300-715 Implementing and Configuring Cisco Identity Services Engine (SISE) v4.0 (300-715 SISE) Questions and Answers
Which two components are required for creating a Native Supplicant Profile within a BYOD flow? (Choose two)
A network engineer needs to deploy 802.1x using Cisco ISE in a wired network environment where thin clients download their system image upon bootup using PXE. For which mode must the switch ports be configured?
When creating a policy within Cisco ISE for network access control, the administrator wants to allow different access restrictions based upon the wireless SSID to which the device is connecting. Which policy condition must be used in order to accomplish this?
An administrator needs to allow guest devices to connect to a private network without requiring usernames and passwords. Which two features must be configured to allow for this? (Choose two.)
An engineer needs to configure Cisco ISE Profiling Services to authorize network access for IP speakers that require access to the intercom system. This traffic needs to be identified if the ToS bit is set to 5 and the destination IP address is the intercom system. What must be configured to accomplish this goal?
There is a need within an organization for a new policy to be created in Cisco ISE. It must validate that a specific anti-virus application is not only installed, but running on a machine before it is allowed access to the network. Which posture condition should the administrator configure in order for this policy to work?
What is a difference between RADIUS versus TACACS+ with regards to packet encryption?
What are two components of the posture requirement when configuring Cisco ISE posture? (Choose two)
A company manager is hosting a conference. Conference participants must connect to an open guest SSID and only use a preassigned code that they enter into the guest portal prior to gaining access to the network. How should the manager configure Cisco ISE to accomplish this goal?
A security administrator is using Cisco ISE to create a BYOD onboarding solution for all employees who use personal devices on the corporate network. The administrator generates a Certificate Signing Request and signs the request using an external Certificate Authority server. Which certificate usage option must be selected when importing the certificate into ISE?
Which two probes must be enabled for the ARP cache to function in the Cisco ISE profile service so that a user can reliably bind the IP address and MAC addresses of endpoints? (Choose two.)
An engineer is using the low-impact mode for a phased deployment of Cisco ISE and is trying to connect to the network prior to authentication. Which access will be denied in this?
The Cisco Wireless LAN Controller and guest portal must be set up in Cisco ISE. These configurations were performed:
• configured all the required Cisco Wireless LAN Controller configurations
• added the wireless controller to Cisco ISE network devices
• created an endpoint identity group
• configured credentials to be sent by email
• configured the SMTP server
• configured an authorization profile with redirection to the guest portal and redirected the access control list
• configured an authentication policy for MAB users
• created an authorization policy
Which two components would be required to complete the configuration? (Choose two.)
An administrator has added a new Cisco ISE PSN to their distributed deployment. Which two features must the administrator enable to accept authentication requests and profile the endpoints correctly, and add them to their respective endpoint identity groups? (Choose two )
Which two Cisco ISE deployment models require two nodes configured with dedicated PAN and MnT personas? (Choose two.)
NO: 184
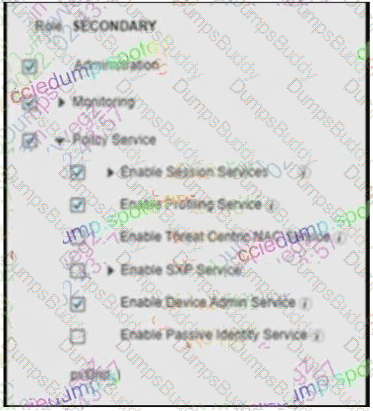
An engineer builds a five-node distributed Cisco ISE deployment The first two deployed nodes are responsible for the primary and secondary administration and monitoring personas Which persona configuration is necessary to have the remaining three Cisco ISE nodes serve as dedicated nodes in the Cisco ISE cube that is responsible only for handling the RADIUS and TACACS+ authentication requests, identity lookups, and policy evaluation?
A)
B)
C)
D)
An engineer wants to learn more about Cisco ISE and deployed a new lab with two nodes. Which two persona configurations allow the engineer to successfully test redundancy of a failed node? (Choose two.)
An administrator is configuring a Cisco ISE posture agent in the client provisioning policy and needs to ensure that the posture policies that interact with clients are monitored, and end users are required to comply with network usage rules Which two resources must be added in Cisco ISE to accomplish this goal? (Choose two)
An engineer deploys Cisco ISE and must configure Active Directory to then use information from Active Directory in an authorization policy. Which two components must be configured, in addition to Active Directory groups, to achieve this goat? (Choose two )
What is an advantage of TACACS+ versus RADIUS authentication when reviewing reports in Cisco ISE?
