300-710 Securing Networks with Cisco Firepower (300-710 SNCF) Questions and Answers
An engineer is configuring multiple Cisco FTD appliances (or use in the network. Which rule must the engineer follow while defining interface objects in Cisco FMC for use with interfaces across multiple devices?
An engineer must configure high availability for the Cisco Firepower devices. The current network topology does not allow for two devices to pass traffic concurrently. How must the devices be implemented in this environment?
A cisco Secure firewall Threat Defence device is configured in inline IPS mode to inspect all traffic that passes through the interfaces in the inline set. Which setting in the inline set configuration must be connected to allow traffic to pass through uninterrupted when VDB updates are being applied?
An engineer must define a URL object on Cisco FMC. What is the correct method to specify the URL without performing SSL inspection?
An engineer wants to perform a packet capture on the Cisco FTD to confirm that the host using IP address 192 168.100.100 has the MAC address of 0042 7734.103 to help troubleshoot aconnectivity issue What is the correct tcpdump command syntax to ensure that the MAC address appears in the packet capture output?
There is an increased amount of traffic on the network and for compliance reasons, management needs visibility into the encrypted traffic What is a result of enabling TLS'SSL decryption to allow this visibility?
An engineer currently has a Cisco FTD device registered to the Cisco FMC and is assigned the address of 10 10.50.12. The organization is upgrading the addressing schemes and there is a requirement to convert the addresses to a format that provides an adequate amount of addresses on the network What should the engineer do to ensure that the new addressing takes effect and can be used for the Cisco FTD to Cisco FMC connection?
An engineer is investigating connectivity problems on Cisco Firepower for a specific SGT. Which command allows the engineer to capture real packets that pass through the firewall using an SGT of 64?
Network users are experiencing Intermittent issues with internet access. An engineer ident med mat the issue Is being caused by NAT exhaustion. How must the engineer change the dynamic NAT configuration to provide internet access for more users without running out of resources?
Which two OSPF routing features are configured in Cisco FMC and propagated to Cisco FTD? (Choosetwo.)
A security engineer needs to configure a network discovery policy on a Cisco FMC appliance and prevent excessive network discovery events from overloading the FMC database? Which action must be taken to accomplish this task?
An engineer must permit SSH on the inside interface of a Cisco Secure Firewall Threat Defense device. SSH is currently permitted only on the management interface. Which type of policy
must the engineer configure?
A network engineer detects a connectivity issue between Cisco Secure Firewall Management Center and Cisco Secure Firewall Threat Defense. Initial troubleshooting indicates that heartbeats and events are not being received. The engineer re-establishes the secure channels between both peers. Which two commands must the engineer run to resolve the issue? (Choose two.)
An engineer has been tasked with using Cisco FMC to determine if files being sent through the network are malware. Which two configuration tasks must be performed to achieve this file lookup? (Choose two).
When using Cisco Threat Response, which phase of the Intelligence Cycle publishes the results of the investigation?
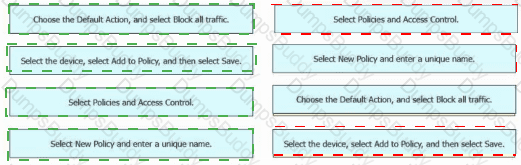
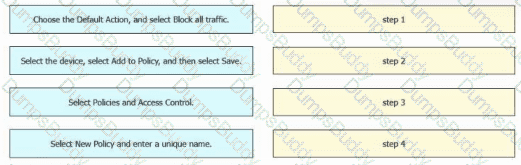
An engineer must create a basic access control policy in the Cisco Secure Firewall Management Center to block all traffic by default. Drag and drop the configuration actions from the left into sequence on the right.
What is the result of specifying of QoS rule that has a rate limit that is greater than the maximum throughput of an interface?
A network engineer implements a new Cisco Firepower device on the network to take advantage of its intrusion detection functionality. There is a requirement to analyze the traffic going across the device, alert on any malicious traffic, and appear as a bump in the wire How should this be implemented?
