200-201 Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) Questions and Answers
After a large influx of network traffic to externally facing devices, a security engineer begins investigating what appears to be a denial of service attack When the packet capture data is reviewed, the engineer notices that the traffic is a single SYN packet to each port Which type of attack is occurring?
What technology should be used for the verified and secure exchange of public keys between entities Tom3350050239 and Dan0932353050?
What is the impact of false negative alerts when compared to true negative alerts?
Which difficulty occurs when log messages are compared from two devices separated by a Layer 3 device that performs Network Address Translation?
An employee received an email from a colleague’s address asking for the password for the domain controller. The employee noticed a missing letter within the sender’s address. What does this incident describe?
An analyst see that this security alert "Default-Botnet-Communication-Detection-By-Endpoint" has been raised from the IPS. The analyst checks and finds that an endpoint communicates to the C&C. How must an impact from this event be categorized?
What is the difference between inline traffic interrogation and traffic mirroring?
Which signature impacts network traffic by causing legitimate traffic to be blocked?
Refer to the exhibit.

An analyst received this alert from the Cisco ASA device, and numerous activity logs were produced. How should this type of evidence be categorized?
Which type of attack involves sending input commands to a web server to access data?
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
Which obfuscation technique is the attacker using?
Which type of data must an engineer capture to analyze payload and header information?
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?
Refer to the exhibit.
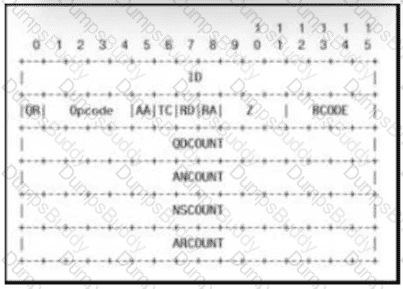
Which field contains DNS header information if the payload is a query or a response?
A large load of data is being transferred to an external destination via UDP 53 port. Which obfuscation technique is used?
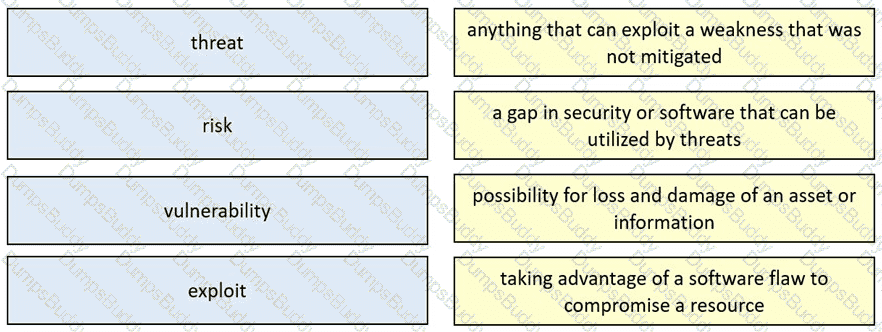
Drag and drop the security concept from the left onto the example of that concept on the right.
Refer to the exhibit.
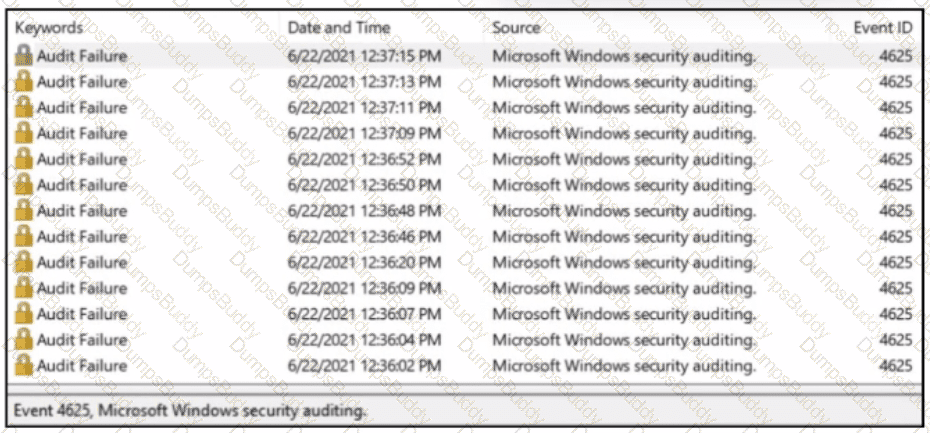
A SOC analyst received a message from SIEM about abnormal activity on the Windows server The analyst checked the Windows event log and saw numerous Audit Failures logs. What is occurring?
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email. When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
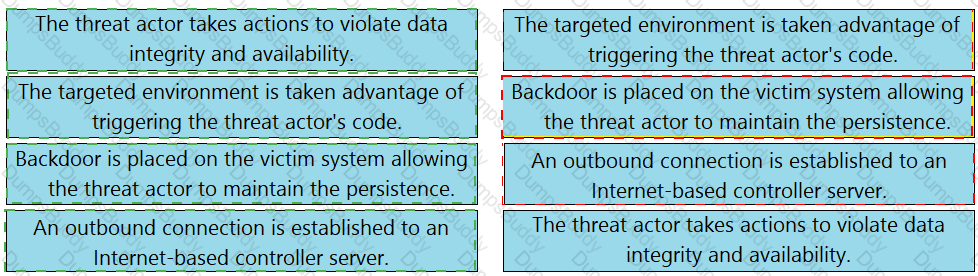
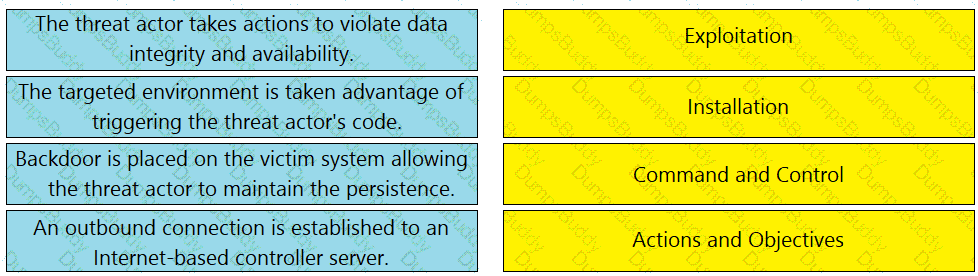
Drag and drop the definitions from the left onto the phases on the right to classify intrusion events according to the Cyber Kill Chain model.
