CPIM-8.0 Certified in Planning and Inventory Management (CPIM 8.0) Questions and Answers
A healthcare organization is preparing an exercise test plan of its Disaster Recovery Plan (DRP) for the Electronic Medical Record (EMR) application. The Business Continuity (BC) analyst is reviewing the requirements of the DRP. The EMR must provide basic charting services within 4 hours, must not lose more than 15 minutes of data, and must be fully functional within 12 hours. At the completion of the exercise, the analyst is preparing a lessons learned report and notes that the EMR was available after 3 hours and 25 minutes of data was lost. Which PRIMARY requirement needs to be addressed because of the exercise?
Corporate fraud has historically been difficult to detect. Which of the following methods has been the MOST helpful in unmasking embezzlement?
Which of the following is the MOST effective approach to reduce the threat of rogue devices being introduced to the internal network?
When implementing a data classification program, Which is MOST important for measuring businesss impact?
An organization wants to control access at a high-traffic entrance using magnetic-stripe cards for identification. Which of the following is the BEST for the organization to utilize?
Company A has acquired Company B. Company A has decided to start a project to convert Company B's enterprise resource planning (ERP) software to the same ERP software that Company A uses. What is a likely reason for this decision?
Which role is MOST accountable for allocating security function resources in order to initiate the information security governance and risk management policy?
Which of the following techniques is BEST suited to preserve the confidentiality of a system’s data?
How would a master production schedule (MPS) be used In an assemble-to-order (ATO) manufacturing environment?
Which of the following does a federated Identity Provider (IDP) need in order to grant access to identity information?
What can help a security professional assess and mitigate vulnerabilities of an embedded device?
A cybersecurity analyst is reviewing a recent incident in which the adversaries were able to move vertically within the network. Which attack phase MOST clearly represents this scenario?
Up-to-date Information about production order status is required to do which of the following tasks?
If all other factors remain the same, when finished goods inventory investment is increased, service levels typically will:
A traffic analysis on an organization's network identifies a significant degree of inefficient resource use as a result of broadcast traffic. The organization wants to reduce the scope of the broadcasts without impeding the flow of traffic. Which of the following devices is the BEST choice to implement to achieve this goal?
An organization is looking to integrate security concepts into the code development process early in development to detect issues before the software is launched. Which advantage does the organization gain from using Static Application Security Testing (SAST) techniques versus dynamic application security testing techniques?
An organization has determined that it needs to retain customer records for at least thirty years to discover generational trends in customer behavior. However, relevant local regulation requires that all Personally Identifiable Information (PII) is deleted after expiration of the customer's engagement with the organization, which is usually no longer than one year. How should the data be handled at the expiration of customer engagement at one year?
A company selling seasonal products is preparing their sales and operations plan for the coming year. Their current labor staffing is at the maximum for their production facility and cannot meet the forecasted demand. The business plan shows they do not have the financial capability to add to the production facility. Which of the following actions would be most appropriate?
What priority control technique is most appropriate for a firm using a cellular production system?
A multinational organization acquires a subsidiary. The acquisition results in the need to integrate a large population of new users into the organization's corporate cloud. What is the MAIN benefit of the organization's Federated Identity Management (FIM) system to address the need?
An organization has decided to advance from qualitative risk assessment to quantitative risk analysis. The information security risk analyst has been tasked with replacing the organization’s qualitative likelihood scale of low, medium, and high with a quantitative approach. Which is the BEST approach for replacing the qualitative input values?
Which of the following is the MOST effective practice for tracking organizational assets when removed from the premises?
Which of the following states of data becomes MOST important to protect as organizations continue to transition toward Application Programming Interface (API)-based solutions?
Which of the following BEST describes the responsibility of an information System Security Officer?
Which of the following statements is true about total productive maintenance (TPM)?
Which of the following mechanisms are PRIMARILY designed to thwart side channel attacks?
A logistics manager Is faced with delivering an order via rail or truck. Shipping via rail costs S300 and takes 14 days. Shipping via truck costs $600 and takes 3 days. If the holding cost is $40 per day, what is the cost to deliver the order?
Which of the following is the BEST option for a security director to use in order to mitigate the risk of inappropriate use of credentials by individuals with administrative rights?
Following the go-live of a new financial software, an organization allowed the Information Technology (IT) officer to maintain all rights and access permissions to help the organization staff should they have challenges in their day-to-day work. What is the BEST way to categorize the situation?
A security engineer is responsible for verifying software reliability prior to commercial deployment. Which of the following factor would BEST be verified to ensure that the software stays reliable?