An engineer is configuring posture assessment for their network access control and needs to use an agent that supports using service conditions as conditions for the assessment. The agent should be run as a background process to avoid user interruption but when it is run. the user can see it. What is the problem?
A network administrator is configuring authorization policies on Cisco ISE There is a requirement to use AD group assignments to control access to network resources After a recent power failure and Cisco ISE rebooting itself, the AD group assignments no longer work What is the cause of this issue?
A Cisco ISE administrator needs to ensure that guest endpoint registrations are only valid for one day When testing the guest policy flow, the administrator sees that the Cisco ISE does not delete the endpoint in the Guest Endpoints identity store after one day and allows access to the guest network after that period. Which configuration is causing this problem?
Refer to the exhibit.
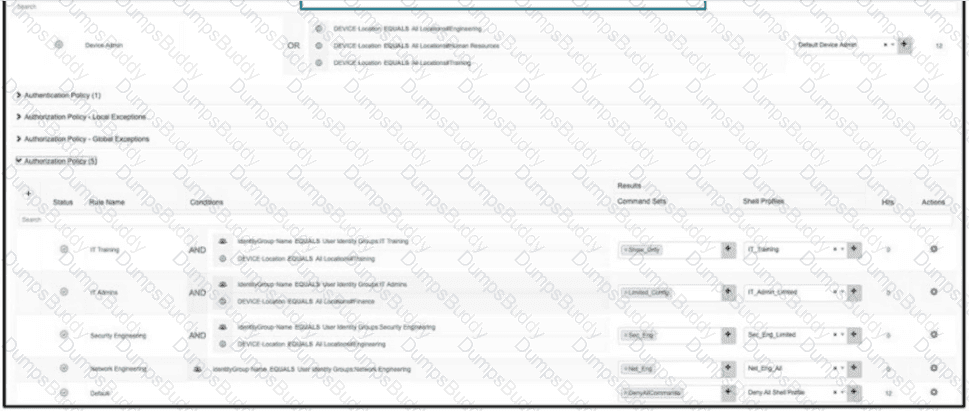
An organization recently implemented network device administration using Cisco ISE. Upon testing the ability to access all of the required devices, a user in the Cisco ISE group IT Admins is attempting to login to a device in their organization's finance department but is unable to. What is the problem?
An engineer is tasked with placing a guest access anchor controller in the DMZ. Which two ports or port sets must be opened up on the firewall to accomplish this task? (Choose two.)
Which two authentication protocols are supported by RADIUS but not by TACACS+? (Choose two.)
An administrator is configuring a Cisco WLC for web authentication Which two client profiling methods are enabled by default if the Apply Cisco ISE Default Settings check box has been selected'? (Choose two.)
An administrator is attempting to join a new node to the primary Cisco ISE node, but receives the error message "Node is Unreachable". What is causing this error?
A Cisco ISE engineer is creating a certificate authentication profile to be used with machine authentication for the network. The engineer wants to be able to compare the user-presented certificate with a certificate stored in Active Directory. What must be done to accomplish this?
A network engineer must create a guest portal for wireless guests on Cisco ISE. The guest users must not be able to create accounts; however, the portal should require a username and password to connect. Which portal type must be created in Cisco ISE to meet the requirements?
An employee logs on to the My Devices portal and marks a currently on-boarded device as ‘Lost’.
Which two actions occur within Cisco ISE as a result oí this action? (Choose two)
NO: 37
In which two ways can users and endpoints be classified for TrustSec?
(Choose Two.)
An engineer is starting to implement a wired 802.1X project throughout the campus. The task is to ensure that the authentication procedure is disabled on the ports but still allows all endpoints to connect to the network. Which port-control option must the engineer configure?
Which Cisco ISE deployment model provides redundancy by having every node in the deployment configured with the Administration. Policy Service, and Monitoring personas to protect from a complete node failure?
Refer to the exhibit.

Which switch configuration change will allow only one voice and one data endpoint on each port?
A network engineer must configure BYOD using Cisco ISE. In the deployment, the users must be able to submit CSR through the end devices. Which two features must be enabled to meet the requirement?
(Choose two.)
A Cisco ISE server sends a CoA to a NAD after a user logs in successfully using CWA Which action does the CoA perform?
A network engineer is configuring guest access and notices that when a guest user registers a second device for access, the first device loses access What must be done to ensure that both devices for a particular user are able to access the guest network simultaneously?
