400-007 Cisco Certified Design Expert (CCDE v3.1) Questions and Answers
Which actions are performed at the distribution layer of the three-layer hierarchical network design model? (Choose two)
A customer with two 10 Mbps Internet links (active-active) experiences degraded performance when one fails. Static routing is used, and bandwidth upgrades aren't possible. The design must be failure-resistant without increasing CAPEX.
Which solution should be proposed?
In an OSPF network with routers connected together with Ethernet cabling, which topology typically takes the longest to converge?
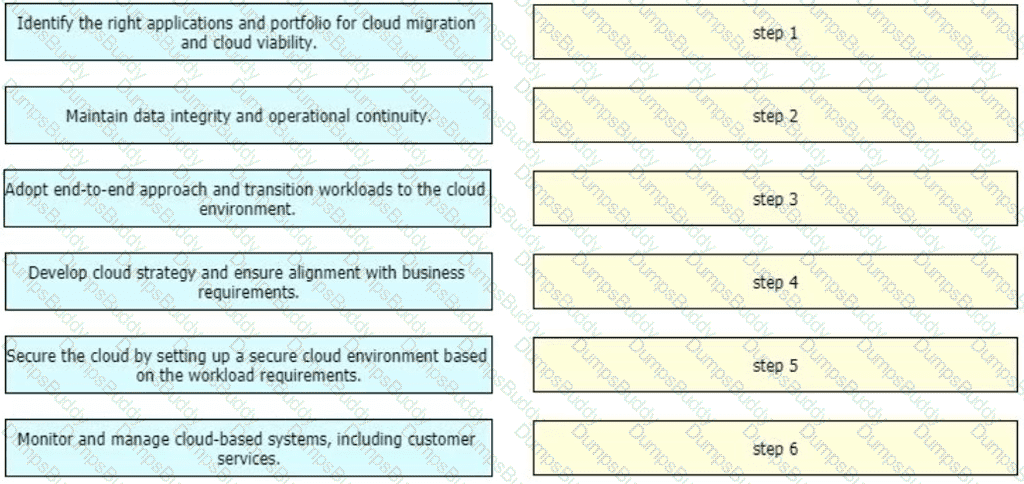
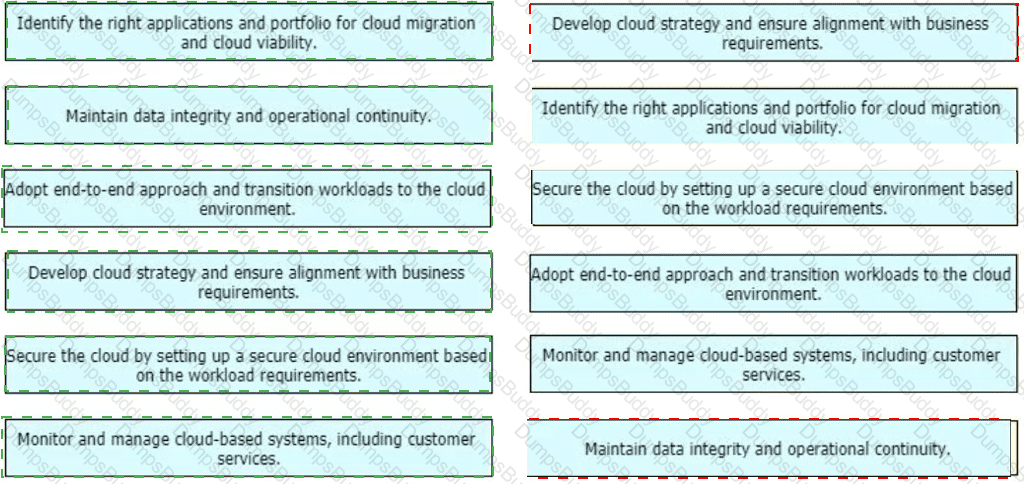
An enterprise wants to migrate an on-premises network to a cloud network, and the design team is finalizing the overall migration process. Drag and drop the options from the left into the correct order on the right.
You are designing a large-scale DMVPN network with more than 500 spokes using EIGRP as the IGP protocol. Which design option eliminates potential tunnel down events on the spoke routers due to the holding time expiration?
A network security team uses a purpose-built tool to actively monitor the campus network, applications, and user activity. The team also analyzes enterprise telemetry data from IPFIX data records that are received from devices in the campus network. Which action can be taken based on the augmented data?
Which solution component helps to achieve comprehensive threat protection and compliance for migration to multicloud SDX architectures?
You are designing a network running both IPv4 and IPv6 to deploy QoS. Which consideration is correct about the QoS for IPv4 and IPv6?
Company XYZ needs advice in redesigning their legacy Layer 2 infrastructure. Which technology should be included in the design to minimize or avoid convergence delays due to STP or FHRP and provide a loop-free topology?
