350-501 Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR) Questions and Answers
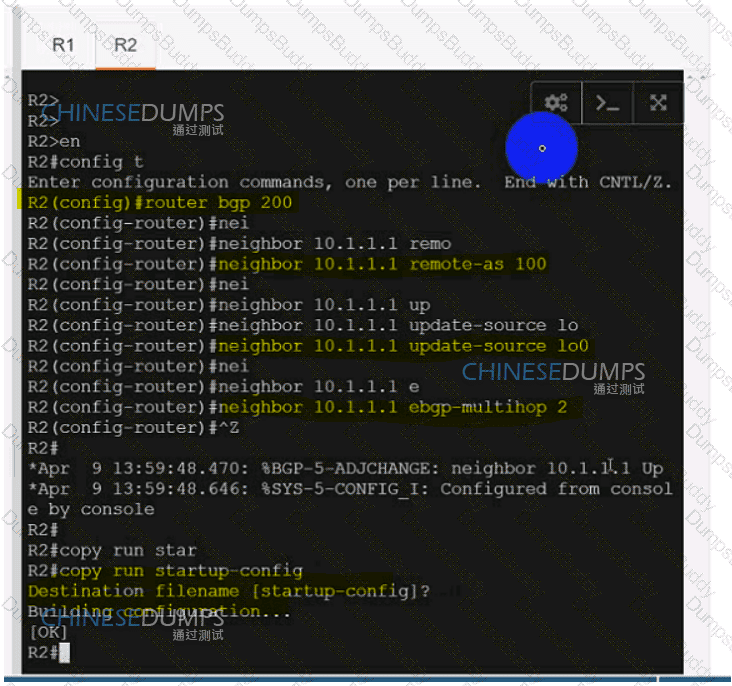
How does Inter-AS Option-A function when two PE routers in different autonomous systems are directly connected?
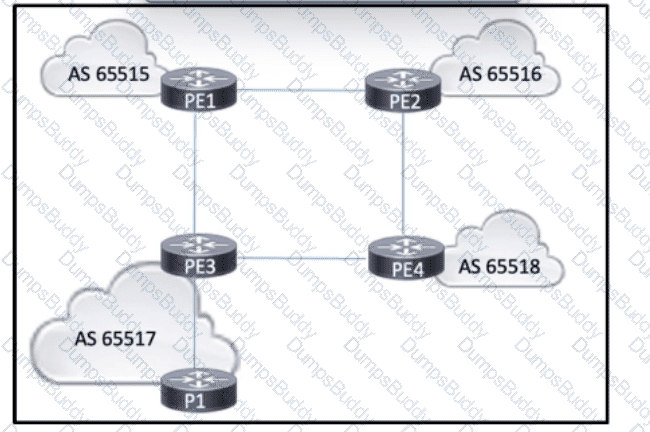
Refer to the exhibit. AS 65517 is running OSPF within the core. BGP is running between all four autonomous systems, interconnecting several ISPs that provide intranet and extranet services. All of the PE routers are connected, and eBGP peering relationships have been established. A network engineer also configured an iBGP peering between PE3 and P1, and the peering is up. However, P1 cannot reach routes outside of AS 65517. Which action must the engineer take so that P1 reaches external routes?)
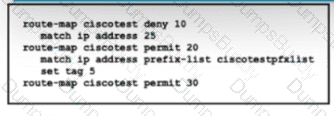
Refer to the exhibit. A client wants to filter routes to a BGP peer to limit access to restricted areas within the network. The engineer configures the route map ciscotest to filter routes from the BGP neighbor. The engineer also sets a tag that will be used for QoS in the future. Which task must be performed to complete the Implementation?
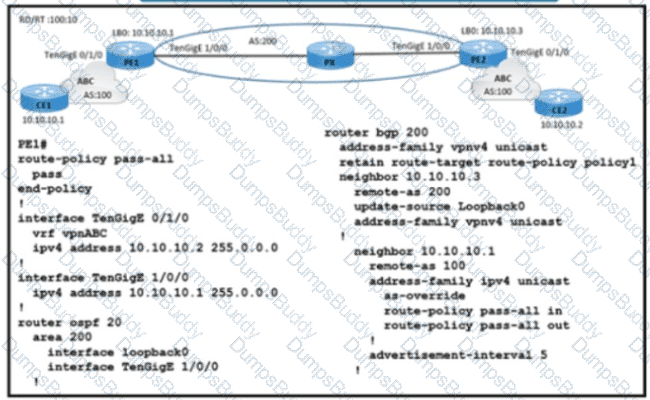
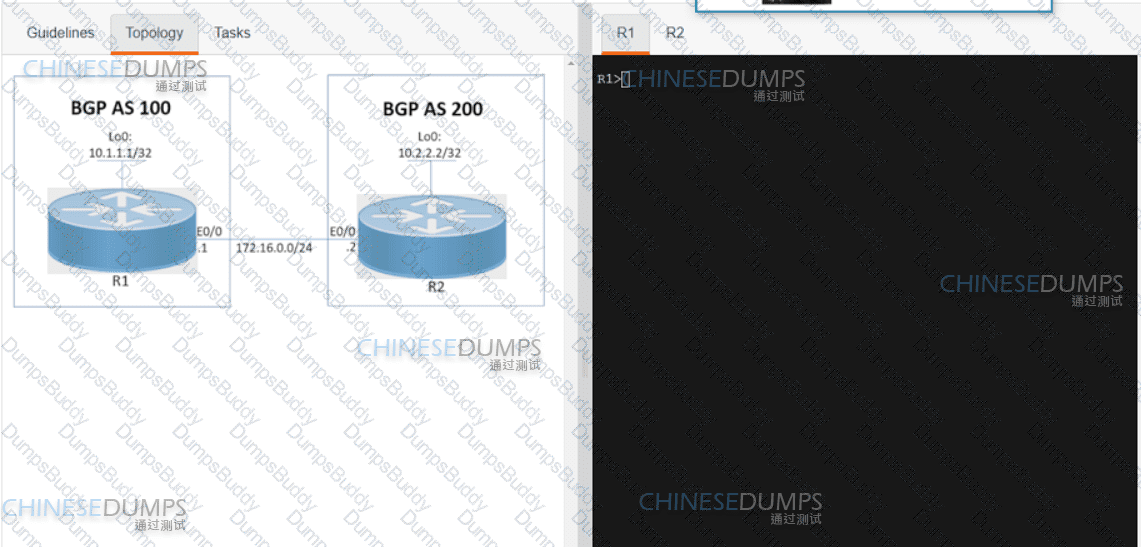
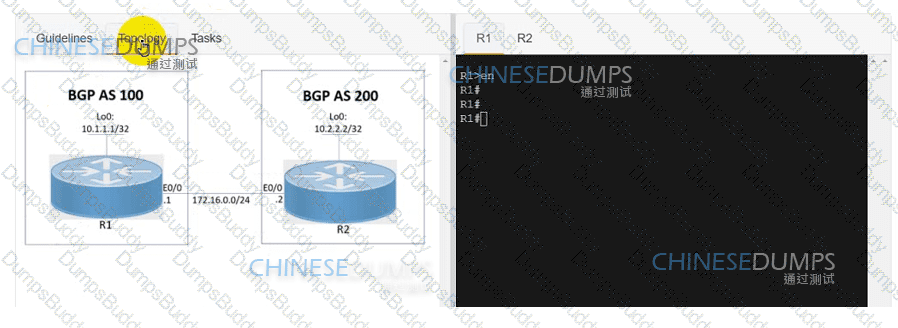
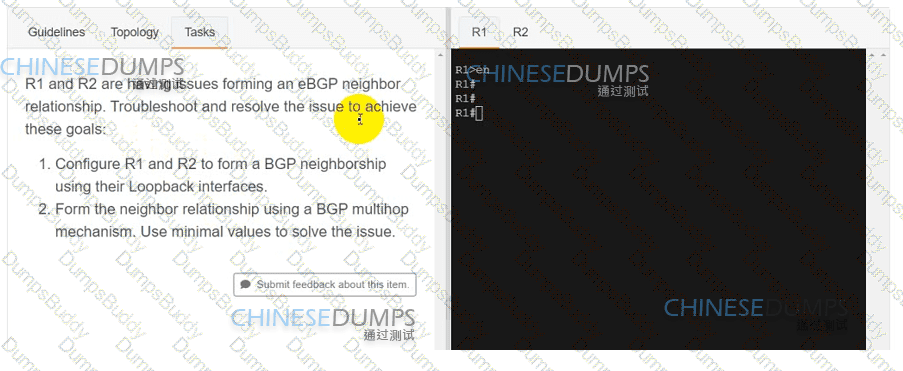
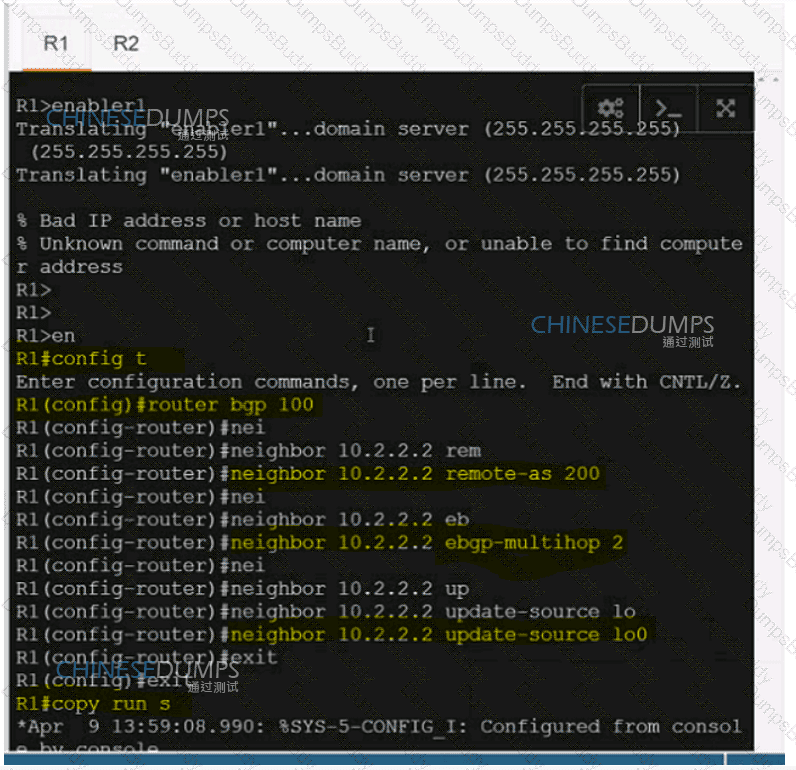
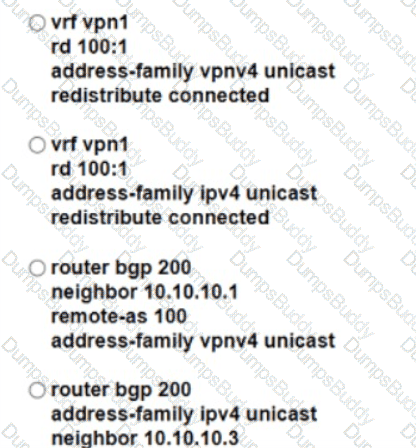
Refer to the exhibit. A service provider engineer Is configuring the connection between CE1 and CE2. AS 200 of the service provider and AS 100 of enterprise ABC should connect using BGP. The engineer already completed the configuration of VRF RT 100:10 of enterprise ABC. Which configuration must the engineer apply on PE1 to meet the requirement?
Refer to the exhibit.
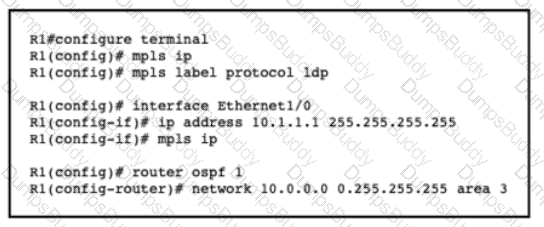
A network engineer is configuring MPLS LDP synchronization on router R1. Which additional configuration must an engineer apply to R1 so that it will synchronize to OSPF process 1?
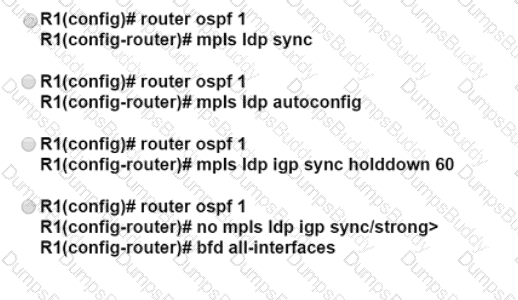
Refer to the exhibit:
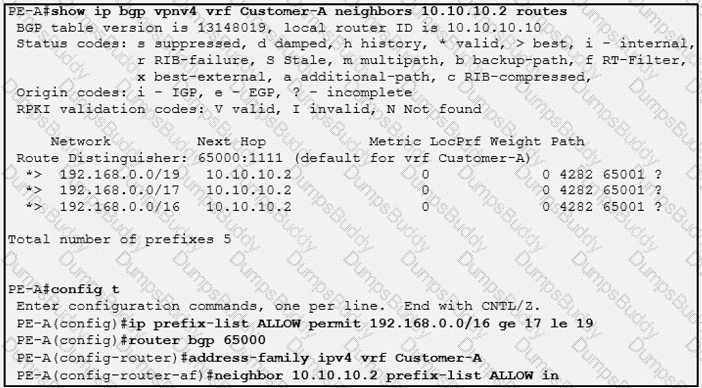
Which three outcomes occur if the prefix list is added to the neighbor? (Choose three)

