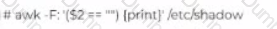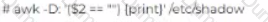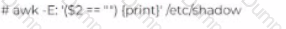312-38 Certified Network Defender (CND) Questions and Answers
Which of the following network security protocols protects from sniffing attacks by encrypting entire communication between the clients and server including user passwords?
Bankofamerica Enterprise is working on an internet and usage policy in a way to control the
internet demand. What group of policy does this belong to?
You are tasked to perform black hat vulnerability assessment for a client. You received official written permission to work with: company site, forum, Linux server with LAMP, where this site is hosted.
Which vulnerability assessment tool should you consider using?
Assume that you are a network administrator and the company has asked you to draft an Acceptable Use Policy (AUP) for employees. Under which category of an information security policy does AUP fall into?
HexCom, a leading IT Company in the USA, realized that their employees were having trouble accessing multiple servers with different passwords. Due to this, the centralized server was also being
overburdened by avoidable network traffic. To overcome the issue, what type of authentication can be given to the employees?
Which of the following helps prevent executing untrusted or untested programs or code from untrusted or unverified third-parties?
Which of the following is not part of the recommended first response steps for network defenders?
Which among the following is used to limit the number of cmdlets or administrative privileges of administrator, user, or service accounts?
John has been working a* a network administrator at an IT company. He wants to prevent misuse of accounts by unauthorized users. He wants to ensure that no accounts have empty passwords. Which of the following commands does John use to list all the accounts with an empty password?
Which type of wireless network attack is characterized by an attacker using a high gain amplifier from a nearby location to drown out the legitimate access point signal?
Identify the network topology where each computer acts as a repeater and the data passes from one computer to the other in a single direction until it reaches the destination.
Which of the following provides a set of voluntary recommended cyber security features to include in network-capable loT devices?
What cryptography technique can encrypt small amounts of data and applies it to digital signatures?
If there is a fire incident caused by an electrical appliance short-circuit, which fire suppressant should be used to control it?
Which type of information security policy addresses the implementation and configuration of technology and user behavior?
Individuals in the organization using system resources against acceptable usage policies indicates which of the following security incident:
Management asked Adam to implement a system allowing employees to use the same credentials to access multiple applications. Adam should implement the--------------------------authentication technique to satisfy the
management request.
Which of the following VPN topologies establishes a persistent connection between an organization's main office and its branch offices using a third-party network or the Internet?
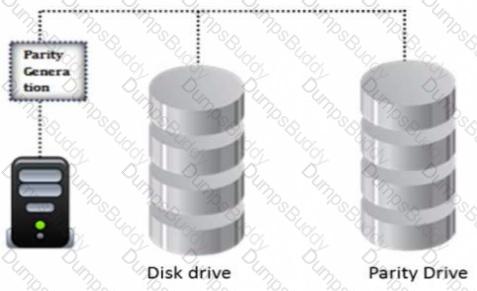
Katie has implemented the RAID level that split data into blocks and evenly write the data to multiple hard drives but does not provide data redundancy. This type of RAID level requires a minimum of________in order to
setup.
Which of the following network security controls can an administrator use to detect, deflect or study attempts to gain unauthorized access to information systems?
Who acts as an intermediary to provide connectivity and transport services between cloud consumers and providers?
John is a network administrator and is monitoring his network traffic with the help of Wireshark. He suspects that someone from outside is making a TCP OS fingerprinting attempt on his organization's network. Which
of the following Wireshark filter(s) will he use to locate the TCP OS fingerprinting attempt?
Which of the following includes examining the probability, impact status, and exposure of risk?
You are using Wireshark to monitor your network traffic and you see a lot of packages with FIN,
PUSH and URG flags activated; what can you infer about this behavior?
Arman transferred some money to his friend’s account using a net banking service. After a few hours, his friend informed him that he hadn’t received the money yet. Arman logged on to the bank’s website to investigate and discovered that the amount had been transferred to an unknown account instead. The bank, upon receiving Arman’s complaint, discovered that someone had established a station between Arman’s and the bank server’s communication system. The station intercepted the communication and inserted another account number replacing his friend’s account number. What is
such an attack called?
Which protocol would the network administrator choose for the wireless network design. If he
needs to satisfy the minimum requirement of 2.4 GHz, 22 MHz of bandwidth, 2 Mbits/s stream for data
rate and use DSSS for modulation.
The network administrator wants to strengthen physical security in the organization. Specifically, to
implement a solution stopping people from entering certain restricted zones without proper credentials.
Which of following physical security measures should the administrator use?
If Myron, head of network defense at Cyberdyne, wants to change the default password policy settings on the company’s Linux systems, which directory should he access?
Which type of risk treatment process Includes not allowing the use of laptops in an organization to ensure its security?
Which of the following provides enhanced password protection, secured loT connections, and encompasses stronger encryption techniques?
James was inspecting ARP packets in his organization's network traffic with the help of Wireshark. He is checking the volume of traffic containing ARP requests as well as the source IP address from which they are
originating. Which type of attack is James analyzing?
