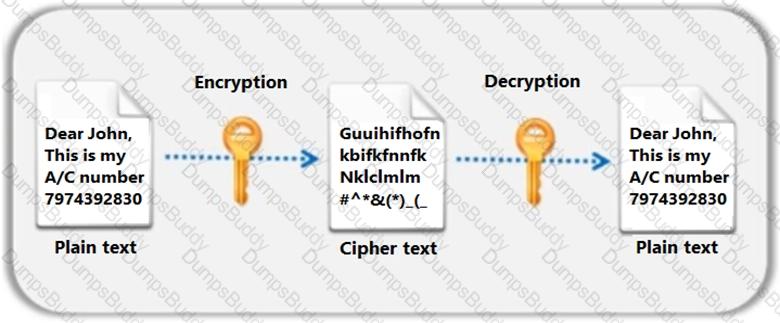
312-96 Certified Application Security Engineer (CASE) JAVA Questions and Answers
According to secure logging practices, programmers should ensure that logging processes are not disrupted by:
To enable the struts validator on an application, which configuration setting should be applied in the struts validator configuration file?
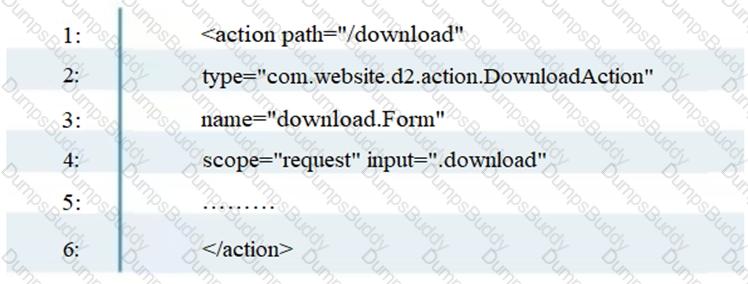
Which of the following Spring Security Framework configuration setting will ensure the protection from session fixation attacks by not allowing authenticated user to login again?
Which of the following elements in web.xml file ensures that cookies will be transmitted over an encrypted channel?
Which of the following configuration settings in server.xml will allow Tomcat server administrator to impose limit on uploading file based on their size?
James is a Java developer working INFR INC. He has written Java code to open a file, read it line by line and display its content in the text editor. He wants to ensure that any unhandled exception raised by the code should automatically close the opened file stream. Which of the following exception handling block should he use for the above purpose?
Which of the following method will you use in place of ex.printStackTrace() method to avoid printing stack trace on error?
The software developer has implemented encryption in the code as shown in the following screenshot.
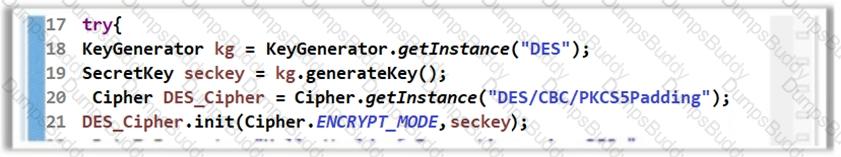
However, using the DES algorithm for encryption is considered to be an insecure coding practice as DES is a weak encryption algorithm. Which of the following symmetric encryption algorithms will you suggest for strong encryption?
Which of the following configurations can help you avoid displaying server names in server response header?