352-011 Cisco Certified Design Expert Practical Exam Questions and Answers
Which two design aspects should a metro service provider consider when planning to deploy REP for his backbone? (Choose two.)
How can jitter be compensated on an IP network that carries real-time VoIP traffic with acceptable voice transmission quality?
Refer to the Exhibit.
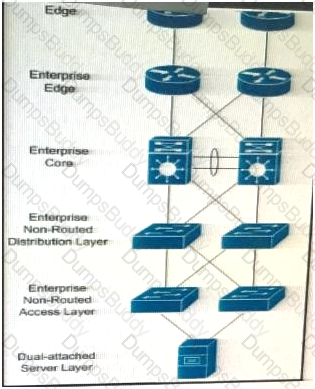
In which three Layers should you use nonstop Forwarding to reduce service impact in case of failure? (Choose three)
Your customer asks you to assist with their traffic policy design. They want to guarantee a minimum amount of bandwidth to certain traffic classes. Which technique would you advise them to implement?
Which two functions are performed at the core layer of the three-layer hierarchical network design model? (Choose two).
ACME Agricultural requires that access to all network devices is granted based on identify validation, and an authentication server was installed for this purpose. Currently the network team uses a list of passwords based on regions to access the internal corporate network devices. Which protocol do you recommend to ensure identify validation from the authentication server to the corporate directory?
A company would like to distribute a virtual machine (VM) hosting cluster between three data centers with the capability to move VMs between sites. The connectivity between data centers is IP only and the new design should use the existing WAN. Which Layer 2 tunneling technology do you recommend?
Which mechanism enables small, unmanaged switches to plug into ports of access switches without risking switch loops?
Which statement about TAP and TUN devices, which are used in a Linux/KVM cloud deployment model, is true?
What is an advantage of placing the IS-IS flooding domain boundary at the core Layer in a three-layer hierarchical network?
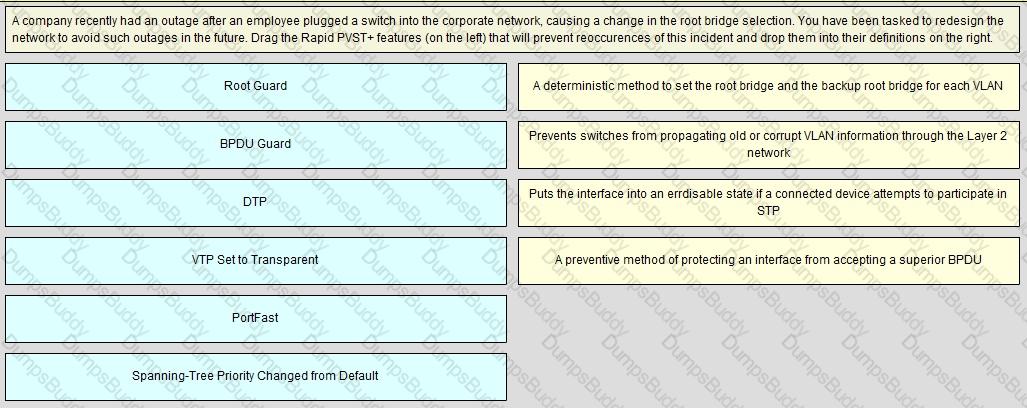
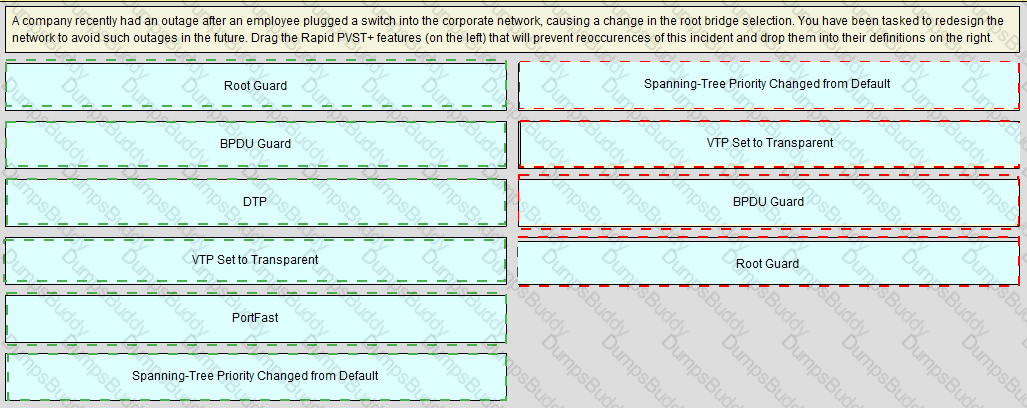
As part of network design, two geographically separated data centers must be interconnected using Ethernet-over-MPLS pseudowire. The link between the sites is stable, the topology has no apparent loops, and the root bridges for the respective VLANs are stable and unchanging. Which aspect must be the part of the design to mitigate the risk of connectivity issues between the data centers?