Management wants to calculate the risk factor for their organization. Kevin, a network administrator in the organization knows how to calculate the risk factor. Certain parameters are required before calculating risk
factor. What are they? (Select all that apply) Risk factor =.............X...............X...........
The security network team is trying to implement a firewall capable of operating only in the session
layer, monitoring the TCP inter-packet link protocol to determine when a requested session is legitimate
or not. Using the type of firewall,they could be able to intercept the communication, making the
external network see that the firewall is the source, and facing the user, who responds from the outside
is the firewall itself. They are just limiting a requirements previous listed, because they have already
have a packet filtering firewall and they must add a cheap solution that meets the objective. What kind
of firewall would you recommend?
The--------------protocol works in the network layer and is responsible for handling the error codes during the delivery of packets. This protocol is also responsible for providing communication in the TCP/IP stack.
-----------is a group of broadband wireless communications standards for Metropolitan Area Networks (MANs)
Identify the Password Attack Technique in which the adversary attacks cryptographic hash functions based on the probability, that if a hashing process is used for creating a key, then the same is
used for other keys?
Who is responsible for executing the policies and plans required for supporting the information technology and computer systems of an organization?
Which of the following commands can be used to disable unwanted services on Debian, Ubuntu and other Debian-based Linux distributions?
Frank is a network technician working for a medium-sized law firm in Memphis. Frank and two other IT employees take care of all the technical needs for the firm. The firm's partners have asked that a secure wireless
network be implemented in the office so employees can move about freely without being tied to a network cable. While Frank and his colleagues are familiar with wired Ethernet technologies, 802.3, they are not familiar
with how to setup wireless in a business environment. What IEEE standard should Frank and the other IT employees follow to become familiar with wireless?
Which of the following types of information can be obtained through network sniffing? (Select all that apply)
Which of the following interfaces uses hot plugging technique to replace computer components without the need to shut down the system?
James is working as a Network Administrator in a reputed company situated in California. He is monitoring his network traffic with the help of Wireshark. He wants to check and analyze the traffic against a PING sweep
attack. Which of the following Wireshark filters will he use?
The company has implemented a backup plan. James is working as a network administrator for the company and is taking full backups of the data every time a backup is initiated. Alex who is a senior security manager
talks to him about using a differential backup instead and asks him to implement this once a full backup of the data is completed. What is/are the reason(s) Alex is suggesting that James use a differential backup?
(Select all that apply)
John, who works as a team lead in Zen Technologies, found that his team members were accessing social networking sites, shopping sites and watching movies during office hours. He approached the
network admin to block such websites. What kind of network security device can be used to implement John’s decision?
Which of the following defines the extent to which an interruption affects normal business operations and the amount of revenue lost due to that interruption?
Implementing access control mechanisms, such as a firewall, to protect the network is an example of which of the following network defense approach?
Who oversees all the incident response activities in an organization and is responsible for all actions of the IR team and IR function?
Which biometric technique authenticates people by analyzing the layer of blood vessels at the back of their eyes?
Identify the firewall technology that monitors the TCP handshake between the packets to determine whether a requested session is legitimate.
An insider in Hexagon, a leading IT company in USA, was testing a packet crafting tool. This tool
generated a lot of malformed TCP/IP packets which crashed the main server’s operating system leading
to restricting the employees’ accesses. Which attack did the insider use in the above situation?
John wants to implement a firewall service that works at the session layer of the OSI model. The firewall must also have the ability to hide the private network information. Which type of firewall service is John thinking of
implementing?
A network designer needs to submit a proposal for a company, which has just published a web
portal for its clients on the internet. Such a server needs to be isolated from the internal network,
placing itself in a DMZ. Faced with this need, the designer will present a proposal for a firewall with
three interfaces, one for the internet network, another for the DMZ server farm and another for the
internal network. What kind of topology will the designer propose?
Jason has set a firewall policy that allows only a specific list of network services and deny everything else. This strategy is known as a____________.
How does Windows’ in-built security component, AppLocker, whitelist applications?
Which of the following refers to the data that is stored or processed by RAM, CPUs, or databases?
James, a network admin in a large US based IT firm, was asked to audit and implement security
controls over all network layers to achieve Defense-in-Depth. While working on this assignment, James
has implemented both blacklisting and whitelisting ACLs. Which layer of defense-in-depth architecture is
Jason working on currently?
You are an IT security consultant working on a contract for a large manufacturing company to audit their entire network. After performing all the tests and building your report, you present a number of recommendations
to the company and what they should implement to become more secure. One recommendation is to install a network-based device that notifies IT employees whenever malicious or questionable traffic is found. From
your talks with the company, you know that they do not want a device that actually drops traffic completely, they only want notification. What type of device are you suggesting?
Elden is working as a network administrator at an IT company. His organization opted for a virtualization technique in which the guest OS is aware of the virtual environment in which it is running and
communicates with the host machines for requesting resources. Identify the virtualization technique implemented by Elden’s organization.