Refer to the exhibit. A large organization is merging the network assets of a recently acquired competitor with one of its own satellite offices in the same geographic area. The newly acquired network is running different routing protocol than the company's primary network. As part of the merger a network engineer implemented this route map Which task must the engineer perform to complete the Implementation?
Refer to the exhibit.
A Cisco engineer is implementing gRPC dial-out on an ASR. Receiver 192.168 1.1 will be assigned one of the subscriptions, and it will manage the ASR. Which command is needed to complete the router configuration?
Refer to the exhibit.
An administrator working for large ISP must connect its two POP sites to provide internet connectivity to its customers. Which configuration must the administrator perform to establish an iBGP session between routers PE1 on POP site 1 and PE2 on POP site 2?
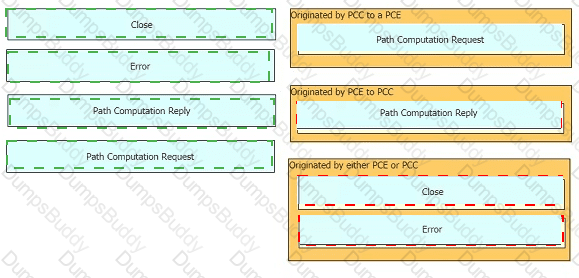
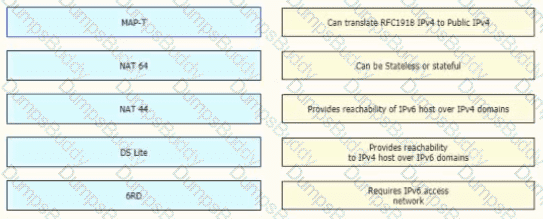
Drag and drop the message types from the left onto the target field of the message originator on the right.
Refer to the exhibit.
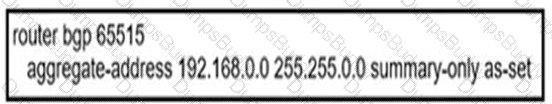
An engineer configured BGP summarization on a customer's network. Which route is advertised to BGP peers?
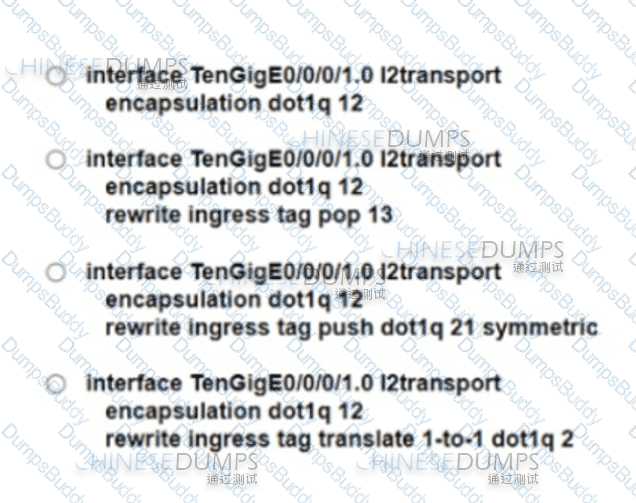
A mod-size service provider uses L2VPN as its standard for connectivity between offices. A small company wants the service provider to connect the company’s two sites across the service provider core. To meet service requirements, the service provider must extend the layer 2 domain between the company’s two locations. Which configuration must the engineer apply to implement an attachment circuit between the two sites using a VLAN tag of 12?
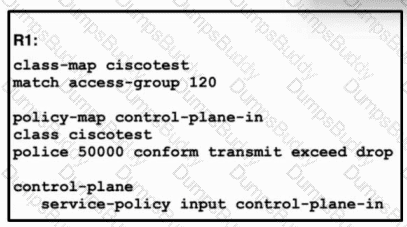
Refer to the exhibit. A network engineer installed router R1 as the new core router and must secure the control plane. The configuration has been applied, and now the engineer is creating ACL 120. Only hosts 192.168.1.1 and 192.168.2.2 should be allowed to access the router using Telnet. All other hosts should be rate-limited, with excess traffic dropped. Which configuration accomplishes this goal?
Refer To the exhibit.
Which BGP attribute should be manipulated to have CE1 use PE1 as the primary path to the Internet?
Which two features will be used when defining SR-TE explicit path hops if the devices are using IP unnumbered interfaces? (Choose two.)
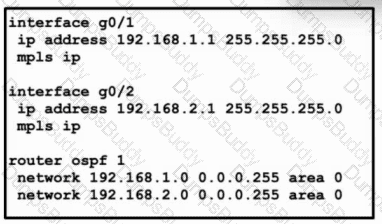
Refer to the exhibit. This enterprise configured MPLS within its network to connect offices that span different geographic areas, with LDP running between connected neighbors. At each office, including headquarters, the networks are running OSPF with a similar configuration.
Which additional action must the engineering team take to support a more reliable connection between MPLS and OSPF?
In MPLS traffic engineering, which FRR operation swaps the label and pushes the backup label?
When configuring traffic engineering tunnels in Cisco MPLS core network, you see the traffic is not taking the expected path in the core.
Which command do you use to quickly check path of a TE tunnel?
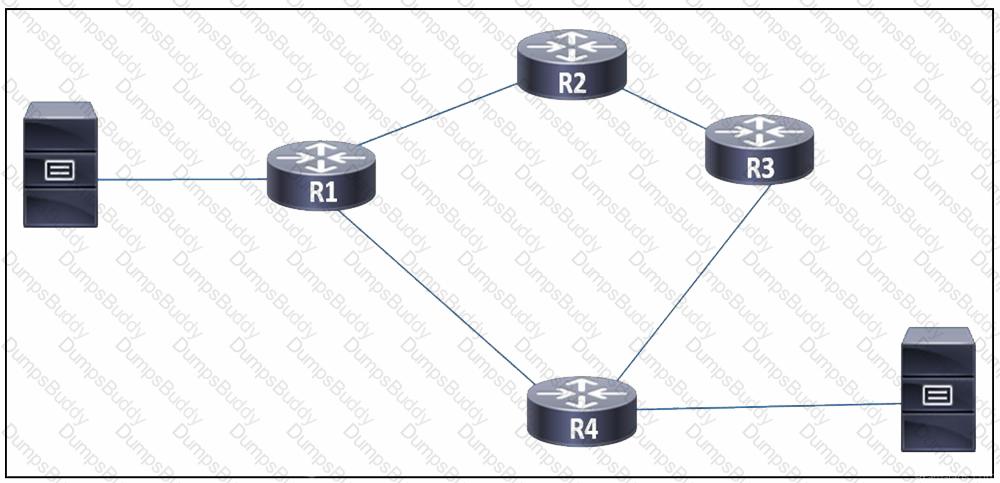
Refer to the exhibit. A network engineer observed congestion between routers R1 and R4, which are connected on a point-to-point link. Two servers that reside on networks on R1 and R4 generate heavy traffic between them with most traffic going from R4 to R1. To improve overall performance, the engineer wants to drop inbound packets that exceed a configured threshold, without disrupting traffic that passes from R4 to R3. Which action must the engineer take to resolve the issue?
Refer to the exhibit.
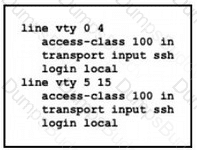
An engineer has started to configure a router for secure remote access as shown. All users who require network access need to be authenticated by the SSH Protocol.Which two actions must the engineer implement to complete the SSH configuration? (Choose two.)
Which is the benefit of implementing model-driven telemetry in a service provider environment?
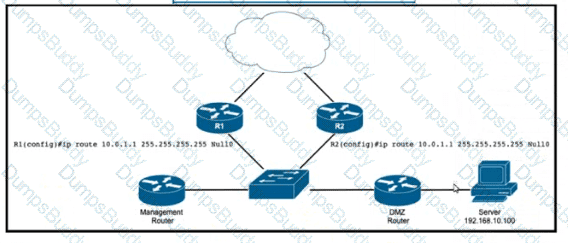

