300-620 Implementing Cisco Application Centric Infrastructure (300-620 DCACI) Questions and Answers
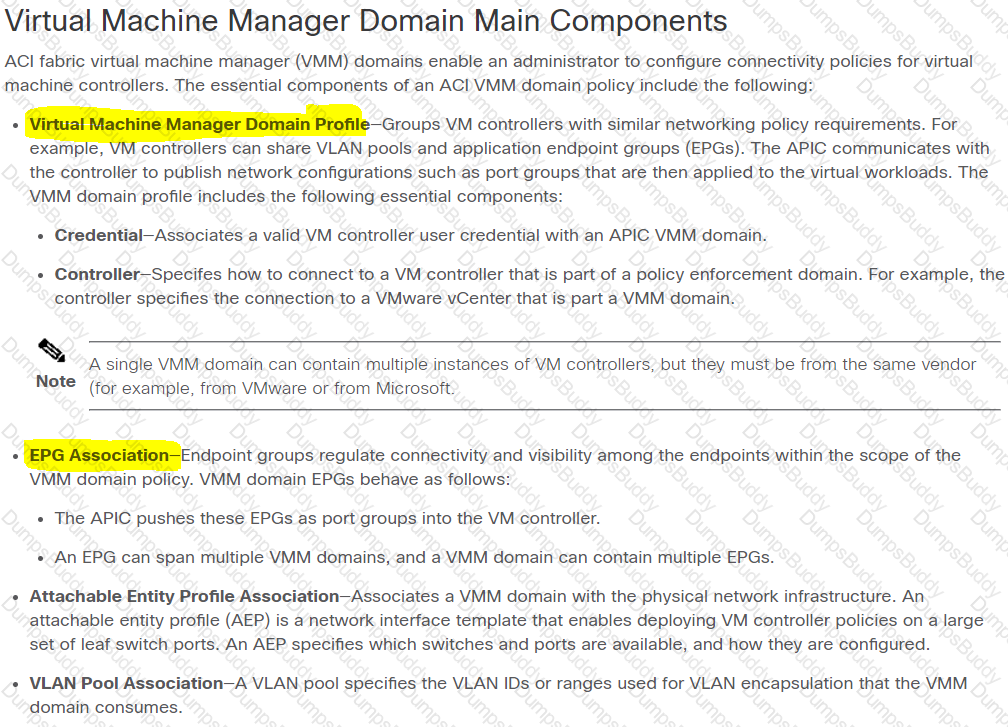
Which two components are essential parts of a Cisco ACI Virtual Machine Manager (VMM) domain policy configuration? (Choose two.)
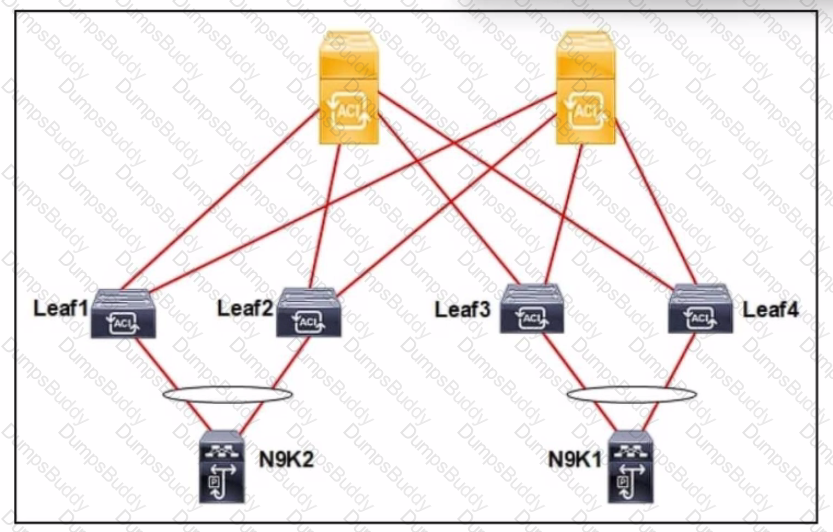
Refer to the exhibit. An engineer connects a Cisco ACI fabric to two different Cisco Nexus 9000 Series Switches. The fabric must be configured to ensure a loop-free topology and N9K1 be configured as the root bridge for VLAN 10. Which action meets these requirements?
Which endpoint learning operation is completed on the egress leaf switch when traffic is received from an L3Out?
An engineer must advertise a bridge domain subnet out of the ACI fabric to an OSPF neighbor. Which two configuration steps are required? (Choose two.)
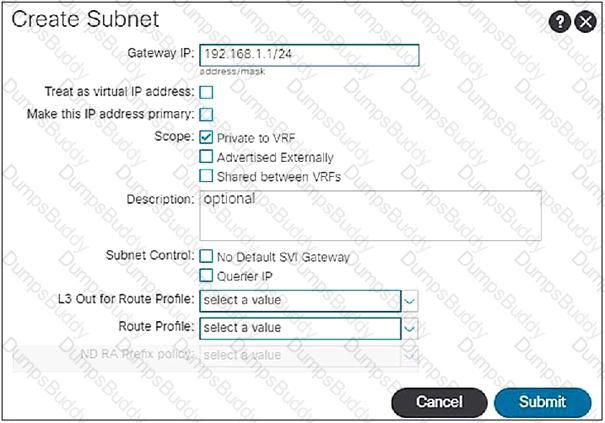
When the subnet is configured on a bridge domain, on which physical devices is the gateway IP address configured?