Company XYZ, a global content provider, owns data centers on different continents. Their data center design involves a standard three-layer design with a Layer 3-only core. VRRP is used as the FHRP. They require VLAN extension across access switches in all data centers and plan to purchase a Layer 2 interconnection between two of their data centers in Europe. In the absence of other business or technical constraints, which termination point is optimal for the Layer 2 interconnection?
A customer migrates from a traditional Layer 2 data center network into a new SDN-based spine-and-leaf VXLAN EVPN data center within the same location. The networks are joined to enable host migration at Layer 2. What is the final migration step after hosts have physically migrated to have traffic flowing through the new network without changing any host configuration?
In outsourced IT services, the RTO is defined within the SLA. Which two support terms are often included in the SLA by IT and other service providers? (Choose two.)
Company XYZ wants to redesign the Layer 2 part of their network to use all uplinks for increased performance, support host reachability with conversational learning, and avoid port-channels. Which other technique can be used?
Company XYZ is running OSPF in their network. They have merged with another company that is running EIGRP as the routing protocol. Company XYZ now needs the two domains to talk to each other with redundancy, while maintaining a loop-free environment. The solution must scale when new networks are added into the network in the near future. Which technology can be used to meet these requirements?
The Company XYZ network is experiencing attacks against their router. Which type of Control Plane Protection must be used on the router to protect all control plane IP traffic that is destined directly for one of the router interfaces?
Company XYZ is designing the network for IPv6 security and they have these design requirements:
A switch or router must deny access to traffic from sources with addresses that are correct but topologically incorrect.
Devices must block Neighbor Discovery Protocol resolution for destination addresses not found in the binding table.
Which two IPv4 security features are recommended for this company? (Choose two)
You are tasked to design a QoS policy for a service provider so they can include it in the design of their MPLS core network. If the design must support an MPLS network with six classes, and CEs will be managed by the service provider, which QoS policy should be recommended?
Drag and drop the QoS technologies from the left onto the correct capabilities on the right

Company XYZ runs OSPF in their network. A design engineer decides to implement hot-potato routing architecture. How can this implementation be achieved?
You were tasked to enhance the security of a network with these characteristics:
A pool of servers is accessed by numerous data centers and remote sites
The servers are accessed via a cluster of firewalls
The firewalls are configured properly and are not dropping traffic
The firewalls occasionally cause asymmetric routing of traffic within the server data center.
Which technology should you recommend to enhance security by limiting traffic that could originate from a hacker compromising a workstation and redirecting flows at the servers?
An IT service provider is upgrading network infrastructure to comply with PCI security standards. The network team finds that 802.1X and VPN authentication based on locally-significant certificates are not available on some legacy phones. Which workaround solution meets the requirement?
As part of workspace digitization, a large enterprise has migrated all their users to Desktop as a Service (DaaS), by hosting the backend system in their on-premises data center. Some of the branches have started to experience disconnections to the DaaS at periodic intervals, however, local users in the data center and head office do not experience this behavior. Which technology can be used to mitigate this issue?
A banking customer determines that it is operating POS and POI terminals that are noncompliant with PCI DSS requirements, as it is running TLSv1.0. The customer plans to migrate the terminals to TLSv1.2. What are two requirements to complete the migration? (Choose two.)
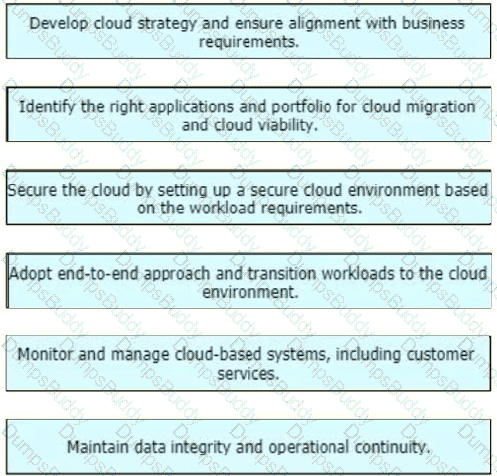
When planning their cloud migration journey, what is crucial for virtually all organizations to perform?
Which solution component helps to achieve rapid migration to the cloud for SaaS and public cloud leveraging SD-WAN capabilities?
Customer XYZ network consists of an MPLS core, IS-IS running as IGP, a pair of BGP route reflectors for route propagation, and a few dozen MPLS-TE tunnels for specific tactical traffic engineering requirements. The customer's engineering department has some questions about the use of the Overload Bit in the IS-IS networks and how it could be used to improve their current network design. Which two concepts about the Overload Bit are true? (Choose two.)
Which two design solutions ensure sub-50 msec of the convergence time after a link failure in the network? (Choose two)
Which two factors must be considered for high availability in campus LAN designs to mitigate concerns about unavailability of network resources? (Choose two.)
A business customer deploys workloads in the public cloud but now faces governance issues related to IT traffic flow and data security. Which action helps identify the issue for further resolution?