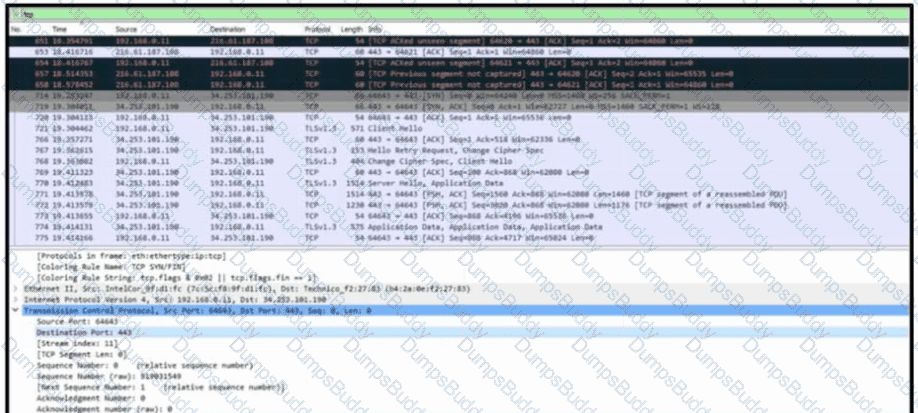
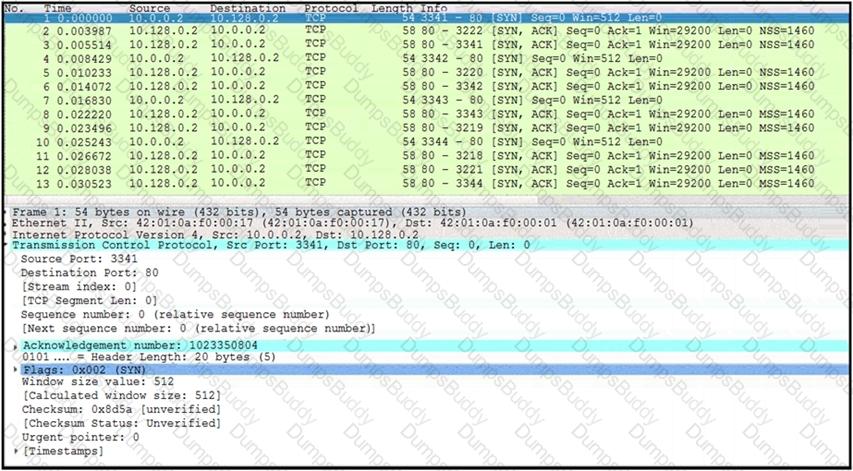
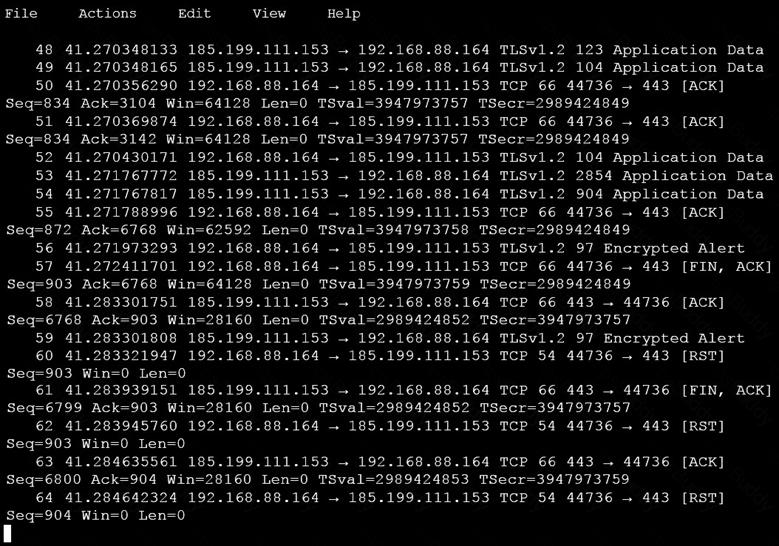
Refer to the exhibit. A communication issue exists between hosts 192.168.0.11 and 34.253.101.190. What is a description of the initial TCP connection?
Drag and drop the type of evidence from the left onto the description of that evidence on the right.

What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?
Which technique obtains information about how the system works without knowing it's design details?
What causes events on a Windows system to show Event Code 4625 in the log messages?
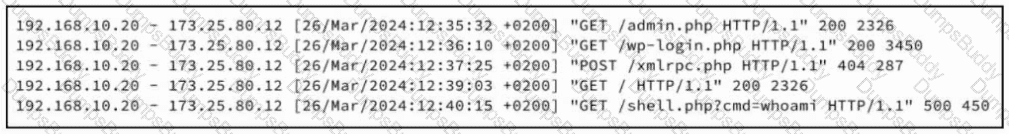
Refer to the exhibit. A security analyst examines Apache web server logs and notices the entries. Which security concern is occurring?
