350-701 Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) Questions and Answers
An organization has a Cisco ESA set up with policies and would like to customize the action assigned for
violations. The organization wants a copy of the message to be delivered with a message added to flag it as a
DLP violation. Which actions must be performed in order to provide this capability?
Which two parameters are used to prevent a data breach in the cloud? (Choose two.)
Drag and drop the VPN functions from the left onto the descriptions on the right.
An engineer must configure Cisco AMP for Endpoints so that it contains a list of files that should not be executed by users. These files must not be quarantined. Which action meets this configuration requirement?
Which statement about the configuration of Cisco ASA NetFlow v9 Secure Event Logging is true?
Which technology provides the benefit of Layer 3 through Layer 7 innovative deep packet inspection,
enabling the platform to identify and output various applications within the network traffic flows?
After a recent breach, an organization determined that phishing was used to gain initial access to the network before regaining persistence. The information gained from the phishing attack was a result of users visiting known malicious websites. What must be done in order to prevent this from happening in the future?
A company discovered an attack propagating through their network via a file. A custom file policy was created in order to track this in the future and ensure no other endpoints execute the infected file. In addition, it was discovered during testing that the scans are not detecting the file as an indicator of compromise. What must be done in order to ensure that the created is functioning as it should?
Refer to the exhibit.
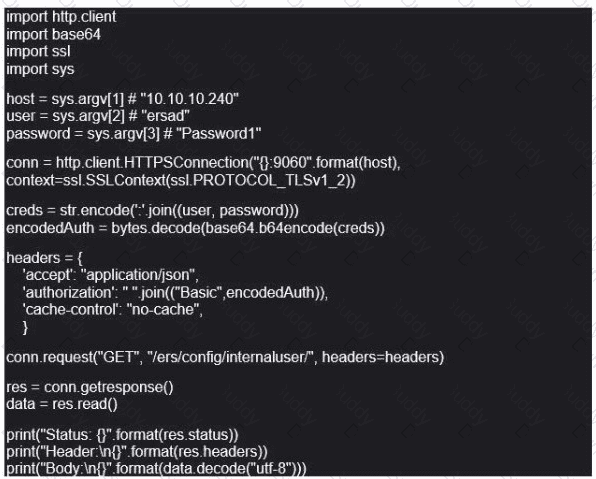
What does the API do when connected to a Cisco security appliance?
An organization is implementing URL blocking using Cisco Umbrella. The users are able to go to some sites
but other sites are not accessible due to an error. Why is the error occurring?
Which solution protects hybrid cloud deployment workloads with application visibility and segmentation?
An organization wants to use Cisco FTD or Cisco ASA devices. Specific URLs must be blocked from being
accessed via the firewall which requires that the administrator input the bad URL categories that the
organization wants blocked into the access policy. Which solution should be used to meet this requirement?
Which statement describes a traffic profile on a Cisco Next Generation Intrusion Prevention System?
An engineer recently completed the system setup on a Cisco WSA Which URL information does the system send to SensorBase Network servers?
Which two capabilities of Integration APIs are utilized with Cisco Catalyst Center? (Choose two.)
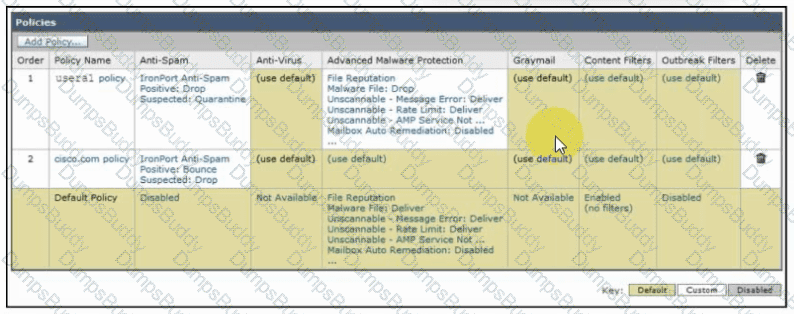
Refer to the exhibit. An engineer must configure an incoming mail policy so that each email sent from usera1@example.com to a domain of @cisco.com is scanned for antispam and advanced malware protection. All other settings will use the default behavior. What must be configured in the incoming mail policy to meet the requirements?
Which component of Cisco umbrella architecture increases reliability of the service?