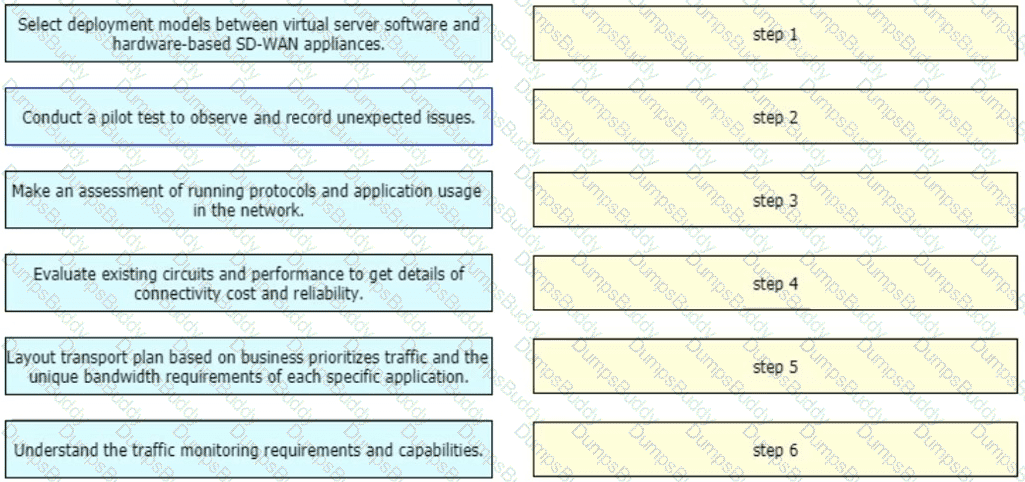
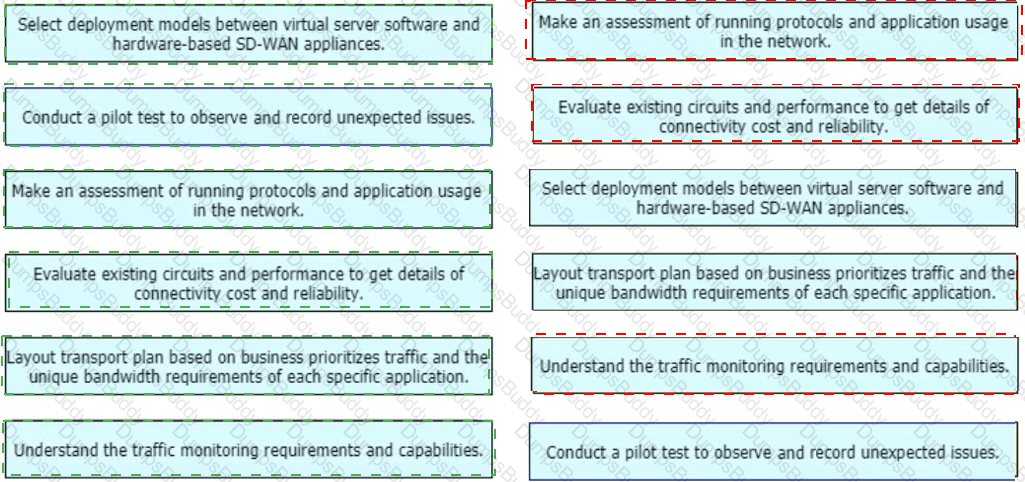
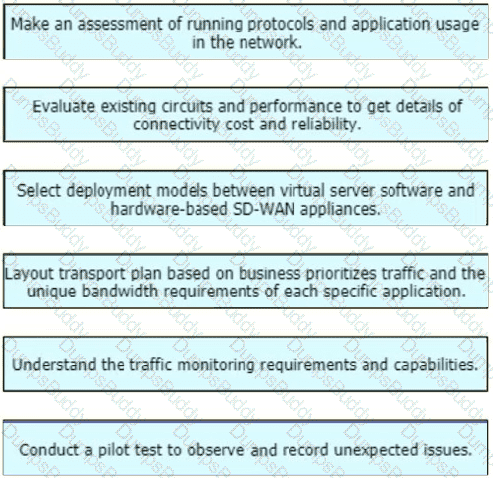
An enterprise organization currently provides WAN connectivity to their branch sites using MPLS technology, and the enterprise network team is considering rolling out SD-WAN services for all sites.
With regards to the deployment planning, drag and drop the actions from the left onto the corresponding steps on the right.
A company requires an RPO of less than 10 seconds to ensure business continuity. Which technology should be deployed?
Company XYZ branch offices connect to headquarters using two links, MPLS and Internet. The company wants to design traffic flow so voice traffic uses MPLS and all other traffic uses either link, avoiding process switching. Which technique can be used?
