The request in a customer environment is IDP Initiated unsolicited SSO. The initial URL is:
https://POCIDP/FIM/sps/saml2idp/sam120/logininitial? RequestBinding=HTTPPost &Partnerld=https://POCSP/isam/sps/abc/saml20 &NameIdFormat=email
The POCIDP is Point of Contact for Identity Provider and POCSP is Point of Contact for Service Provider. The customer wants to configure TargetURL within the Service Provide' Federation configuration in IBM Security Access Manager V9.0.
What will satisfy this requirement?
A customer has setup IBM Security Access Manager V9.0 hardware appliances (AP. A1, A2) in a cluster. The appliances (A1, A2) that host reverse proxies are labeled as "restricted" in the cluster. AP is the Primary of the cluster.
There is one reverse proxy in appliance A1 and two in appliance A2. These reverse proxies are being tuned for performance. The appliance A1 and A2 max socket range has been set to 64510.
What is true in this situation?
A large bank has multiple applications protected by two identically configured WebSEAL servers. One junction supports a reporting application that frequently experiences performance issues which slows response time. The worst case results in the entire site becoming unresponsive when all WebSEAL worker threads on all WebSEAL instances are consumed on the Junctions to this one reporting application.
Which configuration change will prevent this situation from occurring without impacting the behavior of any other application (junction), and keeping the entire site up?
A customer is deploying an IBM Security Access Manager V9.0 solution to protect back end resources and is planning to use an LDAP Server that is set up to use SSL server authentication.
What is required to enable SSL to secure communications with LDAP?
A customer wants to utilize the front-end load balancer (FELB) to share requests between Reverse Proxies. A junctioned application requires the actual client IP address to be passed as a header.
Which FELB option must be enabled to pass an x-forwarded-for header?
Which two resources should a deployment professional check to ensure an appliance is at the very latest level (Choose two.)
In an IBM Security Access Manager (ISAM) V9.0 Federated SSO flow, the ISAM V9.0 appliance is used as the Service Provider. The SSO is I DP initiated. The I DP initiated unsolicited SSO doesn't have the target URL specified where Service Provider should be sending the user after consuming the SAML2.0 Assertion. The implementer of the SSO provider has been given the task of providing Target URL through a mapping rule in the Service Provider configuration.
How should this requirement be achieved in the mapping URL?
A deployment professional is configuring IBM Security Access Manager V9.0 for Management Authentication using remote LDAP.
Which configuration field value is optional?
A deployment professional has created an Access Control Policy to protect sensitive business information:
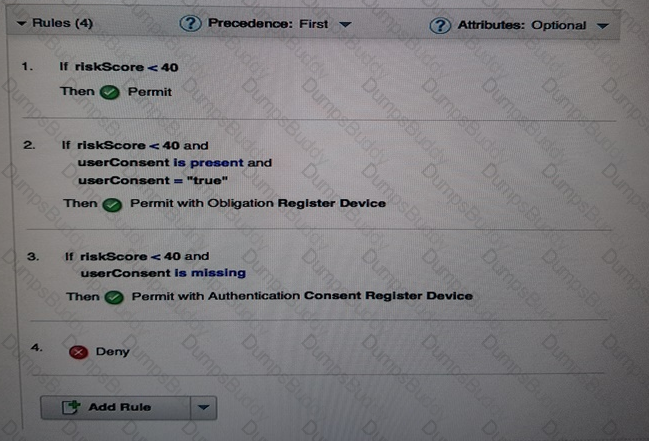
Which Policy decision is returned for a user with a risk score of 35 and has consented to registering a device?
A customer has an IBM Security Access Manager V9.0 appliance cluster spanning two data centers A and B. Data center A has the Primary Master and two Restricted nodes. Data center B has a Secondary Master and two Restricted Nodes. A Load Balancer with redundancy across data centers provides sticky load balancing to reverse proxies in both data centers.
What is true if a disaster recovery testing scenario takes down all appliances in data center A?
An IBM Security Access Manager V9.0 deployment professional responsible for a large cluster notices the clocks among the nodes are not in sync and needs to update settings to ensure the clocks are synchronized.
Which setting should be used to help keep times synchronized?
A customer has just received an IBM Security Access Manager (ISAM) V9.0 hardware appliance and is looking to set it up. The Appliance has been mounted into a rack, attached to a power supply and cabled to the right network switches.
How does the Customer connect directly to an ISAM hardware appliance for initial configuration?
Multiple hostnames are mapped to a single IP address used by a WebSEAL instance, listening on the default HTTPS port. For each host name requested in the browser, WebSEAL needs to present a different certificate.
What can the deployment professional do to meet this requirement?
An IBM Security Access Manager (ISAM) V9.0 environment is configured with Primary and Secondary Master servers. The Primary master node becomes unavailable and ISAM deployment professional promotes the Secondary Master node to a Primary Master.
What happens to the original Primary Master when it becomes available and rejoins the network?
An IBM Security Access Manager (ISAM) V9.0 deployment professional has downloaded a snapshot from an ISAM virtual appliance configured with reverse proxy. This snapshot is being applied to another virtual appliance.
Which condition must be met before applying a snapshot form one virtual appliance to another?
A deployment professional has enabled tracing for the WebSEAL instance to assist developers in troubleshooting the application. A developer requests a trace containing the request message bodies to and from WebSEAL.
Which log file contains this information?
The web security department of an organization has found that their site is vulnerable to Denial of Service, Brute Force, Buffer Overflow and decided to use the Web Application Firewall (WAF) feature available in IBM Security Access Manager V9.0.
Even after enabling WAF, the site is still vulnerable to the above attacks. The deployment professional is pretty sure that the signature for these attacks have been released and has decided to check for X-Force updates.
How should the deployment professional check and update this?