Which setting prevents the learning of Endpoint IP addresses whose subnet does not match the bridge domain subnet?
Which feature dynamically assigns or modifies the EPG association of virtual machines based on their attributes?
How many ARP requests are sent from leaf switches to perform host tracking for local endpoints?
In the context of ACI Multi-Site, when is the information of an endpoint (MAC/IP) that belongs to site 1 advertised to site 2 using the EVPN control plane?
An engineer is creating a configuration import policy that must terminate if the imported configuration is incompatible with the existing system. Which import mode achieves this result?
A Cisco ACI environment consists of multiple silent hosts that are often relocated between leaf switches. When the host is relocated, the bridge domain takes more than a few seconds to relearn the host’s new location. The requirement is to minimize the relocation impact and make the ACI fabric relearn the new location of the host faster. Which action must be taken to meet these requirements?
An engineer must configure a service graph for the policy-based redirect to redirect traffic to a transparent firewall. The policy must be vendor-agnostic to support any firewall appliance, Which two actions accomplish these goals? (Choose two.)
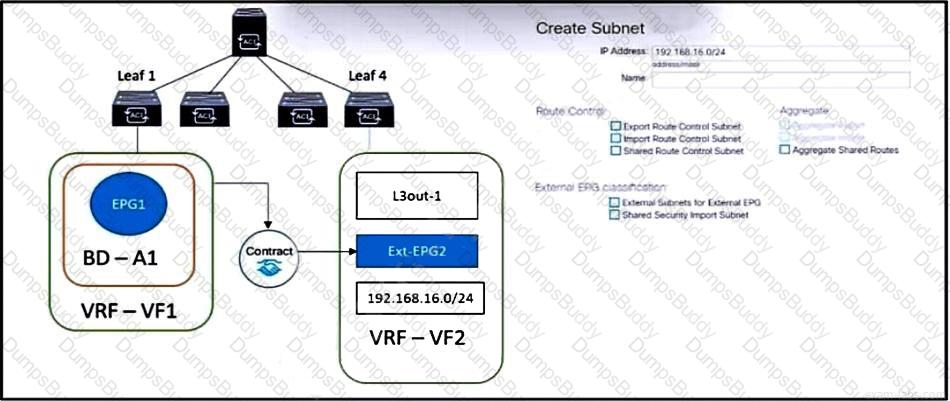
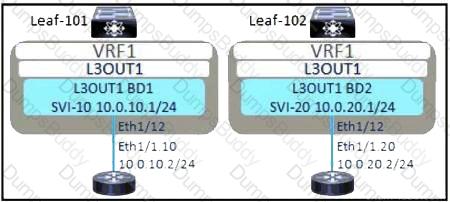
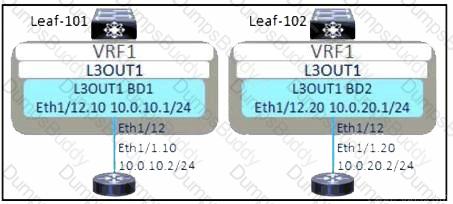
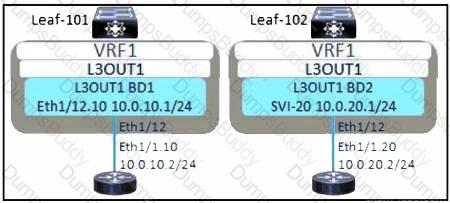
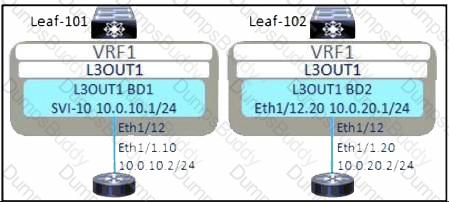
Refer to the exhibit. The external subnet and internal EPG1 must communicate with each other, and the L3Out traffic must leak into the VRF named "VF1". Which configuration set accomplishes these goals?
Refer to the exhibit.
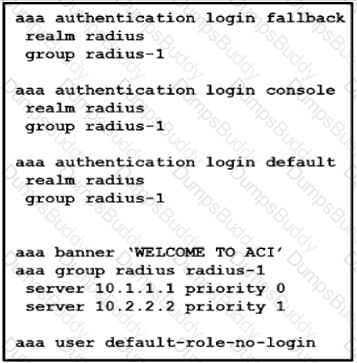
Which action should be taken to ensure authentication if the RADIUS servers are unavailable?
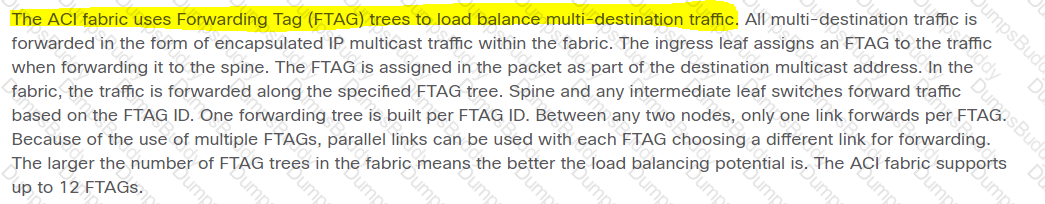
Which method does the Cisco ACI fabric use to load-balance multidestination traffic?