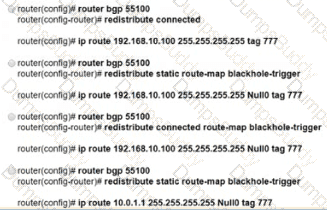
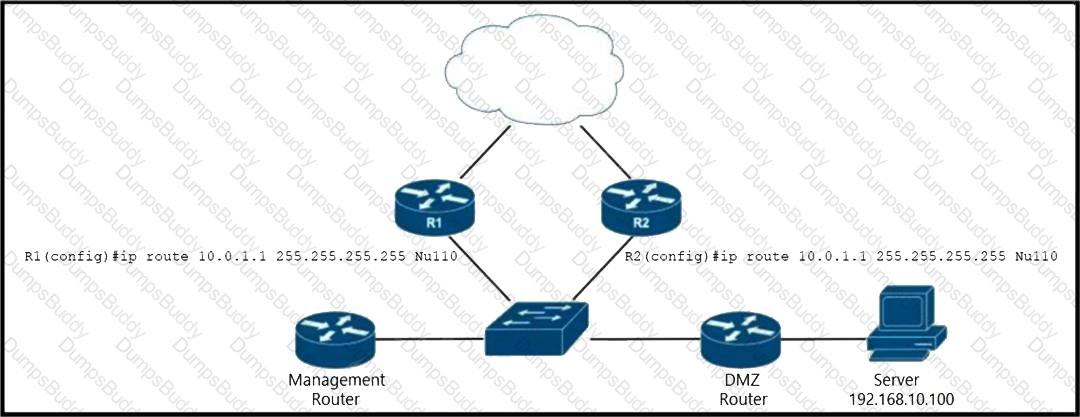
Refer to the exhibit. EIGRP a running across the core lo exchange Internal routes, and each router maintains 6GP adjacency with the other routers on the network. An operator has configured static routes on the edge routers R1 and R2 for IP address 10.0.1.1. which is used as a black hole route as shown. Which configuration should the operator Implement to me management rouler to create a route map that will redistribute lagged static routes into BGP and create a static route to blackhole traffic with tag 777 that Is destined to server at 192.168.10.100?
A company uses PIM-SM multicast with IGMPv2 to stream training videos from a server in one network to hosts in a different network. As the company has grown, the networking team decided to implement SSM to improve efficiency for multicast within Layer 2. Which action must the team take to begin the process?
Refer to the exhibit:
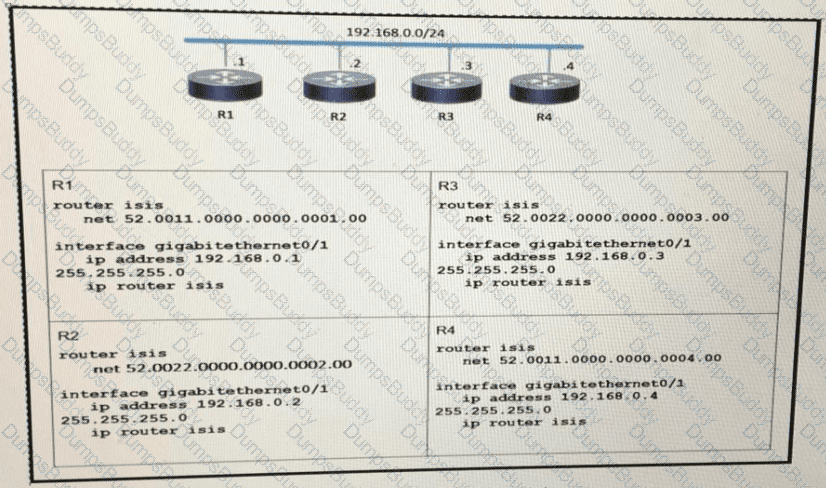
Which two statements about the ISIS topology are true? (Choose two.)
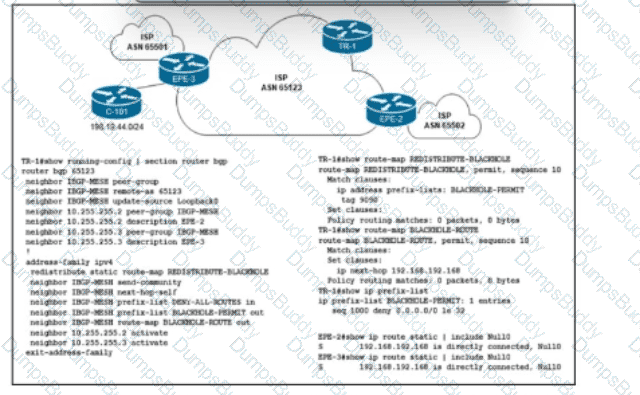
Refer to the exhibit. Customer C-101 in ASN 65123 requested that the ISP blackholes a host route 198.19.44.195, to which the customer is receiving a significant amount of malicious traffic. Which configuration must the network engineer implement on the trigger router TR-1 to fulfill the request without affecting other IP destinations in the customer's block?
Refer to the exhibit.
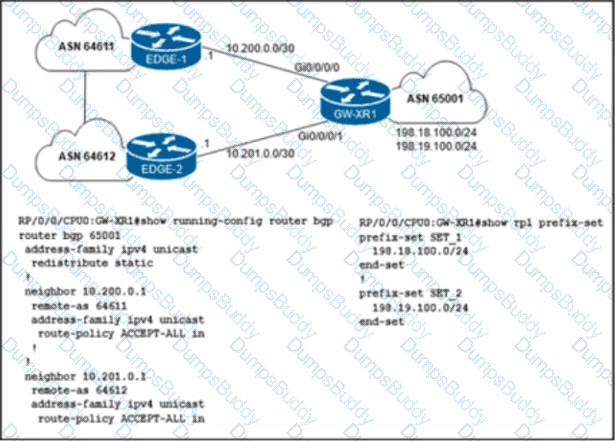
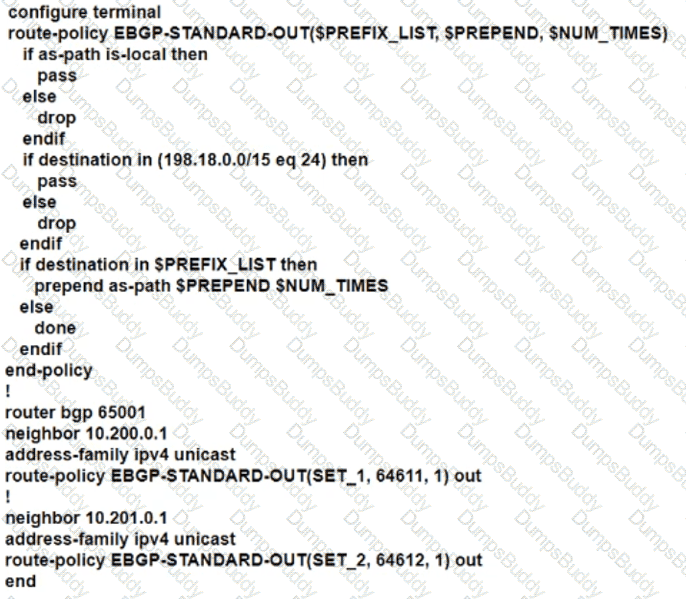
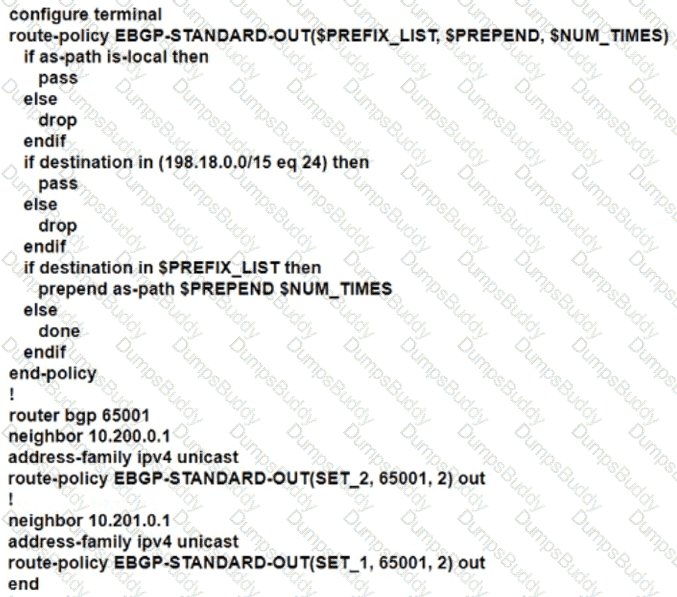
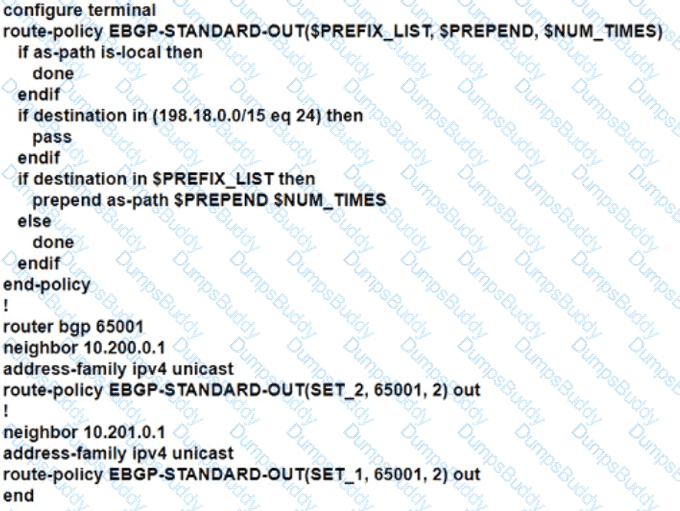
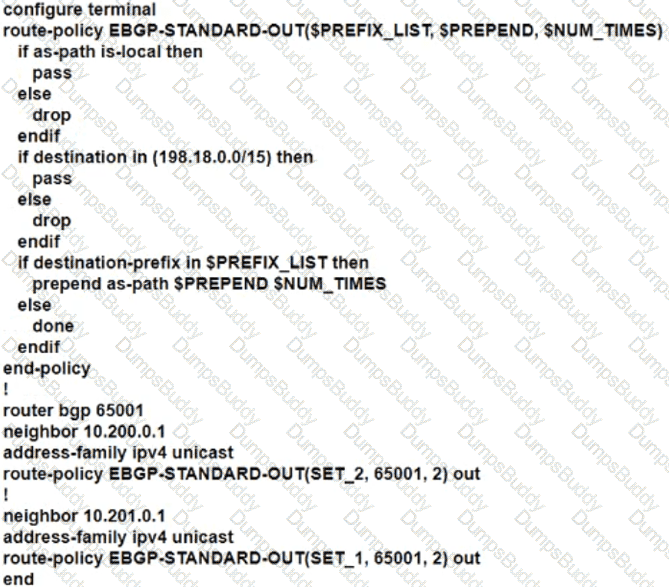
The network engineer who manages ASN 65001 must configure a BGP routing policy on GW-XR1 with these requirements:
• Advertise locally-originated routes and /24 prefixes assigned within the 198.18.0.0/15 range. All other prefixes must be dropped.
• Reachability to 198.18.100.0/24 must be preferred via the EDGE-1 connection.
• Reachability to 198.19.100.0/24 must be preferred via the EDGE-2 connection.
Which configuration must the network engineer implement on GW-XR1?
Which set of facts must the network architect consider when deciding whether to implement SaltStack or Chef?
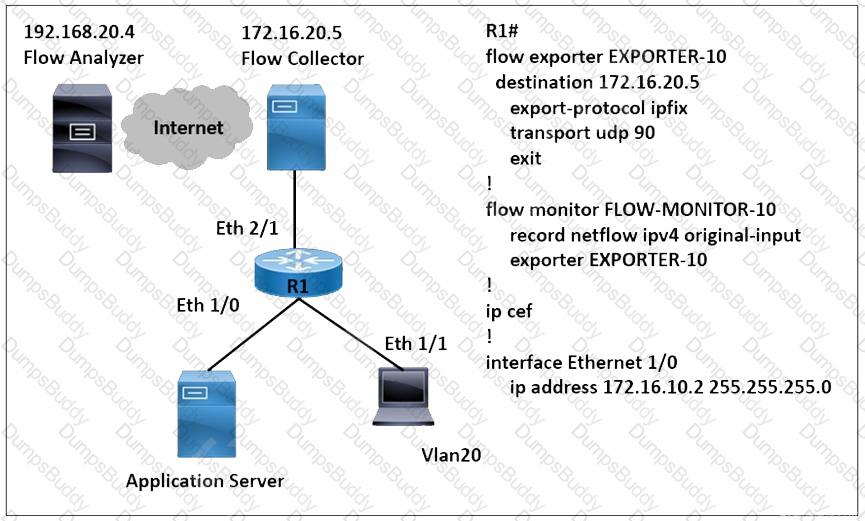
Refer to the exhibit. A network engineer wants to monitor traffic from the application server and send the output to the external monitoring device at 172.16.20.5. Application server traffic should pass through the R1 Eth2/1 interface for further analysis after it is monitored. Which configuration must be applied on the R1 router?
A network operator working for a telecommunication company with an employee Id: 4065 96080 it trying to implement BFD configuration on an existing network of Cisco devices Which task must the engineer perform to enable BFD on the interfaces?
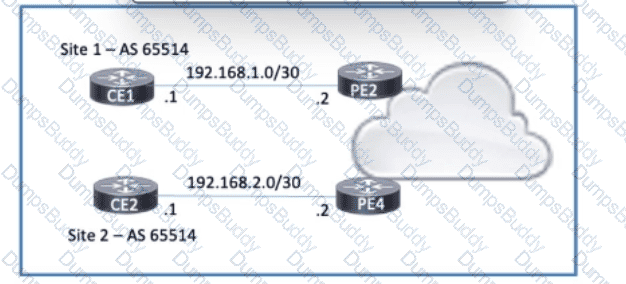
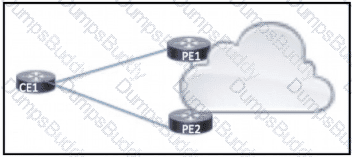
Refer to the exhibit. Company A has two offices that communicate via a service provider in AS 65516. CE1 and CE2 provide connections to the service provider from site 1 and site 2 respectively. Both customer sites use BGP as the PE-CE routing protocol. Which configuration must the engineer apply to ensure that traffic passes between the two sites?
Which configuration mode do you use to apply the mpls Idp graceful-restart command in IOS XE Software? MPLS
A network engineer has configured TE tunnels in the MPLS provider core. Which two steps ensure traffic traverse? (Choose two.)
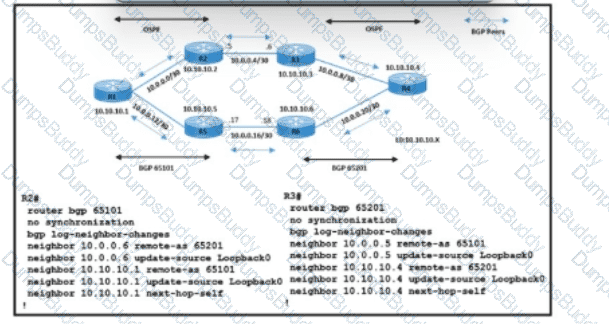
Refer to the exhibit. A network operations team is implementing eBGP on the service provider network. Data traffic between routers R1 and R4 must use the R2-R3 link, which connects AS 65101 and AS65201. iBGP sessions with adjacent routers are up on 10.10.10.1 and 10.10.10.4. The team is now updating the configuration for eBGP peers on routers R2 and R3. Which action must be taken to meet the requirements?
What is a primary benefit of IPoATM or MPLS over ATM backbone service provider networks?
Refer to the exhibit:
You are configuring an administrative domain implement so that devices can dynamically learn the RP?
A network engineer is configuring RIP as the routing protocol between multiple PEs and CEs. The engineer must avoid advertising the same routes back to their sources. Which action should be performed on the routers to accomplish this task?
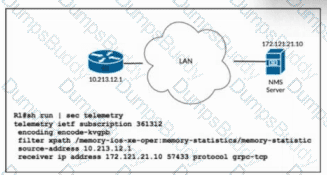
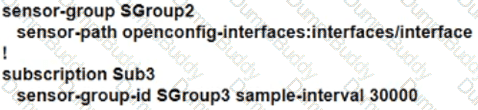
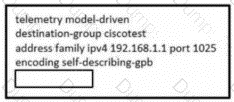
Refer to the exhibit. The network administrator is configuring memory telemetry on router R1. Only kvGPB encoding and gRPC protocol based on RFC 7540 should be used. Updates should be sent every two seconds. Which two commands must the administrator apply to complete the task? (Choose two.)
You are creating new Cisco MPLS TE tunnels. Which type of RSVP message does the headend router send to reserve bandwidth on the path to the tunnel’s router?
Drag and drop the functionalities from the left onto the target fields on the right.
Refer to the exhibit. After a networking team configured this MPLS topology, the supervisor wants to view MPLS labels to verify the path that packets take from router R1 to router R7 The team already Issued an ICMP ping to verify connectivity between the devices. Which task must the team perform to allow the supervisor to view the label switch path?
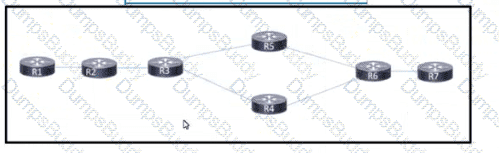
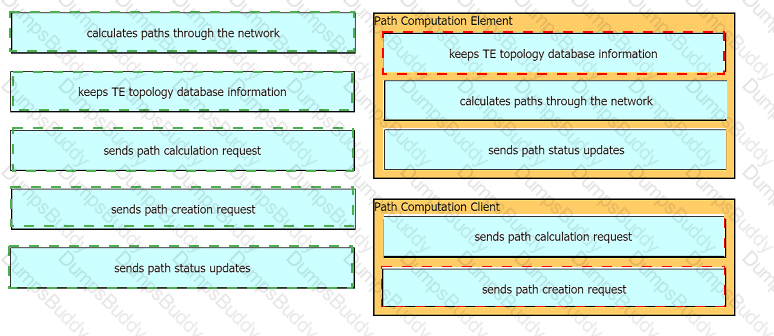
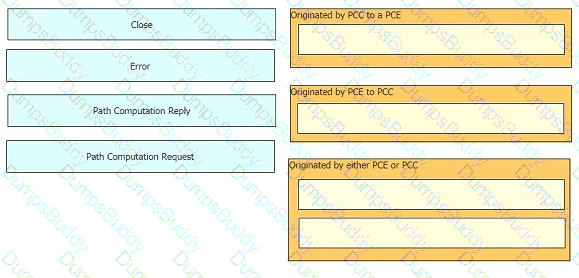
Drag and drop the functions from the left onto the Path Computation Element Protocol roles on the right.
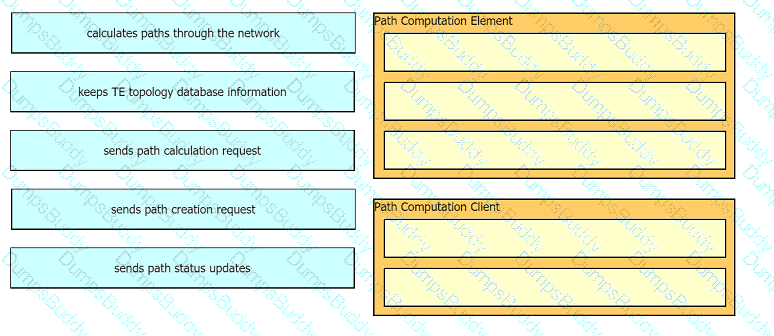
Company A must increase throughput between two non-IEEE 802.3ad switches located in the access and distribution layers. A network engineer must create a link group with the same speed and duplex. The STP protocol must not block any of the group ports. Which action completes the implementation?
An engineer is configuring IEEE 802.1 ad on the access port on a new Cisco router. The access port handles traffic from multiple customer VLANs, and it is expected to mark all customer traffic to the same VLAN without dropping any traffic. Which configuration must the engineer apply?
A)