A company receptionist received a threatening call referencing stealing assets and did not take any action assuming it was a social engineering attempt. Within 48 hours, multiple assets were breached, affecting the confidentiality of sensitive information. What is the threat actor in this incident?
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
A security engineer must investigate a recent breach within the organization. An engineer noticed that a breached workstation is trying to connect to the domain "Ranso4730-mware92-647". which is known as malicious. In which step of the Cyber Kill Chain is this event?
In digital communications, which method is recommended for securely exchanging public keys between users T0n2262144790 and D4n4126220794?
A member of the SOC team is checking the dashboard provided by the Cisco Firepower Manager for further Isolation actions. According to NIST SP800-61, in which phase of incident response is this action?
Which action should be taken if the system is overwhelmed with alerts when false positives and false negatives are compared?
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
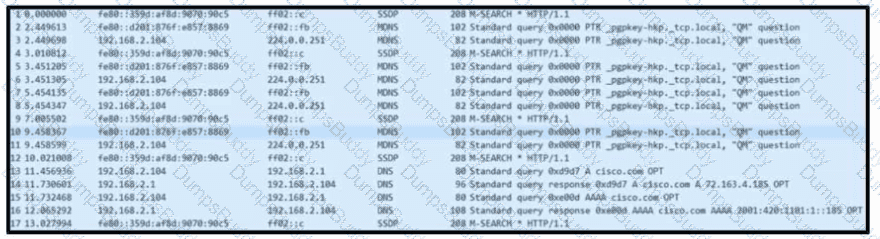
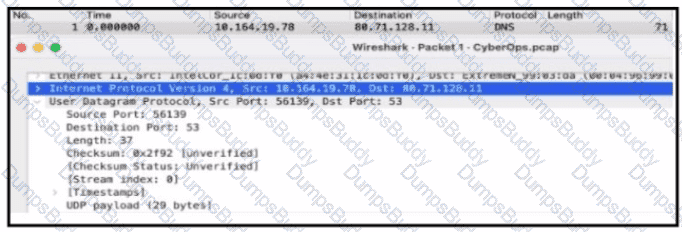
Refer to the exhibit. Based on the .pcap file, which DNS server is used to resolve cisco.com?
An engineer must investigate suspicious connections. Data has been gathered using a tcpdump command on a Linux device and saved as sandboxmatware2022-12-22.pcaps file.The engineer is trying to open the tcpdump in the Wireshark tool. What is the expected result?
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
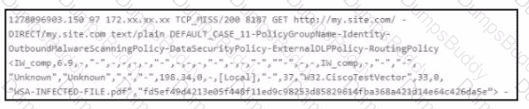
Which event artifact is used to identify HTTP GET requests for a specific file?
Developers must implement tasks on remote Windows environments. They decided to use scripts for enterprise applications through PowerShell. Why does the functionality not work?
A system administrator is ensuring that specific registry information is accurate.
Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
Refer to the exhibit.
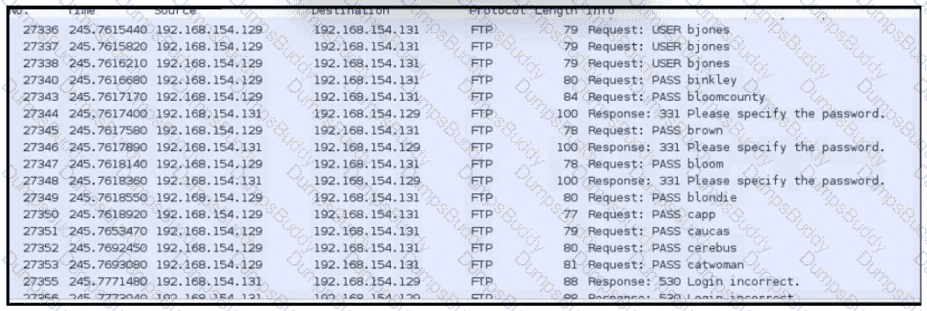
An analyst was given a PCAP file, which is associated with a recent intrusion event in the company FTP server Which display filters should the analyst use to filter the FTP traffic?
Which type of data consists of connection level, application-specific records generated from network traffic?
What is personally identifiable information that must be safeguarded from unauthorized access?

Refer to the exhibit. A SOC team member receives a case from his colleague with notes attached. The artifacts and alerts associated with the case must be analyzed and a conclusion must be provided. What is the cause of the alert?