Which of the following is typically used to control physical access to highly secure facilities?
Access Control Lists (ACL), protection bits, and file passwords are typical examples of which of the following access control methods?
Which of the following benefits typically will be realized when switching from a functional to a cellular layout?
As the organization requires user friendly access to a new web-based application, a software developer decides to implement Single Sign-On (SSO). The developer uses the de-facto standard for web-based applications and the implementation includes the use of a JavaScript Object Notation (JSON) web token. With this information, which is the BEST way for the software developer to establish SSO capability?
In a hospital, during a routine inspection performed by the computerized tomography device technical service, it is discovered that the values of radiation used in scans are one order of magnitude higher than the default setting. If the system has had an unauthorized access, which one of the following concepts BEST describes which core principle has been compromised?
Following the setting of an organization’s risk appetite by senior management, a risk manager needs to prioritize all identified risks for treatment. Each risk has been scored based on its Annualized Loss Expectancy (ALE). Management has asked for an immediate risk mitigation plan focusing on top risks. Which is the MOST effective approach for the risk manager to quickly present a proposal to management?
A security team leader needs to communicate the value of the security program. As the security team leader determines the return on security investments, what is the MOST important aspect to incorporate?
When a third-party needs to receive privileged information, which of the following would be the BEST to
transport the data?
A hot Disaster Recovery (DR) data center is the victim of a data breach. The hackers are able to access and copy 10GB of clear text confidential information. Which of the following could have decreased the amount of exposure from this data breach?
Which of the following is the benefit of using Security Content Automation Protocol (SCAP) version 2 on endpoint devices?
An organization is running a cloud-based application to process the information obtained at point-of-sale devices. Which guideline should be applied to the application?
A company has the following production conditions:
Batch size: 1,000 items
Processing time: 4 minutes per item
Setup time: 2 hours
Utilization: 80%
Efficiency: 80%
Which of the following actions would result in the work being done in the least amount of time?
An attacker wants to decrypt a message and has no knowledge of what may have been in the original message. The attacker chooses to use an attack that will exhaust the keyspace in order to decrypt the message. What type of cryptanalytic attack is the attacker using?
An organization has recently been hacked. To prevent future breaches, the Chief Information Security Officer (CISO) hires a third-party vendor to perform penetration testing on the network. Once complete, the vendor provides to the CISO a final report generated by a high-quality vulnerability scanner. The CISO rejects the report as incomplete.
Why is the vendor's penetration test considered incomplete?
Long lead-time items with stable demand would best be supported by a supply chain:
A company decided not to pursue a business opportunity In a foreign market due to political Instability and currency fluctuations. Which risk control strategy did this business utilize?
Which of the following is the MOST important consideration in a full-scale disaster recovery test?
An organization has identified that an individual has failed to adhere to a given standard set by the organization. Based on the needs of the organization, it was decided that an exception process will be created. What is the PRIMARY benefit of establishing an exception process?
The question below is based on the following alternative schedules for a lot of 1,200.
A company works 8-hour, single-shift days. Setups are 4 hours for Operation 20 and 4 hours for Operation 40. Each operation has multiple machines available.
Which of the following statements is correct?
Which of the following is the MOST significant flaw when using Federated Identity Management (FIM)?
What order BEST reflects the steps when adding threat modeling practices to a Software Development Life Cycle (SDLC)?
According to quality function deployment (QFD), customer needs are gathered through:
The costs provided in the table below are associated with buying a quantity larger than immediately needed. What Is the total landed cost based on this table?
Cost CategoryCost
Custom fees$125
Freight$700
Warehouse rent$200
Matenal cost$500
An organization decides to conduct penetration testing. Senior management is concerned about the potential loss of information through data exfiltration. The organization is currently preparing a major product launch that is time-sensitive. Which of the following methods of testing is MOST appropriate?
An organizational policy requires that any data from organization-issued devices be securely destroyed before disposal. Which method provides the BEST assurance of data destruction?
Which of the following should be done FIRST when implementing an Identity And Management (IAM) solution?
An organization provides customer call center operations for major financial services organizations around the world. As part of a long-term strategy, the organization plans to add healthcare clients to the portfolio. In preparation for contract negotiations with new clients, to which cybersecurity framework(s) should the security team ensure the organization adhere?
An organization donates used computer equipment to a non-profit group. A system administrator used a degausser on both the magnetic and Solid State Drives (SSD) before delivery. A volunteer at the non-profit group discovered some of the drives still contained readable data and alerted the system administrator. What is the BEST solution to ensure that computer equipment does not contain data before release?
