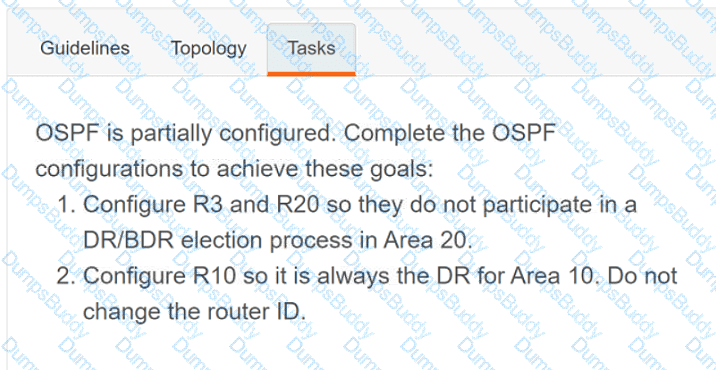
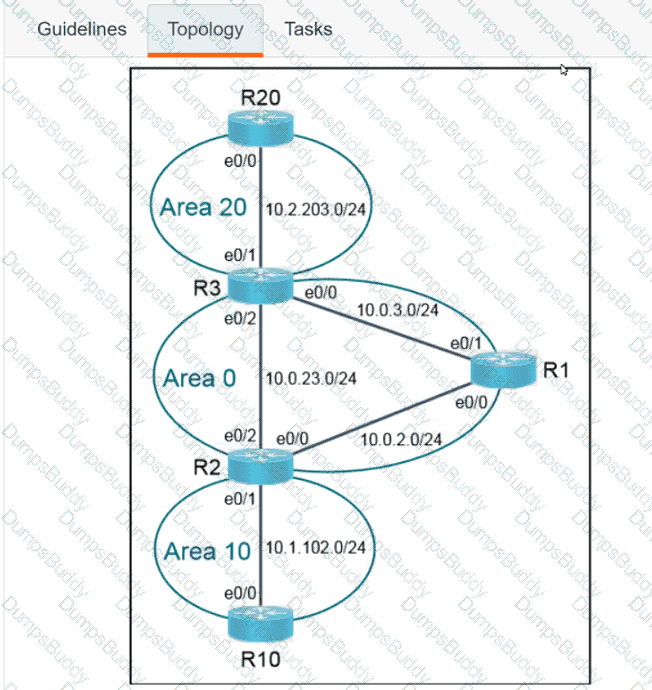
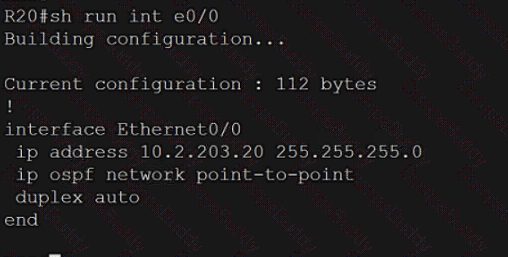
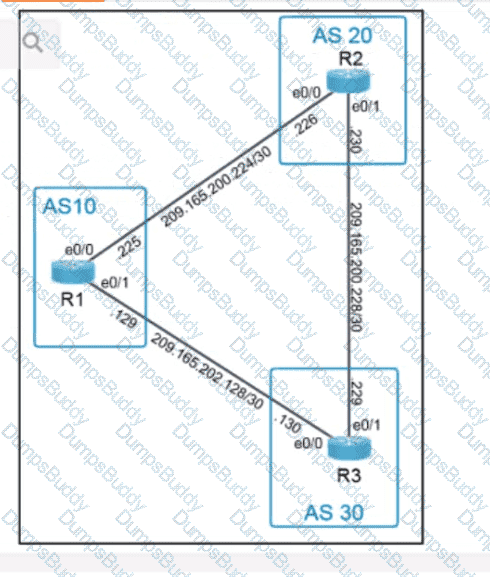
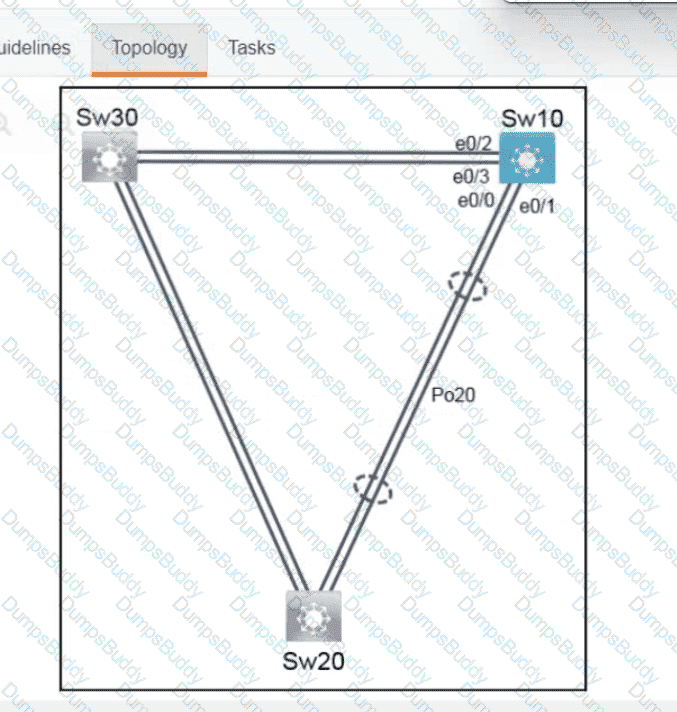
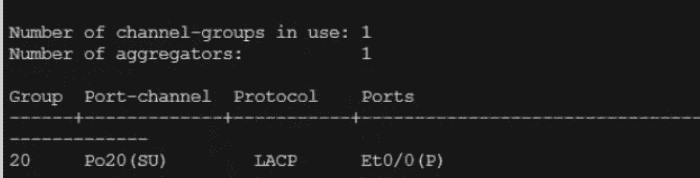
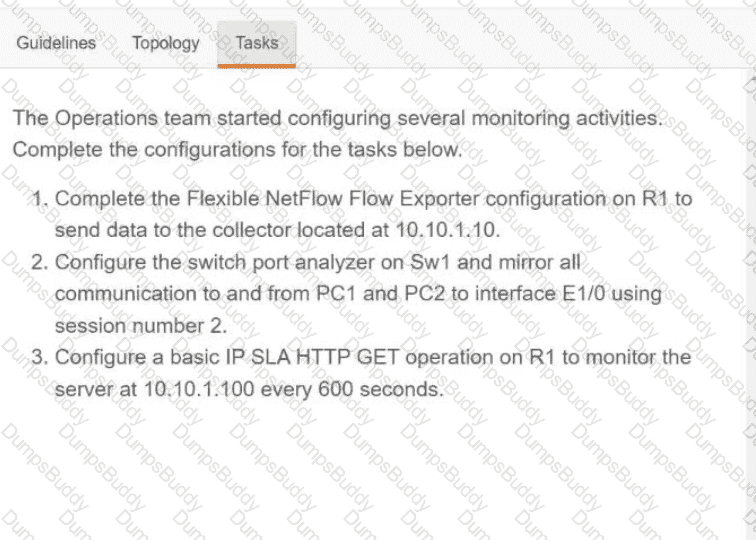
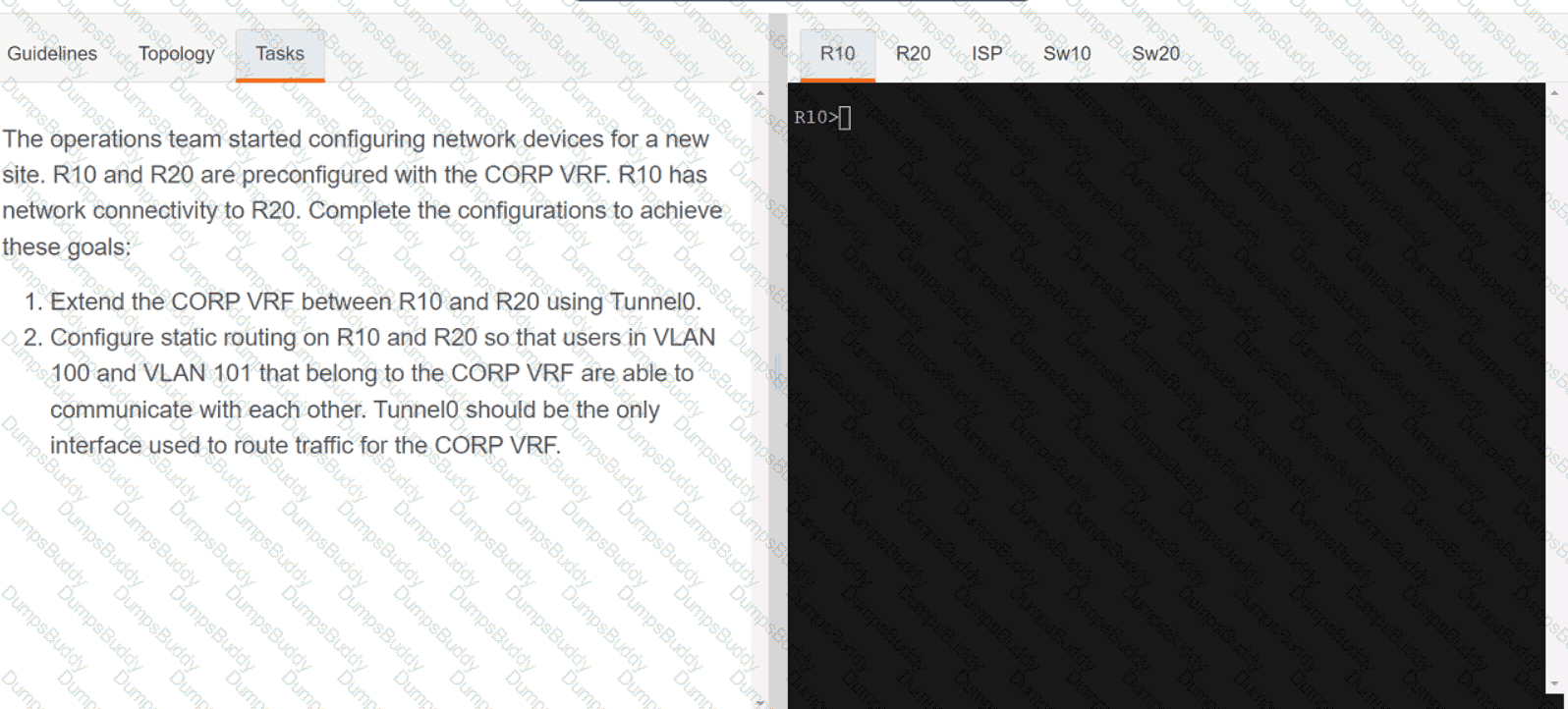
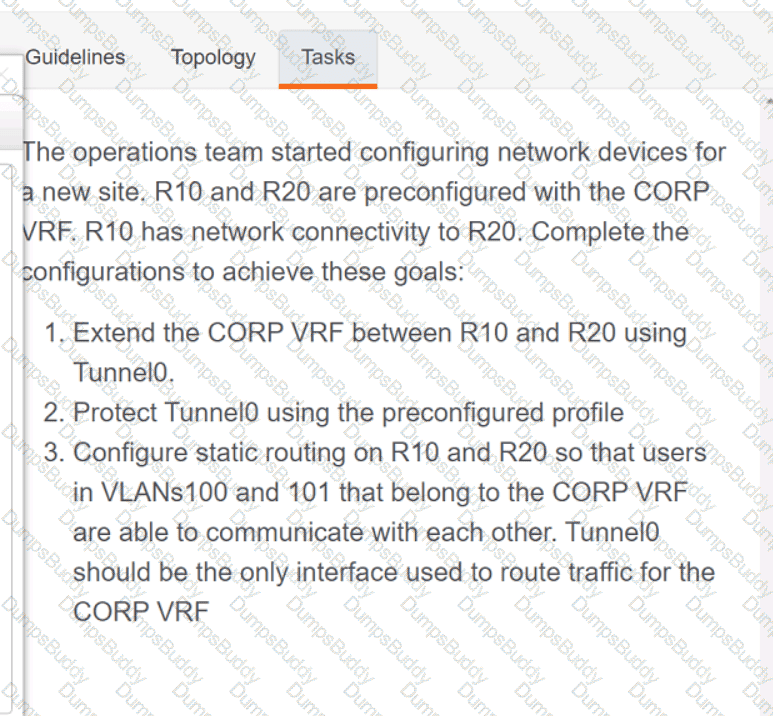
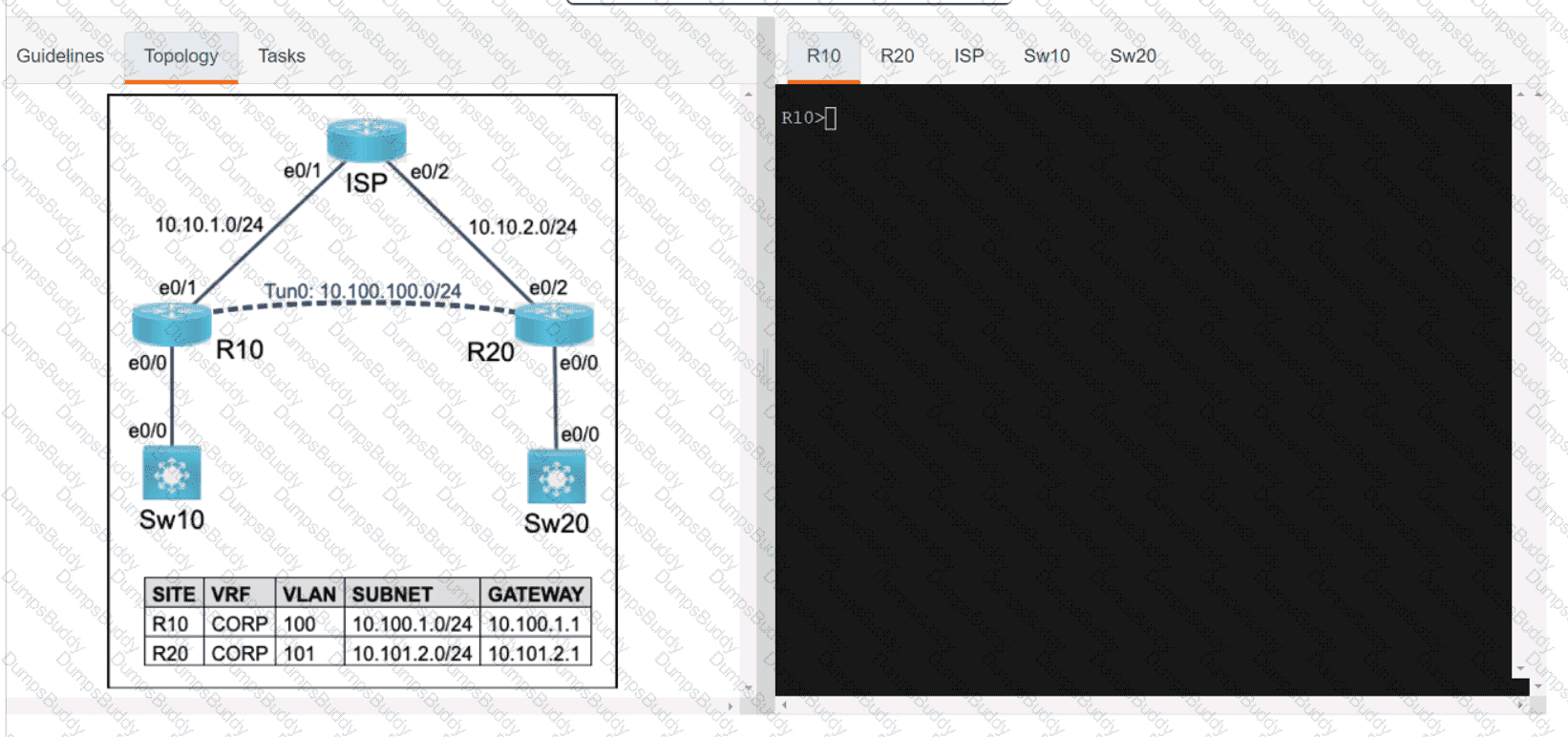
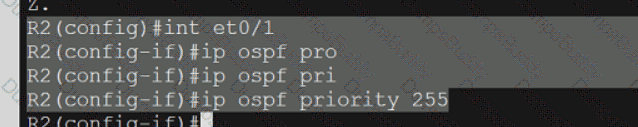
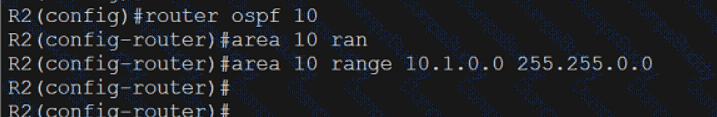
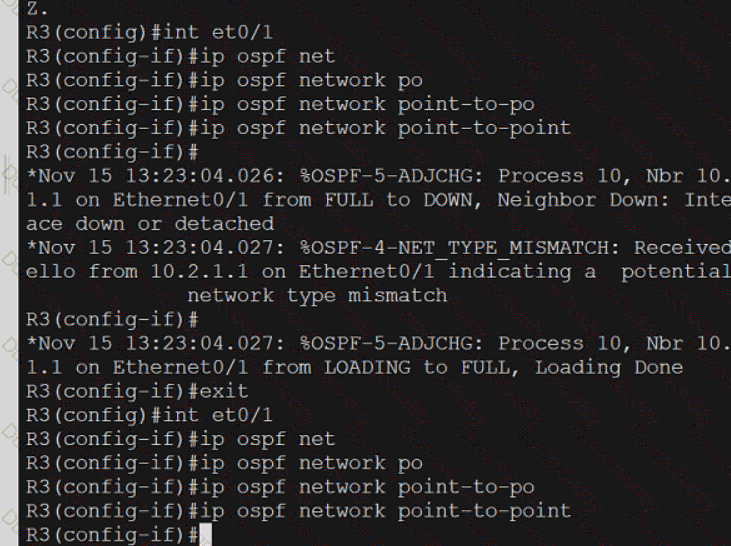
350-401 Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR) Questions and Answers
In which forms can Cisco Catalyst SD-WAN routers be deployed at the perimeter of a site to provide SD-WAN services?