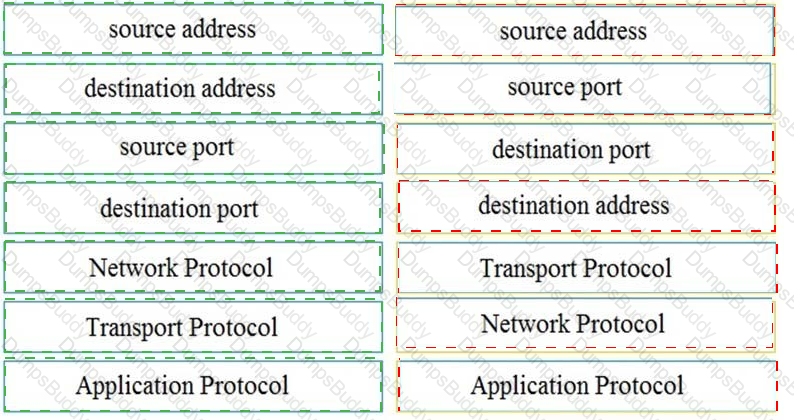
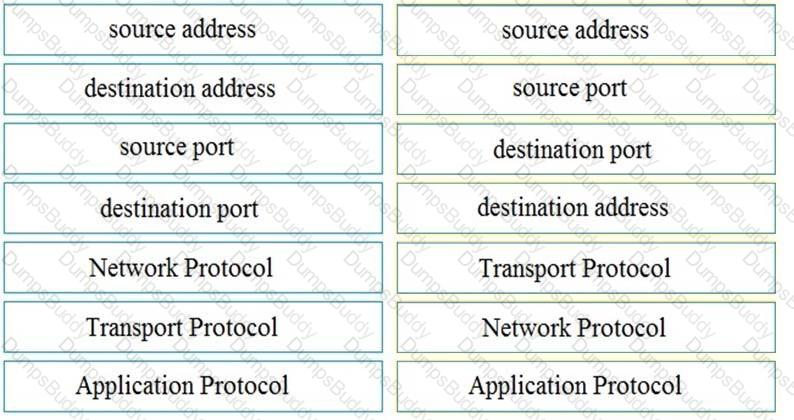
A threat actor penetrated an organization's network. Using the 5-tuple approach, which data points should the analyst use to isolate the compromised host in a grouped set of logs?
During which phase of the forensic process are tools and techniques used to extract information from the collected data?
Which security monitoring data type is associated with application server logs?
A security engineer must determine why a new core application does not work as desired The client can send requests toward the application server but receives no response One of the requirements is to gather all packets Data needs to be reliable without any delay or packet drops Which solution best meets this need?
Refer to the exhibit.
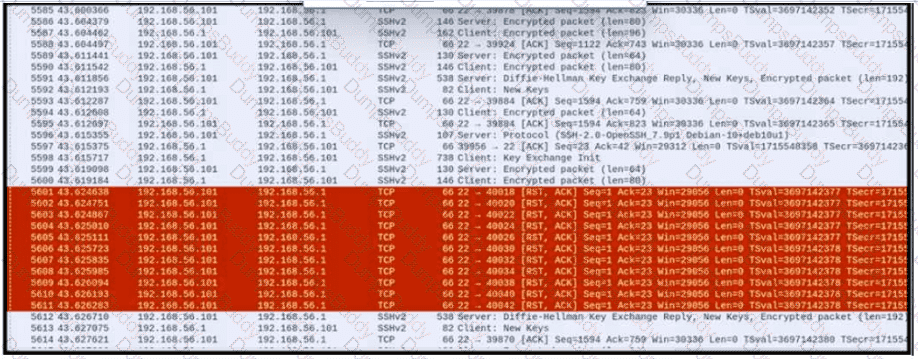
An engineer is analyzing a PCAP file after a recent breach An engineer identified that the attacker used an aggressive ARP scan to scan the hosts and found web and SSH servers. Further analysis showed several SSH Server Banner and Key Exchange Initiations. The engineer cannot see the exact data being transmitted over an encrypted channel and cannot identify how the attacker gained access How did the attacker gain access?
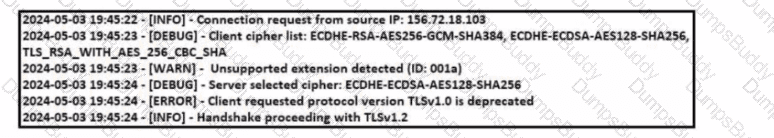
When communicating via TLS, the client initiates the handshake to the server and the server responds back with its certificate for identification.
Which information is available on the server certificate?
Refer to the exhibit.
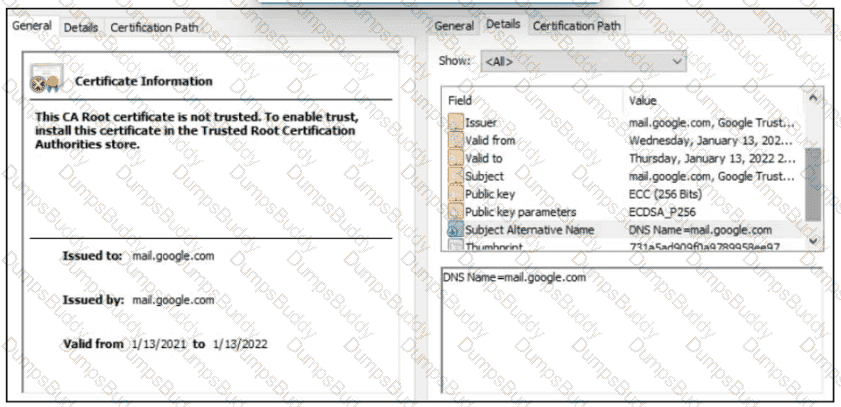
A company employee is connecting to mail google.com from an endpoint device. The website is loaded but with an error. What is occurring?
A user reports that a mobile application is working very slowly. A DDoS detection tool reports high-volume traffic. During which phase does the CSIRT ensure that the incident does not continue and confirm that the organization has taken the required actions?
A network engineer informed a security team of a large amount of traffic and suspicious activity from an unknown source to the company DMZ server The security team reviewed the data and identified a potential DDoS attempt According to NIST, at which phase of incident response is the security team?