Which two dynamic routing protocols are supported when using Cisco ACI to connect to an external Layer 3 network? (Choose two.)
A packet is routed between two endpoints on different Cisco ACI leaf switches. Which VXLAN VNID is applied to the packet?
An engineer created a monitoring policy called Test in a Cisco ACI fabric and had to change the severity level of the monitored object Call home source. Which set of actions prevent the event from appearing in event reports?
An ACI engineer is implementing a Layer 3 out inside the Cisco ACI fabric that must meet these requirements:
The data center core switch must be connected to one of the leaf switches with a single 1G link.
The routes must be exchanged using a link-state routing protocol that supports hierarchical network design.
The data center core switch interface must be using 802.1Q tagging, and each vlan will be configured with a dedicated IP address.
Which set of steps accomplishes these goals?
Which feature should be disabled on a bridge domain when a default gateway for endpoints is on an external device instead of a Cisco ACI bridge domain SVI?
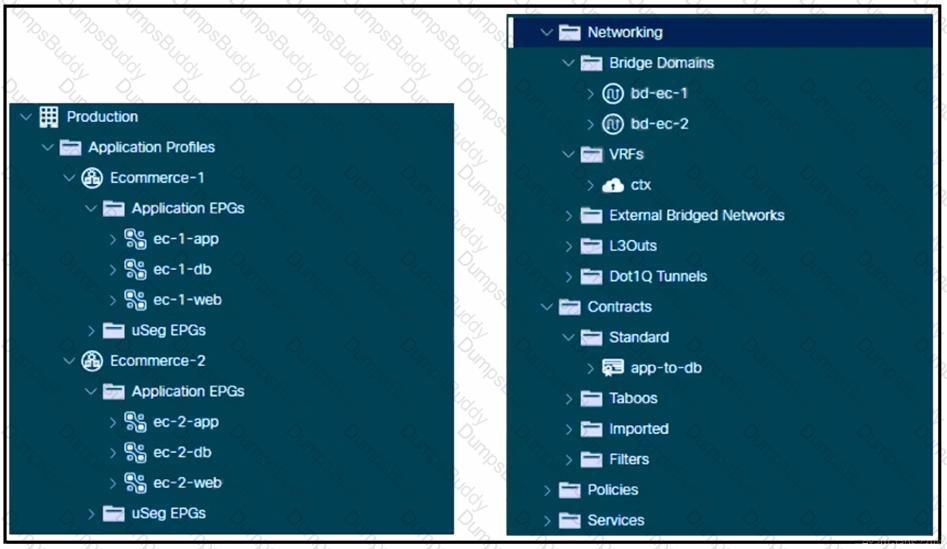
Refer to the exhibit. A Cisco ACI environment hosts two e-commerce applications. The default contract from a common tenant between different application tiers is used, and the applications work as expected. The customer wants to move to more specific contracts to prevent unwanted traffic between EPGs. A network administrator creates the app-to-db contract to meet this objective for the application and database tiers. The application EPGs must communicate only with their respective database EPGs. How should this contract be configured to meet this requirement?
Engineer must configure SNMP inside a Cisco ACI fabric. The engineer has created an SNMP Policy, called SNMP-policy and an SNMP Monitoring Group called SNMP-group1 that Contains five trap receivers. Which configuration set completes the configuration?
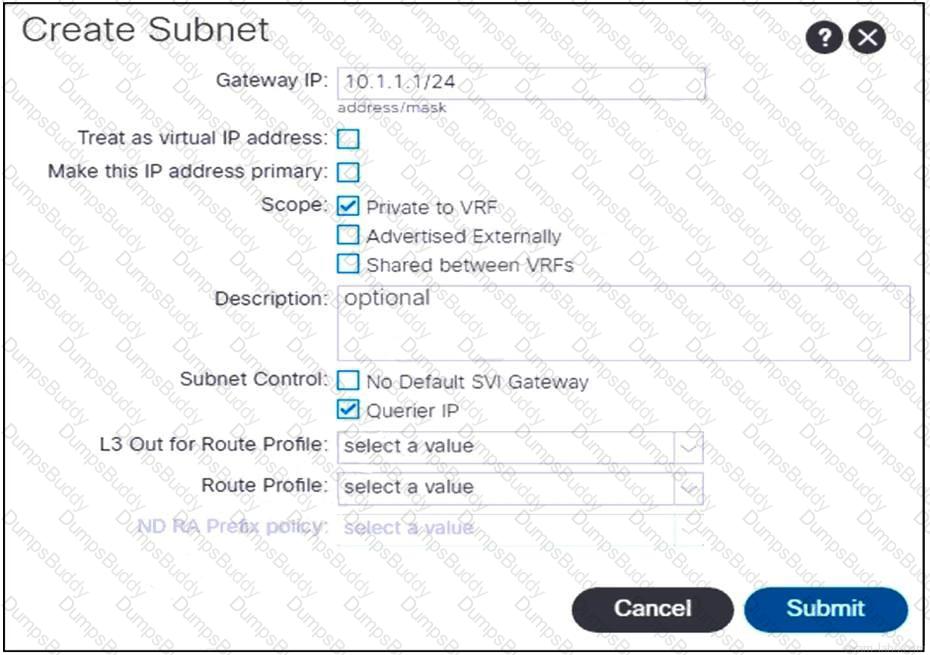
Refer to the exhibit. An engineer configures communication between the EPGs in different tenants. Which action should be taken to create the subnet?