An engineer must deploy a Cisco FTD device. Management wants to examine traffic without requiring network changes that will disrupt end users. Corporate security policy requires the separation of management traffic from data traffic and the use of SSH over Telnet for remote administration. How must the device be deployed to meet these requirements?
An engineer is configuring two new Cisco Secure Firewall Threat Defense devices to replace the existing firewalls. Network traffic must be analyzed for intrusion events without impacting the traffic. What must the engineer implement next to accomplish the goal?
A network security engineer must replace a faulty Cisco FTD device in a high availability pair. Which action must be taken while replacing the faulty unit?
A network administrator wants to block traffictoa known malware site athttps://www.badsite.comand all subdomains while ensuring no packets from any internal client are sent to that site. Which type of policy must the network administrator use to accomplish this goal?
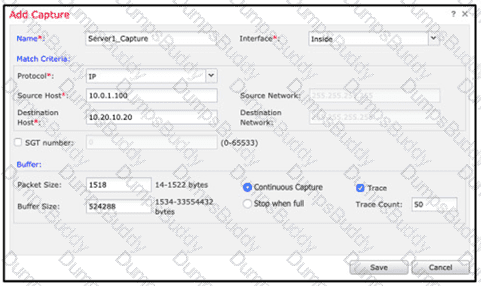
An engineer is troubleshooting a device that cannot connect to a web server. The connection is initiated from the Cisco FTD inside interface and attempting to reach 10.0.1.100 over the non-standard port of 9443 The host the engineer is attempting the connection from is at the IP address of 10.20.10.20. In order to determine what is happening to the packets on the network, the engineer decides to use the FTD packet capture tool Which capture configuration should be used to gather the information needed to troubleshoot this issue?
A)
B)
C)
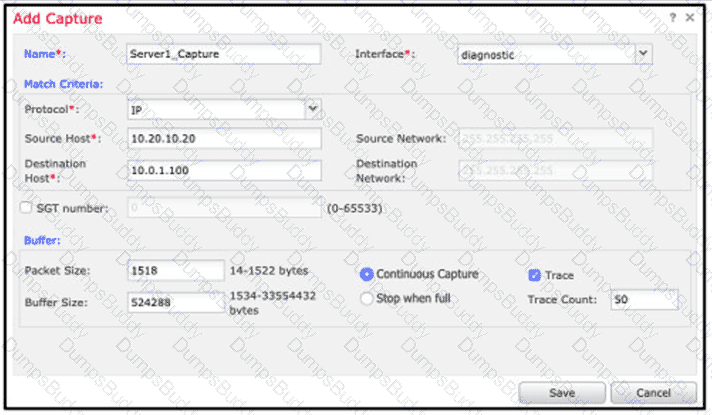
D)
A security engineer is configuring a remote Cisco FTD that has limited resources and internet bandwidth. Which malware action and protection option should be configured to reduce the requirement for cloud lookups?
A network administrator is configuring an FTD in transparent mode. A bridge group is set up and an access policy has been set up to allow all IP traffic. Traffic is not passing through the FTD. What additional configuration is needed?
A network administrator is deploying a Cisco IPS appliance and needs it to operate initially without affecting traffic flows.
It must also collect data to provide a baseline of unwanted traffic before being reconfigured to drop it. Which Cisco IPS mode meets these requirements?
A network administrator notices that inspection has been interrupted on all non-managed interfaces of a device. What is the cause of this?
An administrator is working on a migration from Cisco ASA to the Cisco FTD appliance and needs to test the rules without disrupting the traffic. Which policy type should be used to configure the ASA rules during this phase of the migration?
A Cisco FMC administrator wants to configure fastpathing of trusted network traffic to increase performance. In which type of policy would the administrator configure this feature?
A network engineer must monitor threat events from the console of Cisco Secure Firewall Management Center. The engineer integrates the Cisco Secure Firewall Malware Defense in Secure Firewall Management Center. Which action must the engineer take next?
Refer to the exhibit.
An engineer is modifying an access control policy to add a rule to Inspect all DNS traffic that passes it making the change and deploying the policy, they see that DNS traffic Is not being Inspected by the Snort engine. What is......