In which two customer environments is the Cisco Secure Web Appliance Virtual connector traffic direction method selected? (Choose two.)
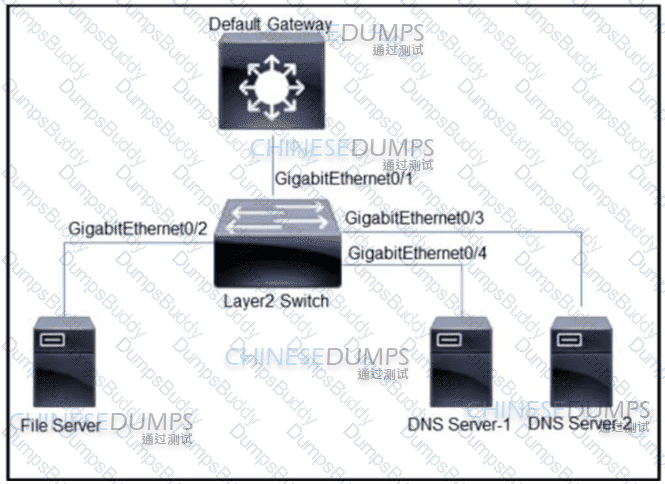
Refer to the exhibit. All servers are in the same VLAN/Subnet. DNS Server-1 and DNS Server-2 must communicate with each other, and all servers must communicate with default gateway multilayer switch. Which type of private VLAN ports should be configured to prevent communication between DNS servers and the file server?

Refer to the exhibit. Consider that any feature of DNS requests, such as the length of the domain name and the number of subdomains, can be used to construct models of expected behavior to which observed values can be compared. Which type of malicious attack are these values associated with?
Which Cisco product provides proactive endpoint protection and allows administrators to centrally manage the
deployment?
A malicious user gained network access by spoofing printer connections that were authorized using MAB on
four different switch ports at the same time. What two catalyst switch security features will prevent further
violations? (Choose two)
A customer has various external HTTP resources available including Intranet Extranet and Internet, with a
proxy configuration running in explicit mode. Which method allows the client desktop browsers to be configured
to select when to connect direct or when to use the proxy?
An engineer is configuring cloud logging on Cisco ASA and needs events to compress. Which component must be configured to accomplish this goal?
Which two kinds of attacks are prevented by multifactor authentication? (Choose two)
Which policy is used to capture host information on the Cisco Firepower Next Generation Intrusion Prevention
System?
Which two features of Cisco DNA Center are used in a Software Defined Network solution? (Choose two)
Drag and drop the features of Cisco ASA with Firepower from the left onto the benefits on the right.
A network engineer is trying to figure out whether FlexVPN or DMVPN would fit better in their environment.
They have a requirement for more stringent security multiple security associations for the connections, more efficient VPN establishment as well consuming less bandwidth. Which solution would be best for this and why?
An organization uses Cisco FMC to centrally manage multiple Cisco FTD devices. The default management
port conflicts with other communications on the network and must be changed. What must be done to ensure
that all devices can communicate together?
What does the Cloudlock Apps Firewall do to mitigate security concerns from an application perspective?
An organization deploys multiple Cisco FTD appliances and wants to manage them using one centralized
solution. The organization does not have a local VM but does have existing Cisco ASAs that must migrate over
to Cisco FTDs. Which solution meets the needs of the organization?
What are two differences between a Cisco WSA that is running in transparent mode and one running in explicit mode? (Choose two)
An administrator enables Cisco Threat Intelligence Director on a Cisco FMC. Which process uses STIX and allows uploads and downloads of block lists?
A Cisco AMP for Endpoints administrator configures a custom detection policy to add specific MD5 signatures The configuration is created in the simple detection policy section, but it does not work What is the reason for this failure?
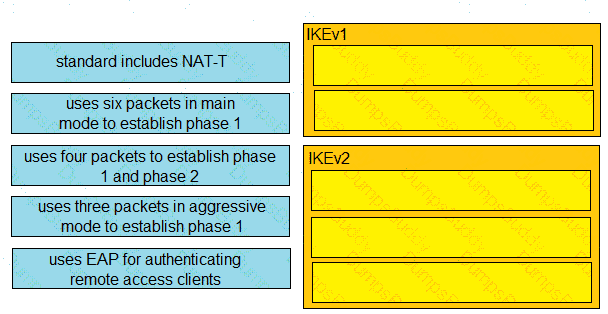
Drag and drop the descriptions from the left onto the correct protocol versions on the right.