Which two southbound interfaces originate from Cisco Catalyst Center (formerly DNA Center) and terminate at fabric underlay switches'? (Choose two.)
Refer to the exhibit. A customer reports occasional brief audio dropouts on its Cisco Wi-Fi phones. The environment consists of a Cisco Catalyst 9800 Series WLC with Catalyst 9120 APs running RRM. The phones connect on the 5-GHz band. Which action resolves this issue?
A response code of 404 is received while using the REST API on Cisco UNA Center to POST to this URI.
/dna/intent/api/v1 /template-programmer/project
What does the code mean?
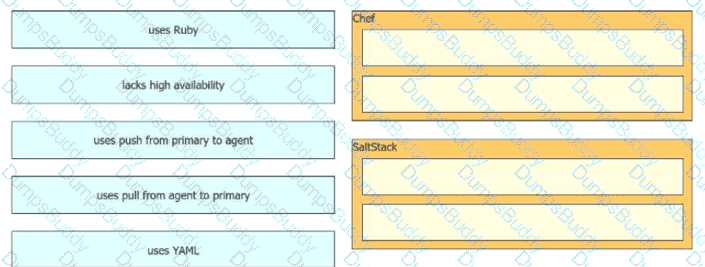
Drag and drop the automation characteristics from the left onto the appropriate tools on the right. Not all options are used.
Which two Cisco SD-Access components provide communication between traditional network elements and the controller layer? (Choose two.)
In a wireless Cisco SD-Access deployment, which roaming method is used when a user moves from one access point to another on a different access switch using a single WLC?
Which feature provides data-plane security for Cisco Catalyst SD-WAN networks'?
Which type of API enables Cisco Catalyst Center (formerly DNA Center) to focus on outcome instead of the individual steps that are required to achieve the outcome?
