistent with the NIST guidelines?
Your manager asks you to review the output of some vulnerability scans and report anything that may require escalation.
Which two findings should you report for further investigation as potential security vulnerabilities?(Choose 2.)
Which security measure can prevent unauthorized devices from automatically connecting to a corporate network through unused switch ports?
Your supervisor suspects that someone is attempting to gain access to a Windows computer by guessing user account IDs and passwords. The supervisor asks you to use the Windows Event Viewer security logs to verify the attempts.
Which two audit policy events provide information to determine whether someone is using invalid credentials to attempt to log in to the computer?(Choose 2.)
Note: You will receive partial credit for each correct selection.
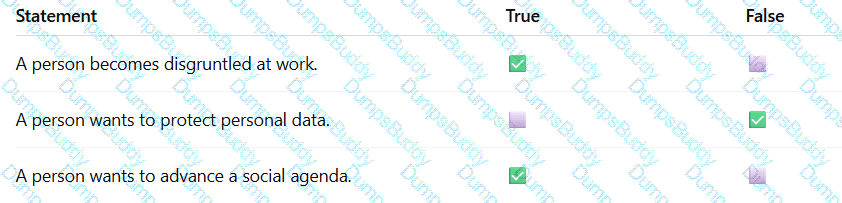
For each statement, selectTrueif it is a common motivation to commit cyber attacks orFalseif it is not.
Note: You will receive partial credit for each correct selection.