A Cisco ACI endpoint group must have its gateway address migrated out of the ACI fabric. An engineer configures EPG-TEST with a static port binding and configures the encap VLAN with the required VLAN. Which configuration set must be used on the bridge domain to meet these requirements?
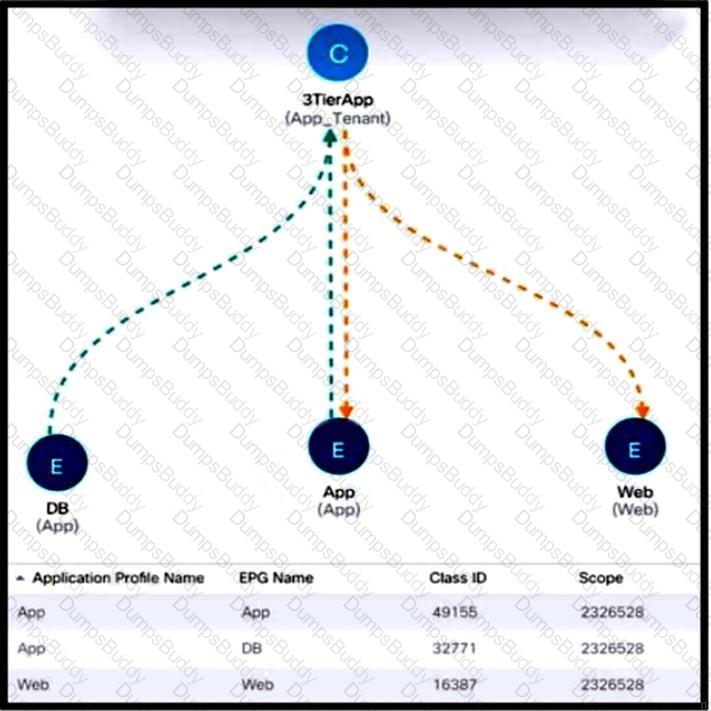
Refer to the exhibit. New e-commerce software is deployed on Cisco ACI fabric. The environment must meet these requirements:
The overall number of contracts must be reduced by reusing the existing contracts within a VRF when possible.
The e-commerce software must communicate only with software EPGs that are part of the same ANP.
The e-commerce software must be prevented from communicating with applications in different ANPs.
Which scope must be selected to meet these requirements?
An engineer discovered an outage on the mgmt0 port of Leaf113 and Leaf114. Both leaf switches were recently registered in the fabric and have health scores of 100. The engineer overs there is no IP address assigned to the mgmt0 interface of the switches. Which action resolves the outage?
What are two PBR characteristics of the Cisco ACI Active-Active Across Pods deployment mode in Cisco ACI Multi-Pod design? (Choose two.)
An engineer is implementing a Cisco ACI environment that consists of more than 20 servers. Two of the servers support only Cisco Discovery Protocol with no order link discovery protocol. The engineer wants the servers to be discovered automatically by the Cisco ACI fabric when connected. Which action must be taken to meet this requirement?
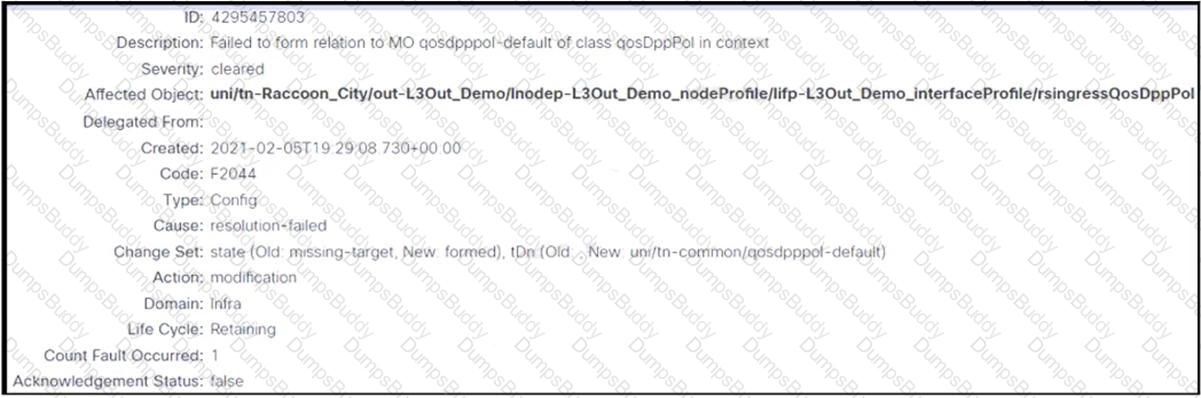
Refer to the exhibit. An engineer configures an L3Out but receives the error presented. Which action clears the fault?
A network engineer must design a method to allow the Cisco ACI to redirect traffic to the firewalls. Only traffic that matches specific L4-L7 policy rules should be redirected. The load must be distributed across multiple firewalls to scale the performance horizontally. Which action must be taken to meet these requirements?
An engineer must create a backup of the Cisco ACI fabric for disaster recovery purposes. The backup must be transferred over a secure and encrypted transport. The backup file must contain all user and password related information. The engineer also wants to process and confirm the backup file validity by using a Python script. This requires the data structure to have a format similar to a Python dictionary. Which configuration set must be used to meet these requirements?
Refer to the exhibit.
