350-901 Developing Applications using Cisco Core Platforms and APIs (DEVCOR) Questions and Answers
A developer corrects an application bug with ID buglDa98416945110x and then installs it on a Cisco Catalyst 9300 series switch. Which command will enable the application called myapp?
Refer to the exhibit.
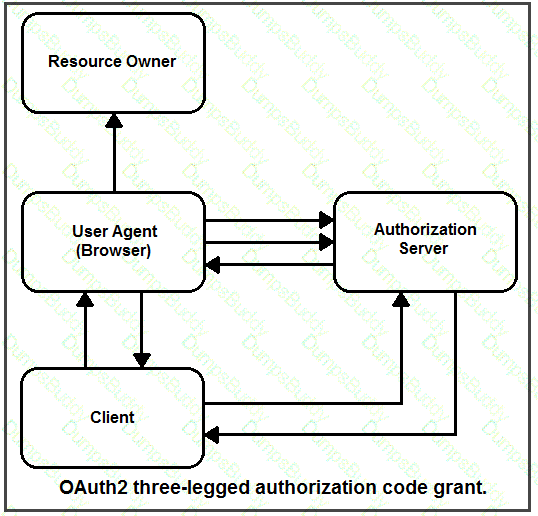
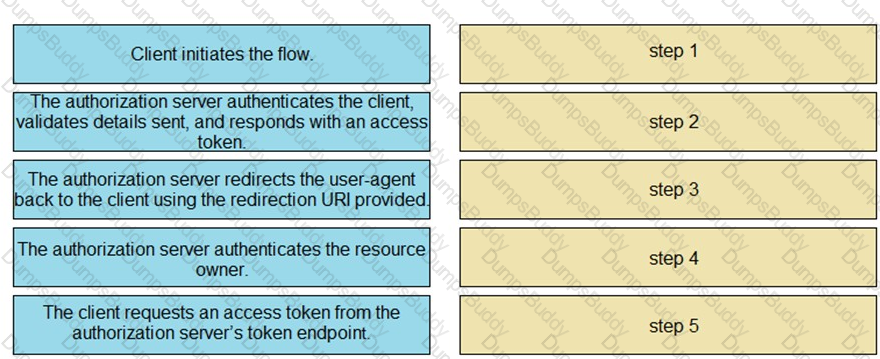
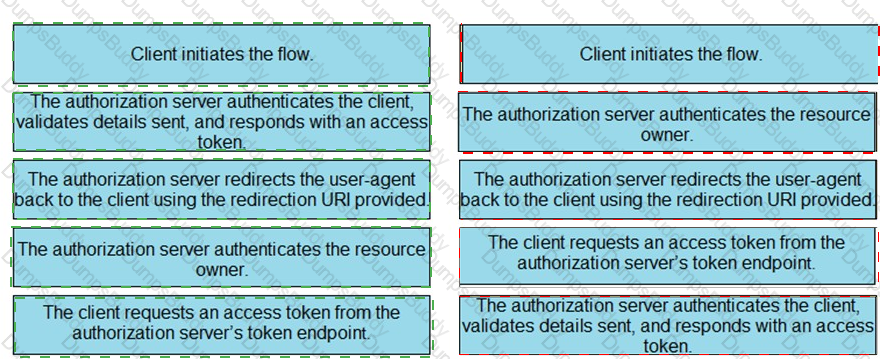
Drag and drop the steps from the left into the correct order of operation on the right for a successful OAuth2 three-legged authorization code grant flow.
A developer is building an application to access a website. When running the application, an HTTP 403 error
code has been received. How should the application be modified to handle this code?
Which type of file is created from issued intermediate, root, and primary certificates for SSL installation on a server?
A cloud native project is being worked on in which all source code and dependencies are written in Python, Ruby, and/or JavaScipt. A change in code triggers a notification to the CI/CD tool to run the CI/CD pipeline.
Which step should be omitted from the pipeline?
Which two countermeasures help reduce the risk of playback attacks? (Choose two.)
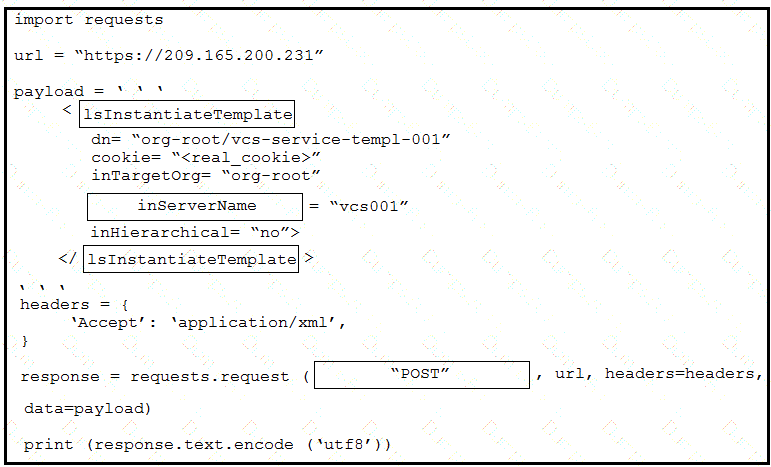
Drag and drop the code from the bottom onto the box where the code is missing to provision a new Cisco Unified Computing System server by using the UCS XML API. Options may be used more than once. Not all options are used.
Which two actions must be taken when an observable microservice application is developed? (Choose two.)
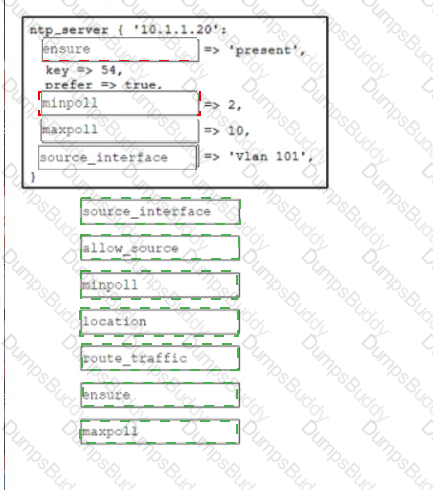
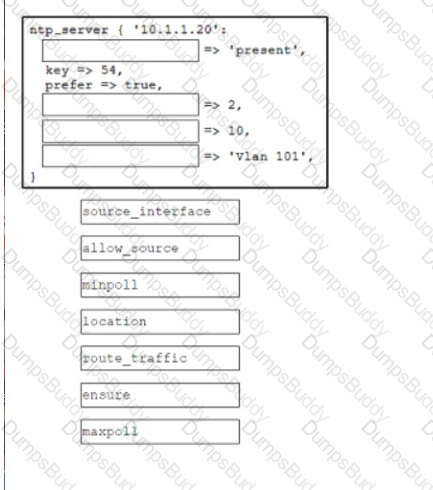
Drag and drop the code from the bottom onto the box where the code is missing to create a Puppet manifest that implements an NTP configuration when applied to a device in the master inventory. Not all options are used.