B)

C)

D)

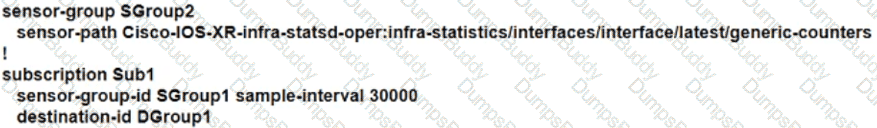
A network engineer implements OSPF on the network and then notices frequent faults in traffic between two routers, particularly on interface TenGigE 0/0/1. The engineer decides to configure NetFlow to monitor the issue. Which configuration must the engineer apply to the router?
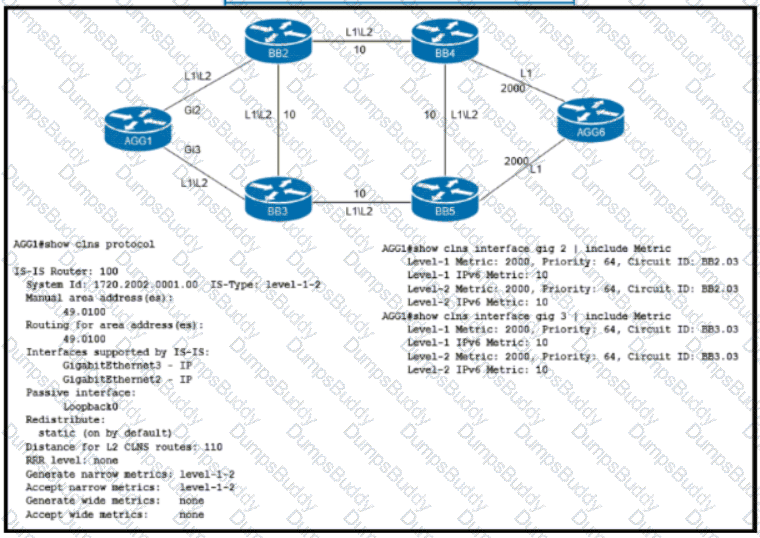
Refer to the exhibit. An engineer is configuring IS-IS on ISP network. Which IS-IS configuration must an engineer implement on router AGG1 so that it establishes connectivity to router AGG6 via the BB3 core router?
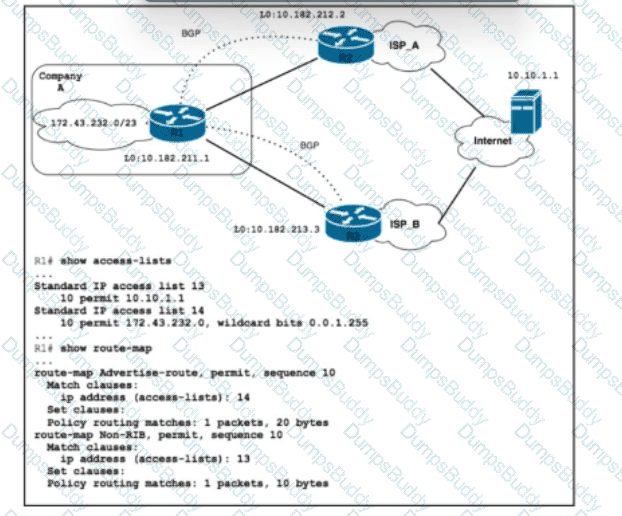
Refer to the exhibit. Company A is connected to multiple upstream ISPs, with ISP_A serving as the primary upstream ISP. The company A subnet 172.43.232.0 should be announced to the secondary ISP_B only when the FTP server with IP address 10.10.1.1 is not accessible via the primary ISP. Which configuration must be applied on R1?
Which two tasks must an engineer perform when implementing LDP NSF on the network? (Choose two.)
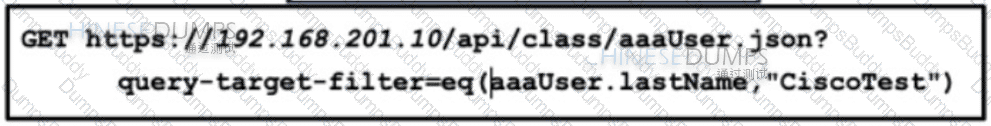
Refer to the exhibit. An engineer configured several network devices to run REST APIs. After testing, the organization plans to use REST APIs throughout the network to manage the network more efficiently. What is the effect if this script?
A new PE router is configured to run OSPF as an IGP with LDP on all interfaces. The engineer is trying to prevent black holes after convergence when the PERSON device loses an LDP session with other PE routers. Which action must the engineer take to implement LDP session protection on a new PE router?
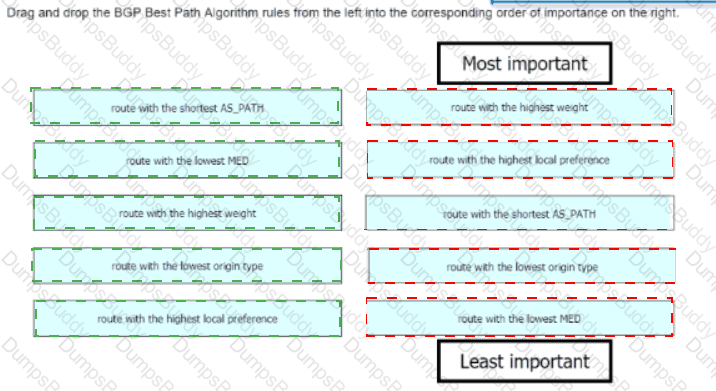
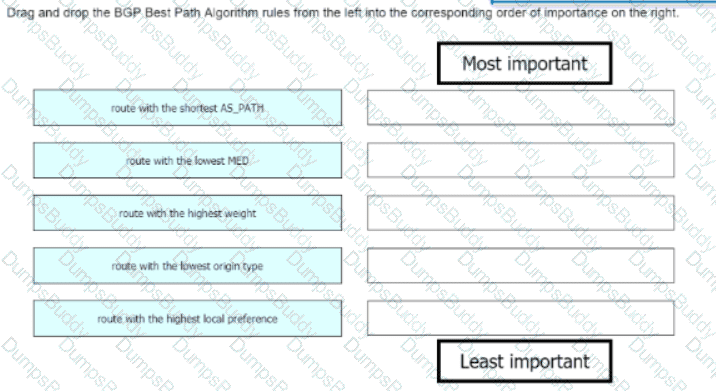
Drag and drop the BGP Best Path Algorithm rules from the left into the corresponding order of importance on the right.
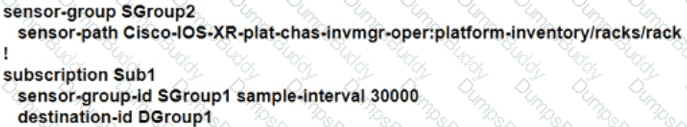
Refer to the exhibit. An organization s network recently experienced several significant outages due to device failures. The network administrator just moved the network devices to a new central data center, and packets are switched using labels. The administrator Is now implementing NSF on the network to reduce potential risk factors in the event of another outage. Which task must the administrator perform on each router as part of the process?
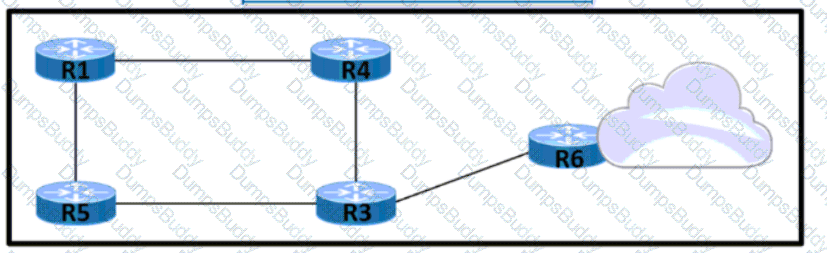
Refer to the exhibit:
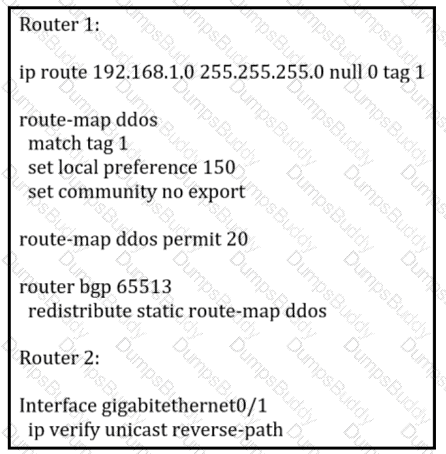
An engineer is preparing to implement data plane security configuration.
Which statement about this configuration is true?
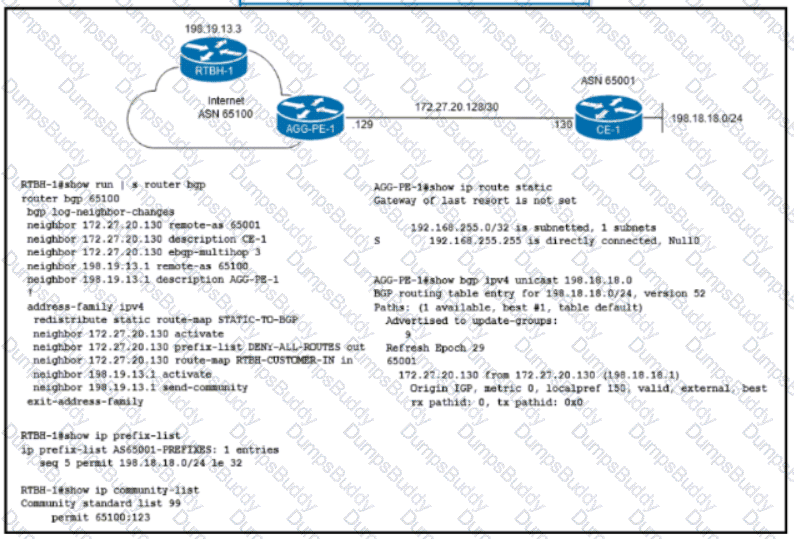
Refer to the exhibit. ISP ASN 65100 provides Internet services to router CE-1 and receives customer prefix 198.18.18.0/24 via eBGP. An administrator for the ISP is now provisioning RTBH services to provide on-demand data-plane security for the customer’s IP space. Which route-map configuration must the administrator apply to router RTBH-1 to complete the implementation of RTBH services to CE-1?
While implementing TTL security, an engineer issues the PE(config-router-af)#neighbor 2.2.2.2 ttl-security hops 2 command. After issuing this command, which BGP packets does the PE accept?
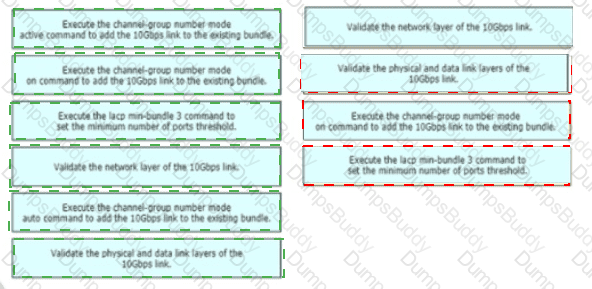
A network engineer is adding 10Gbps link to an existing 2X1Gbps LACP-based LAG to augment its capacity. Network standards require a bundle interface to be take out of service if one of its member links does down, and the new link must be added with minimal impact to the production network. Drag and drop the tasks that the engineer must perform from the left into the sequence on the right. Not all options are used.