Which AP mode allows an engineer to scan configured channels for rogue access points?
Which characteristic applies to the endpoint security aspect of the Cisco Threat Defense architecture?
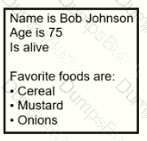
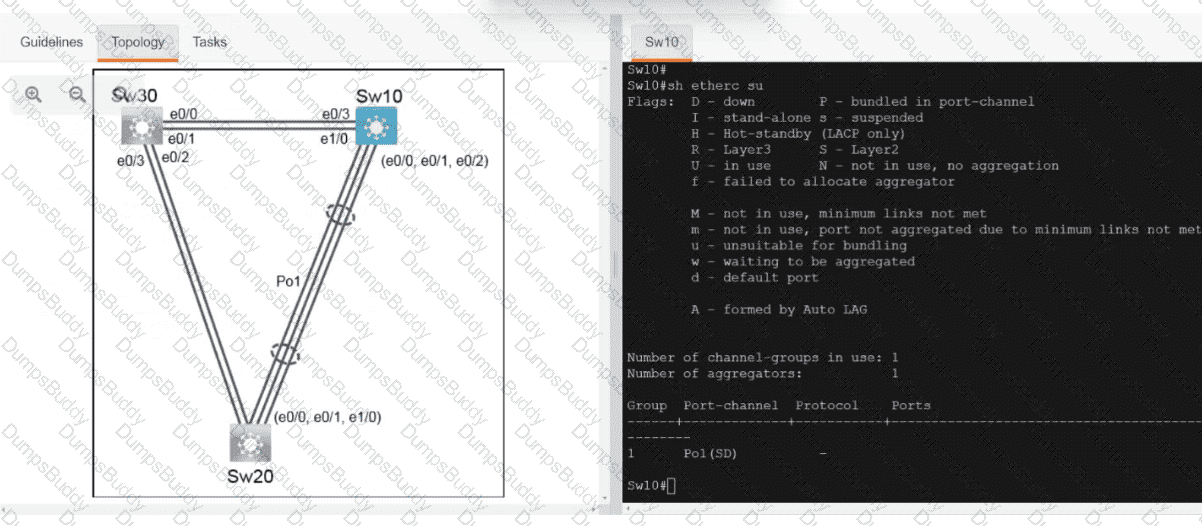
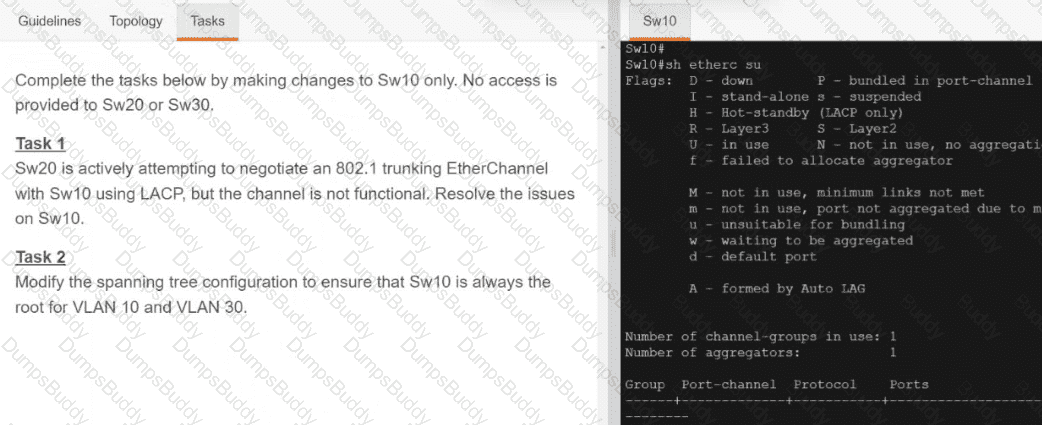
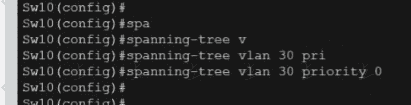
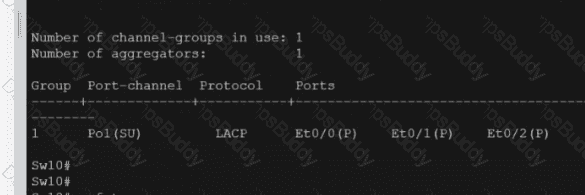
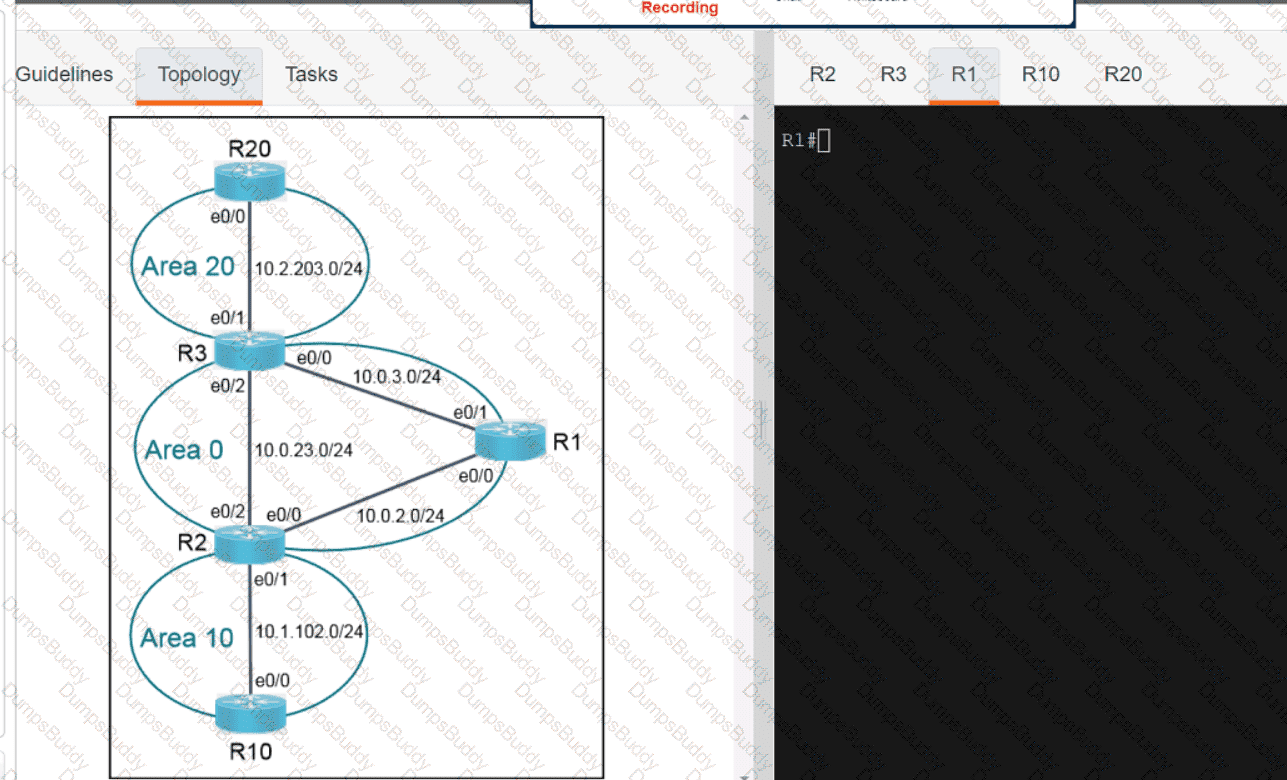
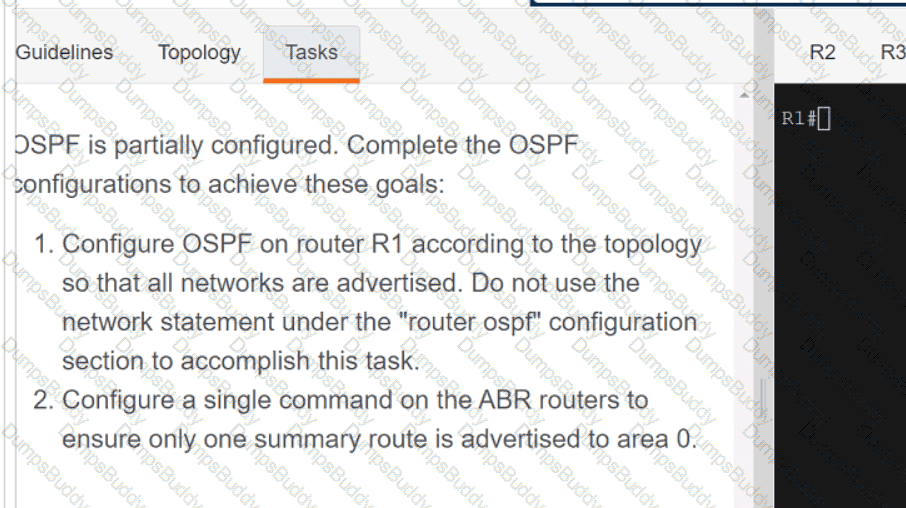
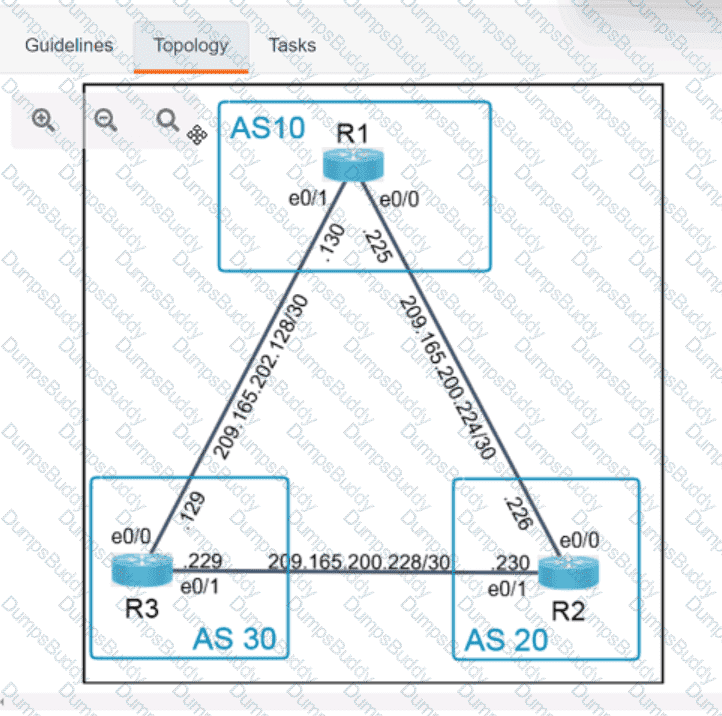
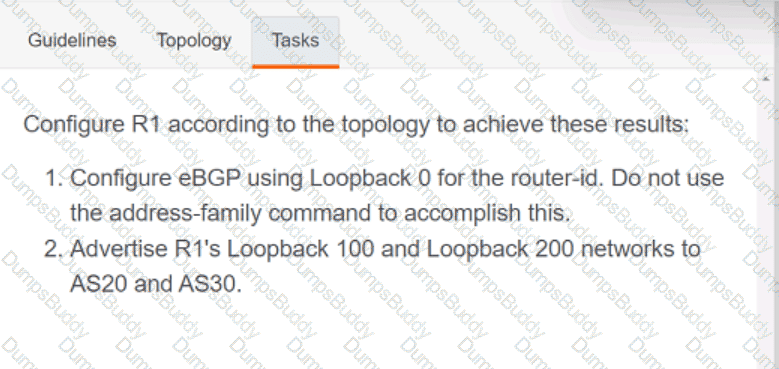
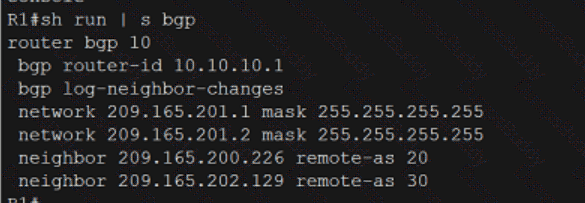
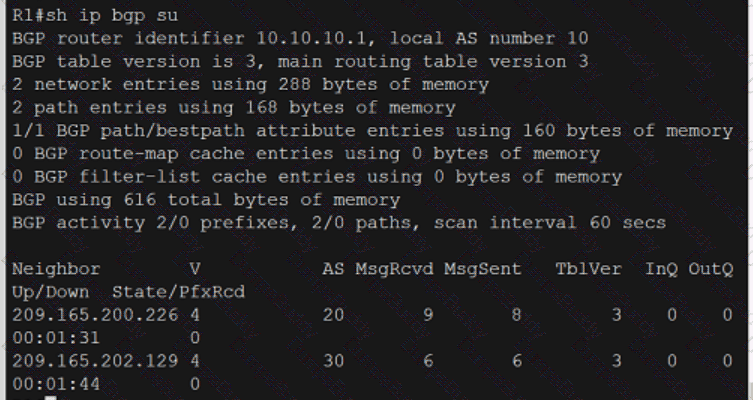
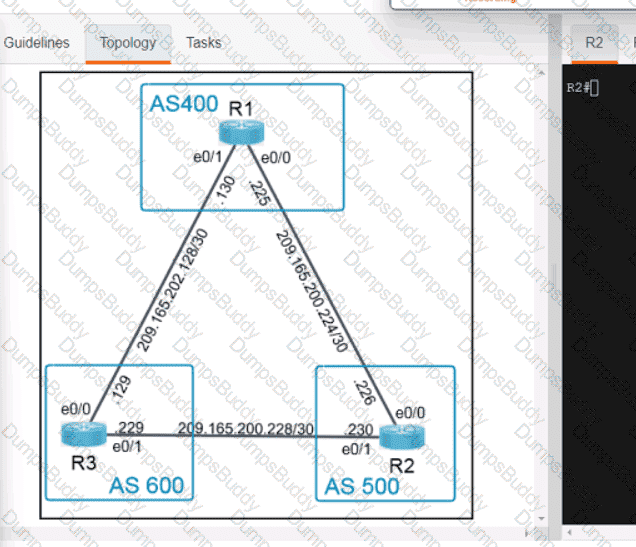
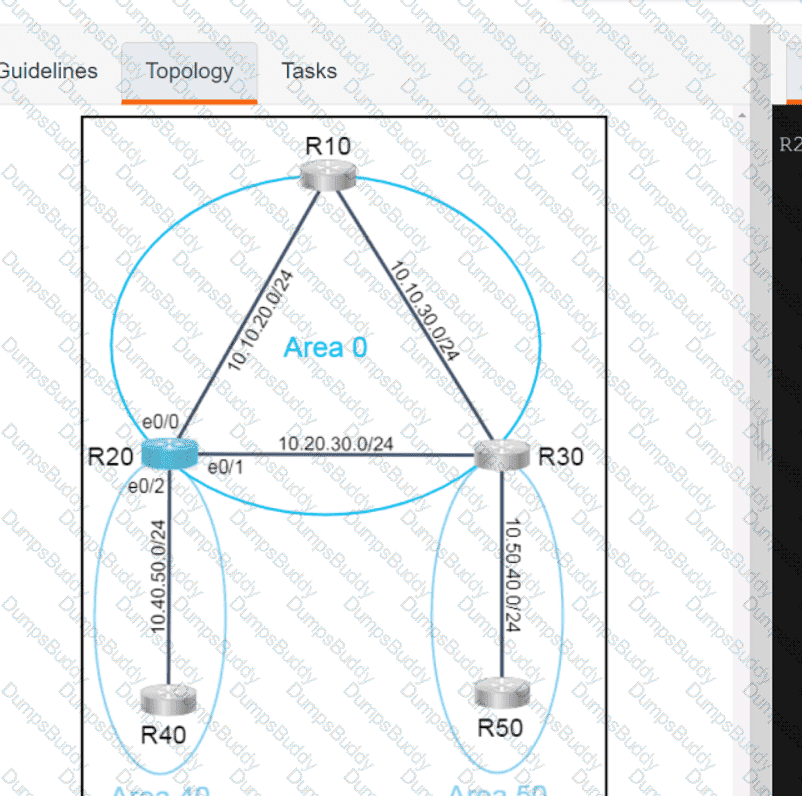