An employee reports that someone has logged into their system and made unapproved changes, files are out of order, and several documents have been placed in the recycle bin. The security specialist reviewed the system logs, found nothing suspicious, and was not able to determine what occurred. The software is up to date; there are no alerts from antivirus and no failed login attempts. What is causing the lack of data visibility needed to detect the attack?
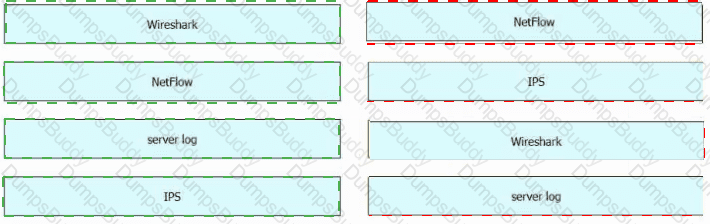
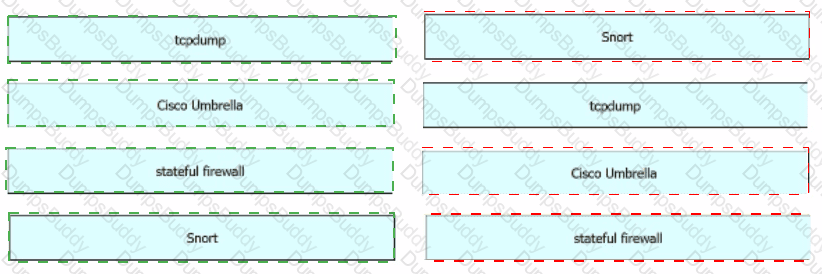
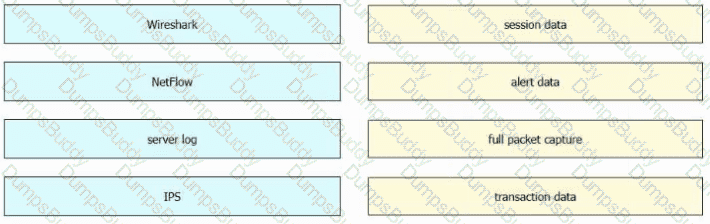
Drag and drop the data sources from the left onto the corresponding data types on the right.
A CMS plugin creates two files that are accessible from the Internet myplugin html and exploitable php A newly discovered exploit takes advantage of an injection vulnerability m exploitable php To exploit the vulnerability an HTTP POST must be sent with specific variables to exploitable php A security engineer notices traffic to the webserver that consists of only HTTP GET requests to myplugin html Which category does this activity fall under?
Which metric should be used when evaluating the effectiveness and scope of a Security Operations Center?
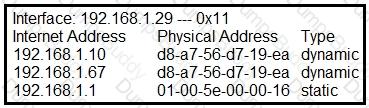
A suspicious user opened a connection from a compromised host inside an organization. Traffic was going through a router and the network administrator was able to identify this flow. The admin was following 5-tuple to collect needed data. Which information was gathered based on this approach?
A company encountered a breach on its web servers using IIS 7 5 Dunng the investigation, an engineer discovered that an attacker read and altered the data on a secure communication using TLS 1 2 and intercepted sensitive information by downgrading a connection to export-grade cryptography. The engineer must mitigate similar incidents in the future and ensure that clients and servers always negotiate with the most secure protocol versions and cryptographic parameters. Which action does the engineer recommend?
Which system monitors local system operation and local network access for violations of a security policy?
What is the name of the technology that searches for and reports on known weaknesses and flaws present in an organization’s IT infrastructure?
A developer is working on a project using a Linux tool that enables writing processes to obtain these required results:
If the process is unsuccessful, a negative value is returned.
If the process is successful, 0 value is returned to the child process, and the process ID is sent to the parent process.
Which component results from this operation?
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
Refer to the exhibit.
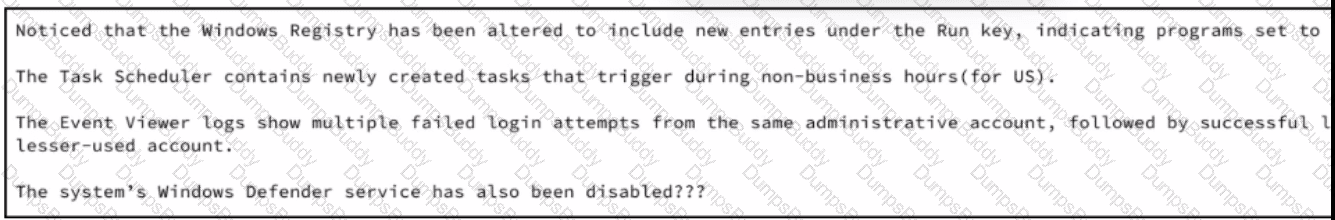
A security analyst wraps up the shift and passed open ticket notes to the night shift SOC team analyst. The ticket name in question is "Investigating suspicious activity on a Windows Server’’. Which operating system components must the analyst prioritize to uncover the attacker's persistence mechanisms?
What is the impact of false positive alerts on business compared to true positive?
What is the practice of giving an employee access to only the resources needed to accomplish their job?
What is the difference between deep packet inspection and stateful inspection?