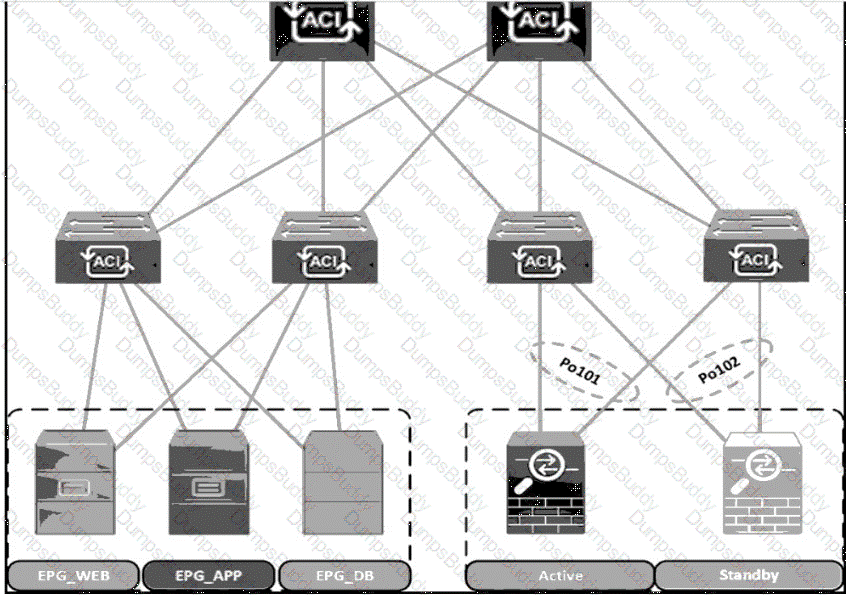
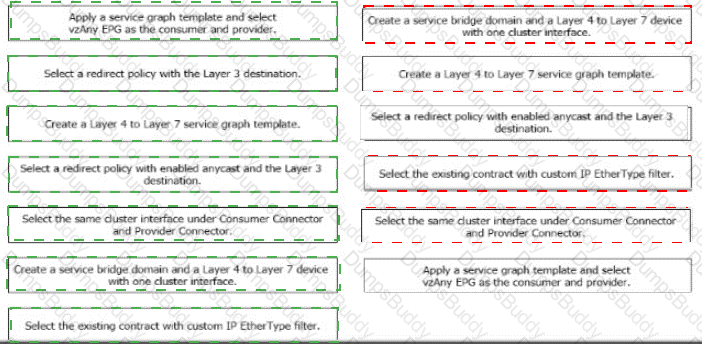
A Cisco ACI fabric is newly deployed, and the security team requires more visibility of all inter-EPG traffic flows. All traffic in a VRF must be forwarded to an existing firewall pair. During fallover, the standby firewall must continue to use the same IP and MAC as the primary firewall. Drag and drop the steps from the left Into the Implementation order on the right to configure the service graph that meets the requirements. (Not all steps are used.)
An engineer must deploy Cisco ACI across 10 geographically separated data centers. Which ACI site deployment feature enables the engineer to control which bridge domains contain Layer 2 flooding?
Network engineer configured a Cisco ACI fabric as follows:
• An EPG called EPG-A is created and associated with a VMM domain called North. •The EPG-A is associated with BD-A and is in an application profile called Apps-A.
• The BD-A is associated with VRF-1 in the Prod tenant.
Which port group must be selected to place VMs in EPG-A?
What is the advantage of implementing an active-active firewall cluster that is stretched across separate pods when anycast services are configured?
Which type of policy configures the suppression of faults that are generated from a port being down?
A network engineer is integrating a new Hyperflex storage duster into an existing Cisco ACI fabric The Hyperflex cluster must be managed by vCenter so a new vSphere Distributed switch must be created In addition the hardware discovery must be performed by a vendor-neutral discovery protocol Which set of steps meets these requirements'?

An engineer is implementing an out-of-band (OOB) management access for the Cisco ACI fabric. The secure access must meet these requirements:
• Only GUI and secure shell must be allowed to access the management interfaces of the ACIs.
• The only IP ranges that must be permitted to connect the fabric will be 10.10.10.0724 and 192.168.15.0/24.
Which configuration set meets these requirements?
Which feature is used to program policy CAM on a leaf switch without sending traffic from VM to the leaf?
Which two IP address types are available for transport over the ISN when they are configured from Cisco ACI Multi-Site Orchestrator? (Choose two.)
Refer to the exhibit.
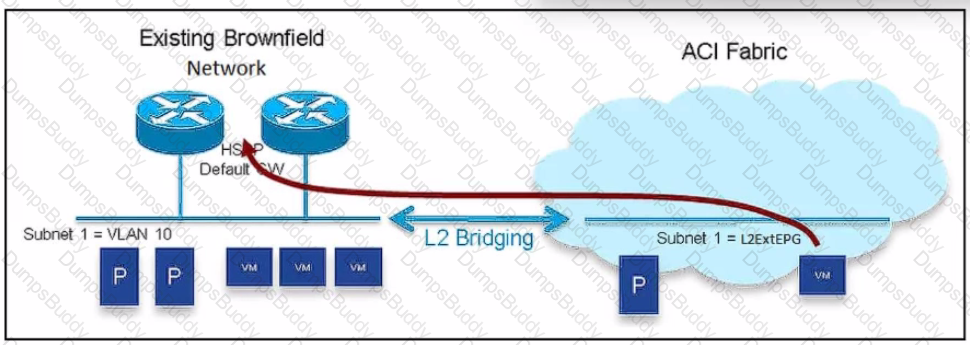
An engineer must migrate workloads from the brownfield network to the Cisco ACI fabric. The VLAN 10 default gateway remains in the router located in the brownfield Network. The bridge domain has already been associated with L20ut. Which two actions must be taken to migrate the workloads? (Choose two.)