Refer to the exhibit.
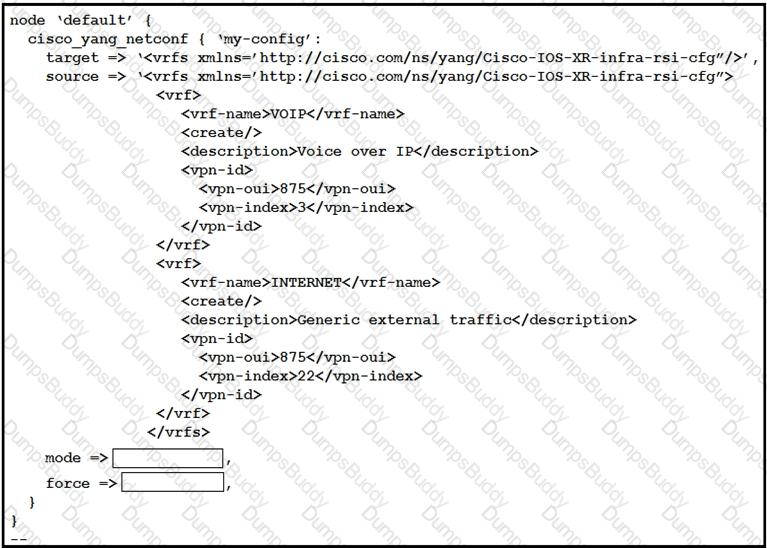
This script uses ciscoyang to configure two VRF instances on a Cisco IOS-XR device using the Yang NETCONF type.
Which two words are required to complete the script? (Choose two.)
Where mus! the data be encrypted to ensure end-to-end encryption when using an API?
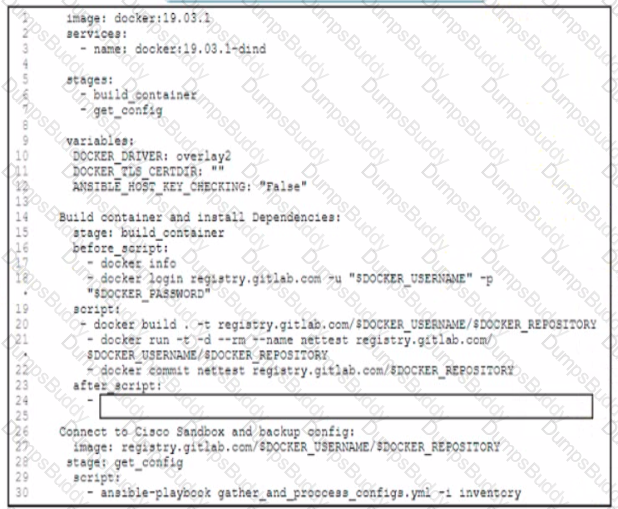
Refer to the exhibit , The command docker build -tag=friendlyhello . is run to build a docker image from the given Dockerfile,
requirements,txt, and app.py, Then the command docker run -p 4000:80 friendlyhello is executed to run the application. Which URL is entered in the web browser to see the content served by the application?
Refer to the exhibit.

An application is being developed as an information repository. The application will be used to store details about television shows, including the scenario, year, and category. Which database type must used for high performance for the data structure?
What is a consideration for using gRPC as the model-driven telemetry protocol on a Cisco IOS XE device?
In the three-legged OAuth2 authorization workflow, which entity grants access to a protected resource?
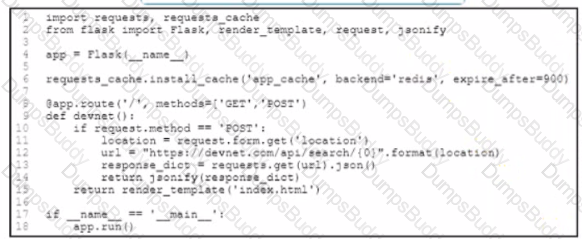
Refer to the exhibit.
An application has been developed to serve the users in an enterprise After HTTP cache controls are implemented m the application users report that they receive state data when they refresh the page Without removing HTTP cache controls, which change ensures that the users get current data when refreshing the page'
An organization manages a large cloud-deployed application that employs a microservices architecture across multiple data centers. Reports have received about application slowness. The container orchestration logs show that faults have been raised in a variety of containers that caused them to fail and then spin up brand new instances.
Which two actions can improve the design of the application to identify the faults? (Choose two.)
Refer to the exhibit.

A developer must review an intern's code for a script they wrote to automate backups to the storage server. The script must connect to the network device and copy the running-config to the server. When considering maintainability, which two changes must be made to the code? (Choose two.)
Refer to the exhibit.
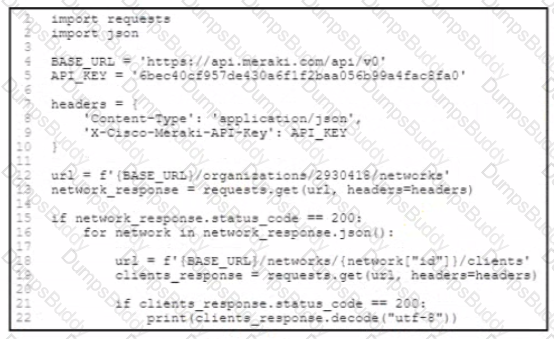
One part of an application routinely uses the Cisco Meraki API to collate data about all clients Other parts of the application also use the Meraki API, but a single API key is used within the application The organization has approximately 4.000 clients across 30 networks Some of the application users report poor performance and missing data. Which two changes improve the performance of the application? (Choose two.)
Refer to the exhibit.