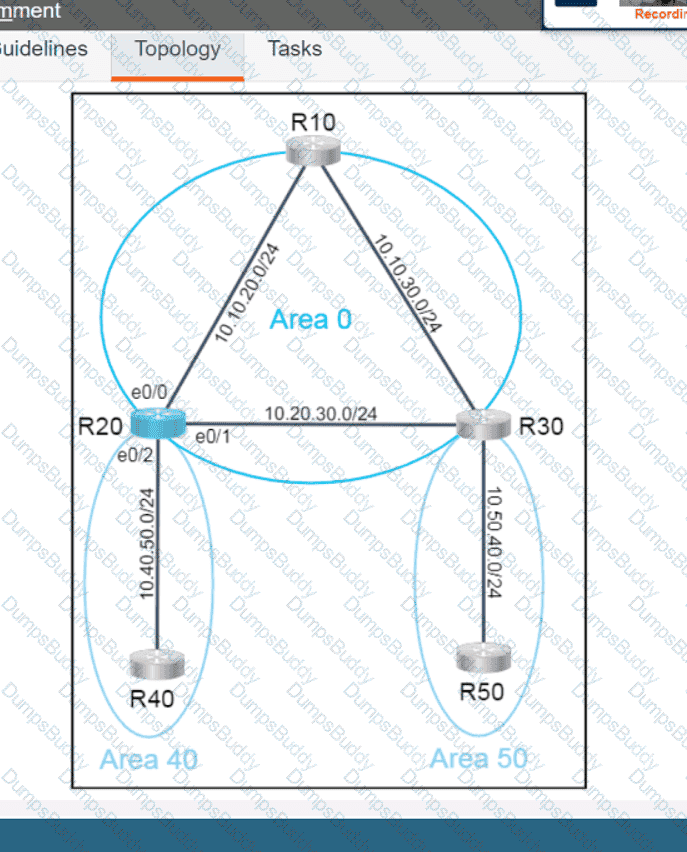
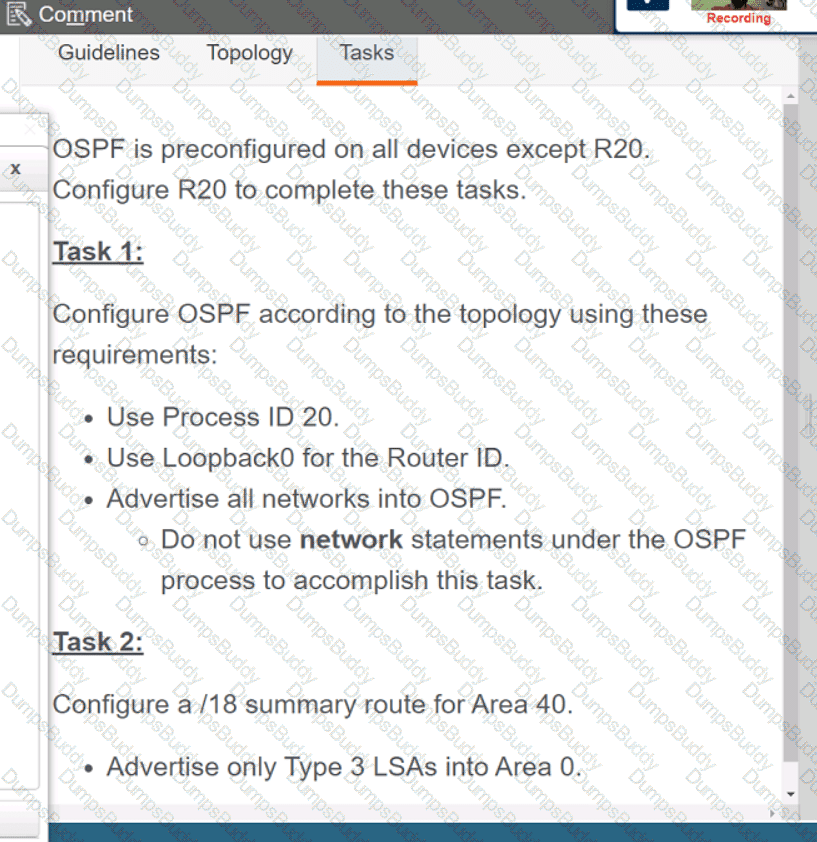
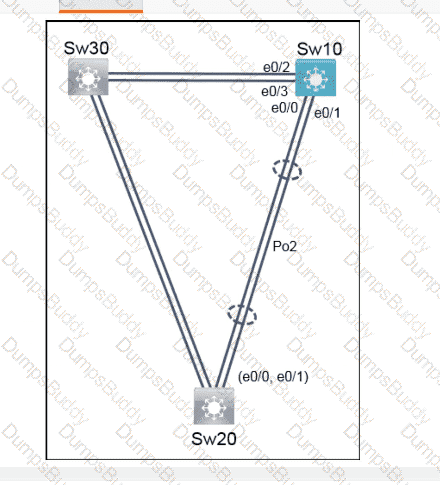
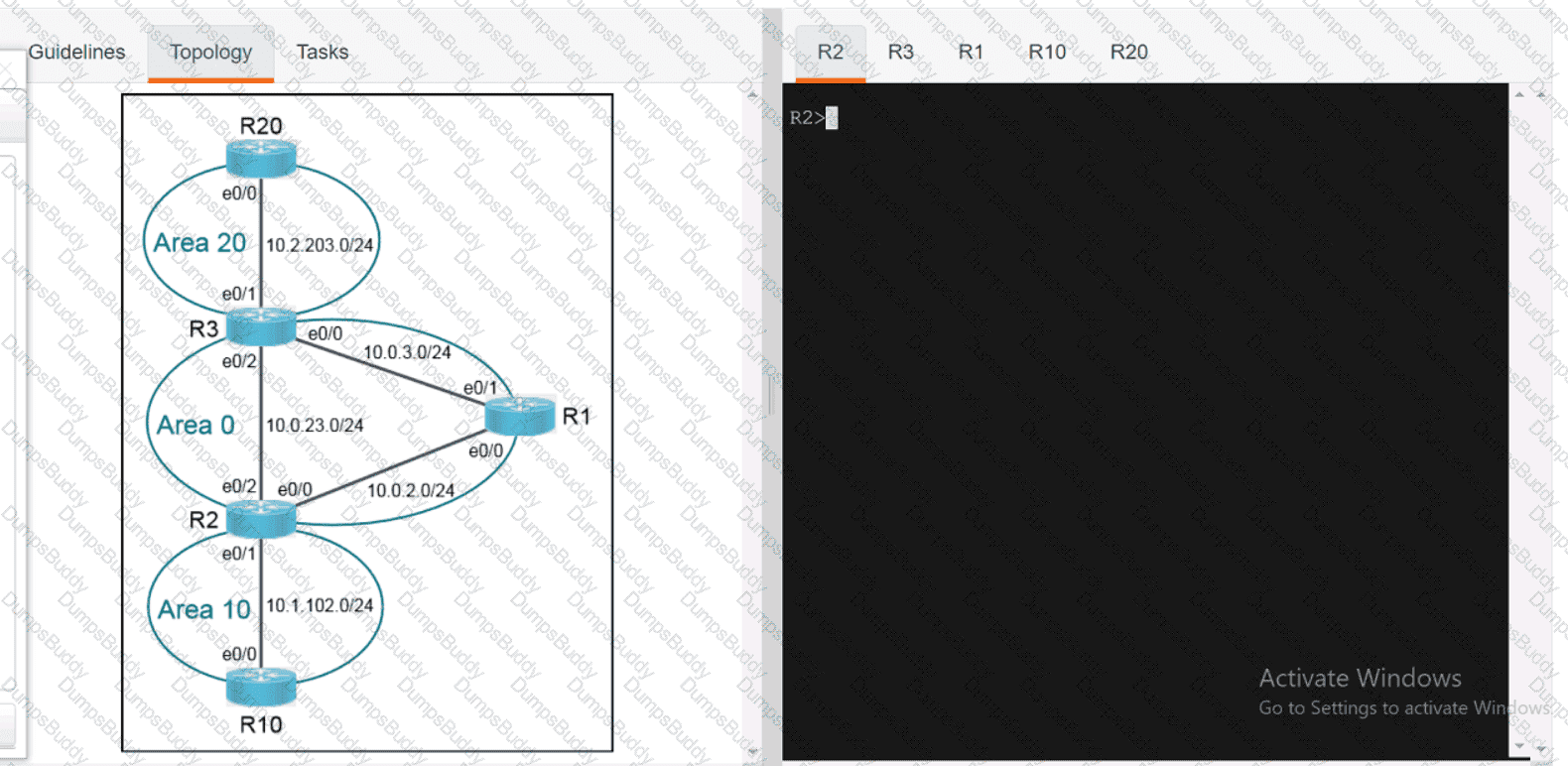
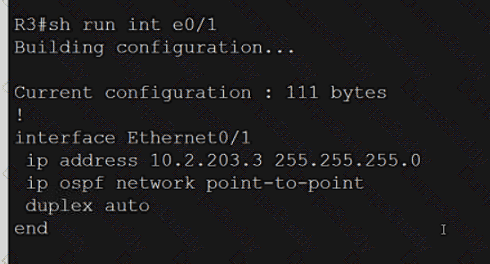
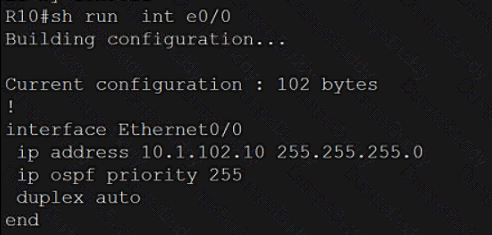
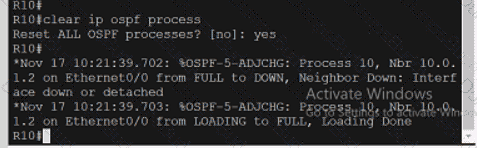
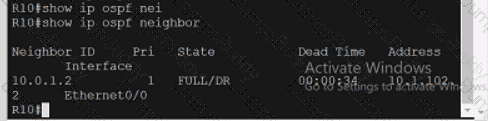
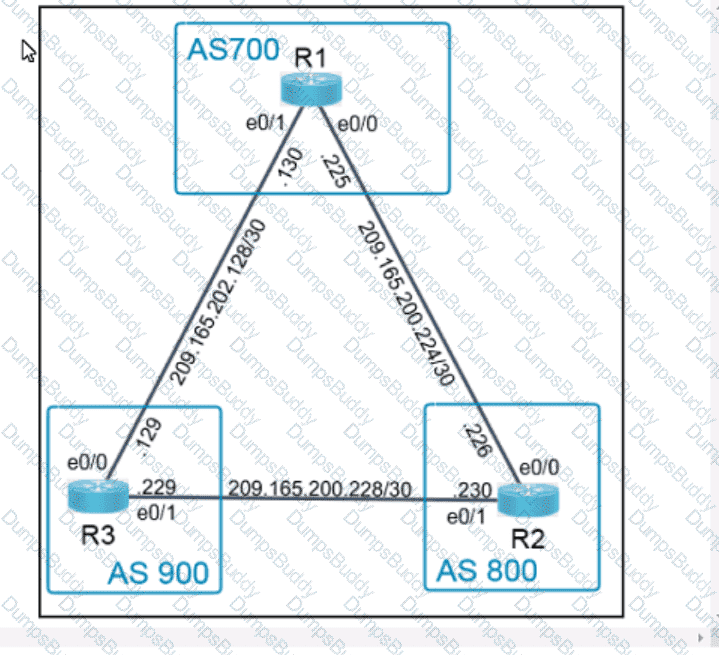
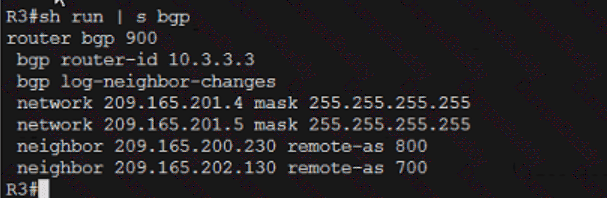
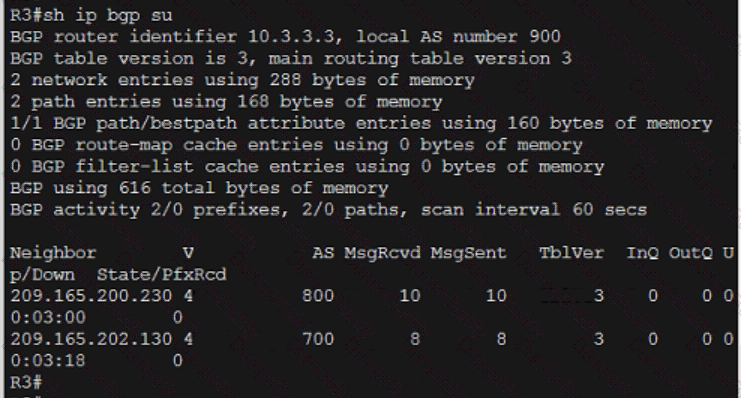
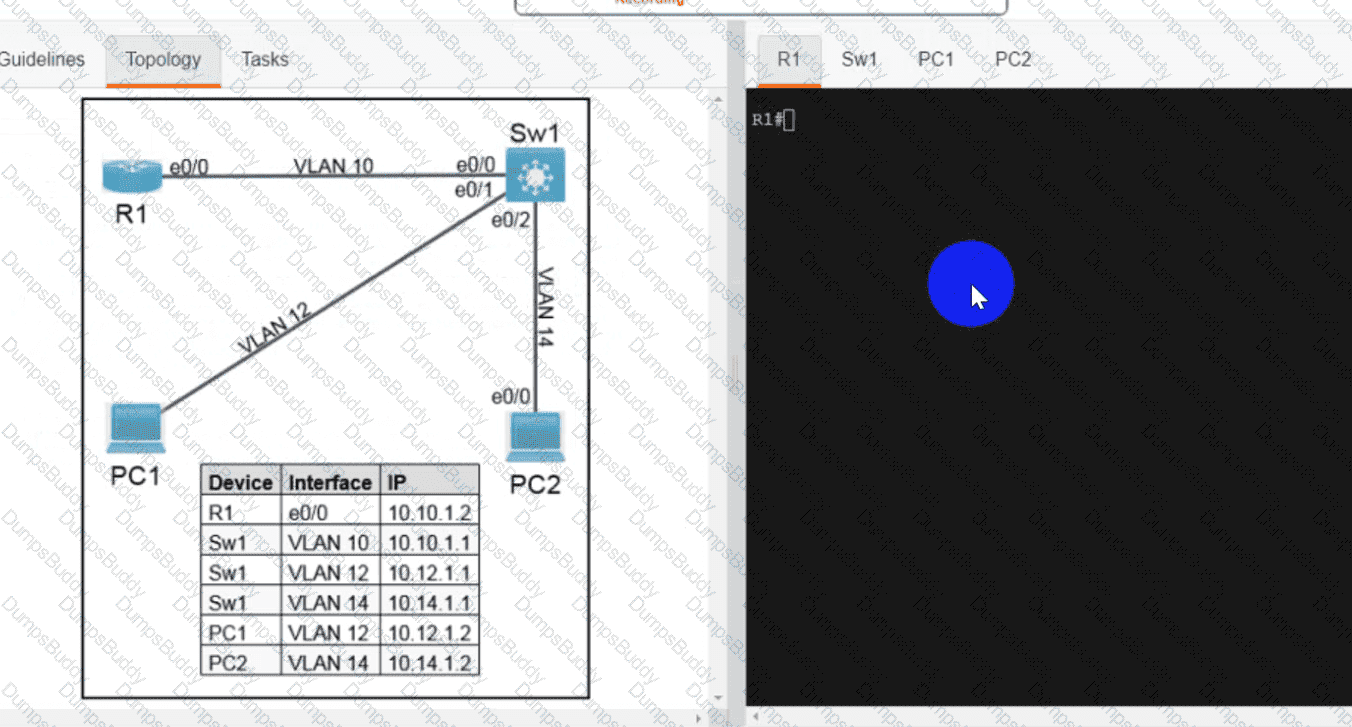
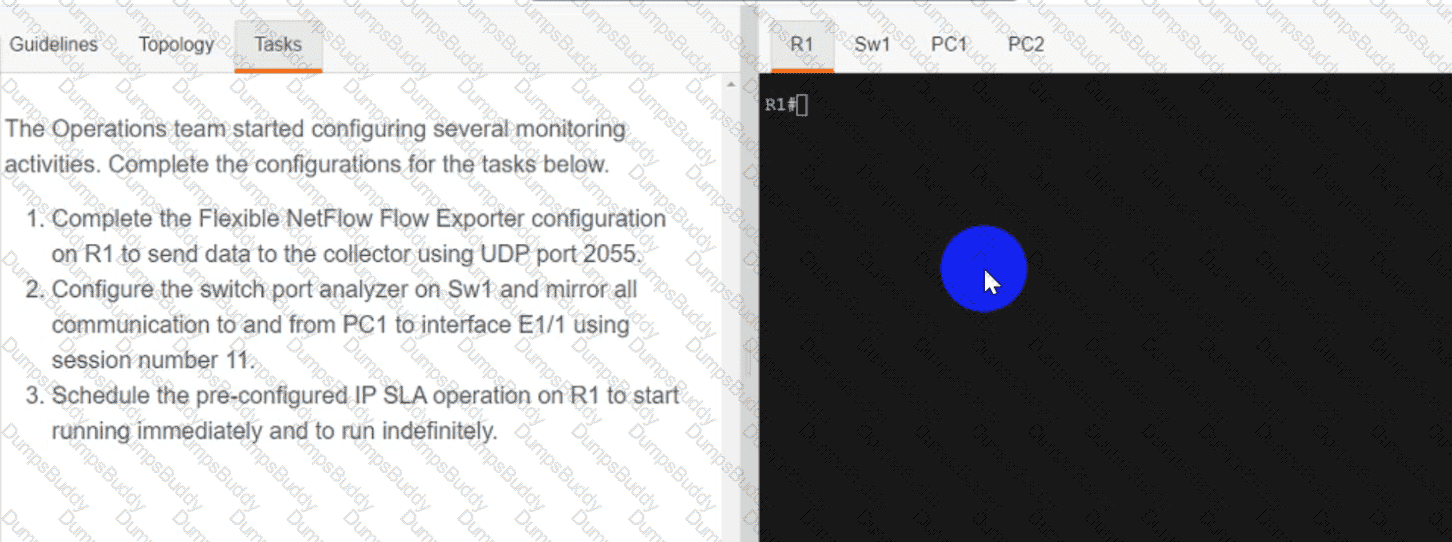
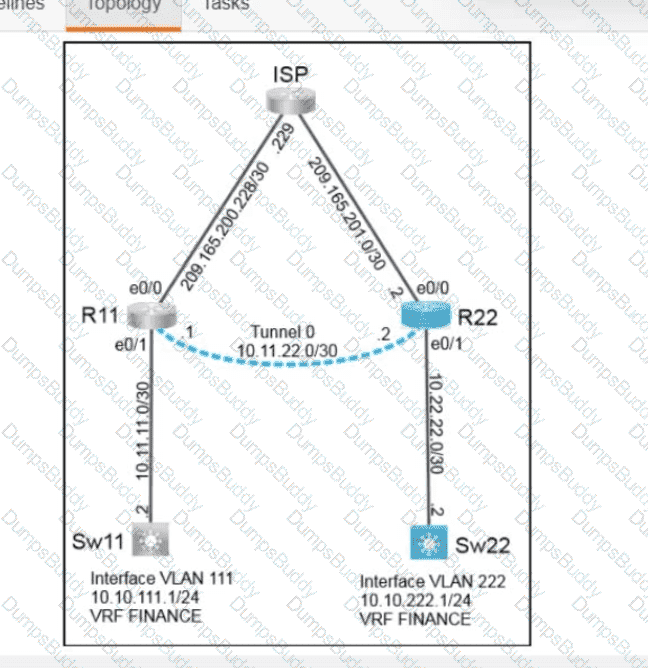
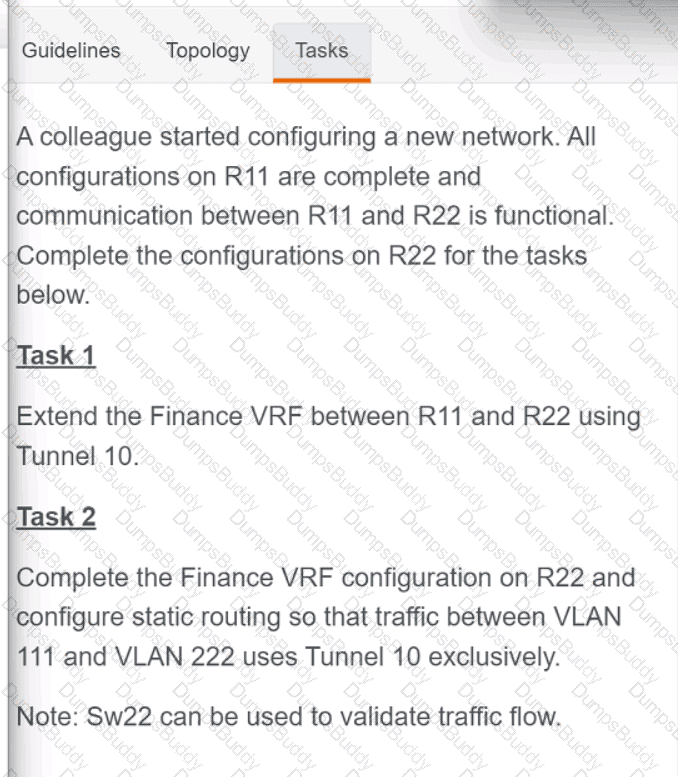
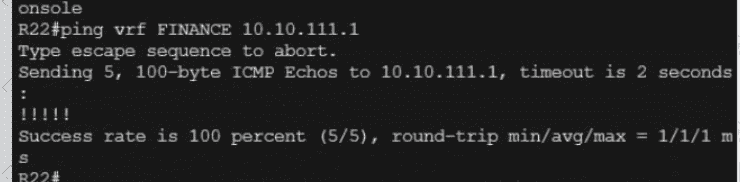
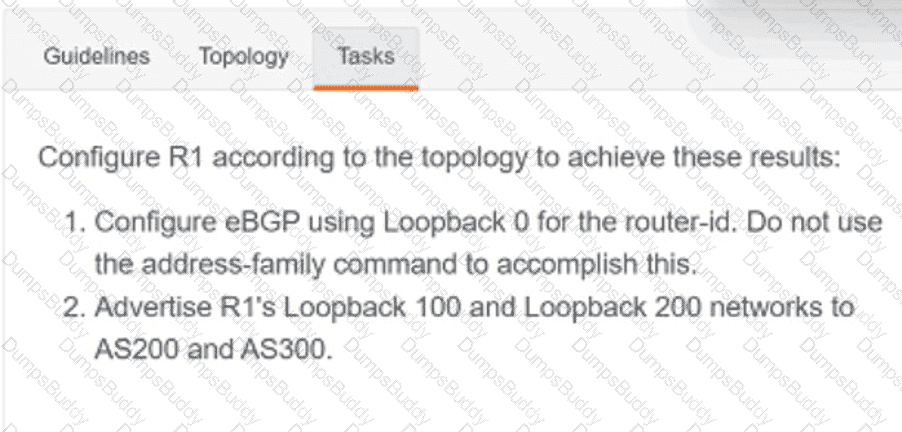