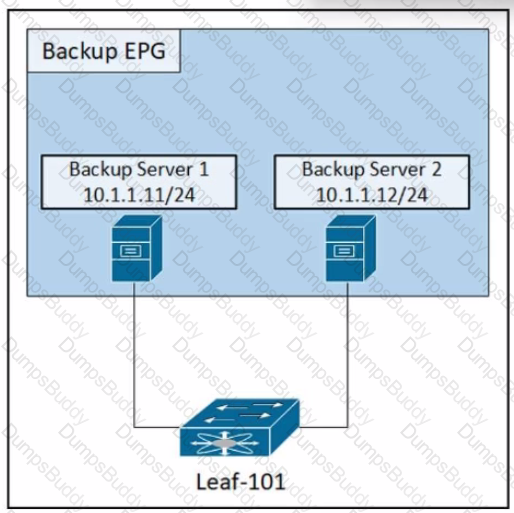
Refer to the exhibit. An engineer must disable the communication between the two backup servers in the backup EPG. Which action accomplishes this goal?
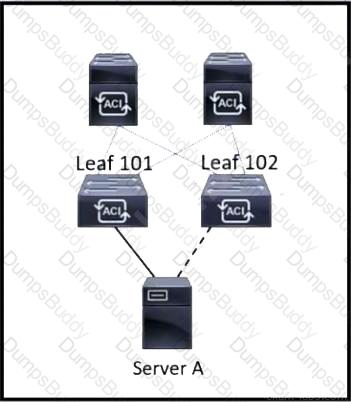
Refer to the exhibit. Server A is connected to the Cisco ACI fabric using two teamed interfaces. One interface in a team is configured as active and the other remains in standby mode. When a failover occurs and the standby interface becomes active, it uses its built-in MAC address to send traffic. Which bridge domain configuration must be applied to resolve the issue?
A network engineer is implementing a Layer 3 Out in the Cisco ACI fabric. The data center core switches must connect to a pair of leaf switches and exchange routes via a routing protocol. In addition, the implementation must meet these criteria;
• The external switch interface must use 802.1Q tagging.
• Access to the internet for the ACI fabric must be the L30ut.
• The L30ut must use a routing protocol that has rapid convergence time and low CPU usage.
Which configuration set meets these requirements?
An engineer configures a one-armed policy-based redirect service Insertion for an unmanaged firewall. The engineer configures these Cisco ACI objects:
a contract named All_Traffic_Allowed
a Layer 4 to Layer 7 device named FW-Device
a policy-based redirect policy named FW-1Arm-Policy-Based RedirectPolicy
Which configuration set redirects the traffic to the firewall?
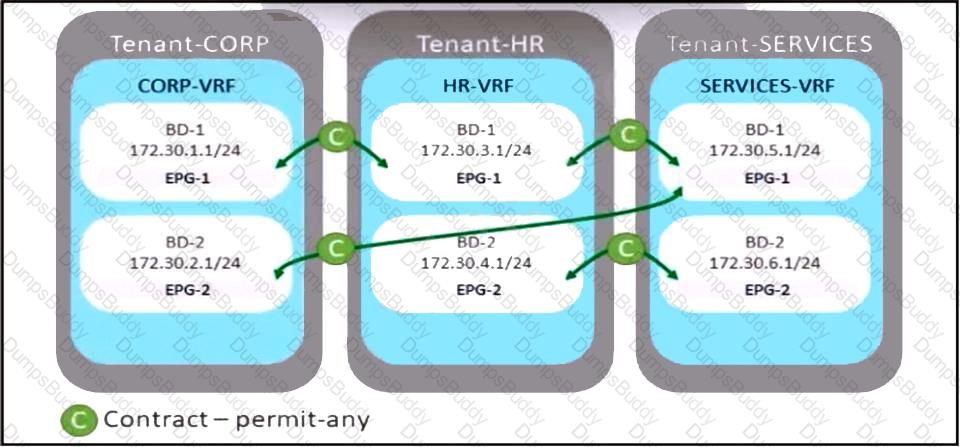
Refer to the exhibit. A company merges three of its departments: CORP, HR, and SERVICES, Currently, the connectivity between departments is achieved by using VRF route leaking. The requirement is to redesign the Cisco ACI networking architecture to communicate between EPGs and BDs from any tenant without configuring contracts or VRF route leaking. Which configuration meets these criteria?
Which routing protocol is supported between Cisco ACI spines and IPNs in a Cisco ACI Multi-Pod environment?
Which statement about ACI syslog is true or Which statement describes the ACI syslog?