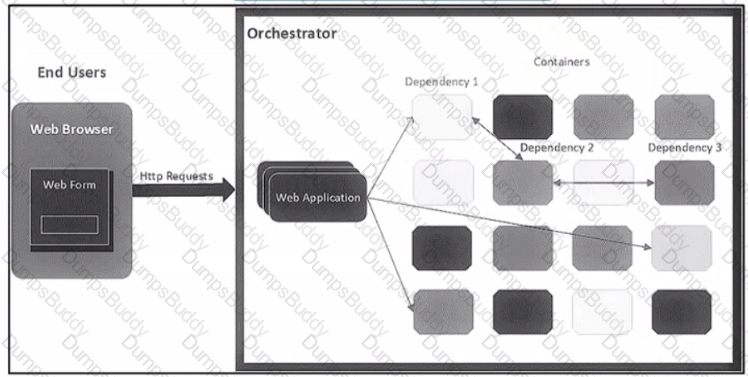
The application follows a containerized microservices architecture that has one container per microservice. The microservices communicate with each other by using REST APIs The double-headed arrows m the diagram display chains of synchronous HTTP calls needed for a single use/request Which action ensures the resilience of the application in the scope of a single user request?
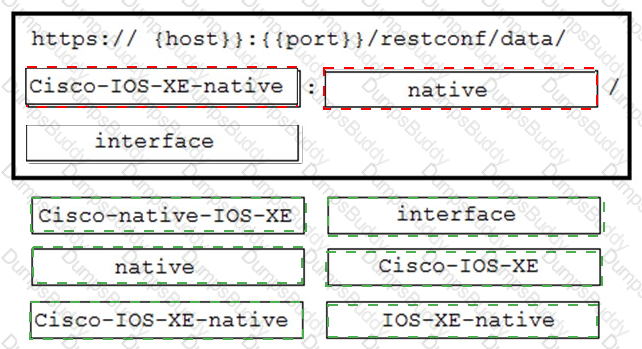
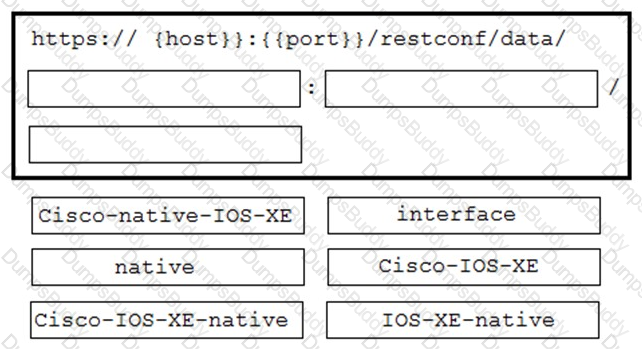
A network engineer needs to retrieve interface data using the Cisco IOS XE YANG Model. Drag and drop the
components from the bottom onto the box where the code is missing to complete the RESTCONF URI. Not all
options are used.
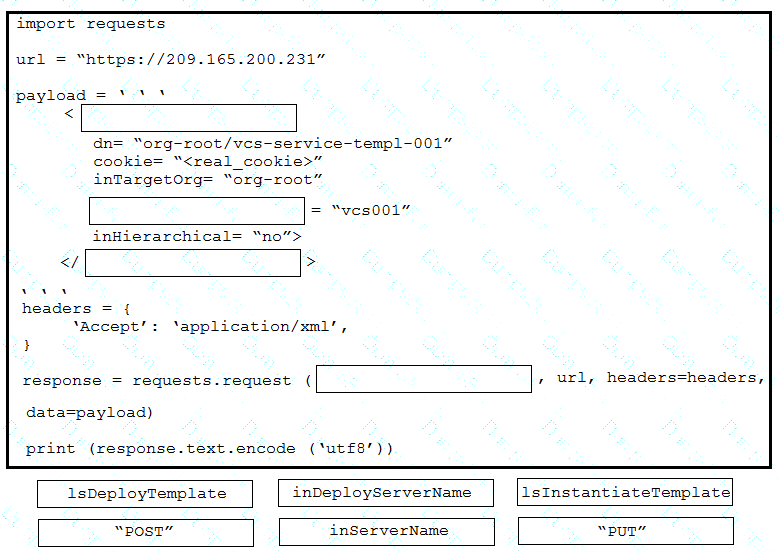
Drag and drop the code from the bottom onto the box where the code is missing to construct a UCS XML API request to generate two service profiles from the template org-root/is-service-template. Not at options are used

Where should distributed load balancing occur in a horizontally scalable architecture?
A developer needs to configure an environment to orchestrate and configure. Which two tools should be used for each task? (Choose two.)
{'lat': 37.4180951010362, 'lng': -122.098531723022, 'address': '', 'serial': 'Q2HP-F5K5-F98Q',
'mac': '88:15:44:ea:f5:bf', 'lanIp': '10.10.10.15',
'url': 'https://n149.meraki.com/DevNet-Sandbox/n/EFZDavc/manage/nodes/new_list/78214561218351',
'model': 'MS220-8P', 'switchProfileId': None, 'firmware': 'switch-11-31', 'floorPlanId': None}
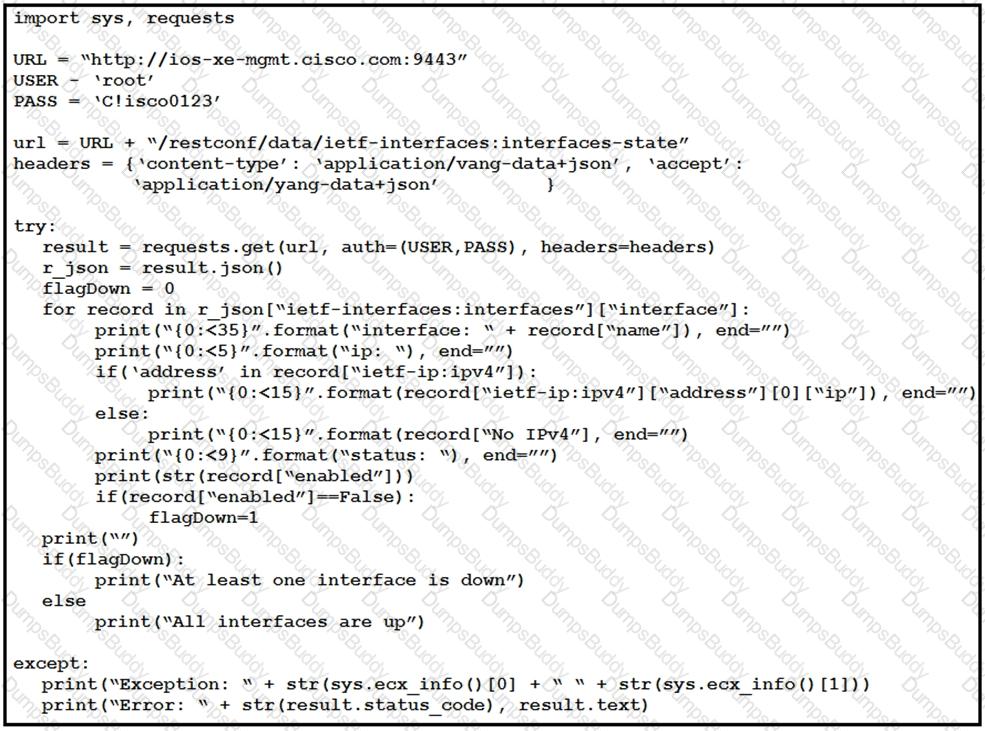
Refer to the exhibit. A developer needs to find the geographical coordinates of a device on the network L_397561557481105433 using a Python script to query the Meraki API. After running response = requests.get() against the Meraki API, the value of response.text is shown in the exhibit.