Which programmable API allows the service provider to plan and optimize the automation of network operations and achieve closed-loop operations?
Refer to me exhibit.
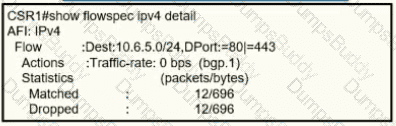
A network operator recently configured BGP FlowSpec for me internal IT network What will be inferred from the configuration deployed on me network?
A network engineer Is implementing a QoS policy for outbound management traffic classification and marking on a CPE device with these requirements:
• Management protocols must be marked with DSCP AF class 2 w4h low drop probability.
• Monitoring protocols must be marked with DSCP AF class 1 with low drop probability.
• All remaining traffic must be marked with a DSCP value of 0.
Which configuration must the engineer implement to satisfy the requirements?
A)

B)

C)

D)

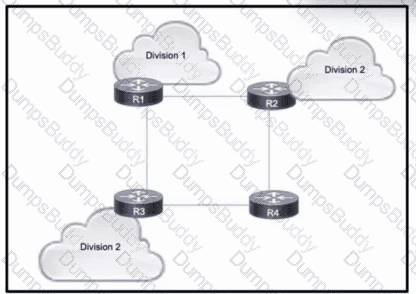
Refer to the exhibit. A large enterprise is migrating its network to use MPLS VPNs between different business divisions. Within the core, routes are shared between the routers using OSPF, and each connected link maintains an MPLS neighbor relationship.
Which action must the migration team take so that LDP neighbor relationships are maintained if a directly-connected link goes down?
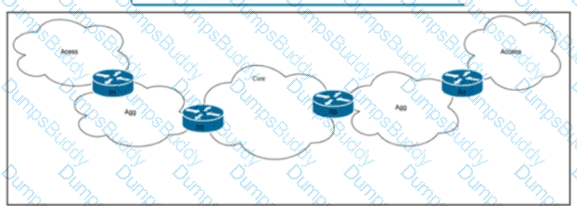
Refer to the exhibit. Tier 1 ISP A purchased several Tier 2 ISPs to increase their customer base and provide more regional coverage. ISP A plans to implement MPLS services in the access layer, with scalability up to 100.000 devices In one packet network and service recovery up to 50 ms. The network architect decided to use different independent IGP and LDP domains and interconnect LSPs that are based on RFC 3107. Which two actions must the network engineer perform to meet the requirements? (Choose two.)
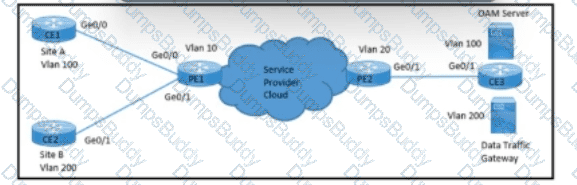
Refer to the exhibit. A network engineer with an employee ID: 5086:72:817 is configuring a connection to manage CE1 from the OAM server on VLAN 100. PE1 must push S-VLAN tag 10 toward PE2 while forwarding traffic from CE1 to the OAM server. PE1 must push S-VLAN tag 20 toward PE2 while forwarding traffic from CE2 to the data traffic gateway. Which configuration must the engineer implement on PE2?
An engineer is implementing IGMP with SSM on a multicampus network that supports video streaming. Which task must the engineer perform as part of the process?
Which action occurs during the traceback phase of the six-phase approach to service provider security?
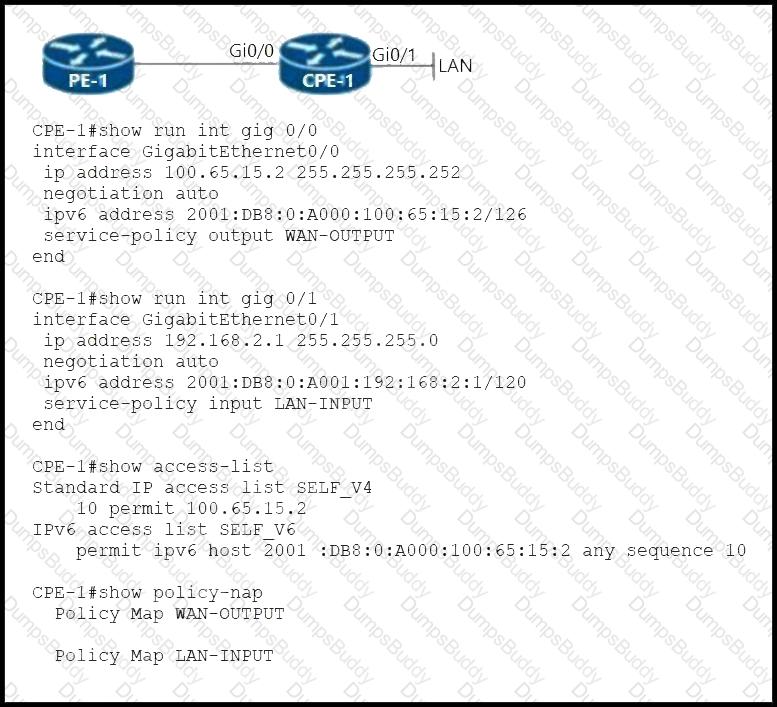
Refer to the exhibit. A network engineer configures CPE-1 for QoS with these requirements:
IPv4 and IPv6 traffic originated by the CPE-1 WAN IP address must be marked with DSCP CS3.
IPv4 LAN traffic must be marked with DSCP CS1.
IPv6 LAN traffic must be marked with DSCP default.
Which configuration must the engineer implement on CPE-1?
An engineer needs to implement QOS mechanism on customer's network as some applications going over the internet are slower than others are. Which two actions must the engineer perform when implementing traffic shaping on the network in order to accomplish this task? (Choose two)
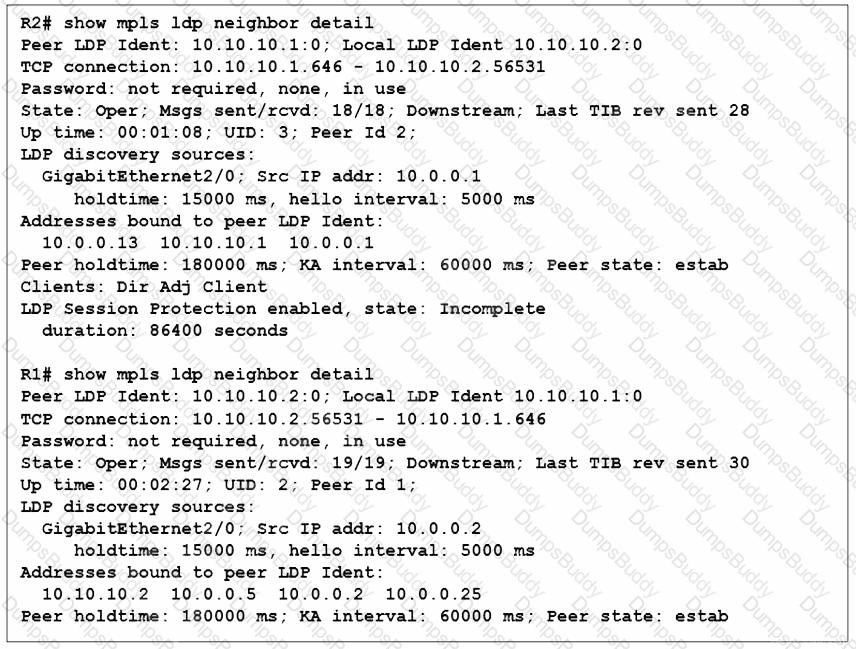
Refer to the exhibit. LDP peering between routers R1 and R2 is dropped when the link between R1 and R2 is taken offline. However, LDP peering between R2 and R3 stays up when the link between R2 and R3 is taken offline. Which action allows MPLS traffic forwarding to continue normally if the link between R1 and R2 goes down?
Refer to the exhibit:
Router R1 and its peer R2 reside on the same subnet in the network, If does it make connections to R27
Refer to the exhibit:

This configuration is being applied on an IOS XR router.
Which statement about this configuration is true?
router(config)# route-map blackhole-trigger
router(config-route-map)# match tag 777
router(config-route-map)# set ip next-hop 10.0.1.1
router(config-route-map)# set origin igp
router{config-route-map)# set community no-export
Refer to the exhibit. EIGRP is running across the core to exchange internal routes, and each router maintains iBGP adjacency with the other routers on the network. An operator has configured static routes on the edge routers R1 and R2 for IP address 10.0.1.1, which is used as a black hole route as shown. Which configuration should the operator implement to the management router to create a route map that will redistribute tagged static routes into BGP and create a static route to blackhole traffic with tag 777 that is destined to the server at 192.168.10.100?
Refer to the exhibit.
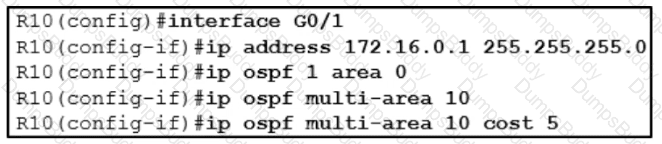
A network engineer is implementing OSPF multiarea. Which command on interface GO/1 resolves adjacency issues in the new area?
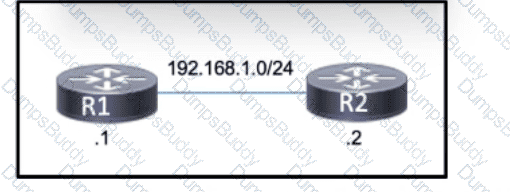
Refer to the exhibit. Routers R1 and R2 support traffic between multiple departments at a company's remote office and exchange routes using OSPF. The link between R1 and R2 has been providing inconsistent performance, particularly during times of peak usage. To help identify the cause, an engineer was asked to implement BFD to detect failures on the link. Which task must the engineer perform?
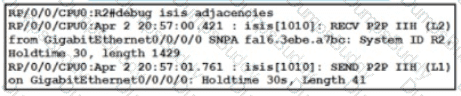
Refer to the exhibit. A network operator is attempting to configure an IS-IS adjacency between two routers, but the adjacency cannot be established. To troubleshoot the problem, the operator collects this debugging output. Which interface are misconfigured on these routers?