An external edge router provides connectivity from a service provider to an enterprise. Which two Internet edge best practices meet compliance regulations? (Choose two)
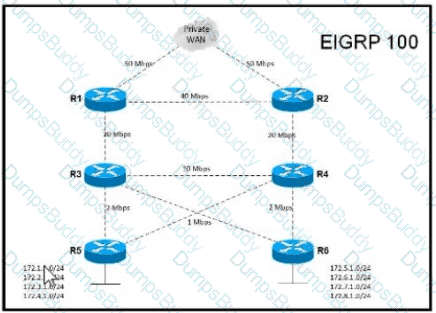
Refer to the exhibit.
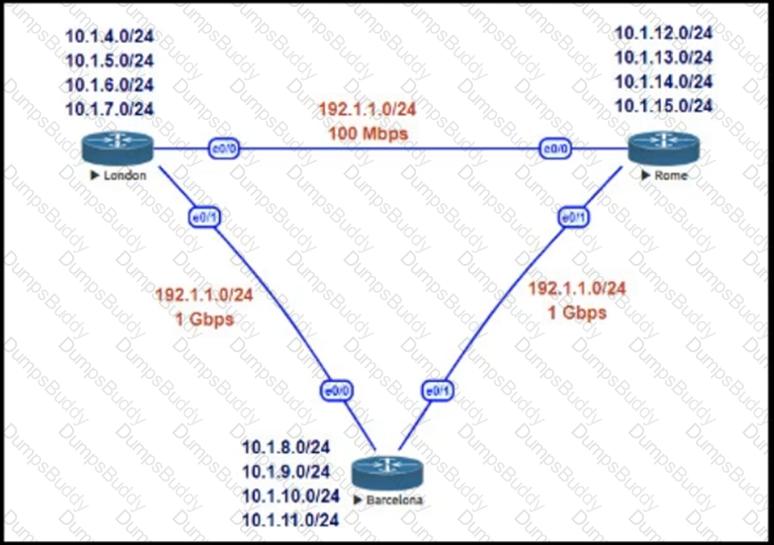
This network is running EIGRP as the routing protocol and the internal networks are being advertised in EIGRP. Based on the link speeds, all traffic between London and Rome is getting propagated via Barcelona and the direct link between London and Rome is not being utilized under normal working circumstances. The EIGRP design should allow for efficiency in the routing table by minimizing the routes being exchanged. The link between London and Rome should be utilized for specific routes. Which two steps accomplish this task? (Choose two.)
A financial company requires that a custom TCP-based stock-trading application be prioritized over all other traffic for the business due to the associated revenue. The company also requires that VoIP be prioritized for manual trades. Which directive should be followed when a QoS strategy is developed for the business?
A business requirement stating that failure of WAN access for dual circuits into an MPLS provider for a Data Centre cannot happen due to related service credits that would need to be paid has led to diversely routed circuits to different points of presence on the provider’s network. What should a network designer also consider as part of the requirement?
In a redundant hub-and-spoke design with inter-spoke links, load oscillation and routing instability occur due to overload conditions. Which two design changes improve resiliency? (Choose two)
An engineer is designing a DMVPN network where OSPF has been chosen as the routing protocol. A spoke-to-spoke data propagation model must be set up. Which two design considerations must be taken into account? (Choose two)
A Tier-3 Service Provider is evolving into a Tier-2 Service Provider due to the amount of Enterprise business it is receiving. The network engineers are re-evaluating their IP/MPLS design considerations in order to support duplicate/overlapping IP addressing from their Enterprise customers within each Layer3 VPN. Which concept would need to be reviewed to ensure stability in their network?
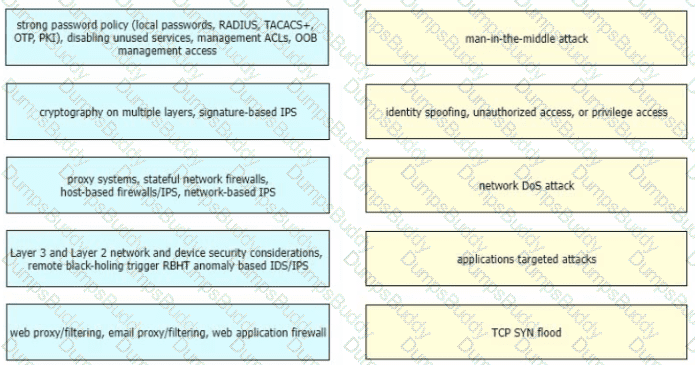
Drag and drop the correct mitigation methods from the left onto the corresponding types of attack on the right
Backups and mirror copies of data are part of RPO (Recovery Point Objective) strategies. If a business wants to reduce their CAPEX for disaster recovery, which solution is most applicable?
An enterprise that runs numerous proprietary applications has major issues with its on-premises server estate hardware, to the point where business-critical functions are compromised. The enterprise accelerates plans to migrate services to the cloud. Which cloud service should be used if the enterprise wants to avoid hardware issues yet have control of its applications and operating system?
Which technology is an open-source infrastructure automation tool that automates repetitive tasks for users who work in networks such as cloud provisioning and intraservice orchestration?