What Python code is needed to retrieve the longitude and latitude coordinates of the device?
Refer to the exhibit.
A network administrator copies SSL certificates to a Cisco NX-OS switch. An Ansible playbook is created to enable NX-API, which will use the new certificate. In the group_vars/vars.yml file, which code snippet must be used to define the properly formatted variables?
A)
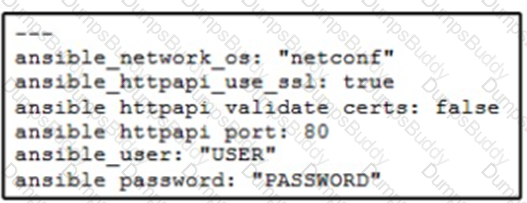
B)
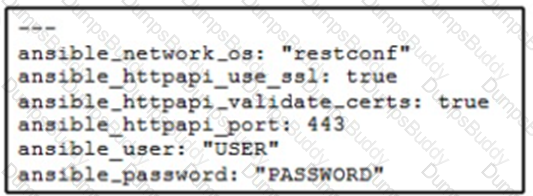
C)
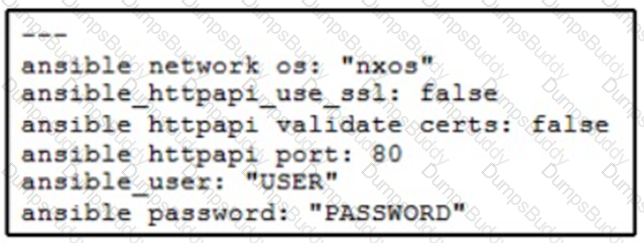
D)
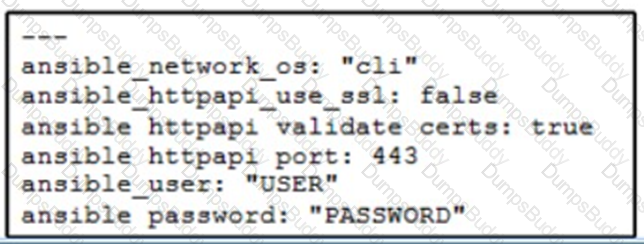
Refer to the exhibit.
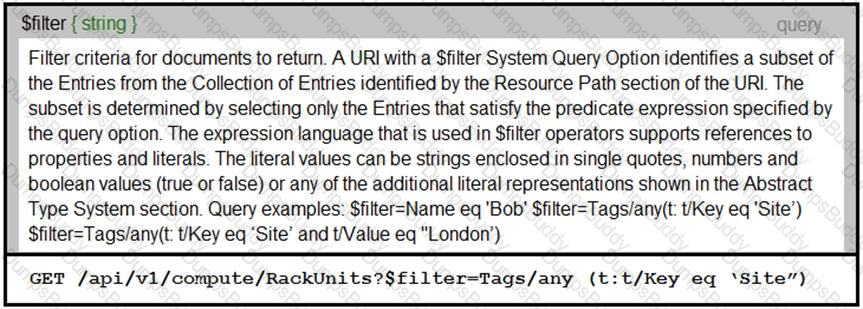
An Intersight API is being used to query RackUnit resources that have a tag keyword set to “Site”. What is the expected output of this command?
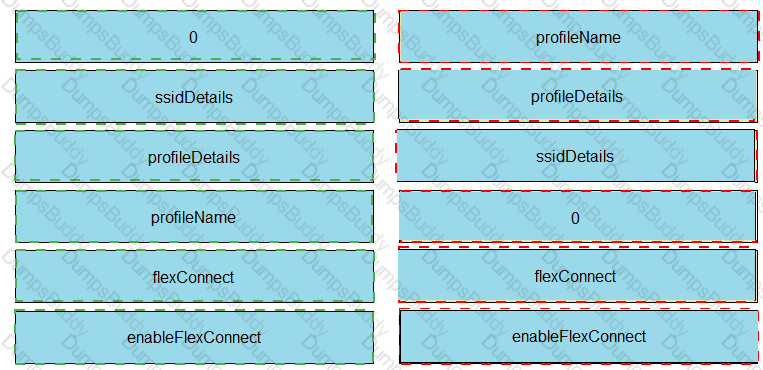
Refer to the exhibit.