Refer to the exhibit.
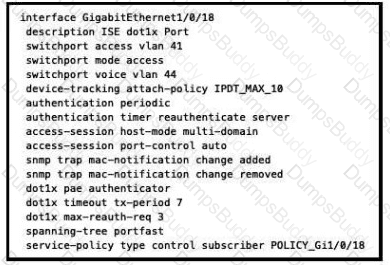
What will occur when this device tries to connect to the port?
Which two request methods of REST API are valid on the Cisco ASA Platform? (Choose two.)
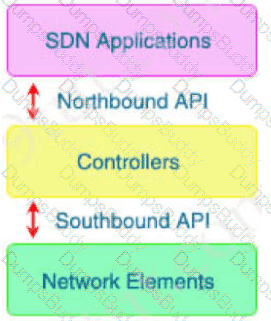
Which type of API is being used when a controller within a software-defined network architecture dynamically
makes configuration changes on switches within the network?
An administrator is adding a new switch onto the network and has configured AAA for network access control. When testing the configuration, the RADIUS authenticates to Cisco ISE but is being rejected. Why is the ip radius source-interface command needed for this configuration?
A switch with Dynamic ARP Inspection enabled has received a spoofed ARP response on a trusted interface.
How does the switch behave in this situation?
Which system facilitates deploying microsegmentation and multi-tenancy services with a policy-based container?
An engineer must force an endpoint to re-authenticate an already authenticated session without disrupting the
endpoint to apply a new or updated policy from ISE. Which CoA type achieves this goal?
A network engineer has entered the snmp-server user andy myv3 auth sha cisco priv aes 256
cisc0380739941 command and needs to send SNMP information to a host at 10.255.254.1. Which command achieves this goal?
A network engineer is tasked with configuring a Cisco ISE server to implement external authentication against Active Directory. What must be considered about the authentication requirements? (Choose two.)
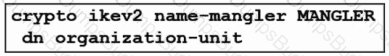
What is the function of the crypto is a kmp key cisc406397954 address 0.0.0.0 0.0.0.0 command when establishing an IPsec VPN tunnel?
Which VPN technology supports a multivendor environment and secure traffic between sites?
An organization wants to reduce their attach surface for cloud applications. They want to understand application communications, detect abnormal application Behavior, and detect vulnerabilities within the applications. Which action accomplishes this task?
A network engineer must migrate a Cisco WSA virtual appliance from one physical host to another physical host by using VMware vMotion. What is a requirement for both physical hosts?
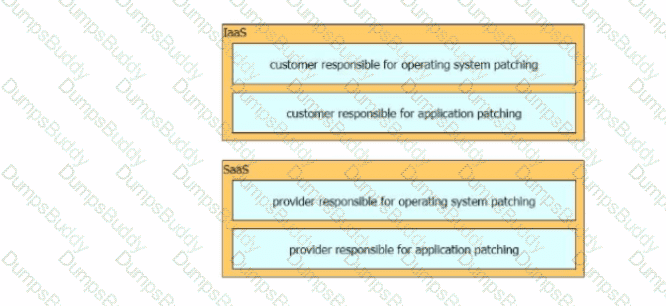
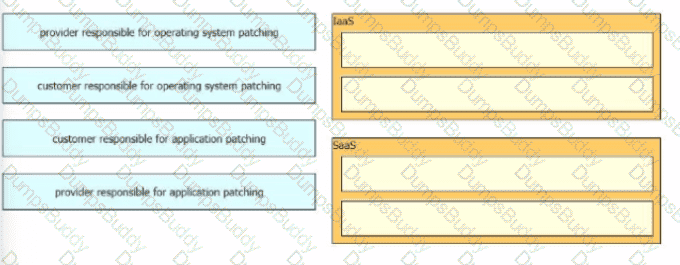
Drag and drop the security responsibilities from the left onto the corresponding cloud service models on the right.
An engineer notices traffic interruption on the network. Upon further investigation, it is learned that broadcast
packets have been flooding the network. What must be configured, based on a predefined threshold, to
address this issue?