An engineer received an alert affecting the degraded performance of a critical server Analysis showed a heavy CPU and memory load What is the next step the engineer should take to investigate this resource usage7
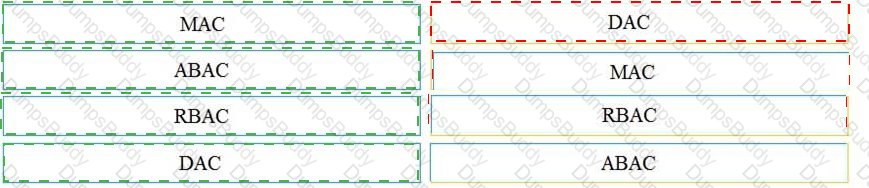
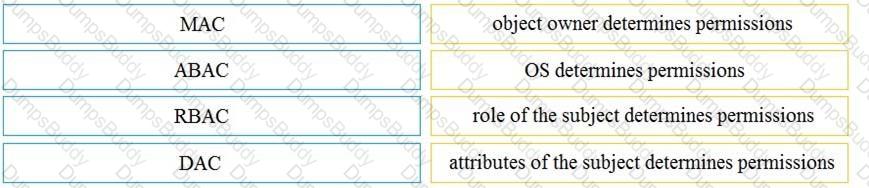
Drag and drop the access control models from the left onto the correct descriptions on the right.
Which evasion method involves performing actions slower than normal to prevent detection?
Refer to the exhibit.
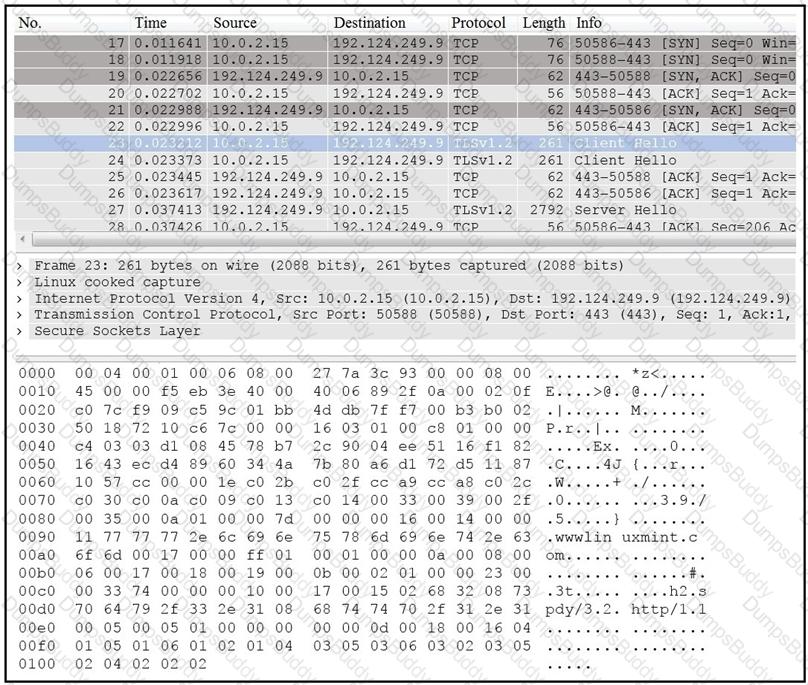
Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.
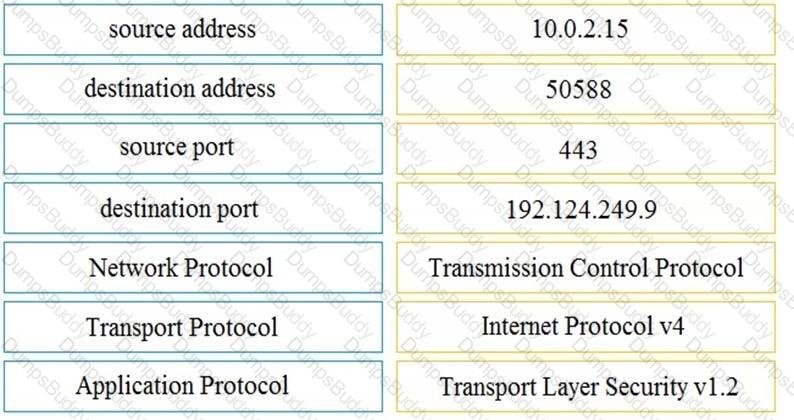
What describes the impact of false-positive alerts compared to false-negative alerts?
What describes the concept of data consistently and readily being accessible for legitimate users?
STION NO: 102
Refer to the exhibit.
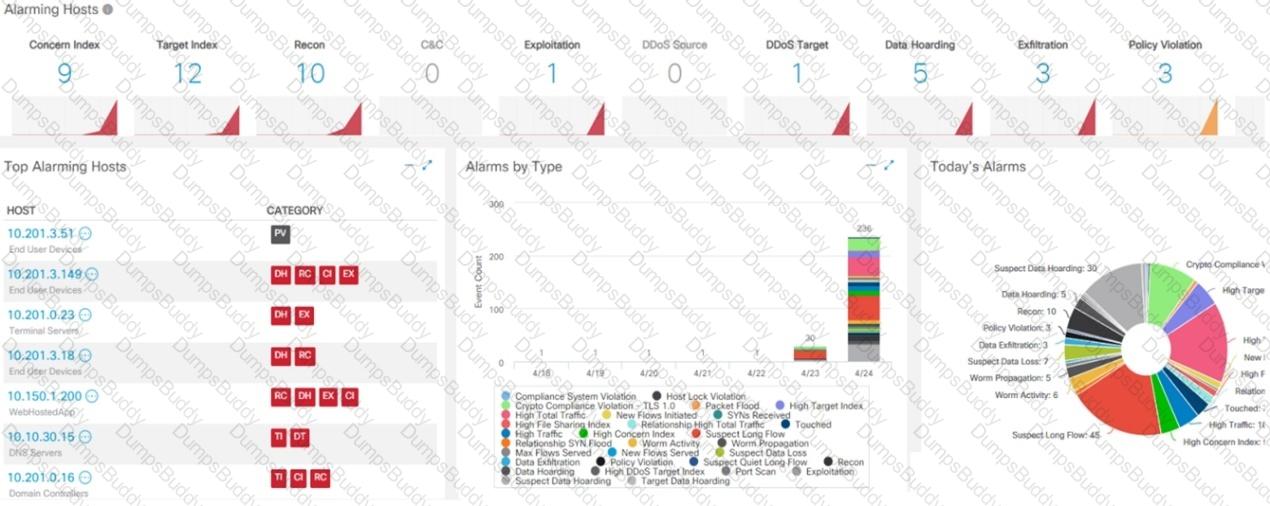
What is the potential threat identified in this Stealthwatch dashboard?
