1z0-116 Oracle Database Security Administration Questions and Answers
You configured Kerberos authentication for databases running on servers A and B.
However a database link connecting the database on server A to the database on server B fails with ORA-12638 Credential retrieval failed.
Where must you make a change to sqlnet.ora to allow the database link to use its stored credentials Instead of trying to use Kerberos?
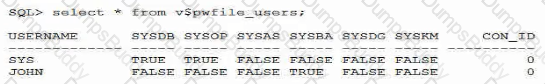
Database Vault realm r protects all tables In the fin schema from DBA access User fin is configured as the owner in realm R.
You must also prevent access to realm r protected tables by user FIN. Which achieves this?
You are Implementing a security policy that makes use of the USERENV namespace.
Which USERRENV value does not change for the duration of a session?
Examine this sqlnet.ora file used by a client application:
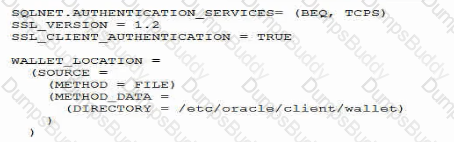
Which three are found in the wallet specified by the directory parameter?
Which three are part of an access control list (ACL) when using Real Application Security?