Refer to the exhibit. An engineer is implementing a certificate-based VPN. What is the result of the existing configuration?
An organization is trying to implement micro-segmentation on the network and wants to be able to gain visibility on the applications within the network. The solution must be able to maintain and force compliance. Which product should be used to meet these requirements?
An organization is using DNS services for their network and want to help improve the security of the DNS infrastructure. Which action accomplishes this task?
In an IaaS cloud services model, which security function is the provider responsible for managing?
Which cloud model is a collaborative effort where infrastructure is shared and jointly accessed by several organizations from a specific group?
How does Cisco Workload Optimization portion of the network do EPP solutions solely performance issues?
The main function of northbound APIs in the SDN architecture is to enable communication between which two areas of a network?
An engineer needs behavioral analysis to detect malicious activity on the hosts, and is configuring the
organization’s public cloud to send telemetry using the cloud provider’s mechanisms to a security device. Which
mechanism should the engineer configure to accomplish this goal?
What is the recommendation in a zero-trust model before granting access to corporate applications and resources?
An engineer needs a cloud solution that will monitor traffic, create incidents based on events, and integrate with
other cloud solutions via an API. Which solution should be used to accomplish this goal?
An engineer is trying to decide between using L2TP or GRE over IPsec for their site-to-site VPN implementation. What must be un solution?
An engineer is configuring Cisco WSA and needs to deploy it in transparent mode. Which configuration component must be used to accomplish this goal?
Which two components do southbound APIs use to communicate with downstream devices? (Choose two.)
Which feature is used in a push model to allow for session identification, host reauthentication, and session termination?
An engineer needs to configure a Cisco Secure Email Gateway (SEG) to prompt users to enter multiple forms of identification before gaining access to the SEG. The SEG must also join a cluster using the preshared key of cisc421555367. What steps must be taken to support this?
Which SNMPv3 configuration must be used to support the strongest security possible?
What is the primary difference between an Endpoint Protection Platform and an Endpoint Detection and
Response?
Which cloud service offering allows customers to access a web application that is being hosted, managed, and maintained by a cloud service provider?
In which situation should an Endpoint Detection and Response solution be chosen versus an Endpoint Protection Platform?
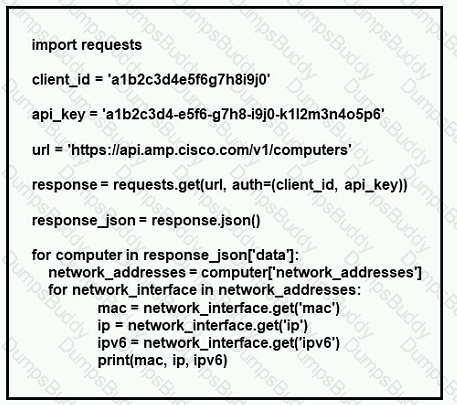
Refer to the exhibit.
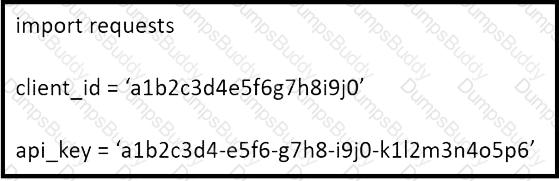
What does the API key do while working with https://api.amp.cisco.com/v1/computers?
An organization wants to secure data in a cloud environment. Its security model requires that all users be
authenticated and authorized. Security configuration and posture must be continuously validated before access is granted or maintained to applications and data. There is also a need to allow certain application traffic and deny all other traffic by default. Which technology must be used to implement these requirements?
Which Cisco ASA deployment model is used to filter traffic between hosts in the same IP subnet using higher-level protocols without readdressing the network?
An engineer needs to detect and quarantine a file named abc424400664 zip based on the MD5 signature of the file using the Outbreak Control list feature within Cisco Advanced Malware Protection (AMP) for Endpoints The configured detection method must work on files of unknown disposition Which Outbreak Control list must be configured to provide this?
Which open standard creates a framework for sharing threat intelligence in a machine-digestible format?
What is the result of running the crypto isakmp key ciscXXXXXXXX address 172.16.0.0 command?
Which feature is leveraged by advanced antimalware capabilities to be an effective endpomt protection platform?
Refer to the exhibit.