Which of the following should Business Impact Analysis (BIA) reports always include?
An organization is implementing an enterprise resource planning system using the traditional waterfall Software development Life Cycle (SDLC) model. When is the BEST time to perform a code review to identity security gaps?
An organization is planning to streamline its Identity and Access Management (IAM) processes and platform. The executive team mandated a compact platform to efficiently manage identities for internal and third-party services access. What is the BEST platform choice?
Which of the following roles is the BEST choice for classifying sensitive data?
During an investigation, a forensic analyst executed a task to allow for the authentication of all documents, data, and objects collected, if required. Which of the options below BEST describes this task?
A manufacturer begins production of an item when a customer order is placed. This is an example of a(n):
Cloud computing introduces the concept of the shared responsibility model. This model can MOST accurately be described as defining shared responsibility between which of the following?
Marketing has requested a significant change in the mix for a product family. The requested change falls between the demand and the planning time fences. The most appropriate action by the master scheduler is to:
In an organization that develops aircrafts for military usage, where will the security team focus its efforts to ensure the organization’s data remains confidential?
Why would a network administrator monitor Internet of Things (IoT) security differently than the security of standards network devices?
Which of the following systems would be the most cost-efficient for inventory management of a low value item?
Which of the following factors is the MOST important consideration for a security team when determining whether cryptographic erasure can be used for disposal of a device?
Which of the following criteria is used to determine safety stock in a distribution center (DC)?
A health care organization's new cloud-based customer-facing application is constantly receiving security events from dubious sources. What BEST describes a security event that compromises the confidentiality, integrity or availability of the application and data?
Which of the following is a PRIMARY benefit of sharing assessment results among key organizational officials across information boundaries?
Which of the following BEST describes an individual modifying something the individual is not supposed to?
An organization is considering options to outsource their Information Technology (IT) operations. Although they do not sell anything on the Internet, they have a strong requirement in uptime of their application. After the offerings received by the Cloud Service Provider (CSP), the IT manager decided it was mandatory to develop processes to continue operations without access to community or public cloud-based applications. Which of the following arguments MOST likely led the IT manager to make this decision?
An organization experienced multiple compromises of endpoints, leading to breaches of systems and data. In updating its strategy to defend against these threats, which of the following BEST considers the organization’s needs?
A web application is found to have SQL injection (SQLI) vulnerabilities. What is the BEST option to remediate?
The question below is based on the following standard and actual data of a production order
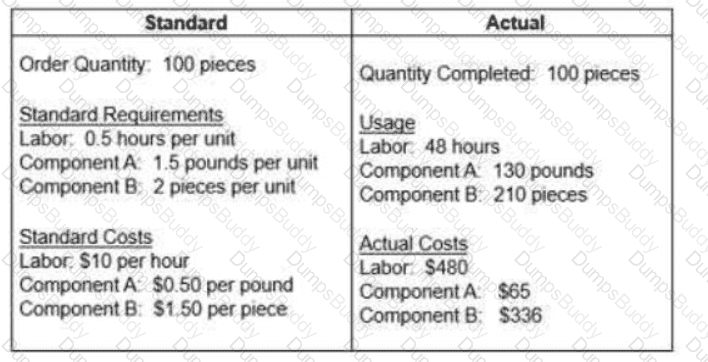
Which of the following statements about variances is true?
Which of the following methods places a replenishment order when the quantity on hand falls below a predetermined level?
Before securing a email system using OpenPGP in an organization, Which of the following actions MUST be performed?
An organization has to conduct quarterly reviews of user authorization access to its primary financial application. Which position is responsible for performing these reviews?
Disaster Recovery Plan (DRP) training can be considered complete when the participants
Which of the following statements is true about the meantime between failures (MTBF) measure?
A manufacturing facility uses common wireless technologies to communicate. The head of security is concerned about eavesdropping by attackers outside the perimeter fence. The distance between the facility and fence is at least 300 feet (100 m). Which of the following wireless technologies is MOST likely to be available to an attacker outside the fence?
An executive wants to ensure that risk related to information operations is managed in accordance with the enterprise's risk management thresholds. What is the BEST way to ensure this consistently occurs?
Which of the following items does the master scheduler have the authority to change in the master scheduling process?
During a manual source code review, an organization discovered a dependency with an open-source library that has a history of being exploited. Which action should the organization take FIRST to assess the risk of depending on the open-source library?
A web developer was recently asked to create an organization portal that allows users to retrieve contacts from a popular social media platform using Hypertext Transfer Protocol Secure (HTTPS). Which of the following is BEST suited for authorizing the resource owner to the social media platform?