A healthcare provider discovers that protected health information of patients was altered without patient consent. The healthcare provider is subject to HIPAA compliance and is required to protect PHI data. Which type of security safeguard should be implemented to resolve this issue?
You are using iSCSI to transfer files between a 10 Gigabit Ethernet storage system and a 1 Gigabit Ethernet server. The performance is only approximately 700 Mbps and output drops are occurring on the server switch port. Which action will improve performance in a cost-effective manner?
Refer to the exhibit.
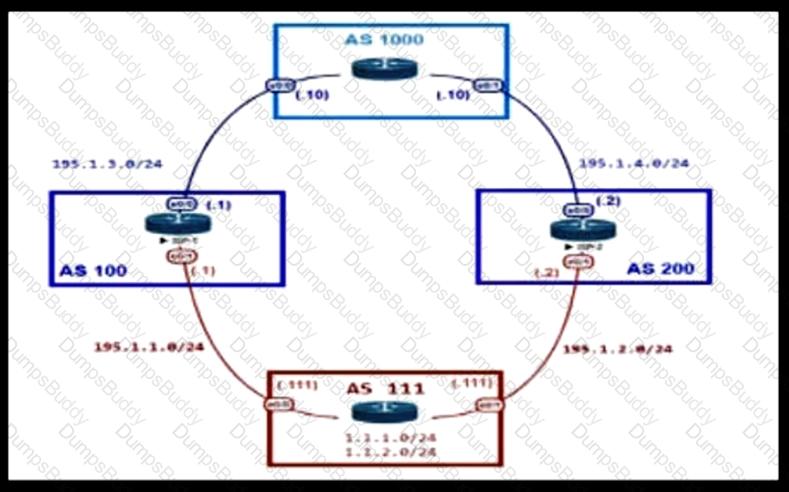
An engineer is designing the network for a multihomed customer running in AS 111. The AS does not have any other ASs connected to it. Which technology is more comprehensive to use in the design to make sure that the AS is not being used as a transit AS?
When an SDN-based model is used to transmit multimedia traffic, which aspect should an architect consider while designing the network?
Company XYZ connects its sites over a private WAN. Their overlay network is running a DMVPN setup where the headquarters site is the hub. The company is planning on implementing multicast routing on the network. What should be used in the multicast routing design?
Refer to the exhibit.
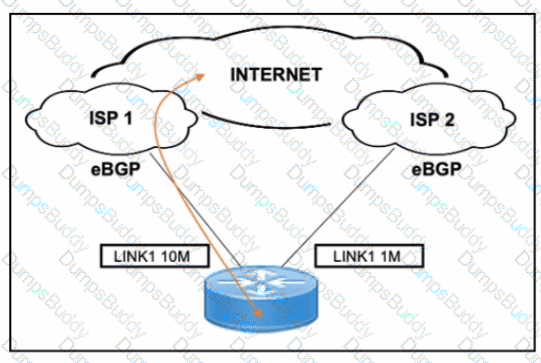
A customer has two eBGP internet links: one primary high-speed (10 Mbps) and one backup low-speed (1 Mbps). The requirement is to use the 10M link (ISP 1) for all inbound/outbound traffic and only use the 1M link (ISP 2) during failure.
What is the correct BGP-based design solution?
Refer to the exhibit.
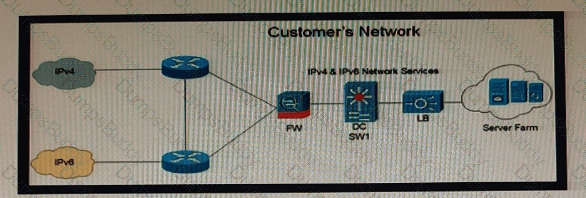
Company XYZ is currently running IPv4 but has decided to start the transition into IPv6. The initial objective is to allow communication based on IPv6 wherever possible, and there should still be support in place for devices that only support IPv4. These devices must be able to communicate to IPv6 devices as well. Which solution must be part of the design?
The SD-WAN architecture is composed of separate orchestration, management, control, and data planes. Which activity happens at the orchestration plane?
You are designing the routing design for two merging companies that have overlapping IP address space. Which of these must you consider when developing the routing and NAT design?
A business requirement is supplied to an architect from a car manufacturer stating their business model is changing to just-in-time manufacturing and a new network is required. The manufacturer does not produce all of the specific components in-house. Which area should the architect focus on initially?
Company XYZ has a hub-and-spoke topology over an SP-managed infrastructure. To measure traffic performance metrics, they implemented IP SLA senders on all spoke CE routers and an IP SLA responder on the hub CE router. What must they monitor to have visibility on the potential performance impact due to the constantly increasing number of spoke sites?
A key to maintaining a highly available network is building in the appropriate redundancy to protect against failure. This redundancy is carefully balanced with the inherent complexity of redundant systems. Which design consideration is relevant for enterprise WAN use cases when it comes to resiliency?