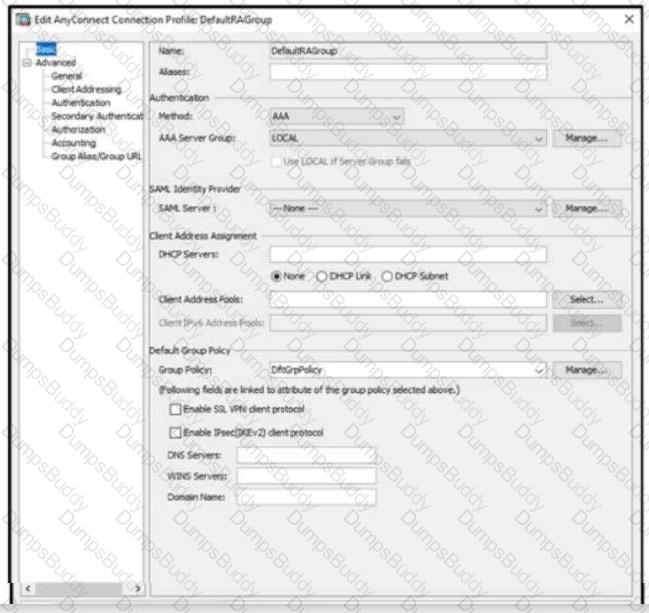
When configuring a remote access VPN solution terminating on the Cisco ASA, an administrator would like to utilize an external token authentication mechanism in conjunction with AAA authentication using machine
certificates. Which configuration item must be modified to allow this?
After deploying a Cisco ESA on your network, you notice that some messages fail to reach their destinations.
Which task can you perform to determine where each message was lost?
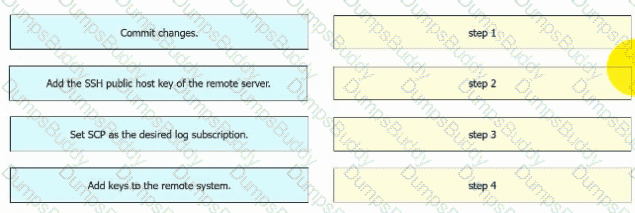
An engineer must configure AsyncOS for Cisco Secure Web Appliance to push log files to a syslog server using the SCP retrieval method. Drag and drop the steps from the left into the sequence on the right to complete the configuration.
When using Cisco AMP for Networks which feature copies a file to the Cisco AMP cloud for analysis?
What is the term for when an endpoint is associated to a provisioning WLAN that is shared with guest
access, and the same guest portal is used as the BYOD portal?
A company identified a phishing vulnerability during a pentest What are two ways the company can protect employees from the attack? (Choose two.)
Which two actions does the Cisco ISE posture module provide that ensures endpoint security? (Choose two.)
An engineer is implementing NTP authentication within their network and has configured both the client and server devices with the command ntp authentication-key 1 md5 Cisc392368270. The server at 1.1.1.1 is attempting to authenticate to the client at 1.1.1.2, however it is unable to do so. Which command is required to enable the client to accept the server’s authentication key?
Which service allows a user to export application usage and performance statistics with Cisco Application Visibility and Control?
Which feature requires a network discovery policy on the Cisco Firepower Next Generation Intrusion Prevention
System?
A company is experiencing exfiltration of credit card numbers that are not being stored on-premise. The
company needs to be able to protect sensitive data throughout the full environment. Which tool should be used
to accomplish this goal?
Which term describes when the Cisco Firepower downloads threat intelligence updates from Cisco Talos?
An attacker needs to perform reconnaissance on a target system to help gain access to it. The system has weak passwords, no encryption on the VPN links, and software bugs on the system’s applications. Which
vulnerability allows the attacker to see the passwords being transmitted in clear text?
Why is it important for the organization to have an endpoint patching strategy?
Which type of API is being used when a security application notifies a controller within a software-defined network architecture about a specific security threat?
A network engineer has configured a NTP server on a Cisco ASA. The Cisco ASA has IP reachability to the
NTP server and is not filtering any traffic. The show ntp association detail command indicates that the
configured NTP server is unsynchronized and has a stratum of 16. What is the cause of this issue?
What is the result of the ACME-Router(config)#login block-for 100 attempts 4 within 60 command on a Cisco IOS router?
Which public cloud provider supports the Cisco Next Generation Firewall Virtual?