An administrator is optimizing the Cisco FTD rules to improve network performance, and wants to bypass inspection for certain traffic types to reduce the load on the Cisco FTD. Which policy must be configured to accomplish this goal?
How should a high-availability pair of Cisco Secure Firewall Threat Defense Virtual appliances be deployed to Cisco Secure Firewall Management Center?
An engineer integrates Cisco FMC and Cisco ISE using pxGrid. Which role is assigned for Cisco FMC?
A network administrator is configuring a Cisco AMP public cloud instance and wants to capture infections and polymorphic variants of a threat to help detect families of malware. Which detection engine meets this requirement?
An engineer is configuring Cisco FMC and wants to limit the time allowed for processing packets through the interface However if the time is exceeded the configuration must allow packets to bypass detection What must be configured on the Cisco FMC to accomplish this task?
Which CLI command is used to generate firewall debug messages on a Cisco Firepower?
What is the advantage of having Cisco Firepower devices send events to Cisco Threat response via the security services exchange portal directly as opposed to using syslog?
Which two conditions must be met to enable high availability between two Cisco FTD devices? (Choose two.)
An engineer must configure a Cisco FMC dashboard in a child domain. Which action must be taken so that the dashboard is visible to the parent domain?
A security engineer found a suspicious file from an employee email address and is trying to upload it for analysis, however the upload is failing. The last registration status is still active. What is the cause for this issue?
A network administrator needs to create a policy on Cisco Firepower to fast-path traffic to avoid Layer 7 inspection. The rate at which traffic is inspected must be optimized. What must be done to achieve this goal?
A network engineer must provide redundancy between two Cisco FTD devices. The redundancy configuration must include automatic configuration, translation, and connection updates. After the initial configuration of the two appliances, which two steps must be taken to proceed with the redundancy configuration? (Choose two.)
An engineer must integrate a thud-party security Intelligence teed with Cisco Secure Firewall Management Center. Secure Firewall Management Center is running Version 6.2 3 and has 8 GB of memory. Which two actions must be taken to implement Throat Intelligence Director? (Choose two.)
Which limitation applies to Cisco Firepower Management Center dashboards in a multidomain environment?
A software development company hosts the website http:dev.company.com for contractors to share code for projects they are working on with internal developers. The web server is on premises and is protected by a Cisco Secure Firewall Threat Defense appliance. The network administrator is worried about someone trying to transmit infected files to internal users via this site. Which type of policy must be able associated with an access control policy to enable Cisco Secure Firewall Malware Defense to detect and block malware?
An organization is using a Cisco FTD and Cisco ISE to perform identity-based access controls. A network administrator is analyzing the Cisco FTD events and notices that unknown user traffic is being allowed through the firewall. How should this be addressed to block the traffic while allowing legitimate user traffic?
An engineer is setting up a new Cisco Secure Firewall Threat Defense appliance to replace the current firewall. The company requests that inline sets be used and that when one interface in
an inline set goes down, the second interface in the inline set goes down. What must the engineer configure to meet the deployment requirements?
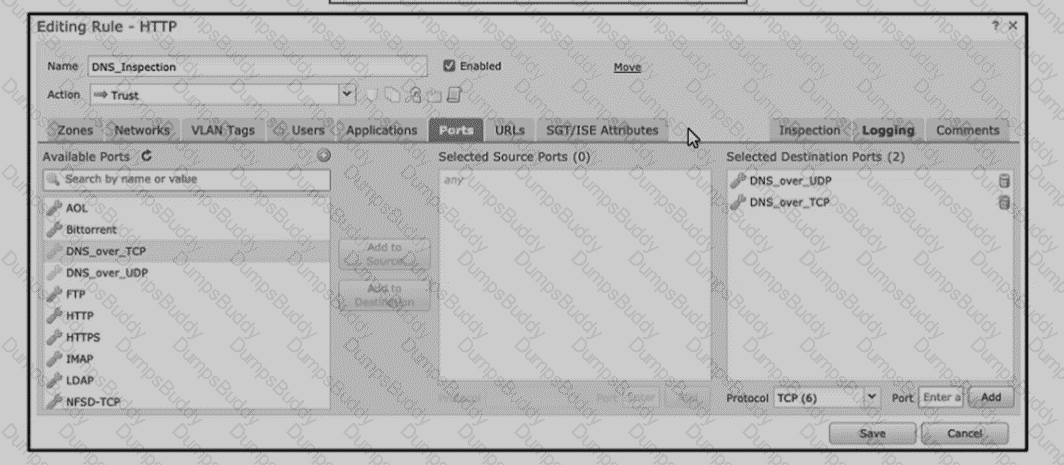
Refer to the exhibit An engineer is modifying an access control pokey to add a rule to inspect all DNS traffic that passes through the firewall After making the change and deploying thepokey they see that DNS traffic is not bang inspected by the Snort engine What is the problem?