Which vulnerability type is used to read, write, or erase information from a database?
What is the difference between inline traffic interrogation (TAPS) and traffic mirroring (SPAN)?
A security expert is working on a copy of the evidence, an ISO file that is saved in CDFS format. Which type of evidence is this file?
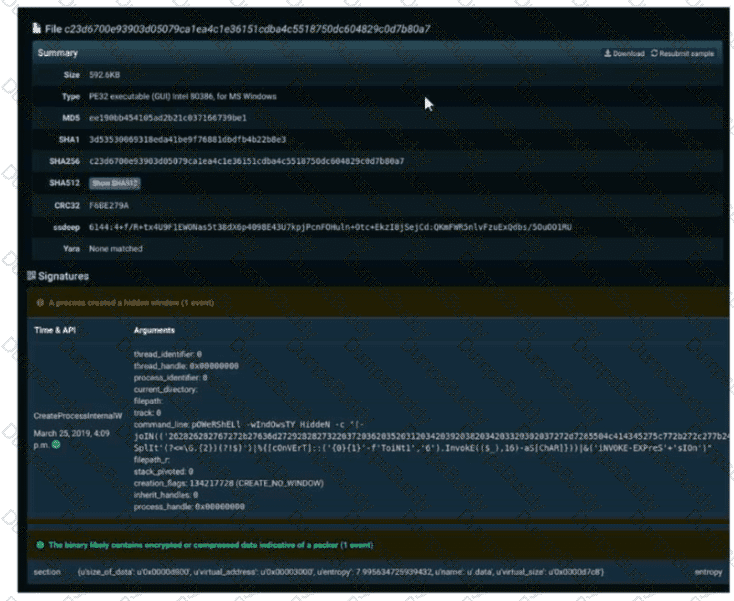
Refer to the exhibit. A SOC engineer is analyzing Cuckoo Sandbox report for a file that has been identified as suspicious by the endpoint security system. What is the state of the file?
Which principle is being followed when an analyst gathers information relevant to a security incident to determine the appropriate course of action?
Exhibit.
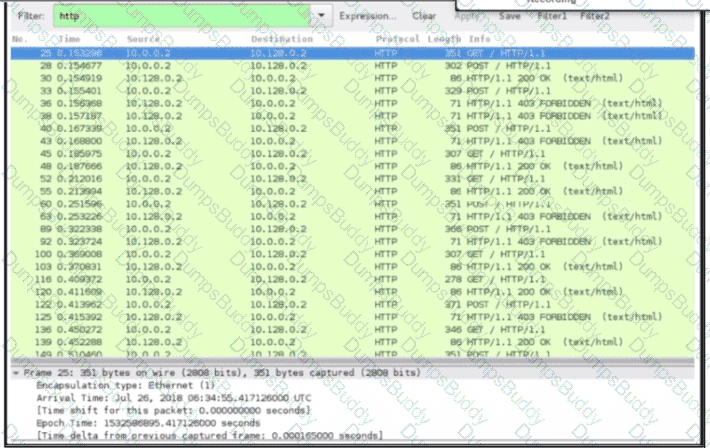
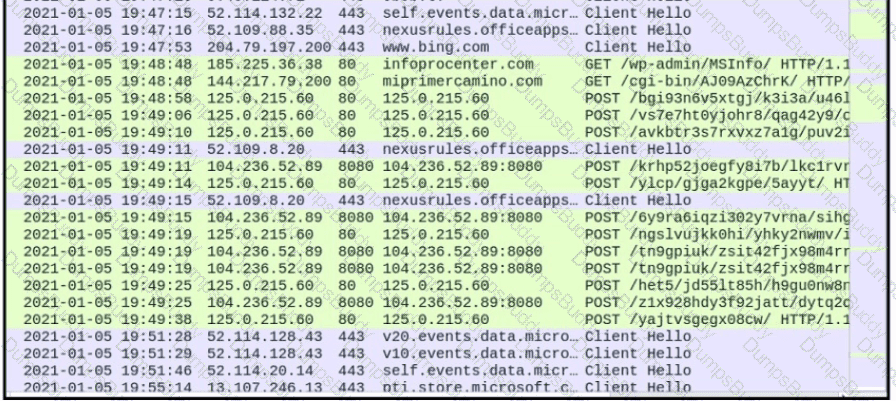
An engineer received a ticket about a slowdown of a web application, Drug analysis of traffic, the engineer suspects a possible attack on a web server. How should the engineer interpret the Wiresharat traffic capture?
Drag and drop the technologies from the left onto the data types the technologies provide on the right.