What is the process In DevSecOps where all changes In the central code repository are merged and synchronized?
A Cisco ISE engineer configures Central Web Authentication (CWA) for wireless guest access and must have the guest endpoints redirect to the guest portal for authentication and authorization. While testing the policy, the engineer notices that the device is not redirected and instead gets full guest access. What must be done for the redirect to work?
An organization recently installed a Cisco WSA and would like to take advantage of the AVC engine to allow the organization to create a policy to control application specific activity. After enabling the AVC engine, what must be done to implement this?
Which action configures the IEEE 802.1X Flexible Authentication feature lo support Layer 3 authentication mechanisms?
What is the term for the concept of limiting communication between applications or containers on the same node?
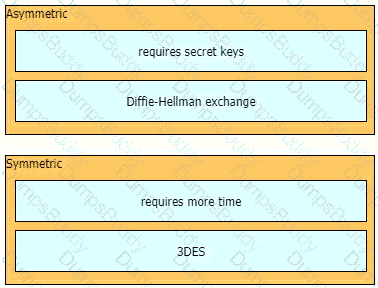
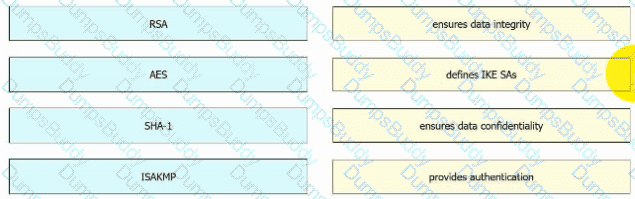
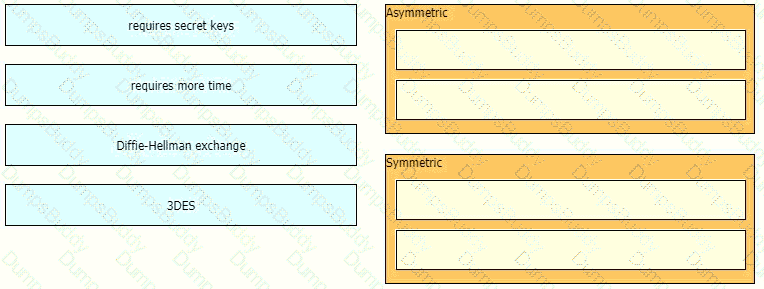
Drag and drop the descriptions from the left onto the encryption algorithms on the right.
What is the process of performing automated static and dynamic analysis of files against preloaded
behavioral indicators for threat analysis?
Which two statements about a Cisco WSA configured in Transparent mode are true? (Choose two)
An engineer wants to generate NetFlow records on traffic traversing the Cisco ASA. Which Cisco ASA
command must be used?
What is the purpose of the Trusted Automated exchange cyber threat intelligence industry standard?
An engineer needs to configure an access control policy rule to always send traffic for inspection without
using the default action. Which action should be configured for this rule?
An engineer has enabled LDAP accept queries on a listener. Malicious actors must be prevented from quickly
identifying all valid recipients. What must be done on the Cisco ESA to accomplish this goal?
Drag and drop the VPN functions from the left onto the description on the right.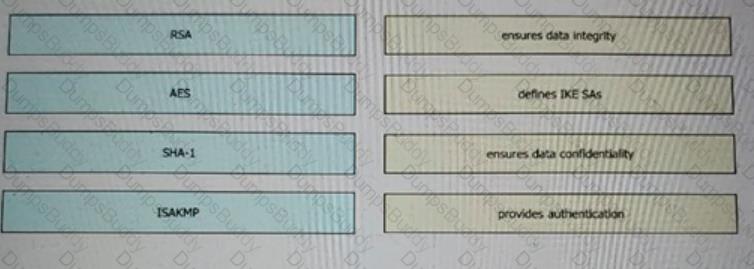
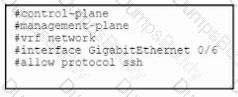
An administrator is implementing management plane protection and must configure an interface on a Cisco router to only terminate management packets that are destined for the router. Which set of IOS commands must be used to complete the implementation?
Which technology provides a combination of endpoint protection endpoint detection, and response?
Which interface mode does a Cisco Secure IPS device use to block suspicious traffic?