Which of the following product design approaches are likely to reduce time to market for a global supply chain?
A security team is analyzing the management of data within the human resources systems, as well as, the intended use of the data, and with whom and how the data will be shared. Which type of assessment is the team MOST likely performing?
A plant uses a level production strategy due to the high costs of hiring and letting go of skilled employees. The constrained resource is due to be upgraded in the fourth month of the planning horizon, and that will reduce capacity for that month by 17%.
Which of the following actions would be appropriate in this situation to maintain current levels of customer service and gross margin?
A large retail organization will be creating new Application Programming Interfaces (API) as part of a customer-facing shopping solution. The solution will accept information from users both inside and outside of the organization. What is the safest software development practice the team can follow to protect the APIs against Structured Query Language Injection (SQLi) attacks?
An Information Technology (IT) professional is seeking a control objective framework that is widely accepted around the world and focuses specifically on information security controls. Which of the following frameworks BEST meets this need?
While doing a penetration test, auditors found an old credential hash for a privileged user. To prevent a privileged user's hash from being cached, what is the MOST appropriate policy to mandate?
Which of the below represents the GREATEST cloud-specific policy and organizational risk?
Which of the following is PRIMARILY responsible for deciding the classification of data in an organization?
What FIRST step should a newly appointed Data Protection Officer (DPO) take to develop an organization's regulatory compliance policy?
Which of the following activities is an example of collaboration between suppliers and operations which would give more lead time visibility?
The Data Loss Prevention (DLP) team in a major financial institution discovered network traffic that involved movement of sensitive material to a Cloud Service Provider (CSP). What action should be taken FIRST in this situation?
An organization is designing a new Disaster Recovery (DR) site. What is the BEST option to harden security of the site?
An organization has been the subject of increasingly sophisticated phishing campaigns in recent months and has detected unauthorized access attempts against its Virtual Private Network (VPN) concentrators. Which of the following implementations would have the GREATEST impact on reducing the risk of credential compromise?
What is the BEST way to plan for power disruptions when implementing a Disaster Recovery Plan (DRP)?
An audit report of security operations has listed some anomalies with third parties being granted access to the internal systems and data without any restrictions.
Which of the following will BEST help remediate this issue?
Which of the following is a core subset of The Open Group Architecture Framework (TOGAF) enterprise architecture model?
The Chief Security Officer (CSO) of an organization would like to have a network security assessment done by the security team. Which of the following is the FIRST step in the security testing methodology?
A security engineer developing software for a professional services organization has a requirement that users cannot have concurrent access to data of clients that are competitors. Which security model should the security engineer implement to meet this requirement?
An organization wants to implement Zero Trust (ZT). The Information Technology (IT) department is already using Multi-Factor Authentication (MFA) and Identity and Access Management (IAM). Which of the following would be the BEST solution for the organization to implement in order to have a ZT network?
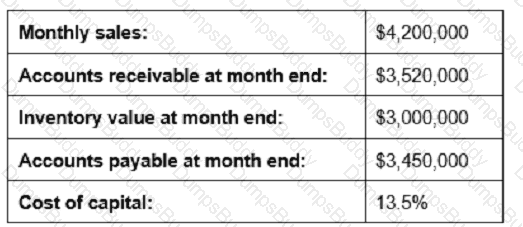
Given the information below, reducing which measure by 10% would contribute most to shortening the cash-to-cash cycle time?
Which of the following is a threat modeling methodology used for accessing threats against applications and Operating Systems (OS)?
Which security audit phase is MOST important to ensure correct controls are applied to classified data in a production environment?
The Chief Information Security Officer (CISO) defined a requirement to install a network security solution that will have the ability to inspect and block data flowing over network in real time. What network deployment scenario will be MOST suitable?
Which of the following statements characterizes a pull system In distribution management?
What is the MAIN reason security is considered as part of the system design phase instead of deferring to later phases?
Which of the following is the workflow of the identity and access provisioning lifecycle?
During a security incident investigation, a security analyst discovered an unauthorized module was compiled into an application package as part of the application assembly phase. This incident occurred immediately prior to being digitally signed and deployed using a deployment pipeline.
Which of the following security controls would BEST prevent this type of incident in the future?
An organization starts to develop a drone inspection and defect detection system includes different subsystems running at different clouds from different service providers. During the architectural design phase, which security architecture principle should be the MOST important for the security engineer to apply?
Which of the following actions provides the BEST evidence for forensic analysis of powered-off device?
