202-450 LPIC-2 - Exam 202 (part 2 of 2), version 4.5 Questions and Answers
Which option within a Nginx server configuration section defines the file system path from which the content of the server is retrieved?
What command creates a SSH key pair? (Specify ONLY the command without any path or parameters)
What is the path to the global Postfix configuration file? (Specify the full name of the file, including path.)
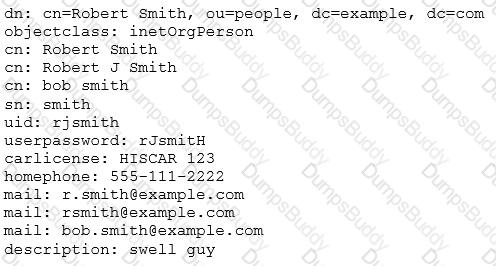
According to this LDIF excerpt, which organizational unit is Robert Smith part of? (Specify only the organizational unit.)
Which BIND option should be used to limit the IP addresses from which slave name servers may connect?
Which of the following statements allow the logical combinations of conditions in Sieve filters? (Choose two.)
Which of the following sshd configuration should be set to no in order to fully disable password based logins? (Choose two.)
Which Postfix command can be used to rebuild all of the alias database files with a single invocation and without the need for any command line arguments?
What command displays NFC kernel statistics? (Specify ONLY the command without any path or parameters.)
A company is transitioning to a new DNS domain name and wants to accept e-mail for both domains for all of its users on a Postfix server.
Which configuration option should be updated to accomplish this?
Which option in named.conf specifies which host are permitted to ask for domain name information from the server?
There is a restricted area in a site hosted by Apache HTTPD, which requires users to authenticate against the file /srv/www/security/sitepasswd.
Which command is used to CHANGE the password of existing users, without losing data, when Basic authentication is being used?
Which Apache HTTPD configuration directive is used to specify the method of authentication, e.g. None or Basic?
Which of the following authentication mechanisms are supported by Dovecot? (Choose three.)
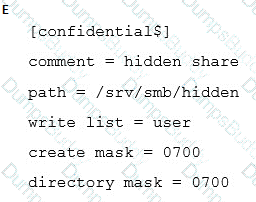
A user requests a “hidden” Samba share, named confidential, similar to the Windows Administration Share. How can this be configured?


Which action in a Sieve filter forwards a message to another email address without changing the message? (Specify ONLY the action’s name without any parameters.)
Which of the following statements in the ISC DHCPD configuration is used to specify whether or not an address pool can be used by nodes which have a corresponding host section in the configuration?
The content of which local file has to be transmitted to a remote SSH server in order to be able to log into the remote server using SSH keys?
The program vsftpd, running in a chroot jail, gives the following error:

Which of the following actions would fix the error?
After the installation of Dovecot, it is observed that the dovecot processes are shown in ps ax like this:

In order to associate the processes with users and peers, the username, IP address of the peer and the connection status, which of the following options must be set?
Which tool creates a Certificate Signing Request (CSR) for serving HTTPS with Apache HTTPD?
Which of the following statements is true regarding the NFSv4 pseudo file system on the NFS server?
To allow X connections to be forwarded from or through an SSH server, what configuration keyword must be set to yes in the sshd configuration file?
Which of the following Samba configuration parameters is functionally identical to the parameter read only=yes?
What is the name of the root element of the LDAP tree holding the configuration of an OpenLDAP server that is using directory based configuration? (Specify ONLY the element’s name without any additional information.)
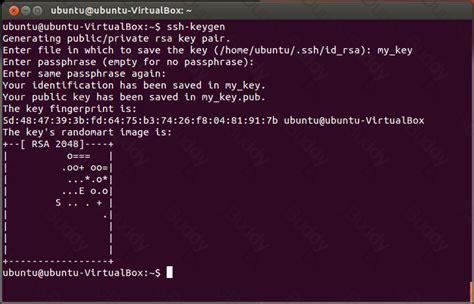 How to Use ssh-keygen to Generate a New SSH Key?
How to Use ssh-keygen to Generate a New SSH Key?
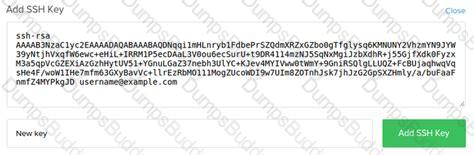 How To Configure SSH Key-Based Authentication on a Linux Server
How To Configure SSH Key-Based Authentication on a Linux Server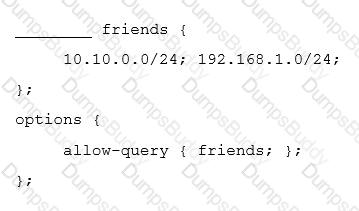
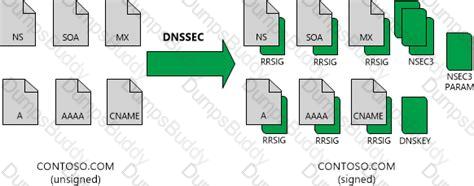 What is DNSSEC on DNS Server in Windows Server?1
What is DNSSEC on DNS Server in Windows Server?1 How DNSSEC Works | Cloudflare
How DNSSEC Works | Cloudflare