If a web server accepts input from the user and passes it to a bash shell, to which attack method is it vulnerable?
Refer to the exhibit.
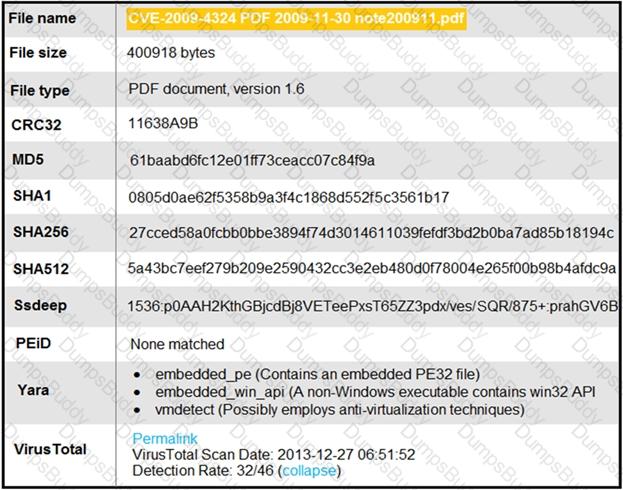
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?
Which incidence response step includes identifying all hosts affected by an attack?
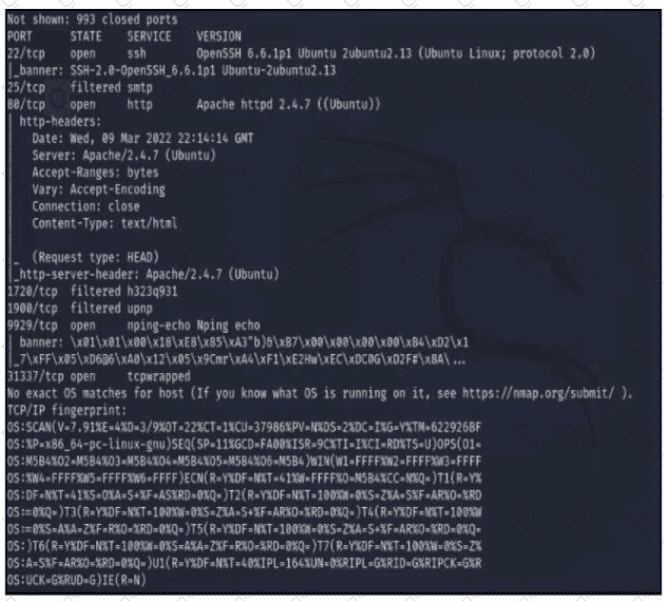
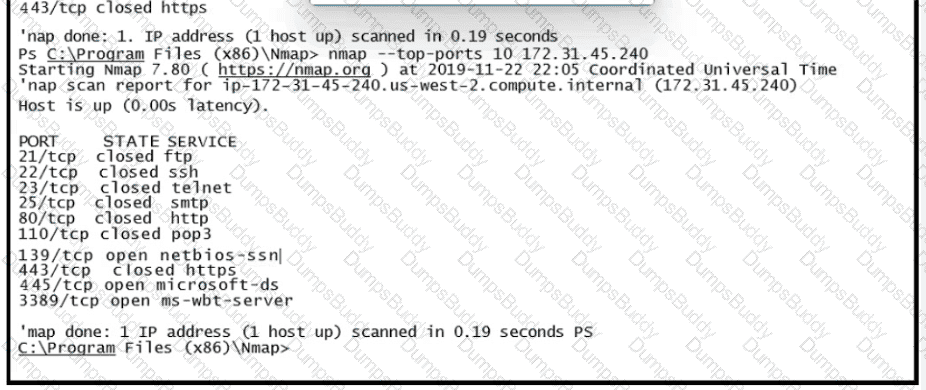
Refer to the exhibit A penetration tester runs the Nmap scan against the company server to uncover possible vulnerabilities and exploit them Which two elements can the penetration tester identity from the scan results? (Choose two.)
An engineer is investigating a case of the unauthorized usage of the “Tcpdump” tool. The analysis revealed that a malicious insider attempted to sniff traffic on a specific interface. What type of information did the malicious insider attempt to obtain?
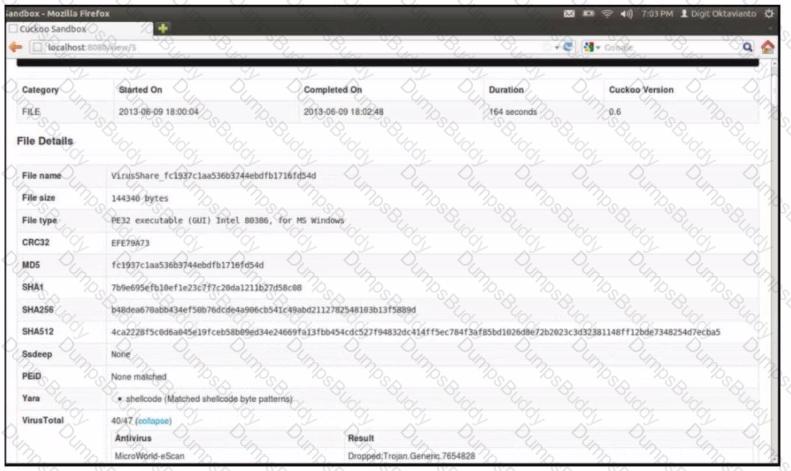


 Table Description automatically generated
Table Description automatically generated
 Graphical user interface, application Description automatically generated
Graphical user interface, application Description automatically generated