Which three default endpoint identity groups does cisco ISE create? (Choose three)
MacOS users are complaining about having to read through wordy instructions when remediating their workstations to gam access to the network Which alternate method should be used to tell users how to remediate?
TION NO: 33
Which portal is used to customize the settings for a user to log in and download the compliance module?
A laptop was stolen and a network engineer added it to the block list endpoint identity group What must be done on a new Cisco ISE deployment to redirect the laptop and restrict access?
What are two requirements of generating a single signing in Cisco ISE by using a certificate provisioning portal, without generating a certificate request? (Choose two )
An ISE administrator must change the inactivity timer for MAB endpoints to terminate the authentication session whenever a switch port that is connected to an IP phone does not detect packets from the device for 30 minutes. Which action must be taken to accomplish this task?
An engineer is configuring web authentication and needs to allow specific protocols to permit DNS traffic. Which type of access list should be used for this configuration?
A policy is being created in order to provide device administration access to the switches on a network. There is a requirement to ensure that if the session is not actively being used, after 10 minutes, it will be disconnected. Which task must be configured in order to meet this requirement?
An engineer is unable to use SSH to connect to a switch after adding the required CLI commands to the device to enable TACACS+. The device administration license has been added to Cisco ISE, and the required policies have been created. Which action is needed to enable access to the switch?
An engineer is configuring sponsored guest access and needs to limit each sponsored guest to a maximum of two devices. There are other guest services in production that rely on the default guest types. How should this configuration change be made without disrupting the other guest services currently offering three or more guest devices per user?
An administrator must deploy the Cisco Secure Client posture agent to employee endpoints that access a wireless network by using URL redirection in Cisco ISE. The compliance module must be downloaded from Cisco and uploaded to the Cisco ISE client provisioning resource. What must be used to upload the compliance module?
An administrator is configuring a new profiling policy within Cisco ISE The organization has several endpoints that are the same device type and all have the same Block ID in their MAC address. The profiler does not currently have a profiling policy created to categorize these endpoints. therefore a custom profiling policy must be created Which condition must the administrator use in order to properly profile an ACME Al Connector endpoint for network access with MAC address
An engineer must use Cisco ISE profiler services to provide network access to Cisco IP phones that cannot support 802.1X. Cisco ISE is configured to use the access switch device sensor information system-description and platform-type to profile Cisco IP phones and allow access. Which two protocols must be configured on the switch to complete the configuration? (Choose two.)
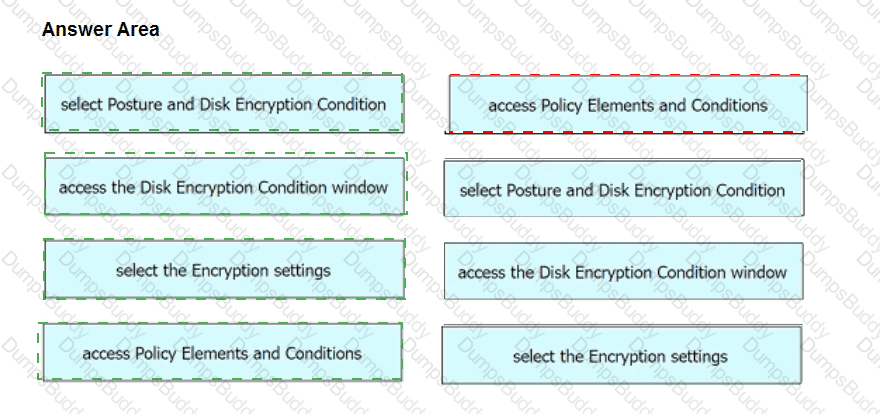
An engineer needs to configure a compliance policy on Cisco ISE to ensure that the latest encryption software is running on the C drive of all endpoints. Drag and drop the configuration steps from the left into the sequence on the right to accomplish this task.
If a user reports a device lost or stolen, which portal should be used to prevent the device from accessing the network while still providing information about why the device is blocked?
A network administrator is currently using Cisco ISE to authenticate devices and users via 802 1X There is now a need to also authorize devices and users using EAP-TLS. Which two additional components must be configured in Cisco ISE to accomplish this'? (Choose two.)
An engineer wants to use certificate authentication for endpoints that connect to a wired network integrated with Cisco ISE. The engineer needs to define the certificate field used as the principal username. Which component would be needed to complete the configuration?
There are several devices on a network that are considered critical and need to be placed into the ISE database and a policy used for them. The organization does not want to use profiling. What must be done to accomplish this goal?