Refer to the exhibit:
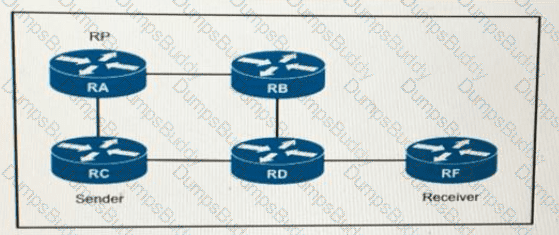
If router A is the RP, which PIM mode can you configure so that devices will send multicast traffic toward the RP?
A network engineer must enable the helper router to terminate the OSPF graceful restart process if it detects any changes in the LSA. Which command enables this feature?
Refer to the exhibit.
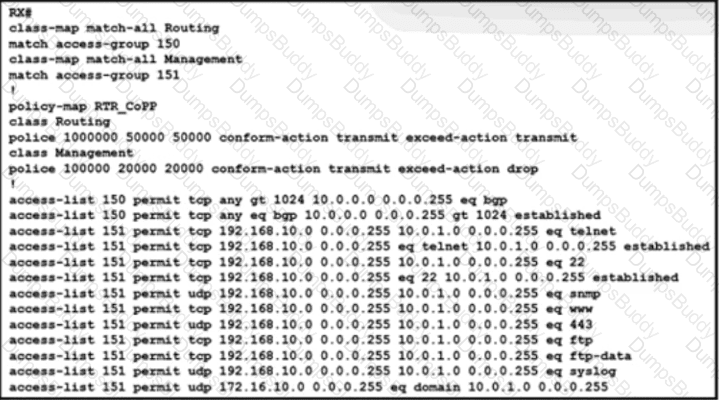
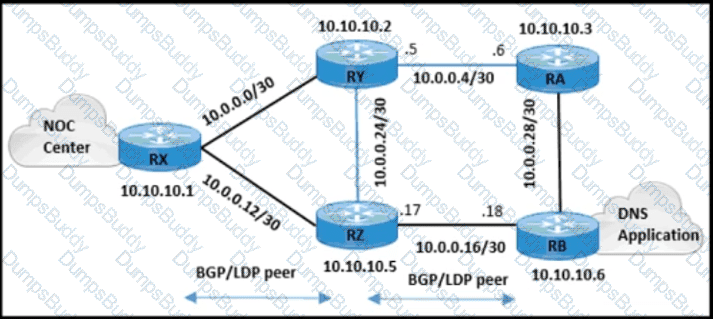
The engineering team wants to limit control traffic on router RX with the following IP address assignments:
• Accepted traffic for router: 10.0.0.0/24
• NOC users IP allocation: 192.168.10.0/24
Which additional configuration must be applied to RX to apply the policy for MSDP?
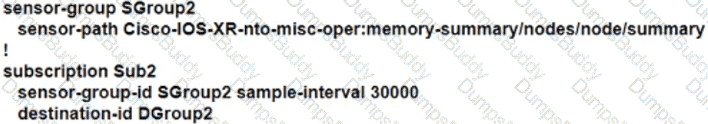
A service provider requires continuous real-time network monitoring to provide reliable SLAs to its customers. To satisfy this requirement, a network administrator is implementing gRPC dial out on an ASR with TLS. Receiver 192.168.10.2 will be assigned one of the subscriptions, and it will manage the ASR. Which configuration must the engineer apply to the router as part of the configuration process?
Refer to the exhibit:
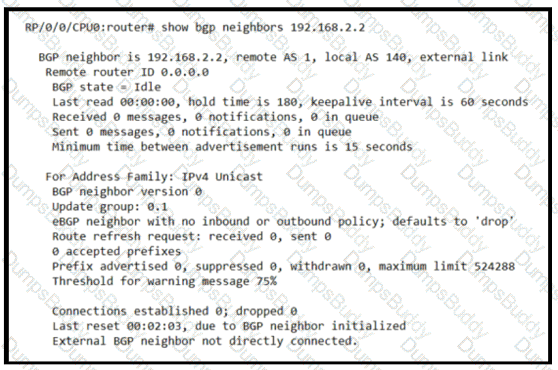
Based on the show/ command output, which result m true after BGP session is established?
You are configuring MPLS traffic-engineering tunnels in the core.
Which two ways exist for the tunnel path across the core? (Choose two )
Refer To the exhibit:

On R1, which output does the show isis neighbors command generate?
A)
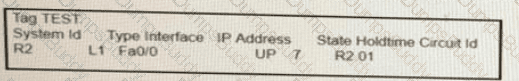
B)

C)
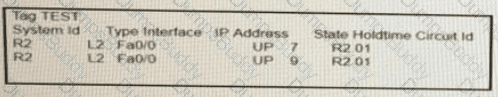
D)

Which MPLS design attribute can you use to provide Internet access to a major customer through a separate dedicated VPN?
Which additional configuration is required for NetFlow to provide traceback information?
Refer to the exhibit.
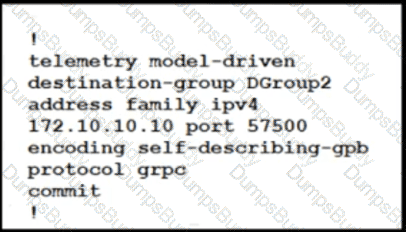
A network engineer at a large ISP Is configuring telemetry streams to monitor the health status of PE routers on the network using gRPC dial-out. The PE routers are located at several data centers in different physical locations, and they are using IS-IS and BGP for routing. Which additional configuration must the engineer implement on the PE routers to meet the goal?
How does TACACS+ facilitate secure connections for user access to network routers?
Refer to the exhibit.
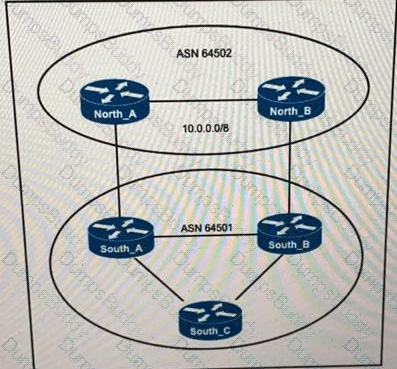
ASN 64501 currently reaches the networks under the 10.0.0.0/8 prefix via the North_B router, which is a slow backup link. The administrator of ASN 64502 wants traffic from ASN 64501 to 10.0.0.0/8 to travel via the primary link North_A. Which change to the network configuration accomplishes this task?
Which function does orchestrated fulfillment perform under the Cisco Network Services Orchestrator model?
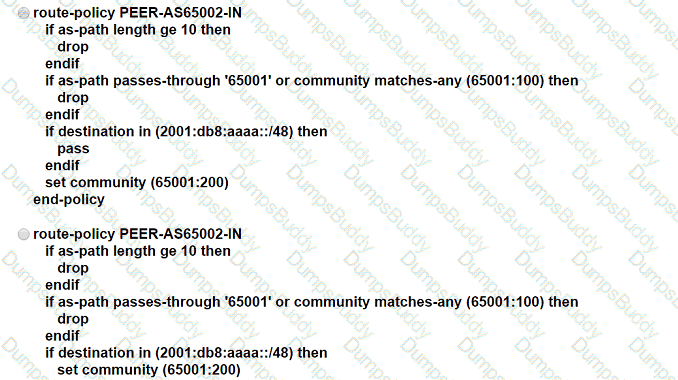
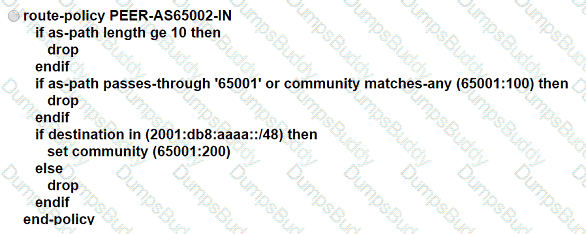
ASN 65001 is peering with ASN 65002 to exchange IPv6 BGP routes. All routes that originate in ASN 65001 have a standard community value of 65001:100, and ASN 65002 is allowed to advertise only 2001 :db8:aaaa::/48. An engineer needs to update the ASN 65001 route-filtering configuration to meet these conditions:
* Looped routes into ASN 65001 and routes that have traversed 10 or more ASNs must be denied.
* Routes accepted into ASN 65001 must be assigned a community value of 65001:200.
Which configuration must the engineer apply to the ASN 65001 border router?

Why is the keyword none needed when implementing management plane security using TACACS?
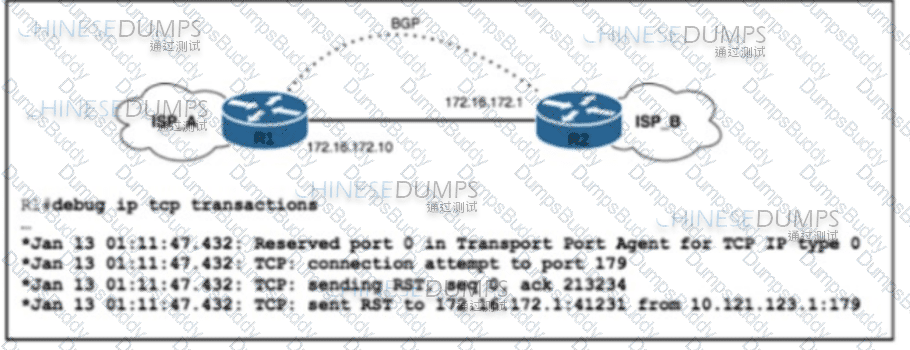
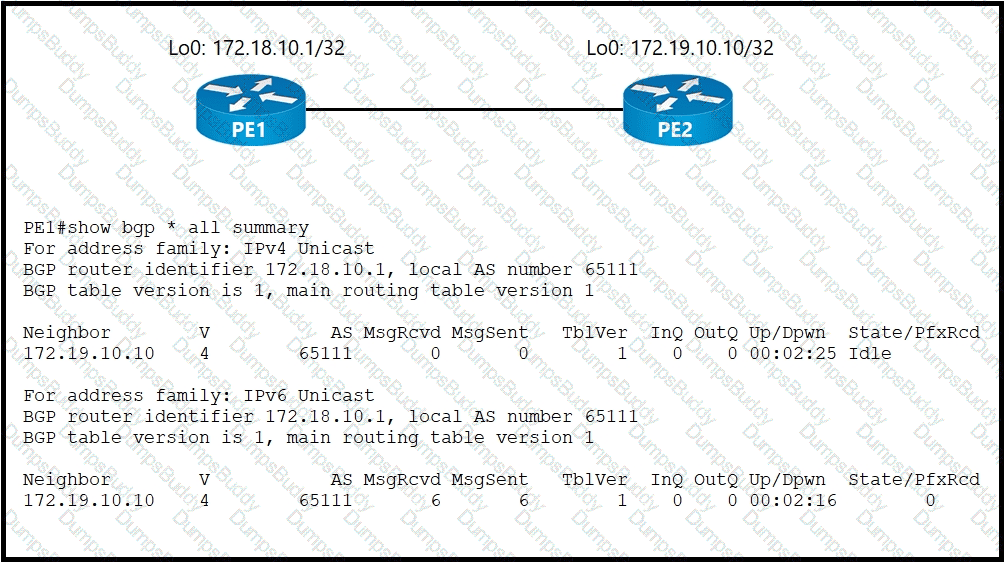
Refer to the exhibit. ISP_A and ISP_B use AS numbers 38321 and 16213 respectively. After a network engineer reloaded router R1, the BGP session with R2 failed to establish. The engineer confirmed BGP next-hop availability with a connectivity test between the router loopback addresses 10.121.123.2 and 10.121.123.1, as well as between interfaces Gi1/1 and Gi1/2. EBGP multihop has been configured on both routers. Which action must the engineer take to resolve the issue?
How can shared services in an MPLS Layer 3 VPN provide Internet access to the customers of a central service provider?
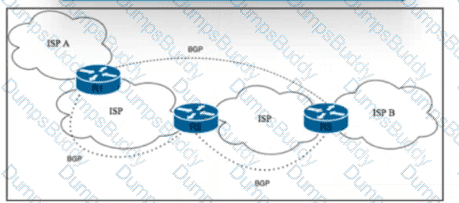
Refer to the exhibit. Tier 1 ISP A is connected to small Tier 3 ISP B. The EBGP routing protocol is used for route exchange. The networking team at ISP A noticed the flapping of BGP sessions with ISP B. The team decides to Improve stability on the network by suppressing the subnet for 30 minutes when a session begins to flap. Which action must the team perform to meet this goal?
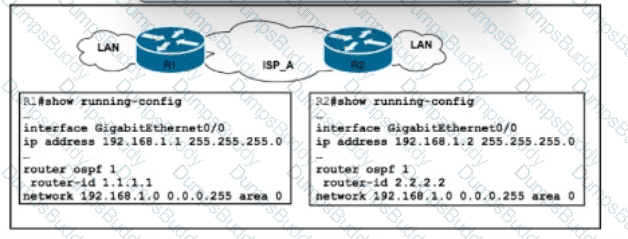
Refer to the exhibit. A growing company with an increasing international presence requires a secure and scalable solution for inter-office data transfer across their geographically dispersed locations. To ensure departmental privacy, the network must enforce granular access control. BGP is running in the network, and two VRF instances with unique route distinguishers and route targets have been configured to segregate critical financial data from regular network traffic. A network engineer with an employee ID: 5086:72:617 must find a solution that allows for future network expansion while maintaining robust security and data privacy between departments. The solution must comply with the RFC 4364 standard. Which action must the engineer take to meet the requirements?
Which protocol does a Cisco MPLS TE tunnel use to maintain paths within the core?
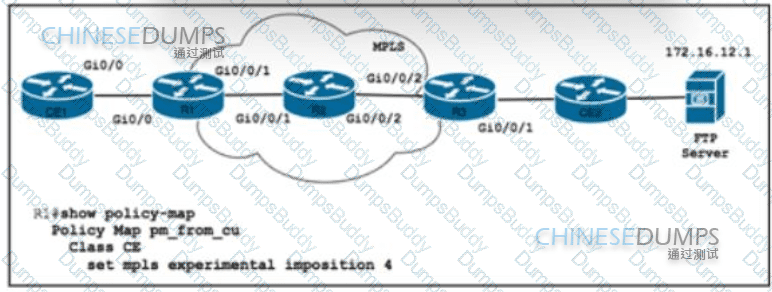
Refer to the exhibit. Router R1 is configured with class map CE with match Ip precedence critical to align with customer contract SLAs. The customer is sending all traffic from CE1 toward the FTP server with IP precedence 5 A network engineer must allow 10% of interface capacity on router R3 Which two actions must the engineer take to accomplish the task? (Choose two )
A network administrator must monitor network usage to provide optimal performance to the network end users when the network is under heavy load. The administrator asked the engineer to install a new server to receive SNMP traps at destination 192.168.1.2. Which configuration must the engineer apply so that all traps are sent to the new server?
A router is configured to perform MPLS LDP graceful restart.
Which three steps are included when the RP sends an LDP initialization to a neighbor to establish an LDP session? (Choose three)
Refer to the exhibit.