An enterprise plans to evolve from a traditional WAN network to a software-defined WAN network. The existing devices have limited capability when it comes to virtualization. As the migration is carried out, enterprise applications and services must not experience any traffic impact. Which implementation plan can be used to accommodate this during the migration phase?
A customer has a functional requirement that states HR systems within a data center should be segmented from other systems that reside in the same data center and same VLAN. The systems run legacy applications by using hard-coded IP addresses. Which segmentation method is suitable and scalable for the customer?
Which two advantages of using DWDM over traditional optical networks are true? (Choose two.)
Which feature must be part of the network design to wait a predetermined amount of time before notifying the routing protocol of a change in the path in the network?
The Layer 3 control plane steers traffic toward destinations. Which two techniques offer a more dynamic, flexible, controlled, and secure control plane design in service provider networks? (Choose two.)
With virtualization applied throughout the network, every physical link may carry one or more virtual links. What is a key drawback of this?
An architect designs a multi-controller network architecture with these requirements:
Achieve fast failover to control traffic when controllers fail.
Yield a short distance and high resiliency in the connection between the switches and the controller.
Reduce connectivity loss and enable smart recovery to improve the SDN survivability.
Improve connectivity by adding path diversity and capacity awareness for controllers.
Which control plane component of the multi-controller must be built to meet the requirements?
During a pre-sales meeting with a potential customer, the customer CTO asks a question about advantages of controller-based networks versus a traditional network. What are two advantages to mention? (Choose two)
Company XYZ has a multicast domain that spans across multiple autonomous systems. The company wants a simplified and controlled approach to interconnecting multicast domains. Which technology is the best fit?
An enterprise solution team is analyzing multilayer architecture and multicontroller SDN solutions for multisite deployments. The analysis focuses on the ability to run tasks on any controller via a standardized interface. Which requirement addresses this ability on a multicontroller platform?
An engineer is designing the QoS strategy for Company XYZ. A lot of scavenger traffic is traversing the 20Mb Internet link. The new design must limit scavenger traffic to 2 Mbps to avoid oversubscription during congestion. Which QoS technique can be used?
A software-defined networking (SDN) controller learns network topology information by using BGP link-state sessions with the route reflectors of an MPLS-enabled network. The controller then uses the topology information to apply on-demand traffic policies to the network through a protocol that is supported from all Layer 3 routers. Each policy is represented as a RIB entry in the control plane of the router. Which SDN model has been implemented?
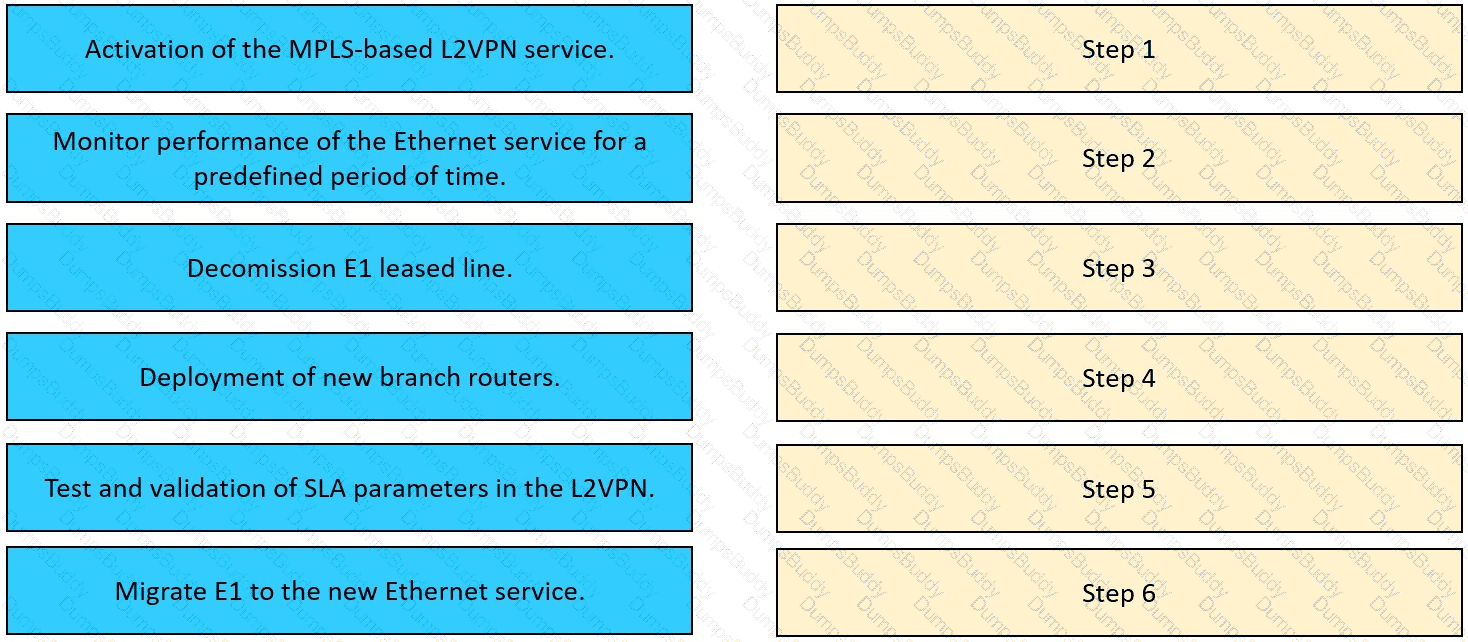
The network team in XYZ Corp wants to modernize their infrastructure and is evaluating an implementation and migration plan to allow integration MPLS-based, Layer 2 Ethernet services managed by a service provider to connect branches and remote offices. To decrease OpEx and improve
response times when network components fail, XYZ Corp decided to acquire and deploy new routers. The network currently is operated over E1 leased lines (2 Mbps) with a managed CE service provided by the telco.