Wireless network users authenticate to Cisco ISE using 802.1X through a Cisco Catalyst switch. An engineer must create an updated configuration to assign a security group tag to the user's traffic using inline tagging to prevent unauthenticated users from accessing a restricted server. The configurations were performed:
• configured Cisco ISE as a Cisco TrustSec AAA server
• configured the switch as a RADIUS device in Cisco ISE
• configured the wireless LAN controller as a TrustSec device in Cisco ISE
• created a security group tog for the wireless users
• created a certificate authentication profile
■ created an identity source sequence
• assigned an appropriate security group tag to the wireless users
• defined security group access control lists to specify an egress policy
• enforced the access control lists on the TrustSec policy matrix in Cisco ISE
• configured TrustSec on the switch
• configured TrustSec on the wireless LAN controller
Which two actions must be taken to complete the configuration? (Choose two.)
What allows an endpoint to obtain a digital certificate from Cisco ISE during a BYOD flow?
A customer wants to set up the Sponsor portal and delegate the authentication flow to a third party for added security while using Kerberos Which database should be used to accomplish this goal?
Which two roles are taken on by the administration person within a Cisco ISE distributed environment? (Choose two.)
Which two task types are included in the Cisco ISE common tasks support for TACACS+ profiles?
(Choose two.)
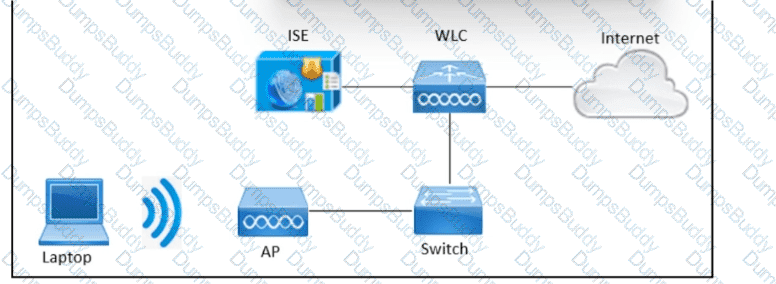
Refer to the exhibit. An engineer needs to configure central web authentication on the Cisco Wireless LAN Controller to use Cisco ISE for all guests connected to the wireless network. The components are configured already:
• Cisco Wireless LAN Controller is fully configured
• authorization profile on the Cisco ISE
• authentication policy on the Cisco ISE
Which component would be configured next on Cisco ISE?
An engineer is implementing network access control using Cisco ISE and needs to separate the traffic based on the network device ID and use the IOS device sensor capability. Which probe must be used to accomplish this task?
Which two features are available when the primary admin node is down and the secondary admin node has not been promoted? (Choose two.)
An engineer is deploying Cisco ISE in a network that contains an existing Cisco Secure Firewall ASA. The customer requested that Cisco TrustSec be configured so that Cisco ISE and the firewall can share SGT information.
Which protocol must be configured on Cisco ISE to meet the requirement?
Which two features should be used on Cisco ISE to enable the TACACS+ feature? (Choose two )
An engineer is creating a new authorization policy to give the endpoints access to VLAN 310 upon successful authentication The administrator tests the 802.1X authentication for the endpoint and sees that it is authenticating successfully What must be done to ensure that the endpoint is placed into the correct VLAN?
What is the maximum number of PSN nodes supported in a medium-sized deployment?
An administrator is configuring a new profiling policy in Cisco ISE for a printer type that is missing from the profiler feed The logical profile Printers must be used in the authorization rule and the rule must be hit. What must be done to ensure that this configuration will be successful^
A Cisco ISE administrator must authenticate users against Microsoft Active Directory. The solution must meet these requirements:
Users and computers must be authenticated.
User groups must be retrieved during authentication.
Which protocol must be added to the allowed protocols on the policy to authenticate the users?
Refer to the exhibit.
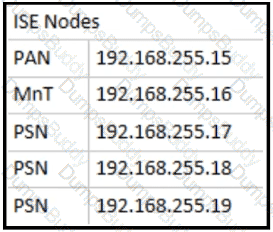
Which two configurations are needed on a catalyst switch for it to be added as a network access device in a Cisco ISE that is being used for 802 1X authentications? (Choose two )

A Cisco ISE administrator must restrict specific endpoints from accessing the network while in closed mode. The requirement is to have Cisco ISE centrally store the endpoints to restrict access from. What must be done to accomplish this task''
An administrator needs to add a new third party network device to be used with Cisco ISE for Guest and BYOD authorizations. Which two features must be configured under Network Device Profile to achieve this? (Choose two.)