Which the link aggregation configuration router is running on Cisco IOS XR software, which LACP interface configuration is needed to add the interface to the bundle?


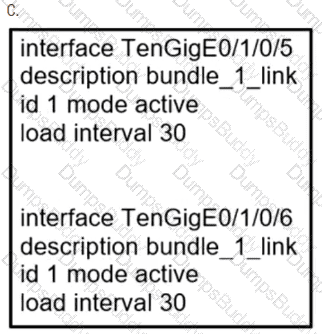
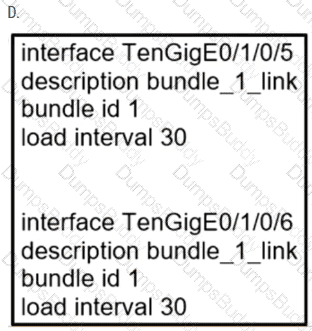
Refer to the exhibit. A company recently deployed a new network using OSPF in the core to share routes. The network administrator selected OSPF as the routing protocol because of its ability to maintain a route database. When the new network was started up, all routers booted normally, but the link between routers R1 and R2 failed to come up. The two routers are located in the same rack at the data center. Which task should an engineer perform to correct the problem?
While implementing TTL security, you issue the PE(config-router-af)#neighbor 2.2.2.2 ttl-security hops 2 command.
After you issue this command, which BGP packets does the PE accept?
Refer to the exhibit:
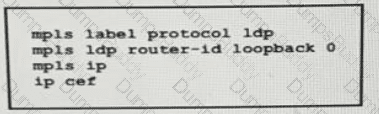
A network operator working for service provider with an employee id 3715 15:021 applied this configuration to a router.
Which additional step should the engineer use to enable LDP?
Refer to the exhibit.
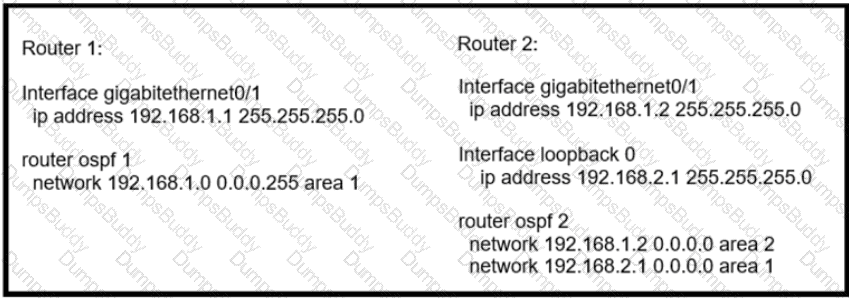
Router 1 is missing the route for the router 2 loopback 0. What should the engineer change to fix the problem?
An engineer Is implementing NSR with OSPF on a large campus that requires high availability. Which task must an engineer perform to complete the process with minimal disruption to traffic?
FRR is configured on a network. What occurs when the headend router on the path is alerted to a link failure over IGP?
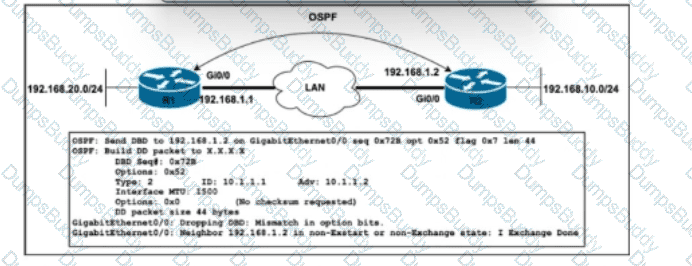
Refer to the exhibit. A network engineer just upgraded the Cisco IOS XE Software to the newest version on OSPF routers R1 and R2, added the point-to-point network type under Gi0/0 on R2, and configured ip route 192.168.10.0 255.255.255.0 192.168.1.2 on R1. After the engineer restarted the routers, R1 entered the Exstart state with its neighbor, but the adjacency has not been established. Which action must the engineer take to resolve the issue?

Refer to the exhibit. An operations team recently located an archive of scripts for deploying routine network changes with an error-free approach. A junior network engineer, who is working to modify the scripts to support RESTCONF, has been asked to document the purpose of each updated script. Which two actions does the given script take? (Choose two.)
Refer to the exhibit.
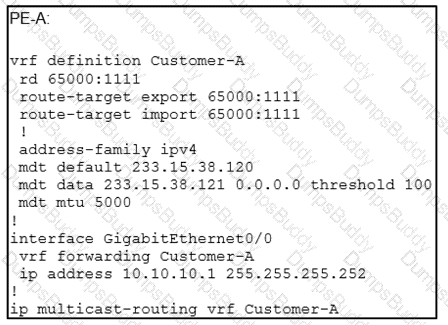
An engineer is implementing Auto-RP and reviewing the configuration of the PE-A. Which configuration permits Auto-RP messages to be forwarded over this interface?
Refer to the exhibit:
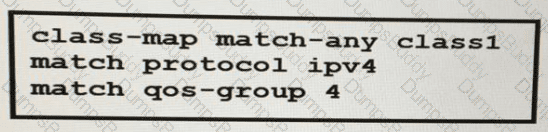
A network engineer is implementing QoS services. Which two statements about the QoS-group keyword on Cisco IOS XR 3re true? (Choose two )
Refer to the exhibit.
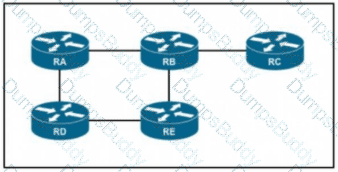
If RC is a stub router, which entry must be injected so that it will send traffic outside the OSPF domain?
Which regular expression query modifier function indicates the start of a string?
An engineering team must implement Unified MPLS to scale an MPLS network. Devices in the core layer use different IGPs, so the team decided to split the network into different areas. The team plans to keep the MPLS services as they are and introduce greater scalability. Which additional action must the engineers take to implement the Unified MPLS?
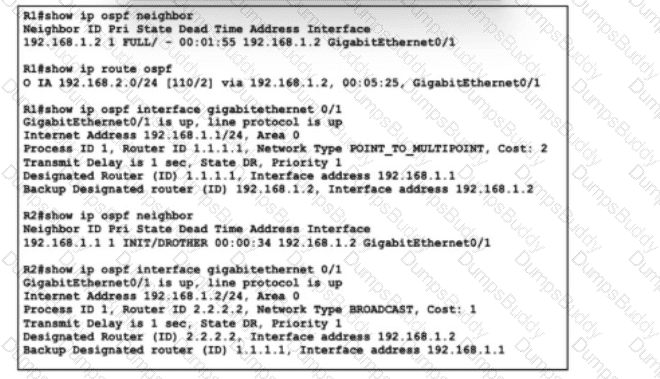
Refer to the exhibit. A junior network engineer has been configuring OSPF on two directly connected routers, R1 and R2, to establish a neighbor adjacency. The engineer also configured ip route 10.1.1.0 255.255.255.0 GigabitEthernet 0/1 10.10.10.1 on R1 to allow inbound management. After the initial configuration, the adjacency failed to form. The engineer changed the cost and area type under the OSPF configuration on R1, but the problem persists. Which action must the engineer take to resolve the issue?
Refer to the exhibit:

Which command is used to complete this configuration for QoS class-based marking?
Refer to the exhibit:
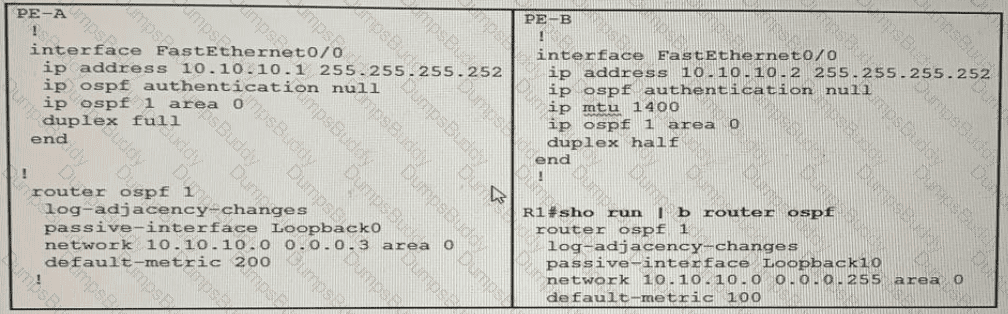
Which configuration prevents the OSPF neighbor from establishing?
Which statement about TLS is accurate when using RESTCONF to write configurations on network devices'?
What happens when a segment-routing TE tunnel loses the link and there is no secondary path in place?
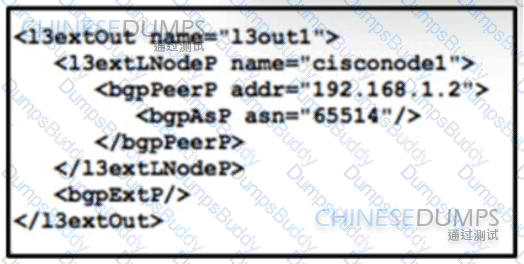
Refer to the exhibit. A global company plans to implement BGP at its newest location to provide connectivity to other offices. The global infrastructure of the company is a multivendor environment. An engineer must review the BGP core configurations at headquarters to determine if they can be repurposed at the new location. The engineer copied this JSON script for review. What is the effect of the script?
Refer to the exhibit.
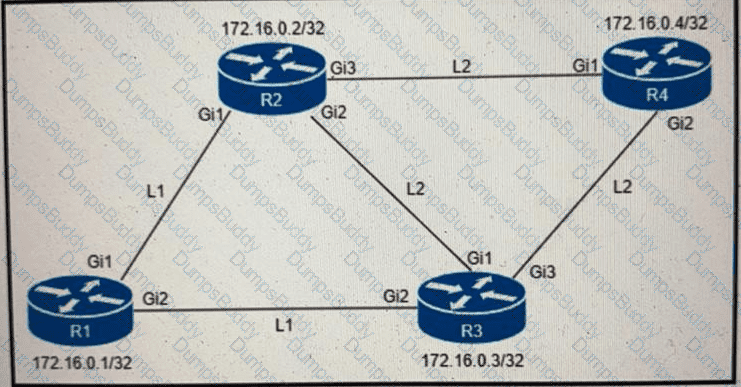
An engineer must configure router R2 as the new P router in the network. Which configuration must be applied to R2 to enable LDP-IGP Sync on its L2 IS-IS adjacencies?
A network engineer must enable multicast on the network to support a new series of webcasts. The PIM protocol has been enabled on the LAN side, with PIM and MSDP capabilities on edge router R1. The multicast source has been configured with IP address FF3A:121, and IP protocol 58 has been enabled and successfully tested in the network. Due to the limitations of some devices on the network, the data flow should take the most efficient path.
Which task must the engineer perform to achieve the goal?
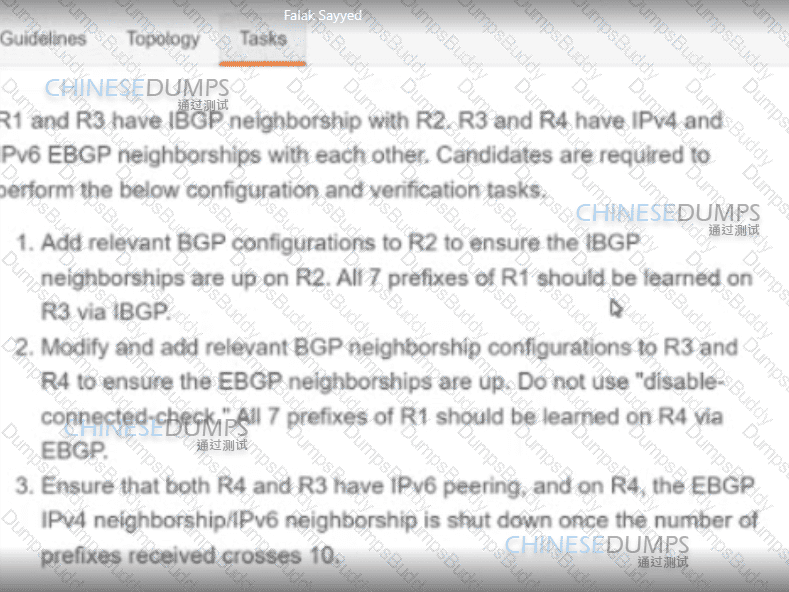
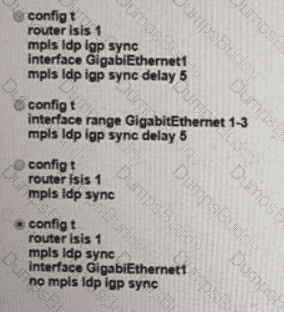
Refer to the exhibit. A network engineer is configuring a new router for iBGP to improve the capacity of a growing network. The router must establish an iBGP peer relationship with its neighbor. The underlay network is already configured with the correct IP addresses. Which step should the engineer apply to complete this task?
Refer to the exhibit.
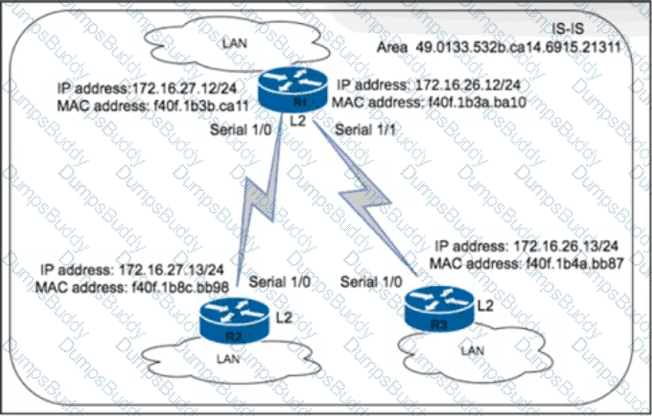
An engineer with an employee 10:4350:47:853 is implementing IS-IS as the new routing protocol in the network. All routers in the network operate as Level 2 routers in the same private autonomous system, and the three branches are connected via dark fibre. The engineer has already implemented IS-IS on router R1 with NET address 49.0133.532b.ca14.6915.21311.F40F.1B3a.ba10.00. Which IS-IS NET address configuration must be implemented on R3 to establish IS-IS connectivity?
Refer to the exhibit:

Router 1 was experiencing a DDoS attack that was traced to interface gjgabitethernet0/1.
Which statement about this configuration is true?
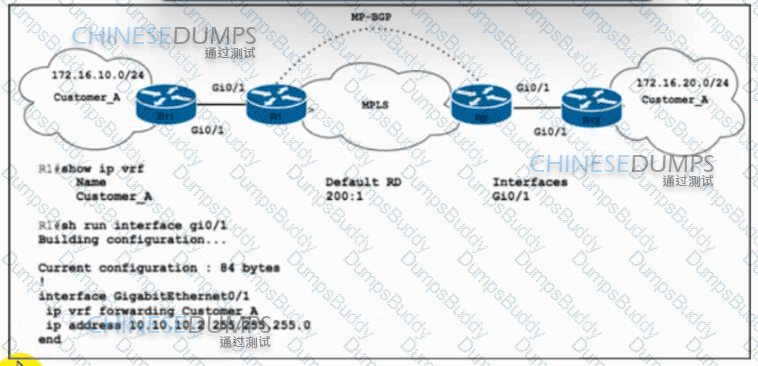
Refer to the exhibit. Customer_A asked ISP_A to connect two offices via an MPLS L3 VPN. Customer_A is currently using only the default route toward ISP_A. The engineer at ISP_A already configured the ip route vrf Customer_A 172.16.10.0 255.255.255.0 10.10.10.1 command on R1. Which action completes the configuration?
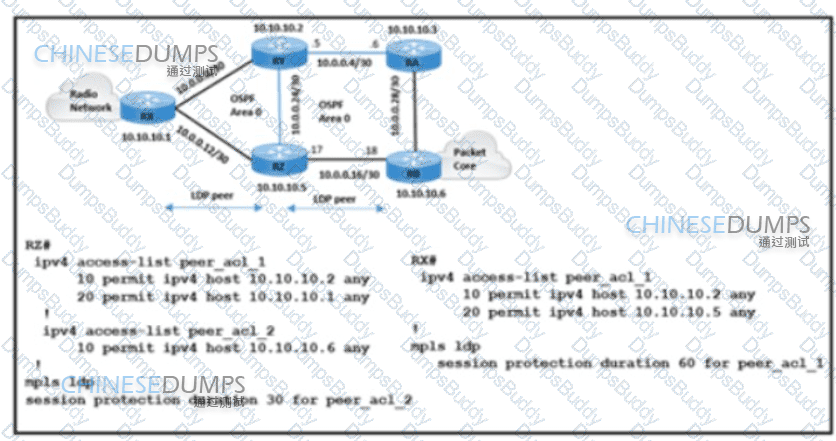
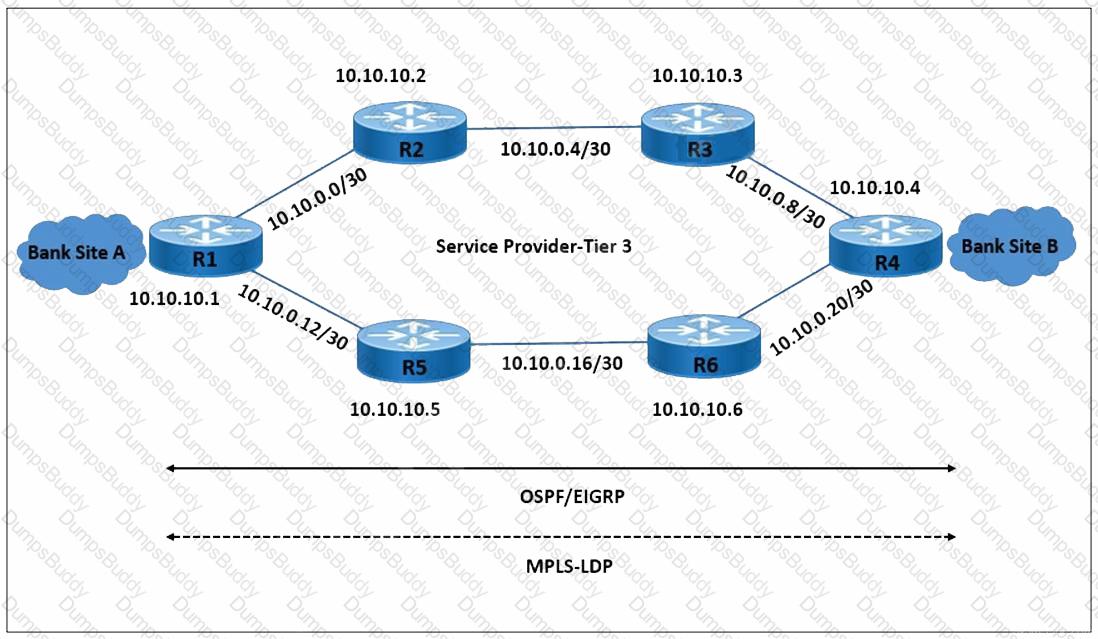
Refer to the exhibit. The radio network and packet core are using the route RX-RZ-RB to establish communication. The LDP session between 10.10.10.5 and 10.10.10.1 is experiencing link flapping at random intervals for 30-45 seconds each time. A network engineer must protect the LDP session and improve MPLS traffic convergence. Which action meets these requirements?
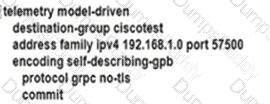
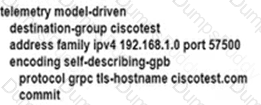
An engineer is developing a configuration script to enable dial-out telemetry streams using gRPC on several new devices. TLS must be disabled on the devices. Which configuration must the engineer apply on the network?
A)
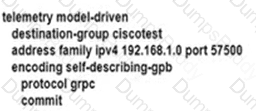
B)
C)
D)
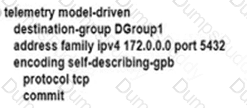
Refer to the exhibit:
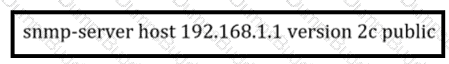
A network administrator wants to enhance the security for SNMP for this configuration.
Which action can the network administrator implement?
Refer to the exhibit:
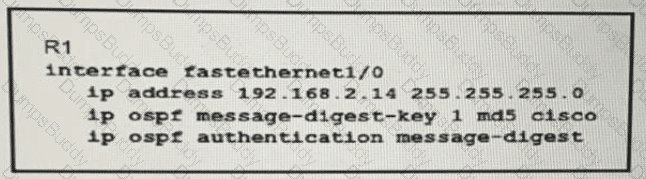
Which condition must be met by the OSPF peer of router R1 before the two devices can establish communication?
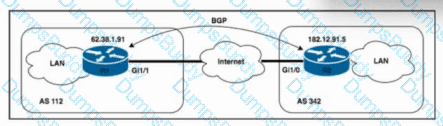
Refer to the exhibit. Routers R1 and R2 are connected over the internet, with the connection passing over four different autonomous systems. The company must mitigate potential DDoS attacks and protect the CPUs of the routers. A network engineer must secure all external connections on edge router R1 based on RFC 5082. R2 has already been secured. Which task should the engineer perform on R1 to achieve the goal?
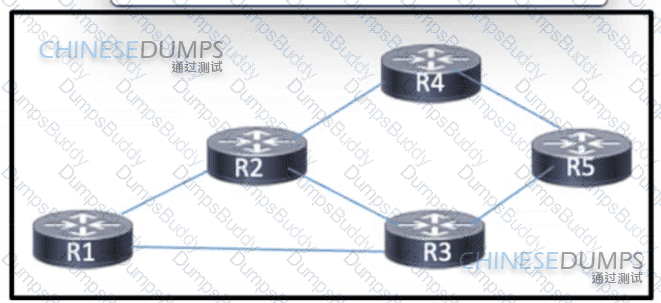
Refer to the exhibit. Routers R1 through R5 are being deployed within the core of a service provider running BGP The core supports distribution of VPNv4 routes using MPLS. R3 currently has multiple paths to reach R4. A network engineer must implement BGP attributes so that R3 can reach R4 via R1. Which action must the engineer take to meet the requirement?
Refer to the exhibit.

Which show command shows statistics for the control plane policy and is used to troubleshoot?
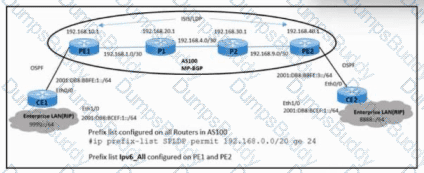
Refer to the exhibit. An engineer must update the configuration of the network with these requirements:
PE routers must define labels for IS-IS learned routes in AS100.
P routers must not receive LDP bindings for the external network in the IPv6 address family.
Which configuration must the engineer implement to meet these requirements?
Refer to the exhibit:
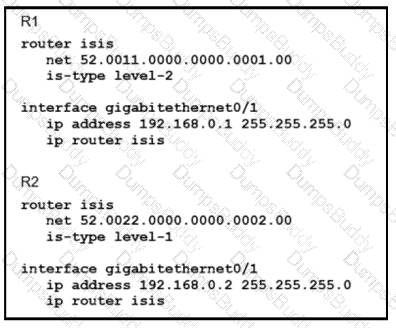
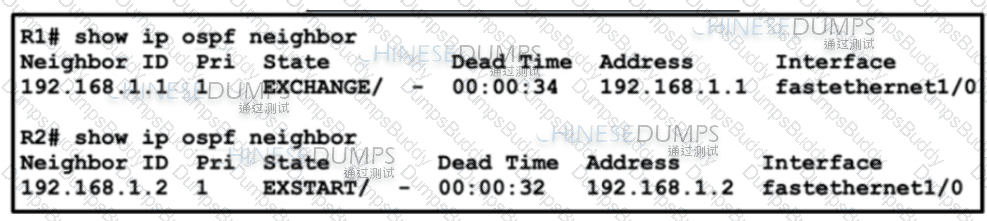
Which statement about the status of the neighbor relationship between R1 and R2 is true?