Drag and drop the implementation steps from the left onto the corresponding targets on the right in the correct order.
Which three components are part of the foundational information security principles of the CIA triad? (Choose three.)
An existing wireless network was designed to support data traffic only. You must now install context-aware services for location tracking. What changes must be applied to the existing wireless network to increase the location accuracy? (Choose two)
Which parameter is the most important factor to consider when deciding service placement in a cloud solution?
Agile and Waterfall are two popular methods for organizing projects. What describes any Agile network design development process?
Which action must be taken before new VoIP systems are implemented on a network to ensure that the network is ready to handle the traffic?
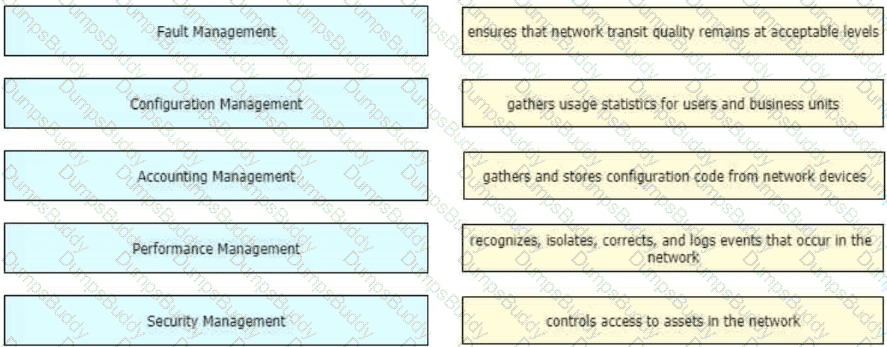
Drag and drop the FCAPS network management reference models from the left onto the correct definitions on the right.
You have been asked to design a high-density wireless network for a university campus. Which two principles would you apply in order to maximize the wireless network capacity? (Choose two.)
Which two protocols are used by SDN controllers to communicate with switches and routers? (Choose two.)
You are designing a network for a branch office. In order to improve convergence time, you are required to use the BFD feature. Which four routing protocols can you use to facilitate this? (Choose four.)
Refer to the exhibit.
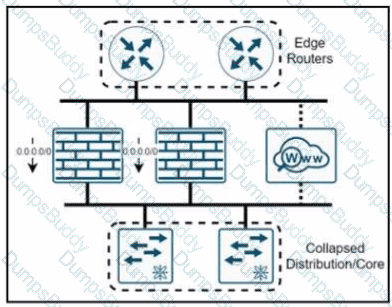
A company named XYZ needs to apply security policies for end-user browsing by installing a secure web proxy appliance. All the web traffic must be inspected by the appliance, and the remaining traffic must be inspected by an NGFW that has been upgraded with intrusion prevention system functionality. In which two ways must the routing be performed? (Choose two)
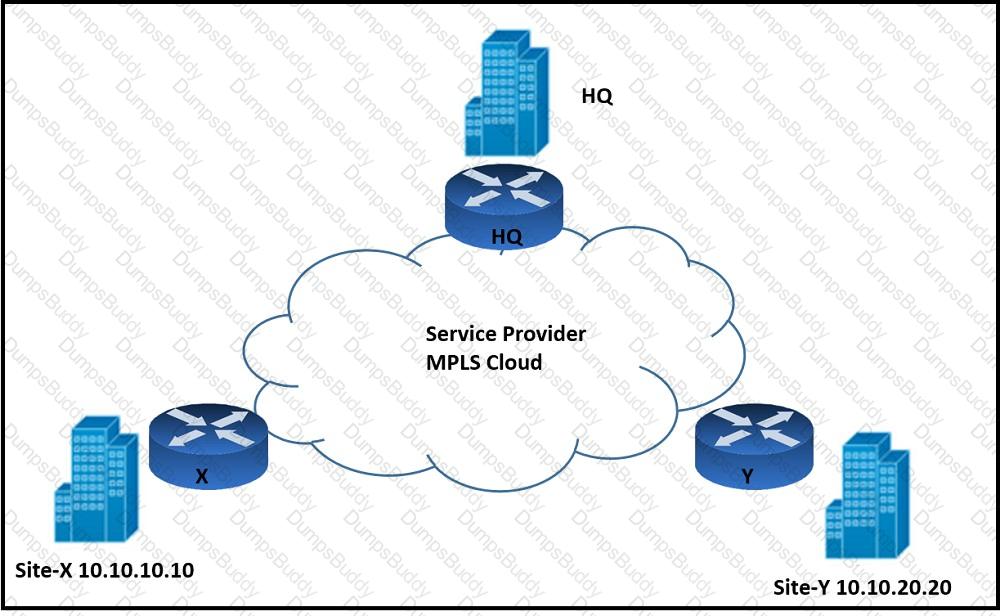
Refer to the exhibit. An architect must design an enterprise WAN that connects the headquarters with 22 branch offices. The number of remote sites is expected to triple in the next three years. The final solution must comply with these requirements:
Only the loopback address of each of the enterprise CE X and Y routers must be advertised to the interconnecting service provider cloud network.