In a make-to-order (MTO) production environment, fluctuations in sales volumes are managed by adjustments to the:
One of the findings in the recent security assessment of a web application reads: "It appears that security is an afterthought in the web application development process. It is recommended that security be addressed earlier in the development process." Which of these choices would BEST remediate this security finding?
Which burden of proof has been applied when a workplace investigation has a 51 percent or greater certainty that allegations are true?
An organization is implementing improvements to secure the Software Development Life Cycle (SDLC). When should defensive three modeling occur?
An organization wishes to utilize a managed Domain Name System (DNS) provider to reduce the risk of users accessing known malicious sites when web browsing. The organization operates DNS forwarders that forward queries for all external domains to the DNS provider. Which of the following techniques could enable the organization to identify client systems that have attempted to access known malicious domains?
What is the MOST appropriate action to take when media classification needs to be downgraded to a less sensitive classification?
A security engineer is reviewing Incident Response (IR) roles and responsibilities. Several roles have static elevated privileges in case an incident occurs. Instead of static access, what is the BEST access method to manage elevated privileges?
If the total part failure rate of a machine is 0.00055 failures per hour, what would be the mean time between failures (MTBF) in hours?
Which of the following planning modules considers the shortest-range planning goals?
An organization has hired a new auditor to review its critical systems infrastructure for vulnerabilities. Which of the following BEST describes the methodology the auditor will use to test whether servers are set up according to the organization's documented policies and standards?
An organization routes traffic between two of its sites using non-revenue network paths provided by peers on an Internet exchange point. What is the MOST appropriate recommendation the organization's security staff can make to prevent a compromise?
As a result of a fault at a cloud service provider’s data center, the customer accounts of a utility organization were corrupted. Under the European Union’s (EU) General Data Protection Regulation (GDPR), which entity bears responsibility for resolving this?
Which of the following documents is the BEST reference to describe application functionality?
The primary consideration In maintenance, repair, and operating (MRO) supply systems typically is:
The planned channels of Inventory disbursement from one or more sources to field warehouses are known as:
Reducing distribution network inventory days of supply will have which of the following Impacts?
A security administrator of a large organization is using Mobile Device Management (MDM) technology for protecting mobile devices. Which of the following is the BEST way to ensure that only company-approved mobile software can be deployed?
An organization has a call center that uses a Voice Over Internet Protocol (VoIP) system. The conversations are sensitive, and the organization is concerned about employees other than the call agents accessing these conversations. What is the MOST effective additional security measure to make?
Which of the following capabilities BEST distinguishes a Next-Generation Firewall (NGFW) from a traditional firewall?
A newly hired Chief Information Security Officer (CISO) is now responsible to build a third-party assurance for their organization. When assessing a third-party, which of the following questions needs to be answered?
Which of the following statements is an assumption on which the economic order quantity (EOQ) model is based?
The development team wants new commercial software to integrate into the current system. What steps can the security office take to ensure the software has no vulnerabilities?
After a data loss event, an organization is reviewing its Identity and Access Management (IAM) governance process. The organization determines that the process is not operating effectively. What should be the FIRST step to effectively manage the IAM governance process?
Broadcast traffic is causing network performance degradation of sensitive equipment.
Which of the following methods is used to prevent the broadcast traffic from impacting availability?
A semiconductor manufacturer is writing a physical asset handling policy. Which of the following is MOST likely to be the rationale for the policy?
Which of the following BEST describes how an Application Programming Interface (API) gateway fits into an application architecture?
What are the FIRST two steps an organization should conduct to classify its assets?
Which of the following should be performed FIRST in the course of a digital forensics investigation?
Typically, rough-cut capacity planning (RCCP) in a job shop environment would review which of the following work centers to determine the ability to execute the plan?
In which of the following phases of the product life cycle is product price most effective in influencing demand?
An organization’s security assessment recommended expanding its secure software development framework to include testing Commercial Off-The-Shelf (COTS) products before deploying those products in production. What is the MOST likely reason for this recommendation?
Which of the following actions hinders the transition from a push system to a pull system?
A financial services organization wants to deploy a wireless network. Which of the following is the WEAKEST option for ensuring a secure network?
The primary reason for tracing a component with scheduling problems to Its master production schedule (MPS) item is to:
The development team wants new commercial software to Integrate into the current systems. What steps can the security office take to ensure the software has no vulnerabilities?
A Structured Query Language (SQL) database is hosted on a hardened, secure server. All unused ports are locked down, but external connections from untrusted networks are still required to be allowed through. What is the BEST way to ensure transactions to/from this server remain secure?