Which two behavioral patterns characterize a ping of death attack? (Choose two)
Which feature enables a Cisco ISR to use the default bypass list automatically for web filtering?
An engineer has been tasked with configuring a Cisco FTD to analyze protocol fields and detect anomalies in the traffic from industrial systems. What must be done to meet these requirements?
What is a functional difference between Cisco AMP for Endpoints and Cisco Umbrella Roaming Client?
A network security engineer must export packet captures from the Cisco FMC web browser while troubleshooting an issue. When navigating to the address https://
Refer to the exhibit.
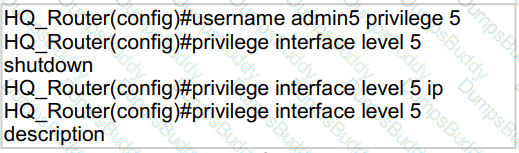
A network administrator configures command authorization for the admin5 user. What is the admin5 user able to do on HQ_Router after this configuration?
An organization plans to upgrade its current email security solutions, and an engineer must deploy Cisco Secure Email. The requirements for the upgrade are:
Implement Data Loss Prevention
Implement mail encryption
Integrate with an existing Cisco IronPort Secure Email Gateway solution
Which Cisco Secure Email license is needed to accomplish this task?
An organization is using Cisco Firepower and Cisco Meraki MX for network security and needs to centrally
manage cloud policies across these platforms. Which software should be used to accomplish this goal?
What are two facts about WSA HTTP proxy configuration with a PAC file? (Choose two.)
An engineer is deploying a Cisco Secure Email Gateway and must ensure it reaches the Cisco update servers to retrieve new rules. The engineer must now manually configure the Outbreak Filter rules on an AsyncOS for Cisco Secure Email Gateway. Only outdated rules must be replaced. Up-to-date rules must be retained. Which action must the engineer take next to complete the configuration?
A security engineer must add destinations into a destination list in Cisco Umbrella. What describes the application of these changes?
When network telemetry is implemented, what is important to be enabled across all network infrastructure devices to correlate different sources?
Which Cisco DNA Center RESTful PNP API adds and claims a device into a workflow?
What limits communication between applications or containers on the same node?
Which type of dashboard does Cisco DNA Center provide for complete control of the network?
In which two ways does the Cisco Advanced Phishing Protection solution protect users? (Choose two.)
What are two recommended approaches to stop DNS tunneling for data exfiltration and command and control call backs? (Choose two.)
Which two solutions help combat social engineering and phishing at the endpoint level? (Choose two.)
An engineer implements Cisco CloudLock to secure a Microsoft Office 365 application in the cloud. The engineer must configure protection for corporate files in case of any incidents. Which two actions must be taken to complete the implementation? (Choose two.)
Which CLI command is used to enable URL filtering support for shortened URLs on the Cisco ESA?
Which two features of Cisco Email Security can protect your organization against email threats? (Choose two)
Which network monitoring solution uses streams and pushes operational data to provide a near real-time view
of activity?
An engineer is configuring Cisco Umbrella and has an identity that references two different policies. Which action ensures that the policy that the identity must use takes precedence over the second one?
An MDM provides which two advantages to an organization with regards to device management? (Choose two)
An engineer is configuring device-hardening on a router in order to prevent credentials from being seen
if the router configuration was compromised. Which command should be used?
Which Cisco platform provides an agentless solution to provide visibility across the network including encrypted traffic analytics to detect malware in encrypted traffic without the need for decryption?
A network engineer must create an access control list on a Cisco Adaptive Security Appliance firewall. The access control list must permit HTTP traffic to the internet from the organization's inside network 192.168.1.0/24. Which IOS command must oe used to create the access control list?
What provides visibility and awareness into what is currently occurring on the network?
What are two characteristics of the RESTful architecture used within Cisco DNA Center? (Choose two.)
When planning a VPN deployment, for which reason does an engineer opt for an active/active FlexVPN
configuration as opposed to DMVPN?
Refer to the exhibit.

An engineer configured wired 802.1x on the network and is unable to get a laptop to authenticate. Which port configuration is missing?
An organization has a requirement to collect full metadata information about the traffic going through their AWS cloud services They want to use this information for behavior analytics and statistics Which two actions must be taken to implement this requirement? (Choose two.)