Fred is a network technician working for Johnson Services, a temporary employment agency in Boston. Johnson Services has three remote offices in New England and the headquarters in Boston where Fred works.
The company relies on a number of customized applications to perform daily tasks and unfortunately these applications require users to be local administrators. Because of this, Fred's supervisor wants to implement
tighter security measures in other areas to compensate for the inherent risks in making those users local admins. Fred's boss wants a solution that will be placed on all computers throughout the company and
monitored by Fred. This solution will gather information on all network traffic to and from the local computers without actually affecting the traffic. What type of solution does Fred's boss want to implement?
Sean has built a site-to-site VPN architecture between the head office and the branch office of his company. When users in the branch office and head office try to communicate with each other, the traffic is
encapsulated. As the traffic passes though the gateway, it is encapsulated again. The header and payload both are encapsulated. This second encapsulation occurs only in the __________implementation of a VPN.
An US-based organization decided to implement a RAID storage technology for their data backup plan. John wants to setup a RAID level that require a minimum of six drives but will meet high fault tolerance and with a
high speed for the data read and write operations. What RAID level is John considering to meet this requirement?
An organization needs to adhere to the______________rules for safeguarding and protecting the electronically stored health information of employees.
Emmanuel works as a Windows system administrator at an MNC. He uses PowerShell to enforce the script execution policy. He wants to allow the execution of the scripts that are signed by a trusted
publisher. Which of the following script execution policy setting this?
Identify the virtualization level that creates a massive pool of storage areas for different virtual machines running on the hardware.
Wallcot, a retail chain in US and Canada, wants to improve the security of their administration
offices. They want to implement a mechanism with two doors. Only one of the doors can be opened at a
time. Once people enter from the first door, they have to be authorized to open the next one. Failing
the authorization, the person will be locked between the doors until an authorized person lets him or
her out. What is such a mechanism called?
Alex is administrating the firewall in the organization's network. What command will he use to check the ports applications open?
John has successfully remediated the vulnerability of an internal application that could have caused a threat to the network. He is scanning the application for the existence of a remediated vulnerability, this process is
called a________and it has to adhere to the_________
Sam wants to implement a network-based IDS in the network. Sam finds out the one IDS solution which works is based on patterns matching. Which type of network-based IDS is Sam implementing?
How can organizations obtain information about threats through human intelligence?
An attacker has access to password hashes of a Windows 7 computer. Which of the following attacks can the attacker use to reveal the passwords?
Michelle is a network security administrator working in an MNC company. She wants to set a
resource limit for CPU in a container. Which command-line allows Michelle to limit a container to 2
CPUs?
Dan and Alex are business partners working together. Their Business-Partner Policy states that they should encrypt their emails before sending to each other. How will they ensure the authenticity of their emails?
Ivan needs to pick an encryption method that is scalable even though it might be slower. He has settled on a method that works where one key is public and the other is private. What encryption method did Ivan settle
on?
John, a network administrator, is configuring Amazon EC2 cloud service for his organization. Identify the type of cloud service modules his organization adopted.
Blake is working on the company's updated disaster and business continuity plan. The last section of the plan covers computer and data incidence response. Blake is outlining the level of severity for each type of
incident in the plan. Unsuccessful scans and probes are at what severity level?
A stateful multilayer inspection firewall combines the aspects of Application level gateway, Circuit level gateway and Packet filtering firewall. On which layers of the OSI model, does the Stateful
multilayer inspection firewall works?
Daniel works as a network administrator in an Information Security company. He has just deployed
an IDS in his organization’s network and wants to calculate the false positive rate for his
implementation. Which of the following formulae can he use to so?
An employee of a medical service company clicked a malicious link in an email sent by an attacker. Suddenly, employees of the company are not able to access billing information or client record as it is
encrypted. The attacker asked the company to pay money for gaining access to their data. Which type of malware attack is described above?
Michelle is a network security administrator working at a multinational company. She wants to provide secure access to corporate data (documents, spreadsheets, email, schedules, presentations, and other enterprise data) on mobile devices across organizations networks without being slowed down and also wants to enable easy and secure sharing of information between devices within an enterprise. Based on the above mentioned requirements, which among the following solution should Michelle implement?
Sam, a network administrator is using Wireshark to monitor the network traffic of the organization. He wants to detect TCP packets with no flag set to check for a specific attack attempt. Which filter will he use to view
the traffic?
Harry has sued the company claiming they made his personal information public on a social networking site in the United States. The company denies the allegations and consulted a/an ______for legal advice to defend
them against this allegation.
James wants to implement certain control measures to prevent denial-of-service attacks against the organization. Which of the following control measures can help James?
Which of the following is a database encryption feature that secures sensitive data by encrypting it in client applications without revealing the encrypted keys to the data engine in MS SQL Server?
Patrick wants to change the file permission of a file with permission value 755 to 744. He used a Linux command chmod [permission Value] [File Name] to make these changes. What will be the change
in the file access?