A network administrator is reviewing a monthly advanced malware risk report and notices a host that Is listed as CnC Connected. Where must the administrator look within Cisco FMC to further determine if this host is infected with malware?
An engineer attempts to pull the configuration for a Cisco FTD sensor to review with Cisco TAC but does not have direct access to the CU for the device. The CLl for the device is managed by Cisco FMC to which the engineer has access. Which action in Cisco FMC grants access to the CLl for the device?
An engineer is integrating Cisco Secure Endpoint with Cisco Secure Firewall Management Center in high availability mode. Malware events detected by Secure Endpoint must also be
received by Secure Firewall Management Center and public cloud services are used. Which two configurations must be selected on both high availability peers independently? (Choose two.)
An engineer is configuring a custom intrusion rule on Cisco FMC. The engineer needs the rule to search the payload or stream for the string "|45 5* 26 27 4 0A|*. Which Keyword must the engineer use with this stung lo create an argument for packed inspection?
An engineer configures a network discovery policy on Cisco FMC. Upon configuration, it is noticed that excessive and misleading events filing the database and overloading the Cisco FMC. A monitored NAT device is executing multiple updates of its operating system in a short period of time. What configurationchange must be made to alleviate this issue?
Which feature sets up multiple interfaces on a Cisco Secure Firewall Threat Defense to be on the same subnet?
A company is in the process of deploying intrusion prevention with Cisco FTDs managed by a Cisco FMC. An engineer must configure policies to detect potential intrusions but not block the suspicious traffic. Which action accomplishes this task?
A network administrator notices that remote access VPN users are not reachable from inside the network. It is determined that routing is configured correctly, however return traffic is entering the firewall but not leaving it What is the reason for this issue?
Which action must be taken on the Cisco FMC when a packet bypass is configured in case the Snort engine is down or a packet takes too long to process?
An engineer must configure email notifications on Cisco Secure Firewall Management Center. TLS encryption must be used to protect the messages from unauthorized access. The engineer adds the IP address of the mail relay host and must set the port number. Which TCP port must the engineer use?
When a Cisco FTD device is configured in transparent firewall mode, on which two interface types can an IP address be configured? (Choose two.)
Which Cisco Advanced Malware Protection for Endpoints policy is used only for monitoring endpoint actively?
The network administrator wants to enhance the network security posture by enabling machine learning tor malware detection due to a concern with suspicious Microsoft executable file types that were seen while creating monthly security reports for the CIO. Which feature must be enabled to accomplish this goal?
An engineer must investigate a connectivity issue from an endpoint behind a Cisco FTD device and a public DNS server. The endpoint cannot perform name resolution queries. Which action must the engineer perform to troubleshoot the issue by simulating real DNS traffic on the Cisco FTD while verifying the Snarl verdict?
An administrator receives reports that users cannot access a cloud-hosted web server. The access control policy was recently updated with several new policy additions and URL filtering. What must be done to troubleshoot the issue and restore access without sacrificing the organization's security posture?
An engineer has been tasked with providing disaster recovery for an organization's primary Cisco FMC. What must be done on the primary and secondary Cisco FMCs to ensure that a copy of the original corporate policy is available if the primary Cisco FMC fails?