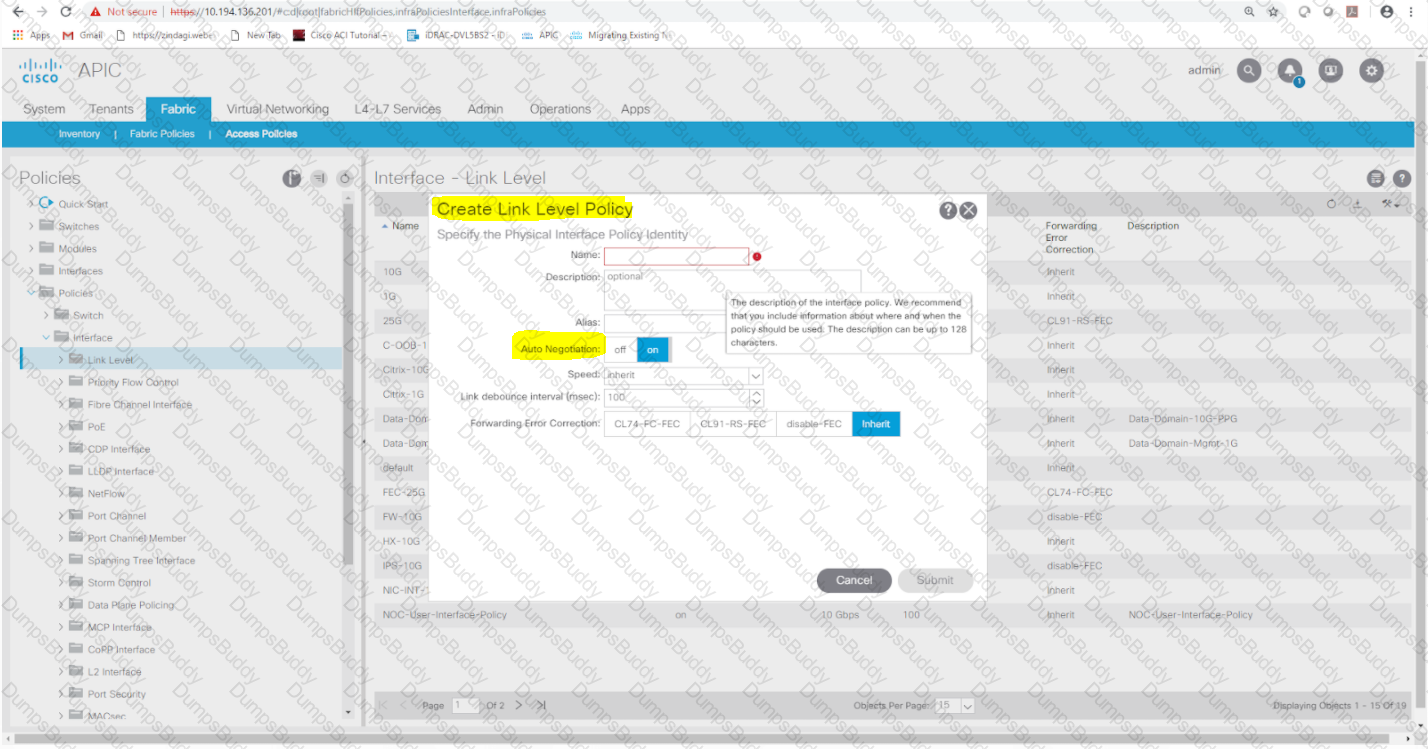
An engineer needs to deploy a leaf access port policy group in ACI Fabric to support the following requirements:
• Control the amount of application data flowing into the system
• Allow the newly connected device to auto-negotiate link speed with the leaf switch
Which two ACI policies must be configured to achieve these requirements? (Choose two.)
An engineer must attach an ESXi host to the Cisco ACI fabric. The host is connected to Leaf 1 and has its gateway IP address 10.10.10.254/24 configured inside the ACI fabric. A new wall is attached to Leaf 2 and mapped to the same EPG and BD as the ESXi host. The engineer must migrate the gateway of the ESXi host to the firewall. Which configuration set complishes this goal?
The customer is looking for redundant interconnection of the existing network to the new ACI fabric. Unicast and multicast traffic must be routed between the two networks. Which L3Out implementation meets these requirements?
Which protocol is used in a Multi-Pod topology to synchronize reachability information across pods?
In a Cisco ACI Multi-Site fabric, the Inter-Site BUM Traffic Allow option is enabled in a specific stretched bridge domain. What is used to forward BUM traffic to all endpoints in the same broadcast domain?
An engineer must securely export Cisco APIC configuration snapshots to a secure, offsite location The exported configuration must be transferred using an encrypted tunnel and encoded with a platform-agnostic data format that provides namespace support Which configuration set must be used?

An engineer is extending an EPG out of the ACI fabric using static path binding. Which statement about the endpoints is true?
In the context of VMM, which protocol between ACI leaf and compute hosts ensures that the policies are pushed to the leaf switches for immediate and on demand resolution immediacy?
A customer must upgrade the Cisco ACI fabric to use a feature from the new code release. However, there is no direct path from the current release to the desired one. Based on the Cisco APIC Upgrade/Downgrade Support Matrix, the administrator must go through one intermediate release.
Which set of steps must be taken to upgrade the fabric to the new release?
Which two types of interfaces are supported on border leaf switches to connect to an external router? (Choose two.)
Which Cisco APIC configuration prevents a remote network that is not configured on the bridge domain from
being learned by the fabric?
An ACI administrator notices a change in the behavior of the fabric. Which action must be taken to determine if a human intervention introduced the change?
How is broadcast forwarded in Cisco ACI Multi-Pod after ARP flooding is enabled?