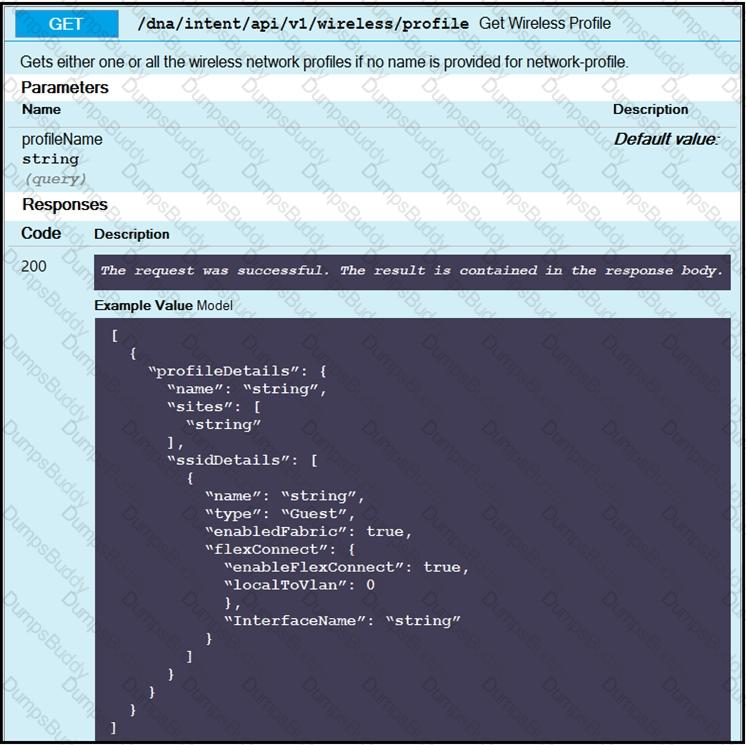
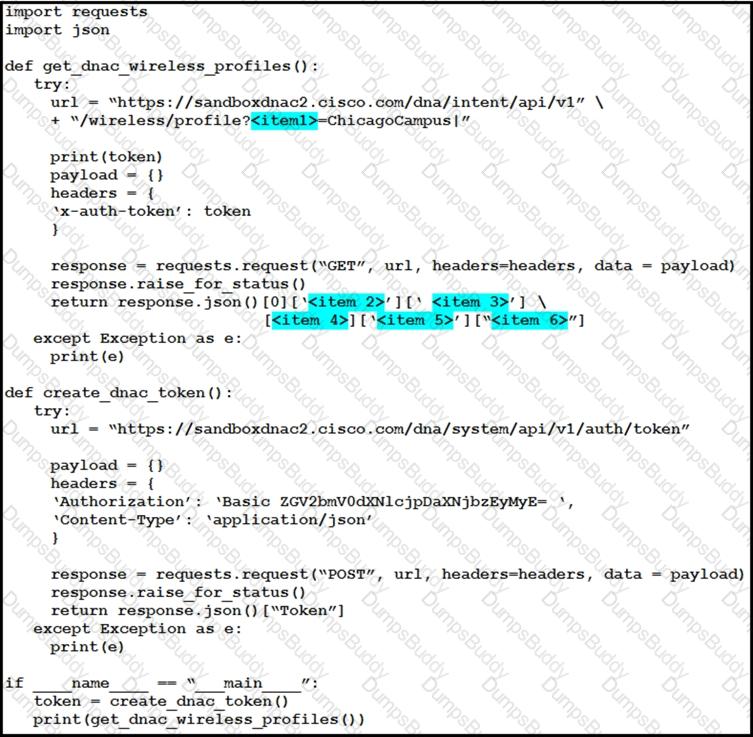
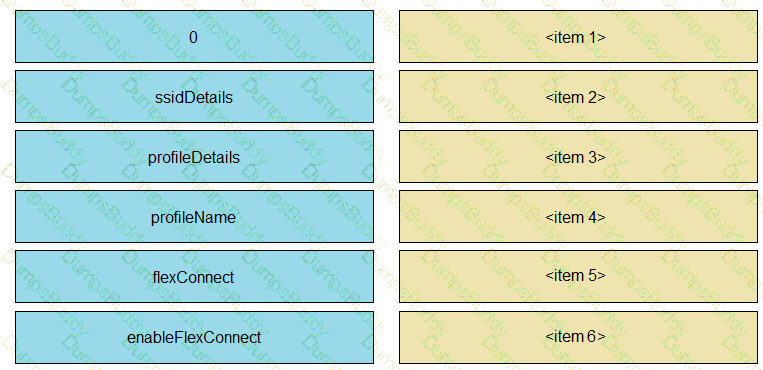
The Python script is supposed to make an API call to Cisco DNA Center querying a wireless profile for the “ChicagoCampus” and then parsing out its enable FlexConnect value. Drag and drop the parts of the Python code from the left onto the item numbers on the right that match the missing sections in the exhibit.
Refer to the exhibit.

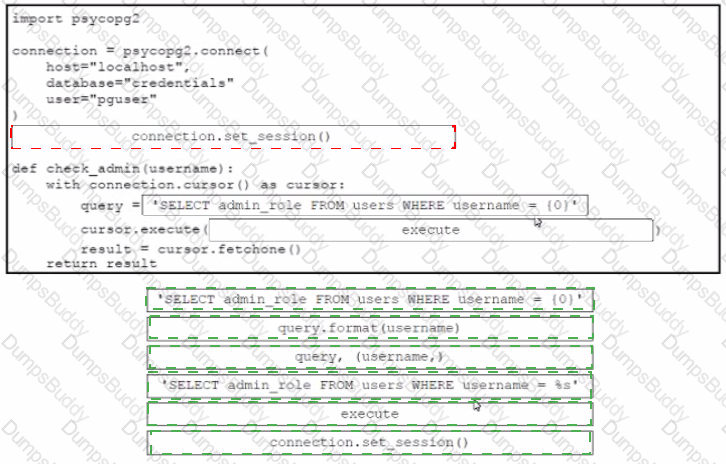
Which action should be performed to avoid an SQL injection attack?
Refer to the exhibit.
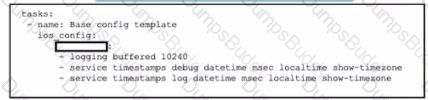
Which word is missing from this Ansible playbook shown, to allow the Cisco IOS XE commands for router configuration to be pushed after the playbook is executed?