An engineer is deploying a Cisco Secure Firewall Management Center appliance. The company must send data to Cisco Secure Network Analytics appliances. Which two actions must the engineer take? (Choose two.)
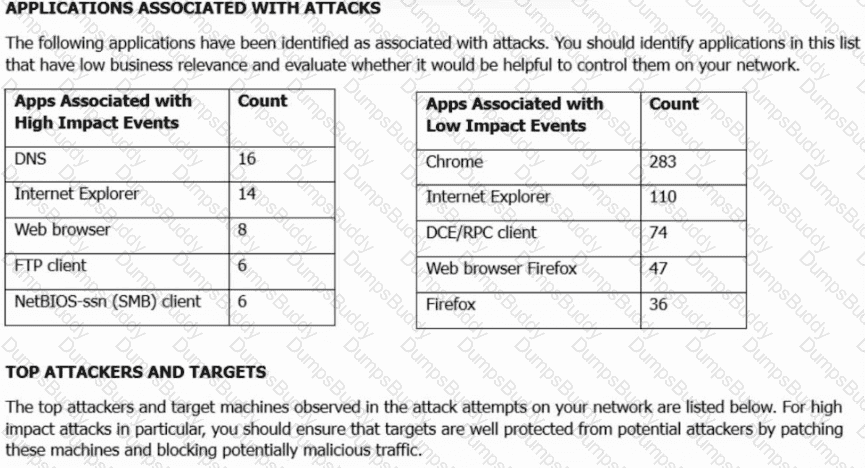
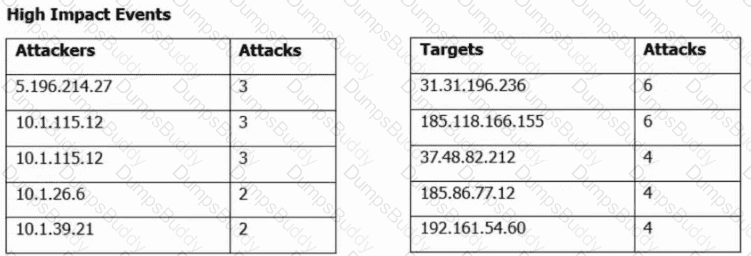
Refer to the exhibit. A security engineer must improve security in an organization and is producing a risk mitigation strategy to present to management for approval. Which action must the security engineer take based on this Attacks Risk Report?
An engineer is monitoring network traffic from their sales and product development departments, which are on two separate networks What must be configured in order to maintain data privacy for both departments?
An organization is migrating their Cisco ASA devices running in multicontext mode to Cisco FTD devices. Which action must be taken to ensure that each context on the Cisco ASA is logically separated in the Cisco FTD devices?
An engineer must implement Cisco Secure Firewall transparent mode due to a new server recently being added that must communicate with an existing server that is currently separated by the firewall. Which implementation action must be taken next by the engineer to accomplish the goal?
An administrator is adding a new URL-based category feed to the Cisco FMC for use within the policies. The intelligence source does not use STIX. but instead uses a .txt file format. Which action ensures that regular updates are provided?
Which Cisco Rapid Threat Containment mitigation action is enabled by integrating pxGrid Adaptive Network Control with Cisco ISE and Cisco Secure Firewall Management Center?
An engineer is reviewing a ticket that requests to allow traffic for some devices that must connect to a server over 8699/udp. The request mentions only one IP address, 172.16.18.15, but the requestor asked for the engineer to open the port for all machines that have been trying to connect to it over the last week. Which action must the engineer take to troubleshoot this issue?
A network administrator is migrating from a Cisco ASA to a Cisco FTD.
EIGRP is configured on the Cisco ASA but it is not available in the Cisco FMC.
Which action must the administrator take to enable this feature on the Cisco FTD?
An engineer defines a new rule while configuring an Access Control Policy. After deploying the policy, the rule is not working as expected and the hit counters associated with the rule are showing zero. What is causing this error?
A network administrator must create an EtherChannel Interface on a new Cisco Firepower 9300 appliance registered with an FMC tor high availability. Where must the administrator create the EtherChannel interface?