An engineer is trying to decide whether to use Cisco Umbrella, Cisco CloudLock, Cisco Stealthwatch, or Cisco AppDynamics Cloud Monitoring for visibility into data transfers as well as protection against data exfiltration Which solution best meets these requirements?
An organization has DHCP servers set up to allocate IP addresses to clients on the LAN. What must be done to ensure the LAN switches prevent malicious DHCP traffic while also distributing IP addresses to the correct endpoints?
When choosing an algorithm to us, what should be considered about Diffie Hellman and RSA for key
establishment?
Which two deployment modes does the Cisco ASA FirePower module support? (Choose two)
Which posture assessment requirement provides options to the client for remediation and requires the
remediation within a certain timeframe?
Which two commands are required when configuring a flow-export action on a Cisco ASA? (Choose two.)
An organization wants to improve its cybersecurity processes and to add intelligence to its data The organization wants to utilize the most current intelligence data for URL filtering, reputations, and vulnerability information that can be integrated with the Cisco FTD and Cisco WSA What must be done to accomplish these objectives?
Which type of data exfiltration technique encodes data in outbound DNS requests to specific servers
and can be stopped by Cisco Umbrella?
Which solution combines Cisco IOS and IOS XE components to enable administrators to recognize
applications, collect and send network metrics to Cisco Prime and other third-party management tools, and prioritize application traffic?
How does Cisco Umbrella protect clients when they operate outside of the corporate network?
Which two capabilities of Integration APIs are utilized with Cisco DNA center? (Choose two)
Which two tasks allow NetFlow on a Cisco ASA 5500 Series firewall? (Choose two)
v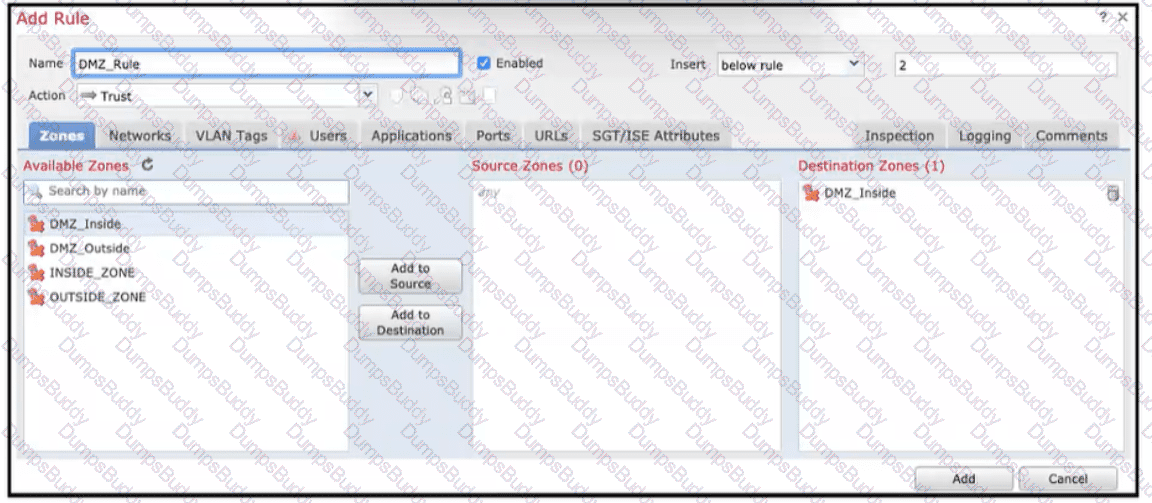
Refer to the exhibit When configuring this access control rule in Cisco FMC, what happens with the traffic destined to the DMZjnside zone once the configuration is deployed?
Which product allows Cisco FMC to push security intelligence observable to its sensors from other products?
What must be configured on Cisco Secure Endpoint to create a custom detection tile list to detect and quarantine future files?
A network administrator has configured TACACS on a network device using the key Cisc0467380030 tor authentication purposes. However, users are unable to authenticate. TACACS server is reachable, but authentication is tailing. Which configuration step must the administrator complete?
A network administrator is configuring SNMPv3 on a new router. The users have already been created;
however, an additional configuration is needed to facilitate access to the SNMP views. What must the
administrator do to accomplish this?
Which Cisco solution extends network visibility, threat detection, and analytics to public cloud environments?