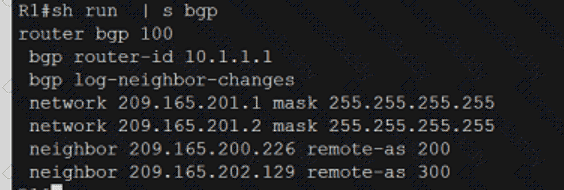
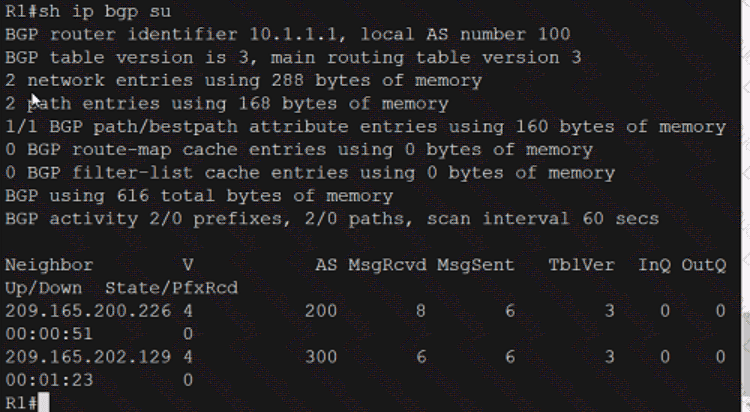
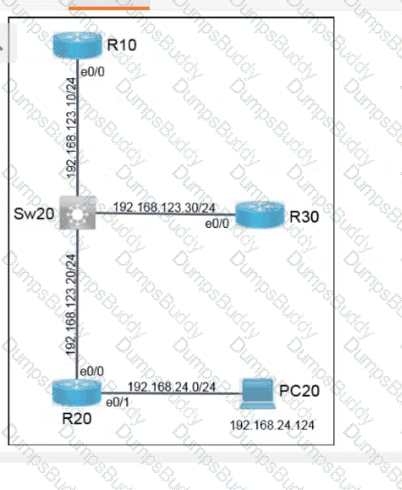
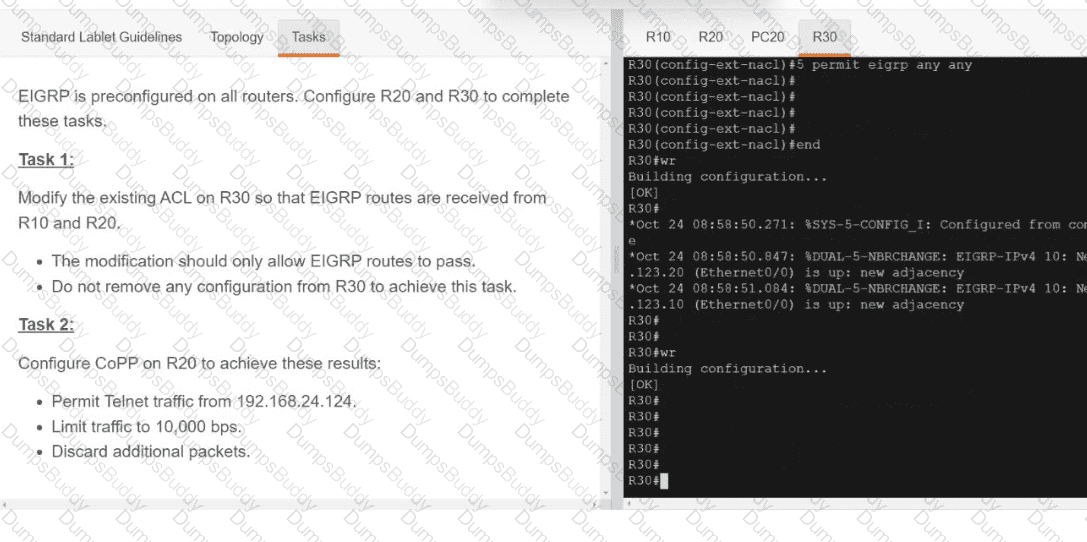
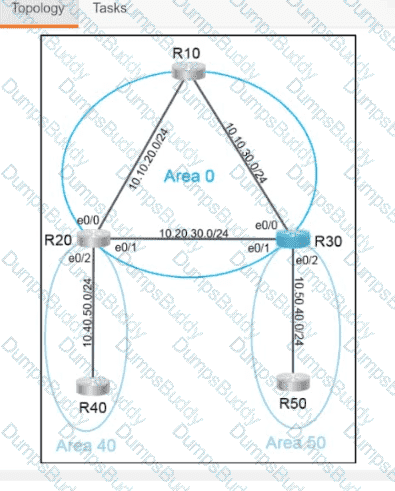
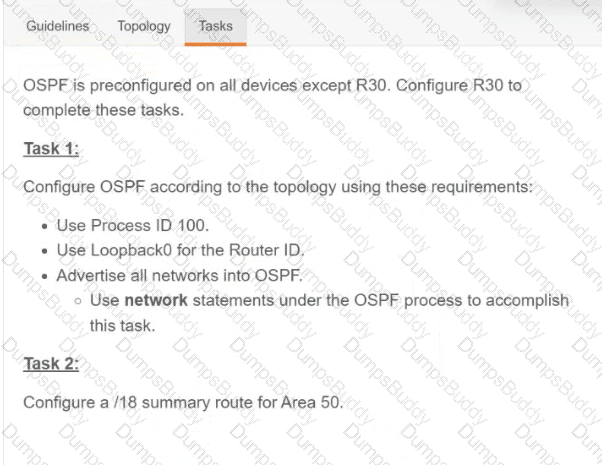
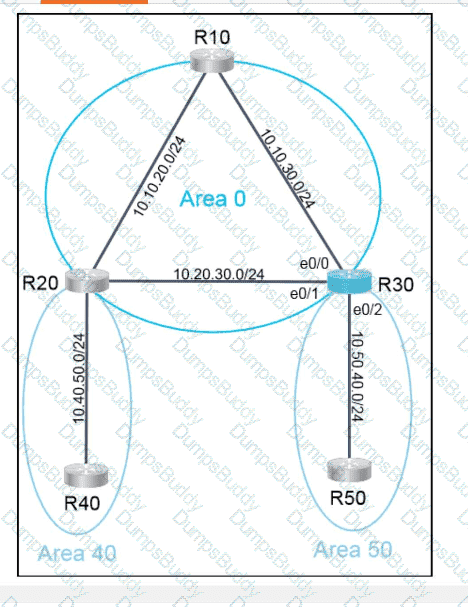
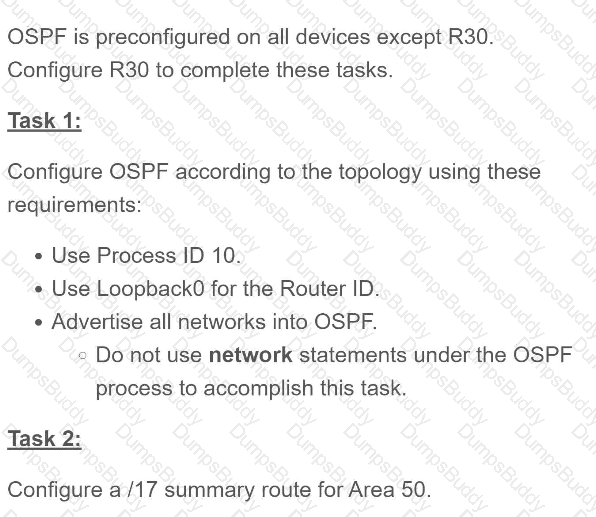
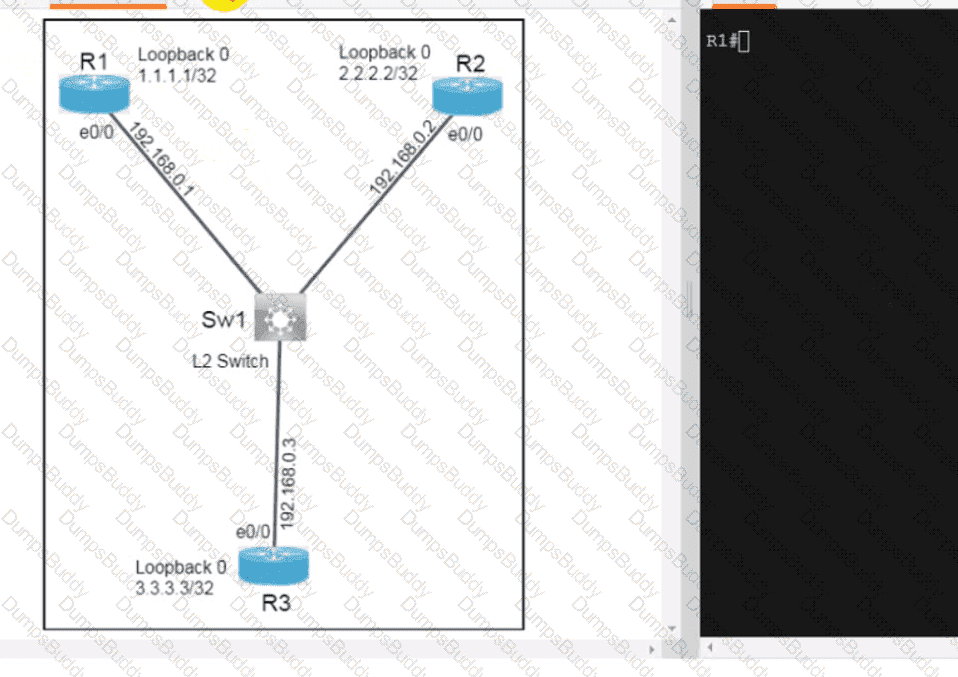
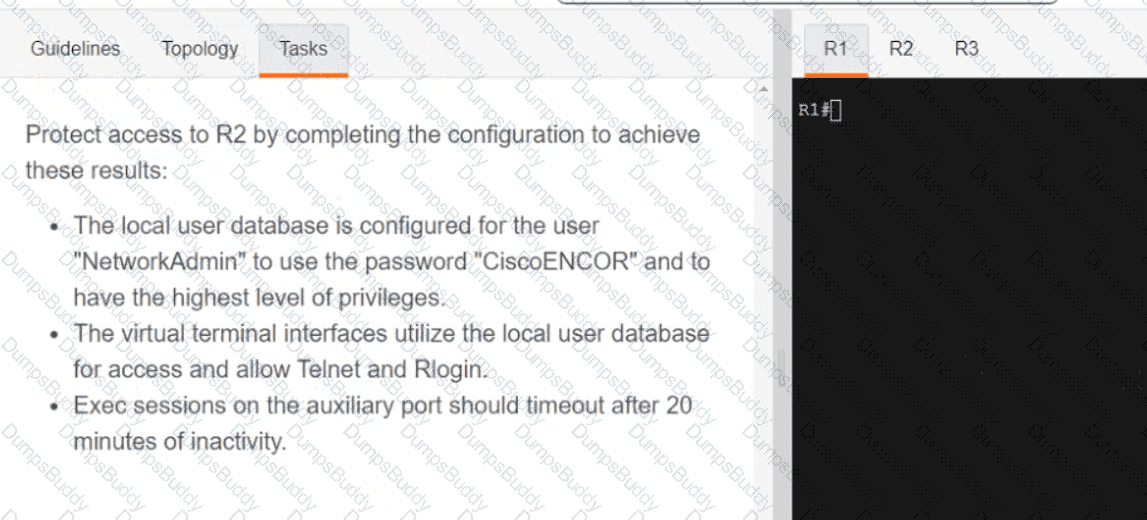
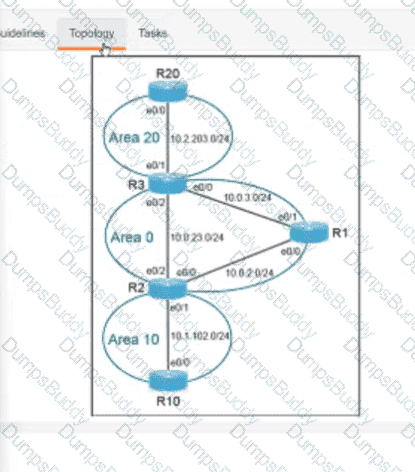
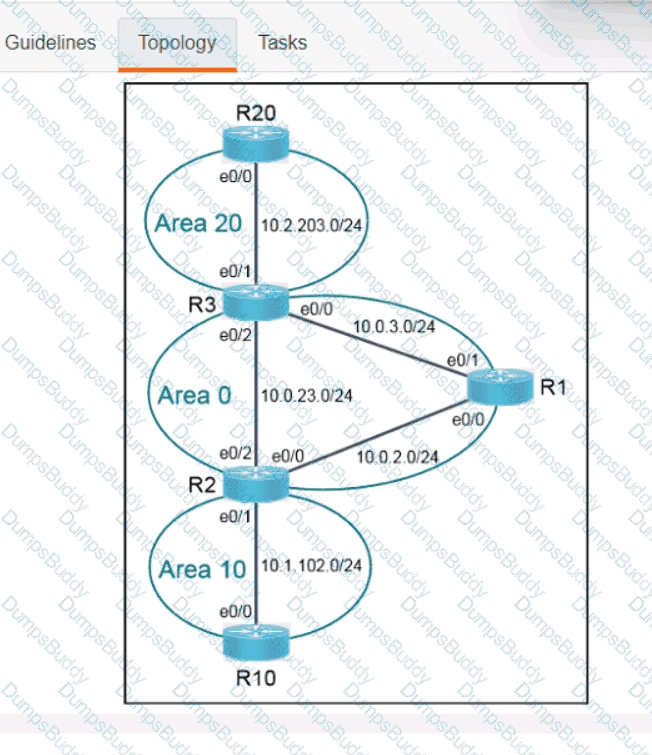
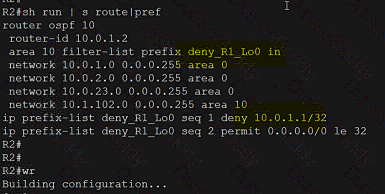
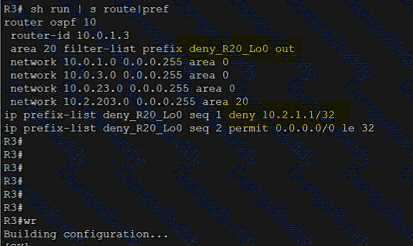
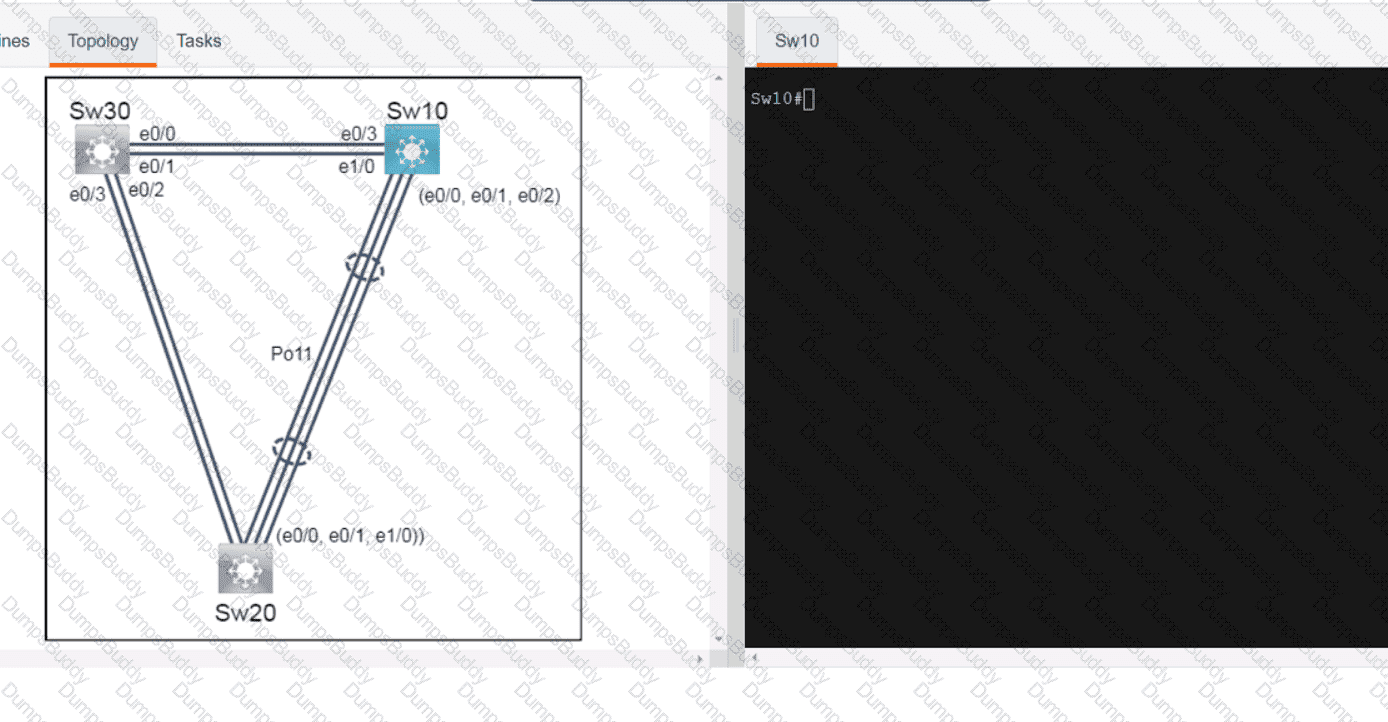
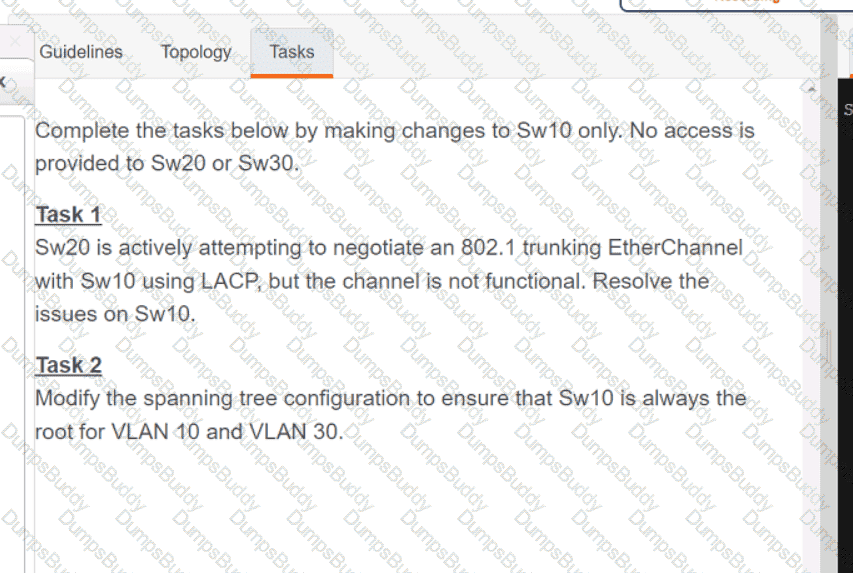
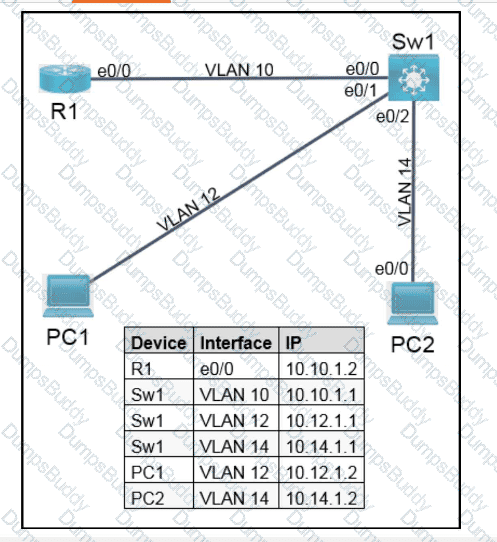