You are designing a new multisite data center network within the same city. You are using the newest routers that run OSPF and DWDM point-to-point interfaces for site-to-site connectivity. Your primary objective is to use the fastest possible method for interface failure detection. Which method achieves this objective?
Which load balancing option for IP-only traffic is the least efficient in terms of EtherChannel physical links utilization?
What is an effect of using ingress filtering to prevent spoofed addresses on a network design?
The enterprise customer ABC Corp will deploy a centralized unified communications application to provide voice, and instant messaging to their branch offices. Some of the branch offices are located in remote locations and are connected via a 1.5 Mb/s Layer 3 VPN connection. Which two ways are the most cost-effective to ensure that this new application is implemented properly? (Choose two)
An enterprise network has two core routers that connect to 200 distribution routers and uses full-mesh iBGP peering between these routers as its routing method. The distribution routers are experiencing high CPU utilization due to the BGP process. Which design solution is the most effective?
VPLS is implemented in a Layer 2 network with 2000 VLANs. Which must be the primary concern to ensure successful deployment of VPLS?
You are consultant network designer for a large GET VPN deployment for a large bank with International coverage. Between 1800 and 2000 remote locations connect to the central location through four hubs using an MPLS backbone and using two keys servers. The bank is concerned with security and replay attacks. Which two actions should you use to tune the GET VPN to meet the bank requirements? (Choose two)
Refer to the exhibit.
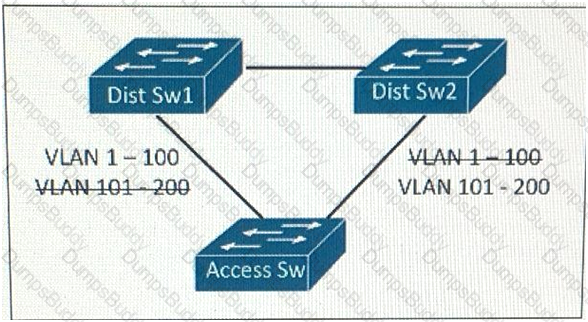
This layer 2 network is expected to add 150 VLANS over the next year, In addition to the existing 50 VLANs within the network which STP types will support this design requirement the least amount of CPU resource and achieving load balancing?
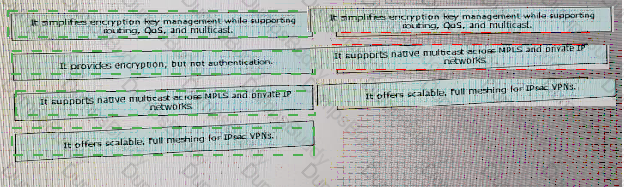
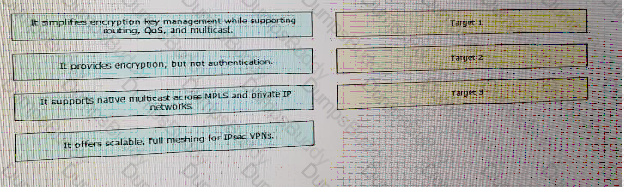
Drag and drop the design characteristics of GET VPN from the left to the right. Not all options are used.
A network has several routers running IS-IS L1L2 mode on the same Ethernet segment. Which action reduces to a minimum the number of IS-IS adjacencies in this segment?
An ISP provides VoIP and internet services to its customers. For security reasons, these services must be transported in different MPLS Layer 3 VPNs over the ISP core network. The customer CEs do not have the ability to segment the services using different VLANs and have only one uplink interface that does not support VLAN tagging. How should you design the network to ensure that VoIP traffic that is received from the CE goes in the VoIP VPN, and that Internet traffic goes into the Internet VPN on the ISP PE devices?
As part of network design, two geographically separated data centers must be interconnected using Ethernet-over-MPLS pseudowire. The link between the sites is stable, the topology has no apparent loops, and the root bridges for the respective VLANs are stable and unchanging. Which aspect must be the part of the design to mitigate the risk of connectivity issues between the data centers?
A Company has these requirements for access to their wireless and wired corporate LANs using 802.1x
Clients devices that corporate assets and have joined the active directory domain are allowed access
Personal devices must be not allowed access
Clients and access servers must be mutually authenticated.
Which solution meets these requirements?
In a VPLS design solution, which situation indicates that BGP must be used instead of LDP in the control plane?