Which two methods should a sponsor select to create bulk guest accounts from the sponsor portal? (Choose two )
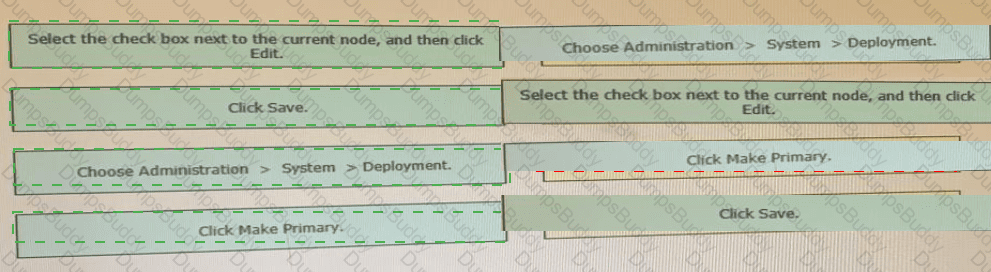
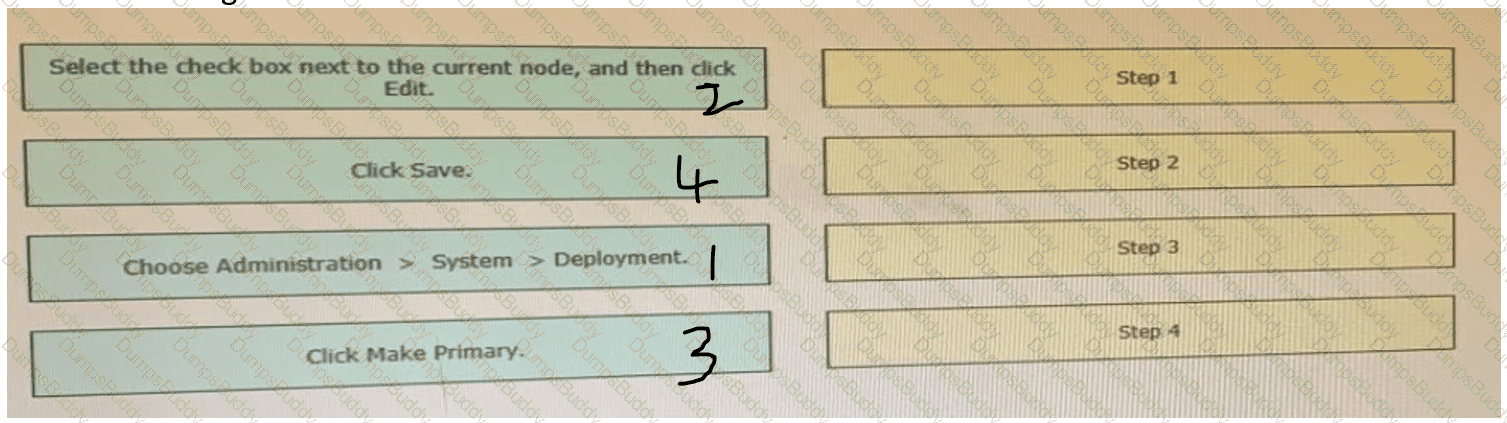
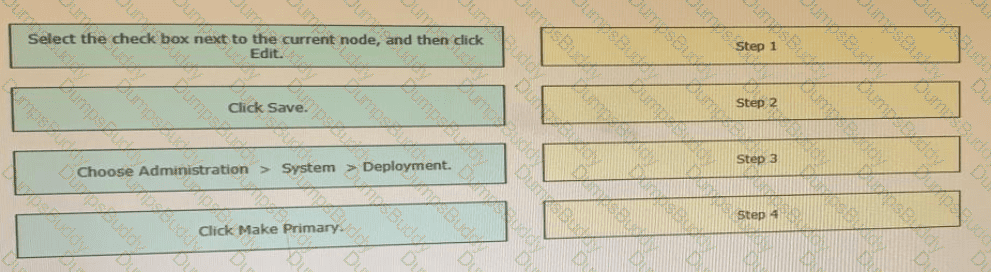
Drag the steps to configure a Cisco ISE node as a primary administration node from the left into the correct order on the night.
In a standalone Cisco ISE deployment, which two personas are configured on a node? (Choose two )