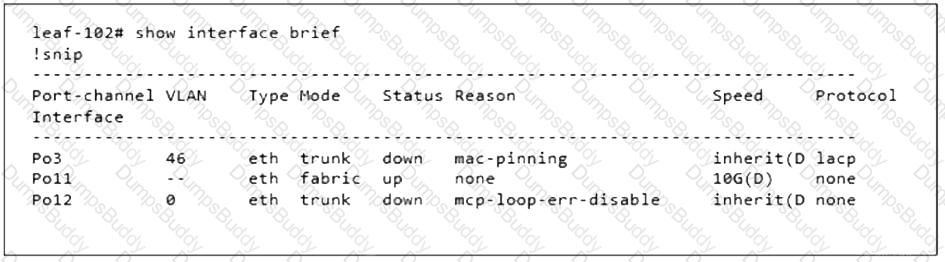
Refer to the exhibit. Which two configuration steps are completed before this output is generated? (Choose two.)
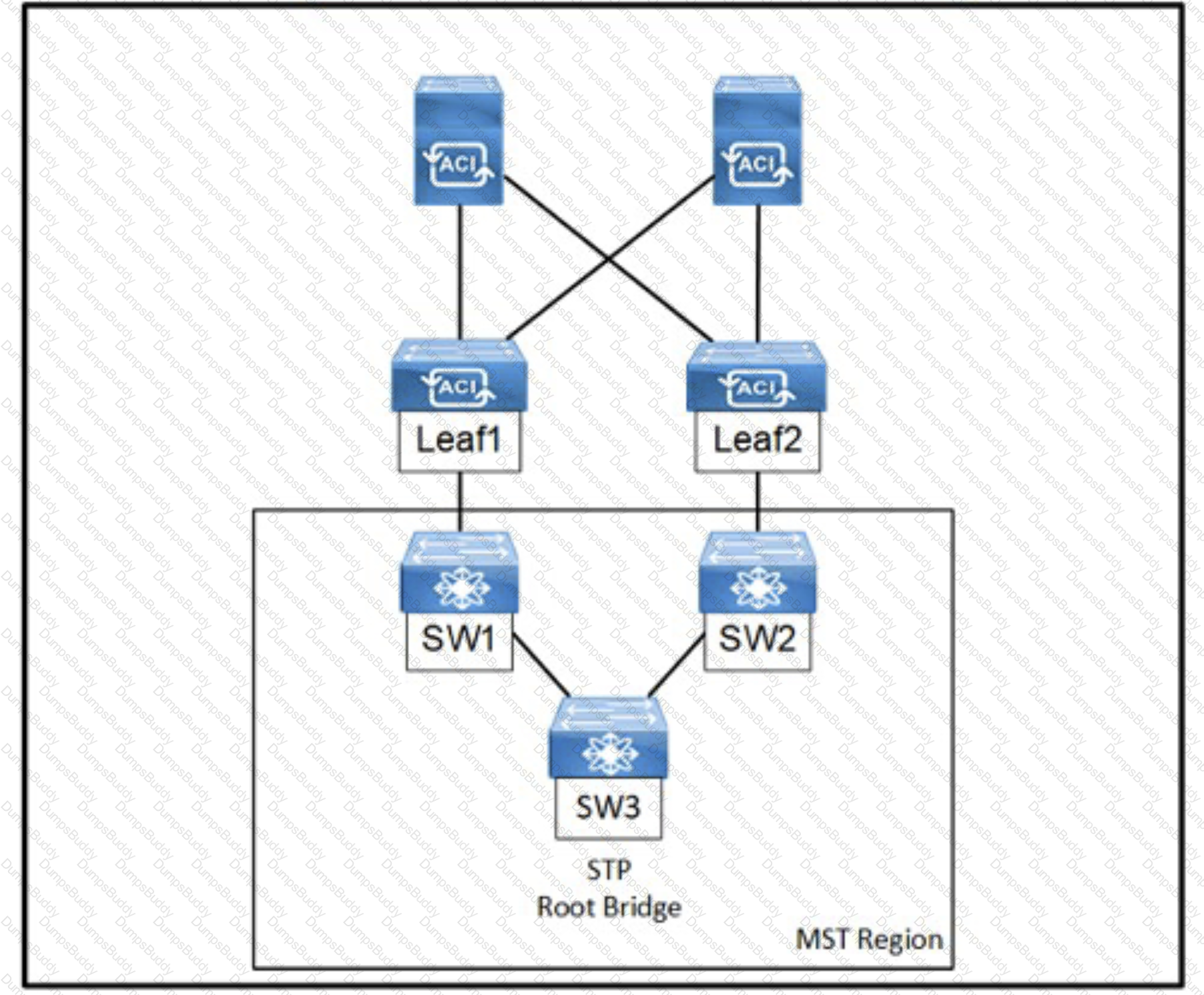
Refer to the exhibit, An engineer is deploying a Cisco ACI environment but experiences a STP loop between switch1 and switch2. Which configuration step is needed to break the STP loop?
Which protocol does ACI use to securely sane the configuration in a remote location?
What are two requirements for the IPN network when implementing a Multi-Pod ACI fabric? (Choose two.)
As part of a migration, legacy non-ACI switches must be connected to the Cisco ACI fabric. All non-ACI switches run per-VLAN RSTP. After the non-ACI switches are connected to Cisco ACI, the STP convergence caused a microloop and significant CPU spike on all switches. Which configuration on the interfaces of the external switches that face the Cisco ACI fabric resolves the problem?