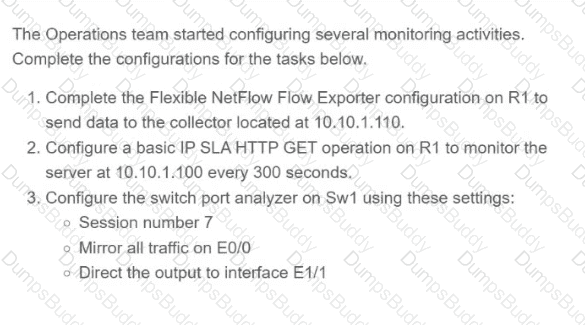
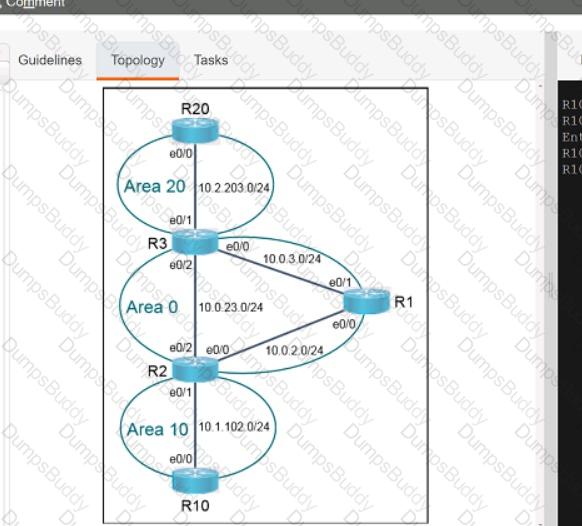
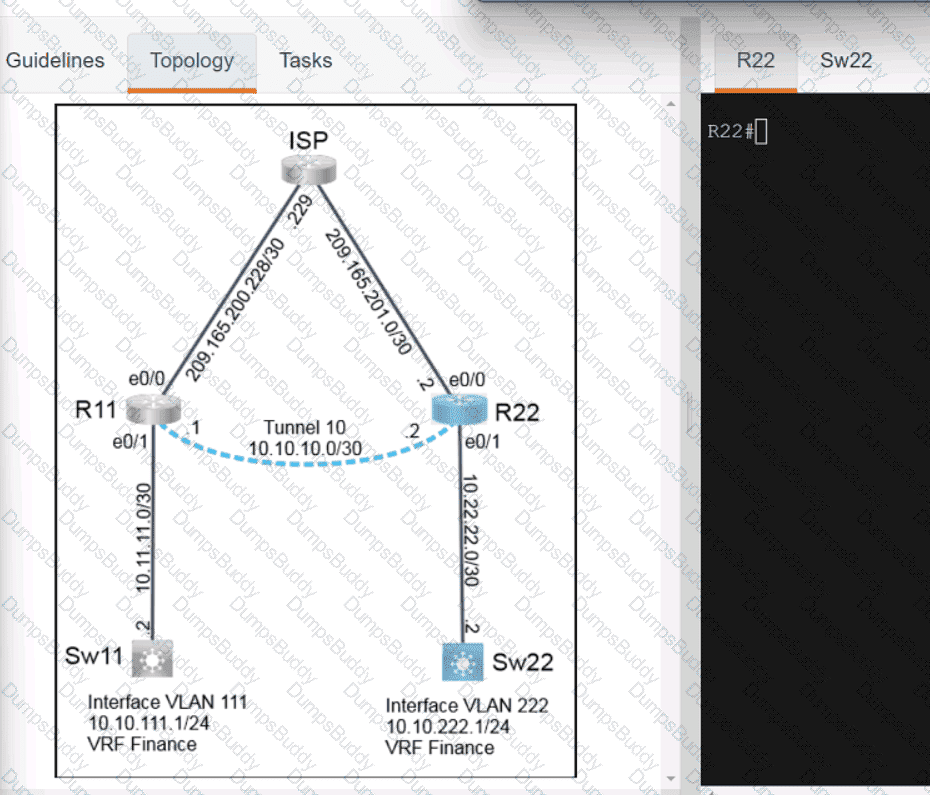
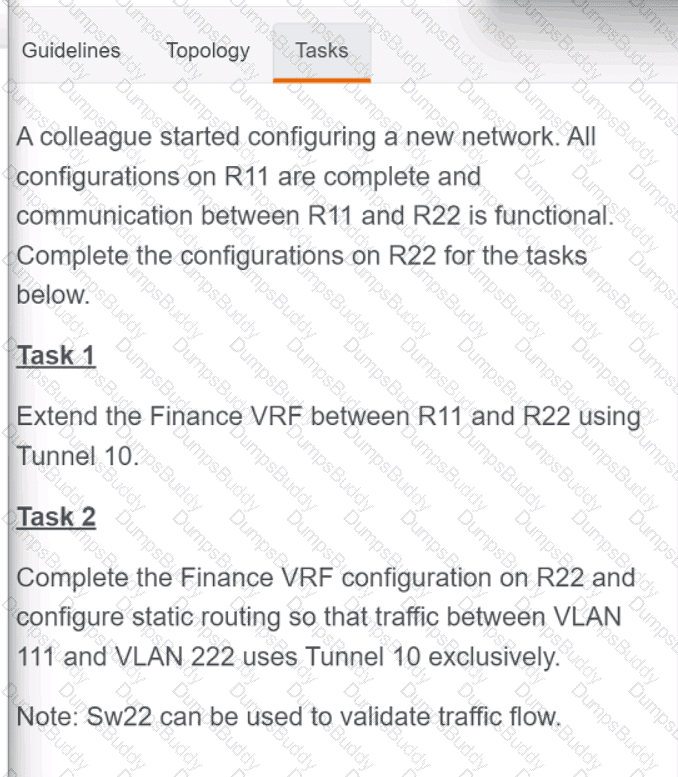
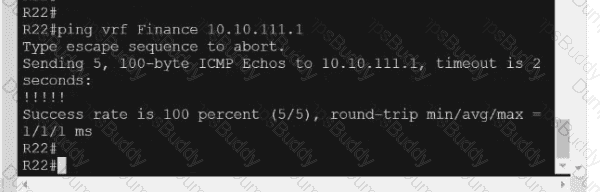
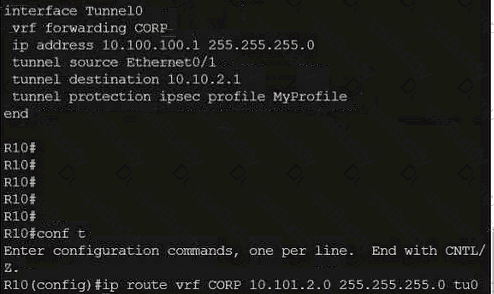
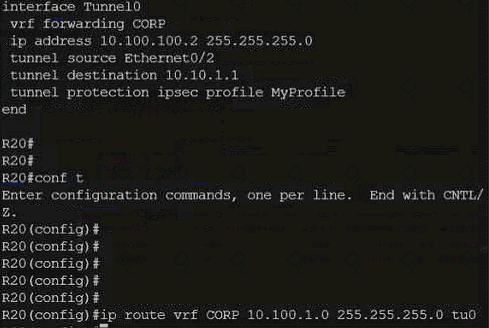
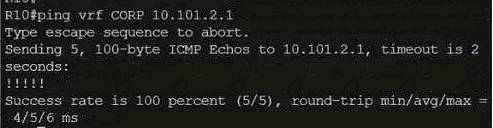
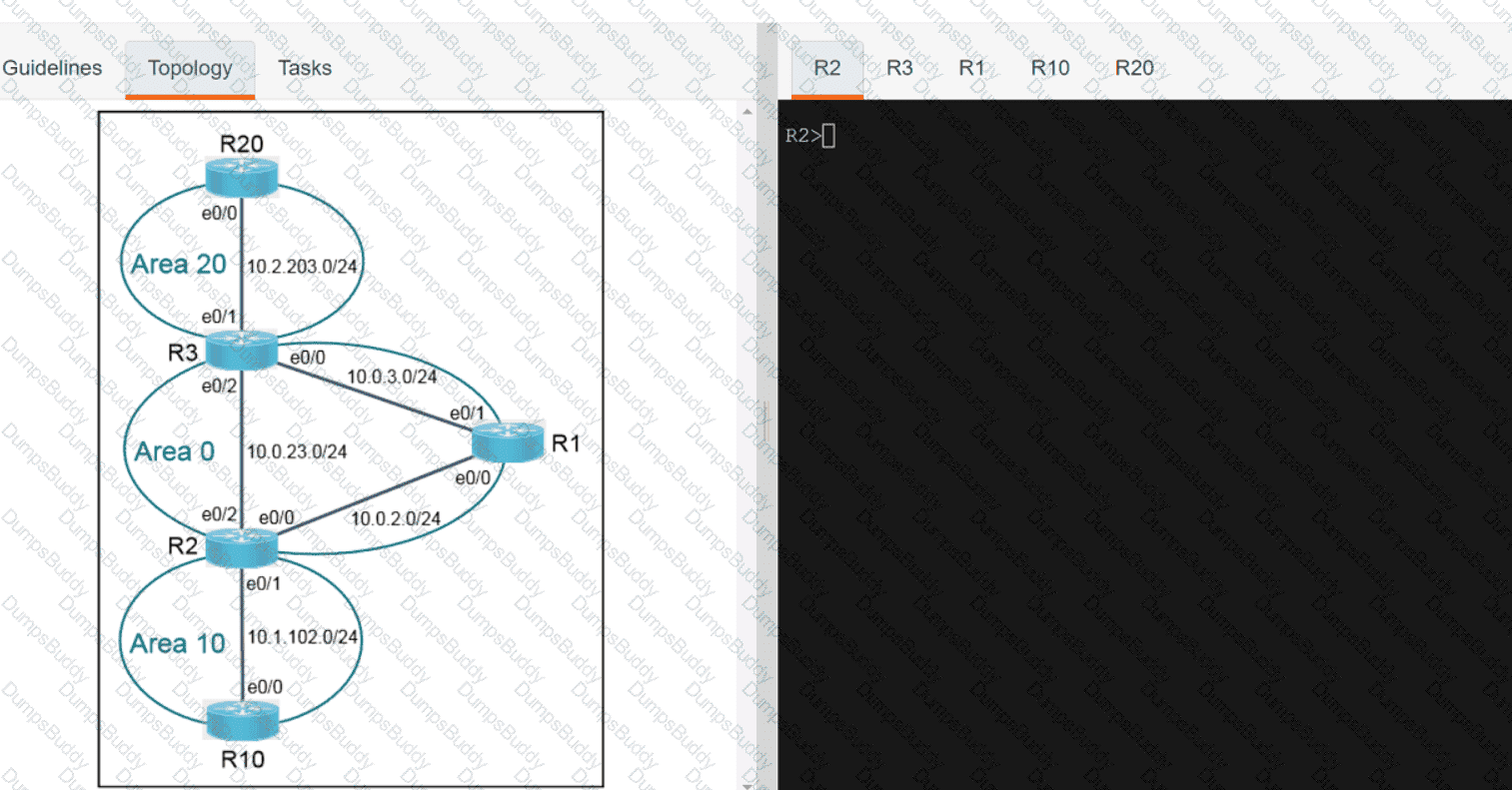
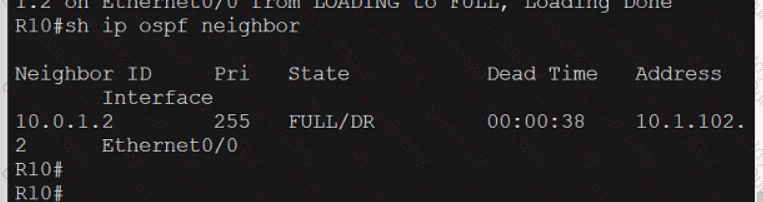
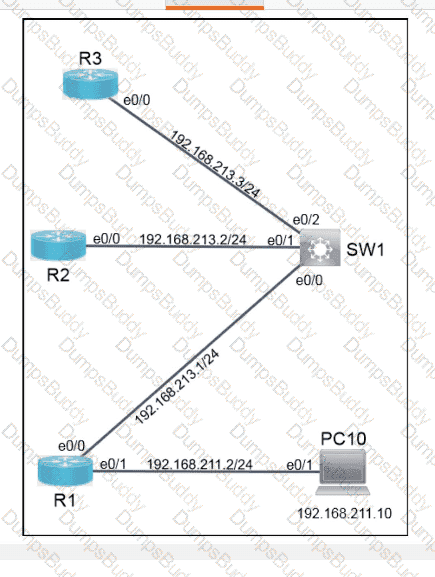
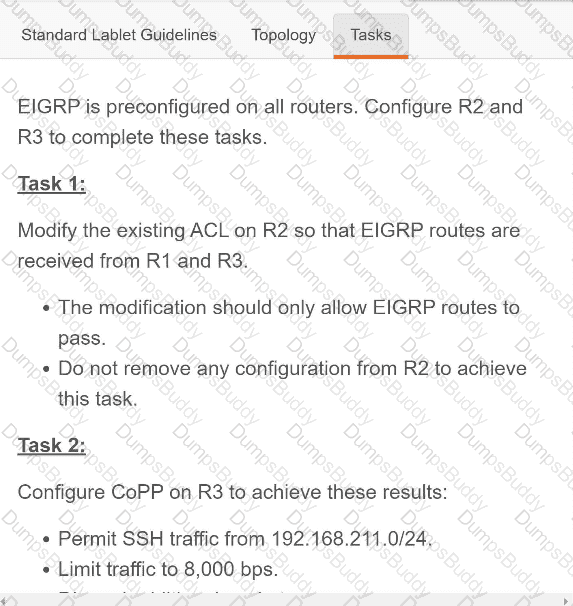
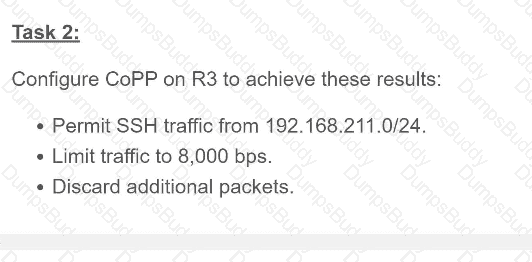
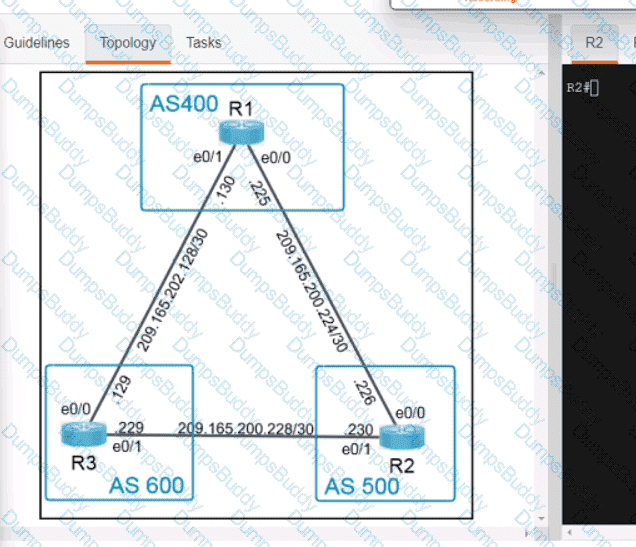
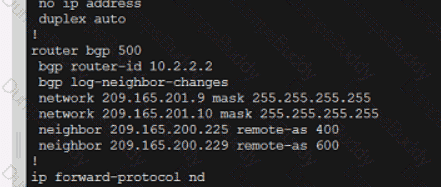
Exhibit.

Security policy requires all idle-exec sessions to be terminated in 600 seconds. Which configuration achieves this goal?