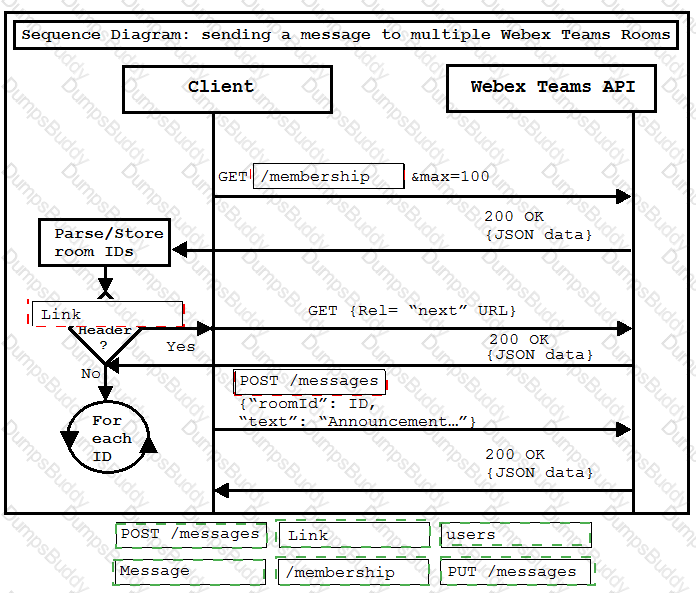
Drag and drop the code from the bottom onto the box where the code is missing in the diagram to show how data is processed in Webex Teams. Not all options are used.
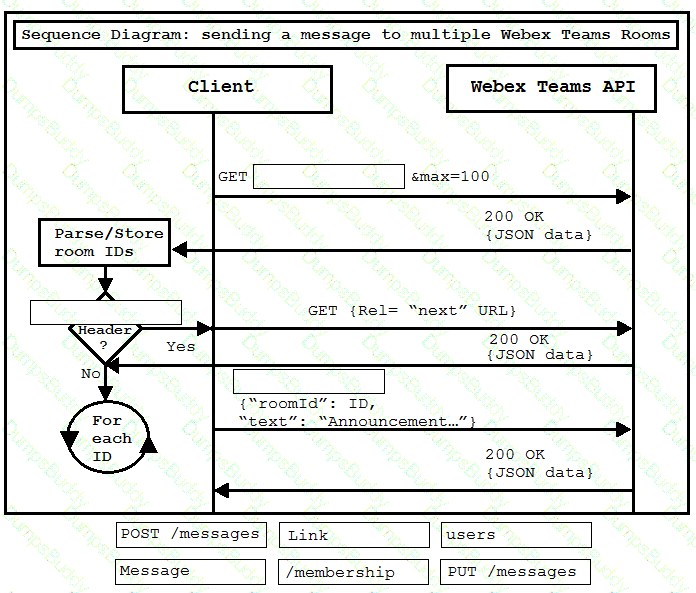
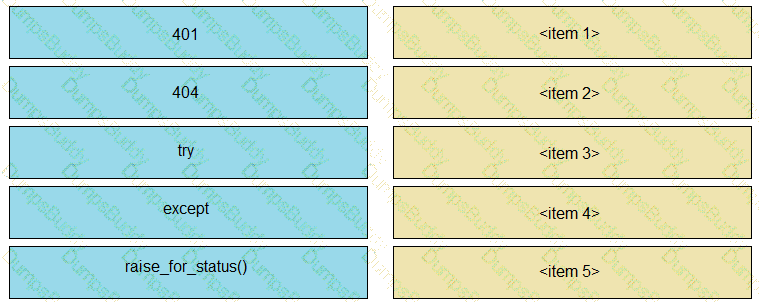
A developer is creating a Python script to use the Webex Teams REST API to list joined spaces, and gracefully handle and print the errors it receives. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script.
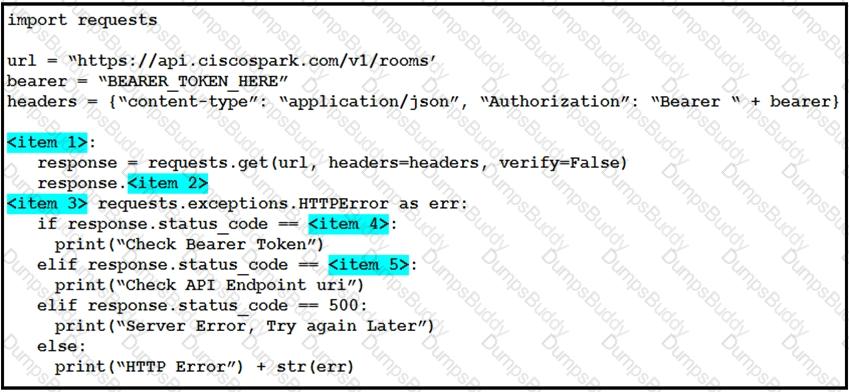
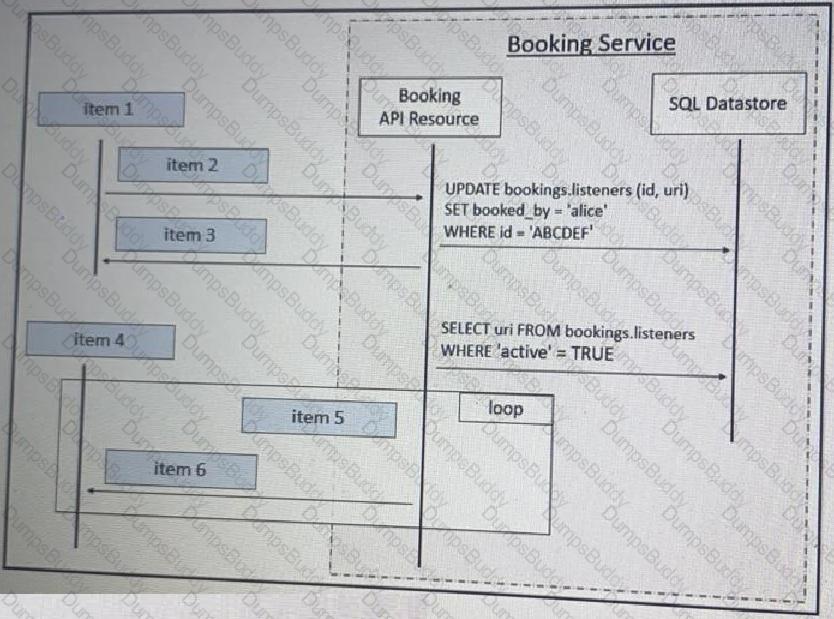
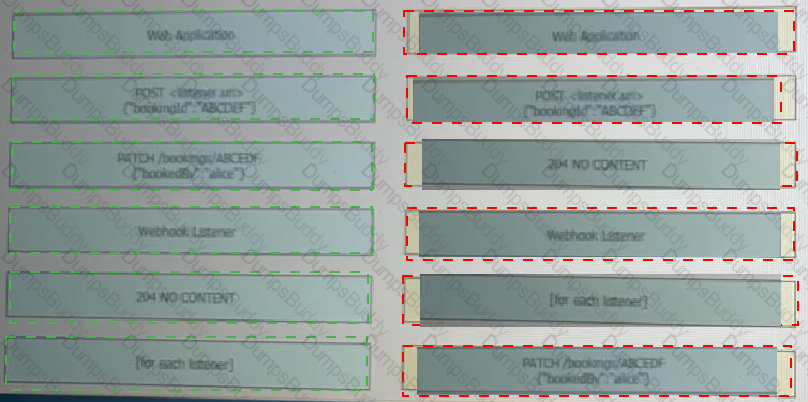
Refer to the exhibit above and click on the tab in the top left corner to view a diagram that describes the typical flow of requests involved when a webhook is created for a booking service. Drag and drop the requests from the left onto the item numbers on the right that match the missing sections in the sequence diagram to design the complete flow of requests involved as a booking is updated from a web application.