The transport layer must carry the VPNv4 label and VPN payload over the MP-BGP control plane.
The transport layer must not be under service provider control.
Which enterprise WAN transport virtualization technique meets the requirements?
Which two aspects are considered when designing a dual hub dual DMVPN cloud topology? (Choose two.)
You want to mitigate failures that are caused by STP loops that occur before UDLD detects the failure or that are caused by a device that is no longer sending BPDUs. Which mechanism do you use along with UDLD?
Which two actions must merchants do to be compliant with the Payment Card Industry Data Security Standard (PCI DSS)? (Choose two.)
You are designing a new Ethernet-based metro-area network for an enterprise customer to connect 50 sites within the same city. OSPF will be the routing protocol used. The customer is primarily concerned with IPv4 address conservation and convergence time. Which two combined actions do you recommend? (Choose two)
A product manufacturing organization is integrating cloud services into their IT solution. The IT team is working on the preparation phase of the implementation approach, which includes the Define Strategy step. This step defines the scope of IT, the application, and the service. What is one topic that should be considered in the Define Strategy step?
A customer asks you to perform a high-level review of their upcoming WAN refresh for remote sites. The review is specially focused on their retail store operations consisting of 500+ locations connected via multipoint IPsec VPN solution. Which routing protocol would be valid but would also be the most restrictive for the expansion of this deployment model?
Which development model is closely associated with traditional project management?
Which technology supports antispoofing and does not have any impact on encryption performance regardless of packet size?
Which two characteristics apply to firewall transparent mode operations in a firewall solution design? (Choose two.)
Company XYZ network runs IPv4 and IPv6 and they want to introduce a multidomain, multicast-based network. The new design should use a flavor of PIM that forwards traffic using SPT. Which technology meets this requirement?
What is a disadvantage of the traditional three-tier architecture model when east-west traffic between different pods must go through the distribution and core layers?
 Table
Description automatically generated
Table
Description automatically generated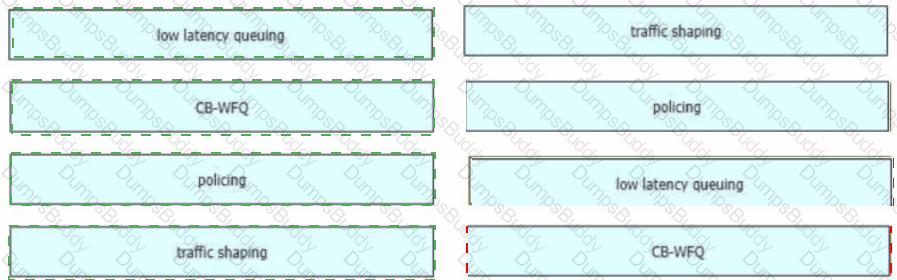
 Table
Description automatically generated with medium confidence
Table
Description automatically generated with medium confidence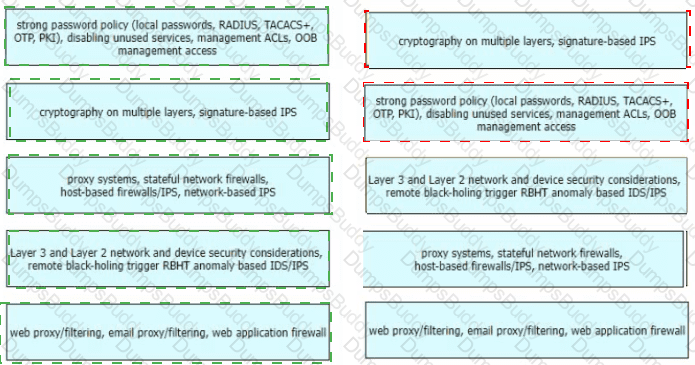

 Table
Description automatically generated
Table
Description automatically generated