Which command is run on an FTD unit to associate the unit to an FMC manager that is at IP address 10.0.0.10, and that has the registration key Cisco123?
A network engineer detects a connectivity issue between Cisco Secure Firewall Management Centre and Cisco Secure Firewall Threat Defense Initial troubleshooting indicates that heartbeats and events not being received. The engineer re-establishes the secure channels between both peers Which two commands must the engineer run to resolve the issue? (Choose two.)
IT management is asking the network engineer to provide high-level summary statistics of the Cisco FTD appliance in the network. The business is approaching a peak season so the need to maintain business uptime is high. Which report type should be used to gather this information?
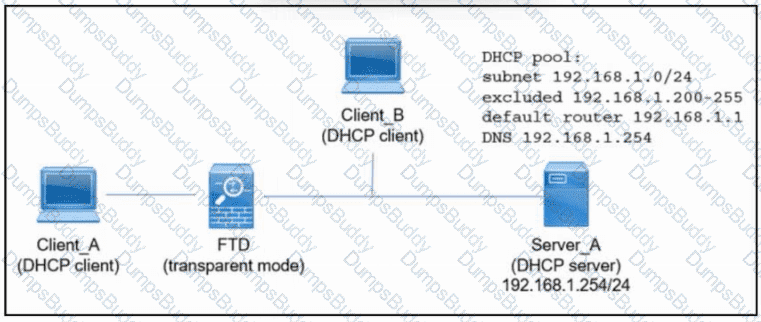
Refer to the exhibit. An engineer is deploying a new instance of Cisco Secure Firewall Threat Defense. Which action must the engineer take next so that Client_A and Client_B receive an IP address via DHCP from Server_A?
An engineer is tasked with deploying an internal perimeter firewall that will support multiple DMZs Each DMZ has a unique private IP subnet range. How is this requirement satisfied?
Refer to the exhibit.
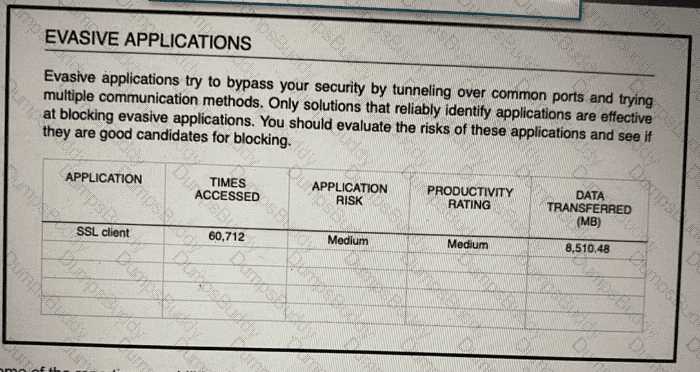
An administrator is looking at some of the reporting capabilities for Cisco Firepower and noticed this section of the Network Risk report showing a lot of SSL activity that cloud be used for evasion. Which action will mitigate this risk?
An engineer is reviewing an existing custom server fingerprint on a Cisco Secure Firewall because the current information is inaccurate. Which action must the engineer take to improve the accuracy of the network discovery rules?
An engineer wants to add an additional Cisco FTD Version 6.2.3 device to their current 6.2.3 deployment to create a high availability pair.
The currently deployed Cisco FTD device is using local management and identical hardware including the available port density to enable the failover and stateful links required in a proper high availability deployment. Which action ensures that the environment is ready to pair the new Cisco FTD with the old one?
An administrator configures the interfaces of a Cisco Secure Firewall Threat Defence device in an inline IPS deployment. The administrator completes these actions:
* identifies the device and the interfaces
* sets the interface mode to inline
* enables the interlaces
Which configuration step must the administrator take next to complete the implementation?
When creating a report template, how can the results be limited to show only the activity of a specific subnet?
A network administrator is configuring an instance of Cisco Secure Firewall Threat Defense, which is registered to Cisco Secure Firewall Management Center, to prevent internal users from downloading executable files from the internet. What must be created and configured by the administrator to meet the requirement?