Drag and drop the code from the bottom onto the where the code is missing to create a host object by using the Cisco Firepower Device Manager API. Not all options are used.

A developer must recommend an appropriate tool to deploy a configuration to hundreds of servers. The configuration management solution must meet these requirements.
• The servers must initiate the connection to obtain updates
• The configuration must be defined in a declarative style
Which tool should be used?
Users report that they are no longer able to process transactions with the online ordering application, and the logging dashboard is
displaying these messages:
Fri Jan 10 19:37:31.123 ESI 2020 [FRONTEND] [NFO: Incoming request to add item to cart from user 45834534858
Fri Jan 10 19:37:31.247 EST 2020 [BACKEND] INFO: Attempting to add item to cart
Fri Jan 10 19:37:31.250 EST 2020 [BACKEND] ERROR: Failed to add item: MYSQLDB ERROR: Connection refused
What is causing the problem seen in these log messages?
Refer to the exhibit.
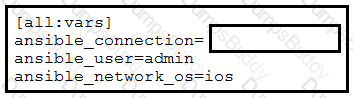
An engineer is configuring Ansible to run playbooks against Cisco IOS XE Software. What
should be configured in ansible.cfg as the connection type?
When an application is designed that requires high availability, what is a reason to use a cross-region cloud?
Refer to the exhibit.
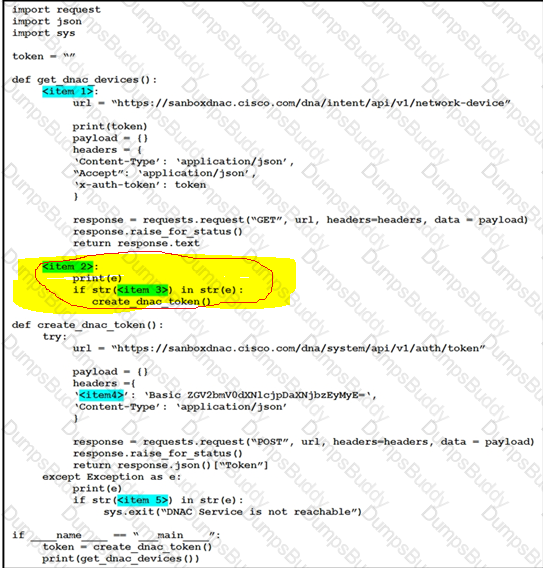
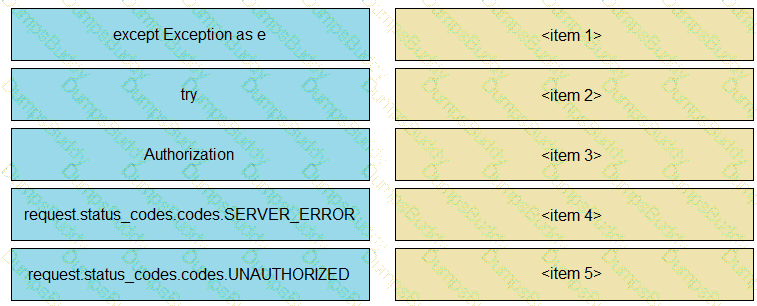
Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script to implement control flow.
A new record-keeping application for employees to track customer orders must be deployed to a company's existing infrastructure. The host servers reside in a data center in a different country to where the majority of users work. The new network configuration for the database server is: •IP: 10.8.32.10
• Subnet Mask: 255.255.255.0
• Hostname: CustOrd423320458-Prod-010
• MAC: 18-46-AC-6F-F4-52.
The performance of the client-side application is a priority due to the high demand placed on it by employees. Which area should the team consider in terms of impact to application performance due to the planned deployment?
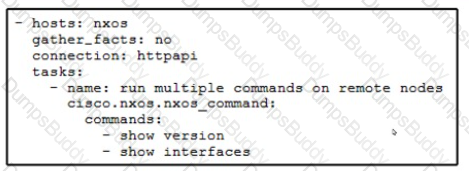
A local data center deployment using Cisco NX-OS switches is scaling and requires automatic configuration at scale Configuration management must be set up for a Cisco NX-OS switch by using Ansible. The Ansible control server is currently located on a different subnet than the switch The solution has these requirements
• The transport protocol used must be encrypted
• The connections must originate from a server m the same local network
• Enable mode must be supported
Which connectivity method must be used?
Refer to the exhibit.
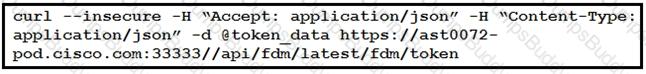
The cURL POST request creates an OAuth access token for authentication with FDM API requests. What is the purpose of the file “@token_data” that cURL is handling?
Refer to the exhibit.
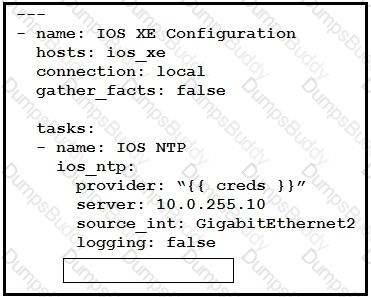
Which key value pair from the ios_ntp Ansible module creates an NTP server peer?