Which network design principle should be followed to improve Layer 2 stability in an enterprise campus design?
What is a characteristic of the Cisco Catalyst Center (formerly DNA Center) Template Editor feature?
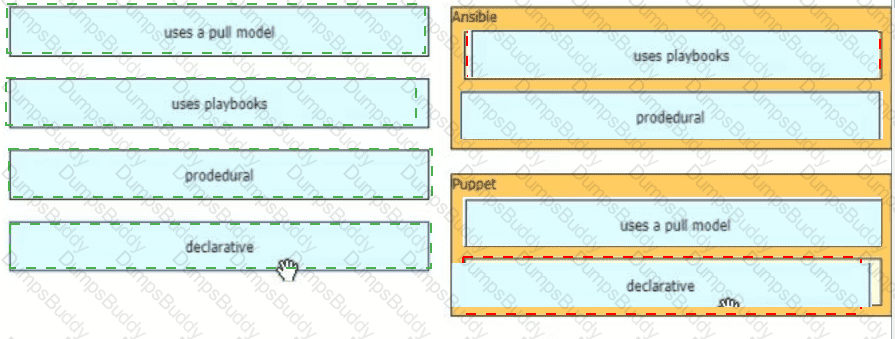
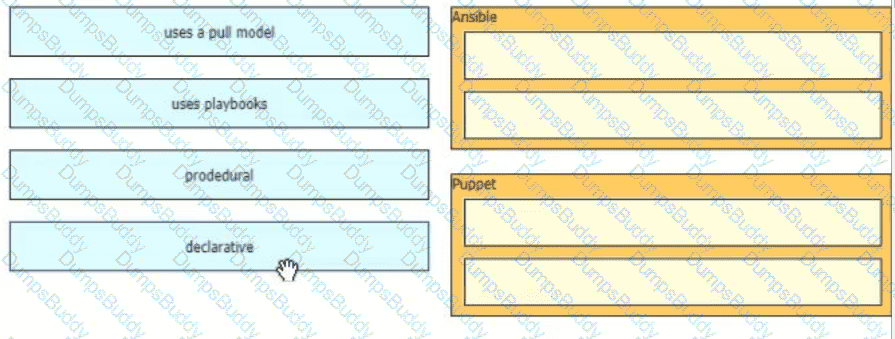
Drag and drop the characteristics from the left onto the orchestration tools that they describe on the right.
A customer has several small branches and wants to deploy a Wi-Fi solution with local management using CAPWAP. Which deployment model meets this requirement?
Which language defines the structure or modelling of data for NETCONF and RESTCONF?