A company has many Cisco FTD devices managed by a Cisco FMC. The security model requires that access control rule logs be collected for analysis. The security engineer is concerned that the Cisco FMC will not be able to process the volume of logging that will be generated. Which configuration addresses this concern?
Which protocol establishes network redundancy in a switched Firepower device deployment?
An engineer must investigate a connectivity issue and decides to use the packet capture feature on Cisco FTD. The goal is to see the real packet going through the Cisco FTD device and see the Snort detection actions as a part of the output. After the capture-traffic command is issued, only the packets are displayed. Which action resolves this issue?
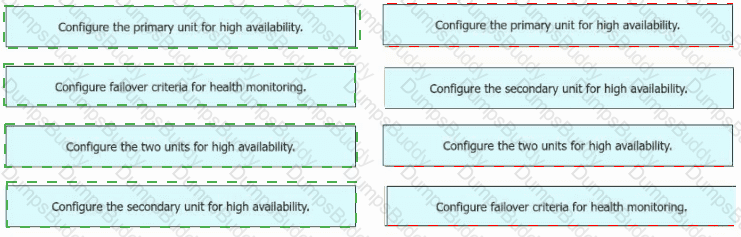
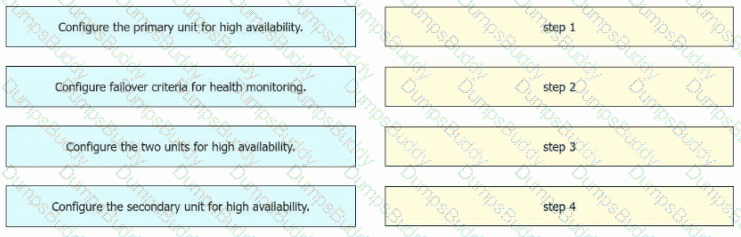
An engineer must configure high availability on two Cisco Secure Firewall Threat Defense appliances. Drag and drop the configuration steps from the left into the sequence on the right.
Which firewall mode is Cisco Secure Firewall Threat Defense in when two physical interfaces are assigned to a named BVI?
A network administrator wants to configure a Cisco Secure Firewall Threat Defense instance managed by Cisco Secure Firewall Management Center to block traffic to known cryptomning networks. Which system settings must the administrator configure in Secure Firewall Management Center to meet the requirement?
What is the disadvantage of setting up a site-to-site VPN in a clustered-units environment?
An engineer is working on a LAN switch and has noticed that its network connection to the mime Cisco IPS has gone down Upon troubleshooting it is determined that the switch is working as expected What must have been implemented for this failure to occur?
An engineer is restoring a Cisco FTD configuration from a remote backup using the command restore remote-manager-backup location 1.1.1.1 admin /volume/home/admin BACKUP_Cisc394602314.zip on a Cisco FMG. After connecting to the repository, an error occurred that prevents the FTD device from accepting the backup file. What is the problem?
The event dashboard within the Cisco FMC has been inundated with low priority intrusion drop events, which are overshadowing high priority events. An engineer has been tasked with reviewing the policies and reducing the low priority events. Which action should be configured to accomplish this task?
A security engineer must create a malware and file policy on a Cisco Secure Firewall Threat Defense device. The solution must ensure that PDF. DOCX, and XLSX files are not sent lo Cisco Secure Malware analytics. What must do configured to meet the requirements''
A security engineer must integrate an external feed containing STIX/TAXII data with Cisco FMC. Which feature must be enabled on the Cisco FMC to support this connection?
An engineer must export a packet capture from Cisco Secure Firewall Management Center to assist in troubleshooting an issue an a Secure Firewall Threat Defense device. When the engineer navigates to URL for Secure Firewall Management Center at:
..
An engineer receives a 403: Forbidden error instead of being provided with the PCAP file. Which action resolves the issue?
An engineer is configuring Cisco Secure Firewall Threat Defense managed by a Secure Firewall Management Center appliance. The company wants remote access VPN users to be reachable from the inside network. What must the engineer configure to meet the requirements?