Refer to the exhibit.

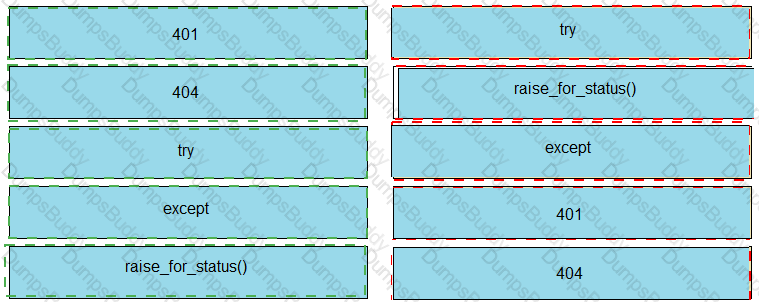
This snippet of a script has recently started exiting abnormally with an exception stating “Unexpected HTTP Response code: 429”.
Which solution handles rate limiting by the remote API?
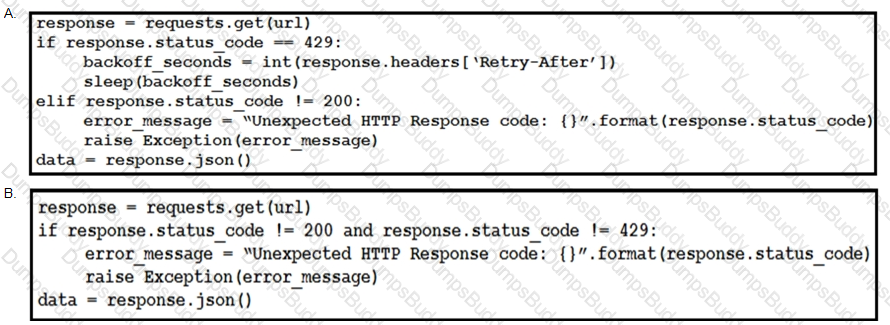
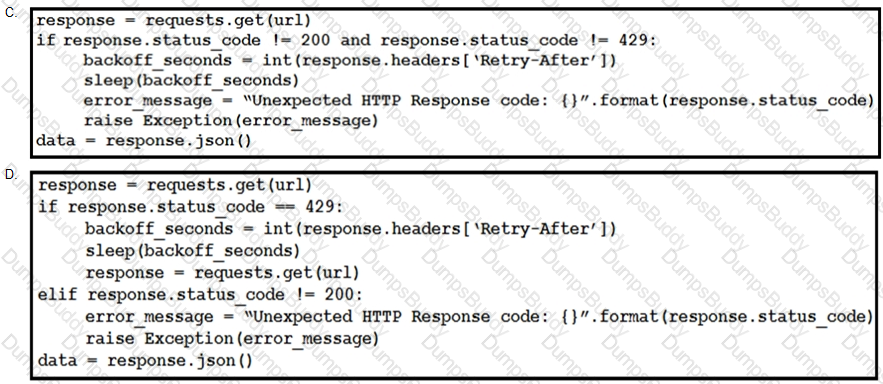
Refer to the exhibit.
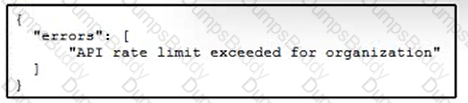
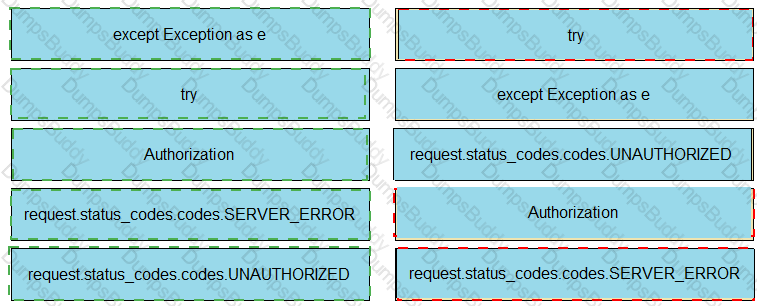
An architect wrote an application to collect device information from the Cisco Meraki Dashboard API. Every time a network change occurs the application collects information and records new endpoint MAC addresses. The application stopped working after the locations and network equipment of a competitor were acquired. Which application approach must be applied to reduce latency and rate limiting?
Drag and drop the code from the bottom onto the box where the code is missing in the Python code to query for user permissions while mitigating against SQL Injection Not all options are used.

Refer to the exhibit.
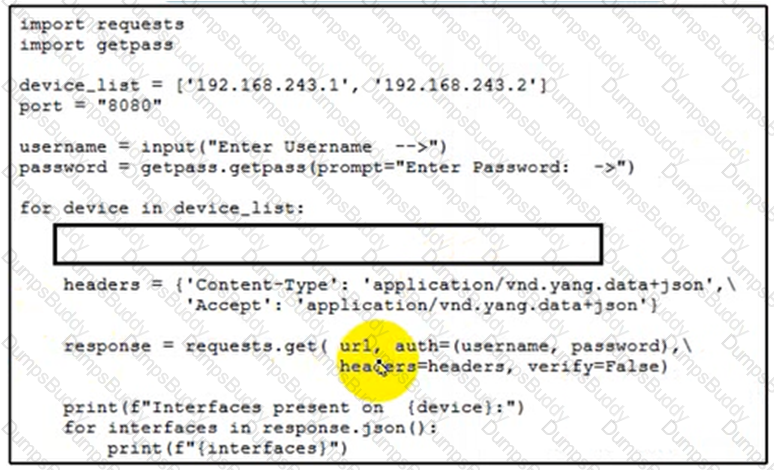
Cisco IOS XE switches are used across the entire network and the description that is filed for all interfaces must be configured. Which code snippet must be placed in the blank in the script to leverage RESTCONF to query all the devices in the device list for the interfaces that are present?
A)

B)
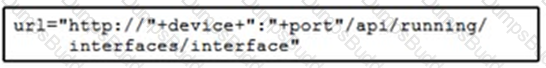
C)
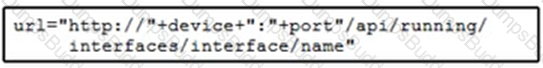
D)


 Graphical user interface, text, application
Description automatically generated
Graphical user interface, text, application
Description automatically generated